Individual Report: Internet Impact, Threats, and Unified Communication
VerifiedAdded on 2021/02/20
|15
|3746
|21
Report
AI Summary
This individual report provides a comprehensive analysis of the internet's impact on both business and society. It begins by exploring the positive aspects, such as enhanced communication, advertising opportunities, and access to information, while also addressing the negative consequences, including cybercrime, information theft, and addiction. The report then delves into the various threats faced by organizations and society, including cybercrime syndicates, hacktivists, corporate espionage, and malware. It identifies the vulnerabilities associated with the Internet of Things (IoT) and human factors. The report also outlines essential security measures, such as using preventative software, avoiding unreliable websites, and employing strong passwords. Finally, the report examines unified communication providers, comparing their features and suitability for business applications, providing a well-rounded view of the internet's role in the modern world.

Individual Report
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Table of Contents
INTRODUCTION...........................................................................................................................1
ASSESSMENT................................................................................................................................1
1) Positive and negative use of internet in an Business and society...........................................1
2)Threat faced by organisation and society using internet and measure security taken when
used online. .................................................................................................................................3
Ray, 2018)........................................................................................................................................4
3) Defferent unified communication providers compare and contrast features and suitability
for business .................................................................................................................................6
CONCLUSION...............................................................................................................................8
REFERENCES................................................................................................................................9
INTRODUCTION...........................................................................................................................1
ASSESSMENT................................................................................................................................1
1) Positive and negative use of internet in an Business and society...........................................1
2)Threat faced by organisation and society using internet and measure security taken when
used online. .................................................................................................................................3
Ray, 2018)........................................................................................................................................4
3) Defferent unified communication providers compare and contrast features and suitability
for business .................................................................................................................................6
CONCLUSION...............................................................................................................................8
REFERENCES................................................................................................................................9

INTRODUCTION
Internet is an computer global network which provide different variety of information
and facilities in communication . Every single information is available on internet. this report
will cover compare and contrast the positive and negative use of an internet to the business and
society. then this report will discuses the threats faced by both organization and society, it will
identify the measure of society and privacy which should be then when internet application or
services are used online and this report will also use two different unified communication
provider then they will compare their features and discussing their suitability in the business.
ASSESSMENT
1) Positive and negative use of internet in an Business and society
There are many positive impact of internet in organization and society both because it can
help them to get any information, trend by using internet but Now a day many organization use
this internet for negative use -
Positive use of internet in Business and society
communication is the primary uses of the internet in society as well as organization. In
organization email allows employees to quickly communicate with each other through email and
messages. Email help to save printing cost of the documents and physical papers . organization
also conduct meeting by using videos from internet. They can advertise their product on internet
and they can get a good result which will help them to growth in their business. They can
increase there product reach to all over the world. Internet is impotent in business to
communicate with their customers about their product and services. It gives a chance to small
organization to take advantages of online advertising which will be less costly for small
organizations(Evren, C 2019.). Business research is to much important to get the all data related
to target markets, target customers a and information about the competitors in a market for this
all internet is cheapest analyze the data and collect information so they can create their product
according to demand of the customers and they can compete with their other competitor in the
market. Organization can also sell their product on the internet by making online sites ,
commerce websites are less costly as compare to physical stores. Internet is very important and
useful tool for internet because they can search any information by using search engine on the
internet. they can also talk and connect with the person who are far away from them, social
networking sites help them to send their messages to all over the world. It is cheapest and best
1
Internet is an computer global network which provide different variety of information
and facilities in communication . Every single information is available on internet. this report
will cover compare and contrast the positive and negative use of an internet to the business and
society. then this report will discuses the threats faced by both organization and society, it will
identify the measure of society and privacy which should be then when internet application or
services are used online and this report will also use two different unified communication
provider then they will compare their features and discussing their suitability in the business.
