Analysis of Securing Internet of Everything: IBM Case Study
VerifiedAdded on 2021/01/02
|13
|3536
|262
Report
AI Summary
This report delves into the critical topic of securing the Internet of Everything (IOE) in the modern age, focusing on the challenges and potential solutions within the rapidly evolving landscape of interconnected devices. The introduction provides an overview of IOE, emphasizing its significance and background, including its aim, objectives, and research questions. A comprehensive literature review explores the definition and growth of IOE, highlighting its economic potential and impact on various sectors, while also addressing the security threats associated with the technology. The research methodology section outlines the type of investigation (qualitative), research design (descriptive), research approach (inductive), and research philosophy (interpretivism) adopted to conduct the study. Data collection methods are also discussed. The report includes a case study on IBM, examining their security protocols and strategies for addressing IOE security issues. The analysis covers threat models, social and economic perspectives, and methods for securing and monitoring IOE, providing valuable insights for securing connected devices. The conclusion and recommendations summarize the key findings and offer suggestions for enhancing IOE security. The report concludes with a list of references.

Securities in the age of
internet of Everything
internet of Everything
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Table of Contents
Title..................................................................................................................................................1
Introduction......................................................................................................................................1
Overview.....................................................................................................................................1
Significance.................................................................................................................................1
Background.................................................................................................................................1
Aim..............................................................................................................................................2
Objectives....................................................................................................................................2
Questions.....................................................................................................................................2
Literature Review.............................................................................................................................2
Research Methodology....................................................................................................................4
Type of investigation...................................................................................................................4
Research design...........................................................................................................................5
Research Approach.....................................................................................................................5
Research philosophy...................................................................................................................5
Data collection method...............................................................................................................5
Accessibility issues.....................................................................................................................6
Validity and reliability................................................................................................................6
Data Analysis...................................................................................................................................6
Conclusion and Recommendation...................................................................................................9
References......................................................................................................................................11
Title..................................................................................................................................................1
Introduction......................................................................................................................................1
Overview.....................................................................................................................................1
Significance.................................................................................................................................1
Background.................................................................................................................................1
Aim..............................................................................................................................................2
Objectives....................................................................................................................................2
Questions.....................................................................................................................................2
Literature Review.............................................................................................................................2
Research Methodology....................................................................................................................4
Type of investigation...................................................................................................................4
Research design...........................................................................................................................5
Research Approach.....................................................................................................................5
Research philosophy...................................................................................................................5
Data collection method...............................................................................................................5
Accessibility issues.....................................................................................................................6
Validity and reliability................................................................................................................6
Data Analysis...................................................................................................................................6
Conclusion and Recommendation...................................................................................................9
References......................................................................................................................................11

Title
To analyse how to secure internet of everything in the present age. A case study on IBM.
Introduction
Overview
This research project is based on how emerging technologies and their related
ecosystems are catalysing the security over internet of everything. Internet of everything that is
defined as is a connection via internet between computing devices which are nowadays
embedded in every objects that are used by the humans. So the main motive of the report is to
secure the the way that the data is transferred between the objects that are using internet. In this
world of IOT the physical things that connects with another physical things through wireless
connections and offering contextual services (Analoui, 2007). This research project aims to
provide the reader ways that will help in securing internet of everything in the modern world.
This research will bring in the mind of the reader that how IOE will assist in optimising the
process through advance data analytics and giving rise to cross cutting applications and services.
Significance
This research proposal will develop a level of understanding regarding IOE and the
security reasons for it. Nowadays it is very important for every user of the internet to use the
security procedures so as to avoid from the malfunctioning or the cyber crimes that are
happening in the modern world. As it is estimated that around 50mn devices will be get
connected to each other till 2020 so there is the increase in demand for security to that connected
things. This study will grow the knowledge of the reader about the security threats and the ways
that will enable to overcome them.
Background
The idea of connecting “things” through internet is a old thought now the evolution has
came and it is now given the idea that “internet of everything” should be applied in the global
world. It is the new paradigm that is changing the way of living of the society and the also our
lives. As the internet are connecting people and the things at a breathtaking pace and bringing
together the information. It is a promising source and helps in expanding the capabilities of the
business also. It also helps in giving richer user experience and also gains the unpredictable
1
To analyse how to secure internet of everything in the present age. A case study on IBM.
