Digital Age Professional Skills: Analysis and Application
VerifiedAdded on 2023/06/04
|12
|3784
|279
Report
AI Summary
This report examines the integrated professional skills required in the digital age, comparing online and offline business operations, and discussing the associated benefits and drawbacks. It addresses crucial measures and challenges related to business and individual privacy and security in the online environment, emphasizing vulnerabilities to hacking, security threats, and data protection issues. The report also contrasts and compares the application, suitability, and features of online tools like TeamViewer and Zoom, which are vital for modern business communication and collaboration. Concluding with the importance of adopting digital technology for growth and the necessity of developing new skills for the 21st century, this report provides insights into navigating the complexities of the digital landscape and enhancing professional capabilities. Desklib offers more solved assignments and resources for students.

Integrated Professional Skills
in Digital Age
in Digital Age
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Table of Contents
INTRODUCTION...........................................................................................................................3
MAIN BODY...................................................................................................................................3
Comparing the aspect of selling product and service offline and online.....................................3
Discussing the measures and challenges of business and individual privacy and security.........5
Comparing and contrasting of application, suitability and features of online tools....................8
CONCLUSION..............................................................................................................................10
REFERENCES................................................................................................................................1
INTRODUCTION...........................................................................................................................3
MAIN BODY...................................................................................................................................3
Comparing the aspect of selling product and service offline and online.....................................3
Discussing the measures and challenges of business and individual privacy and security.........5
Comparing and contrasting of application, suitability and features of online tools....................8
CONCLUSION..............................................................................................................................10
REFERENCES................................................................................................................................1

INTRODUCTION
To an individual and the organization there is the requirement of adapting of the digital
technology as it helps in the growth (Starkey, 2020). According to the 21st century an individual
will able to develop the new skills and the knowledge through digital age. To connect with the
today's world there is the requirement of these skills. To the future competencies there is the
need of expertise in ICT, social intelligence and the creativity. Through the digital age business
will able to improve the communication, retrieval and the storage of data.
The current report will contrast and compare the negative and the positive affect to the
online and the offline product and service sold. The report will discuss the measure and the
challenges of the individual and business security and privacy online. Further, the report will
contrast and compare the applications, features and the suitability of the Team viewer and the
Zoom tools adapted by business.
MAIN BODY
Comparing the aspect of selling product and service offline and online
Positive and the negative of being online
The individual and the business who place themselves online includes many benefits:
Access to the global – It will help the business in gaining more customer by accessing the
global market. The firm will also able to sell and promote the business online.
Unlimited Market – To the providing of the product and the service business is able to
target its potential market due to the global reach through the internet (Wang, Somogyi
and Charlebois, 2020). In a cost effective way business will able to easily expand and
target the market.
Low marketing cost – The business will able to market its product and service at lower
cost through the online platforms. The variety of new customers will be attracted to the
business by providing of the blogs and the articles (Li and et.al., 2021). In the simple
manner the business can be promoted by using the tools such as Google ads for
advertising.
Ease of transactions – Through the internet business and the individual can easily made
the transactions. To make the payment of the product and the service business can use the
secured gateway payments (Ryu, Cho and Lee, 2019). There will be the much easier
To an individual and the organization there is the requirement of adapting of the digital
technology as it helps in the growth (Starkey, 2020). According to the 21st century an individual
will able to develop the new skills and the knowledge through digital age. To connect with the
today's world there is the requirement of these skills. To the future competencies there is the
need of expertise in ICT, social intelligence and the creativity. Through the digital age business
will able to improve the communication, retrieval and the storage of data.
The current report will contrast and compare the negative and the positive affect to the
online and the offline product and service sold. The report will discuss the measure and the
challenges of the individual and business security and privacy online. Further, the report will
contrast and compare the applications, features and the suitability of the Team viewer and the
Zoom tools adapted by business.
MAIN BODY
Comparing the aspect of selling product and service offline and online
Positive and the negative of being online
The individual and the business who place themselves online includes many benefits:
Access to the global – It will help the business in gaining more customer by accessing the
global market. The firm will also able to sell and promote the business online.
Unlimited Market – To the providing of the product and the service business is able to
target its potential market due to the global reach through the internet (Wang, Somogyi
and Charlebois, 2020). In a cost effective way business will able to easily expand and
target the market.
Low marketing cost – The business will able to market its product and service at lower
cost through the online platforms. The variety of new customers will be attracted to the
business by providing of the blogs and the articles (Li and et.al., 2021). In the simple
manner the business can be promoted by using the tools such as Google ads for
advertising.
Ease of transactions – Through the internet business and the individual can easily made
the transactions. To make the payment of the product and the service business can use the
secured gateway payments (Ryu, Cho and Lee, 2019). There will be the much easier
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

making of the payments and the reducing of the paper cash by adapting the latest
technology.
