Internet of Things Assignment: University Name, Semester 1
VerifiedAdded on 2020/02/24
|10
|2461
|49
Homework Assignment
AI Summary
This comprehensive assignment on the Internet of Things (IoT) covers a range of topics, including the concept of a "no user interface" system and its benefits, exemplified by car and payment gateway applications. It details cable specifications, categorizing coaxial, twisted pair, and fiber optic cables based on bandwidth, distance, interference rating, cost, and security. The assignment analyzes the advantages, disadvantages, and applications of various IoT devices such as sensors, RFID, and video tracking. It also addresses security and privacy issues inherent in IoT systems. Furthermore, it explains communication paradigms like blocking mode and publish/subscribe, and command/response paradigms. Finally, the assignment explores Nielson's Law and its relevance to IoT, including its relation to Moore's Law and implications for sensor technology and data stream creation.

Running head: INTERNET OF THINGS
Internet of Things
Name of the Student:
Student ID:
Name of the University:
Author’s note:
Internet of Things
Name of the Student:
Student ID:
Name of the University:
Author’s note:
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1INTERNET OF THINGS
Answer 1
The explanation of the phrase “the best interface for a system is no user interface” is that
it eliminates the development of the user interface for executing the application function at any
technology. It would eliminate the scope for requirement of an interface while processing the
functions of the application by using the technology. The requirement of extra time for the user
to operate in the system would be relinquished by using the no user interface system. The
number of steps required for the operation of the project would be decreased by using the no
interface system in the applications. The benefit of the phrase “the best interface for a system is
no user interface” can be explained with the help of following examples,
Example 1: The functions of the cars have been developed with the help of new user
interface for opening the gate of the car by using the wireless mobile network (Takai et al.,
2013). The number of steps in the opening or closing of the door have been increased as the user
first have to open the application in the mobile device, then go to the option of opening the car
door from the mobile, and request for opening the gate of the car. The network connection would
send the request for opening the door to the server. The server would search for the appropriate
network of the car and it would forward the query to the network. The car would receive the
request and it would process for opening the door. It would be time consuming and the overall
time duration of the project would be very high. The need for the user interface could be reduced
for forming the minimum time duration requirement for the project.
Example 2: The payment through gateway would be deployed for forming the
improvement of the operations and it had formed the effective role in the payment through
development process (Fisher, 2013). The payment gateway would comprise of making the
Answer 1
The explanation of the phrase “the best interface for a system is no user interface” is that
it eliminates the development of the user interface for executing the application function at any
technology. It would eliminate the scope for requirement of an interface while processing the
functions of the application by using the technology. The requirement of extra time for the user
to operate in the system would be relinquished by using the no user interface system. The
number of steps required for the operation of the project would be decreased by using the no
interface system in the applications. The benefit of the phrase “the best interface for a system is
no user interface” can be explained with the help of following examples,
Example 1: The functions of the cars have been developed with the help of new user
interface for opening the gate of the car by using the wireless mobile network (Takai et al.,
2013). The number of steps in the opening or closing of the door have been increased as the user
first have to open the application in the mobile device, then go to the option of opening the car
door from the mobile, and request for opening the gate of the car. The network connection would
send the request for opening the door to the server. The server would search for the appropriate
network of the car and it would forward the query to the network. The car would receive the
request and it would process for opening the door. It would be time consuming and the overall
time duration of the project would be very high. The need for the user interface could be reduced
for forming the minimum time duration requirement for the project.
Example 2: The payment through gateway would be deployed for forming the
improvement of the operations and it had formed the effective role in the payment through
development process (Fisher, 2013). The payment gateway would comprise of making the
2INTERNET OF THINGS
appropriate formation of the system development. However, the payment gateway would
comprise of a number of steps first signing in the platform application, requesting the payment
through the bank server, the bank would process the payment, and the payment would be
received. All these processes are involved in the payment gateway platform and it would result in
forming the issue of exhaustion of resources. The removal of user interface would result in
forming the solution for exhaustion of resources and would increase the process of payment
system.