Introduction
Overview
This research project is based on how emerging technologies and their related
ecosystems are catalysing the security over internet of everything. Internet of everything that is
defined as is a connection via internet between computing devices which are nowadays
embedded in every objects that are used by the humans. So the main motive of the report is to
secure the the way that the data is transferred between the objects that are using internet. In this
world of IOT the physical things that connects with another physical things through wireless
connections and offering contextual services (Analoui, 2007). This research project aims to
provide the reader ways that will help in securing internet of everything in the modern world.
This research will bring in the mind of the reader that how IOE will assist in optimising the
process through advance data analytics and giving rise to cross cutting applications and services.
Significance
This research proposal will develop a level of understanding regarding IOE and the
security reasons for it. Nowadays it is very important for every user of the internet to use the
security procedures so as to avoid from the malfunctioning or the cyber crimes that are
happening in the modern world. As it is estimated that around 50mn devices will be get
connected to each other till 2020 so there is the increase in demand for security to that connected
things. This study will grow the knowledge of the reader about the security threats and the ways
that will enable to overcome them.
Background
The idea of connecting “things” through internet is a old thought now the evolution has
came and it is now given the idea that “internet of everything” should be applied in the global
world. It is the new paradigm that is changing the way of living of the society and the also our
lives. As the internet are connecting people and the things at a breathtaking pace and bringing
together the information. It is a promising source and helps in expanding the capabilities of the
business also. It also helps in giving richer user experience and also gains the unpredictable
1
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

economic opportunities. This IOE will help to create an environment that is connected
intelligently and intuitively. With some benefits it comes with certain weakness also. The main
weakness that arises in this is, security issues, so as to overcome this issue of security various
palms has to created. In the report the company is taken that is IBM which is a cloud service
providing company and is headquartered in Armonk, New York. The company has planned
different security protocols that will help in resolving the security issues related to IOE.
Aim
To analyse how to secure internet of everything in the present age.
Objectives
The main objective of the research is to:
Determine the concept of Internet of Everything
Also to analyse the impact of the securities issues that arises in communication of things.
To determine the threats model that are now available in the connected world
To discuss the social and economic point of view
To define the ways that will help in securing and monitoring IOE.
Questions
In the research the questions that will be tackled are:
What is Internet of Everything
what are the security issues that arises in the communication of “things”.
What are the threat models that are available in the global world.
What are the social and economical points of view of IOE
What are the ways to secure and monitor IOE
Literature Review
The IEEE in its special report defined IOE as a network of items each embedded with
sensors which are connected to the internet. It is defined as the structure that allows all types of
devices and machines to communicate with one another (Boella and Goss-Turner, 2013). It is
one of the fastest growing trends. It is the way of connection that makes the connected devices to
interoperate. This system connects the world to Physical system such as power meters, vehicles,
vending machines, smartwatches etc. The system has been identified by McKinsey global
institute as one of the most under hyped technologies with a economic potential of 2.7 to 6.2 tn
2
intelligently and intuitively. With some benefits it comes with certain weakness also. The main
weakness that arises in this is, security issues, so as to overcome this issue of security various
palms has to created. In the report the company is taken that is IBM which is a cloud service
providing company and is headquartered in Armonk, New York. The company has planned
different security protocols that will help in resolving the security issues related to IOE.
Aim
To analyse how to secure internet of everything in the present age.
Objectives
The main objective of the research is to:
Determine the concept of Internet of Everything
Also to analyse the impact of the securities issues that arises in communication of things.
To determine the threats model that are now available in the connected world
To discuss the social and economic point of view
To define the ways that will help in securing and monitoring IOE.
Questions
In the research the questions that will be tackled are:
What is Internet of Everything
what are the security issues that arises in the communication of “things”.
What are the threat models that are available in the global world.
What are the social and economical points of view of IOE
What are the ways to secure and monitor IOE
Literature Review
The IEEE in its special report defined IOE as a network of items each embedded with
sensors which are connected to the internet. It is defined as the structure that allows all types of
devices and machines to communicate with one another (Boella and Goss-Turner, 2013). It is
one of the fastest growing trends. It is the way of connection that makes the connected devices to
interoperate. This system connects the world to Physical system such as power meters, vehicles,
vending machines, smartwatches etc. The system has been identified by McKinsey global
institute as one of the most under hyped technologies with a economic potential of 2.7 to 6.2 tn
2
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

dollars till 2025. it has been developed at a faster rate and has entered in the living areas of the
humans. These have entered to home, digital healthcare, smart grid and also has enabled to make
smart city. For developing economies it is considered that there will be higher number of uses for
this type of technology. Companies in the field of IT sector can use this technology and can
capitalise on these technology advancements (Angle, and et.al. 2008). IOE can help in leveraging
all the related data and the process to make IOE more relevant and valuable to the people. The
ultimate goal of IOE is to boost operational efficiency, offer new business opportunities and to
improve the quality of life. For example if the person always forgets to close the gas valves then
it can help the individuals to check the gas valve remotely.
