Security Management and Risk Assessment Report: Infosys Analysis
VerifiedAdded on 2022/10/03
|11
|1927
|459
Report
AI Summary
This report provides a comprehensive analysis of security management, focusing on a case study of Infosys. It begins with an overview of system access security policies, highlighting the importance of strict guidelines and technologies like biometrics and cloud access control. The report then delves into a risk assessment of Infosys, examining its IT systems, potential risks in IT components (such as hardware and software failures, malware, viruses, and human error), and the consequences of these risks. It details a risk register, including risk descriptions, impact, likelihood, mitigation plans, and contingency plans. Furthermore, the report explores risk management tools and techniques, specifically the probability matrix, to identify and address critical risks. The conclusion emphasizes the significance of risk management in IT services, the application of models like PPRR, and the importance of staff training and preventative measures to reduce system vulnerabilities. The report references several sources to support its findings.

Running head: MANAGEMENT OF SECURITY
Management of Security
Name of the student
Name of the University
Author note:
Management of Security
Name of the student
Name of the University
Author note:
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1MANAGEMENT OF SECURITY
Table of Contents
Part One: System Access Security Policy.......................................................................................2
Part two: Risk Assessment: Infosys.................................................................................................3
Introduction of the organization:.................................................................................................3
IT systems of the organization:....................................................................................................3
Risk in IT system components.....................................................................................................3
Consequences of the risk:............................................................................................................4
Mitigate risk:................................................................................................................................5
Risk Register:...............................................................................................................................6
Risk management tools and techniques.......................................................................................7
Conclusion...................................................................................................................................8
References........................................................................................................................................9
Table of Contents
Part One: System Access Security Policy.......................................................................................2
Part two: Risk Assessment: Infosys.................................................................................................3
Introduction of the organization:.................................................................................................3
IT systems of the organization:....................................................................................................3
Risk in IT system components.....................................................................................................3
Consequences of the risk:............................................................................................................4
Mitigate risk:................................................................................................................................5
Risk Register:...............................................................................................................................6
Risk management tools and techniques.......................................................................................7
Conclusion...................................................................................................................................8
References........................................................................................................................................9

2MANAGEMENT OF SECURITY
Part One: System Access Security Policy
There are many complexities which may arise while providing health care facilities and
services to individuals and it is the task of the professionals in the department of risk
management to consider this issue seriously. However, some policies can be introduced to
migrate issues like license standards, third party requirements and regulations. The purpose of
the policies are observation of authorized professional practices, maintenance of health
regulations, letting the new as well as the existing employees about the functionality of the
organization. Moreover documentation of the guidelines helps in reduction of the human error.
To secure a hospital’s IT services, implementation of strict policies and guidelines are important
(Ismail et al., 2018). Restricting access to the specific recognized entities is a great policy
towards securing the system.
Controlling the access with the help of Biometric is useful, as the record, “My Health
Record” can be accessed only by the authorized entities such as the doctors, nurses,
administrators and a few others. Cloud Access Control System (Quintuna, 2014)) is also one of
the way for protecting a huge amount of the data for the hospital management along with
keeping records. There is a separate access panel for the admin, who can access all the important
data when and where required. Wireless technologies are used in the modern cloud access
control systems which are handling friendly. The system can be accessed from smart phones and
tablets by the authorized user and the smartphones are provided with biometrics as well. Cloud
hospital security has easy installation process, adaptable and secured.
Part One: System Access Security Policy
There are many complexities which may arise while providing health care facilities and
services to individuals and it is the task of the professionals in the department of risk
management to consider this issue seriously. However, some policies can be introduced to
migrate issues like license standards, third party requirements and regulations. The purpose of
the policies are observation of authorized professional practices, maintenance of health
regulations, letting the new as well as the existing employees about the functionality of the
organization. Moreover documentation of the guidelines helps in reduction of the human error.