Answer 2
The specification of the cables and the categorization of the cables had been done in the
following tables,
Cable Types Coaxial Cable Twisted Pair Cable Fiber Optic Cable
Bandwidth 1GHz 1MHz 75THz
Distance 500m 100m 10 Km when on Single
mode
2Km when on Multi
mode
Interference
rating
Has the tendency of being
least vulnerable to
interference when compare
to the other two types of
cables
Has the tendency of
being limited to
distance and vulnerable
to interference
Has the tendency of
not being vulnerable to
the interference
Cost Medium costing of the cable
when compare to the other
two types of cables
Cheaper than the other
two types of cables
Highest expensive
when compare to the
other two types of
cables
Security As opined by Winzer (2014),
the security would be
moderate when compare to
the other two types of cables
Very Poor in compare
to the other two types
of cables
It is the most secured
type of cable that can
be used for network
connection
appropriate formation of the system development. However, the payment gateway would
comprise of a number of steps first signing in the platform application, requesting the payment
through the bank server, the bank would process the payment, and the payment would be
received. All these processes are involved in the payment gateway platform and it would result in
forming the issue of exhaustion of resources. The removal of user interface would result in
forming the solution for exhaustion of resources and would increase the process of payment
system.
Answer 2
The specification of the cables and the categorization of the cables had been done in the
following tables,
Cable Types Coaxial Cable Twisted Pair Cable Fiber Optic Cable
Bandwidth 1GHz 1MHz 75THz
Distance 500m 100m 10 Km when on Single
mode
2Km when on Multi
mode
Interference
rating
Has the tendency of being
least vulnerable to
interference when compare
to the other two types of
cables
Has the tendency of
being limited to
distance and vulnerable
to interference
Has the tendency of
not being vulnerable to
the interference
Cost Medium costing of the cable
when compare to the other
two types of cables
Cheaper than the other
two types of cables
Highest expensive
when compare to the
other two types of
cables
Security As opined by Winzer (2014),
the security would be
moderate when compare to
the other two types of cables
Very Poor in compare
to the other two types
of cables
It is the most secured
type of cable that can
be used for network
connection
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3INTERNET OF THINGS
Specification of the cables’ categories
1. Co-Axial Cable: According to Ha et al. (2013), there are three types of Co-Axial
Cable namely Type 1, Type 2, and Type 3. The Type 1 Co-Axial cable has the specification of
50 Ohm, RG-11 or Rg-7, and it is applicable for thick power Ethernet. The Type 2 Co-Axial
cable has the specification of 50 Ohm, RG-58, and it is applicable with thin power Internet. The
Type 3 Co-Axial cable has the specification of 75 Ohm, RG-59, and it is applicable with cable
television.
2. Twister Pair Cable: According to Lee et al. (2013), there are three types of
Unprotected Twister Pair Cable namely Type 1, Type 2, and Type 3. The Type 1 Unprotected
Twister Pair cable is basically used for telephone lines and low speed internet data cable. The
Type 2 Shielded Twisted Pair cable is basically used for supporting the 4 MPS implementation.
The Type 3 Foil Shielded Twister Pair cable is basically used for supporting maximum 16 MPS
(although it is used for 10 MPS only).
3. Fibre Optic Cable: There are three types of Fibre Optic Cable and they are Single
Mode Fibre Optic Cable, Multi Mode Fibre Optic Cable, and Plastic Fibre Optic Cable. These
three cables have different ranges of 2Km, 10Km, and 16km respectively.
Answer 3
The following table would analyse the advantages, disadvantages, and application of
using Internet of Things,
IoT Devices: Sensors
Advantages: High current capability and low cost of maintenance for forming the low tech
sensing.
Specification of the cables’ categories
1. Co-Axial Cable: According to Ha et al. (2013), there are three types of Co-Axial
Cable namely Type 1, Type 2, and Type 3. The Type 1 Co-Axial cable has the specification of
50 Ohm, RG-11 or Rg-7, and it is applicable for thick power Ethernet. The Type 2 Co-Axial
cable has the specification of 50 Ohm, RG-58, and it is applicable with thin power Internet. The
Type 3 Co-Axial cable has the specification of 75 Ohm, RG-59, and it is applicable with cable
television.
2. Twister Pair Cable: According to Lee et al. (2013), there are three types of
Unprotected Twister Pair Cable namely Type 1, Type 2, and Type 3. The Type 1 Unprotected
Twister Pair cable is basically used for telephone lines and low speed internet data cable. The
Type 2 Shielded Twisted Pair cable is basically used for supporting the 4 MPS implementation.
The Type 3 Foil Shielded Twister Pair cable is basically used for supporting maximum 16 MPS
(although it is used for 10 MPS only).