As this technology comes with lots of benefits it also poses some security threats to its
adopters. As the previous remote services were typically closed circuit, but nowadays these
systems are connected to the internet remotely and real time monitoring can be done for the
connected devices. These system can open the risks of internet based attacks. For example as it
happened in the case of a car company where it got attacked and was hacked remotely by the
person making him getting the control over the cars steering, brakes and the transmission. It is
also stated in the review that computerised equipments that are operated in the hospitals are more
prone to attack by malware rather than any other instrument that can cause the loosing of lives of
people. The risk of getting the system hacked by the hackers in the technology of IOE is greater.
And if the system is hacked then it may result to a huge loss to the owner of the technology.
Many researches have been done and it is discovered that approximately around 32000 firmware
are affected from potential IOE device manufacturers and it is discovered that around 38
vulnerabilities has affected 123 products. These vulnerabilities will conclude that backdoors will
get opened and unauthorised access would be given to the users which would open up hundreds
of devices to get seriously attacked through the malware.
Often systems are designed to cater to the business requirements only. Threat modelling
is approach that helps in identifying the security threats and vulnerabilities in the application
during the phase of designing the product. This is important because fixing the security issues at
the time of testing is time consuming as well as costs a lot to the company that makes the
product. So the few common steps that helps in modelling the threats are:
3
humans. These have entered to home, digital healthcare, smart grid and also has enabled to make
smart city. For developing economies it is considered that there will be higher number of uses for
this type of technology. Companies in the field of IT sector can use this technology and can
capitalise on these technology advancements (Angle, and et.al. 2008). IOE can help in leveraging
all the related data and the process to make IOE more relevant and valuable to the people. The
ultimate goal of IOE is to boost operational efficiency, offer new business opportunities and to
improve the quality of life. For example if the person always forgets to close the gas valves then
it can help the individuals to check the gas valve remotely.
As this technology comes with lots of benefits it also poses some security threats to its
adopters. As the previous remote services were typically closed circuit, but nowadays these
systems are connected to the internet remotely and real time monitoring can be done for the
connected devices. These system can open the risks of internet based attacks. For example as it
happened in the case of a car company where it got attacked and was hacked remotely by the
person making him getting the control over the cars steering, brakes and the transmission. It is
also stated in the review that computerised equipments that are operated in the hospitals are more
prone to attack by malware rather than any other instrument that can cause the loosing of lives of
people. The risk of getting the system hacked by the hackers in the technology of IOE is greater.
And if the system is hacked then it may result to a huge loss to the owner of the technology.
Many researches have been done and it is discovered that approximately around 32000 firmware
are affected from potential IOE device manufacturers and it is discovered that around 38
vulnerabilities has affected 123 products. These vulnerabilities will conclude that backdoors will
get opened and unauthorised access would be given to the users which would open up hundreds
of devices to get seriously attacked through the malware.
Often systems are designed to cater to the business requirements only. Threat modelling
is approach that helps in identifying the security threats and vulnerabilities in the application
during the phase of designing the product. This is important because fixing the security issues at
the time of testing is time consuming as well as costs a lot to the company that makes the
product. So the few common steps that helps in modelling the threats are:
3

Identify the security objectives: The producing company has to understand the security
requirements of the product and should identify the possible threats so as to achieve the
organisational goals.
Identify assets and external dependencies: as the data, code and systems information are
easily accessible, this will result in high amount of threat top occur. The person who is
developing the security needs to identify the list of assets that should be protected from
the malware.
Identify trust zones: the employees that are developing the programme must identify a
trust zone and a corresponding entry exit points. This will help to define the approach that
will help in data handling and error detection
Document the threat model: threat modelling is the main process and making it
documented helps in creating the team responsibilities. The designer should use the
documentation process that will help them to mitigate security threats. It helps the tester
to create security test.
IOE has the social and economic point of view as the Ecosystem that is generated by this
system includes the smart towns, artificial intelligence, ambient lighting and also a smart life.
