Information Security Risk Management Report: BHP Billiton Case Study
VerifiedAdded on 2020/05/08
|17
|3872
|130
Report
AI Summary
This report provides a comprehensive analysis of information security risk management, focusing on the case of BHP Billiton. It begins with an investigation of tools and techniques for risk identification, including Delphi techniques, root cause analysis, and various diagramming methods. The report then delves into risk assessment, outlining a risk assessment matrix and a risk severity matrix, and proposes a Disaster Recovery (DR) plan. Furthermore, it suggests a Business Continuity Plan (BCP) and analyzes various control measures. The report also includes a logical map of the organizational structure. The report covers a range of security threats and risks, including natural disasters, network failures, malicious coding, identity theft, and cyberattacks, along with proposed mitigation strategies. The report emphasizes the importance of regular audits and the continuous monitoring of risk management plans to ensure their effectiveness.

Running head: INFORMATION SECURITY RISK MANAGEMENT
Information Security Risk Management
Name of the Student
Name of the University
Author Note
Information Security Risk Management
Name of the Student
Name of the University
Author Note
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1
INFORMATION SECURITY RISK MANAGEMENT
Executive summary
The report has evaluated an investigation on the tools and techniques. Then it has designed the
risk analysis matrix and a DR plan. Then it has proposed a BCP and the controls are analyzed in
the report. Lastly, a logical map regarding the organizational structure is discussed in the report.
INFORMATION SECURITY RISK MANAGEMENT
Executive summary
The report has evaluated an investigation on the tools and techniques. Then it has designed the
risk analysis matrix and a DR plan. Then it has proposed a BCP and the controls are analyzed in
the report. Lastly, a logical map regarding the organizational structure is discussed in the report.

2
INFORMATION SECURITY RISK MANAGEMENT
Table of Contents
Introduction:....................................................................................................................................3
1. The investigation:........................................................................................................................3
2. The Risk Management:................................................................................................................5
2.1. Risk assessment:...................................................................................................................5
2.2. Risk Severity Matrix:............................................................................................................7
3. Designing of the DR plan:...........................................................................................................8
4. Proposal for the BCP:..................................................................................................................8
5. Analysis and report on controls:................................................................................................10
6. Logical map of organizational structure:...................................................................................11
Conclusion:....................................................................................................................................12
References:....................................................................................................................................13
INFORMATION SECURITY RISK MANAGEMENT
Table of Contents
Introduction:....................................................................................................................................3
1. The investigation:........................................................................................................................3
2. The Risk Management:................................................................................................................5
2.1. Risk assessment:...................................................................................................................5
2.2. Risk Severity Matrix:............................................................................................................7
3. Designing of the DR plan:...........................................................................................................8
4. Proposal for the BCP:..................................................................................................................8
5. Analysis and report on controls:................................................................................................10
6. Logical map of organizational structure:...................................................................................11
Conclusion:....................................................................................................................................12
References:....................................................................................................................................13
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3
INFORMATION SECURITY RISK MANAGEMENT
Introduction:
There have been always associated with the information systems. The implications of the
risks are happening at the wider context of business. For this BHP Billiton, at Australia is
chosen. It is a multinational mining, metals and petroleum dual-listed public organization. The
various kinds of risks of the company are needed to be identified. A clear understanding is
needed for the organizations to manage the risks.
The following report makes an investigation on the tools and techniques, designed the
risk analysis matrix and a DR plan. Then BCP is proposed and the controls are analyzed. Lastly,
a logical map of the organizational structure is demonstrated.
1. The investigation:
There must be some established techniques and tools for every stage.
The first one is the risk resister. This helps in tracking the risks all through the project
life-cycle. Its activity is same as that of the snap-shot regarding the occurrences in the project
risks. They are the Excel spreadsheets.
