Charles Sturt Uni: ITC506 Information Technology Ethics Assignment
VerifiedAdded on 2021/04/17
|8
|2135
|26
Homework Assignment
AI Summary
This assignment analyzes an ethical dilemma in information technology using the Doing Ethics Technique (DET). The scenario involves a software development project where the manager prioritizes timely delivery over thorough testing, leading to potential security risks. The assignment, completed by a student at Charles Sturt University, examines the facts, identifies stakeholders (client company, consumers, and the development company), and explores ethical issues such as the violation of security and compromising quality for monetary gain. It evaluates options like extending the delivery date and the implications of each choice, ultimately concluding that convincing the client to extend the deadline is the best solution to ensure software quality and maintain the company's reputation. The assignment also references literature to support its arguments and adheres to APA style for referencing.

SCHOOL OF COMPUTING AND MATHS, Charles Sturt University
Information Technology Ethics
Assignment 1: Doing Ethics Technique
Your Name
Student Number
Word Count:1000
Information Technology Ethics
Assignment 1: Doing Ethics Technique
Your Name
Student Number
Word Count:1000
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
Information Technology Ethics
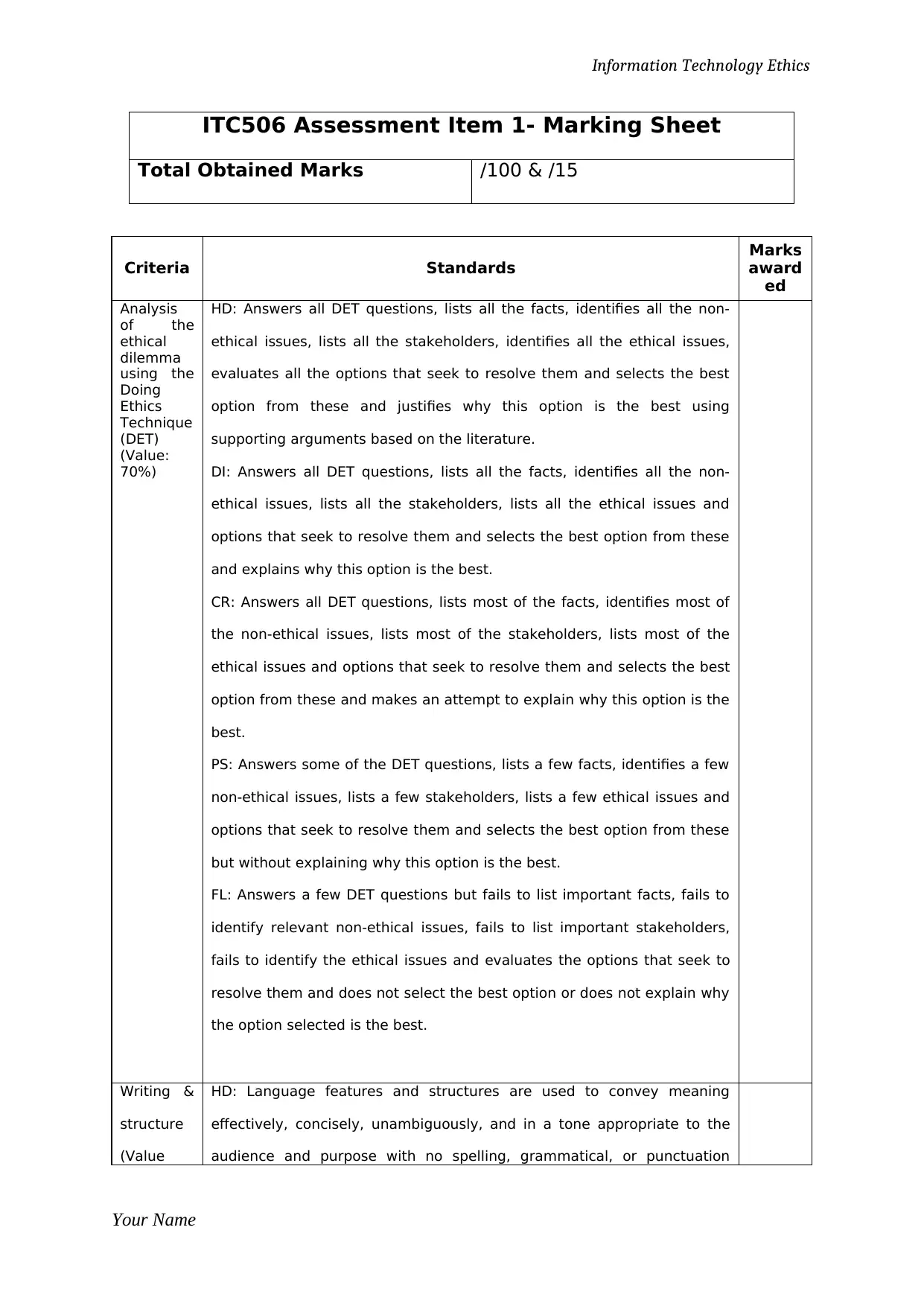
ITC506 Assessment Item 1- Marking Sheet
Total Obtained Marks /100 & /15
Criteria Standards
Marks
award
ed
Analysis
of the
ethical
dilemma
using the
Doing
Ethics
Technique
(DET)
(Value:
70%)
HD: Answers all DET questions, lists all the facts, identifies all the non-
ethical issues, lists all the stakeholders, identifies all the ethical issues,
evaluates all the options that seek to resolve them and selects the best
option from these and justifies why this option is the best using
supporting arguments based on the literature.