To secure a hospital’s IT services, implementation of strict policies and guidelines are important
(Ismail et al., 2018). Restricting access to the specific recognized entities is a great policy
towards securing the system.
Controlling the access with the help of Biometric is useful, as the record, “My Health
Record” can be accessed only by the authorized entities such as the doctors, nurses,
administrators and a few others. Cloud Access Control System (Quintuna, 2014)) is also one of
the way for protecting a huge amount of the data for the hospital management along with
keeping records. There is a separate access panel for the admin, who can access all the important
data when and where required. Wireless technologies are used in the modern cloud access
control systems which are handling friendly. The system can be accessed from smart phones and
tablets by the authorized user and the smartphones are provided with biometrics as well. Cloud
hospital security has easy installation process, adaptable and secured.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3MANAGEMENT OF SECURITY
Part two: Risk Assessment: Infosys
Introduction of the organization:
Infosys is a multinational corporation of India that provides IT services, outsourcing
services and business consulting having its headquarters in the city of Bangalore, Karnataka,
India. After the Tata Consultancy Services, Infosys is the second largest company in India. The
main products of the company are NIA or the Next Gen Integrated Artificial Intelligence
Platform; Infosys Consulting a service for management consulting; analytics platform known as
the Infosys Information Platform or IIP (Bhambhani, Sainy & Gupta, 2018). Infosys also
provides with Edge Verve system that include core banking product developed by the company
itself known as the Finacle and Panaya cloud suite.
IT systems of the organization:
The IT system of the organization consists of people, procedure, hardware, software and
data. An organization is run by the people and is run for the people. The hardware and the
software are the main requirement of the organizational functionality. Data is the asset of the
company that needs security and protection (Larson, Gray & Irwin, 2016).
Risk in IT system components:
If an organization relies completely on the IT systems and IT networks for running their
systems and other key activities, it is very important to stay aware of the nature and the range of
the awaiting risks on the system (Kliem & Ludin, 2019). There are a few general IT threats that
an organization running on the information technology services may have to face:
Failure of the hardware and software- power cuts, loss in energy, data loss or data
corruption may happen
Part two: Risk Assessment: Infosys
Introduction of the organization:
Infosys is a multinational corporation of India that provides IT services, outsourcing
services and business consulting having its headquarters in the city of Bangalore, Karnataka,
India. After the Tata Consultancy Services, Infosys is the second largest company in India. The
main products of the company are NIA or the Next Gen Integrated Artificial Intelligence
Platform; Infosys Consulting a service for management consulting; analytics platform known as
the Infosys Information Platform or IIP (Bhambhani, Sainy & Gupta, 2018). Infosys also
provides with Edge Verve system that include core banking product developed by the company
itself known as the Finacle and Panaya cloud suite.
IT systems of the organization:
The IT system of the organization consists of people, procedure, hardware, software and
data. An organization is run by the people and is run for the people. The hardware and the
software are the main requirement of the organizational functionality. Data is the asset of the
company that needs security and protection (Larson, Gray & Irwin, 2016).
Risk in IT system components:
If an organization relies completely on the IT systems and IT networks for running their
systems and other key activities, it is very important to stay aware of the nature and the range of
the awaiting risks on the system (Kliem & Ludin, 2019). There are a few general IT threats that
an organization running on the information technology services may have to face:
Failure of the hardware and software- power cuts, loss in energy, data loss or data
corruption may happen
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

4MANAGEMENT OF SECURITY
Malware- hackers are present now a days, hence malicious files are created to disrupt
various functionalities of a computer system
Viruses- there are certain codes in that can be put into the computer system which are
capable of self replication; these are malicious files and hinders the computer operations
Scam, spam and phishing- emails or messages that may look original but are not, they are
usually created for deceiving people. This can also be done by redirecting users into some
other page when a link is accessed.
Human error- disposing the data carelessly, using incorrect methodology for processing
the data or opening a virus or malware affected attachment accidentally can cause
disruption and corruption of the devices.
