Aztek IT Risk Management and Outsourcing: A Comprehensive Report
VerifiedAdded on 2020/03/23
|14
|3013
|40
Report
AI Summary
This report provides a comprehensive analysis of IT risk management and outsourcing strategies at Aztek, focusing on the financial services sector. It examines the company's current security posture, including risk control practices, employee training, and data protection measures. The report explores the legal and regulatory requirements associated with outsourcing IT functions, highlighting key concerns such as data protection and intellectual property. It identifies potential threats, vulnerabilities, and consequences related to outsourcing, such as unauthorized access, viruses, and theft. Furthermore, the report discusses the financial impacts of IT outsourcing, including reduced operating costs, increased capital funds, and access to new resources, while also addressing long-term benefits such as improved business focus and access to state-of-the-art capabilities. The report emphasizes the importance of selecting qualified vendors, maintaining control of company affairs, and addressing flexibility issues to mitigate risks and ensure successful outsourcing procedures. Overall, the report offers valuable insights into managing IT risks and leveraging outsourcing for business development and growth.

Running Head: INFORMATION TECHNOLOGY RISK MANAGEMENT 1
Information Technology Risk Management
Student’s Name
Institution
Date
Information Technology Risk Management
Student’s Name
Institution
Date
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

INFORMATION TECHNOLOGY RISK MANAGEMENT 2
EXECUTIVE SUMMARY
It has become a common occurrence for Australian companies to outsource certain
organizational functions for obvious reasons such as cutting down production costs and
ultimately increasing overall performance and efficiency (Sun, R., Gregor, S., & Keating, B.,
2014). Some of the common functions that are outsourced at Aztek and in most Australian
organizations are logistics, payroll, and bookkeeping. It is important to keep in mind that other
organizational functions are almost too integral to the organization to outsource, such as
Information Technology functions. However, most companies have started embracing the idea
after seeing some of the benefits.
INTRODUCTION
Australia’s financial experts are predicting a potentially exponential growth of the country’s
economy in the years to come (McCombie, J., & Thirlwall, A., 2016). This could be attributed to
the fact that there are several factors that positively influence Australia’s Economy at play, such
as the fact the country boasts one of the most advanced and effective service sectors in the world,
which contributes approximately 61% of the country’s GDP and employs roughly 80% of the
national population (Lovelock, C., & Patterson, P., 2015). Australia also reports a very low net
debt to GDP ratios and this helps in strengthening the country’s currency.
With this in mind, it is an undeniable fact that Australia’s relatively strong economy makes the
country a highly competitive commercial environment which means that every company in the
country is doing everything possible to keep up with the competitive trends and times. For us at
Aztek, driving the bottom line requires efficient performance and it means coming up with
EXECUTIVE SUMMARY
It has become a common occurrence for Australian companies to outsource certain
organizational functions for obvious reasons such as cutting down production costs and
ultimately increasing overall performance and efficiency (Sun, R., Gregor, S., & Keating, B.,
2014). Some of the common functions that are outsourced at Aztek and in most Australian
organizations are logistics, payroll, and bookkeeping. It is important to keep in mind that other
organizational functions are almost too integral to the organization to outsource, such as
Information Technology functions. However, most companies have started embracing the idea
after seeing some of the benefits.
INTRODUCTION
Australia’s financial experts are predicting a potentially exponential growth of the country’s
economy in the years to come (McCombie, J., & Thirlwall, A., 2016). This could be attributed to
the fact that there are several factors that positively influence Australia’s Economy at play, such
as the fact the country boasts one of the most advanced and effective service sectors in the world,
which contributes approximately 61% of the country’s GDP and employs roughly 80% of the
national population (Lovelock, C., & Patterson, P., 2015). Australia also reports a very low net
debt to GDP ratios and this helps in strengthening the country’s currency.
With this in mind, it is an undeniable fact that Australia’s relatively strong economy makes the
country a highly competitive commercial environment which means that every company in the
country is doing everything possible to keep up with the competitive trends and times. For us at
Aztek, driving the bottom line requires efficient performance and it means coming up with

INFORMATION TECHNOLOGY RISK MANAGEMENT 3
sustainable and innovative ways of addressing the challenges brought forth by this situation and
we have found the solution in outsourcing.
