Information Technology Security Report: Analysis and Overview
VerifiedAdded on 2023/01/17
|13
|2712
|67
Report
AI Summary
This report delves into the critical aspects of information technology security, commencing with an introduction to cyberwarfare, defining it as the use of computers and networks in the battlespace, highlighting its challenges and motivations, which often revolve around financial gain and access to sensitive information. The report then explores cryptography, emphasizing its role in protecting data through encryption methods, contrasting symmetric and public key encryption, and discussing their respective algorithms, applications, strengths, and weaknesses. The report also covers network security fundamentals, differentiating between Mandatory Access Control and Discretionary Access Control, detailing their characteristics, strengths, weaknesses, and applications in different systems. The report provides a comprehensive overview of the key components of IT security.

Running head: INFORMATION TECHNOLOGY SECURITY
Information Technology Security
Name of the student:
Name of the university:
Author note:
Information Technology Security
Name of the student:
Name of the university:
Author note:
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1INFORMATION TECHNOLOGY SECURITY
Topic 1: Introduction to information security
Cyberwarfare is defined as the type of cyber-attack targeting the battlespace or
warfare which makes uses of computers, networks and online control systems. Both offensive
and defensive operations are involved in the cyberwarfare attacks (Randy and Raymond,
2014). It refers to the attacking of computer viruses and hacking in order to disrupt the
monitoring systems completely. This type of cyber attack often aims in creating damage,
destruction and even death. In cyber warfare it becomes extremely difficult to identify the
force that is causing this attack as it could be military, civilian or industrial as well.
Cyberwarfare has become the greatest challenge for which the entire security of different
nations is concerned. Cyberwarfare is the new battlefield where team of hackers from various
nations duel.
The type of motivating factor that works behind each cyberattacks in todays world is
only profit. According to reports it has been found that cyber crime is estimated to become a
$2.1 trillion problem by the year of 2019. Cyber criminals use financial malwares like Shifu,
Rovnix, Carbanak in order to steal the bank credentials of the victims. They also take the help
of cyber-attacks such as ransomware attack by performing a distributed denial of service
attack in the victim’s computer. His type of attack has gained huge popularity in the recent
years. But money is not only the chief motivating factor for which the hackers perform this
cyber-attack. Hackers often perform this attack on private company who are responsible for
developing technologies for the military use (Solis, 2014). Here the main motive behind these
types of attacks is to gain information about the military or political or economic values. This
type of attacks could be state sponsored where a group of non-profit hackers are performing
this attack on behalf of any state or corporate entity. Besides this reason, there can be also
more personal reasons such as vanity, outrage, revenge or many others. Any company or
Topic 1: Introduction to information security
Cyberwarfare is defined as the type of cyber-attack targeting the battlespace or
warfare which makes uses of computers, networks and online control systems. Both offensive
and defensive operations are involved in the cyberwarfare attacks (Randy and Raymond,
2014). It refers to the attacking of computer viruses and hacking in order to disrupt the
monitoring systems completely. This type of cyber attack often aims in creating damage,
destruction and even death. In cyber warfare it becomes extremely difficult to identify the
force that is causing this attack as it could be military, civilian or industrial as well.
Cyberwarfare has become the greatest challenge for which the entire security of different
nations is concerned. Cyberwarfare is the new battlefield where team of hackers from various
nations duel.
The type of motivating factor that works behind each cyberattacks in todays world is
only profit. According to reports it has been found that cyber crime is estimated to become a
$2.1 trillion problem by the year of 2019. Cyber criminals use financial malwares like Shifu,
Rovnix, Carbanak in order to steal the bank credentials of the victims. They also take the help
of cyber-attacks such as ransomware attack by performing a distributed denial of service
attack in the victim’s computer. His type of attack has gained huge popularity in the recent
years. But money is not only the chief motivating factor for which the hackers perform this
cyber-attack. Hackers often perform this attack on private company who are responsible for
developing technologies for the military use (Solis, 2014). Here the main motive behind these
types of attacks is to gain information about the military or political or economic values. This
type of attacks could be state sponsored where a group of non-profit hackers are performing
this attack on behalf of any state or corporate entity. Besides this reason, there can be also
more personal reasons such as vanity, outrage, revenge or many others. Any company or

2INFORMATION TECHNOLOGY SECURITY
individual may become the victim of cyber attack whose consequences can range to
dangerous outcomes.
