Analysis of IoT: Cables, Paradigms, Security, and Nielsen's Law
VerifiedAdded on 2020/02/24
|10
|1621
|480
Report
AI Summary
This report provides a comprehensive overview of the Internet of Things (IoT). It begins by discussing the concept of eliminating user interfaces for improved efficiency and provides examples. The report then details different types of cables (Twisted Pair, Coaxial, Fiber Optic), their specifications, advantages, disadvantages, and applications. A table summarizes the advantages, disadvantages, and applications of various IoT devices, including sensors, RFID, and video tracking. The report also addresses security vulnerabilities within IoT, highlighting the importance of addressing these issues. It explains communication paradigms, such as blocking mode and publish-subscribe, and compares command/response paradigms. Finally, the report touches upon Nielsen's Law and its implications for IoT, particularly in relation to bandwidth growth and the potential for increased sensor implementation.

Running head: INTERNET OF THINGS
INTERNET OF THINGS
Name of the Student
Name of the University
Author Note
INTERNET OF THINGS
Name of the Student
Name of the University
Author Note
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

2INTERNET OF THINGS
Table of Contents
Question 1........................................................................................................................................3
Question 2........................................................................................................................................3
Question 3........................................................................................................................................4
Question 4........................................................................................................................................5
Question 5........................................................................................................................................6
Question 6........................................................................................................................................7
References........................................................................................................................................8
Table of Contents
Question 1........................................................................................................................................3
Question 2........................................................................................................................................3
Question 3........................................................................................................................................4
Question 4........................................................................................................................................5
Question 5........................................................................................................................................6
Question 6........................................................................................................................................7
References........................................................................................................................................8

3INTERNET OF THINGS
Question 1
The elimination of the interface with the prospective of the user can be related to the term
“The best interface for a system is no user interface”. This can be mainly done by eliminating the
user interface during the implementation of any technology. The most important prospective
with the elimination of the user interface it that, to ensure the continuity and the availability
prospective with the provision of the service which are directly served by the internet of things
(IoT) (Cui, 2016). The no user interface is the best interface because there would be involvement
of fewer steps and therefore the time involved in the processing would be less. The explanation
of the concept can be related to two examples.
Example 1:
There are many options available to the user in order to pay merchants through the use of
NFC. A shopper enters the store and orders a sandwich. In order to pay he takes out his phone
unlock the phone scroll through a ocean of icons and get the desired application then open the
application and wait for it to load . Get the credit card input the details and finally pay for the
sandwich. If the user interface is removed there would be only 3 steps involved. A shopper enters
the store then orders the sandwich and eats the sandwich.
Example 2:
In this scenario the driver approach the car take out the smart phone slides and unlock the
phone make the necessary search and taps a button and unlocks the door and then the car is
unlocked and the door opens. In this case if the user interface is eliminated a driver approaches
the car then unlocks the door of the car and the driver opens the door of the car.
Question 1
The elimination of the interface with the prospective of the user can be related to the term
“The best interface for a system is no user interface”. This can be mainly done by eliminating the
user interface during the implementation of any technology. The most important prospective
with the elimination of the user interface it that, to ensure the continuity and the availability
prospective with the provision of the service which are directly served by the internet of things
(IoT) (Cui, 2016). The no user interface is the best interface because there would be involvement
of fewer steps and therefore the time involved in the processing would be less. The explanation
of the concept can be related to two examples.
Example 1:
There are many options available to the user in order to pay merchants through the use of
NFC. A shopper enters the store and orders a sandwich. In order to pay he takes out his phone
unlock the phone scroll through a ocean of icons and get the desired application then open the
application and wait for it to load . Get the credit card input the details and finally pay for the
sandwich. If the user interface is removed there would be only 3 steps involved. A shopper enters
the store then orders the sandwich and eats the sandwich.