DI: Answers all DET questions, lists all the facts, identifies all the non-
ethical issues, lists all the stakeholders, lists all the ethical issues and
options that seek to resolve them and selects the best option from these
and explains why this option is the best.
CR: Answers all DET questions, lists most of the facts, identifies most of
the non-ethical issues, lists most of the stakeholders, lists most of the
ethical issues and options that seek to resolve them and selects the best
option from these and makes an attempt to explain why this option is the
best.
PS: Answers some of the DET questions, lists a few facts, identifies a few
non-ethical issues, lists a few stakeholders, lists a few ethical issues and
options that seek to resolve them and selects the best option from these
but without explaining why this option is the best.
FL: Answers a few DET questions but fails to list important facts, fails to
identify relevant non-ethical issues, fails to list important stakeholders,
fails to identify the ethical issues and evaluates the options that seek to
resolve them and does not select the best option or does not explain why
the option selected is the best.
Writing &
structure
(Value
HD: Language features and structures are used to convey meaning
effectively, concisely, unambiguously, and in a tone appropriate to the
audience and purpose with no spelling, grammatical, or punctuation
Your Name
ITC506 Assessment Item 1- Marking Sheet
Total Obtained Marks /100 & /15
Criteria Standards
Marks
award
ed
Analysis
of the
ethical
dilemma
using the
Doing
Ethics
Technique
(DET)
(Value:
70%)
HD: Answers all DET questions, lists all the facts, identifies all the non-
ethical issues, lists all the stakeholders, identifies all the ethical issues,
evaluates all the options that seek to resolve them and selects the best
option from these and justifies why this option is the best using
supporting arguments based on the literature.
DI: Answers all DET questions, lists all the facts, identifies all the non-
ethical issues, lists all the stakeholders, lists all the ethical issues and
options that seek to resolve them and selects the best option from these
and explains why this option is the best.
CR: Answers all DET questions, lists most of the facts, identifies most of
the non-ethical issues, lists most of the stakeholders, lists most of the
ethical issues and options that seek to resolve them and selects the best
option from these and makes an attempt to explain why this option is the
best.
PS: Answers some of the DET questions, lists a few facts, identifies a few
non-ethical issues, lists a few stakeholders, lists a few ethical issues and
options that seek to resolve them and selects the best option from these
but without explaining why this option is the best.
FL: Answers a few DET questions but fails to list important facts, fails to
identify relevant non-ethical issues, fails to list important stakeholders,
fails to identify the ethical issues and evaluates the options that seek to
resolve them and does not select the best option or does not explain why
the option selected is the best.