ASSESSMENT
1) Positive and negative use of internet in an Business and society
There are many positive impact of internet in organization and society both because it can
help them to get any information, trend by using internet but Now a day many organization use
this internet for negative use -
Positive use of internet in Business and society
communication is the primary uses of the internet in society as well as organization. In
organization email allows employees to quickly communicate with each other through email and
messages. Email help to save printing cost of the documents and physical papers . organization
also conduct meeting by using videos from internet. They can advertise their product on internet
and they can get a good result which will help them to growth in their business. They can
increase there product reach to all over the world. Internet is impotent in business to
communicate with their customers about their product and services. It gives a chance to small
organization to take advantages of online advertising which will be less costly for small
organizations(Evren, C 2019.). Business research is to much important to get the all data related
to target markets, target customers a and information about the competitors in a market for this
all internet is cheapest analyze the data and collect information so they can create their product
according to demand of the customers and they can compete with their other competitor in the
market. Organization can also sell their product on the internet by making online sites ,
commerce websites are less costly as compare to physical stores. Internet is very important and
useful tool for internet because they can search any information by using search engine on the
internet. they can also talk and connect with the person who are far away from them, social
networking sites help them to send their messages to all over the world. It is cheapest and best
1
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

ways to connect with others , people can use many facilities like shopping , busying any product
this all are they can do on internet there are many e-commerce sides and online store are
available on internet they do not need to go anywhere they can purchase anything from the
internet. They can also start their own business by using internet they can make website and
give all the information related to their business and this is cheapest way to start business for
people(.Joshi, SC and Rose G 2018). They can search data relation to their product and advertise
their product on the internet , internet is best way of self entertainment thy can see movies and
videos for their entertainment. Other sources like books , news reports are also available on the
internet people can read books and see the news by using internet.
Negative use of internet in Business and society
Internet is an very important any best tool until someone do not use this tool in a wrong
way there many organization and many people who use internet in a wrong way to earn more
money steal information
Cyber crime - There are many company who use internet in wrong way they don't care
about there reputation and some of them are fraud , they show that their products are original and
sent duplicate product to the customers and they do not return their money to the customers it
affect on the society they cannot believe on other trusty online sides(Škařupová, K 2015). That is
the reason customers prefer offline shopping more then the online e commerce sides . This all are
comes under the cyber crimes.
Stilling Information - Many organization use internet to steal information of the other
organizations by hacking. it is a wrong use of internet services, they also still their formulas so
they can make same product like them and increase their profitability(Lin, MP Ko H C and Wu J Y
W 2008). Youngster also use internet to leak exams papers so they can pass in their exam without
studying for exam
Email Fraud - People do fraud by email internet services they send emails messages to
the others then they tell them they won money in lottery then they ask for account number and
all bank details then they takeout all the money from their account( Soeters, K E 2001). Over use
of internet is can also create problem, this business for those people.
Addiction of internet – online gaming business create addiction for the teenagers
because teenagers give their most of the time playing games and they cannot concentrate ,
2
this all are they can do on internet there are many e-commerce sides and online store are
available on internet they do not need to go anywhere they can purchase anything from the
internet. They can also start their own business by using internet they can make website and
give all the information related to their business and this is cheapest way to start business for
people(.Joshi, SC and Rose G 2018). They can search data relation to their product and advertise
their product on the internet , internet is best way of self entertainment thy can see movies and
videos for their entertainment. Other sources like books , news reports are also available on the
internet people can read books and see the news by using internet.
Negative use of internet in Business and society
Internet is an very important any best tool until someone do not use this tool in a wrong
way there many organization and many people who use internet in a wrong way to earn more
money steal information
Cyber crime - There are many company who use internet in wrong way they don't care
about there reputation and some of them are fraud , they show that their products are original and
sent duplicate product to the customers and they do not return their money to the customers it
affect on the society they cannot believe on other trusty online sides(Škařupová, K 2015). That is
the reason customers prefer offline shopping more then the online e commerce sides . This all are
comes under the cyber crimes.
Stilling Information - Many organization use internet to steal information of the other
organizations by hacking. it is a wrong use of internet services, they also still their formulas so
they can make same product like them and increase their profitability(Lin, MP Ko H C and Wu J Y
W 2008). Youngster also use internet to leak exams papers so they can pass in their exam without
studying for exam
Email Fraud - People do fraud by email internet services they send emails messages to
the others then they tell them they won money in lottery then they ask for account number and
all bank details then they takeout all the money from their account( Soeters, K E 2001). Over use
of internet is can also create problem, this business for those people.
Addiction of internet – online gaming business create addiction for the teenagers
because teenagers give their most of the time playing games and they cannot concentrate ,
2
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

children spend their time in front of the commuter to playing games(Gatto and Tak 2008).
Companies get profit by make games for them but teenagers are getting addiction from this all.
Prohibited product advertising – There are some e commerce sites who sell product
which is illegal products and that all can harm to health. They sell this products so they can earn
more profits this is easy way to earn money by using internet and it can directly impact on the
society(Evren, 2019). They use social media platforms like Facebook, Instagram and tweeter
because their main targets are teenagers and youngster and this all social media sides allow this
type sides to sell their product. They can sell their products without any restrictions and this
prohibited product addict the teenagers and this side do not take any strict decisions to band this
side who are promoting and selling prohibited products.