Consequences of the risk:
Once the risk is identified, it is essential to analyze them. The analysis of the level of the
risk helps in better understanding of the risk and how important it is to fix them. Level of risk is
calculated as the product of consequence and the likelihood (Niehaus, 2017). Consequence is the
rate at which the company is facing financial loss for that particular risk. It can be divided into
LOW, MEDIUM, HIGH, and VERY HIGH. It is customizable according to the requirement of
the business. The risk which can cause extreme loss in the finance of the company is placed
under VERY HIGH. So that they can be fixed at first. The risks which do not cause much loss
for the company can be placed under the LOW category. The risk which are causing financial
loss of the company at a lesser rate but does not affect the system too much and can be fixed
within a few months’ time, can be placed under MEDIUM category (Bahr, 2018).
Malware- hackers are present now a days, hence malicious files are created to disrupt
various functionalities of a computer system
Viruses- there are certain codes in that can be put into the computer system which are
capable of self replication; these are malicious files and hinders the computer operations
Scam, spam and phishing- emails or messages that may look original but are not, they are
usually created for deceiving people. This can also be done by redirecting users into some
other page when a link is accessed.
Human error- disposing the data carelessly, using incorrect methodology for processing
the data or opening a virus or malware affected attachment accidentally can cause
disruption and corruption of the devices.
Consequences of the risk:
Once the risk is identified, it is essential to analyze them. The analysis of the level of the
risk helps in better understanding of the risk and how important it is to fix them. Level of risk is
calculated as the product of consequence and the likelihood (Niehaus, 2017). Consequence is the
rate at which the company is facing financial loss for that particular risk. It can be divided into
LOW, MEDIUM, HIGH, and VERY HIGH. It is customizable according to the requirement of
the business. The risk which can cause extreme loss in the finance of the company is placed
under VERY HIGH. So that they can be fixed at first. The risks which do not cause much loss
for the company can be placed under the LOW category. The risk which are causing financial
loss of the company at a lesser rate but does not affect the system too much and can be fixed
within a few months’ time, can be placed under MEDIUM category (Bahr, 2018).

5MANAGEMENT OF SECURITY
The risk can be evaluated after the level of risk has been calculated. Evaluation of the risk
is the decision making process where one identify the risk and determines its’ severity and finds
ways to manage it.
Mitigate risk:
There are five steps in risk management in Information Technology. They are stated as
followed:
Risk identification
Risk assessment
Risk mitigation
Development of responses
Reviewing the risk management procedure
There are a few comprehensive approaches generally used by agencies of Australian
emergency management which is based on the PPRR model. The PPRR stands for
Preparedness, Prevention Response and Recovery (Hopkins, 2018).
Practical steps that must be taken for improving the IT security are:
Securing servers, computers and wireless networks
Usage of spy-ware protection
Updating software to its latest version
Data back-ups, using off site or remote storage
Password security
Staff training
Protecting IT data system (McNeil, Frey & Embrechts, 2015).
The risk can be evaluated after the level of risk has been calculated. Evaluation of the risk
is the decision making process where one identify the risk and determines its’ severity and finds
ways to manage it.
Mitigate risk:
There are five steps in risk management in Information Technology. They are stated as
followed:
Risk identification
Risk assessment
Risk mitigation
Development of responses
Reviewing the risk management procedure
There are a few comprehensive approaches generally used by agencies of Australian
emergency management which is based on the PPRR model. The PPRR stands for
Preparedness, Prevention Response and Recovery (Hopkins, 2018).
Practical steps that must be taken for improving the IT security are:
Securing servers, computers and wireless networks
Usage of spy-ware protection
Updating software to its latest version
Data back-ups, using off site or remote storage
Password security
Staff training
Protecting IT data system (McNeil, Frey & Embrechts, 2015).