Example 2:
In this scenario the driver approach the car take out the smart phone slides and unlock the
phone make the necessary search and taps a button and unlocks the door and then the car is
unlocked and the door opens. In this case if the user interface is eliminated a driver approaches
the car then unlocks the door of the car and the driver opens the door of the car.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
4INTERNET OF THINGS
Question 2
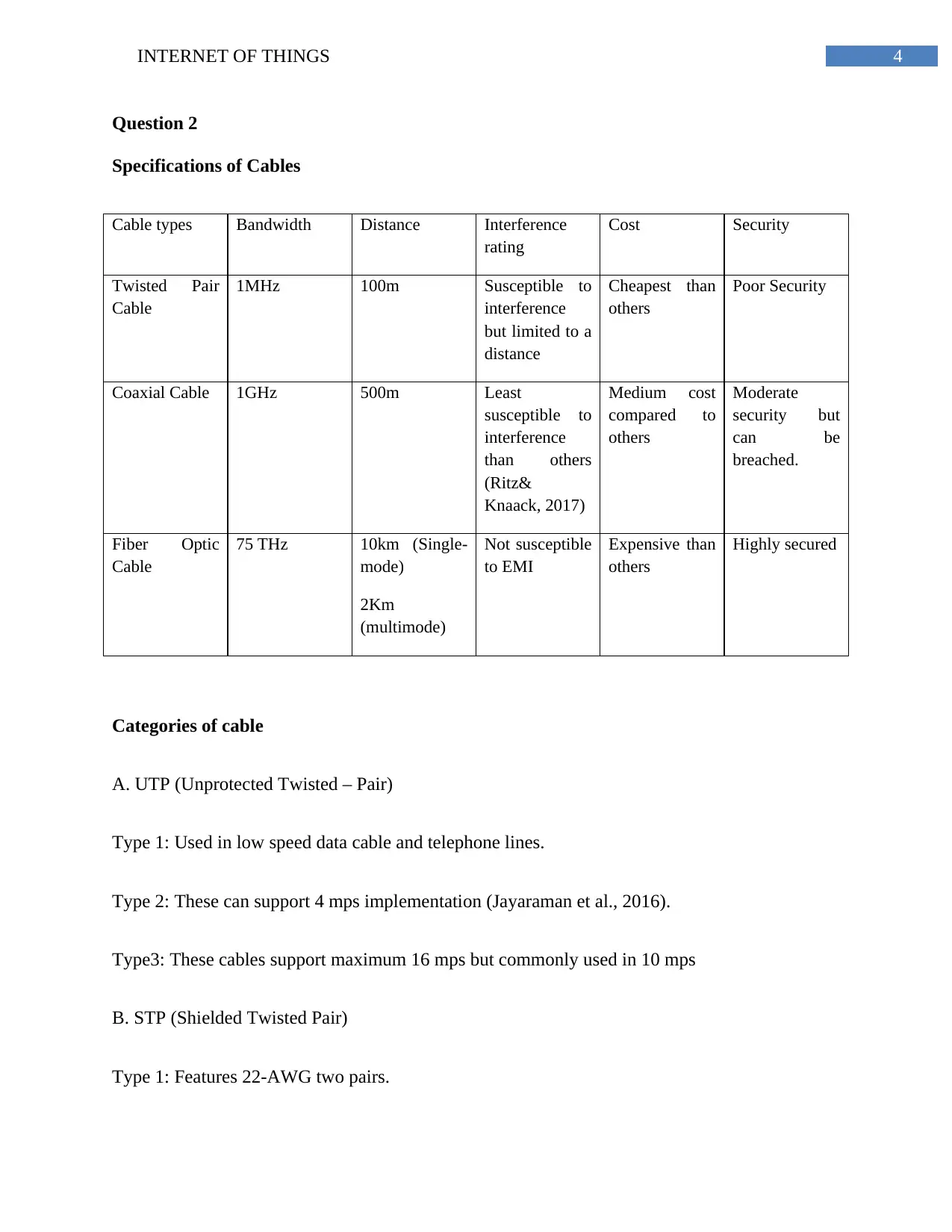
Specifications of Cables
Cable types Bandwidth Distance Interference
rating
Cost Security
Twisted Pair
Cable
1MHz 100m Susceptible to
interference
but limited to a
distance
Cheapest than
others
Poor Security
Coaxial Cable 1GHz 500m Least
susceptible to
interference
than others
(Ritz&
Knaack, 2017)
Medium cost
compared to
others
Moderate
security but
can be
breached.