2)Threat faced by organisation and society using internet and measure security taken when used
online.
Their are several threats of using the internet
Cyber crime syndicates
Today criminal mastermind are still their. Still many of an malicious of hacking attacks
are their because of an firm group. As many of professional people are including in it. Where as
traditional firm organise an crime team that use to run an gambeling. Proceusution , drugs and
extoeation are throe an hates to the ineline funds. Where lot of trop firm cyber crime syndicates
because that leads to more affilitate conglomerate group and small group still hacked. Still more
IT security prons that are against large corporation that dedicate to rogue behavioe (Poushter,
2016).
Small time cons- & funds launders and mules supporting-
As all the cyber criminal industries are not an syndicates. Some are simple
entrepreneurial in nature
This malicious pop-and mom operation still identify the password or it cause nefarious
redirection As in final they wand fund. They initialy fraudulent banking transaction and try to
convert ill-gotten gains to local currency by using fund mules, e-banking, electronic cash
distribution and some another sort of the money laundering (Murdock and Williams, 2017).
Hacktivists
Today cyber crime are seeks to fly under an radar with an exception of growing legions
hacktivists. IT security pros that have to content an raising number of the loose confederations of
3
Companies get profit by make games for them but teenagers are getting addiction from this all.
Prohibited product advertising – There are some e commerce sites who sell product
which is illegal products and that all can harm to health. They sell this products so they can earn
more profits this is easy way to earn money by using internet and it can directly impact on the
society(Evren, 2019). They use social media platforms like Facebook, Instagram and tweeter
because their main targets are teenagers and youngster and this all social media sides allow this
type sides to sell their product. They can sell their products without any restrictions and this
prohibited product addict the teenagers and this side do not take any strict decisions to band this
side who are promoting and selling prohibited products.
2)Threat faced by organisation and society using internet and measure security taken when used
online.
Their are several threats of using the internet
Cyber crime syndicates
Today criminal mastermind are still their. Still many of an malicious of hacking attacks
are their because of an firm group. As many of professional people are including in it. Where as
traditional firm organise an crime team that use to run an gambeling. Proceusution , drugs and
extoeation are throe an hates to the ineline funds. Where lot of trop firm cyber crime syndicates
because that leads to more affilitate conglomerate group and small group still hacked. Still more
IT security prons that are against large corporation that dedicate to rogue behavioe (Poushter,
2016).
Small time cons- & funds launders and mules supporting-
As all the cyber criminal industries are not an syndicates. Some are simple
entrepreneurial in nature
This malicious pop-and mom operation still identify the password or it cause nefarious
redirection As in final they wand fund. They initialy fraudulent banking transaction and try to
convert ill-gotten gains to local currency by using fund mules, e-banking, electronic cash
distribution and some another sort of the money laundering (Murdock and Williams, 2017).
Hacktivists
Today cyber crime are seeks to fly under an radar with an exception of growing legions
hacktivists. IT security pros that have to content an raising number of the loose confederations of
3

individual that dedicated to an political activity like an infamous group. Since the hacking was
existed from first born politically motivated the hackers. Where big changes more of done in
open society are acknowledge as an accepted from political activism. As Political hacking gather
more no. of members that take grievances to an media drum up for the public support and act as
astonished and if they arrested for illegal deeds. It try to imbarrass and that will bring negative
media attention towards victim or causing simply victim firm additional strife. Where political
hacktivism mostly causing money pain to victim and attempt to change victim behaviour (Alaba,
Othman, Hashem and Alotaibi, 2017).
Corporate espionage and Intellectual property theft
Many of IT security have to be content with large group of hackers that may steal
intellectual property by the industries. This way to break an IT firm assets where it dump all
paeewirds over time. Steal gigabytes for an confidential information such as- new products ideas
patents, military secrets, business plans, financial information etc. valuable information passes to
customer foe an stay hidden compromised and financial gain. firm's channel as long as possible.
To reap reward they eavesdrop essential information and gain access of information to begun or
develop their malicious searches and issue tools that seperate fodder from interesting intellectual
property (Ray, 2018).