Since few decades high contour cyber attacks have progressively augmented among
the national administrations such as, China, United States, Russia and many more. As cyber
warfare develops the battleground of choice for industrialized nations managements are able
to introduce direct attacks in contradiction of each other in confidentiality and deprived of the
risk of instigating physical harm. But as computing knowledge is proceeding earlier than
international guidelines and policies, virtual weapons offer a new technique for nations to
remunerate war without inflowing into an actual armed confrontation. This tendency has
caused in a new international threats as cardinal technology becomes progressively integrated
into all facets of life (Korstanje, 2016). Virtually in the modern computerized world, all
businesses are critical to supporting modern civilizations and all computers and their
dependence increases as expertise improves. The increasing confidence on computers
unlocks up the opportunity for spiteful agents to upset or destroy vital data systems and
facilities (Robinson, Jones & Janicke, 2015). As a result, national safety governments are
going outside air land and marine defences and are following urbane cyber security and cyber
warfare policies. Often day cyber bouts are taking compensations of zero-day susceptibility
which refers to software safety flaws that have no community knowledge and consequently
gives the software designers zero days to respond.
Preventive measures are somewhat difficult to figure out in the world pf cyber attack
because the ability of the attackers remains anonymous. However, an unrestricted offensive
cyber warfare attack provides some clues for identifying the attacker (Hruza, Sousek &
Szabo, 2014). It is necessary that strategies of prevention should be adopted in order to
prevent the attacks in the cyber space. Defences can also be developed in order to shift the
defender by identifying he mode of attack and blocking them while patching the
individual may become the victim of cyber attack whose consequences can range to
dangerous outcomes.
Since few decades high contour cyber attacks have progressively augmented among
the national administrations such as, China, United States, Russia and many more. As cyber
warfare develops the battleground of choice for industrialized nations managements are able
to introduce direct attacks in contradiction of each other in confidentiality and deprived of the
risk of instigating physical harm. But as computing knowledge is proceeding earlier than
international guidelines and policies, virtual weapons offer a new technique for nations to
remunerate war without inflowing into an actual armed confrontation. This tendency has
caused in a new international threats as cardinal technology becomes progressively integrated
into all facets of life (Korstanje, 2016). Virtually in the modern computerized world, all
businesses are critical to supporting modern civilizations and all computers and their
dependence increases as expertise improves. The increasing confidence on computers
unlocks up the opportunity for spiteful agents to upset or destroy vital data systems and
facilities (Robinson, Jones & Janicke, 2015). As a result, national safety governments are
going outside air land and marine defences and are following urbane cyber security and cyber
warfare policies. Often day cyber bouts are taking compensations of zero-day susceptibility
which refers to software safety flaws that have no community knowledge and consequently
gives the software designers zero days to respond.
Preventive measures are somewhat difficult to figure out in the world pf cyber attack
because the ability of the attackers remains anonymous. However, an unrestricted offensive
cyber warfare attack provides some clues for identifying the attacker (Hruza, Sousek &
Szabo, 2014). It is necessary that strategies of prevention should be adopted in order to
prevent the attacks in the cyber space. Defences can also be developed in order to shift the
defender by identifying he mode of attack and blocking them while patching the
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3INFORMATION TECHNOLOGY SECURITY
vulnerability. Essential network services should be isolated from usual networks in order to
maintain the data secured. Besides all these counter measures, physical security and
personnel training can also minimize the threat of malicious activities.
Topic 2: Cryptography
Cryptography is essentially important as it allows users to securely protect data, so
that it cannot be accessed by anyone else (Katz & Lindell, 2014). Cryptography method is
used to protect corporate secrets, secure classified information and to protect personal
information to guard against things like identity theft.
In todays setting, encryption is an significant part of calculating in order to keep
records secured and to attain a secured statement. Encryption is the procedure of captivating
data and indoctrination it into a method that cannot be recited by unauthorized folks. There
are two categories of encryption arrangements that are used. These are Symmetric key
encryption and public key encryption.
The comparison between the symmetric and public key encryption are given below:
Factors of comparison Symmetric key encryption Public key encryption
Description Symmetric key encryption
uses the similar key to
encode data as to decrypt
data. This usually makes it
quicker than public key
encryption (Naik & Naik,
2014).
In Public key encryption,
two types of key are used
namely public and private
key. Unlike symmetric key
encryption, each key of
public key encryption
performs unique actions
(Hofheinz & Jager, 2016).
The public key is used to
scramble data whereas the
private key is used to
decrypt data.
Algorithm Symmetric key encryption
uses two types of algorithms
The algorithms of public key
encryption include the RSA
vulnerability. Essential network services should be isolated from usual networks in order to
maintain the data secured. Besides all these counter measures, physical security and
personnel training can also minimize the threat of malicious activities.