3. Fibre Optic Cable: There are three types of Fibre Optic Cable and they are Single
Mode Fibre Optic Cable, Multi Mode Fibre Optic Cable, and Plastic Fibre Optic Cable. These
three cables have different ranges of 2Km, 10Km, and 16km respectively.
Answer 3
The following table would analyse the advantages, disadvantages, and application of
using Internet of Things,
IoT Devices: Sensors
Advantages: High current capability and low cost of maintenance for forming the low tech
sensing.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
4INTERNET OF THINGS
Disadvantages: The sensor would require the physical contact and it is slow in response
Application: Interlocking, Packaging, and parts detection
IoT Devices: RFID
Advantages: Can be read without the use of line of sight and multiple tags are allowed
Disadvantages: Costly in use and a number of processing are involved
Application: Tracking of products like jewellery, pallet, and apparel tracking
IoT Devices: Video Tracking
Advantages: Effective communication and automation of the control functions
Disadvantages: Complex system and privacy exposure is probable
Application: Human to computer interaction and the augmentation of the reality is possible
Answer 4
Security Issues: According to Suo et al. (2012), the security issues can be described as
the harms on the IoT applications that can be occurred due to unauthorized access resulting in
misuse of the information for their personal benefits.
Privacy Issues: As opined by Borgohian, Kumar and Sanyal (2015) the direct
involvement of the private and sensitive information as such account details, precise geo-location
and health location have to face the issue of exposure of the personal information such as
physical condition, habits, and locations.
Answer 5
Blocking Mode-> The blocking mode is characterized by the occurrence of the operating
request of the user and orientation of the endpoint for involving the longer and waiting times of
Disadvantages: The sensor would require the physical contact and it is slow in response
Application: Interlocking, Packaging, and parts detection
IoT Devices: RFID
Advantages: Can be read without the use of line of sight and multiple tags are allowed
Disadvantages: Costly in use and a number of processing are involved
