University IoT Assignment: Cables, Devices, Security and Protocols
VerifiedAdded on 2020/02/24
|12
|2197
|82
Homework Assignment
AI Summary
This document provides a detailed solution to an Internet of Things (IoT) assignment. It begins by addressing the concept of a 'no user interface' system, providing examples such as automated car door systems and contactless payment. The assignment then delves into comparing the specifications of different cable types (coaxial, twisted pair, and fiber optic), including bandwidth, distance, and security considerations, along with cable categories. It proceeds to compare three IoT devices: sensors, RFID, and video tracking, highlighting their advantages, disadvantages, and applications. The solution then discusses security and privacy issues in IoT implications, such as unauthorized access and data breaches. Furthermore, the assignment explores different communication paradigms, including blocking mode, command/response, and publish/subscribe (pub/sub) models, comparing their efficiency and applicability in IoT scenarios. Finally, it addresses Nielson's Law concerning internet bandwidth growth and its implications for IoT, concluding with a comprehensive list of references.

Running head: INTERNET OF THINGS
Internet of Things
Name of the Student
Name of the University
Author Note
Internet of Things
Name of the Student
Name of the University
Author Note
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1
INTERNET OF THINGS
Table of Contents
Answer 1:.........................................................................................................................................3
The Statement..............................................................................................................................3
First Example:..............................................................................................................................3
Second Example:.........................................................................................................................3
Answer 2:.........................................................................................................................................4
Comparing Specifications of Cables:..........................................................................................4
Cables Categories:.......................................................................................................................4
Answer 3:.........................................................................................................................................5
Comparing Three IoT Devices:...................................................................................................5
Answer 4:.........................................................................................................................................7
Security Issues in IoT Implications.............................................................................................7
Privacy Issues in IoT Implications..............................................................................................7
Answer 5:.........................................................................................................................................7
Blocking mode:............................................................................................................................7
Command/Response Paradigm:...................................................................................................8
Publish/Subscribe Paradigm:.......................................................................................................8
Using Pub/Sub Model in Lieu of the Command/Response Paradigm.........................................9
Answer 6:.........................................................................................................................................9
Nielson’s Law..............................................................................................................................9
Nelson’s law Implication in IoT................................................................................................10
References:....................................................................................................................................11
INTERNET OF THINGS
Table of Contents
Answer 1:.........................................................................................................................................3
The Statement..............................................................................................................................3
First Example:..............................................................................................................................3
Second Example:.........................................................................................................................3
Answer 2:.........................................................................................................................................4
Comparing Specifications of Cables:..........................................................................................4
Cables Categories:.......................................................................................................................4
Answer 3:.........................................................................................................................................5
Comparing Three IoT Devices:...................................................................................................5
Answer 4:.........................................................................................................................................7
Security Issues in IoT Implications.............................................................................................7
Privacy Issues in IoT Implications..............................................................................................7
Answer 5:.........................................................................................................................................7
Blocking mode:............................................................................................................................7
Command/Response Paradigm:...................................................................................................8
Publish/Subscribe Paradigm:.......................................................................................................8
Using Pub/Sub Model in Lieu of the Command/Response Paradigm.........................................9
Answer 6:.........................................................................................................................................9
Nielson’s Law..............................................................................................................................9
Nelson’s law Implication in IoT................................................................................................10
References:....................................................................................................................................11

2
INTERNET OF THINGS
Answer 1:
The Statement
The statement “the best interface for a system is no user interface” can be defined as a
system with no user interface implementation by which activities can be done in very few time or
automatically (Rayes & Salam, 2017). Or it can also be defined as elimination of the user
interface system from the whole process of a system in which any technology is being operated.
This elimination can reduce many steps during execution of any system using technology which
will help in completing the works in less time. With no user interface a user can complete his or
her work by escaping several steps and can buy more time in completing that activity. Following
are the examples which can be helpful in making this definition clearer (Rayes & Samer, 2017).
First Example:
Nowadays automobile companies are implementing new and innovative technologies in
the cars in which one of the latest implications is the door opening system using mobile
application. This implication has several steps due to the involvement of user interface system in
the whole system as the user will have to do several steps to open the locked door of the car;
1. User will have to walk near the car
2. Turn his/her phone on
3. Search for the specific application
4. After launching the application, gate will open
With no user interface system this could be done in two steps only:
1. User reaches the car
INTERNET OF THINGS
Answer 1:
The Statement
The statement “the best interface for a system is no user interface” can be defined as a
system with no user interface implementation by which activities can be done in very few time or
automatically (Rayes & Salam, 2017). Or it can also be defined as elimination of the user
interface system from the whole process of a system in which any technology is being operated.
