System Documentation and Internal Controls Analysis Report
VerifiedAdded on 2020/04/01
|9
|1337
|267
Report
AI Summary
This report examines the system documentation and internal controls of Motherboard and More Pty Ltd., a company producing microchips and motherboards, highlighting challenges in warehouse management and a ransomware attack. The report details the company's revenue cycle, identifies internal control weaknesses, and analyzes the impact of a ransomware attack, including the ransom demands and spread of the attack. It provides solutions such as installing anti-ransomware software, backing up data, and blocking malicious emails. The report recommends improving product record-keeping, implementing a proper database management system, and utilizing RFID technology to enhance warehouse inventory management. The conclusion emphasizes the critical importance of addressing cyberattacks and protecting financial data and assets to maintain confidentiality.

Running head: SYSTEM DOCUMENTATION AND INTERNAL CONTROLS
Systems Documentation and Internal Controls
Name of the Student
Name of the University
Author Note
Systems Documentation and Internal Controls
Name of the Student
Name of the University
Author Note
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1
SYSTEM DOCUMENTATION AND INTERNAL CONTROLS
Executive Summary
This report focuses on Motherboard and More Pty Ltd. that produces microchips, motherboards
and graphic cards. The record of the products in the warehouse has been the main problem faced
by the company. The company is unable to maintaining the warehouse management system. The
details of the ransom ware attack has been shown in the report. There are specific solution ti the
attacks have been provided in the report.
SYSTEM DOCUMENTATION AND INTERNAL CONTROLS
Executive Summary
This report focuses on Motherboard and More Pty Ltd. that produces microchips, motherboards
and graphic cards. The record of the products in the warehouse has been the main problem faced
by the company. The company is unable to maintaining the warehouse management system. The
details of the ransom ware attack has been shown in the report. There are specific solution ti the
attacks have been provided in the report.

2
SYSTEM DOCUMENTATION AND INTERNAL CONTROLS
Table of Contents
Introduction..........................................................................................................................3
Revenue Cycle.....................................................................................................................3
Identification of threats........................................................................................................4
Ransom ware Attack............................................................................................................4
Solutions..............................................................................................................................5
Recommendations................................................................................................................5
Conclusion...........................................................................................................................6
References............................................................................................................................7
SYSTEM DOCUMENTATION AND INTERNAL CONTROLS
Table of Contents
Introduction..........................................................................................................................3
Revenue Cycle.....................................................................................................................3
Identification of threats........................................................................................................4
Ransom ware Attack............................................................................................................4
Solutions..............................................................................................................................5
Recommendations................................................................................................................5
Conclusion...........................................................................................................................6
References............................................................................................................................7
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3
SYSTEM DOCUMENTATION AND INTERNAL CONTROLS
Introduction
The attacks over the internet has been increasing the in the modern world. This has
created a major problem or the business organization in the market. This report deals with
Ransom ware attack have caused huge damage to organization. This report depicts accounting
software system of Motherboard and More Pty Ltd. There are various challenges faced by the
company in market. Some recommendations are provided in report for mitigating with the
challenges.
Revenue Cycle
The revenue system of the company has been essential part. The Motherboard and More
Pty Ltd. Company reduces motherboards, graphics cards and microchips in the market. The
transportation and delivery of the products are done by the company. The headquarter of
company is situated in middle of city and its branches is situated in outskirts of the city.
The interface of websites of company has been friendly to users. This has helped in
maintaining the customer interaction with the website (Dickinson, 2017). The user and customer
have to place an order regarding their needs and requirements over the website. After that, the
order is transferred to the warehouse of the company for further evaluation. The packaging of the
products us done in the warehouse of the company. The products are transported to the
destination after the packaging. The workers in the company delivers the product to the
respective customer. The huge amount of orders in the company makes difficult for the workers
to keep the track of the products in warehouse. Therefore, this has created an issue in the
management of the products in warehouse (Gupta & Tripathi, 2017). The inventory system of
company is well established to handle these issues.
SYSTEM DOCUMENTATION AND INTERNAL CONTROLS
Introduction
The attacks over the internet has been increasing the in the modern world. This has
created a major problem or the business organization in the market. This report deals with
Ransom ware attack have caused huge damage to organization. This report depicts accounting
software system of Motherboard and More Pty Ltd. There are various challenges faced by the
company in market. Some recommendations are provided in report for mitigating with the
challenges.
