Internet of Things (IoT) Principles and Applications Assignment
VerifiedAdded on 2020/02/19
|11
|2235
|102
Homework Assignment
AI Summary
This assignment delves into the core concepts of the Internet of Things (IoT). It begins by evaluating the 'no user interface' principle, discussing its advantages in terms of efficiency and error reduction, and providing real-world examples. The assignment then explores cable specifications, categorizing and comparing coaxial, twisted pair, and fiber optic cables based on bandwidth, interference, cost, and security. A table is included to summarize the advantages, disadvantages, and applications of various IoT devices, such as sensors, RFID, and video tracking. The assignment also addresses security and privacy issues within IoT, highlighting potential vulnerabilities. Furthermore, it explains different communication paradigms like blocking mode and publish/subscribe, and command and response paradigms. Lastly, the assignment references Nielson's Law and its implications for IoT development, comparing it to Moore's Law and its impact on sensor technologies. The assignment is well-structured and provides comprehensive insights into the fundamental aspects of the Internet of Things.

Running head: INTERNET OF THINGS
Internet of Things
Name of the Student:
Student ID:
Name of the University:
Author’s note:
Internet of Things
Name of the Student:
Student ID:
Name of the University:
Author’s note:
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1INTERNET OF THINGS
Answer 1
The phrase “the best interface for a system is no user interface” is considered for
evaluating the fact that in applications and operations the use of no interface would be more
convenient in compare to the user interface. The absence of user interface would result in
eliminating the probability of occurrence of errors and delay in completion. The application of
the technology had employed for forming the improvement of efficiency of operations for the
organization. The implication of the interface would tend for the requirement of the some extra
time for forming the completion of the operations. The operations would be highly efficient for
developing the improvement operations in the organization. The “the best interface for a system
is no user interface” can be evaluated by the following examples,
Example 1 the payment in online retail store would comprise of forming the use of an
interface for processing the effective deployment of the operations (Takai et al., 2013). The
payment system would be formed by using a specific system application for forming the
development of the operations of the payment operations. The payment system would be formed
for developing the effective processing of payment systems for retail engineering. The payment
operations would form the deployment of the use of a device for accessing the payment. The
payment would be initiated by using the application interface for requesting the payment option.
The request would get into the network server and then it would proceed for getting to the bank.
The bank would receive the query for paying the mentioned person or organization. It would take
more time for processing the payment operations resulting in decreasing the efficiency of
operations of payment system.
Example 2 the auto gate-lock and open system via smart phone is another user
interface that can be considered as a factor for decreasing the efficiency of operations (Fisher,
Answer 1
The phrase “the best interface for a system is no user interface” is considered for
evaluating the fact that in applications and operations the use of no interface would be more
convenient in compare to the user interface. The absence of user interface would result in
eliminating the probability of occurrence of errors and delay in completion. The application of
the technology had employed for forming the improvement of efficiency of operations for the
organization. The implication of the interface would tend for the requirement of the some extra
time for forming the completion of the operations. The operations would be highly efficient for
developing the improvement operations in the organization. The “the best interface for a system
is no user interface” can be evaluated by the following examples,
Example 1 the payment in online retail store would comprise of forming the use of an
interface for processing the effective deployment of the operations (Takai et al., 2013). The
payment system would be formed by using a specific system application for forming the
development of the operations of the payment operations. The payment system would be formed
for developing the effective processing of payment systems for retail engineering. The payment
operations would form the deployment of the use of a device for accessing the payment. The
payment would be initiated by using the application interface for requesting the payment option.
The request would get into the network server and then it would proceed for getting to the bank.
The bank would receive the query for paying the mentioned person or organization. It would take
more time for processing the payment operations resulting in decreasing the efficiency of
operations of payment system.
Example 2 the auto gate-lock and open system via smart phone is another user
interface that can be considered as a factor for decreasing the efficiency of operations (Fisher,

2INTERNET OF THINGS
2013). The auto gate-lock and open system via smart phone is formed for accessing the function
of gate open and lock via mobile application. In this process the user would have to access the
application for reaching the function of gate opening/closing. The user would send request for
opening/closing the date of the car via application and it would be sent to the network via
cellular network. The request would reach the network of the car. The system would receive the
request for opening the door of the car and would in turn process the opening of the door. It
would take more time for processing the payment operations resulting in decreasing the
efficiency of operations of payment system.
