Information Technology Risk Management Report: VIC System Security
VerifiedAdded on 2020/02/24
|14
|3060
|107
Report
AI Summary
This report provides a comprehensive analysis of IT risk management within the VIC system. It begins by identifying and presenting the security risks and issues associated with the VIC system, including the use of a diagram to illustrate potential threats and mitigation strategies. The report then conducts a comparative analysis of deliberate and accidental threats, ranking them based on their potential impact. It explores several internal and external security challenges and risks linked to the VIC system, such as data confidentiality, improper infrastructure, and lack of planning. Furthermore, the report compares risks and uncertainties, and it details different risk control and mitigation approaches, including avoidance, diversification, duplication, and loss prevention. The report emphasizes the importance of ISMS (Information Security Management System) in addressing these risks and uncertainties, and it offers insights into how organizations can improve their IT risk management strategies. This report is a valuable resource for understanding and addressing the security challenges faced by the VIC system and similar information systems.

Running head: IT RISK MANAGEMENT
Information Technology Risk Management: VIC
Name of the student:
Name of the university:
Information Technology Risk Management: VIC
Name of the student:
Name of the university:
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1IT RISK MANAGEMENT
Table of Contents
1. Present security risks and issues associated to VIC.....................................................................2
2. Diagram description.....................................................................................................................2
3. Comparative analysis of deliberate and accidental threat............................................................3
3.1 Accidental threat....................................................................................................................3
3.2 Deliberate threat.....................................................................................................................4
3.3 Ranking of the threat.............................................................................................................5
3.4 Proper justification for the risk ranking.................................................................................6
4. Several internal and external security challenges and risks linked to VIC system.....................6
5. Comparison of risks and uncertainty...........................................................................................8
6. Different risk control and mitigation approach...........................................................................9
6.1 Risk control methods.............................................................................................................9
6.2 Risk mitigation methods......................................................................................................11
Reference List................................................................................................................................13
Table of Contents
1. Present security risks and issues associated to VIC.....................................................................2
2. Diagram description.....................................................................................................................2
3. Comparative analysis of deliberate and accidental threat............................................................3