Outsourcing Requirements
Business Regulatory and Legislative requirements
Outsourcing ICT functions is a delicate matter as it involves having a third party external firm
managing your company’s critical and important information and data. Key areas of legal
concern include tax issues, transfer of assets, insurance, liability, data protection issues and
intellectual property. The Australian Competition & Consumer Law (ACCL) is usually oversight
on most Australian outsourcing transactions while other Federal and State privacy and data
protection laws are in play in cases of infringement or illegal access/handling of personal
information by the outsourcing provider (Corones, 2014).
The proposal to outsource key Information Technology functions at Aztek has been done in
consideration of Federal and State agencies that are in charge of ensuring that all the legal
procedures are adhered to throughout the implementation period. It is the responsibility of both
Aztek and our potential outsourcing partner to ascertain that there are absolutely no data
protection compromises made as this could lead to legal disputes especially where sensitive data
such as personal clientele information and creation or transmission of public records are at risk.
Current Security State
Organizational security management is not just about identity badge readers and guards at the
gate. It is more than just the individual operational tactics and technologies such as data
sustainable and innovative ways of addressing the challenges brought forth by this situation and
we have found the solution in outsourcing.
Outsourcing Requirements
Business Regulatory and Legislative requirements
Outsourcing ICT functions is a delicate matter as it involves having a third party external firm
managing your company’s critical and important information and data. Key areas of legal
concern include tax issues, transfer of assets, insurance, liability, data protection issues and
intellectual property. The Australian Competition & Consumer Law (ACCL) is usually oversight
on most Australian outsourcing transactions while other Federal and State privacy and data
protection laws are in play in cases of infringement or illegal access/handling of personal
information by the outsourcing provider (Corones, 2014).
The proposal to outsource key Information Technology functions at Aztek has been done in
consideration of Federal and State agencies that are in charge of ensuring that all the legal
procedures are adhered to throughout the implementation period. It is the responsibility of both
Aztek and our potential outsourcing partner to ascertain that there are absolutely no data
protection compromises made as this could lead to legal disputes especially where sensitive data
such as personal clientele information and creation or transmission of public records are at risk.
Current Security State
Organizational security management is not just about identity badge readers and guards at the
gate. It is more than just the individual operational tactics and technologies such as data
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

INFORMATION TECHNOLOGY RISK MANAGEMENT 4
encryption, firewalls, and server securities. At Aztek, organizational security is of utmost
importance and incorporates organization-wide employee training and monitoring, and setting up
of effective and innovative organizational security policies. Aztek has an integrated and risk-
based strategy used in the implementation of our business security program with the aid of the
following risk control practices;
- Risk Evaluation – this is an ongoing process of high-level functions that cover all the
critical to core elements of an organization such as assets and people (Bodie, 2013).
- Technical Risk Control – focuses on security implementation as opposed to Risk
Evaluation that focuses on the company’s security posture and vulnerabilities (Pritchard,
C., & PMP, P., 2014).
- Operational Risk Control – conducted throughout the day to day operations and is
focused on preventing security threats (Robertson, 2016).
Effective management of information security involves pinpointing and expediting risks,
appropriately safeguarding critical data and swiftly palliating security gaps. To achieve effective
information security, the organization's leadership must be consistently involved. Senior
management is responsible for setting the tone for an organization and establishing priorities. It,
therefore, follows that senior management should offer support in terms of ensuring budgets and
resources are available for information security as well emphasizing the importance of effective
and protected information systems.
Aztek has systems set in place to ensure that sensitive data, customer or proprietary, is always
checked when flowing in and out of the organization's databases. This has enabled us to focus
our time, energies and resources into coming up with means to protect our valuable sensitive
encryption, firewalls, and server securities. At Aztek, organizational security is of utmost
importance and incorporates organization-wide employee training and monitoring, and setting up
of effective and innovative organizational security policies. Aztek has an integrated and risk-
based strategy used in the implementation of our business security program with the aid of the
following risk control practices;
- Risk Evaluation – this is an ongoing process of high-level functions that cover all the
critical to core elements of an organization such as assets and people (Bodie, 2013).