Answer 2
The cables specification and their categorization is shown in the following paragraphs as
mentioned,
Coaxial Cables: The coaxial cables have the wider bandwidth of 1GHz that covers a
range of 500m. The interference rating for the coaxial cable is least vulnerable for interference
rating when compared to the other two cable types. The cost of the cables is of optimum price
and it would result in forming the cost controllable operations in the organization. According to
Winzer (2014), the Coaxial cables provide the moderate security option for connectivity.
Twisted Pair Cables: The Twisted Pair cables have the wider bandwidth of 1MHz that
covers a range of 100m. The interference rating for the coaxial cable is most vulnerable for
interference rating and distance when compared to the other two cable types. The cost of the
cables is of cheapest price and it would result in forming the cost controllable operations in the
organization. The Twisted Pair cables provide the least secured option for connectivity.
Fiber Optic Cable: The Fiber Optic cables have the wider bandwidth of 75THz that
covers a range of 10km. The interference rating for the coaxial cable is not all vulnerable for
2013). The auto gate-lock and open system via smart phone is formed for accessing the function
of gate open and lock via mobile application. In this process the user would have to access the
application for reaching the function of gate opening/closing. The user would send request for
opening/closing the date of the car via application and it would be sent to the network via
cellular network. The request would reach the network of the car. The system would receive the
request for opening the door of the car and would in turn process the opening of the door. It
would take more time for processing the payment operations resulting in decreasing the
efficiency of operations of payment system.
Answer 2
The cables specification and their categorization is shown in the following paragraphs as
mentioned,
Coaxial Cables: The coaxial cables have the wider bandwidth of 1GHz that covers a
range of 500m. The interference rating for the coaxial cable is least vulnerable for interference
rating when compared to the other two cable types. The cost of the cables is of optimum price
and it would result in forming the cost controllable operations in the organization. According to
Winzer (2014), the Coaxial cables provide the moderate security option for connectivity.
Twisted Pair Cables: The Twisted Pair cables have the wider bandwidth of 1MHz that
covers a range of 100m. The interference rating for the coaxial cable is most vulnerable for
interference rating and distance when compared to the other two cable types. The cost of the
cables is of cheapest price and it would result in forming the cost controllable operations in the
organization. The Twisted Pair cables provide the least secured option for connectivity.
Fiber Optic Cable: The Fiber Optic cables have the wider bandwidth of 75THz that
covers a range of 10km. The interference rating for the coaxial cable is not all vulnerable for
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
3INTERNET OF THINGS
interference rating when compared to the other two cable types. The cost of the cables is of
highest price and it would result in forming the cost controllable operations in the organization.
The Fiber Optic cables provide the highest security option for connectivity.
Connectivity Cables Categorization
Cable type Cable Category Description
Co-Axial
Cable
Lee et al. have classified the
coaxial cables into three types
namely,
Type I coaxial cable
Type II coaxial cable
Type III coaxial cable
Type I coaxial cable is used for thick power
Internet connectivity and is of RG-7 or RG-11
with 50 ohm resistance.
Type II coaxial cable is used for thin power
Internet connectivity and is of RG-58 with 50
ohm resistance.
Type III coaxial cable is used for cable
television and is of RG-59 with 75 ohm
resistance.
Twister
Pair Cable
Ha et. Al have classified the
Twister Pair cables into three
types namely,
Unprotected Twister Pair cable
Shielded Twisted Pair cable
Foil Shielded Twisted Pair
Unprotected Twister Pair cable is used for data
cable of low speed internet
Shielded Twisted Pair cable is used for
implementation support for 4 MPS
Foil Shielded Twisted Pair is used for
implementation support for 16 MPS
Fibre
Optic
Lee et al. have classified the
coaxial cables into three types
Single Mode Fibre Optic Cable has a range of 2
Km
interference rating when compared to the other two cable types. The cost of the cables is of
highest price and it would result in forming the cost controllable operations in the organization.
The Fiber Optic cables provide the highest security option for connectivity.