This has impacted the society and the ecology in both positive as well as negative way (Boella
and Goss-Turner, 2013). The acceptance of IOE components and trusting them are related to
notional risks. Moving from the individual and organizational level the interest in security issues
in IOE is stated by most European governments which consider the IOE definitely an important
factor of economic and individual goals.
Research Methodology
Research methodology provides the guidance to the researcher so as to complete the
effective research work. Through this section the investigator is able to place way in which the
research can be conducted in an effective manner. So it is the guidance for the investigator to
complete the study in effectual manner. The methodologies that are applicable in this cases are:
Type of investigation
In this the researcher has to identify different types of research work so that they are able
to identify the appropriate level of techniques and methods. The research in the investigation is
identified into two parts that are qualitative and quantitative nature. The report that I have made
4
requirements of the product and should identify the possible threats so as to achieve the
organisational goals.
Identify assets and external dependencies: as the data, code and systems information are
easily accessible, this will result in high amount of threat top occur. The person who is
developing the security needs to identify the list of assets that should be protected from
the malware.
Identify trust zones: the employees that are developing the programme must identify a
trust zone and a corresponding entry exit points. This will help to define the approach that
will help in data handling and error detection
Document the threat model: threat modelling is the main process and making it
documented helps in creating the team responsibilities. The designer should use the
documentation process that will help them to mitigate security threats. It helps the tester
to create security test.
IOE has the social and economic point of view as the Ecosystem that is generated by this
system includes the smart towns, artificial intelligence, ambient lighting and also a smart life.
This has impacted the society and the ecology in both positive as well as negative way (Boella
and Goss-Turner, 2013). The acceptance of IOE components and trusting them are related to
notional risks. Moving from the individual and organizational level the interest in security issues
in IOE is stated by most European governments which consider the IOE definitely an important
factor of economic and individual goals.
Research Methodology
Research methodology provides the guidance to the researcher so as to complete the
effective research work. Through this section the investigator is able to place way in which the
research can be conducted in an effective manner. So it is the guidance for the investigator to
complete the study in effectual manner. The methodologies that are applicable in this cases are:
Type of investigation
In this the researcher has to identify different types of research work so that they are able
to identify the appropriate level of techniques and methods. The research in the investigation is
identified into two parts that are qualitative and quantitative nature. The report that I have made
4
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

includes the qualitative approach of data analysis. It helps in getting the data qualitatively. The
research is qualitative in nature if it deals in human tendency and feelings.
Research design
It is the design that is used to identify the design of the research through which it is done.
There are different types of research design that are used to design the research for the
investigator. Some of the research designs are identified as descriptive, explanatory and
experimental. Descriptive design emphasis on detailed presentment of the research that has been
done (Brown, 2003). It is the description of the existing facts and the figures that are used. The
present study is dealt with the descriptive analysis of the theory that is taken. It is done through
descriptive design that investigator is able to provide the detail evaluation of the different aspects
of the study.
Research Approach
The approaches that are used by the researcher while conducting the study is known as
research approach. The various approaches through which the research work is done are
categorised as inductive and deductive approach. In the case of inductive approach this emphasis
on analysing the existing facts and figures. While deductive approach analysis the created proven
hypothesis. It can be therefore said that the study of research is based on inductive approach. The
investigator is able to identify the reliable nature through this.
Research philosophy
This philosophy determines the patterns that is followed by the investigator fore
conducting the work. The researcher should chose the suitable philosophy so as to support the
study. The philosophies on which the research is based interpretivism or positivity philosophy. In
the case of interpretivism philosophy the investigator tends to adopt qualitative means to
accumulate data. So it is said that the philosophy of interpretivism is suitable and it is adopted to
conduct the investigation.
Data collection method
Data collection method is considered to be the most important area of research work.
Researcher has the option to use the information through primary and the secondary data. It is
considered to be in two ways that are primary and secondary data. In this the sample of 25
employees will be selected. The research is taken into consideration that can extract the relevant
5
research is qualitative in nature if it deals in human tendency and feelings.
Research design
It is the design that is used to identify the design of the research through which it is done.
There are different types of research design that are used to design the research for the
investigator. Some of the research designs are identified as descriptive, explanatory and
experimental. Descriptive design emphasis on detailed presentment of the research that has been
done (Brown, 2003). It is the description of the existing facts and the figures that are used. The
present study is dealt with the descriptive analysis of the theory that is taken. It is done through
descriptive design that investigator is able to provide the detail evaluation of the different aspects
of the study.