Malware mercenaries
Today many industries and group are dedicated solely for writing malware foe an particular
security defences , that attack particular buyers and try to accomplish particular objectives and
sold in open market bidding forums. Often malware componentized and multiphased. Small
program tasked, where once placed securely to make ensure that lives through reboot, where
contacts “mothership” web server to an further instructions (Razzaque and et.al., 2015).
Threats to society
As approches of more interconnected society with an more smart object. More risk also
increased and the vulnerability need to be detected & correct multiply. Internet of things (IOT) is
an technological breakthrough completely revolution to our daily life.
Challenge for data privacy
Internet that represents storage of things, analyses mechanism, data collection that higher
an scale. As more devise connected to the internet, than more elements are require for the
4
existed from first born politically motivated the hackers. Where big changes more of done in
open society are acknowledge as an accepted from political activism. As Political hacking gather
more no. of members that take grievances to an media drum up for the public support and act as
astonished and if they arrested for illegal deeds. It try to imbarrass and that will bring negative
media attention towards victim or causing simply victim firm additional strife. Where political
hacktivism mostly causing money pain to victim and attempt to change victim behaviour (Alaba,
Othman, Hashem and Alotaibi, 2017).
Corporate espionage and Intellectual property theft
Many of IT security have to be content with large group of hackers that may steal
intellectual property by the industries. This way to break an IT firm assets where it dump all
paeewirds over time. Steal gigabytes for an confidential information such as- new products ideas
patents, military secrets, business plans, financial information etc. valuable information passes to
customer foe an stay hidden compromised and financial gain. firm's channel as long as possible.
To reap reward they eavesdrop essential information and gain access of information to begun or
develop their malicious searches and issue tools that seperate fodder from interesting intellectual
property (Ray, 2018).
Malware mercenaries
Today many industries and group are dedicated solely for writing malware foe an particular
security defences , that attack particular buyers and try to accomplish particular objectives and
sold in open market bidding forums. Often malware componentized and multiphased. Small
program tasked, where once placed securely to make ensure that lives through reboot, where
contacts “mothership” web server to an further instructions (Razzaque and et.al., 2015).
Threats to society
As approches of more interconnected society with an more smart object. More risk also
increased and the vulnerability need to be detected & correct multiply. Internet of things (IOT) is
an technological breakthrough completely revolution to our daily life.
Challenge for data privacy
Internet that represents storage of things, analyses mechanism, data collection that higher
an scale. As more devise connected to the internet, than more elements are require for the
4
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

protection. It is challenges to keep the data more privacy; the device itself, the application or the
platform that uses, network (Madakam, Ramaswamy and Tripathi, 2015).
Human factors
The IOT relatively new technological advance and the egnorance of IOT security. Both
of the industries and the individual users is not possible. It also raise the risk of cybersecurity
because of less experience in IT and in human factors.
Data encryption
As transmission of an data from the non-encryted that means present an major security
issues. Also considered the essential from the network security. As the IOT is generally focus on
the mobile device foe an various kinds and the predominantly wireless channels.
Complex system
More device, interaction, people and interfaces than the risk of data or information
security also raise. It shoes diversity and variety in system, So to manage the challenges in
network to be maximize for more security and also raises to get prevent from such security risk
(Whitmore, Agarwal and Da Xu, 2015).
Measures for Internet privacy and security for both industry and society.
It refers to various factors, technologies and techivs that can be used to protect private
and sensitive data, prefernces and communication for both industries and the society. Such
violation and threats may be minimized by several ways. Always use an preventative software
application such as anti-malware, anti-virus, firewalls and anti-spam. My using such application
it helps the user to keep its data more secure and it prevent from threats by keep on update the
application time to time. Avoid shopping on unreliable websites, people should use proper
website instead of using unreliable website to get rid from the threats and risk, and for more
proper security. Always use very strong password that consist of numbers, letters and special
characters. It can be use to minimize the risk of threats And also try to avoid the sharing of
personal data or information through the website with the lower security levels. Try to use proper
security level while sharing an essential data to the other person or client (Jeschke and et.al.,
2017).
5
platform that uses, network (Madakam, Ramaswamy and Tripathi, 2015).
Human factors
The IOT relatively new technological advance and the egnorance of IOT security. Both
of the industries and the individual users is not possible. It also raise the risk of cybersecurity
because of less experience in IT and in human factors.
Data encryption
As transmission of an data from the non-encryted that means present an major security
issues. Also considered the essential from the network security. As the IOT is generally focus on
the mobile device foe an various kinds and the predominantly wireless channels.