3.1 Accidental threat....................................................................................................................3
3.2 Deliberate threat.....................................................................................................................4
3.3 Ranking of the threat.............................................................................................................5
3.4 Proper justification for the risk ranking.................................................................................6
4. Several internal and external security challenges and risks linked to VIC system.....................6
5. Comparison of risks and uncertainty...........................................................................................8
6. Different risk control and mitigation approach...........................................................................9
6.1 Risk control methods.............................................................................................................9
6.2 Risk mitigation methods......................................................................................................11
Reference List................................................................................................................................13
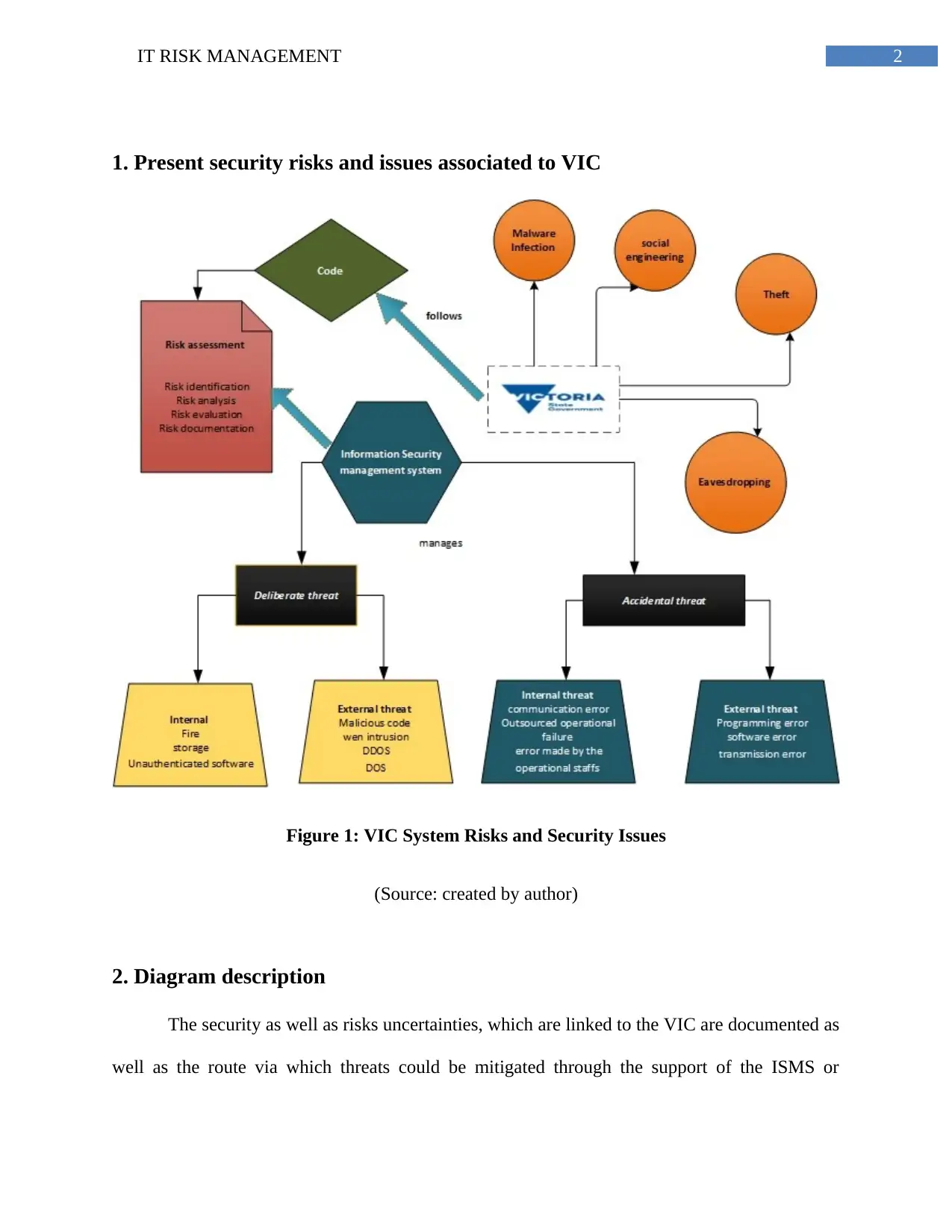
2IT RISK MANAGEMENT
1. Present security risks and issues associated to VIC
Figure 1: VIC System Risks and Security Issues
(Source: created by author)
2. Diagram description
The security as well as risks uncertainties, which are linked to the VIC are documented as
well as the route via which threats could be mitigated through the support of the ISMS or
1. Present security risks and issues associated to VIC
Figure 1: VIC System Risks and Security Issues
(Source: created by author)
2. Diagram description
The security as well as risks uncertainties, which are linked to the VIC are documented as
well as the route via which threats could be mitigated through the support of the ISMS or
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3IT RISK MANAGEMENT
Information Security Management System is clarified within figure 1. As of the model, the
situation has been revealed that, in the rouse of reflecting the current condition of VIC, the
primary threats those are distinguished are separated in two unique portions, for example, think
risk and accidental threat. However, extra risk is correspondingly there, which is the deliberate
threat, on behalf of the VIC this exact risk is not in consideration and concern. For accumulating
the suggested security VIC is necessary to characterize the ISMS. With a specific end goal to
recognize the threats and worries of VIC the safety design ISO/IEC.AS/NZS 17799:2001 is
embraced through the government’s risk supervision specialist.
It has been revealed that the ISMS, VIC, decided code besides the risk assessment
technique are interconnected to one another. The threats of VIC are yet again separated in four
exceptional parts. Merely afterward the effective finishing of these four phases the VIC threat
may be measured by the supervision professional of the business. The explicit progresses of
threats those are illustrious incorporate risk ID, chance examination, chance assessment and risk
documentation. In this manner, this can be accidental that, the figure 1 illustrates to the threats
and their mitigation method. However, with the intention of accumulating an organization of
threats, individual risk appraisal practices are similarly clarified within this report as well as
within the above outline too.