Connectivity Cables Categorization
Cable type Cable Category Description
Co-Axial
Cable
Lee et al. have classified the
coaxial cables into three types
namely,
Type I coaxial cable
Type II coaxial cable
Type III coaxial cable
Type I coaxial cable is used for thick power
Internet connectivity and is of RG-7 or RG-11
with 50 ohm resistance.
Type II coaxial cable is used for thin power
Internet connectivity and is of RG-58 with 50
ohm resistance.
Type III coaxial cable is used for cable
television and is of RG-59 with 75 ohm
resistance.
Twister
Pair Cable
Ha et. Al have classified the
Twister Pair cables into three
types namely,
Unprotected Twister Pair cable
Shielded Twisted Pair cable
Foil Shielded Twisted Pair
Unprotected Twister Pair cable is used for data
cable of low speed internet
Shielded Twisted Pair cable is used for
implementation support for 4 MPS
Foil Shielded Twisted Pair is used for
implementation support for 16 MPS
Fibre
Optic
Lee et al. have classified the
coaxial cables into three types
Single Mode Fibre Optic Cable has a range of 2
Km
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
4INTERNET OF THINGS
Cable namely,
Single Mode Fibre Optic Cable
Multi Mode Fibre Optic Cable
Plastic Fibre Optic Cable
Multi Mode Fibre Optic Cable has a range of 10
Km
Plastic Fibre Optic Cable has a range of 16 Km
Answer 3
The table would compare the advantages, disadvantages, and application for utilizing the
technology of Internet of Things,
IoT
Devices
Advantages Disadvantages Application
Sensors Low Maintenance of
Cost
High Capability of
Current
Requirement of Physical
Contact
Packaging, Interlocking, and
detection of parts
RFID Multiple tags are
allowed
Use of line of sight
Costly for use as there are
number of processes
involved
Pallet, apparel tracking, and
jewellery are tracked by
using RFID
Video
Tracking
Improvement of
Communication
Control Functions
Automation
Exposure of Privacy is
possible
Complex System
Interaction of human to
computer
Realty Augmentation
Cable namely,
Single Mode Fibre Optic Cable
Multi Mode Fibre Optic Cable
Plastic Fibre Optic Cable
Multi Mode Fibre Optic Cable has a range of 10
Km
Plastic Fibre Optic Cable has a range of 16 Km
Answer 3
The table would compare the advantages, disadvantages, and application for utilizing the
technology of Internet of Things,
IoT
Devices
Advantages Disadvantages Application
Sensors Low Maintenance of
Cost
High Capability of
Current
Requirement of Physical
Contact
Packaging, Interlocking, and
detection of parts
RFID Multiple tags are
allowed
Use of line of sight
Costly for use as there are
number of processes
involved
Pallet, apparel tracking, and
jewellery are tracked by
using RFID
Video
Tracking
Improvement of
Communication
Control Functions
Automation
Exposure of Privacy is
possible
Complex System
Interaction of human to
computer
Realty Augmentation

5INTERNET OF THINGS
Answer 4
According to Borgohian, Kumar and Sanyal (2015), the issues of security are the factors
that have an impact on the applications of IoT devices that has been resulted due to unauthentic
entrance in the information system due to gaining of personal benefits.
On the contrary Suo et al. (2012), defines privacy issues as factors of infiltration that
adverse the flow of information and processing. The use of the effective methods of processing
in the organization would tend to form the confidential data to be exposed.
Answer 5
Blocking Mode: The characteristics of blocking mode is formed for analysing the
occurrence of user request at the end point of operations orientation that results in involving
longer wait duration for the completion of operations. It is similar to synchronous mode and the
original message is not transferred.
Subscribe or Publish Paradigm: It is defined as the paradigm for defining the single
directional communication for the subscribers and the publishers.
Figure 1: Publish or Subscribe Paradigm
Command and Response Paradigm: The paradigm is used for communication of the
overhead messages that are required in the organization.
Answer 4
According to Borgohian, Kumar and Sanyal (2015), the issues of security are the factors
that have an impact on the applications of IoT devices that has been resulted due to unauthentic
entrance in the information system due to gaining of personal benefits.
On the contrary Suo et al. (2012), defines privacy issues as factors of infiltration that
adverse the flow of information and processing. The use of the effective methods of processing
in the organization would tend to form the confidential data to be exposed.