This elimination can reduce many steps during execution of any system using technology which
will help in completing the works in less time. With no user interface a user can complete his or
her work by escaping several steps and can buy more time in completing that activity. Following
are the examples which can be helpful in making this definition clearer (Rayes & Samer, 2017).
First Example:
Nowadays automobile companies are implementing new and innovative technologies in
the cars in which one of the latest implications is the door opening system using mobile
application. This implication has several steps due to the involvement of user interface system in
the whole system as the user will have to do several steps to open the locked door of the car;
1. User will have to walk near the car
2. Turn his/her phone on
3. Search for the specific application
4. After launching the application, gate will open
With no user interface system this could be done in two steps only:
1. User reaches the car
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
3
INTERNET OF THINGS
2. Gates are open
This can be done by implementing sensor in the keys and the car, as whenever the owner
reaches to the car with the keys the gate will automatically opens.
Second Example:
Another example which can be helpful in transparency of this topic is the new merchant
payment system which is trending nowadays. User generally move to the café or the restaurant
and orders the food or beverage then he or she has to again take phone out, search for the
application, look into the application make payment procedures and then he can left out the café
or the restaurant. Again various steps can be reduced by “no user interface system”, by this user
will enter the café, orders whatever he wants and after eating or drinking he can leave that
restaurant and the payment will be made automatically.
Answer 2:
Comparing Specifications of Cables:
Types of
cables
Bandwidth Distance Interference
rating
Cost Security
Coaxial
Cable
1GHz 500m Less susceptible
to interference
than Twisted
pair cables
Neither much
costly nor
cheap.
Not
invincible,
security
moderate but
can be
breached
(Agha,
Babiker &
Mustafa,
2015)
Twisted Pair
Cable
1MHz 100m Susceptible to
interference,
however limited
to a distance
Most cheaper
than others
Security is
not at all.
INTERNET OF THINGS
2. Gates are open
This can be done by implementing sensor in the keys and the car, as whenever the owner
reaches to the car with the keys the gate will automatically opens.
Second Example:
Another example which can be helpful in transparency of this topic is the new merchant
payment system which is trending nowadays. User generally move to the café or the restaurant
and orders the food or beverage then he or she has to again take phone out, search for the
application, look into the application make payment procedures and then he can left out the café
or the restaurant. Again various steps can be reduced by “no user interface system”, by this user
will enter the café, orders whatever he wants and after eating or drinking he can leave that
restaurant and the payment will be made automatically.
Answer 2:
Comparing Specifications of Cables:
Types of
cables
Bandwidth Distance Interference
rating
Cost Security
Coaxial
Cable
1GHz 500m Less susceptible
to interference
than Twisted
pair cables
Neither much
costly nor
cheap.
Not
invincible,
security
moderate but
can be
breached
(Agha,
Babiker &
Mustafa,
2015)
Twisted Pair
Cable
1MHz 100m Susceptible to
interference,
however limited
to a distance
Most cheaper
than others
Security is
not at all.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
4
INTERNET OF THINGS
Fibre Optic
Cable
75 THz 10km
(Single-
mode)
2Km
(multimode)
Not susceptible
to
Electromagnetic
Interference
(EMI)
Highly
expensive
than both the
cables
Security is
very high and
breaching is
almost
impossible
(Alimam,
2015).
Cables Categories:
Twisted Pair Cable:
1. STP- Shielded Twisted Pair
Type A: Inherit type 1 with 4 telephone pairs (Sommer and Franz, 2012).
Type B: Features 22-AWG two pairs.
Type C: Features two pairs of shielded 26-AWG.
2. UTP- Unprotected Twisted-Pair
Type A: These can support 4 mps implementation (Lee et al., 2013).
Type B: Used in low speed data cable and telephone lines.
Type C: These cables can support maximum speed of 16 mps but are commonly
used at 10 mps speed.
3. Co-Axial Cable:
Type A: 50-Ohm RG-58, applicable with thin Ethernet (Ha et al., 2013).
Type B: 50-Ohm RG-7 or RG-11, applicable with thick Ethernet.