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
6MANAGEMENT OF SECURITY
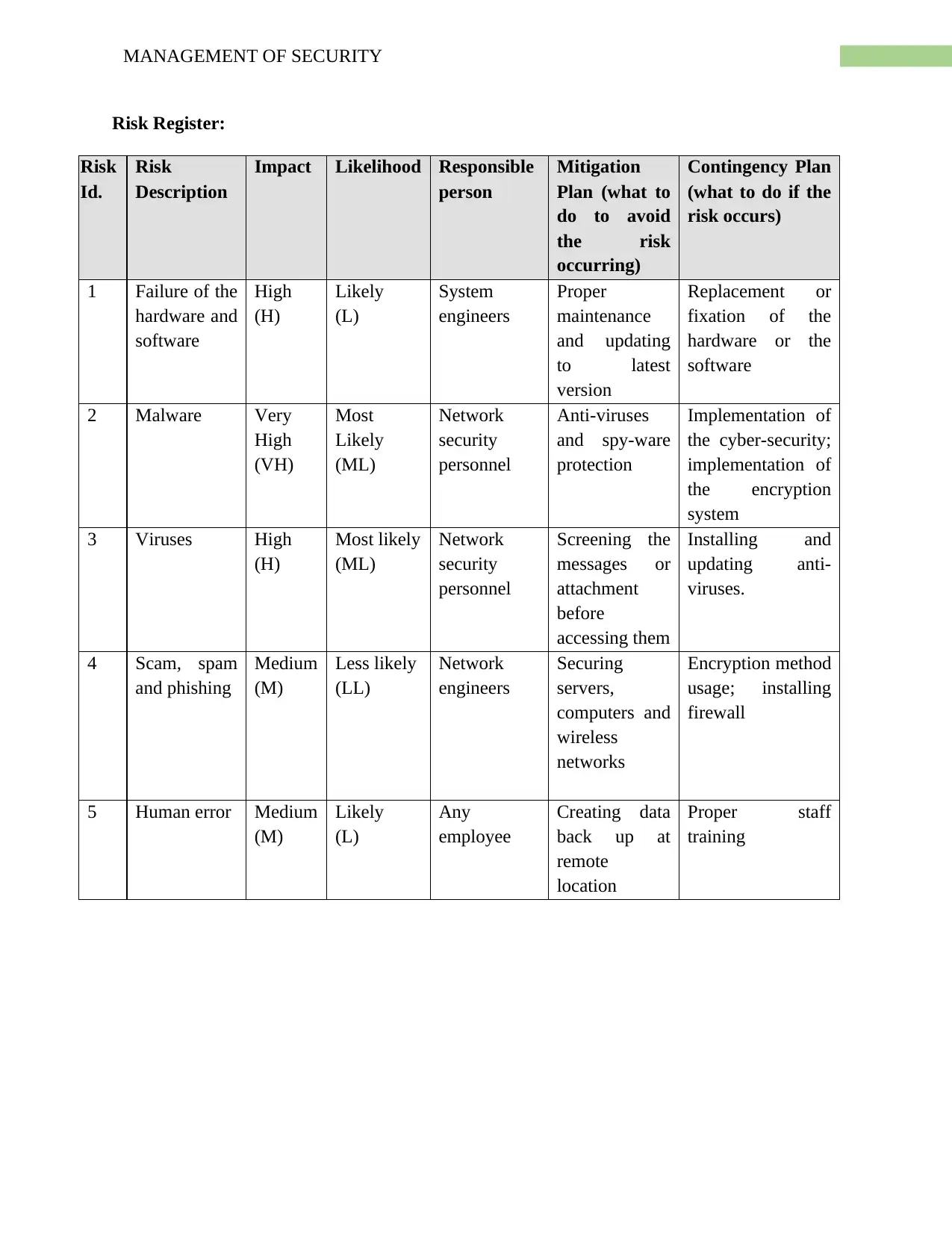
Risk Register:
Risk
Id.