- Technical Risk Control – focuses on security implementation as opposed to Risk
Evaluation that focuses on the company’s security posture and vulnerabilities (Pritchard,
C., & PMP, P., 2014).
- Operational Risk Control – conducted throughout the day to day operations and is
focused on preventing security threats (Robertson, 2016).
Effective management of information security involves pinpointing and expediting risks,
appropriately safeguarding critical data and swiftly palliating security gaps. To achieve effective
information security, the organization's leadership must be consistently involved. Senior
management is responsible for setting the tone for an organization and establishing priorities. It,
therefore, follows that senior management should offer support in terms of ensuring budgets and
resources are available for information security as well emphasizing the importance of effective
and protected information systems.
Aztek has systems set in place to ensure that sensitive data, customer or proprietary, is always
checked when flowing in and out of the organization's databases. This has enabled us to focus
our time, energies and resources into coming up with means to protect our valuable sensitive
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

INFORMATION TECHNOLOGY RISK MANAGEMENT 5
data. We have a formal and documented inventory of all the company's systems that aid in the
transmission, processing or storage of sensitive data and information. This includes a backup of
the operating system as well as the major applications installed for the purpose of the above
processes.
Risk Assessment Result
There are always risks involved when allocating any of a company’s functions or responsibilities
to someone else. Identifying the right people for the job is key to ensuring successful and
effective outsourcing procedures. Some of the risks involved are;
- Ensuring that the outside vendor is qualified for the job
- Maintaining control of company affairs
- Sustaining in-house employee morale
- Keeping up with the rapidly evolving Information Technologies
- Managing switching costs
- Addressing flexibility issues
The above issues can be addressed by ascertaining that Aztek contracts vendors whose culture
fits with the company’s employees and clients. We have to evaluate the potential vendor’s track-
record history, their financial security, experience with current or future technologies and their
organizational skills (Brindley, 2017). This will help in choosing the most appropriate vendor for
the IT functions and minimize the risks stated above.
FINANCIAL SERVICE SECTOR REVIEW
data. We have a formal and documented inventory of all the company's systems that aid in the
transmission, processing or storage of sensitive data and information. This includes a backup of
the operating system as well as the major applications installed for the purpose of the above
processes.
Risk Assessment Result
There are always risks involved when allocating any of a company’s functions or responsibilities
to someone else. Identifying the right people for the job is key to ensuring successful and
effective outsourcing procedures. Some of the risks involved are;
- Ensuring that the outside vendor is qualified for the job
- Maintaining control of company affairs
- Sustaining in-house employee morale
- Keeping up with the rapidly evolving Information Technologies
- Managing switching costs
- Addressing flexibility issues
The above issues can be addressed by ascertaining that Aztek contracts vendors whose culture
fits with the company’s employees and clients. We have to evaluate the potential vendor’s track-
record history, their financial security, experience with current or future technologies and their
organizational skills (Brindley, 2017). This will help in choosing the most appropriate vendor for
the IT functions and minimize the risks stated above.
FINANCIAL SERVICE SECTOR REVIEW

INFORMATION TECHNOLOGY RISK MANAGEMENT 6
Although the world has experienced tough financial recent times – since 2008 – reports predict
that there has been a rapid growth in Information Technology Outsourcing in the financial sector
and that the trend will be sustained even after the financial crisis is over (Brown, C., & Davis, K.,
2015). This is evidence that Information Technology is the crown jewel of the financial services
sector. Information technology at Aztek is part of our firm's infrastructure and therefore it is
closely linked to our business strategy. The need for having both paper and electronic volumes of
information, and the fact that financial processes have been almost totally digitized means that IT
is no longer a utility in financial entities and has become a central and integral part of any
organization. Aztek requires that the vendors possess advanced Information Technologies that
can handle enormous transaction volumes such as overseeing the management of collections and
payments.