The next one is the risk identification. For identifying, the risks at BHP Billiton
successfully the every possible method are to be thought of eventually. However, there have
been few things that are unknown. Here some of tools and techniques are useful to identify the
hidden risks (Ivan et al., 2012). The first one is the Delphi techniques where the experts of the
panels are been asked various queries, here the unbiased data are retrieved about what the experts
have been agreeing to. Next, the root cause analysis fetches the problems to seek whether the
INFORMATION SECURITY RISK MANAGEMENT
Introduction:
There have been always associated with the information systems. The implications of the
risks are happening at the wider context of business. For this BHP Billiton, at Australia is
chosen. It is a multinational mining, metals and petroleum dual-listed public organization. The
various kinds of risks of the company are needed to be identified. A clear understanding is
needed for the organizations to manage the risks.
The following report makes an investigation on the tools and techniques, designed the
risk analysis matrix and a DR plan. Then BCP is proposed and the controls are analyzed. Lastly,
a logical map of the organizational structure is demonstrated.
1. The investigation:
There must be some established techniques and tools for every stage.
The first one is the risk resister. This helps in tracking the risks all through the project
life-cycle. Its activity is same as that of the snap-shot regarding the occurrences in the project
risks. They are the Excel spreadsheets.
The next one is the risk identification. For identifying, the risks at BHP Billiton
successfully the every possible method are to be thought of eventually. However, there have
been few things that are unknown. Here some of tools and techniques are useful to identify the
hidden risks (Ivan et al., 2012). The first one is the Delphi techniques where the experts of the
panels are been asked various queries, here the unbiased data are retrieved about what the experts
have been agreeing to. Next, the root cause analysis fetches the problems to seek whether the
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

4
INFORMATION SECURITY RISK MANAGEMENT
complete effects could be prevented. Then there are the diagramming techniques that are referred
to as the compact versions of the risks. This includes the cause and effect diagrams, influence
diagrams and flow charts. Lastly, there is the benchmarking to compare between the departments
or periods. The anomalies in the data of benchmarking could spot the risks that could be missed
as the analysis is done in the isolation.
The tools and techniques could be utilized for analyzing the effect of risk on the BHP
Billiton as the quantitative risk analysis. There are basically more complicated than the
qualitative ones. One of the popular risks analysis has been including the FMEA or the “Failure
Modes and Effect Analysis” determining how and where the process could fail. The activities are
taken to identify the address the sections of the processes where the failure is likely (Feng, Wang
& Li, 2014). Then there is the sensitivity analysis where various variables are introduced to
display the effect on the risks. The analysis highlights what might happen as the predictions fail
to materialize. The last one is the decision tree. It is a diagram consisting of braches showing the
results of various decisions and the random events. The decision trees must be coupled with the
monetary value technique expected to display the economic effects of various results.
Then there is the qualitative risk analysis helping to decide what risks are to be focused
on. One of example of this is the RAG or the red, amber and green status where the risks are
categorized into three groups. The criteria for every group relied on the impact of quality and
time and the likelihood of the happenings. Then the risk categorization deals with the more
effective managing of the risks. The categorizing of risks through various categories like the root
cause allow for the risk management approach coordinately ("Does risk matter? Disengagement
from risk management in information systems projects", 2017). The risk urgency analysis could
INFORMATION SECURITY RISK MANAGEMENT
complete effects could be prevented. Then there are the diagramming techniques that are referred
to as the compact versions of the risks. This includes the cause and effect diagrams, influence
diagrams and flow charts. Lastly, there is the benchmarking to compare between the departments
or periods. The anomalies in the data of benchmarking could spot the risks that could be missed
as the analysis is done in the isolation.
The tools and techniques could be utilized for analyzing the effect of risk on the BHP
Billiton as the quantitative risk analysis. There are basically more complicated than the
qualitative ones. One of the popular risks analysis has been including the FMEA or the “Failure
Modes and Effect Analysis” determining how and where the process could fail. The activities are
taken to identify the address the sections of the processes where the failure is likely (Feng, Wang
& Li, 2014). Then there is the sensitivity analysis where various variables are introduced to
display the effect on the risks. The analysis highlights what might happen as the predictions fail
to materialize. The last one is the decision tree. It is a diagram consisting of braches showing the
results of various decisions and the random events. The decision trees must be coupled with the
monetary value technique expected to display the economic effects of various results.