Risk
Description
Impact Likelihood Responsible
person
Mitigation
Plan (what to
do to avoid
the risk
occurring)
Contingency Plan
(what to do if the
risk occurs)
1 Failure of the
hardware and
software
High
(H)
Likely
(L)
System
engineers
Proper
maintenance
and updating
to latest
version
Replacement or
fixation of the
hardware or the
software
2 Malware Very
High
(VH)
Most
Likely
(ML)
Network
security
personnel
Anti-viruses
and spy-ware
protection
Implementation of
the cyber-security;
implementation of
the encryption
system
3 Viruses High
(H)
Most likely
(ML)
Network
security
personnel
Screening the
messages or
attachment
before
accessing them
Installing and
updating anti-
viruses.
4 Scam, spam
and phishing
Medium
(M)
Less likely
(LL)
Network
engineers
Securing
servers,
computers and
wireless
networks
Encryption method
usage; installing
firewall
5 Human error Medium
(M)
Likely
(L)
Any
employee
Creating data
back up at
remote
location
Proper staff
training
Risk Register:
Risk
Id.
Risk
Description
Impact Likelihood Responsible
person
Mitigation
Plan (what to
do to avoid
the risk
occurring)
Contingency Plan
(what to do if the
risk occurs)
1 Failure of the
hardware and
software
High
(H)
Likely
(L)
System
engineers
Proper
maintenance
and updating
to latest
version
Replacement or
fixation of the
hardware or the
software
2 Malware Very
High
(VH)
Most
Likely
(ML)
Network
security
personnel
Anti-viruses
and spy-ware
protection
Implementation of
the cyber-security;
implementation of
the encryption
system
3 Viruses High
(H)
Most likely
(ML)
Network
security
personnel
Screening the
messages or
attachment
before
accessing them
Installing and
updating anti-
viruses.
4 Scam, spam
and phishing
Medium
(M)
Less likely
(LL)
Network
engineers
Securing
servers,
computers and
wireless
networks
Encryption method
usage; installing
firewall
5 Human error Medium
(M)
Likely
(L)
Any
employee
Creating data
back up at
remote
location
Proper staff
training
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
7MANAGEMENT OF SECURITY
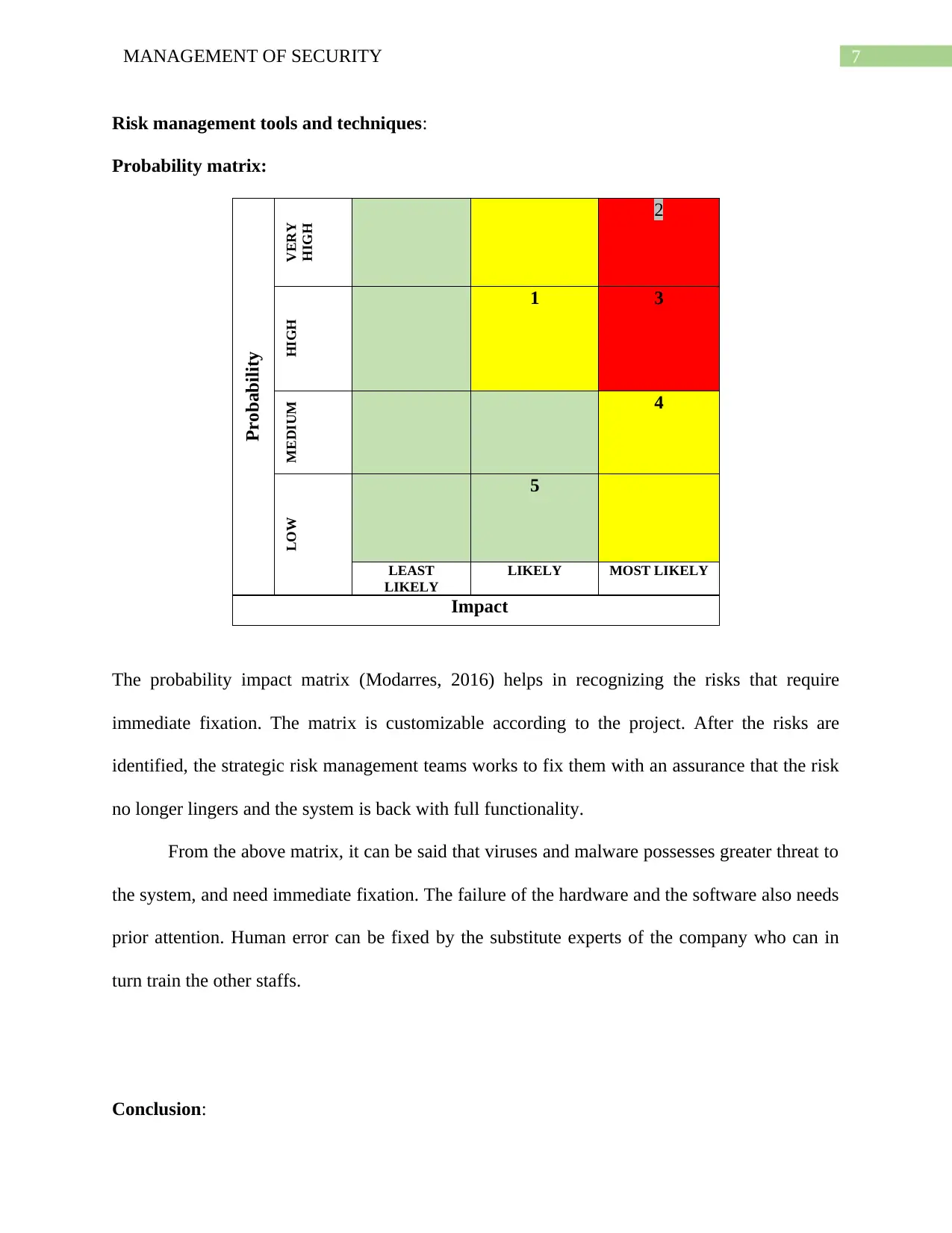
Risk management tools and techniques:
Probability matrix:Probability