The negative effect to the business and the individual going online:
No option of trial – The products such as clothes, shoes, electronics, furniture and many
more items purchased by the customers does not have the option of trial of the product
(Li and et.al., 2021). Most of the retail business has provides the option of reviewing of
products through clicking of photos and the videos. Though many of the customers prefer
to trial the product before purchasing.
Impersonal – There is also no relationship between the customers and the business while
shopping online. In the offline mode customer has the option to complaint about the
product by directly reaching to the stores (Wang, Somogyi and Charlebois, 2020). The
individual customer will not be able to satisfy through the online responses.
Productivity – There is the defined work of the individual and the hours of the business
were scheduled in offline stores. There is the dedicated hour of operation. Thus, in the
online stores business remains open all time. Thus, if the time was not managed properly
there will be the low productivity of the business (Ryu, Cho and Lee, 2019). The training
will be held in few days, weeks or months. To the job profiles of the employees they will
not get the satisfaction in some cases.
Positive and the negative of being offline
To the individual and business the positive of being offline are:
Loyalty building – There will be the loyalty of the brand and the product as there is the
visuality of the buying of the product. There will be the good relationship between the
business and the consumer and there will also be easy promoting of the service and the
product to the consumer (Wang, Somogyi and Charlebois, 2020).
Personal connection – The concept of personalized will be more better created in the case
of offline business. To get the solution of the problem an individual can directly reach to
the stores.
Damage avoiding – In the case of the offline shopping there will be the less damage to
the product and the service while transporting or the shipment. The buyer will only
responsible for the good after purchasing it (Ryu, Cho and Lee, 2019).
technology.
The negative effect to the business and the individual going online:
No option of trial – The products such as clothes, shoes, electronics, furniture and many
more items purchased by the customers does not have the option of trial of the product
(Li and et.al., 2021). Most of the retail business has provides the option of reviewing of
products through clicking of photos and the videos. Though many of the customers prefer
to trial the product before purchasing.
Impersonal – There is also no relationship between the customers and the business while
shopping online. In the offline mode customer has the option to complaint about the
product by directly reaching to the stores (Wang, Somogyi and Charlebois, 2020). The
individual customer will not be able to satisfy through the online responses.
Productivity – There is the defined work of the individual and the hours of the business
were scheduled in offline stores. There is the dedicated hour of operation. Thus, in the
online stores business remains open all time. Thus, if the time was not managed properly
there will be the low productivity of the business (Ryu, Cho and Lee, 2019). The training
will be held in few days, weeks or months. To the job profiles of the employees they will
not get the satisfaction in some cases.
Positive and the negative of being offline
To the individual and business the positive of being offline are:
Loyalty building – There will be the loyalty of the brand and the product as there is the
visuality of the buying of the product. There will be the good relationship between the
business and the consumer and there will also be easy promoting of the service and the
product to the consumer (Wang, Somogyi and Charlebois, 2020).
Personal connection – The concept of personalized will be more better created in the case
of offline business. To get the solution of the problem an individual can directly reach to
the stores.
Damage avoiding – In the case of the offline shopping there will be the less damage to
the product and the service while transporting or the shipment. The buyer will only
responsible for the good after purchasing it (Ryu, Cho and Lee, 2019).
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Online frauds were avoided – There is low or the no chances of fraud as the transaction
was made in the cash form or through the live card payments. In the online shopping the
fraud is much more (Li and et.al., 2021). Companies portfolio also strengthened and the
brand trust was also established by the individual.
There are some negatives of the offline business are:
To facilitate the product and the service to the customer most of the offline business
venture lease or build the property. Thus, in the e-commerce business the product and the
service were available through the website of the company to the global market (Ryu,
Cho and Lee, 2019).
To the area of the work the offline store reach is limited. There is the huge level of
customer base and the reach in the online stores.
This impacts in the growth of the business as for the offline business there is the limited
market (Li and et.al., 2021). Thus, due to reduce in the reach and market position most of
the offline business have to shut down as they were occurring the continuous loss.
To the offline stores the customer were decreasing because of the shifting to the online
stores. The traditional market in today's era is reducing as most of the people prefer to
shop from there home or from their comfort place.
Thus, it has been identified that both the offline and the online business contains
advantages and disadvantages (Starkey, 2020). To achieve the success and the profit in the
business most of the business chooses both the offline and the online method which help the
business to grow further. Choosing the both option will help the business in reaching the both
potential customers.
Discussing the measures and challenges of business and individual privacy and security
Thus, while shifting to the online individual and the business faces several measures and
the challenges of privacy and security (Barth and et.al., 2019). To the security and the privacy of
the individual there is very important to understand the challenges of security and privacy. It will
help in the reducing of the hazardous situations.
On the regular basis there are the challenges which were faced are:
Vulnerability due to hacking – The devices which were linked with the hacking
includes the potential risks. In many countries this impacts in the spread of vulnerability,
the hackers were unauthorized accessing the user id. To invading the houses hackers were
was made in the cash form or through the live card payments. In the online shopping the
fraud is much more (Li and et.al., 2021). Companies portfolio also strengthened and the
brand trust was also established by the individual.
