MITS5004: IT Security - Information Technology Risk Assessment Report
VerifiedAdded on 2022/10/05
|10
|2137
|431
Report
AI Summary
This report provides a comprehensive IT risk assessment, evaluating vulnerabilities, threats, and mitigation strategies within an information management system. It begins with an introduction highlighting the importance of risk assessment in safeguarding data from technological advancements and hacking attempts, and emphasizing the role of IT security in data protection. The report details the purpose and scope of the assessment, outlining testing methods, including the use of tools like NIST and NSA guidelines, and describes the risk assessment methodology, which includes resource analysis, threat identification, and countermeasure implementation. A system description is provided, emphasizing the use of secure Cisco routers and firewalls within an intranet environment. The report also covers the information management system, the responsible IT security team, and a table outlining potential threats, categorizing them as those caused by fires, water damage, espionage, theft, hacking, malicious code, eavesdropping, data integrity loss, fraud, power disruptions, hardware denial of service, and program errors. The report concludes by reiterating the significance of regular audit reports and the importance of risk assessment in implementing new security policies, with a list of references to support the analysis.

Information Technology and Risk Assessment Report 1
Information Technology and Risk assessment
Affiliate Institution
Student
Date
Information Technology and Risk assessment
Affiliate Institution
Student
Date
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Information Technology and Risk Assessment Report 2
Table of Contents
Introduction.................................................................................................................................................2
Purpose........................................................................................................................................................3
Scope...........................................................................................................................................................4
Testing methods..........................................................................................................................................4
Risk assessment methodology.....................................................................................................................4
System description......................................................................................................................................5
Information management system...........................................................................................................6
Responsible team....................................................................................................................................6
Potential threats......................................................................................................................................6
Conclusion...................................................................................................................................................7
Table of Contents
Introduction.................................................................................................................................................2
Purpose........................................................................................................................................................3
Scope...........................................................................................................................................................4
Testing methods..........................................................................................................................................4
Risk assessment methodology.....................................................................................................................4
System description......................................................................................................................................5
Information management system...........................................................................................................6
Responsible team....................................................................................................................................6
Potential threats......................................................................................................................................6
Conclusion...................................................................................................................................................7

Information Technology and Risk Assessment Report 3
Introduction
Most of the companies experiences high risks because of the constant advancement in
technology. They feel that their data are not safe on the internet. This is because hackers have
become a problematic as they are ever busy working round the clock to ensure that they still
from these companies. [16]However, Risk Assessment and Risk management is an important
tool which can help in ensuring that all the company information remain safe. In IT security is
the most important factor to be considered. This days, most companies have migrated most of
their data and information into the cloud. Cloud computing is a working technology which has
really made all things possible. [16] Our data are stored over the space and hence a step in data
security has been achieved through this feature
However, data backup as a form of data security has been achieved, but hacking remains a major
threat as most of the data has been just exposed all over the internet. This data may be sniffed or
spoofed by hackers from the space. So it is still a bigger challenge whatsoever.[5]
Risk assessment and Risk management will help to ensure that:
The application are provided with enough security level of protection for IT systems
To ensure that the IT systems meet the ISO standards
The company is fully satisfied with the IT system and provide a very user friendly IT
environment.
The acceptable level of risk is met. [14]
The risk assessment report clearly describes the information management system in which the
company is using to manage its customers and the members of the staff. [10]The system can be
any IT application which the company is using to ensure that the management processes are
Introduction
Most of the companies experiences high risks because of the constant advancement in
technology. They feel that their data are not safe on the internet. This is because hackers have
become a problematic as they are ever busy working round the clock to ensure that they still
from these companies. [16]However, Risk Assessment and Risk management is an important
tool which can help in ensuring that all the company information remain safe. In IT security is
the most important factor to be considered. This days, most companies have migrated most of
their data and information into the cloud. Cloud computing is a working technology which has
really made all things possible. [16] Our data are stored over the space and hence a step in data
security has been achieved through this feature
However, data backup as a form of data security has been achieved, but hacking remains a major
threat as most of the data has been just exposed all over the internet. This data may be sniffed or
spoofed by hackers from the space. So it is still a bigger challenge whatsoever.[5]
Risk assessment and Risk management will help to ensure that:
The application are provided with enough security level of protection for IT systems
To ensure that the IT systems meet the ISO standards
The company is fully satisfied with the IT system and provide a very user friendly IT
environment.