Fiber Optic
Cable
75 THz 10km (Single-
mode)
2Km
(multimode)
Not susceptible
to EMI
Expensive than
others
Highly secured
Categories of cable
A. UTP (Unprotected Twisted – Pair)
Type 1: Used in low speed data cable and telephone lines.
Type 2: These can support 4 mps implementation (Jayaraman et al., 2016).
Type3: These cables support maximum 16 mps but commonly used in 10 mps
B. STP (Shielded Twisted Pair)
Type 1: Features 22-AWG two pairs.
Question 2
Specifications of Cables
Cable types Bandwidth Distance Interference
rating
Cost Security
Twisted Pair
Cable
1MHz 100m Susceptible to
interference
but limited to a
distance
Cheapest than
others
Poor Security
Coaxial Cable 1GHz 500m Least
susceptible to
interference
than others
(Ritz&
Knaack, 2017)
Medium cost
compared to
others
Moderate
security but
can be
breached.
Fiber Optic
Cable
75 THz 10km (Single-
mode)
2Km
(multimode)
Not susceptible
to EMI
Expensive than
others
Highly secured
Categories of cable
A. UTP (Unprotected Twisted – Pair)
Type 1: Used in low speed data cable and telephone lines.
Type 2: These can support 4 mps implementation (Jayaraman et al., 2016).
Type3: These cables support maximum 16 mps but commonly used in 10 mps
B. STP (Shielded Twisted Pair)
Type 1: Features 22-AWG two pairs.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
5INTERNET OF THINGS
Type 2: Inherit type 1 with 4 telephone pairs
Type 3: Features two pairs of shielded 26-AWG
C. Co-Axial Cable
Type 1: 50-Ohm RG-7 or RG-11, applicable with thick Ethernet.
Type 2: 50-Ohm RG-58, applicable with thin Ethernet.
Type 3: 75-Ohm RG-59, applicable with cable television.
Question 3
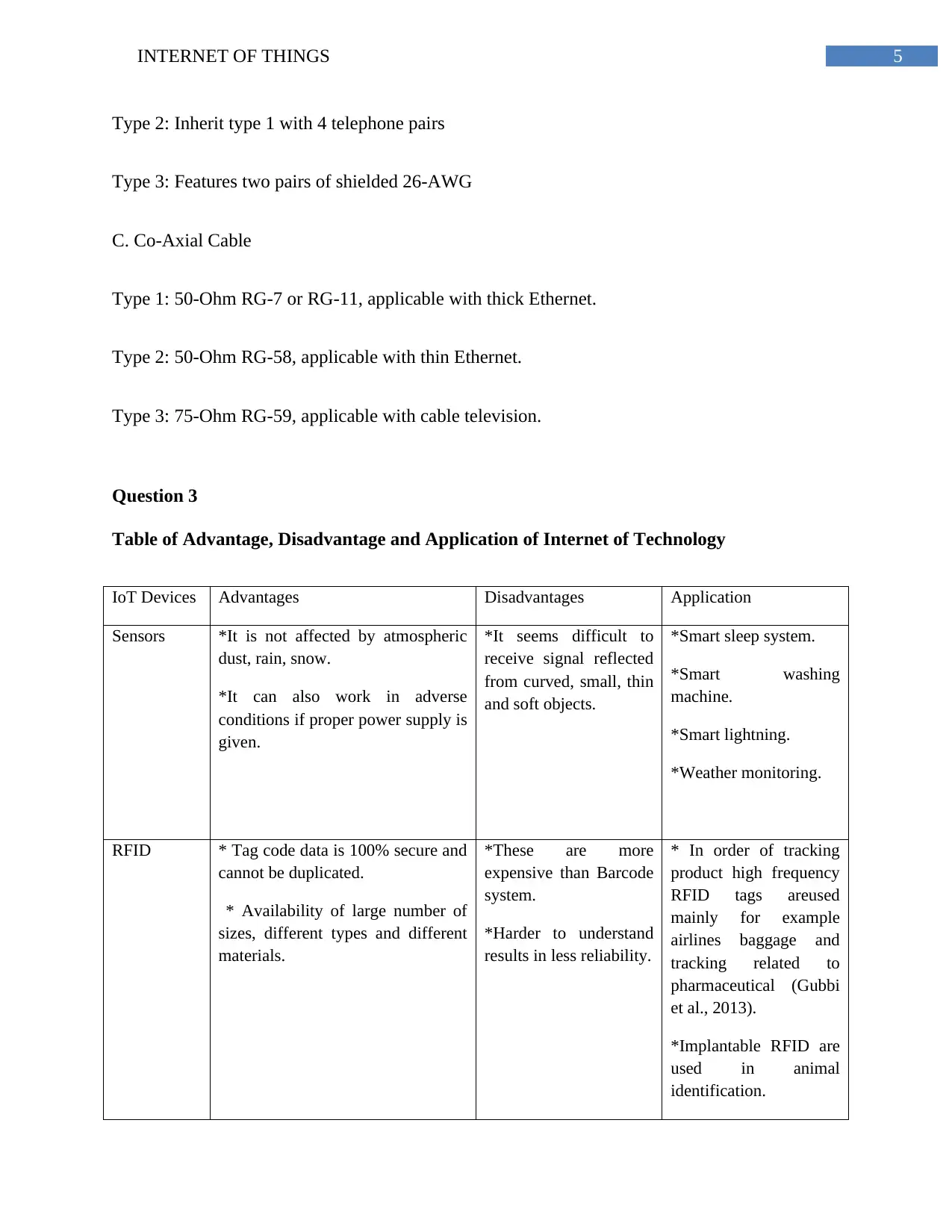
Table of Advantage, Disadvantage and Application of Internet of Technology
IoT Devices Advantages Disadvantages Application
Sensors *It is not affected by atmospheric
dust, rain, snow.