Revenue Cycle
The revenue system of the company has been essential part. The Motherboard and More
Pty Ltd. Company reduces motherboards, graphics cards and microchips in the market. The
transportation and delivery of the products are done by the company. The headquarter of
company is situated in middle of city and its branches is situated in outskirts of the city.
The interface of websites of company has been friendly to users. This has helped in
maintaining the customer interaction with the website (Dickinson, 2017). The user and customer
have to place an order regarding their needs and requirements over the website. After that, the
order is transferred to the warehouse of the company for further evaluation. The packaging of the
products us done in the warehouse of the company. The products are transported to the
destination after the packaging. The workers in the company delivers the product to the
respective customer. The huge amount of orders in the company makes difficult for the workers
to keep the track of the products in warehouse. Therefore, this has created an issue in the
management of the products in warehouse (Gupta & Tripathi, 2017). The inventory system of
company is well established to handle these issues.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
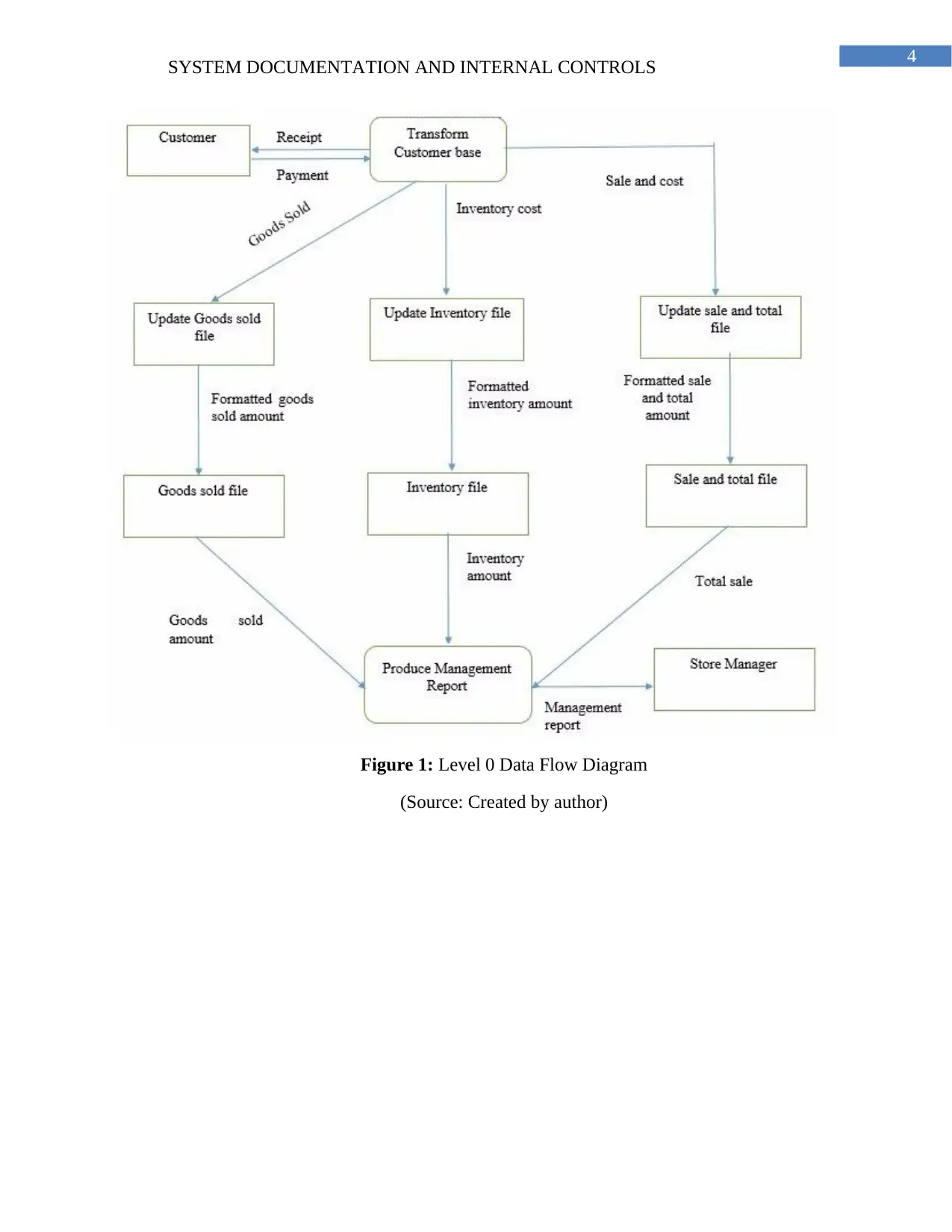
4
SYSTEM DOCUMENTATION AND INTERNAL CONTROLS
Figure 1: Level 0 Data Flow Diagram
(Source: Created by author)
SYSTEM DOCUMENTATION AND INTERNAL CONTROLS
Figure 1: Level 0 Data Flow Diagram
(Source: Created by author)
5
SYSTEM DOCUMENTATION AND INTERNAL CONTROLS
The delivery of the products to the respective customers have satisfied the customer in the
market. The satisfaction level of the customers has been high in respect to the company in the
market.