Application: Tracking of products like jewellery, pallet, and apparel tracking
IoT Devices: Video Tracking
Advantages: Effective communication and automation of the control functions
Disadvantages: Complex system and privacy exposure is probable
Application: Human to computer interaction and the augmentation of the reality is possible
Answer 4
Security Issues: According to Suo et al. (2012), the security issues can be described as
the harms on the IoT applications that can be occurred due to unauthorized access resulting in
misuse of the information for their personal benefits.
Privacy Issues: As opined by Borgohian, Kumar and Sanyal (2015) the direct
involvement of the private and sensitive information as such account details, precise geo-location
and health location have to face the issue of exposure of the personal information such as
physical condition, habits, and locations.
Answer 5
Blocking Mode-> The blocking mode is characterized by the occurrence of the operating
request of the user and orientation of the endpoint for involving the longer and waiting times of
5INTERNET OF THINGS
operation. The blocking mode is a synchronous mode where the original message would not be
received by the originator.
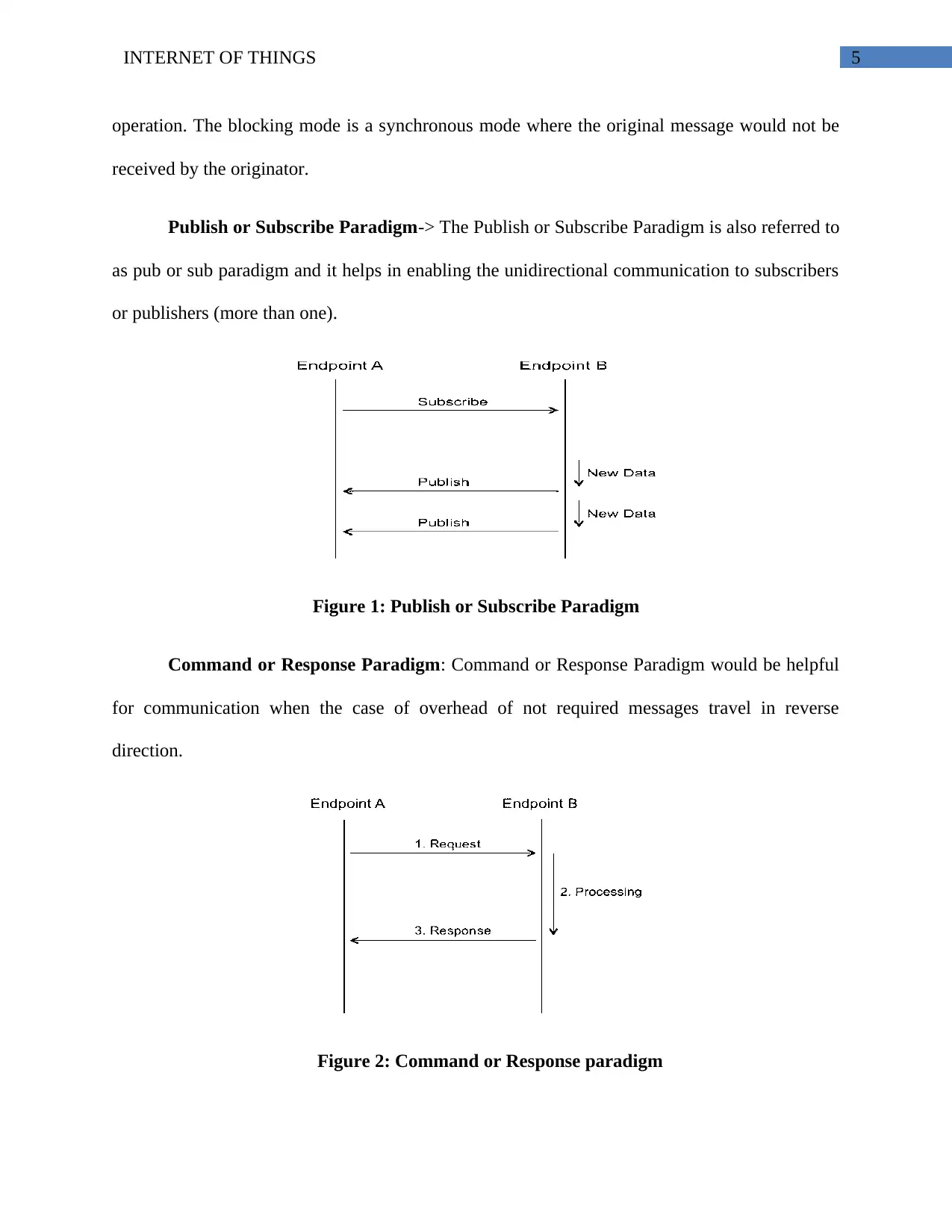
Publish or Subscribe Paradigm-> The Publish or Subscribe Paradigm is also referred to
as pub or sub paradigm and it helps in enabling the unidirectional communication to subscribers
or publishers (more than one).
Figure 1: Publish or Subscribe Paradigm
Command or Response Paradigm: Command or Response Paradigm would be helpful
for communication when the case of overhead of not required messages travel in reverse
direction.
Figure 2: Command or Response paradigm
operation. The blocking mode is a synchronous mode where the original message would not be
received by the originator.
Publish or Subscribe Paradigm-> The Publish or Subscribe Paradigm is also referred to
as pub or sub paradigm and it helps in enabling the unidirectional communication to subscribers
or publishers (more than one).
Figure 1: Publish or Subscribe Paradigm
Command or Response Paradigm: Command or Response Paradigm would be helpful
for communication when the case of overhead of not required messages travel in reverse
direction.