*It can also work in adverse
conditions if proper power supply is
given.
*It seems difficult to
receive signal reflected
from curved, small, thin
and soft objects.
*Smart sleep system.
*Smart washing
machine.
*Smart lightning.
*Weather monitoring.
RFID * Tag code data is 100% secure and
cannot be duplicated.
* Availability of large number of
sizes, different types and different
materials.
*These are more
expensive than Barcode
system.
*Harder to understand
results in less reliability.
* In order of tracking
product high frequency
RFID tags areused
mainly for example
airlines baggage and
tracking related to
pharmaceutical (Gubbi
et al., 2013).
*Implantable RFID are
used in animal
identification.
Type 2: Inherit type 1 with 4 telephone pairs
Type 3: Features two pairs of shielded 26-AWG
C. Co-Axial Cable
Type 1: 50-Ohm RG-7 or RG-11, applicable with thick Ethernet.
Type 2: 50-Ohm RG-58, applicable with thin Ethernet.
Type 3: 75-Ohm RG-59, applicable with cable television.
Question 3
Table of Advantage, Disadvantage and Application of Internet of Technology
IoT Devices Advantages Disadvantages Application
Sensors *It is not affected by atmospheric
dust, rain, snow.
*It can also work in adverse
conditions if proper power supply is
given.
*It seems difficult to
receive signal reflected
from curved, small, thin
and soft objects.
*Smart sleep system.
*Smart washing
machine.
*Smart lightning.
*Weather monitoring.
RFID * Tag code data is 100% secure and
cannot be duplicated.
* Availability of large number of
sizes, different types and different
materials.
*These are more
expensive than Barcode
system.
*Harder to understand
results in less reliability.
* In order of tracking
product high frequency
RFID tags areused
mainly for example
airlines baggage and
tracking related to
pharmaceutical (Gubbi
et al., 2013).
*Implantable RFID are
used in animal
identification.