There are some negatives of the offline business are:
To facilitate the product and the service to the customer most of the offline business
venture lease or build the property. Thus, in the e-commerce business the product and the
service were available through the website of the company to the global market (Ryu,
Cho and Lee, 2019).
To the area of the work the offline store reach is limited. There is the huge level of
customer base and the reach in the online stores.
This impacts in the growth of the business as for the offline business there is the limited
market (Li and et.al., 2021). Thus, due to reduce in the reach and market position most of
the offline business have to shut down as they were occurring the continuous loss.
To the offline stores the customer were decreasing because of the shifting to the online
stores. The traditional market in today's era is reducing as most of the people prefer to
shop from there home or from their comfort place.
Thus, it has been identified that both the offline and the online business contains
advantages and disadvantages (Starkey, 2020). To achieve the success and the profit in the
business most of the business chooses both the offline and the online method which help the
business to grow further. Choosing the both option will help the business in reaching the both
potential customers.
Discussing the measures and challenges of business and individual privacy and security
Thus, while shifting to the online individual and the business faces several measures and
the challenges of privacy and security (Barth and et.al., 2019). To the security and the privacy of
the individual there is very important to understand the challenges of security and privacy. It will
help in the reducing of the hazardous situations.
On the regular basis there are the challenges which were faced are:
Vulnerability due to hacking – The devices which were linked with the hacking
includes the potential risks. In many countries this impacts in the spread of vulnerability,
the hackers were unauthorized accessing the user id. To invading the houses hackers were

connecting with the devices. Thus, when the individual home was hacked by the hacker
there is no privacy of the individual (Khan, Brohi and Zaman, 2020). The hackers also
target the home cameras of the individual which allows them to get the access of the
activities of the individual. In the current time solving the issue of hacking contains a lot
of time. To secure there devices manufacture should be active and take the responsibility
of handling the issue. The devices which were linked with the network connection should
be secured and also the application of the software should be securely built.
Threat of security – In the today's world most of the security challenges faced to the
business due to the human elements (Tawalbeh and et.al., 2020). Due to the failing of the
human there are the lot of the attacks and the breaches to the company was successful.
Data protection – The large number of the necessary information can be collected
through the various sites. Through the malicious hackers the data of the business was
hacked. In most of the business the data has been leaked as due to the poor management.
Most of the employees who were leaving the premises were leaking the data of the
business through the medium of the internet (Srinivas, Das and Kumar, 2019). The
devices which were connected to the internet includes a lot of information in it, thus this
lead the business in the risk while connecting with the device. There are incurred many
cybercrime issues as by the identifying the protection of the data.
The identified challenges can be addressed through the measurement:
Training of the employees – Training the employees in the proper and the organized
manner is important for the business (Tawalbeh and et.al., 2020). Business should
provide the training to the employees that they should follow the session of the online
privacy and the security.
Anti virus – The business should regularly use the anti virus software for avoiding the
threat of hacking. In the business every computer should have the installation of the
software and it was suggested that it should be updated timely (Srinivas, Das and Kumar,
2019). Avoiding of the unnecessary malware attacks and the virus to the system was
necessary. To the internet connection there should be important of having the firewall.
Software updating – To operate the system business needs to track that the installed
software updates were downloaded timely. The attacks of prone to the software can be
there is no privacy of the individual (Khan, Brohi and Zaman, 2020). The hackers also
target the home cameras of the individual which allows them to get the access of the
activities of the individual. In the current time solving the issue of hacking contains a lot
of time. To secure there devices manufacture should be active and take the responsibility
of handling the issue. The devices which were linked with the network connection should
be secured and also the application of the software should be securely built.
Threat of security – In the today's world most of the security challenges faced to the
business due to the human elements (Tawalbeh and et.al., 2020). Due to the failing of the
human there are the lot of the attacks and the breaches to the company was successful.
Data protection – The large number of the necessary information can be collected
through the various sites. Through the malicious hackers the data of the business was
hacked. In most of the business the data has been leaked as due to the poor management.
Most of the employees who were leaving the premises were leaking the data of the
business through the medium of the internet (Srinivas, Das and Kumar, 2019). The
devices which were connected to the internet includes a lot of information in it, thus this
lead the business in the risk while connecting with the device. There are incurred many
cybercrime issues as by the identifying the protection of the data.
The identified challenges can be addressed through the measurement:
Training of the employees – Training the employees in the proper and the organized
manner is important for the business (Tawalbeh and et.al., 2020). Business should
provide the training to the employees that they should follow the session of the online
privacy and the security.
Anti virus – The business should regularly use the anti virus software for avoiding the
threat of hacking. In the business every computer should have the installation of the
software and it was suggested that it should be updated timely (Srinivas, Das and Kumar,
2019). Avoiding of the unnecessary malware attacks and the virus to the system was
necessary. To the internet connection there should be important of having the firewall.
Software updating – To operate the system business needs to track that the installed
software updates were downloaded timely. The attacks of prone to the software can be
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

avoided through the licensing of the expired software timely (Khan, Brohi and Zaman,
2020).