3. Comparative analysis of deliberate and accidental threat
3.1 Accidental threat
Subsequent to studying, threats connected to VIC has been uncovered government
opposes various threats. Taken as an example, deliberate and accidental threat along with the
ordinary threat. Amongst these threats, the deliberate along with accidental threats are
Information Security Management System is clarified within figure 1. As of the model, the
situation has been revealed that, in the rouse of reflecting the current condition of VIC, the
primary threats those are distinguished are separated in two unique portions, for example, think
risk and accidental threat. However, extra risk is correspondingly there, which is the deliberate
threat, on behalf of the VIC this exact risk is not in consideration and concern. For accumulating
the suggested security VIC is necessary to characterize the ISMS. With a specific end goal to
recognize the threats and worries of VIC the safety design ISO/IEC.AS/NZS 17799:2001 is
embraced through the government’s risk supervision specialist.
It has been revealed that the ISMS, VIC, decided code besides the risk assessment
technique are interconnected to one another. The threats of VIC are yet again separated in four
exceptional parts. Merely afterward the effective finishing of these four phases the VIC threat
may be measured by the supervision professional of the business. The explicit progresses of
threats those are illustrious incorporate risk ID, chance examination, chance assessment and risk
documentation. In this manner, this can be accidental that, the figure 1 illustrates to the threats
and their mitigation method. However, with the intention of accumulating an organization of
threats, individual risk appraisal practices are similarly clarified within this report as well as
within the above outline too.
3. Comparative analysis of deliberate and accidental threat
3.1 Accidental threat
Subsequent to studying, threats connected to VIC has been uncovered government
opposes various threats. Taken as an example, deliberate and accidental threat along with the
ordinary threat. Amongst these threats, the deliberate along with accidental threats are
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

4IT RISK MANAGEMENT
concerning VIC the most. The identification of accidental threats are the effect of the mistakes
and exclusion done by the staff and users (Jouini, Rabai & Aissa, 2014). The data security level
issue for the most part happens because of absence of concern of the representatives, employed
for the VIC.
It is recognized that, mistakes within program, code and application are the concerns
those for the most part influences the present circumstance of the organization. Regardless of the
possibility that the framework utilized by the organization gets smashed then that is additionally
a accidental threat that disturbs the general business functionalities, buyer's certainty and
legitimate liabilities also. Then again the other coaccidental threats may happen if legitimate
mindfulness is not produced among the clients if the organization (Nurse et al., 2014). In the
meantime because of mistaken information documentation the UI may end up noticeably
confounded because of this reason, the, believability, classification and the accessibility of data
additionally may get intruded. Distinctive specialized disappointment, for example, absence of
reinforcement office, business progression positioning is the accidental threats happened in VIC.
3.2 Deliberate threat
The reason respects are referred to as the threats, which incorporate each stiff-necked
decimation and information control, programming and equipment control and data
commandeering too. In the event that the representatives, who are included to the Company are
insufficient genuine or observed to be displeased at that point, potential source level issues may
be happened. The other individual for whom this sort of issues could happened incorporate
shoppers, culprits, outsider specialists, fear based oppressors, programmers, initiates and so on
(Jouini, Rabai & Aissa, 2014). Because of deliberate threats the issues those might happen
incorporate budgetary loss of notoriety, validity, unwavering quality and confirmation, absence
concerning VIC the most. The identification of accidental threats are the effect of the mistakes
and exclusion done by the staff and users (Jouini, Rabai & Aissa, 2014). The data security level
issue for the most part happens because of absence of concern of the representatives, employed
for the VIC.
It is recognized that, mistakes within program, code and application are the concerns
those for the most part influences the present circumstance of the organization. Regardless of the
possibility that the framework utilized by the organization gets smashed then that is additionally
a accidental threat that disturbs the general business functionalities, buyer's certainty and
legitimate liabilities also. Then again the other coaccidental threats may happen if legitimate
mindfulness is not produced among the clients if the organization (Nurse et al., 2014). In the
meantime because of mistaken information documentation the UI may end up noticeably
confounded because of this reason, the, believability, classification and the accessibility of data
additionally may get intruded. Distinctive specialized disappointment, for example, absence of
reinforcement office, business progression positioning is the accidental threats happened in VIC.