Complex system
More device, interaction, people and interfaces than the risk of data or information
security also raise. It shoes diversity and variety in system, So to manage the challenges in
network to be maximize for more security and also raises to get prevent from such security risk
(Whitmore, Agarwal and Da Xu, 2015).
Measures for Internet privacy and security for both industry and society.
It refers to various factors, technologies and techivs that can be used to protect private
and sensitive data, prefernces and communication for both industries and the society. Such
violation and threats may be minimized by several ways. Always use an preventative software
application such as anti-malware, anti-virus, firewalls and anti-spam. My using such application
it helps the user to keep its data more secure and it prevent from threats by keep on update the
application time to time. Avoid shopping on unreliable websites, people should use proper
website instead of using unreliable website to get rid from the threats and risk, and for more
proper security. Always use very strong password that consist of numbers, letters and special
characters. It can be use to minimize the risk of threats And also try to avoid the sharing of
personal data or information through the website with the lower security levels. Try to use proper
security level while sharing an essential data to the other person or client (Jeschke and et.al.,
2017).
5
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
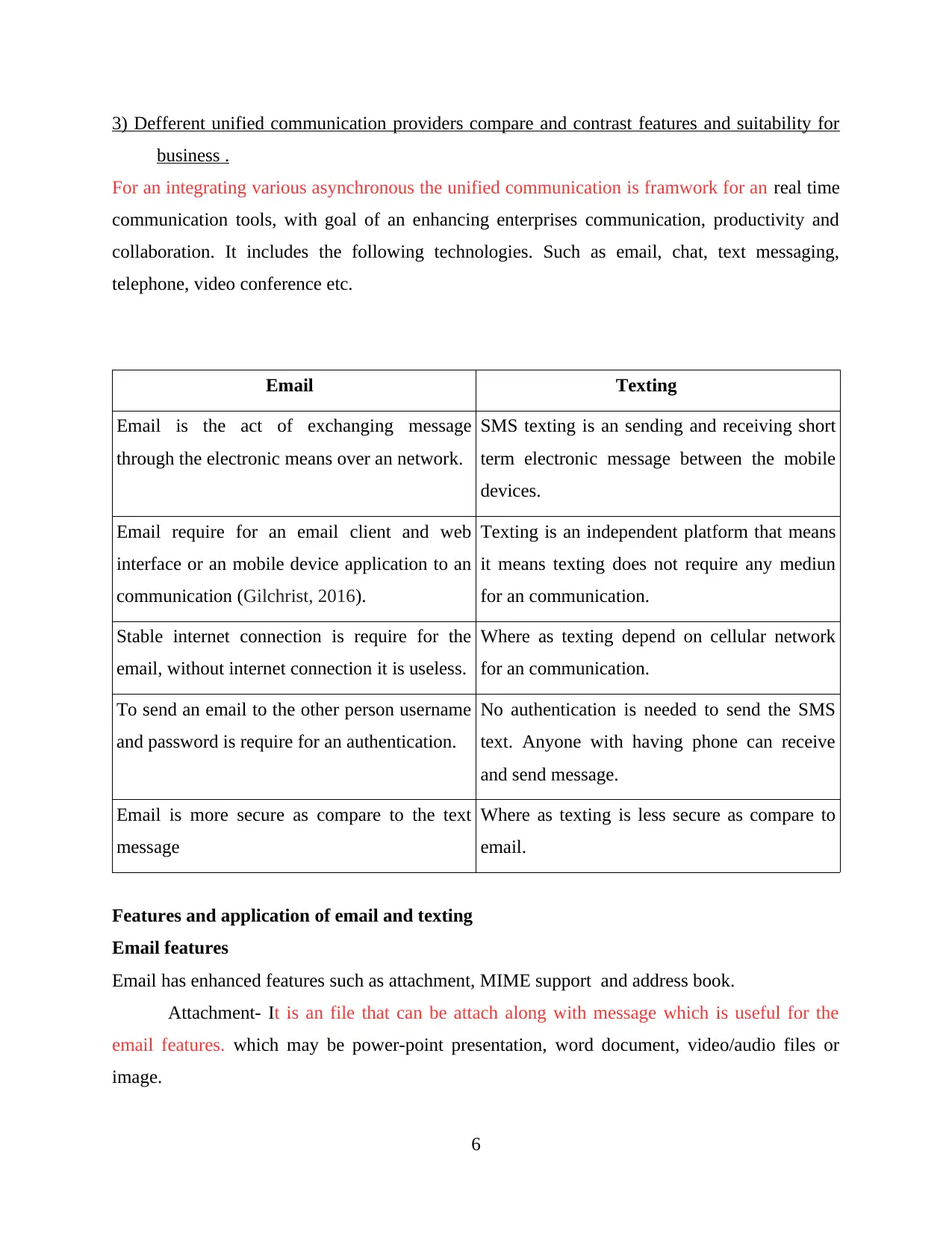
3) Defferent unified communication providers compare and contrast features and suitability for
business .