The acceptable level of risk is met. [14]
The risk assessment report clearly describes the information management system in which the
company is using to manage its customers and the members of the staff. [10]The system can be
any IT application which the company is using to ensure that the management processes are
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Information Technology and Risk Assessment Report 4
made easier. All the vulnerabilities that may be existing within the information system are stated
in the risk analysis report. Also possible solutions are also given to enable to solve the said
problems.
Purpose
The main idea about this report is to help in the management of the organization. As we know
that IT is an enabler for the rapid growth of any company. Risk analysis report entails the
technical solutions and controls which will help to gap the high risk to threats in any information
management systems. [10]
By carrying out this assessment report, we will be able to outline all the vulnerabilities which
may be existing in an information management system. [13]This vulnerabilities will be analyzed
and the solution is provided to make the information management system more secure.
This report is conducted by the risk assessment and management team. The team will carry out a
thorough audit and identifies all the loopholes and find ways on how to zip them. The team will
carry out the process by collecting the data and then come up with an analyzed and compiled
report. This report will be presented to the company manager for implementation and policy
making. [13]
Ensure data are
secure/Authentication
Other Departments
Hardware Department
Networks
and
security
Business Applications
Database Enter data/retrieve secure data
Data monitoring/ retrieval
Hardware requirements are secure
IT Department and Its Functions
made easier. All the vulnerabilities that may be existing within the information system are stated
in the risk analysis report. Also possible solutions are also given to enable to solve the said
problems.
Purpose
The main idea about this report is to help in the management of the organization. As we know
that IT is an enabler for the rapid growth of any company. Risk analysis report entails the
technical solutions and controls which will help to gap the high risk to threats in any information
management systems. [10]
By carrying out this assessment report, we will be able to outline all the vulnerabilities which
may be existing in an information management system. [13]This vulnerabilities will be analyzed
and the solution is provided to make the information management system more secure.
This report is conducted by the risk assessment and management team. The team will carry out a
thorough audit and identifies all the loopholes and find ways on how to zip them. The team will
carry out the process by collecting the data and then come up with an analyzed and compiled
report. This report will be presented to the company manager for implementation and policy
making. [13]
Ensure data are
secure/Authentication
Other Departments
Hardware Department
Networks
and
security
Business Applications
Database Enter data/retrieve secure data
Data monitoring/ retrieval
Hardware requirements are secure
IT Department and Its Functions
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Information Technology and Risk Assessment Report 5
Scope
The scope of this report is to evaluate all the vulnerabilities in the information management
system. The report will be covered in the areas of operational level. Management level and the
technical level. [6]This report is limited to information management system security threats,
attacks and vulnerabilities. It will be carried out through conducting interviews from the site
visits and conducting the environmental security reviews.
Testing methods
Risk assessment team will conduct physical testing of the management information system so
that raw results are achieved. System testing will be done step by step to ensure that no field is
left unchecked. [11] This is because programmers may be prone to minor errors. Therefore,
testing the software program before use is paramount and will help to gap any vulnerability. For
example, the program are expected to validate all the fields before deployment of the software to
be used by users. [7]
Vulnerabilities threats can be calculated by use of various tools to check the system
vulnerability. While carrying out this report, the following tools were used for testing the system
security issues;
NIST, Guidelines on Electronic Mail Security, SP-800-45, September 2002.
National Security Agency (NSA), Windows 2000 Guides.
NSA, Windows NT Guides.
NSA, Cisco Router Guides.
NSA, E-mail and Executable Content Guides[1]
Risk assessment methodology
The risk analysis report is carried out in four distinct phases which include the following.
Scope
The scope of this report is to evaluate all the vulnerabilities in the information management
system. The report will be covered in the areas of operational level. Management level and the
technical level. [6]This report is limited to information management system security threats,
attacks and vulnerabilities. It will be carried out through conducting interviews from the site
visits and conducting the environmental security reviews.