Type C: 75-Ohm RG-59, applicable with cable television.
INTERNET OF THINGS
Fibre Optic
Cable
75 THz 10km
(Single-
mode)
2Km
(multimode)
Not susceptible
to
Electromagnetic
Interference
(EMI)
Highly
expensive
than both the
cables
Security is
very high and
breaching is
almost
impossible
(Alimam,
2015).
Cables Categories:
Twisted Pair Cable:
1. STP- Shielded Twisted Pair
Type A: Inherit type 1 with 4 telephone pairs (Sommer and Franz, 2012).
Type B: Features 22-AWG two pairs.
Type C: Features two pairs of shielded 26-AWG.
2. UTP- Unprotected Twisted-Pair
Type A: These can support 4 mps implementation (Lee et al., 2013).
Type B: Used in low speed data cable and telephone lines.
Type C: These cables can support maximum speed of 16 mps but are commonly
used at 10 mps speed.
3. Co-Axial Cable:
Type A: 50-Ohm RG-58, applicable with thin Ethernet (Ha et al., 2013).
Type B: 50-Ohm RG-7 or RG-11, applicable with thick Ethernet.
Type C: 75-Ohm RG-59, applicable with cable television.
5
INTERNET OF THINGS
4. Fibre Optic Cable:
There is only one type of fibre optic cable.
Answer 3:
Comparing Three IoT Devices:
IoT Devices Advantages Disadvantages Application
Sensors Sensors are not affected by
atmospheric dust, rain, snow.
Working is not affected in
adverse conditions if proper
power supply is given.
Sensing distance is more than
inductive or capacitive
proximity sensors’ sensing
device (Alamri et al., 2013).
Problem in
receiving signals
from curved, small,
soft and thin objects
are the
disadvantages with
this device.
Weather monitoring.
Smart sleep system.
Smart lightning.
Smart washing
machine.
Smart internet mirror
In medical, Blood
Pressure monitoring.
RFID RFID used for tagging are
completely secured and cannot
be duplicated
Messages can be exchanged
from long distances
There are various types of
RFID which can be applicable
for all the conditions (Garrido
Less reliable as it is
harder to understand
More expensive
than Barcode
system.
Longer than the
Barcode labels in
It is widely used for
tracking products in
which RFID are
implemented to
detect the location of
the product or item.
Apparel,
pharmaceutical
INTERNET OF THINGS
4. Fibre Optic Cable:
There is only one type of fibre optic cable.
Answer 3:
Comparing Three IoT Devices:
IoT Devices Advantages Disadvantages Application
Sensors Sensors are not affected by
atmospheric dust, rain, snow.
Working is not affected in
adverse conditions if proper
power supply is given.
Sensing distance is more than
inductive or capacitive
proximity sensors’ sensing
device (Alamri et al., 2013).
Problem in
receiving signals
from curved, small,
soft and thin objects
are the
disadvantages with
this device.
Weather monitoring.
Smart sleep system.
Smart lightning.
Smart washing
machine.
Smart internet mirror
In medical, Blood
Pressure monitoring.
RFID RFID used for tagging are
completely secured and cannot
be duplicated
Messages can be exchanged
from long distances
There are various types of
RFID which can be applicable
for all the conditions (Garrido
Less reliable as it is
harder to understand
More expensive
than Barcode
system.
Longer than the
Barcode labels in
It is widely used for
tracking products in
which RFID are
implemented to
detect the location of
the product or item.
Apparel,
pharmaceutical
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
6
INTERNET OF THINGS
Azevedo & Carvalho, 2012).
Data base for this device is
portable and long read range.
The device is much effective
and efficient, means less
chances of errors
size.
Mostly can be used
for tagging only.
At a particular time
more than one RFID
can respond
jewellery tracking,
and baggage tracking
(Gubbi et al., 2013).
It has replaced
barcode systems in
the libraries
It has also
application in the
museum, school and
the universities.
Implantable RFID
are used in the
animal identification
too.
Video
Tracking
Collects information
Automation and control.
Communication between
devices.
Monitoring work places and
project procedures
Livelihood can be improved.
Unavailability of
international
standard
compatibility for
video tracking
equipments.
This system is
highly complex as
compared to other
Augmentation of
reality
Human-computer
interaction.
Video
communication.
Medical imaging.
INTERNET OF THINGS
Azevedo & Carvalho, 2012).