Impacts of IT Outsourcing to Financial Services
Despite the several risks involved with outsourcing core and integral IT functions, Aztek will
benefit from several short-term and long-term benefits. The following are some of the short-term
advantages to the company’s financial services sector at Aztek;
i) Reduced Operating costs – a survey conducted by experts in our financial services
sector show that reduced operating costs is one of the most compelling short-term
benefits as it could lead to a 9% reduction in operating costs if we proceed with
outsourcing Information Technology functions.
ii) More capital funds – the need to invest capital in non-core business functions to the
organization will be eliminated by the outsourcing of IT functions hence capital funds
will be more available for the more integral areas of our business. The need to
Although the world has experienced tough financial recent times – since 2008 – reports predict
that there has been a rapid growth in Information Technology Outsourcing in the financial sector
and that the trend will be sustained even after the financial crisis is over (Brown, C., & Davis, K.,
2015). This is evidence that Information Technology is the crown jewel of the financial services
sector. Information technology at Aztek is part of our firm's infrastructure and therefore it is
closely linked to our business strategy. The need for having both paper and electronic volumes of
information, and the fact that financial processes have been almost totally digitized means that IT
is no longer a utility in financial entities and has become a central and integral part of any
organization. Aztek requires that the vendors possess advanced Information Technologies that
can handle enormous transaction volumes such as overseeing the management of collections and
payments.
Impacts of IT Outsourcing to Financial Services
Despite the several risks involved with outsourcing core and integral IT functions, Aztek will
benefit from several short-term and long-term benefits. The following are some of the short-term
advantages to the company’s financial services sector at Aztek;
i) Reduced Operating costs – a survey conducted by experts in our financial services
sector show that reduced operating costs is one of the most compelling short-term
benefits as it could lead to a 9% reduction in operating costs if we proceed with
outsourcing Information Technology functions.
ii) More capital funds – the need to invest capital in non-core business functions to the
organization will be eliminated by the outsourcing of IT functions hence capital funds
will be more available for the more integral areas of our business. The need to
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

INFORMATION TECHNOLOGY RISK MANAGEMENT 7
illustrate return on equity from non-integral areas' capital investments will be
eliminated thus improving our corporate financial measurements (Oshri, I., Kotlarsky,
J., 2015).
iii) Infusion of cash – handing over of our IT functions will involve the transfer of assets
such as facilities, equipment, and licenses from Aztek management to the new
provider. This means that, in effect, these assets will be sold to the provider as part of
the transaction resulting in a cash payment to Aztek.
iv) Access to new resources – outsourcing our IT functions will go a long way in
fostering our foundations when expanding to new geographical markets. New areas
will bring about the need to build up technological facilities from the ground up and
outsourcing will eliminate this need thus leading to saving the resources required for
this process (Herrera, A., & Camacho, S., 2017).
v) Better overall IT management – by outsourcing, Aztek will have the option of
managing IT functions that could have gone out of control. This can however not
allow for relinquishment of management responsibility.
There are also several long-term benefits reaped from outsourcing of IT functions as listed
below;
i) Improved business focus – Information Technology, being such a core component
of any entity, tends to siphon off enormous amounts of management attention and
resources at Aztek. There, therefore, comes the need to alleviate the management of
this burden and outsourcing will allow the company to allocate its resources to other
broader business issues while leaving operational matters to outside professionals.
illustrate return on equity from non-integral areas' capital investments will be
eliminated thus improving our corporate financial measurements (Oshri, I., Kotlarsky,
J., 2015).
iii) Infusion of cash – handing over of our IT functions will involve the transfer of assets
such as facilities, equipment, and licenses from Aztek management to the new
provider. This means that, in effect, these assets will be sold to the provider as part of
the transaction resulting in a cash payment to Aztek.
iv) Access to new resources – outsourcing our IT functions will go a long way in
fostering our foundations when expanding to new geographical markets. New areas
will bring about the need to build up technological facilities from the ground up and
outsourcing will eliminate this need thus leading to saving the resources required for
this process (Herrera, A., & Camacho, S., 2017).
v) Better overall IT management – by outsourcing, Aztek will have the option of
managing IT functions that could have gone out of control. This can however not
allow for relinquishment of management responsibility.