Topic 2: Cryptography
Cryptography is essentially important as it allows users to securely protect data, so
that it cannot be accessed by anyone else (Katz & Lindell, 2014). Cryptography method is
used to protect corporate secrets, secure classified information and to protect personal
information to guard against things like identity theft.
In todays setting, encryption is an significant part of calculating in order to keep
records secured and to attain a secured statement. Encryption is the procedure of captivating
data and indoctrination it into a method that cannot be recited by unauthorized folks. There
are two categories of encryption arrangements that are used. These are Symmetric key
encryption and public key encryption.
The comparison between the symmetric and public key encryption are given below:
Factors of comparison Symmetric key encryption Public key encryption
Description Symmetric key encryption
uses the similar key to
encode data as to decrypt
data. This usually makes it
quicker than public key
encryption (Naik & Naik,
2014).
In Public key encryption,
two types of key are used
namely public and private
key. Unlike symmetric key
encryption, each key of
public key encryption
performs unique actions
(Hofheinz & Jager, 2016).
The public key is used to
scramble data whereas the
private key is used to
decrypt data.
Algorithm Symmetric key encryption
uses two types of algorithms
The algorithms of public key
encryption include the RSA
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
4INFORMATION TECHNOLOGY SECURITY
namely, Stream cipher
algorithm which operates on
single bits and the Block
cipher algorithm which
operates on fixed length of
grouped bits known as
blocks (Kansa & Mittal,
2014).
algorithm, ECC algorithm
and Rabin cryptosystems.
Application Symmetric key encryption is
typically used for bulk
encryption methods where
large amount of data needs
to be encrypted. For
example, in database
encryption. It is also applied
in the field of payment
applications, validation
systems and random number
generation system.
Public key encryption are
generally applied in business
applications such as for
digital signatures.
Modern day application of
public key encryption is
used in encrypting
WhatsApp to provide end to
end encryption of the
sessions between WhatsApp
clients.
Strengths
Symmetric key encryption
helps in providing
authentication till the keys
used in the encryption
process remains secured, it
helps in encrypting data very
quickly, it allows encryption
and decryption of
information using the same
key only.
Asymmetric key encryption
or public key encryption
helps in protecting
information transfer through
unsecured communication
channel (Ma et al., 2015). As
it is mathematically
infeasible to decrypt the
private key using the public
key in the outside world,
hence the public key can be
easily exposed. This
prevents the copying of a
key by third parties and
spying the communication
between sender and receiver.
Weakness
The problem with this type
of encryption is that in order
to decrypt the figures, the
symmetric key needs to be
obtainable. This causes two
glitches one is that the key
needs to be warehoused
securely. If an aggressor
gains access to this key they
could decrypt any facts that
the key was cast-off to
encrypt. Another problem
with this type of encryption
is that if additional party
needs to decrypt the
Though public key
encryption works extremely
well ensuring security, but
still it has some serious
weaknesses. Firstly, it is
based on complicated
mathematics as a result of
which computers need to
work very hard to encrypt
and decrypt the information.
It becomes a serious
problem while working with
large quantities of encrypted
data.
Another weakness that arises
namely, Stream cipher
algorithm which operates on
single bits and the Block
cipher algorithm which
operates on fixed length of
grouped bits known as
blocks (Kansa & Mittal,
2014).
algorithm, ECC algorithm
and Rabin cryptosystems.
Application Symmetric key encryption is
typically used for bulk
encryption methods where
large amount of data needs
to be encrypted. For
example, in database
encryption. It is also applied
in the field of payment
applications, validation
systems and random number
generation system.
Public key encryption are
generally applied in business
applications such as for
digital signatures.
Modern day application of
public key encryption is
used in encrypting
WhatsApp to provide end to
end encryption of the
sessions between WhatsApp
clients.
Strengths
Symmetric key encryption
helps in providing
authentication till the keys
used in the encryption
process remains secured, it
helps in encrypting data very
quickly, it allows encryption
and decryption of
information using the same
key only.
Asymmetric key encryption
or public key encryption
helps in protecting
information transfer through
unsecured communication
channel (Ma et al., 2015). As
it is mathematically
infeasible to decrypt the
private key using the public
key in the outside world,
hence the public key can be
easily exposed. This
prevents the copying of a
key by third parties and
spying the communication
between sender and receiver.