Data base for this device is
portable and long read range.
The device is much effective
and efficient, means less
chances of errors
size.
Mostly can be used
for tagging only.
At a particular time
more than one RFID
can respond
jewellery tracking,
and baggage tracking
(Gubbi et al., 2013).
It has replaced
barcode systems in
the libraries
It has also
application in the
museum, school and
the universities.
Implantable RFID
are used in the
animal identification
too.
Video
Tracking
Collects information
Automation and control.
Communication between
devices.
Monitoring work places and
project procedures
Livelihood can be improved.
Unavailability of
international
standard
compatibility for
video tracking
equipments.
This system is
highly complex as
compared to other
Augmentation of
reality
Human-computer
interaction.
Video
communication.
Medical imaging.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7
INTERNET OF THINGS
IoT devices.
Privacy and security
issues are related to
this implication.
Answer 4:
Security and Privacy Issues in IoT Implications
The new and innovative implications of IoT devices in the technologies are improving
the livelihood but also leading towards the security threats of those individuals. Firstly, based on
the examples in question one it can be seen that and unauthorized individual can have access to
the application and the key which has sensor and use the car for own purpose (Sicari et al.,
2015). These implications can be used as a bridge for the unauthorized users or hackers, who can
manipulate or compromise the information of and data by certain coding. This new implication
involves personal data and information which are vulnerable to the attack and can lead to several
privacy issues to the individuals.
Answer 5:
Blocking mode:
In this process, the endpoint originated from the operating side request will take a while
to get a response of its requested message. The technique used for measuring the water level in
this case is a synchronous case which will not allow receiving the asynchronous message
(Swetina et al., 2014). In this technology Originator will be responsible for initiating the
exchange of the information between both the receiver and the originator sides.
INTERNET OF THINGS
IoT devices.
Privacy and security
issues are related to
this implication.
Answer 4:
Security and Privacy Issues in IoT Implications
The new and innovative implications of IoT devices in the technologies are improving
the livelihood but also leading towards the security threats of those individuals. Firstly, based on
the examples in question one it can be seen that and unauthorized individual can have access to
the application and the key which has sensor and use the car for own purpose (Sicari et al.,
2015). These implications can be used as a bridge for the unauthorized users or hackers, who can
manipulate or compromise the information of and data by certain coding. This new implication
involves personal data and information which are vulnerable to the attack and can lead to several
privacy issues to the individuals.