There are also several long-term benefits reaped from outsourcing of IT functions as listed
below;
i) Improved business focus – Information Technology, being such a core component
of any entity, tends to siphon off enormous amounts of management attention and
resources at Aztek. There, therefore, comes the need to alleviate the management of
this burden and outsourcing will allow the company to allocate its resources to other
broader business issues while leaving operational matters to outside professionals.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

INFORMATION TECHNOLOGY RISK MANAGEMENT 8
ii) Access to state of the art capabilities – outsourcing providers are by their very
nature specialized professionals in their field of work. Thus, they bring world-class
and large-scale global resources to meet the requirements of their customers.
iii) Shared risks – the financial services sector at Aztek requires being more flexible and
dynamic for it to be able to deal with the tremendous risks associated with the
investments that the company is about to make. Outsourcing allows for agreements to
be made on sharing risks and this results in both parties being able to adequately
adapt to changing opportunities (Rost, 2016).
CURRENT SECURITY POSTURE
Aztek is dedicated to ensuring that the integrity of our transactions and the security of our system
is always intact for the purpose of protecting our reputation and maintaining good relationships
with our clients, service providers, and partners. Conversely, several measurements have been
put in place to ensure the smooth running of security features at Aztek.
- We ensure that we always have a fortified change-control process that is meticulously
enforced. All changes made to the security systems, including emergency changes, are
utterly documented and then formally reviewed and approved to avoid security
vulnerabilities that could lead to a breach.
- Aztek has a new robust configuration management process with sensitive systems that are
hardened and built with requisite functionality through the use of a managed
configuration software tool and an automated build process (Leon, 2015). The software is
better than its predecessor as it conducts frequent and regular checks on the security systems to
prevent server creep by maintaining hardened change-control protocols.
ii) Access to state of the art capabilities – outsourcing providers are by their very
nature specialized professionals in their field of work. Thus, they bring world-class
and large-scale global resources to meet the requirements of their customers.
iii) Shared risks – the financial services sector at Aztek requires being more flexible and
dynamic for it to be able to deal with the tremendous risks associated with the
investments that the company is about to make. Outsourcing allows for agreements to
be made on sharing risks and this results in both parties being able to adequately
adapt to changing opportunities (Rost, 2016).
CURRENT SECURITY POSTURE
Aztek is dedicated to ensuring that the integrity of our transactions and the security of our system