Back ups – To the all important data of the company the back up copies should be
created by the business and it is very important. To avoid the unnecessary situations such
as the prone to the attack on the information the back up is important (Barth and et.al.,
2019). The function of the company will operate smoothly when the data of the company
does not lose.
Physical access controlling – To the computers it was necessary that the access is
properly controlled physically. ISMS policies should be necessarily followed by the
employees. The difficult password should be used by the business (Khan, Brohi and
Zaman, 2020). The employees in the organization should be updated the password on the
timely and regular basis. Thus, unwanted threats of the hacking or the leaking of the data
can be avoided through controlling the physical access.
Wi-Fi network securing – Wi-Fi networks should be always secured. Securing of the
internet is important for the organization which installed the Wi-Fi in the work place. The
hacking of the password of the Wi-Fi can be avoided by hiding the device in the proper
place (Srinivas, Das and Kumar, 2019). The Wi-Fi network can also be secured through
virtually barging in the premises of office.
Accounts of individual – Sharing of the accounts should not be allowed to the
employees. Sharing of the accounts will lead in the security threat increasing. There is not
allowed to access the others account by the employees (Khan, Brohi and Zaman, 2020).
Accessing to the another account may lead to the punishment.
Limited access – Accessing of the data should be limited, as more access leads to more
leakage of data. The users which were not allowed to access the information will be
penalized if they access the data (Barth and et.al., 2019). From the unauthorized persons
the informations should be encrypted properly.
Never equate small to safe – Many companies thinks that there data is out of breach,
safe from the hackers, viruses and the malware, even after the major exposure of
cybercrime. The small business have the beliefs that there business will not be targeted
by the hacker which leads in the more cyber attacks to the business (Srinivas, Das and
Kumar, 2019).
2020).
Back ups – To the all important data of the company the back up copies should be
created by the business and it is very important. To avoid the unnecessary situations such
as the prone to the attack on the information the back up is important (Barth and et.al.,
2019). The function of the company will operate smoothly when the data of the company
does not lose.
Physical access controlling – To the computers it was necessary that the access is
properly controlled physically. ISMS policies should be necessarily followed by the
employees. The difficult password should be used by the business (Khan, Brohi and
Zaman, 2020). The employees in the organization should be updated the password on the
timely and regular basis. Thus, unwanted threats of the hacking or the leaking of the data
can be avoided through controlling the physical access.
Wi-Fi network securing – Wi-Fi networks should be always secured. Securing of the
internet is important for the organization which installed the Wi-Fi in the work place. The
hacking of the password of the Wi-Fi can be avoided by hiding the device in the proper
place (Srinivas, Das and Kumar, 2019). The Wi-Fi network can also be secured through
virtually barging in the premises of office.
Accounts of individual – Sharing of the accounts should not be allowed to the
employees. Sharing of the accounts will lead in the security threat increasing. There is not
allowed to access the others account by the employees (Khan, Brohi and Zaman, 2020).
Accessing to the another account may lead to the punishment.
Limited access – Accessing of the data should be limited, as more access leads to more
leakage of data. The users which were not allowed to access the information will be
penalized if they access the data (Barth and et.al., 2019). From the unauthorized persons
the informations should be encrypted properly.
Never equate small to safe – Many companies thinks that there data is out of breach,
safe from the hackers, viruses and the malware, even after the major exposure of
cybercrime. The small business have the beliefs that there business will not be targeted
by the hacker which leads in the more cyber attacks to the business (Srinivas, Das and
Kumar, 2019).
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Comparing and contrasting of application, suitability and features of online tools
When lock-down become new normal after pandemic, most of the businesses and
customers went digital. Online has become new mode to conduct business practices which aids
to serve people with demanded goods and services through online. There is hike in markets after
post pandemic concerns as it raised awareness among people and made them more conscious
about their health. Technological business aids employee to interact and communicate with each
other in most effective ways (Oloyede, Faruk and Raji, 2022). With the ease of online tools helps
employees to focus on their work and enhanced productivity. It serves chance to take quick
actions as it can be done through visual management feature. It allows all necessitate information
to be reflected in the easiest way which can be easily understood by other individual. Online
platform facilities serve business with chance to interact with customers in most lucrative ways.
It enhances flexibility and way of conducting business which makes business to be most
significant and concerned in the marketplace. Pandemic has altered various changes in the
economy whereby business also initiated their steps towards following the modern trend. Online
has become highly recommended technological aspect which forms company to promote their
useful activities accordingly.
In this manner the two major tools used by most of the business was zoom and team
viewer. Both applications serve suitable facilities and chance for business to create continuity in
their business process. Zoom is considered as one of the best platforms to conduct meetings and
other general talks. In that concern many companies gone virtual for meetings and it is the safest
as well as affordable. Such approaches towards business operations is familiar with permanent
access even after impact of crisis. Thus, shift towards online considered beneficial for business
as it enhanced chance for business to conduct favourable practices and form the valuable image.