Weakness
The problem with this type
of encryption is that in order
to decrypt the figures, the
symmetric key needs to be
obtainable. This causes two
glitches one is that the key
needs to be warehoused
securely. If an aggressor
gains access to this key they
could decrypt any facts that
the key was cast-off to
encrypt. Another problem
with this type of encryption
is that if additional party
needs to decrypt the
Though public key
encryption works extremely
well ensuring security, but
still it has some serious
weaknesses. Firstly, it is
based on complicated
mathematics as a result of
which computers need to
work very hard to encrypt
and decrypt the information.
It becomes a serious
problem while working with
large quantities of encrypted
data.
Another weakness that arises
5INFORMATION TECHNOLOGY SECURITY
information, a secured
network needs to be used to
handover the key.
with the public key
encryption is that many
public keys uses third parties
in order to certify the public
keys. The third parties
digitally approve the public
key and generates a digital
certificate in turn. Problem
will arise in cases when the
authorizing party gets
compromised and hackers
try to issue false certificates
causing transfer of data in
the wrong destination.
Recent research trends In symmetric key encryption
methods, researches are
going on to develop a new
symmetric encryption
system which is based on
evolution algorithm. The
research is based on
combining a ciphering
evolution system with a new
ciphering method known as
fragmentation. This research
trend will help in allowing to
alter the appearance of
characters from a given text.
Most of the financial
transactions are safeguarded
using the public key
encryption method but
unfortunately, the public key
encryption scheme is tough
to devise against CCAs.
Current researches are going
on to develop a anew
technique for these error
prone CCA schemes and
turning them into a secured
CCA schemes.
Examples Examples of symmetric key
encryption includes-
Blowfish, RC4, RC5, AES
The most common example
of public key encryption is
RSA
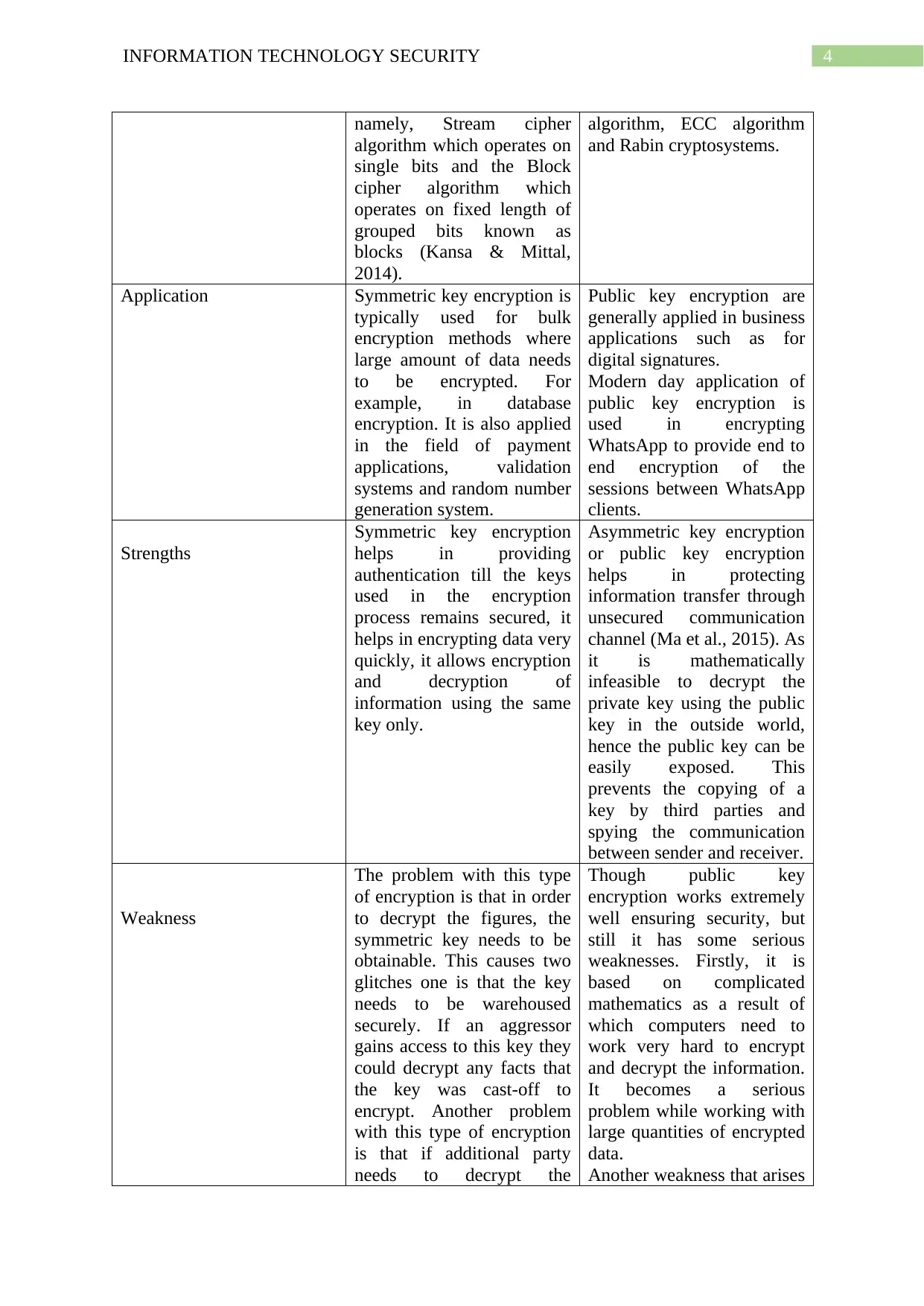
Symmetric key encryption
information, a secured
network needs to be used to
handover the key.