6INTERNET OF THINGS
Video
Tracking
*Communication between devices.
*Automation and control.
*Collects information.
*There is not any
compatibility of
international standard
for the monitoring
equipments (Li & Da
Xu, 2017).
*Human-computer
interaction.
*Augmentation of
reality.
.
Question 4
Some of the most vulnerability found on any Internet of things aspect has mainly brought
the internet of things security more upper hands that need addressing quickly (Bughin & Chui,
2017). The researchers have found that critical vulnerability in a wide span of Internet of things
have leveraged mainly by the hackers to carry out the active they intent to perform. This can be
included with monitoring the leverage of the live feeds with this aspect. wearable are also a
thread in recent times as hackers can use the motion sensor aspect embedded in the system to
steal the information and take the information and make use of it in order to achieve something.
Before the security aspect of the internet of things (IoT) was ignored but now it is playing an
important role in every sphere. This implementation is also playing an active role in the federal
government level. Several measures have already been taken to take care of the issue and reduce
the loop holes which have previously gained access in times (Osseiran et al., 2016)
Question 5
In the blocking mode phase, the operation request that generates the end point will have
to wait in order to get respond of its request made after the initialization of the end point
Video
Tracking
*Communication between devices.
*Automation and control.
*Collects information.
*There is not any
compatibility of
international standard
for the monitoring
equipments (Li & Da
Xu, 2017).
*Human-computer
interaction.
*Augmentation of
reality.
.
Question 4
Some of the most vulnerability found on any Internet of things aspect has mainly brought
the internet of things security more upper hands that need addressing quickly (Bughin & Chui,
2017). The researchers have found that critical vulnerability in a wide span of Internet of things
have leveraged mainly by the hackers to carry out the active they intent to perform. This can be
included with monitoring the leverage of the live feeds with this aspect. wearable are also a
thread in recent times as hackers can use the motion sensor aspect embedded in the system to
steal the information and take the information and make use of it in order to achieve something.
Before the security aspect of the internet of things (IoT) was ignored but now it is playing an