Identification of threats
The threats and risks in the company has been identified by the research department of
the company. Following are the risks in company:
Internal Control Weaknesses There is no counting for inventory items.
Effect of the Weaknesses The products record is not kept correct that
have caused loss in the products.
Control methods The data and information of products have to
be stored and the database or inventory bf the
company that helps in maintaining record of
products in warehouse. There is a requirement
of a close camera I the warehouse that helps
in monitoring the warehouse properly.
Ransom ware Attack
The ransom ware attacks was initiated in the May 2017 causing damage to many
companies all over the world. Many data and files were hacked and a ransom was asked for
recovering them (Collier, 2017). The hackers used to misuse the data and information of the
company and asked for certain amount of ransom to stop misuse of files and information. The
SYSTEM DOCUMENTATION AND INTERNAL CONTROLS
The delivery of the products to the respective customers have satisfied the customer in the
market. The satisfaction level of the customers has been high in respect to the company in the
market.
Identification of threats
The threats and risks in the company has been identified by the research department of
the company. Following are the risks in company:
Internal Control Weaknesses There is no counting for inventory items.
Effect of the Weaknesses The products record is not kept correct that
have caused loss in the products.
Control methods The data and information of products have to
be stored and the database or inventory bf the
company that helps in maintaining record of
products in warehouse. There is a requirement
of a close camera I the warehouse that helps
in monitoring the warehouse properly.
Ransom ware Attack
The ransom ware attacks was initiated in the May 2017 causing damage to many
companies all over the world. Many data and files were hacked and a ransom was asked for
recovering them (Collier, 2017). The hackers used to misuse the data and information of the
company and asked for certain amount of ransom to stop misuse of files and information. The
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

6
SYSTEM DOCUMENTATION AND INTERNAL CONTROLS
underlying ransom was asked US$300. This sum was increased after few hours. The attacks
spread from one system to another system with the help of viruses and malwares over the
internet (Mohurle & Patil, 2017). The security gaps in the protocol of the networks of the
companies have helped in the attacks. After the attack, Microsoft declared that they are preparing
fundamental patches that helps in mitigating with the viruses. The users used to update the
windows frequently that causes obsolete for the other windows version. Most of the users were
updating their windows version in order to be safe from the ransom ware attack (Martin, Kinross
& Hankin, 2017). There are has been many attacks in the hospitals of England. According to a
survey, there were $57,000 ransom were collected from 99 countries all over the world.
Solutions
The severity of the ransom ware attacks has given rise to various solutions to the
challenges faced by the business organizations. The best way to remain safe from the ransom
ware attack is by installing an antivirus of ransom ware virus (Chinthapalli, 2017). This antivirus
helps in preventing the system and network from the ransom ware attack in the business
organization. This antivirus helps in locating the information about the place of the attacker.
Therefore, the user can back up the data and information on other external devices. Backing up
data helps in recovering the lost data and information due to cyber-attacks (Collier, 2017). They
used to email various malwares and viruses that causes data breach form the email account if the
user. Therefore, blockage of such emails is necessary for remaining safe from the ransom ware
attacks.
Recommendations
It can be recommended that the Motherboard and More Pty Ltd. have to focus on keeping
the record of the products in the warehouse. This helps in minimizing the loss of products in the
SYSTEM DOCUMENTATION AND INTERNAL CONTROLS
underlying ransom was asked US$300. This sum was increased after few hours. The attacks
spread from one system to another system with the help of viruses and malwares over the
internet (Mohurle & Patil, 2017). The security gaps in the protocol of the networks of the
companies have helped in the attacks. After the attack, Microsoft declared that they are preparing
fundamental patches that helps in mitigating with the viruses. The users used to update the
windows frequently that causes obsolete for the other windows version. Most of the users were
updating their windows version in order to be safe from the ransom ware attack (Martin, Kinross
& Hankin, 2017). There are has been many attacks in the hospitals of England. According to a
survey, there were $57,000 ransom were collected from 99 countries all over the world.
