Intel Network Infrastructure: Objectives and Design Presentation
VerifiedAdded on 2022/08/18
|13
|862
|11
Presentation
AI Summary
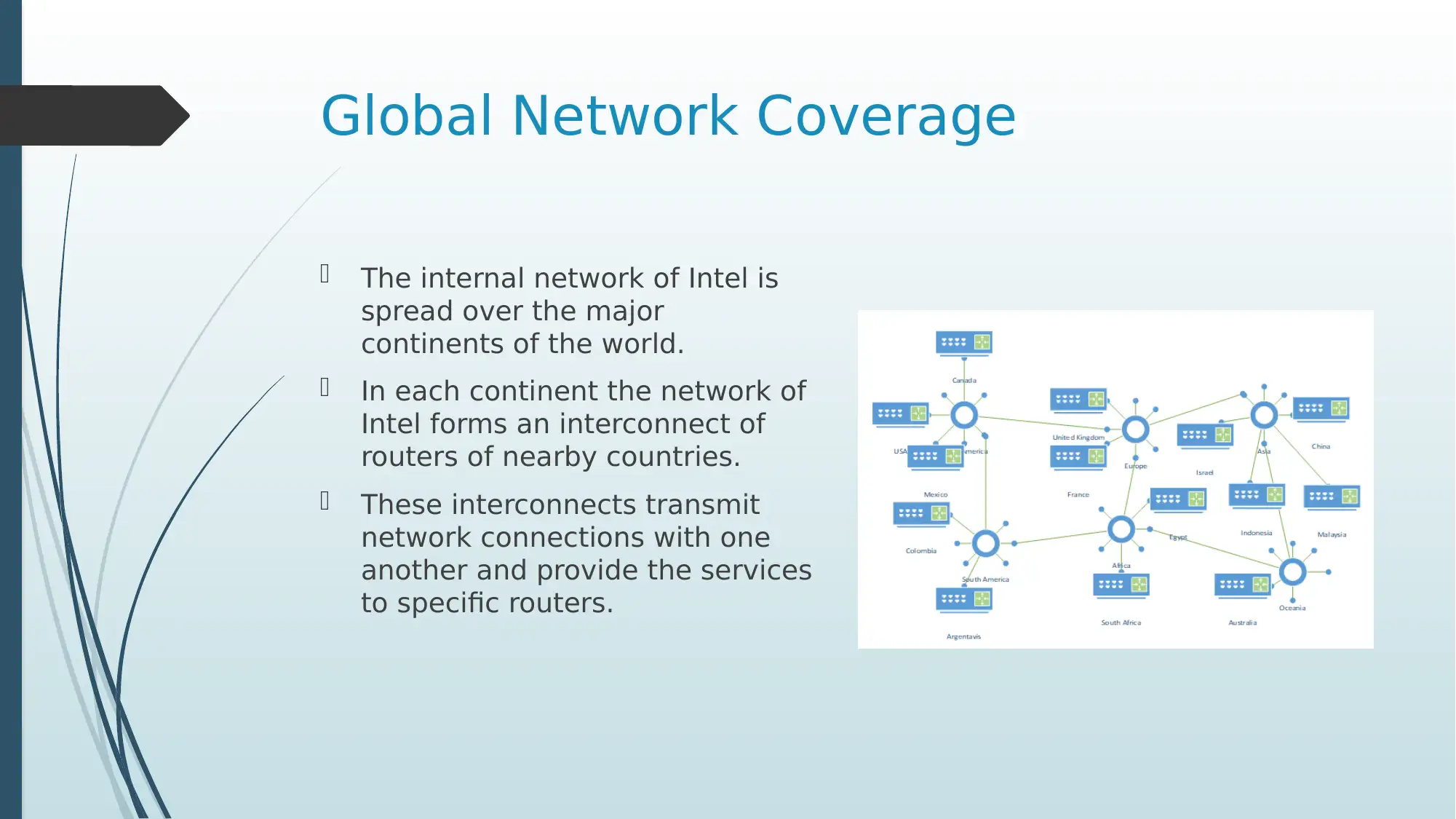
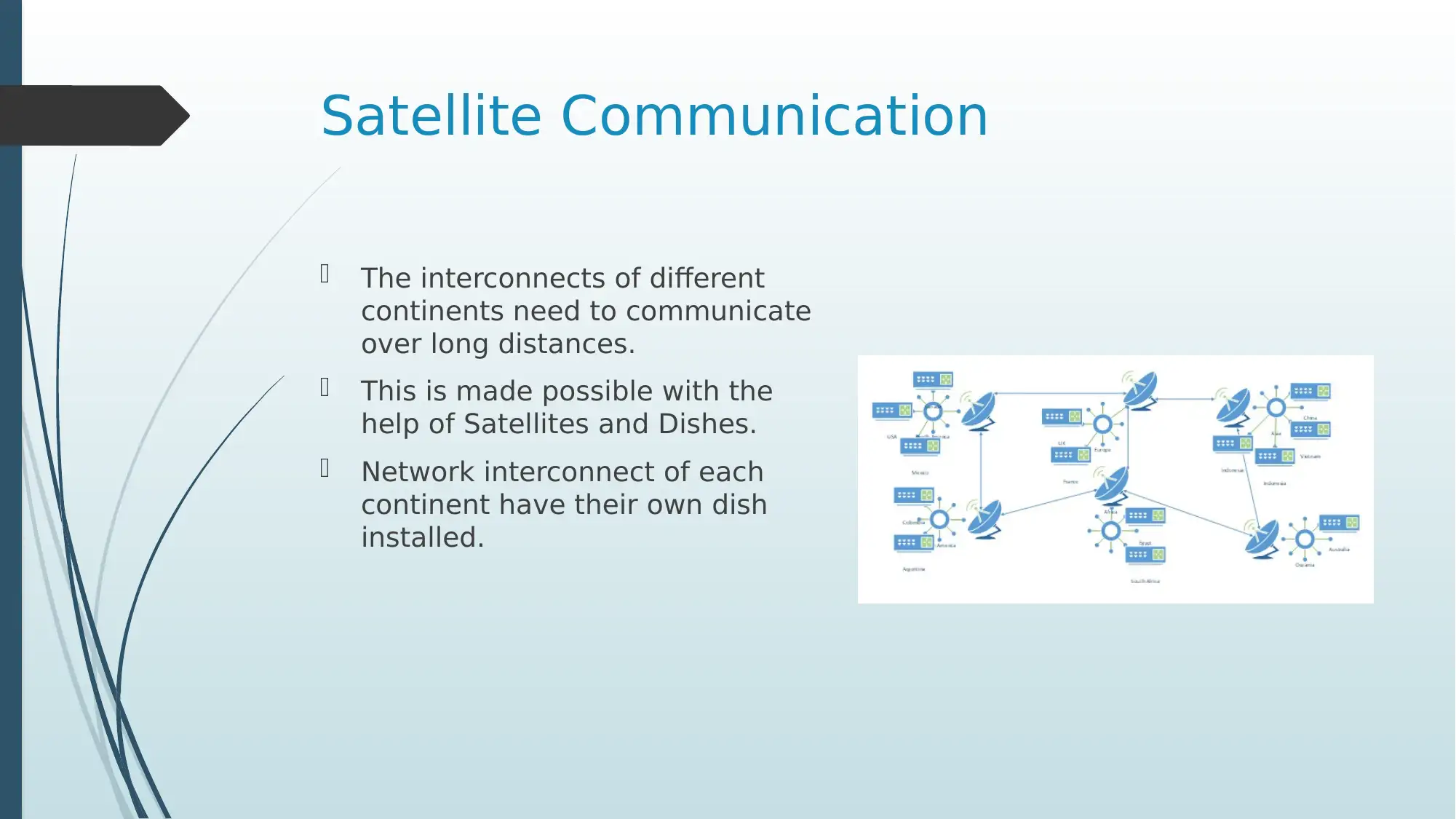
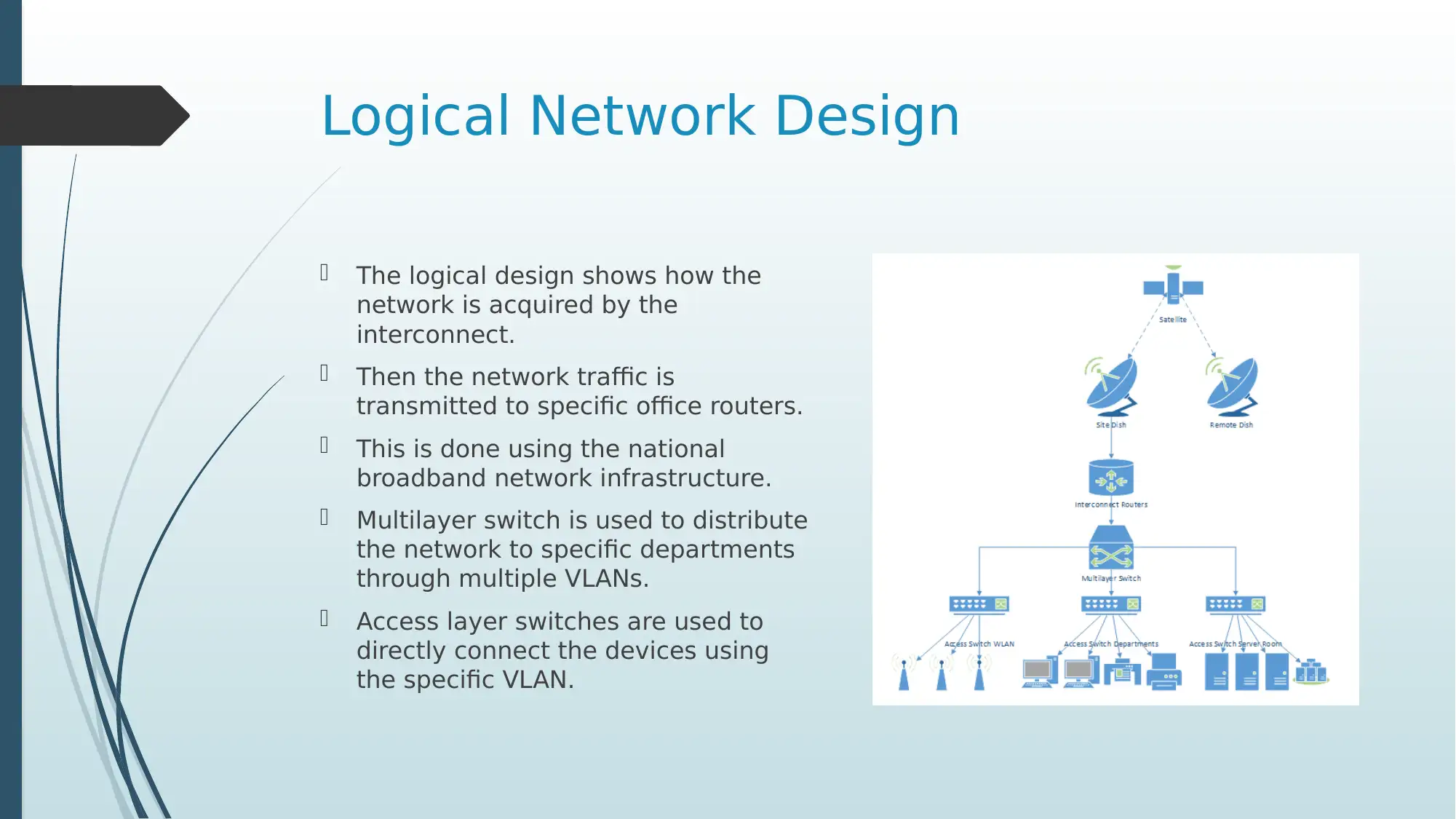
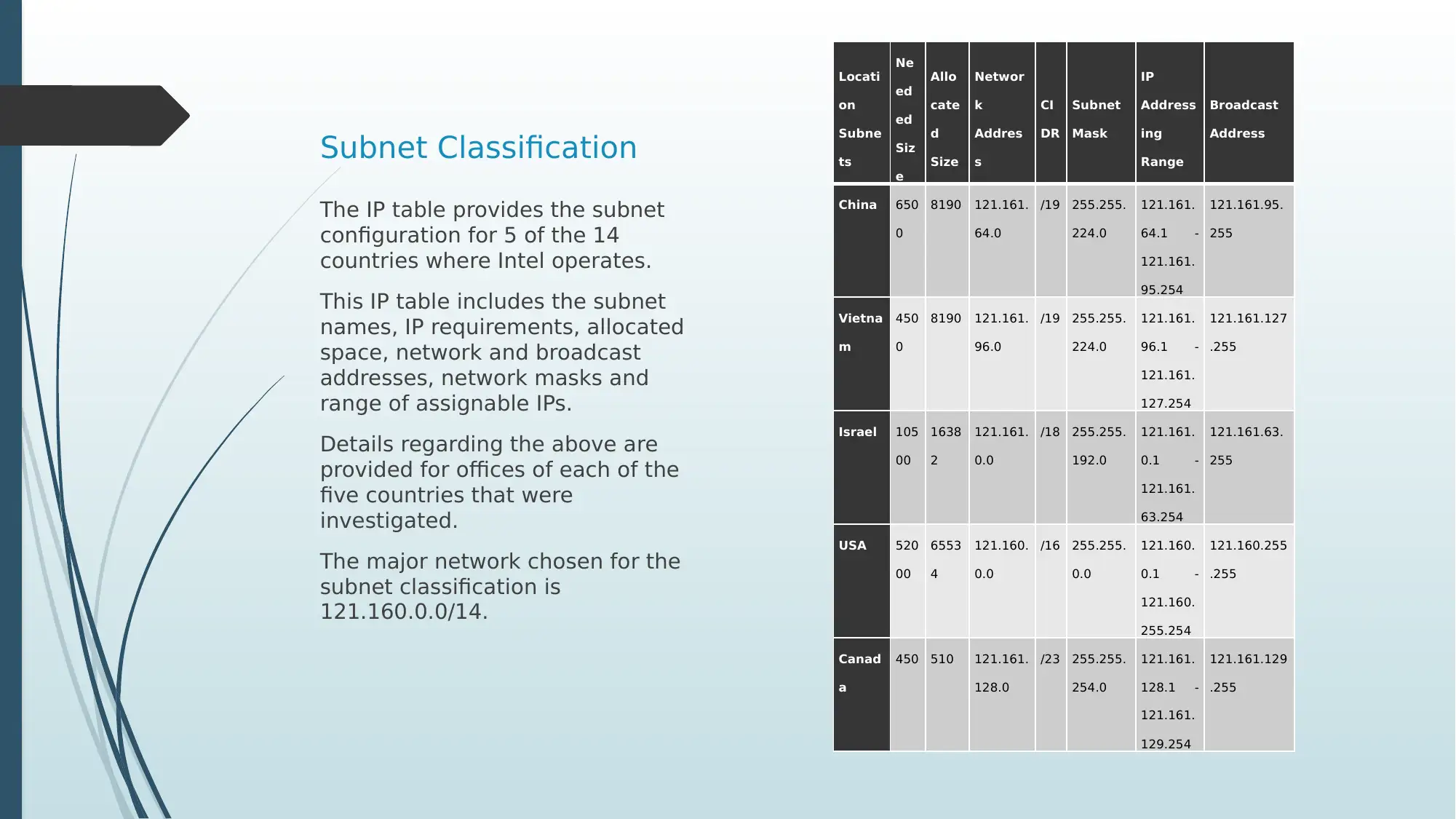