Testing methods
Risk assessment team will conduct physical testing of the management information system so
that raw results are achieved. System testing will be done step by step to ensure that no field is
left unchecked. [11] This is because programmers may be prone to minor errors. Therefore,
testing the software program before use is paramount and will help to gap any vulnerability. For
example, the program are expected to validate all the fields before deployment of the software to
be used by users. [7]
Vulnerabilities threats can be calculated by use of various tools to check the system
vulnerability. While carrying out this report, the following tools were used for testing the system
security issues;
NIST, Guidelines on Electronic Mail Security, SP-800-45, September 2002.
National Security Agency (NSA), Windows 2000 Guides.
NSA, Windows NT Guides.
NSA, Cisco Router Guides.
NSA, E-mail and Executable Content Guides[1]
Risk assessment methodology
The risk analysis report is carried out in four distinct phases which include the following.

Information Technology and Risk Assessment Report 6
1. The risk analysis of resources, security threats, security controls, and vulnerabilities
2. Counter measures implementations
3. Decision making and control measures
4. Regular review of audit program[2]
System description
After the system analysis and design has been completed, a new system is designed to provide a
solution to the existing system. The system must be a highly validated and sensitive to security
threats. The proposed system must be well tested and is free from bugs. This means that the team
will be responsible for testing all security related features. As the security is the most important
tool in information management system.[3]
In this report, the case study show that the system is comprising of both the hardware and
software components. However, the information management system is designed in such a way
that it will use a highly secured cisco routers and firewalls. This will help to prevent attackers
from intruding into the system and steal the resources belonging to the company. Cisco routers
consists of WPS security features which is basically hard for system hackers from hacking the
information system. [12]
The new system will be working under the intranet environment which will help to protect the
system from being modified by hackers. Intranet is a highly secured internet connection to the
computers communicating together over the management information system. [8]
However, regarding to the integrated system developed, this report outlines only the security risk
and features established to ensure that the system developed meet the standards and the