Then there is the qualitative risk analysis helping to decide what risks are to be focused
on. One of example of this is the RAG or the red, amber and green status where the risks are
categorized into three groups. The criteria for every group relied on the impact of quality and
time and the likelihood of the happenings. Then the risk categorization deals with the more
effective managing of the risks. The categorizing of risks through various categories like the root
cause allow for the risk management approach coordinately ("Does risk matter? Disengagement
from risk management in information systems projects", 2017). The risk urgency analysis could

5
INFORMATION SECURITY RISK MANAGEMENT
be utilized for narrowing down the risks recognized in the status of RAG. This focuses over the
timing elements of the risks. Here the priorities are given to the risks that are imminent.
As the quantitative and the qualitative analysis are done, the proper responses to address
the risks are done. Firstly, the avoidance could be done through the removal where the case
around the risk is changed. Then the mitigation is done to lessen the impact or chance of risk.
Then there is the transference or the shift of risks and the effect on the third party. Lastly, there is
the acceptance, the contingency plan for dealing with the effects.
The risk monitoring helps in keeping the eye over the plan. It includes the status meetings
for reporting on the development of the risk management at BHP Billiton. The frequent status
meetings ensure the risks that are to the forefront of the mind of the individuals. Then there are
the risk audits for evaluating how effectively the reactions to the risks have been. This could be
utilized to analyze the risk management process ("Information security: Anish Bhimani at
TEDxUConn 2013", 2017). The findings, objectives and format of the risk audit require to be
documented clearly to develop the process of risk management.
The techniques and tools that have not been used effectively never helps in risk
management. This might need some time to seek which one could suit the business. However,
there have plenty to go for such that one moves to next, as any specific technique or tools not
work out.
INFORMATION SECURITY RISK MANAGEMENT
be utilized for narrowing down the risks recognized in the status of RAG. This focuses over the
timing elements of the risks. Here the priorities are given to the risks that are imminent.
As the quantitative and the qualitative analysis are done, the proper responses to address
the risks are done. Firstly, the avoidance could be done through the removal where the case
around the risk is changed. Then the mitigation is done to lessen the impact or chance of risk.
Then there is the transference or the shift of risks and the effect on the third party. Lastly, there is
the acceptance, the contingency plan for dealing with the effects.
The risk monitoring helps in keeping the eye over the plan. It includes the status meetings
for reporting on the development of the risk management at BHP Billiton. The frequent status
meetings ensure the risks that are to the forefront of the mind of the individuals. Then there are
the risk audits for evaluating how effectively the reactions to the risks have been. This could be
utilized to analyze the risk management process ("Information security: Anish Bhimani at
TEDxUConn 2013", 2017). The findings, objectives and format of the risk audit require to be
documented clearly to develop the process of risk management.