Figure 2: Command or Response paradigm
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
6INTERNET OF THINGS
Total time saving= propagation delay of 12ms + time required for receiving the message 1ms
= 13ms
Answer 6
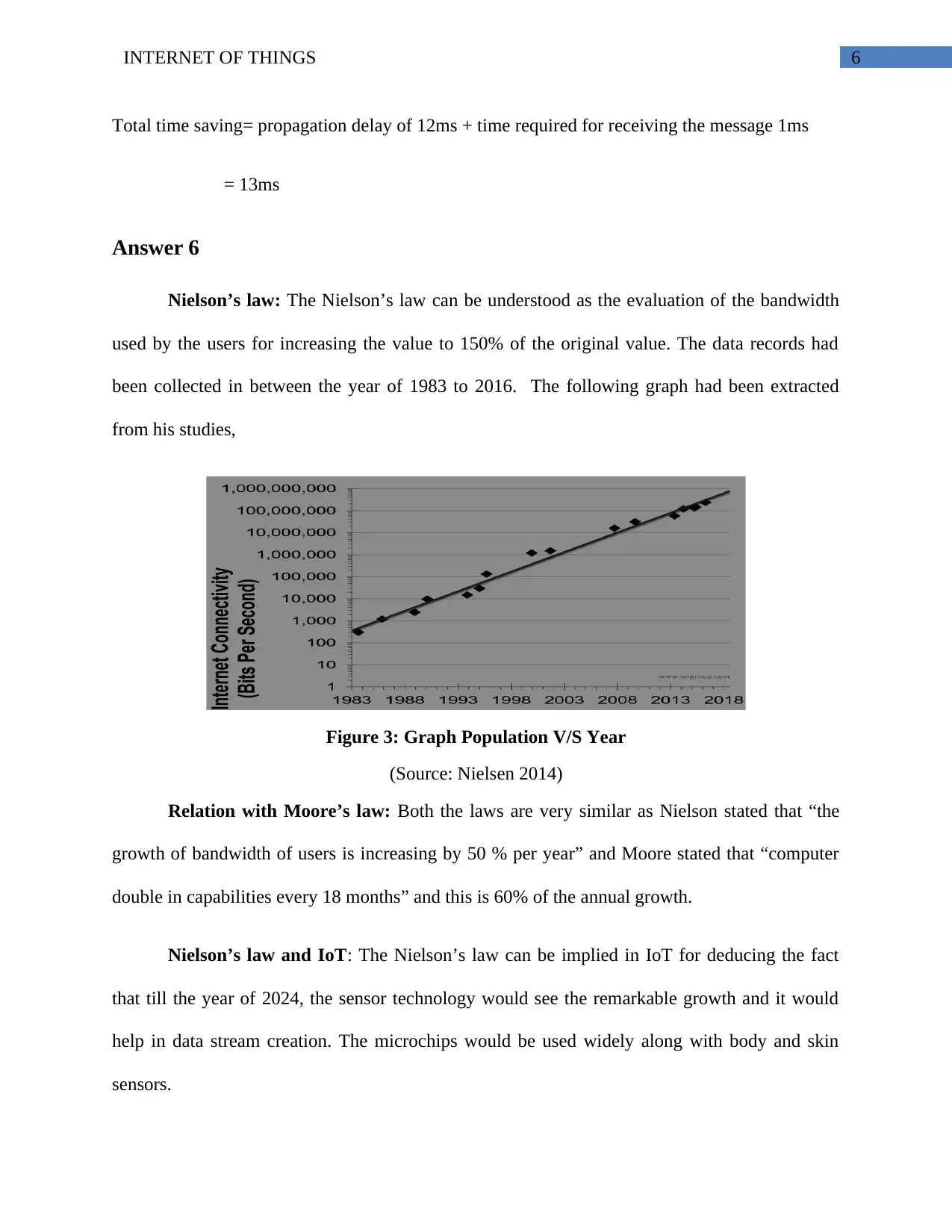
Nielson’s law: The Nielson’s law can be understood as the evaluation of the bandwidth
used by the users for increasing the value to 150% of the original value. The data records had
been collected in between the year of 1983 to 2016. The following graph had been extracted
from his studies,
Figure 3: Graph Population V/S Year
(Source: Nielsen 2014)
Relation with Moore’s law: Both the laws are very similar as Nielson stated that “the
growth of bandwidth of users is increasing by 50 % per year” and Moore stated that “computer
double in capabilities every 18 months” and this is 60% of the annual growth.
Nielson’s law and IoT: The Nielson’s law can be implied in IoT for deducing the fact
that till the year of 2024, the sensor technology would see the remarkable growth and it would
help in data stream creation. The microchips would be used widely along with body and skin
sensors.
Total time saving= propagation delay of 12ms + time required for receiving the message 1ms
= 13ms
Answer 6
Nielson’s law: The Nielson’s law can be understood as the evaluation of the bandwidth
used by the users for increasing the value to 150% of the original value. The data records had
been collected in between the year of 1983 to 2016. The following graph had been extracted
from his studies,
Figure 3: Graph Population V/S Year
(Source: Nielsen 2014)
Relation with Moore’s law: Both the laws are very similar as Nielson stated that “the
growth of bandwidth of users is increasing by 50 % per year” and Moore stated that “computer
double in capabilities every 18 months” and this is 60% of the annual growth.