3.2 Deliberate threat
The reason respects are referred to as the threats, which incorporate each stiff-necked
decimation and information control, programming and equipment control and data
commandeering too. In the event that the representatives, who are included to the Company are
insufficient genuine or observed to be displeased at that point, potential source level issues may
be happened. The other individual for whom this sort of issues could happened incorporate
shoppers, culprits, outsider specialists, fear based oppressors, programmers, initiates and so on
(Jouini, Rabai & Aissa, 2014). Because of deliberate threats the issues those might happen
incorporate budgetary loss of notoriety, validity, unwavering quality and confirmation, absence

5IT RISK MANAGEMENT
of open certainty, absence of trustworthiness, responsibility, realness and privacy too. Then
again, because of absence of essence of use firewall, Daniel of Services, malevolent assault, and
DDoS are the deliberate threats that are incessantly influencing the overall framework stream of
VIC. It has been discovered that asset starvation assault can expend the framework assets
(Atymtayeva, Kozhakhmet & Bortsova, 2014). With a specific end goal to true blue the entrance
of the clients the switch and space name server assaults and access the table sections. Indeed, if
the system framework gets over-burden at that point, the whole framework stream additionally
gets intruded. The following list represent the potential reasons for generating deliberate threats
of VIC system.
1) Absence of use of use firewall
2) Failure of utilizing the most recent adaptation of working framework
3) Immense malignant assault
4) No ease of use of antivirus and information insurance component
5) Over the information correspondence approach absence of physical security
6) Un-encryption of all the correspondence
7) Unseemly system administration
3.3 Ranking of the threat
The ranks of threats of VIC system has been visualized through the following table.
Risk Ranking
Communication error Extreme
Hardware disaster High
Unsuitable network supervision High
of open certainty, absence of trustworthiness, responsibility, realness and privacy too. Then
again, because of absence of essence of use firewall, Daniel of Services, malevolent assault, and
DDoS are the deliberate threats that are incessantly influencing the overall framework stream of
VIC. It has been discovered that asset starvation assault can expend the framework assets
(Atymtayeva, Kozhakhmet & Bortsova, 2014). With a specific end goal to true blue the entrance
of the clients the switch and space name server assaults and access the table sections. Indeed, if
the system framework gets over-burden at that point, the whole framework stream additionally
gets intruded. The following list represent the potential reasons for generating deliberate threats
of VIC system.
1) Absence of use of use firewall
2) Failure of utilizing the most recent adaptation of working framework
3) Immense malignant assault
4) No ease of use of antivirus and information insurance component
5) Over the information correspondence approach absence of physical security
6) Un-encryption of all the correspondence
7) Unseemly system administration
3.3 Ranking of the threat
The ranks of threats of VIC system has been visualized through the following table.
Risk Ranking
Communication error Extreme
Hardware disaster High
Unsuitable network supervision High
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

6IT RISK MANAGEMENT
Deficiency of convenience Extreme
Lack of confidentiality Extreme
Malicious attack Extreme
Software failure Extreme
3.4 Proper justification for the risk ranking
Subsequent to measuring the accidental and deliberate threats, both, this is being
discovered that the threats are affecting the common constancy of VIC. Deliberate threats are not
considered within fundamental phase. However, the accidental threats is often determined at the
fundamental phase. Controlling the accidental threats are possible. However, appropriate
observing methodologies then again the consider threats cannot be calculated and organized by
the management professional of VIC effectually. On the basis of these standards the deliberate
threat is situated within the temporary accidental threats, creates owing to the nonappearance of
consideration of the staff. Consequently, if the legislature movement toward becoming worry
about their employment parts and obligations at that point, accidental threats may be measured
effortlessly by the VIC's management expert. It is the tenacity behind that the accidental risk is
positioned as great however not great such as the deliberate threat.
4. Several internal and external security challenges and risks linked to VIC
system
Because of absence of risk and risk administration approaches the VIC is confronting real
level difficulties both the inward and outside. These threats are likewise hampering the basic
leadership of the VIC.
Deficiency of convenience Extreme
Lack of confidentiality Extreme
Malicious attack Extreme
Software failure Extreme
3.4 Proper justification for the risk ranking
Subsequent to measuring the accidental and deliberate threats, both, this is being
discovered that the threats are affecting the common constancy of VIC. Deliberate threats are not
considered within fundamental phase. However, the accidental threats is often determined at the
fundamental phase. Controlling the accidental threats are possible. However, appropriate
observing methodologies then again the consider threats cannot be calculated and organized by
the management professional of VIC effectually. On the basis of these standards the deliberate
threat is situated within the temporary accidental threats, creates owing to the nonappearance of
consideration of the staff. Consequently, if the legislature movement toward becoming worry
about their employment parts and obligations at that point, accidental threats may be measured
effortlessly by the VIC's management expert. It is the tenacity behind that the accidental risk is
positioned as great however not great such as the deliberate threat.