important role in every sphere. This implementation is also playing an active role in the federal
government level. Several measures have already been taken to take care of the issue and reduce
the loop holes which have previously gained access in times (Osseiran et al., 2016)
Question 5
In the blocking mode phase, the operation request that generates the end point will have
to wait in order to get respond of its request made after the initialization of the end point
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
7INTERNET OF THINGS
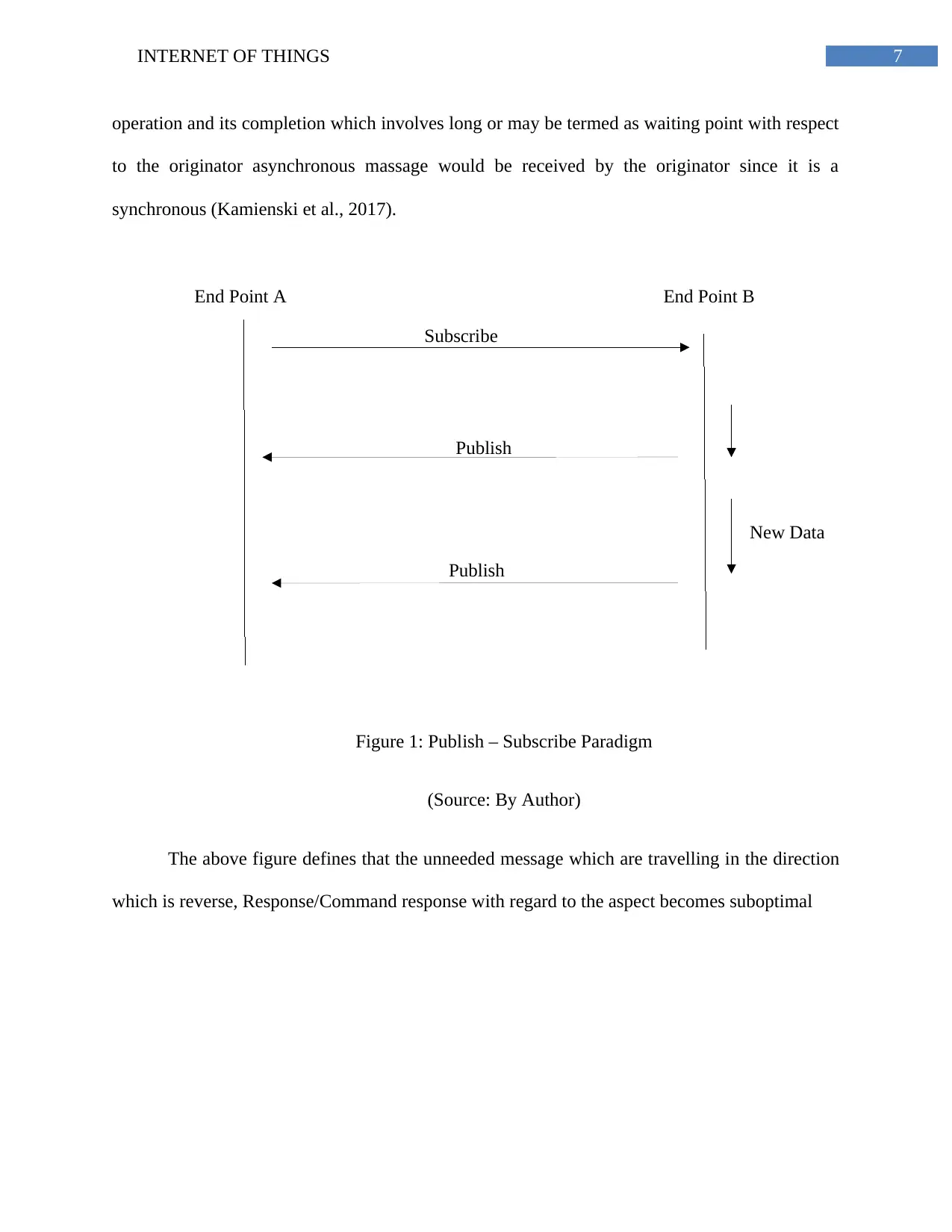
Publish
Publish
Subscribe
End Point BEnd Point A
New Data
operation and its completion which involves long or may be termed as waiting point with respect
to the originator asynchronous massage would be received by the originator since it is a
synchronous (Kamienski et al., 2017).
Figure 1: Publish – Subscribe Paradigm
(Source: By Author)
The above figure defines that the unneeded message which are travelling in the direction
which is reverse, Response/Command response with regard to the aspect becomes suboptimal
Publish
Publish
Subscribe
End Point BEnd Point A
New Data
operation and its completion which involves long or may be termed as waiting point with respect
to the originator asynchronous massage would be received by the originator since it is a
synchronous (Kamienski et al., 2017).
Figure 1: Publish – Subscribe Paradigm
(Source: By Author)
The above figure defines that the unneeded message which are travelling in the direction
which is reverse, Response/Command response with regard to the aspect becomes suboptimal
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

8INTERNET OF THINGS
Endpoint A Endpoint B
1. Request
3. Response
Processing
Figure 2: Command/Response paradigm
(Source: By Author)
Total time saving will be 6ms in the propagation delay between the application and
sensor + 1ms in receiving that message. Total time saving is 7ms.
Question 6
Nielson’s Law: User Bandwidth increases up to 60% every year which is less than
Moore’s Law related to speed of computer. This new law fits data from the time period of 1983
to 2016 (Kumar et al., 2017). Nielson’s Law which is related to internet bandwidth states that, a
high end user’s connection speed grows by average 50% every year (Mulani & Pingle,2016).
Implication of Nelson’s law in IoT
Endpoint A Endpoint B
1. Request
3. Response
Processing
Figure 2: Command/Response paradigm
(Source: By Author)
Total time saving will be 6ms in the propagation delay between the application and
sensor + 1ms in receiving that message. Total time saving is 7ms.