is always intact for the purpose of protecting our reputation and maintaining good relationships
with our clients, service providers, and partners. Conversely, several measurements have been
put in place to ensure the smooth running of security features at Aztek.
- We ensure that we always have a fortified change-control process that is meticulously
enforced. All changes made to the security systems, including emergency changes, are
utterly documented and then formally reviewed and approved to avoid security
vulnerabilities that could lead to a breach.
- Aztek has a new robust configuration management process with sensitive systems that are
hardened and built with requisite functionality through the use of a managed
configuration software tool and an automated build process (Leon, 2015). The software is
better than its predecessor as it conducts frequent and regular checks on the security systems to
prevent server creep by maintaining hardened change-control protocols.
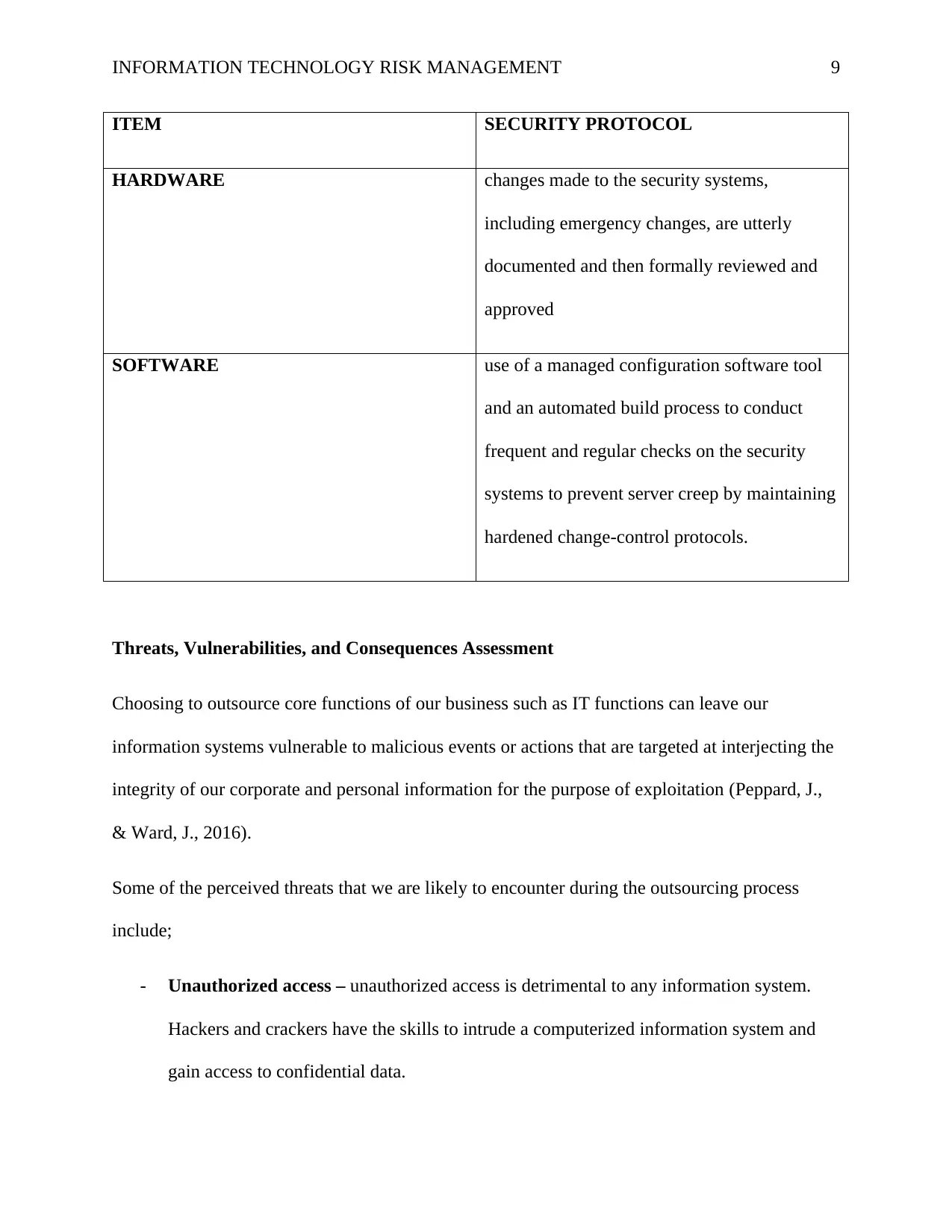
INFORMATION TECHNOLOGY RISK MANAGEMENT 9
ITEM SECURITY PROTOCOL
HARDWARE changes made to the security systems,
including emergency changes, are utterly
documented and then formally reviewed and
approved
SOFTWARE use of a managed configuration software tool
and an automated build process to conduct
frequent and regular checks on the security
systems to prevent server creep by maintaining
hardened change-control protocols.
Threats, Vulnerabilities, and Consequences Assessment
Choosing to outsource core functions of our business such as IT functions can leave our
information systems vulnerable to malicious events or actions that are targeted at interjecting the
integrity of our corporate and personal information for the purpose of exploitation (Peppard, J.,
& Ward, J., 2016).
Some of the perceived threats that we are likely to encounter during the outsourcing process
include;
- Unauthorized access – unauthorized access is detrimental to any information system.
Hackers and crackers have the skills to intrude a computerized information system and
gain access to confidential data.
ITEM SECURITY PROTOCOL
HARDWARE changes made to the security systems,
including emergency changes, are utterly
documented and then formally reviewed and
approved
SOFTWARE use of a managed configuration software tool
and an automated build process to conduct
frequent and regular checks on the security
systems to prevent server creep by maintaining
hardened change-control protocols.
Threats, Vulnerabilities, and Consequences Assessment
Choosing to outsource core functions of our business such as IT functions can leave our
information systems vulnerable to malicious events or actions that are targeted at interjecting the
integrity of our corporate and personal information for the purpose of exploitation (Peppard, J.,
& Ward, J., 2016).
Some of the perceived threats that we are likely to encounter during the outsourcing process
include;
- Unauthorized access – unauthorized access is detrimental to any information system.