requirements by the company.
1. The risk analysis of resources, security threats, security controls, and vulnerabilities
2. Counter measures implementations
3. Decision making and control measures
4. Regular review of audit program[2]
System description
After the system analysis and design has been completed, a new system is designed to provide a
solution to the existing system. The system must be a highly validated and sensitive to security
threats. The proposed system must be well tested and is free from bugs. This means that the team
will be responsible for testing all security related features. As the security is the most important
tool in information management system.[3]
In this report, the case study show that the system is comprising of both the hardware and
software components. However, the information management system is designed in such a way
that it will use a highly secured cisco routers and firewalls. This will help to prevent attackers
from intruding into the system and steal the resources belonging to the company. Cisco routers
consists of WPS security features which is basically hard for system hackers from hacking the
information system. [12]
The new system will be working under the intranet environment which will help to protect the
system from being modified by hackers. Intranet is a highly secured internet connection to the
computers communicating together over the management information system. [8]
However, regarding to the integrated system developed, this report outlines only the security risk
and features established to ensure that the system developed meet the standards and the
requirements by the company.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
Information Technology and Risk Assessment Report 7
Information management system
This system is a secure system that was developed to make the company’s management
processes secure and easy to manage. The risk analysis report was carried out by the IT security
team to ensure that the system is fully free from bugs. [1]
Responsible team
This report was carried out in the essence that the quality of service offered by the company is
maintain at high quality. This is to keep the company competitive and maintain customer
relationship. This is the reason why the IT security team is responsible for taking an assessment
risk analysis and designing Risk Analysis Report on regular basis to ensure that no one has harm
the companies profile. [9]
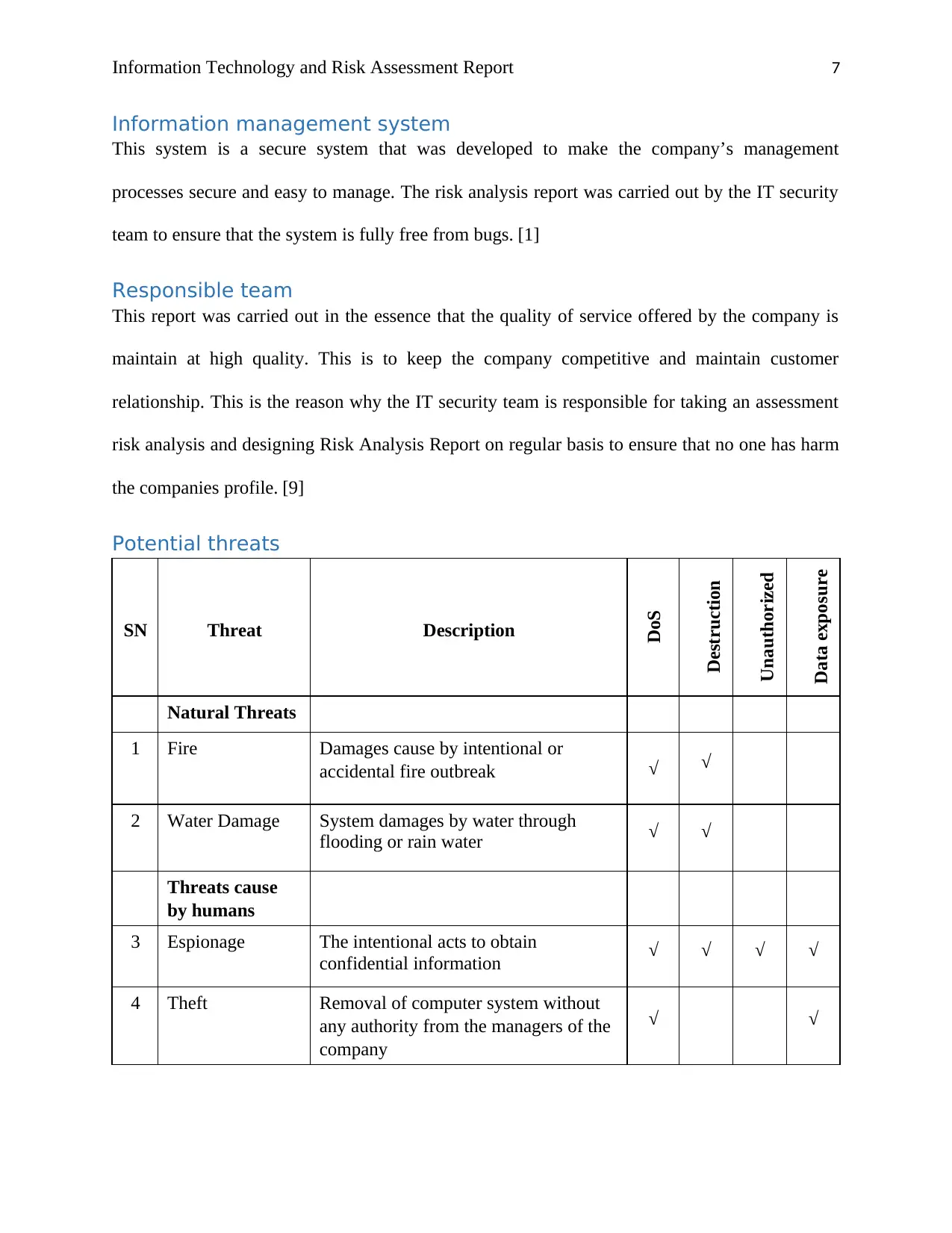
Potential threats
SN Threat Description
DoS
Destruction
Unauthorized
modification
Data exposure
Natural Threats
1 Fire Damages cause by intentional or
accidental fire outbreak √ √
2 Water Damage System damages by water through