Research Approach
The approaches that are used by the researcher while conducting the study is known as
research approach. The various approaches through which the research work is done are
categorised as inductive and deductive approach. In the case of inductive approach this emphasis
on analysing the existing facts and figures. While deductive approach analysis the created proven
hypothesis. It can be therefore said that the study of research is based on inductive approach. The
investigator is able to identify the reliable nature through this.
Research philosophy
This philosophy determines the patterns that is followed by the investigator fore
conducting the work. The researcher should chose the suitable philosophy so as to support the
study. The philosophies on which the research is based interpretivism or positivity philosophy. In
the case of interpretivism philosophy the investigator tends to adopt qualitative means to
accumulate data. So it is said that the philosophy of interpretivism is suitable and it is adopted to
conduct the investigation.
Data collection method
Data collection method is considered to be the most important area of research work.
Researcher has the option to use the information through primary and the secondary data. It is
considered to be in two ways that are primary and secondary data. In this the sample of 25
employees will be selected. The research is taken into consideration that can extract the relevant
5
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

information. It can be done through the distribution of the questionnaire that the feedbacks will
be generated from the samples. The primary and the secondary data information will be collected
so that the research project can be taken into consideration.
Accessibility issues
The accessibility issues emphasize on the accessibility of the relevant information and
resources. The investigator faces the issues with the relevant information (Cartwright, 2005). The
investigator needs to invest a good amount of money and time for the purpose of conducting the
research. In the case researcher has ensures that the investment of adequate amount of resource
for the purpose of extracting relevant information.
Validity and reliability
It is essential for the investigator to produce the valid and reliable result. Validity and
dependability are thoughtful to be two important aspects for the research. In order to fulfill
measure of validity, the investigator needs to pull out information from reliable sources. It can
consequently said that the study planned herewith proves to be valid and reliable in nature.
Data Analysis
1. Are you aware about the concept of Internet of everything?
Yes 20
No 5
2. What is the influence of internet of things for IBM?
Positive 22
Negative 3
3. Do you think internet of everything helps in the development of IBM?
Yes 23
No 2
4. What are the advantages of using Internet of everything in IBM?
Assist in better performance 8
Better communications 5
Cost reduction 5
All the above 7
5. Give your own view on internet of everything
6
be generated from the samples. The primary and the secondary data information will be collected
so that the research project can be taken into consideration.
Accessibility issues
The accessibility issues emphasize on the accessibility of the relevant information and
resources. The investigator faces the issues with the relevant information (Cartwright, 2005). The
investigator needs to invest a good amount of money and time for the purpose of conducting the
research. In the case researcher has ensures that the investment of adequate amount of resource
for the purpose of extracting relevant information.
Validity and reliability
It is essential for the investigator to produce the valid and reliable result. Validity and
dependability are thoughtful to be two important aspects for the research. In order to fulfill
measure of validity, the investigator needs to pull out information from reliable sources. It can
consequently said that the study planned herewith proves to be valid and reliable in nature.