For an integrating various asynchronous the unified communication is framwork for an real time
communication tools, with goal of an enhancing enterprises communication, productivity and
collaboration. It includes the following technologies. Such as email, chat, text messaging,
telephone, video conference etc.
Email Texting
Email is the act of exchanging message
through the electronic means over an network.
SMS texting is an sending and receiving short
term electronic message between the mobile
devices.
Email require for an email client and web
interface or an mobile device application to an
communication (Gilchrist, 2016).
Texting is an independent platform that means
it means texting does not require any mediun
for an communication.
Stable internet connection is require for the
email, without internet connection it is useless.
Where as texting depend on cellular network
for an communication.
To send an email to the other person username
and password is require for an authentication.
No authentication is needed to send the SMS
text. Anyone with having phone can receive
and send message.
Email is more secure as compare to the text
message
Where as texting is less secure as compare to
email.
Features and application of email and texting
Email features
Email has enhanced features such as attachment, MIME support and address book.
Attachment- It is an file that can be attach along with message which is useful for the
email features. which may be power-point presentation, word document, video/audio files or
image.
6
business .
For an integrating various asynchronous the unified communication is framwork for an real time
communication tools, with goal of an enhancing enterprises communication, productivity and
collaboration. It includes the following technologies. Such as email, chat, text messaging,
telephone, video conference etc.
Email Texting
Email is the act of exchanging message
through the electronic means over an network.
SMS texting is an sending and receiving short
term electronic message between the mobile
devices.
Email require for an email client and web
interface or an mobile device application to an
communication (Gilchrist, 2016).
Texting is an independent platform that means
it means texting does not require any mediun
for an communication.
Stable internet connection is require for the
email, without internet connection it is useless.
Where as texting depend on cellular network
for an communication.
To send an email to the other person username
and password is require for an authentication.
No authentication is needed to send the SMS
text. Anyone with having phone can receive
and send message.
Email is more secure as compare to the text
message
Where as texting is less secure as compare to
email.
Features and application of email and texting
Email features
Email has enhanced features such as attachment, MIME support and address book.
Attachment- It is an file that can be attach along with message which is useful for the
email features. which may be power-point presentation, word document, video/audio files or
image.
6

Address Book- It is an another mail program features that allows users to store an
information about an people whom they want to communicate regularly by sending an email.
Here some key features of address books are. Nick name, phone number, email address etc. of
the people. It helps to memorize email of address for an people. It make the work easier. While
select the name from the list (Sethi and Sarangi, 2017).
Email Application
Their are several email client that are specially chosen because of each application have unique
featurs such as Thunderbird, Window mail, thunderbird etc.
Thunderbird- this is one of the best email client for browser experience. It is an open way
that means there's is an large community support for adding features, like an ability to search for
an web that is right from the app. Of an cource, openly source or way add-ons aren't subject for
an usability requirement, So that it can need to use discrition while selecting the once use
(Akyildiz and et.al., 2015).
Mailbird- Mailbird is lack in text on page. It's all about its icons. Where imagine without
text label, that can see. It can be customized for more conventional and even it can tweak the
look of application with some of the flashy templates. It integrates with an 50 application and
services, because of which makes it great choice for users that live in the inbox (Rose, Eldridge
and Chapin, 2015).
Texting features
Send group Broadcasts- Here create many different group as you would like to choose the
name and merge the message and templates & than send an message to direct group of more than
100 contact at the time or message to an personalize text.
Convert into one to one conversation- As the text message reposes that can begin
“popping up”in the TextUs web portal that opening the door to an dozens of an personal, and one
to conversatiins (Poushter, 2016).
Safe and secure and cell notification- while sending text message put an mind at rest
because all messages are encrypted and has to be saved securely in the cloud. So it is an more
secure and safe. And also get an notification when reaches in smartphone, tablets or computers.
Texting applications
7
information about an people whom they want to communicate regularly by sending an email.