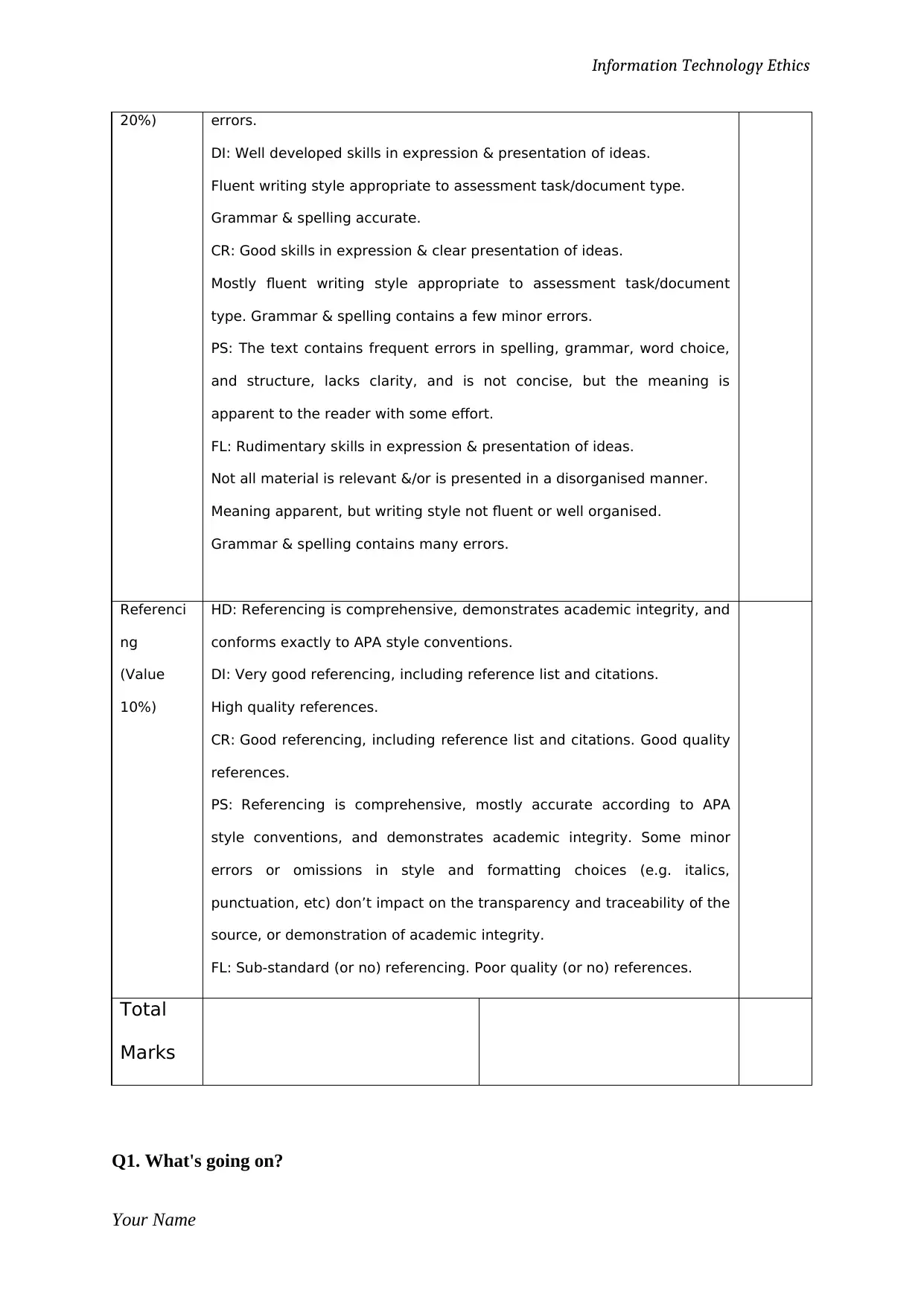
Writing &
structure
(Value
HD: Language features and structures are used to convey meaning
effectively, concisely, unambiguously, and in a tone appropriate to the
audience and purpose with no spelling, grammatical, or punctuation
Your Name
Information Technology Ethics
20%) errors.
DI: Well developed skills in expression & presentation of ideas.
Fluent writing style appropriate to assessment task/document type.
Grammar & spelling accurate.
CR: Good skills in expression & clear presentation of ideas.
Mostly fluent writing style appropriate to assessment task/document
type. Grammar & spelling contains a few minor errors.
PS: The text contains frequent errors in spelling, grammar, word choice,
and structure, lacks clarity, and is not concise, but the meaning is
apparent to the reader with some effort.
FL: Rudimentary skills in expression & presentation of ideas.
Not all material is relevant &/or is presented in a disorganised manner.
Meaning apparent, but writing style not fluent or well organised.
Grammar & spelling contains many errors.
Referenci
ng
(Value
10%)
HD: Referencing is comprehensive, demonstrates academic integrity, and
conforms exactly to APA style conventions.
DI: Very good referencing, including reference list and citations.
High quality references.
CR: Good referencing, including reference list and citations. Good quality
references.