Question 6
Nielson’s Law: User Bandwidth increases up to 60% every year which is less than
Moore’s Law related to speed of computer. This new law fits data from the time period of 1983
to 2016 (Kumar et al., 2017). Nielson’s Law which is related to internet bandwidth states that, a
high end user’s connection speed grows by average 50% every year (Mulani & Pingle,2016).
Implication of Nelson’s law in IoT

9INTERNET OF THINGS
It is estimated around the year 2024 it might be expected that the technology with respect
to the sensor will eventually break through the implementation of the “trillion sensor”. The
implementation would directly help in creating the data stream virtual with respect to every
surrounding surface. The car would be implemented with sensor even houses and clothing.
Microchip will be a trending aspect which may include body sensor and skin sensor (Bonomi et
al., 2017).
It is estimated around the year 2024 it might be expected that the technology with respect
to the sensor will eventually break through the implementation of the “trillion sensor”. The
implementation would directly help in creating the data stream virtual with respect to every
surrounding surface. The car would be implemented with sensor even houses and clothing.
Microchip will be a trending aspect which may include body sensor and skin sensor (Bonomi et
al., 2017).
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

10INTERNET OF THINGS
References
Bughin, J., & Chui, M. (2017). The Internet of Things: Assessing Its Potential and Identifying
the Enablers Needed to Capture the Opportunity. In The Internet of Things in the Modern
Business Environment (pp. 111-125). IGI Global.
Cui, X. (2016). The internet of things. In Ethical Ripples of Creativity and Innovation (pp. 61-
68). Palgrave Macmillan, London.
Jayaraman, P. P., Yavari, A., Georgakopoulos, D., Morshed, A., & Zaslavsky, A. (2016).
Internet of things platform for smart farming: Experiences and lessons learnt. Sensors,
16(11), 1884.
Kamienski, C., Jentsch, M., Eisenhauer, M., Kiljander, J., Ferrera, E., Rosengren, P., ... & Sadok,
D. (2017). Application development for the Internet of Things: A context-aware mixed
criticality systems development platform. Computer Communications, 104, 1-16.
Li, S., & Da Xu, L. (2017). Securing the Internet of Things. Syngress.
Mulani, T. T., & Pingle, S. V. (2016). Internet of things. International Research Journal of
Multidisciplinary Studies, 2(3).
Osseiran, A., Elloumi, O., Song, J., & Monserrat, J. F. (2017). Internet of Things. IEEE
Communications Standards Magazine, 1(2), 84-84.
Ritz, J., & Knaack, Z. (2017). internet of things. Technology & Engineering Teacher, 76(6).
References
Bughin, J., & Chui, M. (2017). The Internet of Things: Assessing Its Potential and Identifying
the Enablers Needed to Capture the Opportunity. In The Internet of Things in the Modern
Business Environment (pp. 111-125). IGI Global.
Cui, X. (2016). The internet of things. In Ethical Ripples of Creativity and Innovation (pp. 61-
68). Palgrave Macmillan, London.
Jayaraman, P. P., Yavari, A., Georgakopoulos, D., Morshed, A., & Zaslavsky, A. (2016).
Internet of things platform for smart farming: Experiences and lessons learnt. Sensors,
16(11), 1884.
Kamienski, C., Jentsch, M., Eisenhauer, M., Kiljander, J., Ferrera, E., Rosengren, P., ... & Sadok,
D. (2017). Application development for the Internet of Things: A context-aware mixed
criticality systems development platform. Computer Communications, 104, 1-16.
Li, S., & Da Xu, L. (2017). Securing the Internet of Things. Syngress.
Mulani, T. T., & Pingle, S. V. (2016). Internet of things. International Research Journal of
Multidisciplinary Studies, 2(3).
Osseiran, A., Elloumi, O., Song, J., & Monserrat, J. F. (2017). Internet of Things. IEEE
Communications Standards Magazine, 1(2), 84-84.
Ritz, J., & Knaack, Z. (2017). internet of things. Technology & Engineering Teacher, 76(6).
1 out of 10
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2025 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