flooding or rain water √ √
Threats cause
by humans
3 Espionage The intentional acts to obtain
confidential information √ √ √ √
4 Theft Removal of computer system without
any authority from the managers of the
company
√ √
Information management system
This system is a secure system that was developed to make the company’s management
processes secure and easy to manage. The risk analysis report was carried out by the IT security
team to ensure that the system is fully free from bugs. [1]
Responsible team
This report was carried out in the essence that the quality of service offered by the company is
maintain at high quality. This is to keep the company competitive and maintain customer
relationship. This is the reason why the IT security team is responsible for taking an assessment
risk analysis and designing Risk Analysis Report on regular basis to ensure that no one has harm
the companies profile. [9]
Potential threats
SN Threat Description
DoS
Destruction
Unauthorized
modification
Data exposure
Natural Threats
1 Fire Damages cause by intentional or
accidental fire outbreak √ √
2 Water Damage System damages by water through
flooding or rain water √ √
Threats cause
by humans
3 Espionage The intentional acts to obtain
confidential information √ √ √ √
4 Theft Removal of computer system without
any authority from the managers of the
company
√ √
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
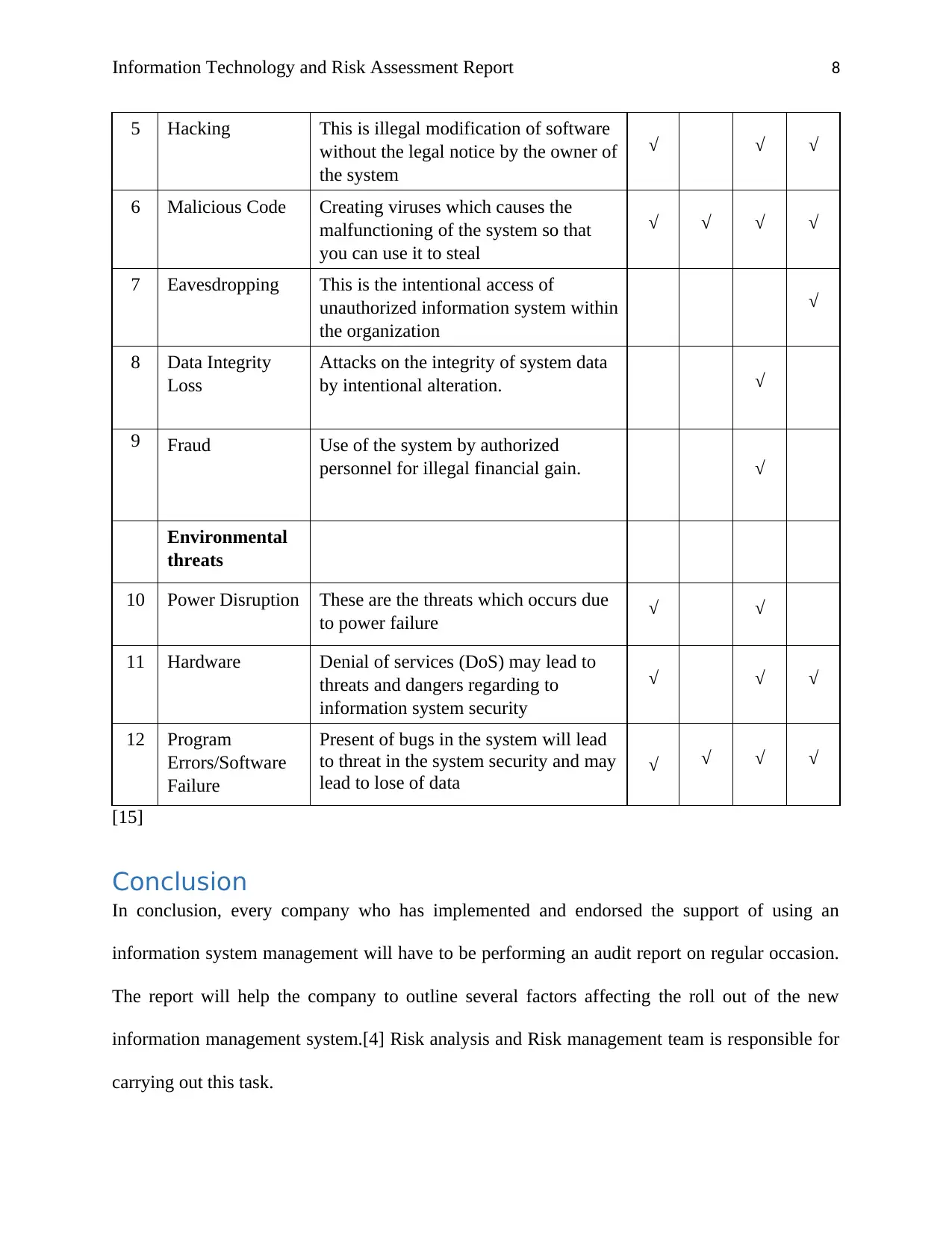
Information Technology and Risk Assessment Report 8
5 Hacking This is illegal modification of software
without the legal notice by the owner of
the system
√ √ √
6 Malicious Code Creating viruses which causes the
malfunctioning of the system so that
you can use it to steal
√ √ √ √
7 Eavesdropping This is the intentional access of
unauthorized information system within
the organization
√
8 Data Integrity
Loss
Attacks on the integrity of system data
by intentional alteration. √
9 Fraud Use of the system by authorized
personnel for illegal financial gain. √
Environmental
threats
10 Power Disruption These are the threats which occurs due
to power failure √ √
11 Hardware Denial of services (DoS) may lead to
threats and dangers regarding to
information system security
√ √ √
12 Program
Errors/Software
Failure
Present of bugs in the system will lead
to threat in the system security and may
lead to lose of data √ √ √ √
[15]
Conclusion
In conclusion, every company who has implemented and endorsed the support of using an
information system management will have to be performing an audit report on regular occasion.
The report will help the company to outline several factors affecting the roll out of the new