Nielson’s law and IoT: The Nielson’s law can be implied in IoT for deducing the fact
that till the year of 2024, the sensor technology would see the remarkable growth and it would
help in data stream creation. The microchips would be used widely along with body and skin
sensors.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7INTERNET OF THINGS
References
Borgohain, T., Kumar, U., & Sanyal, S. (2015). Survey of security and privacy issues of Internet
of Things. arXiv preprint arXiv:1501.02211.
Fisher, M. (2013). U.S. Patent No. 8,352,323. Washington, DC: U.S. Patent and Trademark
Office.
Ha, S. K., Kim, G. S., Choi, S. M., Kim, S. K., Kim, J. G., Park, M., ... & Sim, K. (2013). PHILS
based protection system design for an HTS power cable installed in a grid. 대대대대대대 대대대대 대대대,
339-340.
Lee, W., Cheon, M., Hyun, C. H., & Park, M. (2013). Development of building fire safety
system with automatic security firm monitoring capability. Fire safety journal, 58, 65-73.
Nielsen, J. (2014). Nielsen’s Law of Internet Bandwidth, 1998.
Singh, D., Tripathi, G., & Jara, A. J. (2014, March). A survey of Internet-of-Things: Future
vision, architecture, challenges and services. In Internet of things (WF-IoT), 2014 IEEE world
forum on (pp. 287-292). IEEE.
Sommer, J., & Franz, W. (2012). A Component-based Simulation Model and its Implementation
of a Switched Ethernet Network.
Suo, H., Wan, J., Zou, C., & Liu, J. (2012, March). Security in the internet of things: a review.
In Computer Science and Electronics Engineering (ICCSEE), 2012 international conference
on (Vol. 3, pp. 648-651). IEEE.
References
Borgohain, T., Kumar, U., & Sanyal, S. (2015). Survey of security and privacy issues of Internet
of Things. arXiv preprint arXiv:1501.02211.
Fisher, M. (2013). U.S. Patent No. 8,352,323. Washington, DC: U.S. Patent and Trademark
Office.
Ha, S. K., Kim, G. S., Choi, S. M., Kim, S. K., Kim, J. G., Park, M., ... & Sim, K. (2013). PHILS
based protection system design for an HTS power cable installed in a grid. 대대대대대대 대대대대 대대대,
339-340.
Lee, W., Cheon, M., Hyun, C. H., & Park, M. (2013). Development of building fire safety
system with automatic security firm monitoring capability. Fire safety journal, 58, 65-73.
Nielsen, J. (2014). Nielsen’s Law of Internet Bandwidth, 1998.
Singh, D., Tripathi, G., & Jara, A. J. (2014, March). A survey of Internet-of-Things: Future
vision, architecture, challenges and services. In Internet of things (WF-IoT), 2014 IEEE world
forum on (pp. 287-292). IEEE.
Sommer, J., & Franz, W. (2012). A Component-based Simulation Model and its Implementation
of a Switched Ethernet Network.
Suo, H., Wan, J., Zou, C., & Liu, J. (2012, March). Security in the internet of things: a review.
In Computer Science and Electronics Engineering (ICCSEE), 2012 international conference
on (Vol. 3, pp. 648-651). IEEE.

8INTERNET OF THINGS
Takai, I., Ito, S., Yasutomi, K., Kagawa, K., Andoh, M., & Kawahito, S. (2013). LED and
CMOS image sensor based optical wireless communication system for automotive
applications. IEEE Photonics Journal, 5(5), 6801418-6801418.
Tozlu, S., Senel, M., Mao, W., & Keshavarzian, A. (2012). Wi-Fi enabled sensors for internet of
things: A practical approach. IEEE Communications Magazine, 50(6).
Winzer, P. J. (2014). Spatial multiplexing in fiber optics: The 10x scaling of metro/core
capacities. Bell Labs Technical Journal, 19, 22-30.
Borgohain, T., Kumar, U., & Sanyal, S. (2015). Survey of security and privacy issues of Internet
of Things. arXiv preprint arXiv:1501.02211.
Fisher, M. (2013). U.S. Patent No. 8,352,323. Washington, DC: U.S. Patent and Trademark
Office.
Ha, S. K., Kim, G. S., Choi, S. M., Kim, S. K., Kim, J. G., Park, M., ... & Sim, K. (2013). PHILS
based protection system design for an HTS power cable installed in a grid. 대 대 대 대 대 대
대대대대 대대대, 339-340.