Data Analysis
1. Are you aware about the concept of Internet of everything?
Yes 20
No 5
2. What is the influence of internet of things for IBM?
Positive 22
Negative 3
3. Do you think internet of everything helps in the development of IBM?
Yes 23
No 2
4. What are the advantages of using Internet of everything in IBM?
Assist in better performance 8
Better communications 5
Cost reduction 5
All the above 7
5. Give your own view on internet of everything
6
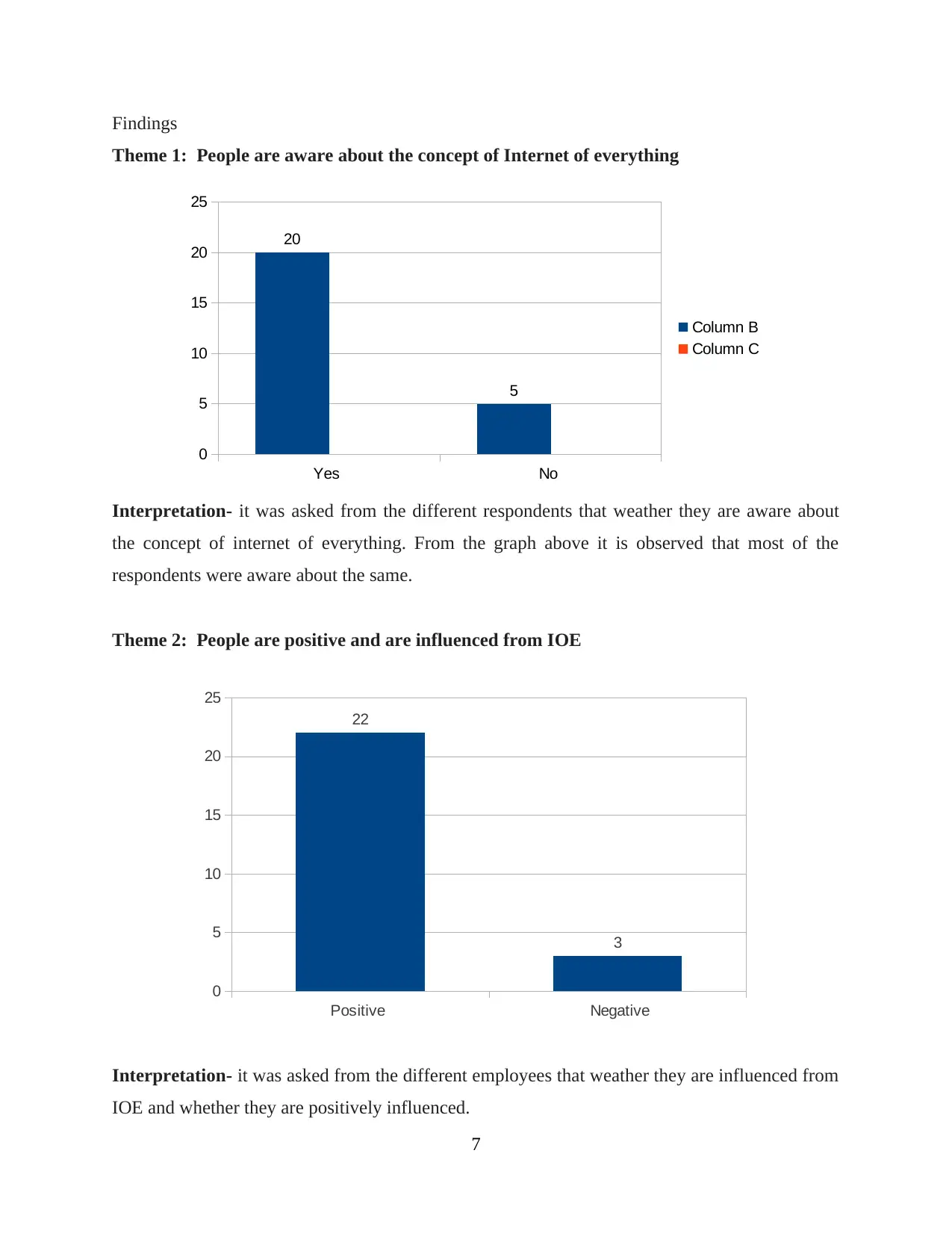
Findings
Theme 1: People are aware about the concept of Internet of everything
Interpretation- it was asked from the different respondents that weather they are aware about
the concept of internet of everything. From the graph above it is observed that most of the
respondents were aware about the same.
Theme 2: People are positive and are influenced from IOE
Interpretation- it was asked from the different employees that weather they are influenced from
IOE and whether they are positively influenced.
7
Yes No
0
5
10
15
20
25
20
5
Column B
Column C
Positive Negative
0
5
10
15
20
25
22
3
Theme 1: People are aware about the concept of Internet of everything
Interpretation- it was asked from the different respondents that weather they are aware about
the concept of internet of everything. From the graph above it is observed that most of the
respondents were aware about the same.
Theme 2: People are positive and are influenced from IOE
Interpretation- it was asked from the different employees that weather they are influenced from
IOE and whether they are positively influenced.