There are several benefits which is favoured by online practices in order to reflect better working
aspects (Shayaa and et.al., 2018). In the context of online tools there is vast differentiation
between zoom and team viewer can be described clearly. Team viewer cover better security as
zoom is originate to be controversial for this. But it is an amazing tool which forms meeting
experience in completely different way.
Particulars Zoom Team viewer
Features Provides easy access to
conduct meetings,
Session features – it
includes annotations
When lock-down become new normal after pandemic, most of the businesses and
customers went digital. Online has become new mode to conduct business practices which aids
to serve people with demanded goods and services through online. There is hike in markets after
post pandemic concerns as it raised awareness among people and made them more conscious
about their health. Technological business aids employee to interact and communicate with each
other in most effective ways (Oloyede, Faruk and Raji, 2022). With the ease of online tools helps
employees to focus on their work and enhanced productivity. It serves chance to take quick
actions as it can be done through visual management feature. It allows all necessitate information
to be reflected in the easiest way which can be easily understood by other individual. Online
platform facilities serve business with chance to interact with customers in most lucrative ways.
It enhances flexibility and way of conducting business which makes business to be most
significant and concerned in the marketplace. Pandemic has altered various changes in the
economy whereby business also initiated their steps towards following the modern trend. Online
has become highly recommended technological aspect which forms company to promote their
useful activities accordingly.
In this manner the two major tools used by most of the business was zoom and team
viewer. Both applications serve suitable facilities and chance for business to create continuity in
their business process. Zoom is considered as one of the best platforms to conduct meetings and
other general talks. In that concern many companies gone virtual for meetings and it is the safest
as well as affordable. Such approaches towards business operations is familiar with permanent
access even after impact of crisis. Thus, shift towards online considered beneficial for business
as it enhanced chance for business to conduct favourable practices and form the valuable image.
There are several benefits which is favoured by online practices in order to reflect better working
aspects (Shayaa and et.al., 2018). In the context of online tools there is vast differentiation
between zoom and team viewer can be described clearly. Team viewer cover better security as
zoom is originate to be controversial for this. But it is an amazing tool which forms meeting
experience in completely different way.
Particulars Zoom Team viewer
Features Provides easy access to
conduct meetings,
Session features – it
includes annotations
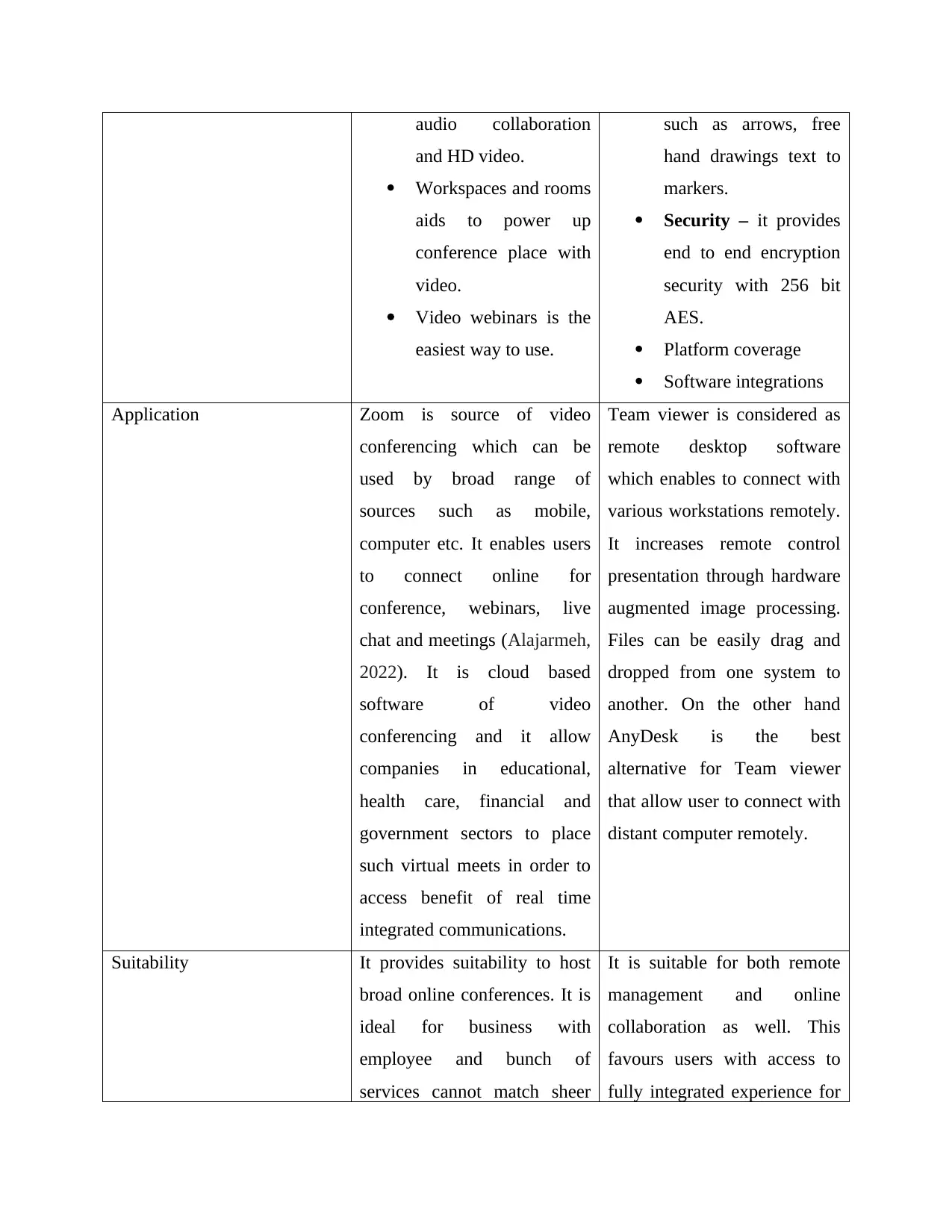
audio collaboration
and HD video.