PS: Referencing is comprehensive, mostly accurate according to APA
style conventions, and demonstrates academic integrity. Some minor
errors or omissions in style and formatting choices (e.g. italics,
punctuation, etc) don’t impact on the transparency and traceability of the
source, or demonstration of academic integrity.
FL: Sub-standard (or no) referencing. Poor quality (or no) references.
Total
Marks
Q1. What's going on?
Your Name
20%) errors.
DI: Well developed skills in expression & presentation of ideas.
Fluent writing style appropriate to assessment task/document type.
Grammar & spelling accurate.
CR: Good skills in expression & clear presentation of ideas.
Mostly fluent writing style appropriate to assessment task/document
type. Grammar & spelling contains a few minor errors.
PS: The text contains frequent errors in spelling, grammar, word choice,
and structure, lacks clarity, and is not concise, but the meaning is
apparent to the reader with some effort.
FL: Rudimentary skills in expression & presentation of ideas.
Not all material is relevant &/or is presented in a disorganised manner.
Meaning apparent, but writing style not fluent or well organised.
Grammar & spelling contains many errors.
Referenci
ng
(Value
10%)
HD: Referencing is comprehensive, demonstrates academic integrity, and
conforms exactly to APA style conventions.
DI: Very good referencing, including reference list and citations.
High quality references.
CR: Good referencing, including reference list and citations. Good quality
references.
PS: Referencing is comprehensive, mostly accurate according to APA
style conventions, and demonstrates academic integrity. Some minor
errors or omissions in style and formatting choices (e.g. italics,
punctuation, etc) don’t impact on the transparency and traceability of the
source, or demonstration of academic integrity.
FL: Sub-standard (or no) referencing. Poor quality (or no) references.
Total
Marks
Q1. What's going on?
Your Name
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Information Technology Ethics
To make the system live within time that the team has undertaken, the higher manager
wants to complete the project as soon as possible. Still there are certain constrains in doing
that as suggested by ken, the developer. The primary concern is the testing of the system. It is
not possible to meet both the requirements of testing and finishing the project at the same
time as pointed out by ken. It will require time to test the system. So Ken wants to extend the
project further. He request the management to extend the project at least by one month so that
right amount of effort can be put in developing the system as error free as possible. However,
the manager is not satisfied with the approach at all. He argues that if they cannot deliver the
project within time it will be harmful for the reputation of the company and he wants to
submit it anyhow. However Ken does not agree with the viewpoint of the manager as he is
much more concerned with the quality and security of the system which cannot be reviewed
without testing. Even after explaining the importance of testing, he cannot convince the
manger about asking more time from the client. The manger wants the project ready at any
cost, no matter how justified Ken’s viewpoint is.
Now this present a tough situation for Ken as it is difficult for him to choose between
the options he has. Either he has to go with the manager and let the system go live without
testing, or he should listen to his mind. Now to choose the later over the former, he has to go
against the authorities. Now this create another problem for Ken. It is obvious that if he is
determined to go against the authorities , he should either resign or need to give much more
effort in proving his point to such an extent that the authorities finally decide to go with the
decision of Ken that he previously offered.
Q2. What are the facts?
Following the discussion, some facts have been highlighted in this section:
Your Name
To make the system live within time that the team has undertaken, the higher manager
wants to complete the project as soon as possible. Still there are certain constrains in doing
that as suggested by ken, the developer. The primary concern is the testing of the system. It is
not possible to meet both the requirements of testing and finishing the project at the same
time as pointed out by ken. It will require time to test the system. So Ken wants to extend the
project further. He request the management to extend the project at least by one month so that
right amount of effort can be put in developing the system as error free as possible. However,
the manager is not satisfied with the approach at all. He argues that if they cannot deliver the
project within time it will be harmful for the reputation of the company and he wants to
submit it anyhow. However Ken does not agree with the viewpoint of the manager as he is
much more concerned with the quality and security of the system which cannot be reviewed
without testing. Even after explaining the importance of testing, he cannot convince the
manger about asking more time from the client. The manger wants the project ready at any
cost, no matter how justified Ken’s viewpoint is.
Now this present a tough situation for Ken as it is difficult for him to choose between
the options he has. Either he has to go with the manager and let the system go live without
testing, or he should listen to his mind. Now to choose the later over the former, he has to go
against the authorities. Now this create another problem for Ken. It is obvious that if he is
determined to go against the authorities , he should either resign or need to give much more
effort in proving his point to such an extent that the authorities finally decide to go with the
decision of Ken that he previously offered.