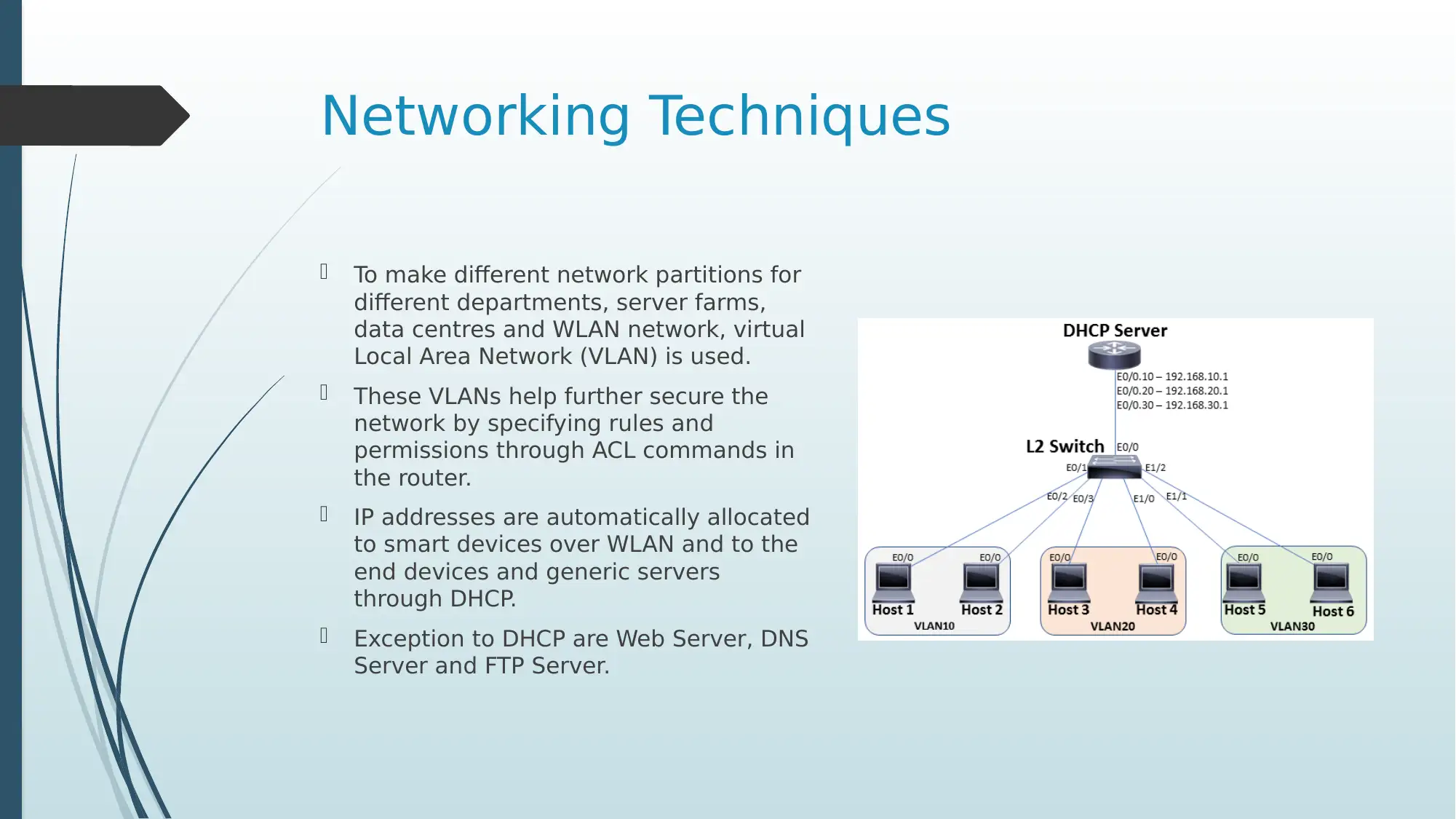
This presentation offers an in-depth investigation of Intel Corporation's network infrastructure. It begins with a business description of Intel, highlighting its global reach and the necessity of robust network communications. The presentation delves into the methods of communication, including the use of advanced features like SDN and NFV for network management. It explores Intel's global network coverage, detailing how different continents connect and transmit data. The logical network design is explained, illustrating how connections are provided to end devices. A crucial aspect is the subnet classification, showcasing how Intel performs IP address allocation, supported by an IP table detailing subnet configurations for five countries. The presentation also covers various networking technologies, including VLANs and DHCP, and concludes with best practices for secure networking, such as using advanced security features and enterprise-class security suites. References to relevant research papers are provided. The presentation aims to give an understanding of how large corporations manage their networking activities.
1 out of 13














![[object Object]](/_next/static/media/star-bottom.7253800d.svg)