4. Several internal and external security challenges and risks linked to VIC
system
Because of absence of risk and risk administration approaches the VIC is confronting real
level difficulties both the inward and outside. These threats are likewise hampering the basic
leadership of the VIC.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7IT RISK MANAGEMENT
Deficiency of planning precedence: Beforehand executing the risk management program
within VIC, legitimate arranging is required to be embraced by the administration expert. On the
off chance that the organization neglects to receive precise arrangement then it will neglect to
actualize the best possible system. After the thought of statistic points of view of VIC it is
characterized, that the organization requires concentrating appropriately on the money related or
business structure of the organization (Kent, 2015). It has been discovered that if the
organization neglects to consider the business outline at that point, the organization will confront
this issue persistently.
Data confidentiality: The informations consume within the server of VIC stores unique
isolated information within their capacity. Along these lines, observance in attention the final
objective to continue the classification of the informations it is particularly significant to
actualize genuine security relatively assurance component (Han et al., 2014). In any case, the
organization is neglecting to embrace these security perspectives, hence the principle encounter
that the business is challenging is forfeiture of information taxonomy.
Improper infrastructure of the VIC: The Business abandonments to hold suitable
framework. Taken as an example, up and coming information management. Reminding the final
objective for alleviating this examination legitimate, information system management system is
must have been combined by VIC, within the predefined divisions (Egoeze et al., 2014).
Lack of preparation of requirement: The Business abandonments for receiving every
single important necessity those are compulsory to upsurge the present situation of the business.
In any case, because of absence of legitimate prerequisite game plan the organization
abandonments to stretch fitting assurance besides secrecy to their data storing.
Deficiency of planning precedence: Beforehand executing the risk management program
within VIC, legitimate arranging is required to be embraced by the administration expert. On the
off chance that the organization neglects to receive precise arrangement then it will neglect to
actualize the best possible system. After the thought of statistic points of view of VIC it is
characterized, that the organization requires concentrating appropriately on the money related or
business structure of the organization (Kent, 2015). It has been discovered that if the
organization neglects to consider the business outline at that point, the organization will confront
this issue persistently.
Data confidentiality: The informations consume within the server of VIC stores unique
isolated information within their capacity. Along these lines, observance in attention the final
objective to continue the classification of the informations it is particularly significant to
actualize genuine security relatively assurance component (Han et al., 2014). In any case, the
organization is neglecting to embrace these security perspectives, hence the principle encounter
that the business is challenging is forfeiture of information taxonomy.
Improper infrastructure of the VIC: The Business abandonments to hold suitable
framework. Taken as an example, up and coming information management. Reminding the final
objective for alleviating this examination legitimate, information system management system is
must have been combined by VIC, within the predefined divisions (Egoeze et al., 2014).
Lack of preparation of requirement: The Business abandonments for receiving every
single important necessity those are compulsory to upsurge the present situation of the business.
In any case, because of absence of legitimate prerequisite game plan the organization
abandonments to stretch fitting assurance besides secrecy to their data storing.

8IT RISK MANAGEMENT
VIC substance: The security preparation of VIC is not produced conferring to the
necessity of the clients relatively agents. All over again it similarly abandonments to go about
rendering to the current condition of the business (Gladstone, 2014). On behalf of this particular
motive the security planning of VIC is opposing important problems.
5. Comparison of risks and uncertainty
After examination of the VIC, it is determined that, every one of the establishments are
confronting both the kind of problems as far as threats and vulnerability. In spite of the fact that
the two threats and vulnerability are influencing the business structure of VC Government yet at
the same time there is immense distinction between the threats and vulnerability. In light of
specific factors the contrast between the threats and vulnerability are distinguished. The
differences are as follows:
Factors Risks Uncertainty
Control The situational threats of an
association can be controlled
by the administration expert
effortlessly.
It is especially troublesome
the control the vulnerability.
Measurement Threats of an organization can
be measured effortlessly by
the risk administration
professional of an enterprise.
The uncertainty or situational
blunders could not be
measured effectively by the
administration specialist.