Hackers and crackers have the skills to intrude a computerized information system and
gain access to confidential data.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

INFORMATION TECHNOLOGY RISK MANAGEMENT 10
- Viruses – Viruses are software deliberately written to infiltrate a computer system
without the user's knowledge or permission and can duplicate themselves and infect other
computers on the network (Taylor, R. W., & Liederbach, J., 2014).
- Theft – this entails the loss of important company software, hardware or data. It can be
broken down into data theft, physical theft, and identity theft.
- Vandalism – this is the deliberate damage to an organization's property, software, data,
and hardware.
Addressing Threats and Vulnerabilities
Since cybercrime has become a booming business in recent years, Aztek has taken serious
measures to minimize the chances of becoming victimized by cybercrime and the threats facing
our information systems. Some of the measures taken by our experts during the development of
the project include;
i) Installing a custom Anti-Virus software on all computers, servers, PCs, and laptops
for all the employees whether used at work or remotely from home.
ii) Ensuring regular Anti-Virus updates
iii) Establishing a customized firewall that blocks unwanted traffic from the
organization’s network
iv) Educating all our users on dealing with suspicious emails and scanning for malicious
software downloads.
THREAT MEASURES
- Viruses – Viruses are software deliberately written to infiltrate a computer system
without the user's knowledge or permission and can duplicate themselves and infect other
computers on the network (Taylor, R. W., & Liederbach, J., 2014).
- Theft – this entails the loss of important company software, hardware or data. It can be
broken down into data theft, physical theft, and identity theft.
- Vandalism – this is the deliberate damage to an organization's property, software, data,
and hardware.
Addressing Threats and Vulnerabilities
Since cybercrime has become a booming business in recent years, Aztek has taken serious
measures to minimize the chances of becoming victimized by cybercrime and the threats facing
our information systems. Some of the measures taken by our experts during the development of
the project include;
i) Installing a custom Anti-Virus software on all computers, servers, PCs, and laptops
for all the employees whether used at work or remotely from home.
ii) Ensuring regular Anti-Virus updates
iii) Establishing a customized firewall that blocks unwanted traffic from the
organization’s network
iv) Educating all our users on dealing with suspicious emails and scanning for malicious
software downloads.
THREAT MEASURES
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
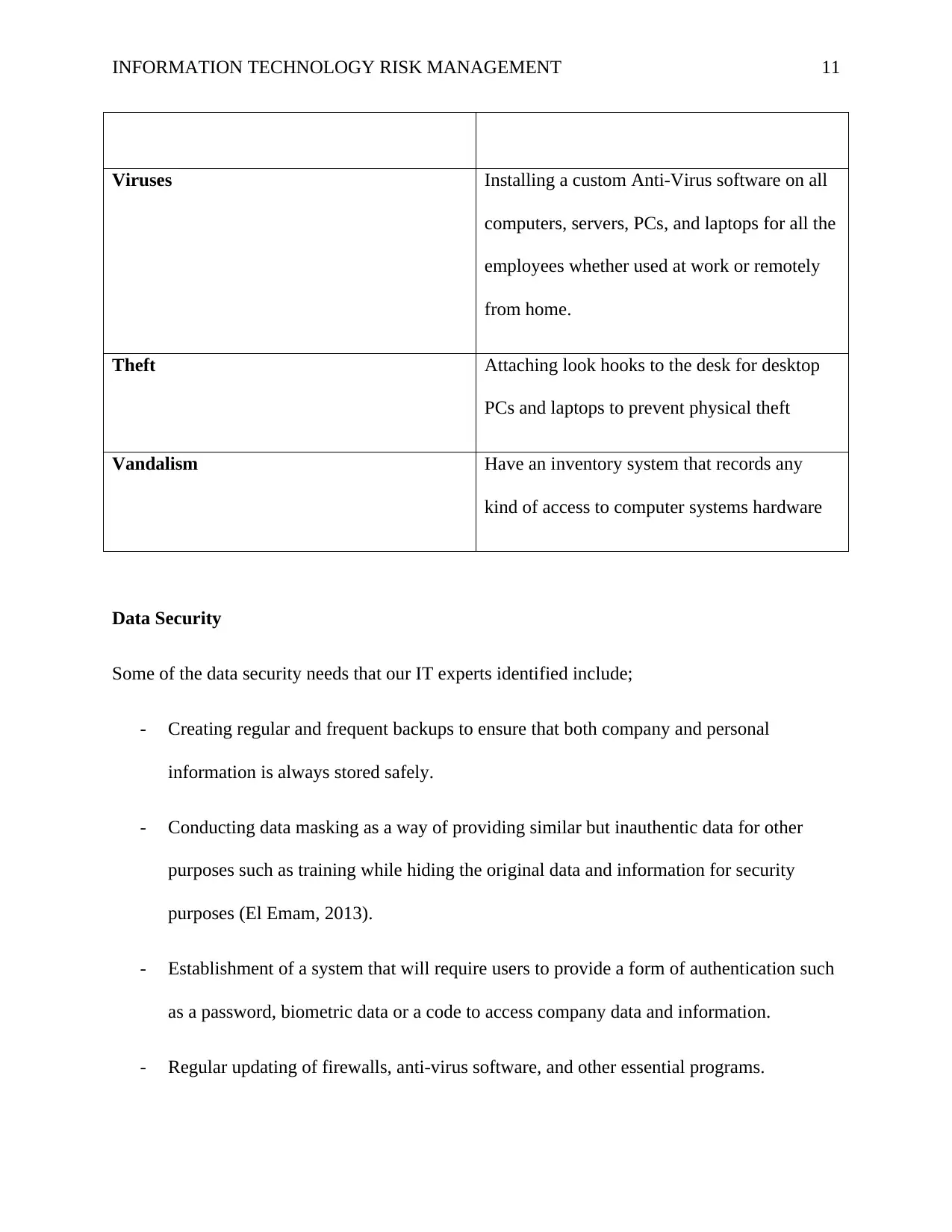
INFORMATION TECHNOLOGY RISK MANAGEMENT 11
Viruses Installing a custom Anti-Virus software on all
computers, servers, PCs, and laptops for all the
employees whether used at work or remotely
from home.