The techniques and tools that have not been used effectively never helps in risk
management. This might need some time to seek which one could suit the business. However,
there have plenty to go for such that one moves to next, as any specific technique or tools not
work out.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
6
INFORMATION SECURITY RISK MANAGEMENT
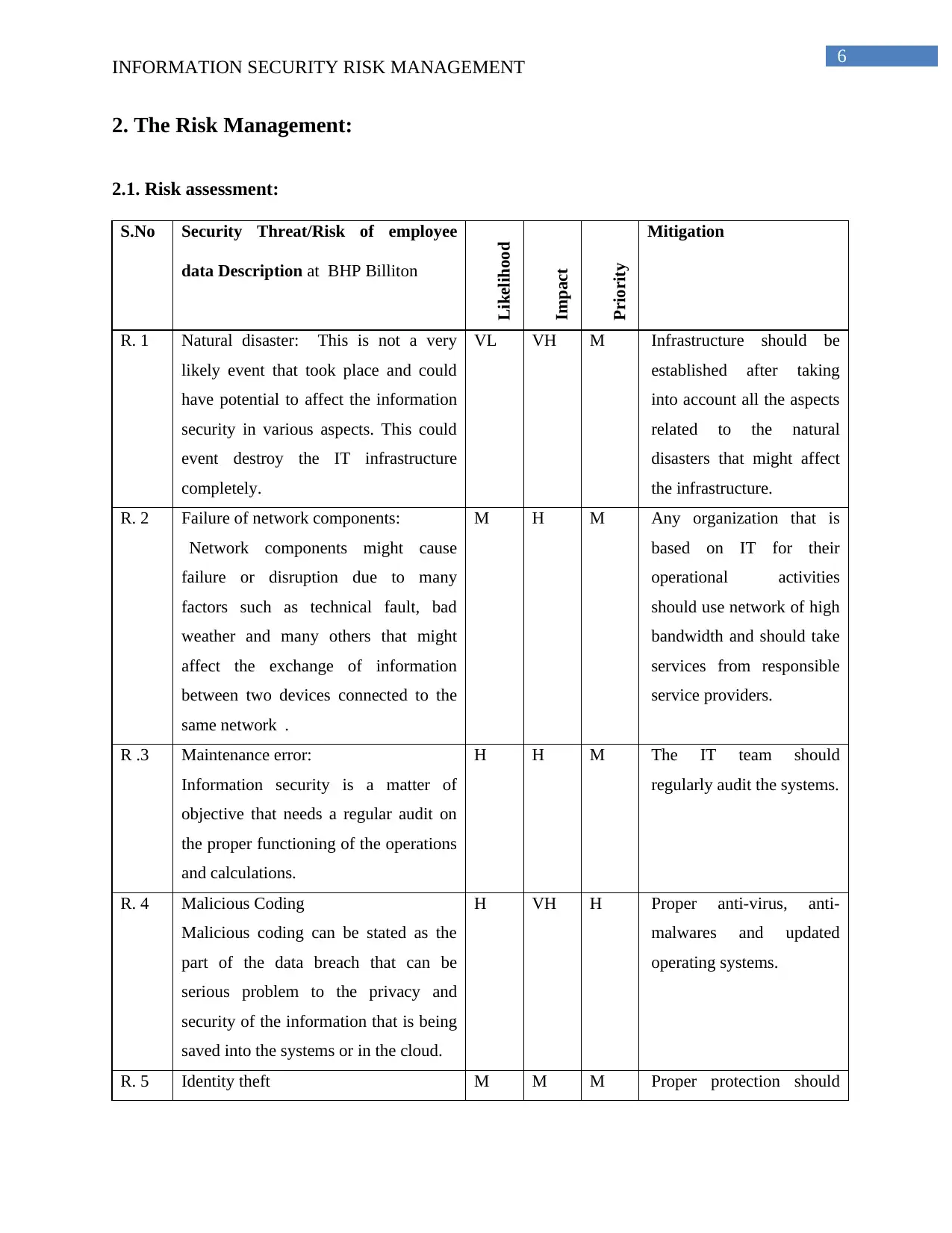
2. The Risk Management:
2.1. Risk assessment:
S.No Security Threat/Risk of employee
data Description at BHP Billiton
Likelihood
Impact
Priority
Mitigation
R. 1 Natural disaster: This is not a very
likely event that took place and could
have potential to affect the information
security in various aspects. This could
event destroy the IT infrastructure
completely.
VL VH M Infrastructure should be
established after taking
into account all the aspects
related to the natural
disasters that might affect
the infrastructure.
R. 2 Failure of network components:
“Network components might cause
failure or disruption due to many
factors such as technical fault, bad
weather and many others that might
affect the exchange of information
between two devices connected to the
same network”.
M H M Any organization that is
based on IT for their
operational activities
should use network of high
bandwidth and should take
services from responsible
service providers.
R .3 Maintenance error:
Information security is a matter of
objective that needs a regular audit on
the proper functioning of the operations
and calculations.
H H M The IT team should
regularly audit the systems.