Outcome If there must be an incidence
of threats, the normal
If there must be an incidence
of Indecision the results are
VIC substance: The security preparation of VIC is not produced conferring to the
necessity of the clients relatively agents. All over again it similarly abandonments to go about
rendering to the current condition of the business (Gladstone, 2014). On behalf of this particular
motive the security planning of VIC is opposing important problems.
5. Comparison of risks and uncertainty
After examination of the VIC, it is determined that, every one of the establishments are
confronting both the kind of problems as far as threats and vulnerability. In spite of the fact that
the two threats and vulnerability are influencing the business structure of VC Government yet at
the same time there is immense distinction between the threats and vulnerability. In light of
specific factors the contrast between the threats and vulnerability are distinguished. The
differences are as follows:
Factors Risks Uncertainty
Control The situational threats of an
association can be controlled
by the administration expert
effortlessly.
It is especially troublesome
the control the vulnerability.
Measurement Threats of an organization can
be measured effortlessly by
the risk administration
professional of an enterprise.
The uncertainty or situational
blunders could not be
measured effectively by the
administration specialist.
Outcome If there must be an incidence
of threats, the normal
If there must be an incidence
of Indecision the results are
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

9IT RISK MANAGEMENT
consequences by and large
match. In the event that the
event outcome are recognized
then that may be qualified
effortlessly likewise. Different
theoretical models are there
done the support of those
threats may be maintained a
strategic distance from and
moderated.
likewise obscure to the clients.
As of its quantitative nature,
the weakness of the
framework cannot be
restrained with any such
hypothetical representations.
Probability The odds of risk events is
higher rather the likelihood is
too high
On the other hand, odds of
events of vulnerability is not
relegated.
Risk minimization Threats could be limited
effortlessly with various risk
moderation approaches
The authoritative vulnerability
cannot be limited effortlessly.
6. Different risk control and mitigation approach
6.1 Risk control methods
Avoidance: Avoidance is amongst best measures for risk control technique. If
organization’s efforts at keeping up an important separation from the privation have been
supportive, by that time there is a no likelihood that associations will meet the keen influences of
consequences by and large
match. In the event that the
event outcome are recognized
then that may be qualified
effortlessly likewise. Different
theoretical models are there
done the support of those
threats may be maintained a
strategic distance from and
moderated.
likewise obscure to the clients.
As of its quantitative nature,
the weakness of the
framework cannot be
restrained with any such
hypothetical representations.
Probability The odds of risk events is
higher rather the likelihood is
too high
On the other hand, odds of
events of vulnerability is not
relegated.
Risk minimization Threats could be limited
effortlessly with various risk
moderation approaches
The authoritative vulnerability
cannot be limited effortlessly.
6. Different risk control and mitigation approach
6.1 Risk control methods
Avoidance: Avoidance is amongst best measures for risk control technique. If
organization’s efforts at keeping up an important separation from the privation have been
supportive, by that time there is a no likelihood that associations will meet the keen influences of
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

10IT RISK MANAGEMENT
that actual risk influence, in any case (Newton, & Asimakopoulou, 2015). This is the motive
avoidance is the elementary of the risk control methods, which are protected in upon. It is a
practice on behalf of deliberately removal a risk.
Diversification: Within the risk control technique distribution of enterprise properties
regarding changed create lines of enterprise that suggest individual possessions as well as
besides connection in arranged endeavors. With broadening, a gigantic salary risk from one line
of industry would not create miserable smarts the association's crucial apprehension.
Duplication: This risk control tactic on an exceptionally fundamental level joins the
generation of a course of action outline. It is as frequently as possible central with execution. A
disaster inside an information framework's server ought not to pass with everything taken into
account business to a stop. Or, on the other hand possibly, a fortress over server should be
quickly available for getting to if the significant server flops fantastically (Fleming, &
Koppelman, 2016). Another repetition circumstance as a threat control process is the time while
an affiliation utilizes the aids of a disaster recovery viewpoint.