Theft Attaching look hooks to the desk for desktop
PCs and laptops to prevent physical theft
Vandalism Have an inventory system that records any
kind of access to computer systems hardware
Data Security
Some of the data security needs that our IT experts identified include;
- Creating regular and frequent backups to ensure that both company and personal
information is always stored safely.
- Conducting data masking as a way of providing similar but inauthentic data for other
purposes such as training while hiding the original data and information for security
purposes (El Emam, 2013).
- Establishment of a system that will require users to provide a form of authentication such
as a password, biometric data or a code to access company data and information.
- Regular updating of firewalls, anti-virus software, and other essential programs.
Viruses Installing a custom Anti-Virus software on all
computers, servers, PCs, and laptops for all the
employees whether used at work or remotely
from home.
Theft Attaching look hooks to the desk for desktop
PCs and laptops to prevent physical theft
Vandalism Have an inventory system that records any
kind of access to computer systems hardware
Data Security
Some of the data security needs that our IT experts identified include;
- Creating regular and frequent backups to ensure that both company and personal
information is always stored safely.
- Conducting data masking as a way of providing similar but inauthentic data for other
purposes such as training while hiding the original data and information for security
purposes (El Emam, 2013).
- Establishment of a system that will require users to provide a form of authentication such
as a password, biometric data or a code to access company data and information.
- Regular updating of firewalls, anti-virus software, and other essential programs.

INFORMATION TECHNOLOGY RISK MANAGEMENT 12
The above measures can be reinforced by conducting the following activities;
i) Allowing your employees to only access the data they need to perform their jobs
while strictly instructing them not to share passwords and access codes
ii) The IT department should always remove all kinds of personal data and information
before disposing off computers or before upgrading the computer systems
iii) Installing anti-spyware software on all computers and computer systems to monitor
any spyware activity.
The above measures can be reinforced by conducting the following activities;
i) Allowing your employees to only access the data they need to perform their jobs
while strictly instructing them not to share passwords and access codes
ii) The IT department should always remove all kinds of personal data and information
before disposing off computers or before upgrading the computer systems
iii) Installing anti-spyware software on all computers and computer systems to monitor
any spyware activity.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 14
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