R. 4 Malicious Coding
Malicious coding can be stated as the
part of the data breach that can be
serious problem to the privacy and
security of the information that is being
saved into the systems or in the cloud.
H VH H Proper anti-virus, anti-
malwares and updated
operating systems.
R. 5 Identity theft M M M Proper protection should
INFORMATION SECURITY RISK MANAGEMENT
2. The Risk Management:
2.1. Risk assessment:
S.No Security Threat/Risk of employee
data Description at BHP Billiton
Likelihood
Impact
Priority
Mitigation
R. 1 Natural disaster: This is not a very
likely event that took place and could
have potential to affect the information
security in various aspects. This could
event destroy the IT infrastructure
completely.
VL VH M Infrastructure should be
established after taking
into account all the aspects
related to the natural
disasters that might affect
the infrastructure.
R. 2 Failure of network components:
“Network components might cause
failure or disruption due to many
factors such as technical fault, bad
weather and many others that might
affect the exchange of information
between two devices connected to the
same network”.
M H M Any organization that is
based on IT for their
operational activities
should use network of high
bandwidth and should take
services from responsible
service providers.
R .3 Maintenance error:
Information security is a matter of
objective that needs a regular audit on
the proper functioning of the operations
and calculations.
H H M The IT team should
regularly audit the systems.
R. 4 Malicious Coding
Malicious coding can be stated as the
part of the data breach that can be
serious problem to the privacy and
security of the information that is being
saved into the systems or in the cloud.
H VH H Proper anti-virus, anti-
malwares and updated
operating systems.
R. 5 Identity theft M M M Proper protection should
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
7
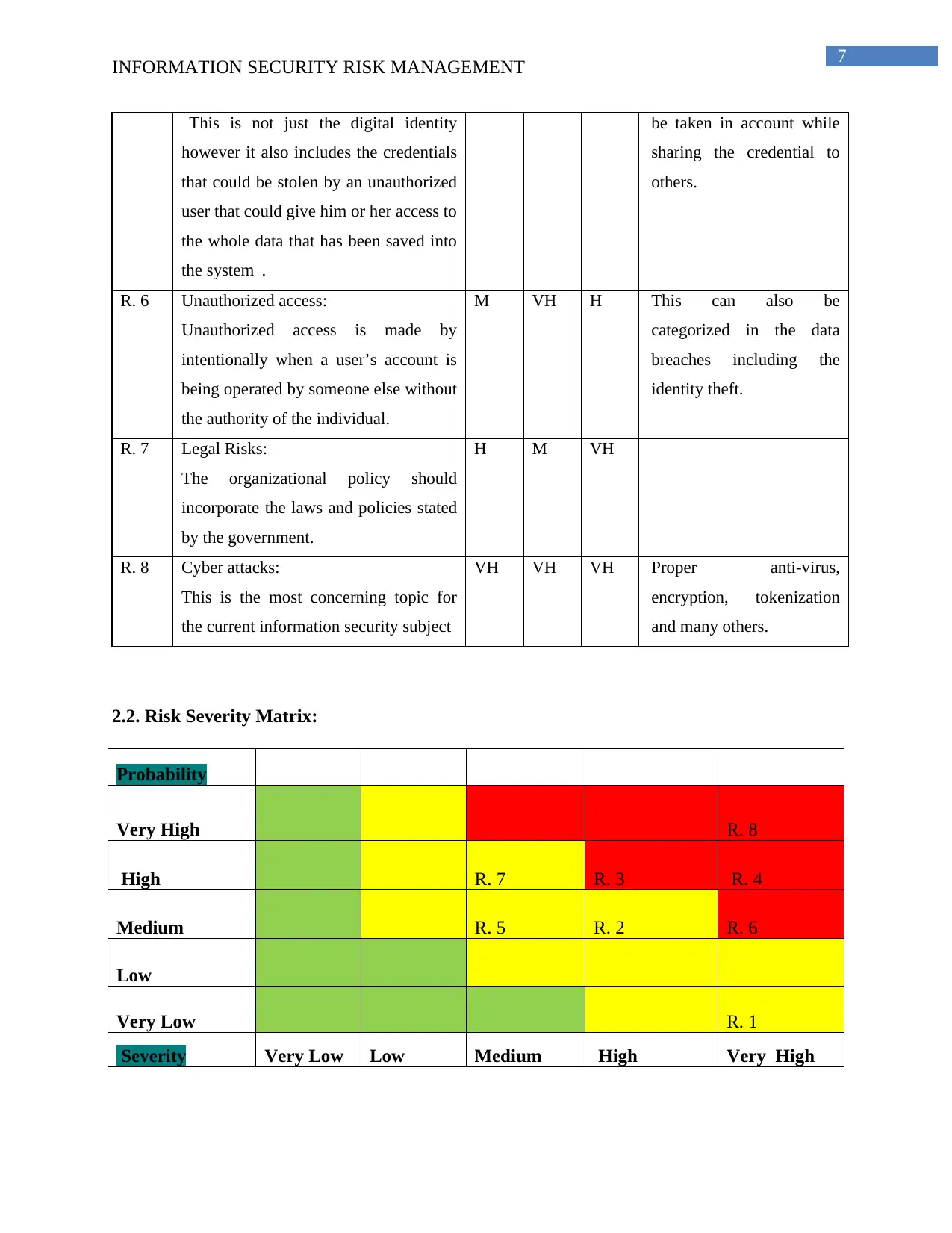
INFORMATION SECURITY RISK MANAGEMENT
“This is not just the digital identity
however it also includes the credentials
that could be stolen by an unauthorized
user that could give him or her access to
the whole data that has been saved into
the system”.
be taken in account while
sharing the credential to
others.
R. 6 Unauthorized access:
Unauthorized access is made by
intentionally when a user’s account is
being operated by someone else without
the authority of the individual.
M VH H This can also be