Loss Prevention: This control technique is a framework that reasons for direction, as
opposed to butchers. As contrasting to in step a vital parcel as of a threat totally, this system
distinguishes a risk though attempts to oblige the risk subsequently. Taken as an example,
safeguarding standard inside a dispersal emphasis realizes that it is weak to theft. In any case,
meanwhile there sincerely is no factual methodology for managing continue an important design
from it, single disaster recovery activity application is envisioned in terms of considerate the
threat. This representation often intersect investigating security protections, protected rooms and
camcorders.
that actual risk influence, in any case (Newton, & Asimakopoulou, 2015). This is the motive
avoidance is the elementary of the risk control methods, which are protected in upon. It is a
practice on behalf of deliberately removal a risk.
Diversification: Within the risk control technique distribution of enterprise properties
regarding changed create lines of enterprise that suggest individual possessions as well as
besides connection in arranged endeavors. With broadening, a gigantic salary risk from one line
of industry would not create miserable smarts the association's crucial apprehension.
Duplication: This risk control tactic on an exceptionally fundamental level joins the
generation of a course of action outline. It is as frequently as possible central with execution. A
disaster inside an information framework's server ought not to pass with everything taken into
account business to a stop. Or, on the other hand possibly, a fortress over server should be
quickly available for getting to if the significant server flops fantastically (Fleming, &
Koppelman, 2016). Another repetition circumstance as a threat control process is the time while
an affiliation utilizes the aids of a disaster recovery viewpoint.
Loss Prevention: This control technique is a framework that reasons for direction, as
opposed to butchers. As contrasting to in step a vital parcel as of a threat totally, this system
distinguishes a risk though attempts to oblige the risk subsequently. Taken as an example,
safeguarding standard inside a dispersal emphasis realizes that it is weak to theft. In any case,
meanwhile there sincerely is no factual methodology for managing continue an important design
from it, single disaster recovery activity application is envisioned in terms of considerate the
threat. This representation often intersect investigating security protections, protected rooms and
camcorders.

11IT RISK MANAGEMENT
Loss Reduction: Loss reduction distinguishes risk along with perceiving through the
deprivation that might occur for the reason of presence of risk. The approach will attempt for
pushing the occurrence on the condition, there have to be an event or a quip risk consequence.
Taken as an example, a cooperation may essential to stock flammable substantial in a dissolving
emphasis (Schwalbe, 2015).
Separation: It is a control tactic that fuses dispersing basic possessions. It assurances that
if something extraneous happens at an area, the result to the association is limited to the points of
attention principally at that area.
6.2 Risk mitigation methods
Through a specific true aim to decrease the threats unique risk mitigation approaches are
obligatory to be clutched by the organization authority of VIC.
Acceptance of risk: Threats are often restricted if risks are identified by the organization
master. This will provide various standard decision for the organization manager for calming
perils.
Risk avoidance: Through the avoidance of risk threats can be moderated. In light of the
situating the perils could be sidestepped. Despite the way that avoidance of risk is considered as
an exclusive approach yet in the meantime with the assistance of this technique the risks can be
easily restricted.
Risk Limitation: Distinctive business uses this risk limitation technique to the extent a
huge part of the cases (Schwalbe, 2015). This surmises affiliations must cutoff its introduction to
taking a couple of exercises. Both the risk affirmation and avoidance systems.
Loss Reduction: Loss reduction distinguishes risk along with perceiving through the
deprivation that might occur for the reason of presence of risk. The approach will attempt for
pushing the occurrence on the condition, there have to be an event or a quip risk consequence.
Taken as an example, a cooperation may essential to stock flammable substantial in a dissolving
emphasis (Schwalbe, 2015).
Separation: It is a control tactic that fuses dispersing basic possessions. It assurances that
if something extraneous happens at an area, the result to the association is limited to the points of
attention principally at that area.
6.2 Risk mitigation methods
Through a specific true aim to decrease the threats unique risk mitigation approaches are
obligatory to be clutched by the organization authority of VIC.
Acceptance of risk: Threats are often restricted if risks are identified by the organization
master. This will provide various standard decision for the organization manager for calming
perils.
Risk avoidance: Through the avoidance of risk threats can be moderated. In light of the
situating the perils could be sidestepped. Despite the way that avoidance of risk is considered as
an exclusive approach yet in the meantime with the assistance of this technique the risks can be
easily restricted.
Risk Limitation: Distinctive business uses this risk limitation technique to the extent a
huge part of the cases (Schwalbe, 2015). This surmises affiliations must cutoff its introduction to
taking a couple of exercises. Both the risk affirmation and avoidance systems.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 14
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