Answer 5:
Blocking mode:
In this process, the endpoint originated from the operating side request will take a while
to get a response of its requested message. The technique used for measuring the water level in
this case is a synchronous case which will not allow receiving the asynchronous message
(Swetina et al., 2014). In this technology Originator will be responsible for initiating the
exchange of the information between both the receiver and the originator sides.
8
INTERNET OF THINGS
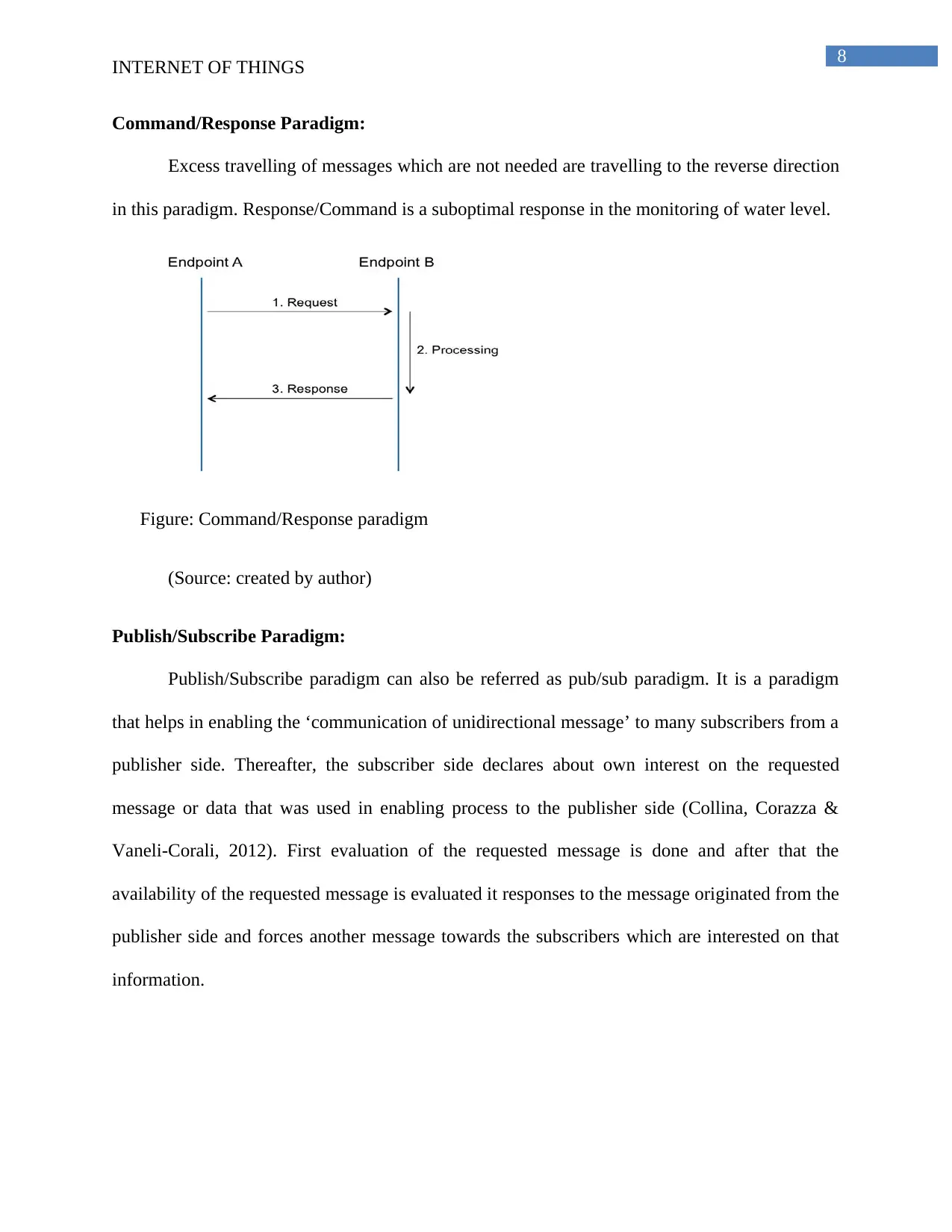
Command/Response Paradigm:
Excess travelling of messages which are not needed are travelling to the reverse direction
in this paradigm. Response/Command is a suboptimal response in the monitoring of water level.
Figure: Command/Response paradigm
(Source: created by author)
Publish/Subscribe Paradigm:
Publish/Subscribe paradigm can also be referred as pub/sub paradigm. It is a paradigm
that helps in enabling the ‘communication of unidirectional message’ to many subscribers from a
publisher side. Thereafter, the subscriber side declares about own interest on the requested
message or data that was used in enabling process to the publisher side (Collina, Corazza &
Vaneli-Corali, 2012). First evaluation of the requested message is done and after that the
availability of the requested message is evaluated it responses to the message originated from the
publisher side and forces another message towards the subscribers which are interested on that
information.
INTERNET OF THINGS
Command/Response Paradigm:
Excess travelling of messages which are not needed are travelling to the reverse direction
in this paradigm. Response/Command is a suboptimal response in the monitoring of water level.
Figure: Command/Response paradigm
(Source: created by author)
Publish/Subscribe Paradigm:
Publish/Subscribe paradigm can also be referred as pub/sub paradigm. It is a paradigm
that helps in enabling the ‘communication of unidirectional message’ to many subscribers from a
publisher side. Thereafter, the subscriber side declares about own interest on the requested
message or data that was used in enabling process to the publisher side (Collina, Corazza &
Vaneli-Corali, 2012). First evaluation of the requested message is done and after that the
availability of the requested message is evaluated it responses to the message originated from the
publisher side and forces another message towards the subscribers which are interested on that
information.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

9
INTERNET OF THINGS
Figure: Publish-Subscribe Paradigm
(Source: created by author)
Using Pub/Sub Model in Lieu of the Command/Response Paradigm
6ms will be saved in the propagation delay between the sensor and the application and
1ms will be saved in receiving that message. Thus, total time saving will be 6ms + 1ms which
equals 7ms.
Answer 6:
Nielson’s Law
Based on the data collected on the internet users every year, Nielson stated law, which
states that the “growth of bandwidth of users is increasing by 50 % per year” (Nielson, 2014).