Workspaces and rooms
aids to power up
conference place with
video.
Video webinars is the
easiest way to use.
such as arrows, free
hand drawings text to
markers.
Security – it provides
end to end encryption
security with 256 bit
AES.
Platform coverage
Software integrations
Application Zoom is source of video
conferencing which can be
used by broad range of
sources such as mobile,
computer etc. It enables users
to connect online for
conference, webinars, live
chat and meetings (Alajarmeh,
2022). It is cloud based
software of video
conferencing and it allow
companies in educational,
health care, financial and
government sectors to place
such virtual meets in order to
access benefit of real time
integrated communications.
Team viewer is considered as
remote desktop software
which enables to connect with
various workstations remotely.
It increases remote control
presentation through hardware
augmented image processing.
Files can be easily drag and
dropped from one system to
another. On the other hand
AnyDesk is the best
alternative for Team viewer
that allow user to connect with
distant computer remotely.
Suitability It provides suitability to host
broad online conferences. It is
ideal for business with
employee and bunch of
services cannot match sheer
It is suitable for both remote
management and online
collaboration as well. This
favours users with access to
fully integrated experience for
and HD video.
Workspaces and rooms
aids to power up
conference place with
video.
Video webinars is the
easiest way to use.
such as arrows, free
hand drawings text to
markers.
Security – it provides
end to end encryption
security with 256 bit
AES.
Platform coverage
Software integrations
Application Zoom is source of video
conferencing which can be
used by broad range of
sources such as mobile,
computer etc. It enables users
to connect online for
conference, webinars, live
chat and meetings (Alajarmeh,
2022). It is cloud based
software of video
conferencing and it allow
companies in educational,
health care, financial and
government sectors to place
such virtual meets in order to
access benefit of real time
integrated communications.
Team viewer is considered as
remote desktop software
which enables to connect with
various workstations remotely.
It increases remote control
presentation through hardware
augmented image processing.
Files can be easily drag and
dropped from one system to
another. On the other hand
AnyDesk is the best
alternative for Team viewer
that allow user to connect with
distant computer remotely.
Suitability It provides suitability to host
broad online conferences. It is
ideal for business with
employee and bunch of
services cannot match sheer
It is suitable for both remote
management and online
collaboration as well. This
favours users with access to
fully integrated experience for
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
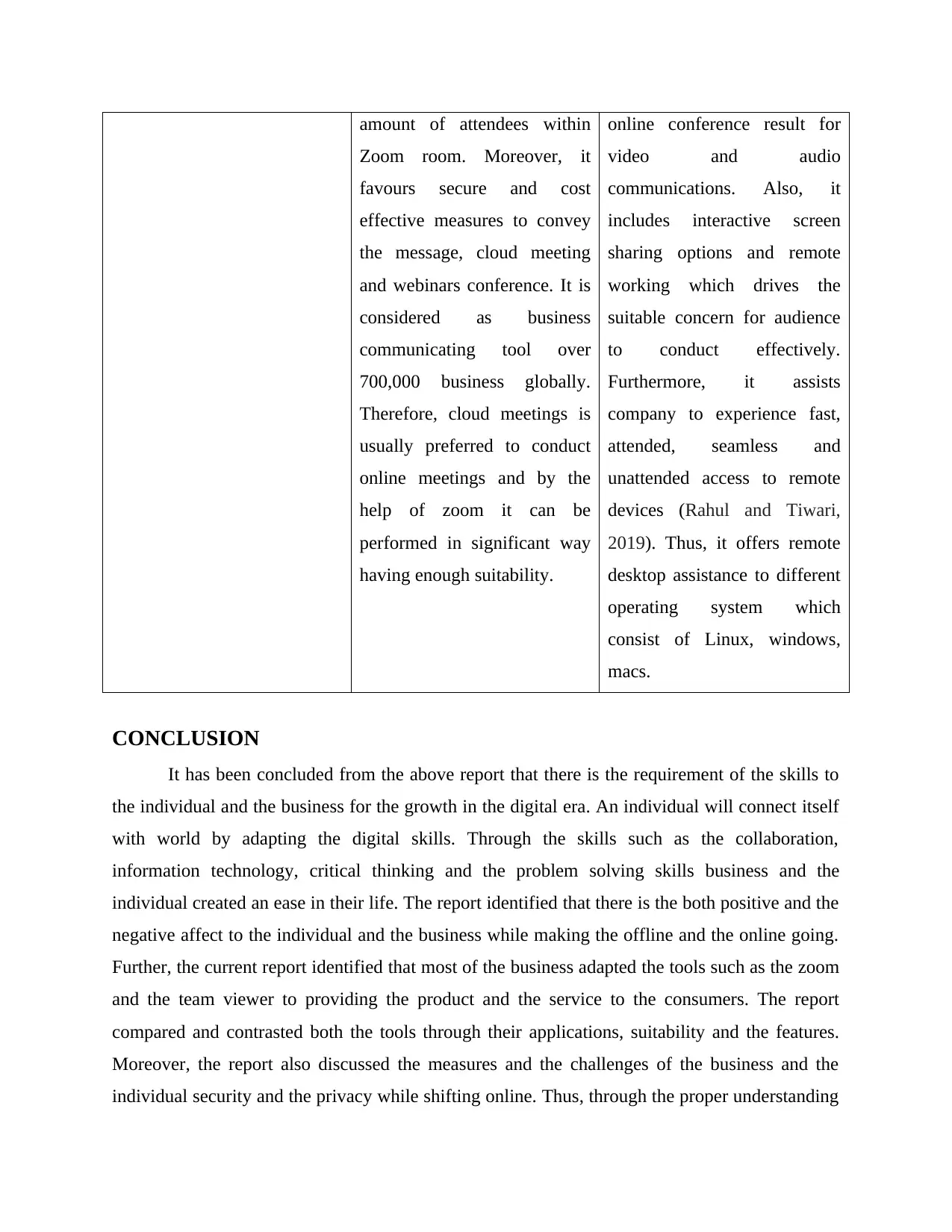
amount of attendees within
Zoom room. Moreover, it
favours secure and cost
effective measures to convey
the message, cloud meeting
and webinars conference. It is
considered as business
communicating tool over
700,000 business globally.
Therefore, cloud meetings is
usually preferred to conduct
online meetings and by the
help of zoom it can be
performed in significant way
having enough suitability.
online conference result for
video and audio
communications. Also, it
includes interactive screen
sharing options and remote