Answer 5
Blocking Mode: The characteristics of blocking mode is formed for analysing the
occurrence of user request at the end point of operations orientation that results in involving
longer wait duration for the completion of operations. It is similar to synchronous mode and the
original message is not transferred.
Subscribe or Publish Paradigm: It is defined as the paradigm for defining the single
directional communication for the subscribers and the publishers.
Figure 1: Publish or Subscribe Paradigm
Command and Response Paradigm: The paradigm is used for communication of the
overhead messages that are required in the organization.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
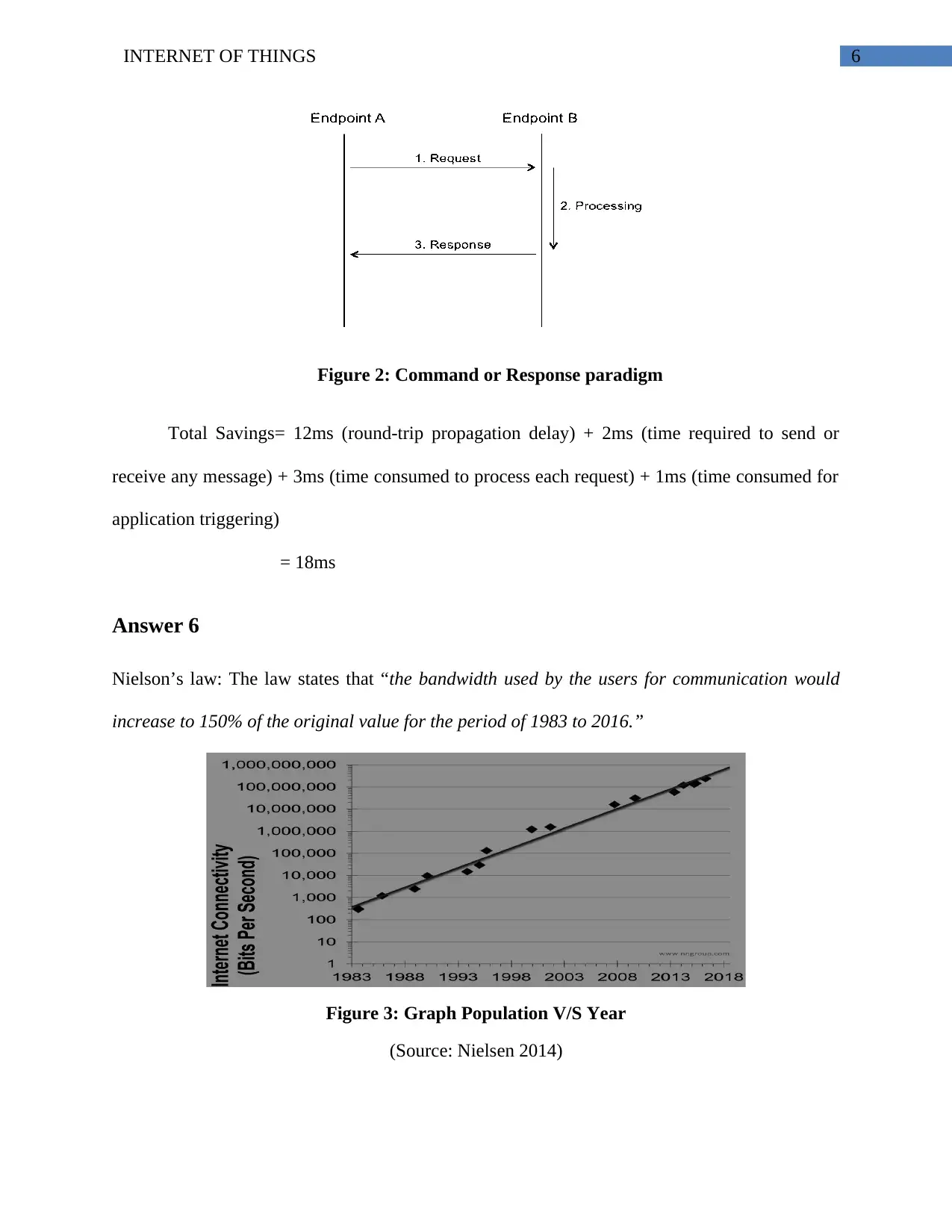
6INTERNET OF THINGS
Figure 2: Command or Response paradigm
Total Savings= 12ms (round-trip propagation delay) + 2ms (time required to send or
receive any message) + 3ms (time consumed to process each request) + 1ms (time consumed for
application triggering)
= 18ms
Answer 6
Nielson’s law: The law states that “the bandwidth used by the users for communication would
increase to 150% of the original value for the period of 1983 to 2016.”