VERY
HIGH 2
HIGH
1 3
MEDIUM 4
LOW
5
LEAST
LIKELY
LIKELY MOST LIKELY
Impact
The probability impact matrix (Modarres, 2016) helps in recognizing the risks that require
immediate fixation. The matrix is customizable according to the project. After the risks are
identified, the strategic risk management teams works to fix them with an assurance that the risk
no longer lingers and the system is back with full functionality.
From the above matrix, it can be said that viruses and malware possesses greater threat to
the system, and need immediate fixation. The failure of the hardware and the software also needs
prior attention. Human error can be fixed by the substitute experts of the company who can in
turn train the other staffs.
Conclusion:
Risk management tools and techniques:
Probability matrix:Probability
VERY
HIGH 2
HIGH
1 3
MEDIUM 4
LOW
5
LEAST
LIKELY
LIKELY MOST LIKELY
Impact
The probability impact matrix (Modarres, 2016) helps in recognizing the risks that require
immediate fixation. The matrix is customizable according to the project. After the risks are
identified, the strategic risk management teams works to fix them with an assurance that the risk
no longer lingers and the system is back with full functionality.
From the above matrix, it can be said that viruses and malware possesses greater threat to
the system, and need immediate fixation. The failure of the hardware and the software also needs
prior attention. Human error can be fixed by the substitute experts of the company who can in
turn train the other staffs.
Conclusion:

8MANAGEMENT OF SECURITY
Hence, it can be concluded that Infosys is a multinational corporation of India that
provides IT services which takes certain steps for the risk management in the IT services’
components. The identification of the risk is important for an organization as the consequences
of the risk can be severe for some components. Australian emergency management agencies
follow the PPRR model for the mitigation of the risk. Moreover, training the stuffs and taking
some preventive security measure can reduce the chances of occurrence of risk in the system.