Q2. What are the facts?
Following the discussion, some facts have been highlighted in this section:
Your Name
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Information Technology Ethics
Testing helps to keep system secure:
Software testing has a significant role in the software development which makes software
more secure, reliable and robust (Han et al., 2015). According to the authors, testing helps to
strengthen the security by combining three key features of system security:
1. Confidentiality – it helps to keep the data private that the system deals with
2. Integrity – it keep the accuracy and integrity of the data that the system executes
3. Robustness – it helps to make the system robust by finding out necessary
improvement needed to protect the system from unauthorized access.
Software testing removes bugs:
Software testing is done in order to find out if the system has any bugs before the
system is made available for use. This helps to remove bugs, the software might encounter
during the execution (Bernstein, 2014). Though , it is expected to provide the best efforts in
designing the software, it is impossible to make software that is completely error free. Sooner
or later the software will eventually create issues when it comes about execution or
performance (Fleischmann et al. , 2016). Software testing are aimed in producing software
that works correctly with fewer errors.
Q3. What are the issues?
There are some issues regarding the project, which will be discussed below:
Integration of software testing:
The result of not incorporating the testing technology with the software has a direct
linkage with the software security. Although it is essential to finish the development within
the stated period and opting for software testing will further make the process delayed, still
Your Name
Testing helps to keep system secure:
Software testing has a significant role in the software development which makes software
more secure, reliable and robust (Han et al., 2015). According to the authors, testing helps to
strengthen the security by combining three key features of system security:
1. Confidentiality – it helps to keep the data private that the system deals with
2. Integrity – it keep the accuracy and integrity of the data that the system executes
3. Robustness – it helps to make the system robust by finding out necessary
improvement needed to protect the system from unauthorized access.
Software testing removes bugs:
Software testing is done in order to find out if the system has any bugs before the
system is made available for use. This helps to remove bugs, the software might encounter
during the execution (Bernstein, 2014). Though , it is expected to provide the best efforts in
designing the software, it is impossible to make software that is completely error free. Sooner
or later the software will eventually create issues when it comes about execution or
performance (Fleischmann et al. , 2016). Software testing are aimed in producing software
that works correctly with fewer errors.
Q3. What are the issues?
There are some issues regarding the project, which will be discussed below:
Integration of software testing:
The result of not incorporating the testing technology with the software has a direct
linkage with the software security. Although it is essential to finish the development within
the stated period and opting for software testing will further make the process delayed, still
Your Name

Information Technology Ethics
supplying the product without testing will make the system less secure as testing helps to find
out issues that lead to security concern of any software (Wright & Cache, 2015).
Delivery of product within time:
Due to inefficient planning and lack of proper management the company was unable
to finish the project well before due date. The development is in such a condition that either
they have to take more time in finishing the project or they have to complete it somehow
which will definitely affect the quality of the project.
Q4. Who is affected?
The client company will be the affected most if the software is delivered to the
company overlooking the quality measures like security, reliability and availability of the
system. Not only the client company, the consumers will also have to deal with the same as
company will not be able to ensure their security.
Additionally, if the manufacturing company cannot deliver the product in time and
fail to satisfy the client it will surely affect the reputation of the organization which might see
them loosing further contact from the client.
Q5. What are the ethical issues and their implications?
Violation of security:
Whenever an organization is creating any product that will be used by the client
organizations, it is the concern of the enterprise to treat the project with the highest priority
best design procedure needs to be followed so that the end product is highly secure. On the
other hand, in this setting the designing company is overlooking the security matters just to
deliver the product timely to satisfy the authorities.
This move can be regarded as extremely unethical as it encompasses the violation of
data security of the customers the client organization deals with.
Compromising of quality over money:
To provide the project timely and to bag the next project from the client, they are
planning to compromise with the overall quality of the product as they consider the testing
less important. On the other hand, the program director thinks that making the system
Your Name
supplying the product without testing will make the system less secure as testing helps to find
out issues that lead to security concern of any software (Wright & Cache, 2015).
Delivery of product within time:
Due to inefficient planning and lack of proper management the company was unable
to finish the project well before due date. The development is in such a condition that either
they have to take more time in finishing the project or they have to complete it somehow
which will definitely affect the quality of the project.
Q4. Who is affected?
The client company will be the affected most if the software is delivered to the
company overlooking the quality measures like security, reliability and availability of the
system. Not only the client company, the consumers will also have to deal with the same as
company will not be able to ensure their security.