working which drives the
suitable concern for audience
to conduct effectively.
Furthermore, it assists
company to experience fast,
attended, seamless and
unattended access to remote
devices (Rahul and Tiwari,
2019). Thus, it offers remote
desktop assistance to different
operating system which
consist of Linux, windows,
macs.
CONCLUSION
It has been concluded from the above report that there is the requirement of the skills to
the individual and the business for the growth in the digital era. An individual will connect itself
with world by adapting the digital skills. Through the skills such as the collaboration,
information technology, critical thinking and the problem solving skills business and the
individual created an ease in their life. The report identified that there is the both positive and the
negative affect to the individual and the business while making the offline and the online going.
Further, the current report identified that most of the business adapted the tools such as the zoom
and the team viewer to providing the product and the service to the consumers. The report
compared and contrasted both the tools through their applications, suitability and the features.
Moreover, the report also discussed the measures and the challenges of the business and the
individual security and the privacy while shifting online. Thus, through the proper understanding
Zoom room. Moreover, it
favours secure and cost
effective measures to convey
the message, cloud meeting
and webinars conference. It is
considered as business
communicating tool over
700,000 business globally.
Therefore, cloud meetings is
usually preferred to conduct
online meetings and by the
help of zoom it can be
performed in significant way
having enough suitability.
online conference result for
video and audio
communications. Also, it
includes interactive screen
sharing options and remote
working which drives the
suitable concern for audience
to conduct effectively.
Furthermore, it assists
company to experience fast,
attended, seamless and
unattended access to remote
devices (Rahul and Tiwari,
2019). Thus, it offers remote
desktop assistance to different
operating system which
consist of Linux, windows,
macs.
CONCLUSION
It has been concluded from the above report that there is the requirement of the skills to
the individual and the business for the growth in the digital era. An individual will connect itself
with world by adapting the digital skills. Through the skills such as the collaboration,
information technology, critical thinking and the problem solving skills business and the
individual created an ease in their life. The report identified that there is the both positive and the
negative affect to the individual and the business while making the offline and the online going.
Further, the current report identified that most of the business adapted the tools such as the zoom
and the team viewer to providing the product and the service to the consumers. The report
compared and contrasted both the tools through their applications, suitability and the features.
Moreover, the report also discussed the measures and the challenges of the business and the
individual security and the privacy while shifting online. Thus, through the proper understanding
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

and the learning of the digital skills business was able to achieve the profit in competitive world.