categorized in the data
breaches including the
identity theft.
R. 7 Legal Risks:
The organizational policy should
incorporate the laws and policies stated
by the government.
H M VH
R. 8 Cyber attacks:
This is the most concerning topic for
the current information security subject
VH VH VH Proper anti-virus,
encryption, tokenization
and many others.
2.2. Risk Severity Matrix:
Probability
Very High R. 8
High R. 7 R. 3 R. 4
Medium R. 5 R. 2 R. 6
Low
Very Low R. 1
Severity Very Low Low Medium High Very High
INFORMATION SECURITY RISK MANAGEMENT
“This is not just the digital identity
however it also includes the credentials
that could be stolen by an unauthorized
user that could give him or her access to
the whole data that has been saved into
the system”.
be taken in account while
sharing the credential to
others.
R. 6 Unauthorized access:
Unauthorized access is made by
intentionally when a user’s account is
being operated by someone else without
the authority of the individual.
M VH H This can also be
categorized in the data
breaches including the
identity theft.
R. 7 Legal Risks:
The organizational policy should
incorporate the laws and policies stated
by the government.
H M VH
R. 8 Cyber attacks:
This is the most concerning topic for
the current information security subject
VH VH VH Proper anti-virus,
encryption, tokenization
and many others.
2.2. Risk Severity Matrix:
Probability
Very High R. 8
High R. 7 R. 3 R. 4
Medium R. 5 R. 2 R. 6
Low
Very Low R. 1
Severity Very Low Low Medium High Very High

8
INFORMATION SECURITY RISK MANAGEMENT
INFORMATION SECURITY RISK MANAGEMENT
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

9
INFORMATION SECURITY RISK MANAGEMENT
3. Designing of the DR plan:
All kinds of business requires the risk management plan like buying of the liability
insurance or need full-time managers employed to execute that. The contingency plan determines
the risks as the business faces of BHP Billiton and the steps to taken as the risks are identified.
Most of the business could determine that they are most likely meet and cost them the most as
they come passed by (Spears & Barki, 2010). For designing the DR plan, the most vital business
activities are needed to be determined along with the applications or data required to support
them. Firstly, the critical business processes are to be identified. Then the dependencies are
labeled involving the outlining the applications on which the business process has been
depending.