Here some key features of address books are. Nick name, phone number, email address etc. of
the people. It helps to memorize email of address for an people. It make the work easier. While
select the name from the list (Sethi and Sarangi, 2017).
Email Application
Their are several email client that are specially chosen because of each application have unique
featurs such as Thunderbird, Window mail, thunderbird etc.
Thunderbird- this is one of the best email client for browser experience. It is an open way
that means there's is an large community support for adding features, like an ability to search for
an web that is right from the app. Of an cource, openly source or way add-ons aren't subject for
an usability requirement, So that it can need to use discrition while selecting the once use
(Akyildiz and et.al., 2015).
Mailbird- Mailbird is lack in text on page. It's all about its icons. Where imagine without
text label, that can see. It can be customized for more conventional and even it can tweak the
look of application with some of the flashy templates. It integrates with an 50 application and
services, because of which makes it great choice for users that live in the inbox (Rose, Eldridge
and Chapin, 2015).
Texting features
Send group Broadcasts- Here create many different group as you would like to choose the
name and merge the message and templates & than send an message to direct group of more than
100 contact at the time or message to an personalize text.
Convert into one to one conversation- As the text message reposes that can begin
“popping up”in the TextUs web portal that opening the door to an dozens of an personal, and one
to conversatiins (Poushter, 2016).
Safe and secure and cell notification- while sending text message put an mind at rest
because all messages are encrypted and has to be saved securely in the cloud. So it is an more
secure and safe. And also get an notification when reaches in smartphone, tablets or computers.
Texting applications
7
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

texting applications use internet connection for receving and sending the message. Their is
different form of SMS that use own protocol to receive and send message anywhere by an
cellular or mobile connection (Alaba, Othman, Hashem and Alotaibi, 2017).
Telegram- It is one of the secure original messaging apps that puts
an security that is the heart if the application. It can be used to send text message, videos, photos,
and file to another telegram users, Here user can make group to chats with a whopping of
200,000 participants, and also conversation are stored in accessible and cloud from any of
telegram client (Ray, 2018).
Facebook Messenger- This application include all basic messaging features that you
expect and some probably won't Here sent text to group of up to 100 people or individual and
react to an message that with stickers, emoji and GIFs. Here user can send photos, videos, voice
message or capture own media by using messenger camera and also with its fun Snap-chat- like
an filters. User can create polls to an fast get group opinion for an idea (Razzaque and et.al.,
2015).
Business suitableity
Email is the best way to sent the information or message of the organisation via email as it is an
more secure and lot of data can be send through email any updates and notifications can be
delivered to customers by company through email. Email is an effective mode of communicating
and engage people in organisation. Texting also suitable for sending the message to receiver. It is
also one of the best source of transferring the message to the client or customer. It is also one of
the best secure way to send the message to individual or group of an people together. Hence Both
mail and texting is best way for the suitability of the business (Madakam, Ramaswamy and
Tripathi, 2015).
CONCLUSION
From the above study it is concluded that internet can help the business through various
way for the communication. Internet has various positive and negative impact on the business
and society. Through internet information can be passed to many people in the business market.
Management is required to take sup[port of correct tool to exchange information so that correct
detail can be passed in correct manner to staff members in business unit.
8
different form of SMS that use own protocol to receive and send message anywhere by an
cellular or mobile connection (Alaba, Othman, Hashem and Alotaibi, 2017).
Telegram- It is one of the secure original messaging apps that puts
an security that is the heart if the application. It can be used to send text message, videos, photos,
and file to another telegram users, Here user can make group to chats with a whopping of
200,000 participants, and also conversation are stored in accessible and cloud from any of
telegram client (Ray, 2018).
Facebook Messenger- This application include all basic messaging features that you
expect and some probably won't Here sent text to group of up to 100 people or individual and
react to an message that with stickers, emoji and GIFs. Here user can send photos, videos, voice
message or capture own media by using messenger camera and also with its fun Snap-chat- like
an filters. User can create polls to an fast get group opinion for an idea (Razzaque and et.al.,
2015).
Business suitableity
Email is the best way to sent the information or message of the organisation via email as it is an
more secure and lot of data can be send through email any updates and notifications can be
delivered to customers by company through email. Email is an effective mode of communicating
and engage people in organisation. Texting also suitable for sending the message to receiver. It is
also one of the best source of transferring the message to the client or customer. It is also one of
the best secure way to send the message to individual or group of an people together. Hence Both
mail and texting is best way for the suitability of the business (Madakam, Ramaswamy and
Tripathi, 2015).