7
Yes No
0
5
10
15
20
25
20
5
Column B
Column C
Positive Negative
0
5
10
15
20
25
22
3
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
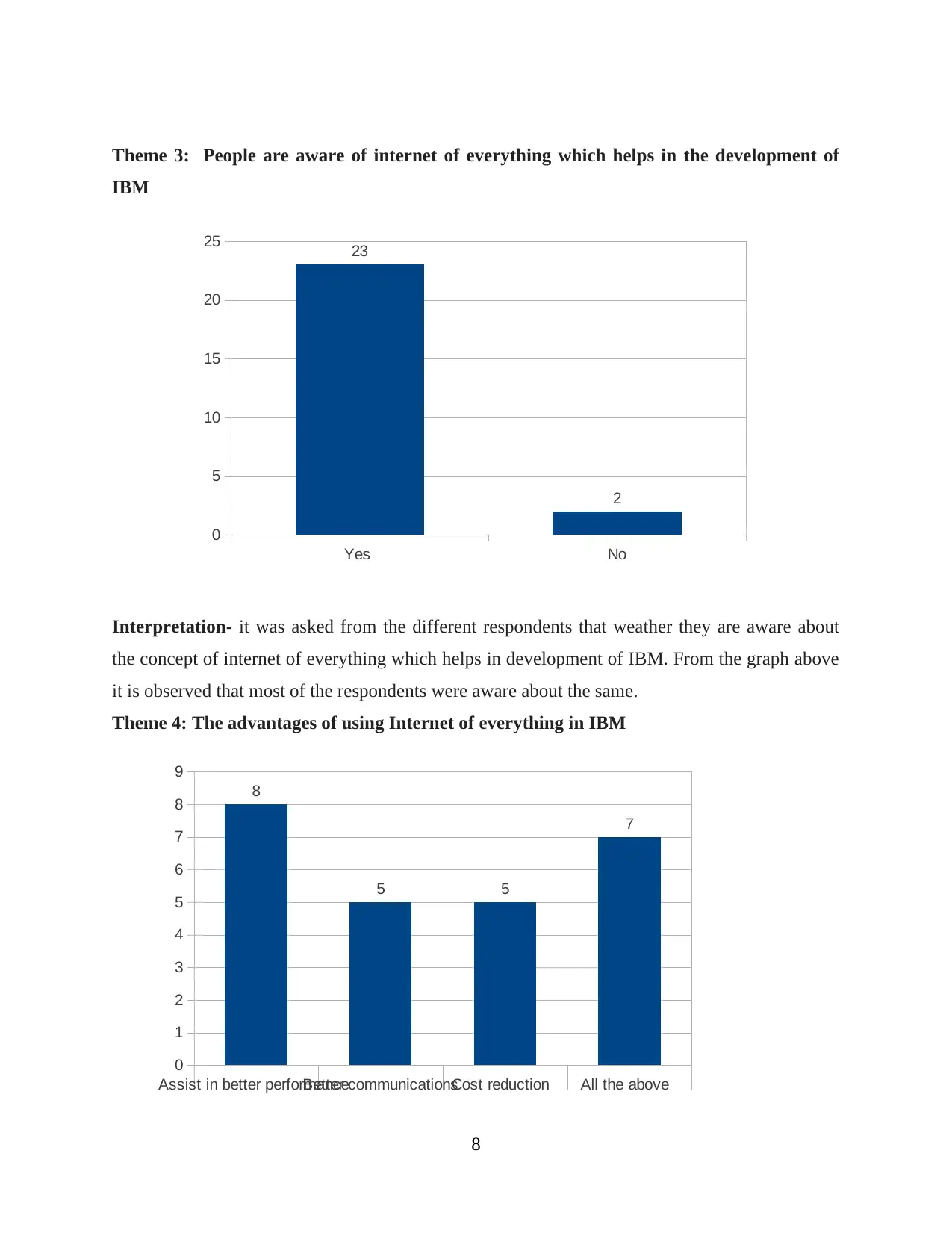
Theme 3: People are aware of internet of everything which helps in the development of
IBM
Interpretation- it was asked from the different respondents that weather they are aware about
the concept of internet of everything which helps in development of IBM. From the graph above
it is observed that most of the respondents were aware about the same.
Theme 4: The advantages of using Internet of everything in IBM
8
Yes No
0
5
10
15
20
25 23
2
Assist in better performanceBetter communicationsCost reduction All the above
0
1
2
3
4
5
6
7
8
9
8
5 5
7
IBM
Interpretation- it was asked from the different respondents that weather they are aware about
the concept of internet of everything which helps in development of IBM. From the graph above
it is observed that most of the respondents were aware about the same.