The vital applications are to be defined making the list of the applications including the
most important restoration time. Then the present strategy of data recovery is needed to be
assessed. After that, enough information is to be gathered for determining the requirements of the
recovery time (Tams & Hill, 2015). Next, a business impact analysis or BIA is to be performed
for BHP Billiton. Next, the RPO or Recovery Point objectives are to be defined and the RTQ or
the recovery time objectives are to be distinguished. Then the MTD or the minimum tolerable
downtime is to be designated. Then the risks are to be assessed, theories are tested, accordingly
redesigned and new solutions are implemented. Lastly, the Emergency Response Procedure is to
be developed, align procedures and ultimately a team is formed.
INFORMATION SECURITY RISK MANAGEMENT
3. Designing of the DR plan:
All kinds of business requires the risk management plan like buying of the liability
insurance or need full-time managers employed to execute that. The contingency plan determines
the risks as the business faces of BHP Billiton and the steps to taken as the risks are identified.
Most of the business could determine that they are most likely meet and cost them the most as
they come passed by (Spears & Barki, 2010). For designing the DR plan, the most vital business
activities are needed to be determined along with the applications or data required to support
them. Firstly, the critical business processes are to be identified. Then the dependencies are
labeled involving the outlining the applications on which the business process has been
depending.
The vital applications are to be defined making the list of the applications including the
most important restoration time. Then the present strategy of data recovery is needed to be
assessed. After that, enough information is to be gathered for determining the requirements of the
recovery time (Tams & Hill, 2015). Next, a business impact analysis or BIA is to be performed
for BHP Billiton. Next, the RPO or Recovery Point objectives are to be defined and the RTQ or
the recovery time objectives are to be distinguished. Then the MTD or the minimum tolerable
downtime is to be designated. Then the risks are to be assessed, theories are tested, accordingly
redesigned and new solutions are implemented. Lastly, the Emergency Response Procedure is to
be developed, align procedures and ultimately a team is formed.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

10
INFORMATION SECURITY RISK MANAGEMENT
4. Proposal for the BCP:
As the business, makes decision to mitigate or adopt the risk, this turns to be beneficial
from having the contingency plan for dealing with the case that could happen. It could range
from the plan of fire evacuation to appoint the emergency coordinator for helping the media
contacts or evacuations (Cong & Romero, 2013). The risk managers of BHP Billiton are able to
create the in-depth plan for dealing with the most likely cases the organization must face or the
ones doing the most damages. Then they must interact with the plans to every required personnel
at work and schedule the drills possibly, providing the training or purchasing the equipment.
Regarding the evaluation of the plan, the business at BHP Billiton enquires to review the
plans occasionally making sure that they have been updated. Further they must also examine the
plans after any emergency takes plan for ensuring that the plan must work in the way as it was
been expected to be and to make any adjustments needed (Ivan et al., 2012).
The plans of the project risk have been balancing the investment to eradicate against the
advantages of the project. The team often creates the alternative approach to accomplish the
project aims as any risk event is determined frustrating the accomplishing the project goals.
These are known s the contingency plans using the train for transporting the necessary equipment
for the project (Agrawal, Campoe & Pierce, 2014). As any critical piece of equipment has been
late, the effect on the schedule could be mitigated through making changes for the schedule for
accommodating the delivery of late equipment.
The contingency funds are the funds that are set beside through the project team for
addressing the unforeseen events causing the expenses of the projects to rise. The projects with
the profiles of high-risks would typically have the huge contingency budgets (Ko & Choo, 2015).
INFORMATION SECURITY RISK MANAGEMENT
4. Proposal for the BCP:
As the business, makes decision to mitigate or adopt the risk, this turns to be beneficial
from having the contingency plan for dealing with the case that could happen. It could range
from the plan of fire evacuation to appoint the emergency coordinator for helping the media
contacts or evacuations (Cong & Romero, 2013). The risk managers of BHP Billiton are able to
create the in-depth plan for dealing with the most likely cases the organization must face or the
ones doing the most damages. Then they must interact with the plans to every required personnel
at work and schedule the drills possibly, providing the training or purchasing the equipment.