Figure 3: Graph Population V/S Year
(Source: Nielsen 2014)
Figure 2: Command or Response paradigm
Total Savings= 12ms (round-trip propagation delay) + 2ms (time required to send or
receive any message) + 3ms (time consumed to process each request) + 1ms (time consumed for
application triggering)
= 18ms
Answer 6
Nielson’s law: The law states that “the bandwidth used by the users for communication would
increase to 150% of the original value for the period of 1983 to 2016.”
Figure 3: Graph Population V/S Year
(Source: Nielsen 2014)
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7INTERNET OF THINGS
Moore’s law and Nielson’s law have similarities with each other as both of them
exercises the development of technology and increment of the capabilities of computer (60%)
and bandwidth (50%) respectively.
The Nielson’s law had been helpful for forming the development of the IoT application
with the help of development of sensor technologies. The advent of microchips had been
possible due to the analysis of the Nielson’s law.
Moore’s law and Nielson’s law have similarities with each other as both of them
exercises the development of technology and increment of the capabilities of computer (60%)
and bandwidth (50%) respectively.
The Nielson’s law had been helpful for forming the development of the IoT application
with the help of development of sensor technologies. The advent of microchips had been
possible due to the analysis of the Nielson’s law.

8INTERNET OF THINGS
References
Borgohain, T., Kumar, U., & Sanyal, S. (2015). Survey of security and privacy issues of Internet
of Things. arXiv preprint arXiv:1501.02211.
Fisher, M. (2013). U.S. Patent No. 8,352,323. Washington, DC: U.S. Patent and Trademark
Office.
Ha, S. K., Kim, G. S., Choi, S. M., Kim, S. K., Kim, J. G., Park, M., ... & Sim, K. (2013). PHILS
based protection system design for an HTS power cable installed in a grid. 대대대대대대 대대대대 대대대,
339-340.
Lee, W., Cheon, M., Hyun, C. H., & Park, M. (2013). Development of building fire safety
system with automatic security firm monitoring capability. Fire safety journal, 58, 65-73.
Nielsen, J. (2014). Nielsen’s Law of Internet Bandwidth, 1998.
Singh, D., Tripathi, G., & Jara, A. J. (2014, March). A survey of Internet-of-Things: Future
vision, architecture, challenges and services. In Internet of things (WF-IoT), 2014 IEEE world
forum on (pp. 287-292). IEEE.
Sommer, J., & Franz, W. (2012). A Component-based Simulation Model and its Implementation
of a Switched Ethernet Network.
Suo, H., Wan, J., Zou, C., & Liu, J. (2012, March). Security in the internet of things: a review.
In Computer Science and Electronics Engineering (ICCSEE), 2012 international conference
on (Vol. 3, pp. 648-651). IEEE.
References
Borgohain, T., Kumar, U., & Sanyal, S. (2015). Survey of security and privacy issues of Internet
of Things. arXiv preprint arXiv:1501.02211.
Fisher, M. (2013). U.S. Patent No. 8,352,323. Washington, DC: U.S. Patent and Trademark
Office.
Ha, S. K., Kim, G. S., Choi, S. M., Kim, S. K., Kim, J. G., Park, M., ... & Sim, K. (2013). PHILS
based protection system design for an HTS power cable installed in a grid. 대대대대대대 대대대대 대대대,
339-340.
Lee, W., Cheon, M., Hyun, C. H., & Park, M. (2013). Development of building fire safety
system with automatic security firm monitoring capability. Fire safety journal, 58, 65-73.
Nielsen, J. (2014). Nielsen’s Law of Internet Bandwidth, 1998.