Hence, it can be concluded that Infosys is a multinational corporation of India that
provides IT services which takes certain steps for the risk management in the IT services’
components. The identification of the risk is important for an organization as the consequences
of the risk can be severe for some components. Australian emergency management agencies
follow the PPRR model for the mitigation of the risk. Moreover, training the stuffs and taking
some preventive security measure can reduce the chances of occurrence of risk in the system.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

9MANAGEMENT OF SECURITY
References:
Bahr, N. J. (2018). System safety engineering and risk assessment: a practical approach. CRC
press.
Bhambhani, G., Sainy, M., & Gupta, R. (2018). An Empirical Research on Impact of HRD
Climate on Infosys Pune. Journal of Technology Management for Growing Economies,
9(1), 7-21.
Hopkin, P. (2018). Fundamentals of risk management: understanding, evaluating and
implementing effective risk management. Kogan Page Publishers.
Ismail, W., Alwi, N. H. M., Ismail, R., Bahari, M., & Zakaria, O. (2018). Readiness of
Information Security Management Systems (ISMS) Policy on Hospital Staff Using e-
Patuh System. Journal of Telecommunication, Electronic and Computer Engineering
(JTEC), 10(1-11), 47-52.
Kliem, R. L., & Ludin, I. S. (2019). Reducing project risk. Routledge.
Larson, E. W., Gray, C. F., & Irwin, M. H. (2016). University of Missouri–St.
Louis…………………. Syllabus LOGOM 6347... Project Management InfoSys 6847…
Financial and Project Management Fall 2016 A Blended Offering.
McNeil, A. J., Frey, R., & Embrechts, P. (2015). Quantitative Risk Management: Concepts,
Techniques and Tools-revised edition. Princeton university press.
Modarres, M. (2016). Risk analysis in engineering: techniques, tools, and trends. CRC press.
Niehaus, G. (2017). Enterprise Risk Management and the Risk Management Process. In The
Palgrave Handbook of Unconventional Risk Transfer (pp. 109-142). Palgrave Macmillan,
Cham.
Quintuna, X. (2014). U.S. Patent No. 8,914,441. Washington, DC: U.S. Patent and Trademark
Office.
References:
Bahr, N. J. (2018). System safety engineering and risk assessment: a practical approach. CRC
press.
Bhambhani, G., Sainy, M., & Gupta, R. (2018). An Empirical Research on Impact of HRD
Climate on Infosys Pune. Journal of Technology Management for Growing Economies,
9(1), 7-21.
Hopkin, P. (2018). Fundamentals of risk management: understanding, evaluating and
implementing effective risk management. Kogan Page Publishers.
Ismail, W., Alwi, N. H. M., Ismail, R., Bahari, M., & Zakaria, O. (2018). Readiness of
Information Security Management Systems (ISMS) Policy on Hospital Staff Using e-
Patuh System. Journal of Telecommunication, Electronic and Computer Engineering
(JTEC), 10(1-11), 47-52.
Kliem, R. L., & Ludin, I. S. (2019). Reducing project risk. Routledge.
Larson, E. W., Gray, C. F., & Irwin, M. H. (2016). University of Missouri–St.
Louis…………………. Syllabus LOGOM 6347... Project Management InfoSys 6847…
Financial and Project Management Fall 2016 A Blended Offering.
McNeil, A. J., Frey, R., & Embrechts, P. (2015). Quantitative Risk Management: Concepts,
Techniques and Tools-revised edition. Princeton university press.
Modarres, M. (2016). Risk analysis in engineering: techniques, tools, and trends. CRC press.
Niehaus, G. (2017). Enterprise Risk Management and the Risk Management Process. In The
Palgrave Handbook of Unconventional Risk Transfer (pp. 109-142). Palgrave Macmillan,
Cham.
Quintuna, X. (2014). U.S. Patent No. 8,914,441. Washington, DC: U.S. Patent and Trademark
Office.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

10MANAGEMENT OF SECURITY
1 out of 11
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.