Regarding the evaluation of the plan, the business at BHP Billiton enquires to review the
plans occasionally making sure that they have been updated. Further they must also examine the
plans after any emergency takes plan for ensuring that the plan must work in the way as it was
been expected to be and to make any adjustments needed (Ivan et al., 2012).
The plans of the project risk have been balancing the investment to eradicate against the
advantages of the project. The team often creates the alternative approach to accomplish the
project aims as any risk event is determined frustrating the accomplishing the project goals.
These are known s the contingency plans using the train for transporting the necessary equipment
for the project (Agrawal, Campoe & Pierce, 2014). As any critical piece of equipment has been
late, the effect on the schedule could be mitigated through making changes for the schedule for
accommodating the delivery of late equipment.
The contingency funds are the funds that are set beside through the project team for
addressing the unforeseen events causing the expenses of the projects to rise. The projects with
the profiles of high-risks would typically have the huge contingency budgets (Ko & Choo, 2015).

11
INFORMATION SECURITY RISK MANAGEMENT
Though the quantity of the contingency allocated in the budget has been the functions of the risks
determined in the process of risk analysis, the contingency is managed typically as a single item
in the budget of the project.
Again, some project managers have been allocating the budget of contingency to the
items within the budget having large risks. This has been instead of developing one line item
within the budget regarding the contingencies. The approach has been allowing the project team
in tracking the usage of the contingency against the risk plans. The approach also allocates the
roles for managing the budget of the risks to the managers who have been responsible for the line
items (Ivan et al., 2012). Moreover, the availability of those contingency funds within the budget
of line item might also rise the usage of the contingency funds for solving the issues instead of
finding the less costly or alterative solutions. Maximum of the project managers has been
managing those contingency plans, particularly on the more complicated projects. This is done
with the approval of the manager needed before the contingency funds could be utilized.
5. Analysis and report on controls:
The face-to-face interaction and the project team participation have been required to
encourage the open communication and trust. These are needed for effective risk identification.
While the smaller and the specialized groups are able to perform the risk assessment and the
effective current risk identification at BHP Billiton needs input from the complete project team
and from the others outside that (Ivan et al., 2012). While the smaller and the specialized groups
could perform the risk analysis and risk assessment, the risk recognition needs input from the
complete project team and external to that. The risk recognition has been due to the reason of
early the activation of the IPT has been vital to the project success. The process of risk
INFORMATION SECURITY RISK MANAGEMENT
Though the quantity of the contingency allocated in the budget has been the functions of the risks
determined in the process of risk analysis, the contingency is managed typically as a single item
in the budget of the project.
Again, some project managers have been allocating the budget of contingency to the
items within the budget having large risks. This has been instead of developing one line item
within the budget regarding the contingencies. The approach has been allowing the project team
in tracking the usage of the contingency against the risk plans. The approach also allocates the
roles for managing the budget of the risks to the managers who have been responsible for the line
items (Ivan et al., 2012). Moreover, the availability of those contingency funds within the budget
of line item might also rise the usage of the contingency funds for solving the issues instead of
finding the less costly or alterative solutions. Maximum of the project managers has been
managing those contingency plans, particularly on the more complicated projects. This is done
with the approval of the manager needed before the contingency funds could be utilized.
5. Analysis and report on controls:
The face-to-face interaction and the project team participation have been required to
encourage the open communication and trust. These are needed for effective risk identification.
While the smaller and the specialized groups are able to perform the risk assessment and the
effective current risk identification at BHP Billiton needs input from the complete project team
and from the others outside that (Ivan et al., 2012). While the smaller and the specialized groups
could perform the risk analysis and risk assessment, the risk recognition needs input from the
complete project team and external to that. The risk recognition has been due to the reason of
early the activation of the IPT has been vital to the project success. The process of risk
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 17
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