information management system.[4] Risk analysis and Risk management team is responsible for
carrying out this task.
5 Hacking This is illegal modification of software
without the legal notice by the owner of
the system
√ √ √
6 Malicious Code Creating viruses which causes the
malfunctioning of the system so that
you can use it to steal
√ √ √ √
7 Eavesdropping This is the intentional access of
unauthorized information system within
the organization
√
8 Data Integrity
Loss
Attacks on the integrity of system data
by intentional alteration. √
9 Fraud Use of the system by authorized
personnel for illegal financial gain. √
Environmental
threats
10 Power Disruption These are the threats which occurs due
to power failure √ √
11 Hardware Denial of services (DoS) may lead to
threats and dangers regarding to
information system security
√ √ √
12 Program
Errors/Software
Failure
Present of bugs in the system will lead
to threat in the system security and may
lead to lose of data √ √ √ √
[15]
Conclusion
In conclusion, every company who has implemented and endorsed the support of using an
information system management will have to be performing an audit report on regular occasion.
The report will help the company to outline several factors affecting the roll out of the new
information management system.[4] Risk analysis and Risk management team is responsible for
carrying out this task.

Information Technology and Risk Assessment Report 9
Also, Risk Assessment is known to be the most important tool to be used while implementing
new policies concerning the security threats and system vulnerabilities. The department must
ensure that the system and the hardware to be used are free from vulnerability. This will ensure
that counterfeit products are forfeited at all.
References
[1]C. Axelrod, Outsourcing information security. Boston: Artech House, 2004.
[2]M. Aydın, Non-traditional security threats and regional cooperation in the southern caucasus.
Amsterdam: IOS Press, 2011.
[3]T. Canavan and K. Crowder, Joomla! web security. Birmingham, UK: Packt Pub., 2008.
[4]M. Erbschloe, Implementing homeland security for enterprise IT. Boston: Digital Press, 2004.
[5]D. Hoffman, Blackjacking. Indianapolis, IN: Wiley Pub., 2007.
[6]L. Issel, "Theory for advances in health care management research", Health Care Management
Review, vol. 43, no. 2, p. 91, 2018. Available: 10.1097/hmr.0000000000000201.
[7]S. Jones, Securing tyrants or fostering reform?. Santa Monica, CA: RAND Corp., 2006.
[8]M. Jost and M. Cobb, IIS security. New York: McGraw-Hill/Osborne, 2002.
[9]R. Lal, Central Asia and its Asian neighbors. Santa Monica, CA: RAND Corp., 2006.
[10]R. Oppliger, Security technologies for the World Wide Web. Boston, MA: Artech House,
2000.