with the public key
encryption is that many
public keys uses third parties
in order to certify the public
keys. The third parties
digitally approve the public
key and generates a digital
certificate in turn. Problem
will arise in cases when the
authorizing party gets
compromised and hackers
try to issue false certificates
causing transfer of data in
the wrong destination.
Recent research trends In symmetric key encryption
methods, researches are
going on to develop a new
symmetric encryption
system which is based on
evolution algorithm. The
research is based on
combining a ciphering
evolution system with a new
ciphering method known as
fragmentation. This research
trend will help in allowing to
alter the appearance of
characters from a given text.
Most of the financial
transactions are safeguarded
using the public key
encryption method but
unfortunately, the public key
encryption scheme is tough
to devise against CCAs.
Current researches are going
on to develop a anew
technique for these error
prone CCA schemes and
turning them into a secured
CCA schemes.
Examples Examples of symmetric key
encryption includes-
Blowfish, RC4, RC5, AES
The most common example
of public key encryption is
RSA
Symmetric key encryption
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
6INFORMATION TECHNOLOGY SECURITY
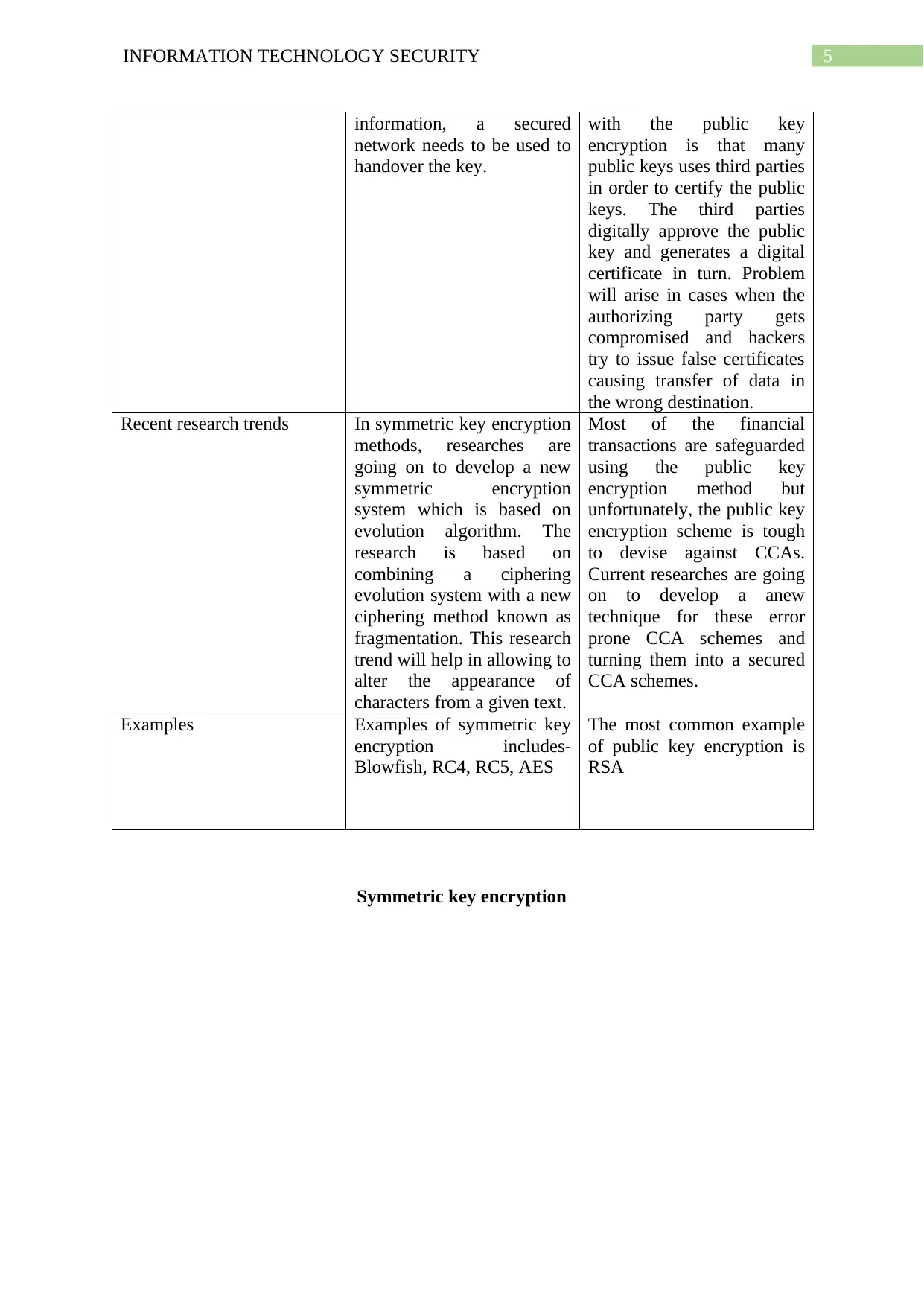
Public key encryption
Topic 3: Network Security Fundamentals
Network safety is defined as the action to defend the honesty and usability of the data and its
system. Securing network involves both hardware and software skills which helps in handling
the access to the system without authorization. Network access control is one of the
approaches of network security that helps in unifying the endpoints of a security technology.
Public key encryption
Topic 3: Network Security Fundamentals
Network safety is defined as the action to defend the honesty and usability of the data and its
system. Securing network involves both hardware and software skills which helps in handling
the access to the system without authorization. Network access control is one of the
approaches of network security that helps in unifying the endpoints of a security technology.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7INFORMATION TECHNOLOGY SECURITY
There are two types of network access control, one is the Mandatory Access Control and the
other is the Discretionary Access Control.
Mandatory Access Control:
Description: Mandatory Access Control is referred to the type of admission control in which
the functioning system compels the capability of an originator in accessing the general