Nielson’s law states, “A high-end user’s collection speed grows by 50% per year” and proposed
the following graph:
INTERNET OF THINGS
Figure: Publish-Subscribe Paradigm
(Source: created by author)
Using Pub/Sub Model in Lieu of the Command/Response Paradigm
6ms will be saved in the propagation delay between the sensor and the application and
1ms will be saved in receiving that message. Thus, total time saving will be 6ms + 1ms which
equals 7ms.
Answer 6:
Nielson’s Law
Based on the data collected on the internet users every year, Nielson stated law, which
states that the “growth of bandwidth of users is increasing by 50 % per year” (Nielson, 2014).
Nielson’s law states, “A high-end user’s collection speed grows by 50% per year” and proposed
the following graph:
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
10
INTERNET OF THINGS
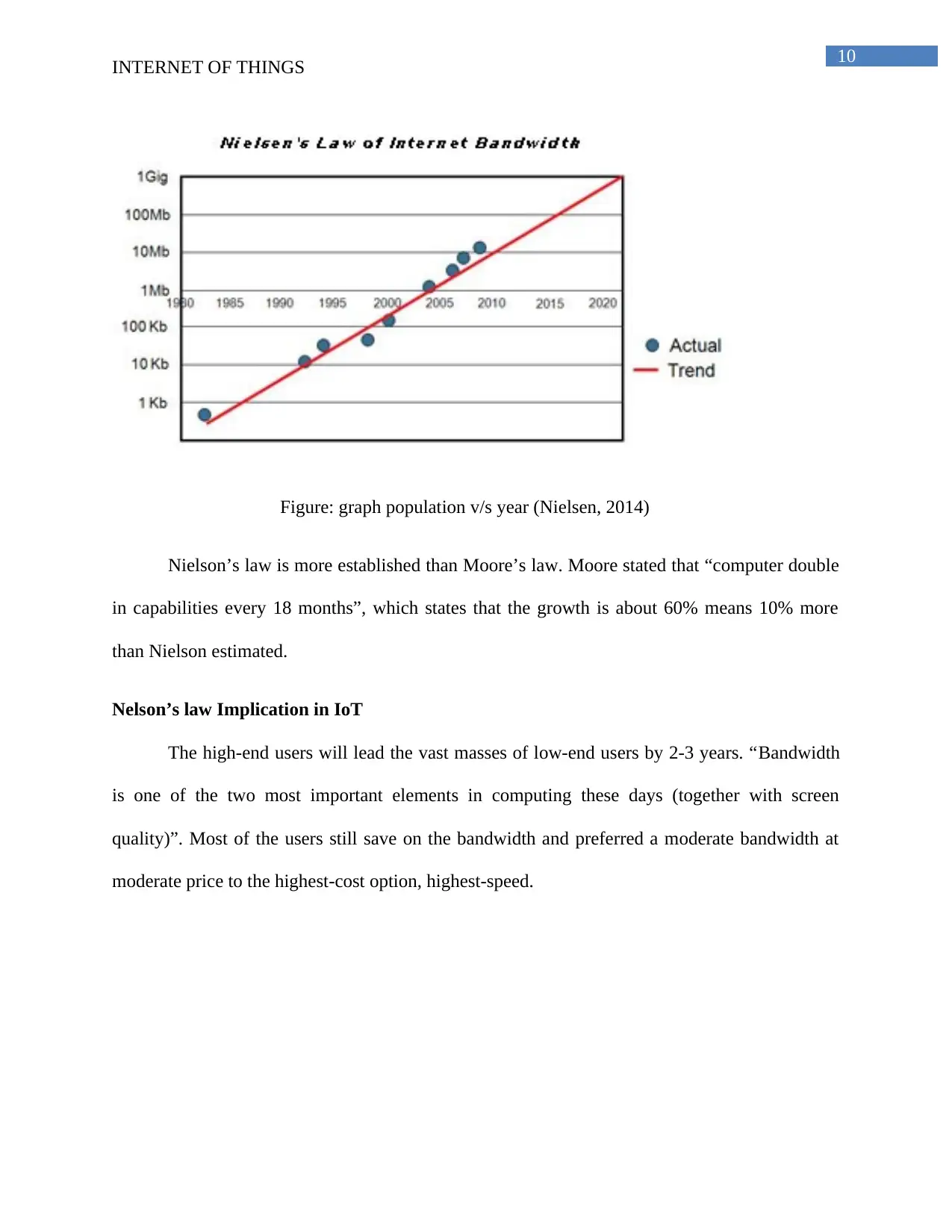
Figure: graph population v/s year (Nielsen, 2014)
Nielson’s law is more established than Moore’s law. Moore stated that “computer double
in capabilities every 18 months”, which states that the growth is about 60% means 10% more
than Nielson estimated.