It has also been identified that most of the business survived in the pandemic by adapting the
digital era.
It has also been identified that most of the business survived in the pandemic by adapting the
digital era.

REFERENCES
Books and Journals
Alajarmeh, N., 2022. The extent of mobile accessibility coverage in WCAG 2.1: Sufficiency of
success criteria and appropriateness of relevant conformance levels pertaining to
accessibility problems encountered by users who are visually impaired. Universal
Access in the Information Society. 21(2). pp.507-532.
Barth, S., and et.al., 2019. Putting the privacy paradox to the test: Online privacy and security
behaviors among users with technical knowledge, privacy awareness, and financial
resources. Telematics and informatics. 41. pp.55-69.
Khan, N.A., Brohi, S.N. and Zaman, N., 2020. Ten deadly cyber security threats amid COVID-
19 pandemic.
Li, Y., and et.al., 2021. Reveal or hide? Impact of demonstration on pricing decisions
considering showrooming behavior. Omega. 102. p.102329.
Oloyede, A.A., Faruk, N. and Raji, W.O., 2022. COVID-19 lockdown and remote attendance
teaching in developing countries: A review of some online pedagogical
resources. African Journal of Science, Technology, Innovation and Development. 14(3).
pp.678-696.
Rahul, K. and Tiwari, A.K., 2019. FQI: feature‐based reduced‐reference image quality
assessment method for screen content images. IET Image Processing. 13(7). pp.1170-
1180.
Ryu, M.H., Cho, Y. and Lee, D., 2019. Should small-scale online retailers diversify distribution
channels into offline channels? Focused on the clothing and fashion industry. Journal of
Retailing and Consumer Services. 47. pp.74-77.
Shayaa, S., and et.al., 2018. Sentiment analysis of big data: methods, applications, and open
challenges. IEEE Access. 6. pp.37807-37827.
Srinivas, J., Das, A.K. and Kumar, N., 2019. Government regulations in cyber security:
Framework, standards and recommendations. Future generation computer systems. 92.
pp.178-188.
Starkey, L., 2020. A review of research exploring teacher preparation for the digital
age. Cambridge Journal of Education. 50(1). pp.37-56.
Tawalbeh, L.A., and et.al., 2020. IoT Privacy and security: Challenges and solutions. Applied
Sciences. 10(12). p.4102.
Wang, O., Somogyi, S. and Charlebois, S., 2020. Food choice in the e-commerce era: a
comparison between business-to-consumer (B2C), online-to-offline (O2O) and new
retail. British Food Journal.
Books and Journals
Alajarmeh, N., 2022. The extent of mobile accessibility coverage in WCAG 2.1: Sufficiency of
success criteria and appropriateness of relevant conformance levels pertaining to
accessibility problems encountered by users who are visually impaired. Universal
Access in the Information Society. 21(2). pp.507-532.
Barth, S., and et.al., 2019. Putting the privacy paradox to the test: Online privacy and security
behaviors among users with technical knowledge, privacy awareness, and financial
resources. Telematics and informatics. 41. pp.55-69.
Khan, N.A., Brohi, S.N. and Zaman, N., 2020. Ten deadly cyber security threats amid COVID-
19 pandemic.
Li, Y., and et.al., 2021. Reveal or hide? Impact of demonstration on pricing decisions
considering showrooming behavior. Omega. 102. p.102329.
Oloyede, A.A., Faruk, N. and Raji, W.O., 2022. COVID-19 lockdown and remote attendance
teaching in developing countries: A review of some online pedagogical
resources. African Journal of Science, Technology, Innovation and Development. 14(3).
pp.678-696.
Rahul, K. and Tiwari, A.K., 2019. FQI: feature‐based reduced‐reference image quality
assessment method for screen content images. IET Image Processing. 13(7). pp.1170-
1180.
Ryu, M.H., Cho, Y. and Lee, D., 2019. Should small-scale online retailers diversify distribution
channels into offline channels? Focused on the clothing and fashion industry. Journal of
Retailing and Consumer Services. 47. pp.74-77.
Shayaa, S., and et.al., 2018. Sentiment analysis of big data: methods, applications, and open
challenges. IEEE Access. 6. pp.37807-37827.
Srinivas, J., Das, A.K. and Kumar, N., 2019. Government regulations in cyber security:
Framework, standards and recommendations. Future generation computer systems. 92.
pp.178-188.
Starkey, L., 2020. A review of research exploring teacher preparation for the digital
age. Cambridge Journal of Education. 50(1). pp.37-56.
Tawalbeh, L.A., and et.al., 2020. IoT Privacy and security: Challenges and solutions. Applied
Sciences. 10(12). p.4102.
Wang, O., Somogyi, S. and Charlebois, S., 2020. Food choice in the e-commerce era: a
comparison between business-to-consumer (B2C), online-to-offline (O2O) and new
retail. British Food Journal.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 12
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.