Additionally, if the manufacturing company cannot deliver the product in time and
fail to satisfy the client it will surely affect the reputation of the organization which might see
them loosing further contact from the client.
Q5. What are the ethical issues and their implications?
Violation of security:
Whenever an organization is creating any product that will be used by the client
organizations, it is the concern of the enterprise to treat the project with the highest priority
best design procedure needs to be followed so that the end product is highly secure. On the
other hand, in this setting the designing company is overlooking the security matters just to
deliver the product timely to satisfy the authorities.
This move can be regarded as extremely unethical as it encompasses the violation of
data security of the customers the client organization deals with.
Compromising of quality over money:
To provide the project timely and to bag the next project from the client, they are
planning to compromise with the overall quality of the product as they consider the testing
less important. On the other hand, the program director thinks that making the system
Your Name
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Information Technology Ethics
available without testing will make the system of poor quality. From the discussion , this
move can be regarded as unethical and it has the potential to affect the client both in terms of
security and reputation. Additionally, the reputation of the manufacturing company will also
be affected.
Q6. What could have been done about it?
In order to the project and deliver it within the specified time frame, the project must
have been in full swing right from the beginning and if not, the speed of planning the parts
of the project needed to be accelerated rather than opting for unethical means .
Q7. What are the options?
Bearing in mind the existing situation, two choices are accessible right now
Either the upper consultants should request the client organization for lengthening the date of
distribution or they can simply decline to finish the task in the due period.
Q8. Which option is the best and why?
From the available options, the best choice is evidently to induce the company for
prolonging the delivery for if they select to decline ending the project, it will make a bad
impression about the business and they may not be able to get the next venture for the
company. Conversely, if they succeed in convincing the consumer about the significance of
lengthening the delivery date by means of presenting them the magnitudes of delivering the
product without the making the testing done , mutually both ends will have the benefits.
References
Your Name
available without testing will make the system of poor quality. From the discussion , this
move can be regarded as unethical and it has the potential to affect the client both in terms of
security and reputation. Additionally, the reputation of the manufacturing company will also
be affected.
Q6. What could have been done about it?
In order to the project and deliver it within the specified time frame, the project must
have been in full swing right from the beginning and if not, the speed of planning the parts
of the project needed to be accelerated rather than opting for unethical means .
Q7. What are the options?
Bearing in mind the existing situation, two choices are accessible right now
Either the upper consultants should request the client organization for lengthening the date of
distribution or they can simply decline to finish the task in the due period.
Q8. Which option is the best and why?
From the available options, the best choice is evidently to induce the company for
prolonging the delivery for if they select to decline ending the project, it will make a bad
impression about the business and they may not be able to get the next venture for the
company. Conversely, if they succeed in convincing the consumer about the significance of
lengthening the delivery date by means of presenting them the magnitudes of delivering the
product without the making the testing done , mutually both ends will have the benefits.
References
Your Name
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Information Technology Ethics
Bernstein, D. J. (2014). Caesar: Competition for authenticated software: Security,
applicability, and robustness.
Fleischmann, M., Amirpur, M., Grupp, T., Benlian, A., & Hess, T. (2016). The role of
software testing in information systems continuance—An experimental study from a
user perspective. Decision Support Systems, 83, 83-96.
Han, J., Susilo, W., Mu, Y., Zhou, J., & Au, M. H. A. (2015). Improving privacy and security
in decentralized ciphertext-policy attribute-based encryption. IEEE transactions on
information forensics and security, 10(3), 665-678.
Wright, J., & Cache, J. (2015). Hacking exposed wireless: wireless security secrets &
solutions. McGraw-Hill Education Group.
Your Name
Bernstein, D. J. (2014). Caesar: Competition for authenticated software: Security,
applicability, and robustness.
Fleischmann, M., Amirpur, M., Grupp, T., Benlian, A., & Hess, T. (2016). The role of
software testing in information systems continuance—An experimental study from a
user perspective. Decision Support Systems, 83, 83-96.
Han, J., Susilo, W., Mu, Y., Zhou, J., & Au, M. H. A. (2015). Improving privacy and security
in decentralized ciphertext-policy attribute-based encryption. IEEE transactions on
information forensics and security, 10(3), 665-678.
Wright, J., & Cache, J. (2015). Hacking exposed wireless: wireless security secrets &
solutions. McGraw-Hill Education Group.
Your Name
1 out of 8
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