Singh, D., Tripathi, G., & Jara, A. J. (2014, March). A survey of Internet-of-Things: Future
vision, architecture, challenges and services. In Internet of things (WF-IoT), 2014 IEEE world
forum on (pp. 287-292). IEEE.
Sommer, J., & Franz, W. (2012). A Component-based Simulation Model and its Implementation
of a Switched Ethernet Network.
Suo, H., Wan, J., Zou, C., & Liu, J. (2012, March). Security in the internet of things: a review.
In Computer Science and Electronics Engineering (ICCSEE), 2012 international conference
on (Vol. 3, pp. 648-651). IEEE.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

9INTERNET OF THINGS
Takai, I., Ito, S., Yasutomi, K., Kagawa, K., Andoh, M., & Kawahito, S. (2013). LED and
CMOS image sensor based optical wireless communication system for automotive
applications. IEEE Photonics Journal, 5(5), 6801418-6801418.
Tozlu, S., Senel, M., Mao, W., & Keshavarzian, A. (2012). Wi-Fi enabled sensors for internet of
things: A practical approach. IEEE Communications Magazine, 50(6).
Winzer, P. J. (2014). Spatial multiplexing in fiber optics: The 10x scaling of metro/core
capacities. Bell Labs Technical Journal, 19, 22-30.
Borgohain, T., Kumar, U., & Sanyal, S. (2015). Survey of security and privacy issues of Internet
of Things. arXiv preprint arXiv:1501.02211.
Fisher, M. (2013). U.S. Patent No. 8,352,323. Washington, DC: U.S. Patent and Trademark
Office.
Ha, S. K., Kim, G. S., Choi, S. M., Kim, S. K., Kim, J. G., Park, M., ... & Sim, K. (2013). PHILS
based protection system design for an HTS power cable installed in a grid. 대 대 대 대 대 대
대대대대 대대대, 339-340.
Lee, W., Cheon, M., Hyun, C. H., & Park, M. (2013). Development of building fire safety
system with automatic security firm monitoring capability. Fire safety journal, 58, 65-73.
Nielsen, J. (2014). Nielsen’s Law of Internet Bandwidth, 1998.
Singh, D., Tripathi, G., & Jara, A. J. (2014, March). A survey of Internet-of-Things: Future
vision, architecture, challenges and services. In Internet of things (WF-IoT), 2014 IEEE
world forum on (pp. 287-292). IEEE.
Takai, I., Ito, S., Yasutomi, K., Kagawa, K., Andoh, M., & Kawahito, S. (2013). LED and
CMOS image sensor based optical wireless communication system for automotive
applications. IEEE Photonics Journal, 5(5), 6801418-6801418.
Tozlu, S., Senel, M., Mao, W., & Keshavarzian, A. (2012). Wi-Fi enabled sensors for internet of
things: A practical approach. IEEE Communications Magazine, 50(6).
Winzer, P. J. (2014). Spatial multiplexing in fiber optics: The 10x scaling of metro/core
capacities. Bell Labs Technical Journal, 19, 22-30.
Borgohain, T., Kumar, U., & Sanyal, S. (2015). Survey of security and privacy issues of Internet
of Things. arXiv preprint arXiv:1501.02211.
Fisher, M. (2013). U.S. Patent No. 8,352,323. Washington, DC: U.S. Patent and Trademark
Office.
Ha, S. K., Kim, G. S., Choi, S. M., Kim, S. K., Kim, J. G., Park, M., ... & Sim, K. (2013). PHILS
based protection system design for an HTS power cable installed in a grid. 대 대 대 대 대 대
대대대대 대대대, 339-340.
Lee, W., Cheon, M., Hyun, C. H., & Park, M. (2013). Development of building fire safety
system with automatic security firm monitoring capability. Fire safety journal, 58, 65-73.
Nielsen, J. (2014). Nielsen’s Law of Internet Bandwidth, 1998.
Singh, D., Tripathi, G., & Jara, A. J. (2014, March). A survey of Internet-of-Things: Future
vision, architecture, challenges and services. In Internet of things (WF-IoT), 2014 IEEE
world forum on (pp. 287-292). IEEE.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

10INTERNET OF THINGS
1 out of 11
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