operations of a target (Bacis et al., 2015).
Strengths: In this type of access control, strength lies in the fact that only those subject’s
accesses are allowed where the subject’s clearance is equal or greater than the label of the
object. Another strength of MAC is that the system helps in determining the access policy for
preserving the confidentiality of the data.
Weakness: The major weakness of the Mandatory Access Control policy is that it lacks
flexibility and it is somewhat difficult to implement the access control in systems as it
involves complex programming.
Application: Mandatary Access Control has its application in the SUSE Linux where the
type of access control is named as App Armor. It utilizes a Linux kernel feature called as the
LSM which provides a kernel API to allow module of codes to govern the ACL (Paraboschi,
Bacis & Mutti, 2015). Except this the MAC is also applied in FreeBSD to support the access
control as a part of the Trusted BSD project.
There are two types of network access control, one is the Mandatory Access Control and the
other is the Discretionary Access Control.
Mandatory Access Control:
Description: Mandatory Access Control is referred to the type of admission control in which
the functioning system compels the capability of an originator in accessing the general
operations of a target (Bacis et al., 2015).
Strengths: In this type of access control, strength lies in the fact that only those subject’s
accesses are allowed where the subject’s clearance is equal or greater than the label of the
object. Another strength of MAC is that the system helps in determining the access policy for
preserving the confidentiality of the data.
Weakness: The major weakness of the Mandatory Access Control policy is that it lacks
flexibility and it is somewhat difficult to implement the access control in systems as it
involves complex programming.
Application: Mandatary Access Control has its application in the SUSE Linux where the
type of access control is named as App Armor. It utilizes a Linux kernel feature called as the
LSM which provides a kernel API to allow module of codes to govern the ACL (Paraboschi,
Bacis & Mutti, 2015). Except this the MAC is also applied in FreeBSD to support the access
control as a part of the Trusted BSD project.
8INFORMATION TECHNOLOGY SECURITY
Discretionary Access Control:
Description: In this type of access control, the subject is given the full control over the
objects for accessing them as well as sharing the object with other subjects (Sandhu, 2015).
Here the subjects are given the flexibility to control and empower their own data.