Lee, W., Cheon, M., Hyun, C. H., & Park, M. (2013). Development of building fire safety
system with automatic security firm monitoring capability. Fire safety journal, 58, 65-73.
Nielsen, J. (2014). Nielsen’s Law of Internet Bandwidth, 1998.
Singh, D., Tripathi, G., & Jara, A. J. (2014, March). A survey of Internet-of-Things: Future
vision, architecture, challenges and services. In Internet of things (WF-IoT), 2014 IEEE
world forum on (pp. 287-292). IEEE.
Takai, I., Ito, S., Yasutomi, K., Kagawa, K., Andoh, M., & Kawahito, S. (2013). LED and
CMOS image sensor based optical wireless communication system for automotive
applications. IEEE Photonics Journal, 5(5), 6801418-6801418.
Tozlu, S., Senel, M., Mao, W., & Keshavarzian, A. (2012). Wi-Fi enabled sensors for internet of
things: A practical approach. IEEE Communications Magazine, 50(6).
Winzer, P. J. (2014). Spatial multiplexing in fiber optics: The 10x scaling of metro/core
capacities. Bell Labs Technical Journal, 19, 22-30.
Borgohain, T., Kumar, U., & Sanyal, S. (2015). Survey of security and privacy issues of Internet
of Things. arXiv preprint arXiv:1501.02211.
Fisher, M. (2013). U.S. Patent No. 8,352,323. Washington, DC: U.S. Patent and Trademark
Office.
Ha, S. K., Kim, G. S., Choi, S. M., Kim, S. K., Kim, J. G., Park, M., ... & Sim, K. (2013). PHILS
based protection system design for an HTS power cable installed in a grid. 대 대 대 대 대 대
대대대대 대대대, 339-340.
Lee, W., Cheon, M., Hyun, C. H., & Park, M. (2013). Development of building fire safety
system with automatic security firm monitoring capability. Fire safety journal, 58, 65-73.
Nielsen, J. (2014). Nielsen’s Law of Internet Bandwidth, 1998.
Singh, D., Tripathi, G., & Jara, A. J. (2014, March). A survey of Internet-of-Things: Future
vision, architecture, challenges and services. In Internet of things (WF-IoT), 2014 IEEE
world forum on (pp. 287-292). IEEE.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

9INTERNET OF THINGS
Sommer, J., & Franz, W. (2012). A Component-based Simulation Model and its Implementation
of a Switched Ethernet Network.
Suo, H., Wan, J., Zou, C., & Liu, J. (2012, March). Security in the internet of things: a review.
In Computer Science and Electronics Engineering (ICCSEE), 2012 international
conference on (Vol. 3, pp. 648-651). IEEE.
Takai, I., Ito, S., Yasutomi, K., Kagawa, K., Andoh, M., & Kawahito, S. (2013). LED and
CMOS image sensor based optical wireless communication system for automotive
applications. IEEE Photonics Journal, 5(5), 6801418-6801418.
Tozlu, S., Senel, M., Mao, W., & Keshavarzian, A. (2012). Wi-Fi enabled sensors for internet of
things: A practical approach. IEEE Communications Magazine, 50(6).
Winzer, P. J. (2014). Spatial multiplexing in fiber optics: The 10x scaling of metro/core
capacities. Bell Labs Technical Journal, 19, 22-30.
Sommer, J., & Franz, W. (2012). A Component-based Simulation Model and its Implementation
of a Switched Ethernet Network.
Suo, H., Wan, J., Zou, C., & Liu, J. (2012, March). Security in the internet of things: a review.
In Computer Science and Electronics Engineering (ICCSEE), 2012 international
conference on (Vol. 3, pp. 648-651). IEEE.
Takai, I., Ito, S., Yasutomi, K., Kagawa, K., Andoh, M., & Kawahito, S. (2013). LED and
CMOS image sensor based optical wireless communication system for automotive
applications. IEEE Photonics Journal, 5(5), 6801418-6801418.
Tozlu, S., Senel, M., Mao, W., & Keshavarzian, A. (2012). Wi-Fi enabled sensors for internet of
things: A practical approach. IEEE Communications Magazine, 50(6).
Winzer, P. J. (2014). Spatial multiplexing in fiber optics: The 10x scaling of metro/core
capacities. Bell Labs Technical Journal, 19, 22-30.
1 out of 10
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2025 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