Nelson’s law Implication in IoT
The high-end users will lead the vast masses of low-end users by 2-3 years. “Bandwidth
is one of the two most important elements in computing these days (together with screen
quality)”. Most of the users still save on the bandwidth and preferred a moderate bandwidth at
moderate price to the highest-cost option, highest-speed.
INTERNET OF THINGS
Figure: graph population v/s year (Nielsen, 2014)
Nielson’s law is more established than Moore’s law. Moore stated that “computer double
in capabilities every 18 months”, which states that the growth is about 60% means 10% more
than Nielson estimated.
Nelson’s law Implication in IoT
The high-end users will lead the vast masses of low-end users by 2-3 years. “Bandwidth
is one of the two most important elements in computing these days (together with screen
quality)”. Most of the users still save on the bandwidth and preferred a moderate bandwidth at
moderate price to the highest-cost option, highest-speed.

11
INTERNET OF THINGS
References:
Al Agha, M. T., Amin Babiker, A., & Mustafa, N. Applying The Analytical Hierarchy Process
To Select The Transmission Lines Type In Telecoms.
Alamri, A., Ansari, W. S., Hassan, M. M., Hossain, M. S., Alelaiwi, A., & Hossain, M. A.
(2013). A survey on sensor-cloud: architecture, applications, and
approaches. International Journal of Distributed Sensor Networks, 9(2), 917923.
Alimam, F. E. R. A. M. (2015). Fiber Optics Access Network Planning(Doctoral dissertation,
Sudan University of Science and Technology).
Collina, M., Corazza, G. E., & Vanelli-Coralli, A. (2012, September). Introducing the QEST
broker: Scaling the IoT by bridging MQTT and REST. In Personal indoor and mobile
radio communications (pimrc), 2012 ieee 23rd international symposium on (pp. 36-41).
IEEE.
Garrido Azevedo, S., & Carvalho, H. (2012). Contribution of RFID technology to better
management of fashion supply chains. International Journal of Retail & Distribution
Management, 40(2), 128-156.
Nielsen, J. (2014). Nielsen’s Law of Internet Bandwidth, 1998.
Rayes, A., & Salam, S. (2017). Internet of Things (IoT) Overview. In Internet of Things From
Hype to Reality (pp. 1-34). Springer International Publishing.
Rayes, A., & Samer, S. (2017). Internet of Things—From Hype to Reality. Springer International
Publishing, Cham, Switzerland.
INTERNET OF THINGS
References:
Al Agha, M. T., Amin Babiker, A., & Mustafa, N. Applying The Analytical Hierarchy Process
To Select The Transmission Lines Type In Telecoms.
Alamri, A., Ansari, W. S., Hassan, M. M., Hossain, M. S., Alelaiwi, A., & Hossain, M. A.
(2013). A survey on sensor-cloud: architecture, applications, and
approaches. International Journal of Distributed Sensor Networks, 9(2), 917923.
Alimam, F. E. R. A. M. (2015). Fiber Optics Access Network Planning(Doctoral dissertation,
Sudan University of Science and Technology).
Collina, M., Corazza, G. E., & Vanelli-Coralli, A. (2012, September). Introducing the QEST
broker: Scaling the IoT by bridging MQTT and REST. In Personal indoor and mobile
radio communications (pimrc), 2012 ieee 23rd international symposium on (pp. 36-41).
IEEE.
Garrido Azevedo, S., & Carvalho, H. (2012). Contribution of RFID technology to better
management of fashion supply chains. International Journal of Retail & Distribution
Management, 40(2), 128-156.
Nielsen, J. (2014). Nielsen’s Law of Internet Bandwidth, 1998.
Rayes, A., & Salam, S. (2017). Internet of Things (IoT) Overview. In Internet of Things From
Hype to Reality (pp. 1-34). Springer International Publishing.
Rayes, A., & Samer, S. (2017). Internet of Things—From Hype to Reality. Springer International
Publishing, Cham, Switzerland.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 12
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2025 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