Strengths: The strengths of Discretionary Access Control include that the users can transfer
the objects to other users, users can determine the access type of the other user, after
attempting several accesses the authorization fails and restricts the user from performing any
such access further.
Weakness: Though the Discretionary Access Control is easy to implement but still it has
some major weaknesses such as-
1. This type of access control inherits vulnerabilities such as Trojan Horse Attack
2. It includes the ACL maintenance
Discretionary Access Control:
Description: In this type of access control, the subject is given the full control over the
objects for accessing them as well as sharing the object with other subjects (Sandhu, 2015).
Here the subjects are given the flexibility to control and empower their own data.
Strengths: The strengths of Discretionary Access Control include that the users can transfer
the objects to other users, users can determine the access type of the other user, after
attempting several accesses the authorization fails and restricts the user from performing any
such access further.
Weakness: Though the Discretionary Access Control is easy to implement but still it has
some major weaknesses such as-
1. This type of access control inherits vulnerabilities such as Trojan Horse Attack
2. It includes the ACL maintenance
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

9INFORMATION TECHNOLOGY SECURITY
3. It grants and revokes the permissions of maintenance
4. It has limited negative power of authorization.
Application: Discretionary access control is widely used in the field of database management
systems where it helps in the capability to access specific data records in a specified mode
including reading, writing, deleting and updating of data (Barka, Mathew & Atif, 2015). A
user who wants to create a database is given the privilege to get access to the objects created
in other tables and thus helps in flexible use of databases.
3. It grants and revokes the permissions of maintenance
4. It has limited negative power of authorization.
Application: Discretionary access control is widely used in the field of database management
systems where it helps in the capability to access specific data records in a specified mode
including reading, writing, deleting and updating of data (Barka, Mathew & Atif, 2015). A
user who wants to create a database is given the privilege to get access to the objects created
in other tables and thus helps in flexible use of databases.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
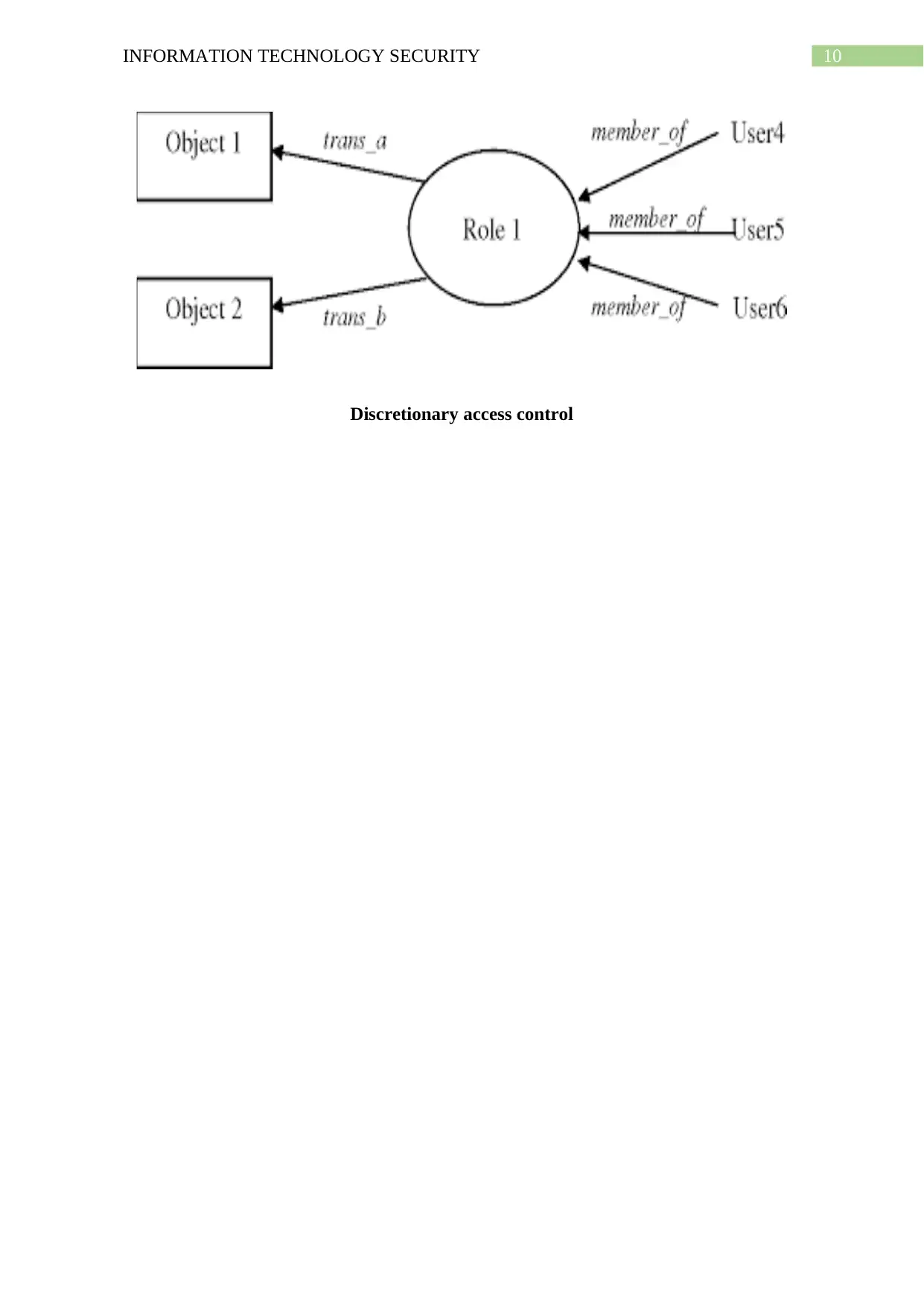
10INFORMATION TECHNOLOGY SECURITY
Discretionary access control
Discretionary access control

11INFORMATION TECHNOLOGY SECURITY
References:
Bacis, E., Mutti, S., Capelli, S., & Paraboschi, S. (2015, September). DockerPolicyModules:
mandatory access control for docker containers. In 2015 IEEE Conference on
Communications and Network Security (CNS) (pp. 749-750). IEEE.
Barka, E., Mathew, S. S., & Atif, Y. (2015, May). Securing the web of things with role-based
access control. In International Conference on Codes, Cryptology, and Information
Security(pp. 14-26). Springer, Cham.
Hofheinz, D., & Jager, T. (2016). Tightly secure signatures and public-key
encryption. Designs, Codes and Cryptography, 80(1), 29-61.
Hruza, P., Sousek, R., & Szabo, S. (2014). Cyber-attacks and attack protection.
Kansal, S., & Mittal, M. (2014, December). Performance evaluation of various symmetric
encryption algorithms. In 2014 International Conference on Parallel, Distributed and
Grid Computing (pp. 105-109). IEEE.
Katz, J., & Lindell, Y. (2014). Introduction to modern cryptography. CRC press.
Korstanje, M. E. (Ed.). (2016). Threat mitigation and detection of cyber warfare and
terrorism activities. IGI Global.
Ma, S., Huang, Q., Zhang, M., & Yang, B. (2015). Efficient public key encryption with
equality test supporting flexible authorization. IEEE Transactions on Information
Forensics and Security, 10(3), 458-470.
Naik, P. G., & Naik, G. R. (2014). Symmetric key encryption using genetic
algorithm. International Journal of Latest Trends in Engineering and Technology
(IJLTET), 3(3), 118-128.
References:
Bacis, E., Mutti, S., Capelli, S., & Paraboschi, S. (2015, September). DockerPolicyModules:
mandatory access control for docker containers. In 2015 IEEE Conference on
Communications and Network Security (CNS) (pp. 749-750). IEEE.
Barka, E., Mathew, S. S., & Atif, Y. (2015, May). Securing the web of things with role-based
access control. In International Conference on Codes, Cryptology, and Information
Security(pp. 14-26). Springer, Cham.
Hofheinz, D., & Jager, T. (2016). Tightly secure signatures and public-key
encryption. Designs, Codes and Cryptography, 80(1), 29-61.
Hruza, P., Sousek, R., & Szabo, S. (2014). Cyber-attacks and attack protection.
Kansal, S., & Mittal, M. (2014, December). Performance evaluation of various symmetric
encryption algorithms. In 2014 International Conference on Parallel, Distributed and
Grid Computing (pp. 105-109). IEEE.
Katz, J., & Lindell, Y. (2014). Introduction to modern cryptography. CRC press.
Korstanje, M. E. (Ed.). (2016). Threat mitigation and detection of cyber warfare and
terrorism activities. IGI Global.
Ma, S., Huang, Q., Zhang, M., & Yang, B. (2015). Efficient public key encryption with
equality test supporting flexible authorization. IEEE Transactions on Information
Forensics and Security, 10(3), 458-470.
Naik, P. G., & Naik, G. R. (2014). Symmetric key encryption using genetic
algorithm. International Journal of Latest Trends in Engineering and Technology
(IJLTET), 3(3), 118-128.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 13
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