CONCLUSION
From the above study it is concluded that internet can help the business through various
way for the communication. Internet has various positive and negative impact on the business
and society. Through internet information can be passed to many people in the business market.
Management is required to take sup[port of correct tool to exchange information so that correct
detail can be passed in correct manner to staff members in business unit.
8
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

REFERENCES
Akyildiz, I.F., Pierobon, M., Balasubramaniam, S. and Koucheryavy, Y., 2015. The internet of
bio-nano things. IEEE Communications Magazine. 53(3). pp.32-40.
Alaba, F.A., Othman, M., Hashem, I.A.T. and Alotaibi, F., 2017. Internet of Things security: A
survey. Journal of Network and Computer Applications. 88. pp.10-28.
Gilchrist, A., 2016. Industry 4.0: the industrial internet of things. Apress.
Jeschke, S., Brecher, C., Meisen, T., Özdemir, D. and Eschert, T., 2017. Industrial internet of
things and cyber manREFERENCESufacturing systems. In Industrial Internet of
Things (pp. 3-19). Springer, Cham.
Madakam, S., Ramaswamy, R. and Tripathi, S., 2015. Internet of Things (IoT): A literature
review. Journal of Computer and Communications. 3(05). p.164.
Murdock, W.Q. and Williams, P.A., 2017. Computerized smart gaming tournament system for
the internet. U.S. Patent 9,662,558.
Poushter, J., 2016. Smartphone ownership and internet usage continues to climb in emerging
economies. Pew Research Center. 22. pp.1-44.
Ray, P.P., 2018. A survey on Internet of Things architectures.Journal of King Saud University-
Computer and Information Sciences. 30(3). pp.291-319.
Razzaque, M.A., Milojevic-Jevric, M., Palade, A. and Clarke, S., 2015. Middleware for internet
of things: a survey. IEEE Internet of things journal. 3(1). pp.70-95.
Rose, K., Eldridge, S. and Chapin, L., 2015. The internet of things: An overview. The Internet
Society (ISOC). 80.
Sethi, P. and Sarangi, S.R., 2017. Internet of things: architectures, protocols, and
applications. Journal of Electrical and Computer Engineering, 2017.
Whitmore, A., Agarwal, A. and Da Xu, L., 2015. The Internet of Things—A survey of topics and
trends. Information Systems Frontiers. 17(2). pp.261-274.
9
Akyildiz, I.F., Pierobon, M., Balasubramaniam, S. and Koucheryavy, Y., 2015. The internet of
bio-nano things. IEEE Communications Magazine. 53(3). pp.32-40.
Alaba, F.A., Othman, M., Hashem, I.A.T. and Alotaibi, F., 2017. Internet of Things security: A
survey. Journal of Network and Computer Applications. 88. pp.10-28.
Gilchrist, A., 2016. Industry 4.0: the industrial internet of things. Apress.
Jeschke, S., Brecher, C., Meisen, T., Özdemir, D. and Eschert, T., 2017. Industrial internet of
things and cyber manREFERENCESufacturing systems. In Industrial Internet of
Things (pp. 3-19). Springer, Cham.
Madakam, S., Ramaswamy, R. and Tripathi, S., 2015. Internet of Things (IoT): A literature
review. Journal of Computer and Communications. 3(05). p.164.
Murdock, W.Q. and Williams, P.A., 2017. Computerized smart gaming tournament system for
the internet. U.S. Patent 9,662,558.
Poushter, J., 2016. Smartphone ownership and internet usage continues to climb in emerging
economies. Pew Research Center. 22. pp.1-44.
Ray, P.P., 2018. A survey on Internet of Things architectures.Journal of King Saud University-
Computer and Information Sciences. 30(3). pp.291-319.
Razzaque, M.A., Milojevic-Jevric, M., Palade, A. and Clarke, S., 2015. Middleware for internet
of things: a survey. IEEE Internet of things journal. 3(1). pp.70-95.
Rose, K., Eldridge, S. and Chapin, L., 2015. The internet of things: An overview. The Internet
Society (ISOC). 80.
Sethi, P. and Sarangi, S.R., 2017. Internet of things: architectures, protocols, and
applications. Journal of Electrical and Computer Engineering, 2017.
Whitmore, A., Agarwal, A. and Da Xu, L., 2015. The Internet of Things—A survey of topics and
trends. Information Systems Frontiers. 17(2). pp.261-274.
9

10
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 15
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