Theme 4: The advantages of using Internet of everything in IBM
8
Yes No
0
5
10
15
20
25 23
2
Assist in better performanceBetter communicationsCost reduction All the above
0
1
2
3
4
5
6
7
8
9
8
5 5
7
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Interpretation- it was asked from the different respondents that weather it is advantageous for
the company to use internet of everything for the development of IBM. From the graph above it
is observed that most of the respondents that internet of everything is useful in IBM
Conclusion and Recommendation
It can be concluded from the above research that the term IoE or Internet of Everything is
a concept which originated at the organisation Cisco, which emphasise on machine – to –
machine communications which report a system that encloses people as well as processes
(Chatha., Butt. and Tariq. 2015). Cisco defines the concept as intelligent network of people,
process, data and other things. This is a broad concept which involves any sort of physical or
virtual object which can be made accountable and can provide the ability to transfer data without
human to machine input.
Basically, the concept has evolved over the years and ever since there have been increase
in the security threats as the involvement of the people and development of the ubiquitous
communications through various different sources such as internet, privacy related security
threats are emerging. In context of security threats which came into existence in the era of IoE as
well as the threats which have not yet been realised, organisations have to take it into
consideration how to defend the data and the customers of the organisation. The business
enterprises are looking for the ways to reach to the local and global intelligence required by them
in order to use this information to make the correct decisions in protection of data owing to the
increasing security threats.
Further, it can be concluded that with the expanding IoT services the business enterprises
should include tailored security and privacy levels to ensure protection. The organisations are
relying on technological advancements for protecting the security, still the firewall is the biggest
piece of security software (Denisi, Budwar, and Varma, 2008). The company's are increasing the
security budget which means that the partners, vendors, etc. have a bigger role to play in the
providing security solutions across the market. Also, the government is making huge investments
into projects such as e-governance services and smart city projects, which means that the demand
of security solutions will increase.
The IoE has evolved all the way more as the various technological industries have
recently joined to provide the services of the concept in everyday life of the people, such as
houses, cars and lives. It has been applied to tuning into the cars, monitoring the health, safe
9
the company to use internet of everything for the development of IBM. From the graph above it
is observed that most of the respondents that internet of everything is useful in IBM
Conclusion and Recommendation
It can be concluded from the above research that the term IoE or Internet of Everything is
a concept which originated at the organisation Cisco, which emphasise on machine – to –
machine communications which report a system that encloses people as well as processes
(Chatha., Butt. and Tariq. 2015). Cisco defines the concept as intelligent network of people,
process, data and other things. This is a broad concept which involves any sort of physical or
virtual object which can be made accountable and can provide the ability to transfer data without
human to machine input.
Basically, the concept has evolved over the years and ever since there have been increase
in the security threats as the involvement of the people and development of the ubiquitous
communications through various different sources such as internet, privacy related security
threats are emerging. In context of security threats which came into existence in the era of IoE as
well as the threats which have not yet been realised, organisations have to take it into
consideration how to defend the data and the customers of the organisation. The business
enterprises are looking for the ways to reach to the local and global intelligence required by them
in order to use this information to make the correct decisions in protection of data owing to the
increasing security threats.
Further, it can be concluded that with the expanding IoT services the business enterprises
should include tailored security and privacy levels to ensure protection. The organisations are
relying on technological advancements for protecting the security, still the firewall is the biggest
piece of security software (Denisi, Budwar, and Varma, 2008). The company's are increasing the
security budget which means that the partners, vendors, etc. have a bigger role to play in the
providing security solutions across the market. Also, the government is making huge investments
into projects such as e-governance services and smart city projects, which means that the demand
of security solutions will increase.
The IoE has evolved all the way more as the various technological industries have
recently joined to provide the services of the concept in everyday life of the people, such as
houses, cars and lives. It has been applied to tuning into the cars, monitoring the health, safe
9

driving and adjusting to the traffic jams, monitoring the babies, and providing wearable tech.
These changes have ensured that the technological advancements have worked in the making the
lives of the people better.
Recommendations
In accordance to the research it can be suggested that one should go for the IoE enabled
products which are produced by the vendors, who update their product firewall on the regular
basis. Another, suggestion can be use of secure passwords and making an inquiry about how well
the manufacturer and vendors resolve or manages the vulnerabilities arising in the devices.
10
These changes have ensured that the technological advancements have worked in the making the
lives of the people better.
Recommendations
In accordance to the research it can be suggested that one should go for the IoE enabled
products which are produced by the vendors, who update their product firewall on the regular
basis. Another, suggestion can be use of secure passwords and making an inquiry about how well
the manufacturer and vendors resolve or manages the vulnerabilities arising in the devices.
10
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 13
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2025 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