[11]M. Sharpe and A. Agboluaje, Science and society in the face of the new security threats.
Amsterdam: IOS Press, 2006.
Also, Risk Assessment is known to be the most important tool to be used while implementing
new policies concerning the security threats and system vulnerabilities. The department must
ensure that the system and the hardware to be used are free from vulnerability. This will ensure
that counterfeit products are forfeited at all.
References
[1]C. Axelrod, Outsourcing information security. Boston: Artech House, 2004.
[2]M. Aydın, Non-traditional security threats and regional cooperation in the southern caucasus.
Amsterdam: IOS Press, 2011.
[3]T. Canavan and K. Crowder, Joomla! web security. Birmingham, UK: Packt Pub., 2008.
[4]M. Erbschloe, Implementing homeland security for enterprise IT. Boston: Digital Press, 2004.
[5]D. Hoffman, Blackjacking. Indianapolis, IN: Wiley Pub., 2007.
[6]L. Issel, "Theory for advances in health care management research", Health Care Management
Review, vol. 43, no. 2, p. 91, 2018. Available: 10.1097/hmr.0000000000000201.
[7]S. Jones, Securing tyrants or fostering reform?. Santa Monica, CA: RAND Corp., 2006.
[8]M. Jost and M. Cobb, IIS security. New York: McGraw-Hill/Osborne, 2002.
[9]R. Lal, Central Asia and its Asian neighbors. Santa Monica, CA: RAND Corp., 2006.
[10]R. Oppliger, Security technologies for the World Wide Web. Boston, MA: Artech House,
2000.
[11]M. Sharpe and A. Agboluaje, Science and society in the face of the new security threats.
Amsterdam: IOS Press, 2006.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Information Technology and Risk Assessment Report 10
[12]G. Tamer and H. Çetinkaya, "Impact of quality management system on health institutions",
Health Care Academician Journal, vol. 5, no. 2, p. 97, 2018. Available: 10.5455/sad.13-
1525267367.
[13]T. Aven and O. Renn, "An Evaluation of the Treatment of Risk and Uncertainties in the
IPCC Reports on Climate Change", Risk Analysis, vol. 35, no. 4, pp. 701-712, 2014. Available:
10.1111/risa.12298.
[14]H. Gebresilassie, "Empirical Analysis on Potential Risk Factors for Domestic Violence
against Women in Ethiopia", Journal of Scientific Research and Reports, pp. 1-11, 2019.
Available: 10.9734/jsrr/2019/v24i230152.
[15]"Luxembourg", IMF Staff Country Reports, vol. 17, no. 261, 2017. Available:
10.5089/9781484316832.002.
[16]G. Cimini, T. Squartini, D. Garlaschelli and A. Gabrielli, "Systemic Risk Analysis on
Reconstructed Economic and Financial Networks", Scientific Reports, vol. 5, no. 1, 2015.
Available: 10.1038/srep15758.
[12]G. Tamer and H. Çetinkaya, "Impact of quality management system on health institutions",
Health Care Academician Journal, vol. 5, no. 2, p. 97, 2018. Available: 10.5455/sad.13-
1525267367.
[13]T. Aven and O. Renn, "An Evaluation of the Treatment of Risk and Uncertainties in the
IPCC Reports on Climate Change", Risk Analysis, vol. 35, no. 4, pp. 701-712, 2014. Available:
10.1111/risa.12298.
[14]H. Gebresilassie, "Empirical Analysis on Potential Risk Factors for Domestic Violence
against Women in Ethiopia", Journal of Scientific Research and Reports, pp. 1-11, 2019.
Available: 10.9734/jsrr/2019/v24i230152.
[15]"Luxembourg", IMF Staff Country Reports, vol. 17, no. 261, 2017. Available:
10.5089/9781484316832.002.
[16]G. Cimini, T. Squartini, D. Garlaschelli and A. Gabrielli, "Systemic Risk Analysis on
Reconstructed Economic and Financial Networks", Scientific Reports, vol. 5, no. 1, 2015.
Available: 10.1038/srep15758.
1 out of 10
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.