Solutions
The severity of the ransom ware attacks has given rise to various solutions to the
challenges faced by the business organizations. The best way to remain safe from the ransom
ware attack is by installing an antivirus of ransom ware virus (Chinthapalli, 2017). This antivirus
helps in preventing the system and network from the ransom ware attack in the business
organization. This antivirus helps in locating the information about the place of the attacker.
Therefore, the user can back up the data and information on other external devices. Backing up
data helps in recovering the lost data and information due to cyber-attacks (Collier, 2017). They
used to email various malwares and viruses that causes data breach form the email account if the
user. Therefore, blockage of such emails is necessary for remaining safe from the ransom ware
attacks.
Recommendations
It can be recommended that the Motherboard and More Pty Ltd. have to focus on keeping
the record of the products in the warehouse. This helps in minimizing the loss of products in the
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7
SYSTEM DOCUMENTATION AND INTERNAL CONTROLS
company. A proper database management is required in the company that hekpsn in maintaining
the details of the products in the warehouse. The company have to use RFID that helps in
digitalizing the product in the warehouse. With the use of the RFID, the workers can keep close
look in the products and monitors its location in the warehouse. Thus might help in minimizing
the risk of the loss of products in warehouse.
Conclusion
In conclusion, it is said that the cyber-attacks over organization have caused critical loss
to the companies in the market. The loss of financial data and assets have damaged
confidentiality of companies in the market. The case study of Motherboard and More Pty Ltd.
have focused on challenges faced by company in managing products in warehouse. There are
recommendations provided for resolving issues in company.
SYSTEM DOCUMENTATION AND INTERNAL CONTROLS
company. A proper database management is required in the company that hekpsn in maintaining
the details of the products in the warehouse. The company have to use RFID that helps in
digitalizing the product in the warehouse. With the use of the RFID, the workers can keep close
look in the products and monitors its location in the warehouse. Thus might help in minimizing
the risk of the loss of products in warehouse.
Conclusion
In conclusion, it is said that the cyber-attacks over organization have caused critical loss
to the companies in the market. The loss of financial data and assets have damaged
confidentiality of companies in the market. The case study of Motherboard and More Pty Ltd.
have focused on challenges faced by company in managing products in warehouse. There are
recommendations provided for resolving issues in company.

8
SYSTEM DOCUMENTATION AND INTERNAL CONTROLS
References
Chinthapalli, K. (2017). The hackers holding hospitals to ransom. BMJ, 357, j2214.
Collier, R. (2017). NHS ransomware attack spreads worldwide.
Dickinson, D. (2017). Cybersecurity: Going Beyond Protection to Boost Resiliency.
Gupta, G., & Tripathi, K. (2017). STUDY ON RANSOMWARE ATTACK AND ITS
PREVENTION. International Education and Research Journal, 3(5).
Martin, G., Kinross, J., & Hankin, C. (2017). Effective cybersecurity is fundamental to patient
safety.
Mohurle, S., & Patil, M. (2017). A brief study of Wannacry Threat: Ransomware Attack
2017. International Journal, 8(5).
Sittig, D. F., & Singh, H. (2016). A socio-technical approach to preventing, mitigating, and
recovering from ransomware attacks. Applied clinical informatics, 7(2), 624.
SYSTEM DOCUMENTATION AND INTERNAL CONTROLS
References
Chinthapalli, K. (2017). The hackers holding hospitals to ransom. BMJ, 357, j2214.
Collier, R. (2017). NHS ransomware attack spreads worldwide.
Dickinson, D. (2017). Cybersecurity: Going Beyond Protection to Boost Resiliency.
Gupta, G., & Tripathi, K. (2017). STUDY ON RANSOMWARE ATTACK AND ITS
PREVENTION. International Education and Research Journal, 3(5).
Martin, G., Kinross, J., & Hankin, C. (2017). Effective cybersecurity is fundamental to patient
safety.
Mohurle, S., & Patil, M. (2017). A brief study of Wannacry Threat: Ransomware Attack
2017. International Journal, 8(5).
Sittig, D. F., & Singh, H. (2016). A socio-technical approach to preventing, mitigating, and
recovering from ransomware attacks. Applied clinical informatics, 7(2), 624.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 9
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





