System Analysis: IoT Security Issues, Challenges, and Solutions
VerifiedAdded on 2020/03/16
|8
|2085
|53
Report
AI Summary
This report provides a detailed analysis of the security challenges facing the Internet of Things (IoT). It begins with an introduction to IoT, covering its definition, pillars, and the reasons behind its rapid growth, while also acknowledging its limitations. The report then delves into the critical security issues, including data encryption, data authentication, side-channel attacks, and hardware vulnerabilities. It identifies four major issues and discusses the challenges and solutions to overcome them, such as device range, latency, manufacturability tests, flexible infrastructure, and digital certification. The report concludes by emphasizing the importance of ongoing security measures and advancements in the IoT landscape, ensuring the protection of users and their data. The report is a comprehensive overview of IoT security concerns and potential solutions, offering insights into the current state and future of IoT security.

Running Head: System Analysis
Internet of Things
Security Issues and Solutions
Internet of Things
Security Issues and Solutions
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1
System Analysis
Table of Contents
Introduction to IoT................................................................................................................................2
Pillars of IOT.........................................................................................................................................3
Why IoT?..............................................................................................................................................4
Limitations of IoT.................................................................................................................................5
Security Issues of IoT............................................................................................................................5
The four major and critical issues in IoT are.....................................................................................5
IoT Security challenges and solutions to overcome from the issues..................................................6
Conclusion.............................................................................................................................................7
References.............................................................................................................................................8
System Analysis
Table of Contents
Introduction to IoT................................................................................................................................2
Pillars of IOT.........................................................................................................................................3
Why IoT?..............................................................................................................................................4
Limitations of IoT.................................................................................................................................5
Security Issues of IoT............................................................................................................................5
The four major and critical issues in IoT are.....................................................................................5
IoT Security challenges and solutions to overcome from the issues..................................................6
Conclusion.............................................................................................................................................7
References.............................................................................................................................................8

2
System Analysis
Introduction to IoT
Internet of Things is the growing technology in today’s scenario locally and globally. It is
also known as the internet of everything. It is the technology prototype which is being used in
the global networks for the machine devices which provides the facilities to interact with the
other systems all over the world. It has been grown in an extraordinary speed during the past
few years. The term IoT is being introduced by Kevin Ashton in 1999 and it is been defined
as the uniquely identified objects and a virtual way of designing and development of the
internet like structure. It the upcoming technology and vastly enhanced in the world of
internet (Gatsis & Pappas, 2017). It is been widely used in the various platforms where the
users gets easily access to this technology i.e. it involves the user interaction accessing to the
mobile devices, smart phones, gadgets, tablets, etc. It is also known as Machine-to-Machine
technology which causes the changing in the accessibility to the internet in the current
scenario. Moreover, the accessibility of the technology by the users is bringing the biggest
change in the society and the culture so as to bring the different forms of visibility and the
interventions over the internet. The technology is been used for making the real time analysis.
It is usually used for introducing and to make predictions or to prevent from the provision
outages. It is capable of building the communication and transferring of the data over the
various networks between human interactions towards the machines (Gubbi et al., 2013).
IoT has involved into three different stages:
1. IoT has involved in making the identifications and addressing of the sensor
devices and to the various other devices that it grant the permission to the
sensors for accessibility to collect the data.
2. Various software’s and applications is being used for the collecting and
analysing of the data for the linking purpose.
3. Decision is been made and the data is been transmitted on the basis of request
made to the servers (Heer et al, 2011).
System Analysis
Introduction to IoT
Internet of Things is the growing technology in today’s scenario locally and globally. It is
also known as the internet of everything. It is the technology prototype which is being used in
the global networks for the machine devices which provides the facilities to interact with the
other systems all over the world. It has been grown in an extraordinary speed during the past
few years. The term IoT is being introduced by Kevin Ashton in 1999 and it is been defined
as the uniquely identified objects and a virtual way of designing and development of the
internet like structure. It the upcoming technology and vastly enhanced in the world of
internet (Gatsis & Pappas, 2017). It is been widely used in the various platforms where the
users gets easily access to this technology i.e. it involves the user interaction accessing to the
mobile devices, smart phones, gadgets, tablets, etc. It is also known as Machine-to-Machine
technology which causes the changing in the accessibility to the internet in the current
scenario. Moreover, the accessibility of the technology by the users is bringing the biggest
change in the society and the culture so as to bring the different forms of visibility and the
interventions over the internet. The technology is been used for making the real time analysis.
It is usually used for introducing and to make predictions or to prevent from the provision
outages. It is capable of building the communication and transferring of the data over the
various networks between human interactions towards the machines (Gubbi et al., 2013).
IoT has involved into three different stages:
1. IoT has involved in making the identifications and addressing of the sensor
devices and to the various other devices that it grant the permission to the
sensors for accessibility to collect the data.
2. Various software’s and applications is being used for the collecting and
analysing of the data for the linking purpose.
3. Decision is been made and the data is been transmitted on the basis of request
made to the servers (Heer et al, 2011).
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
3
System Analysis
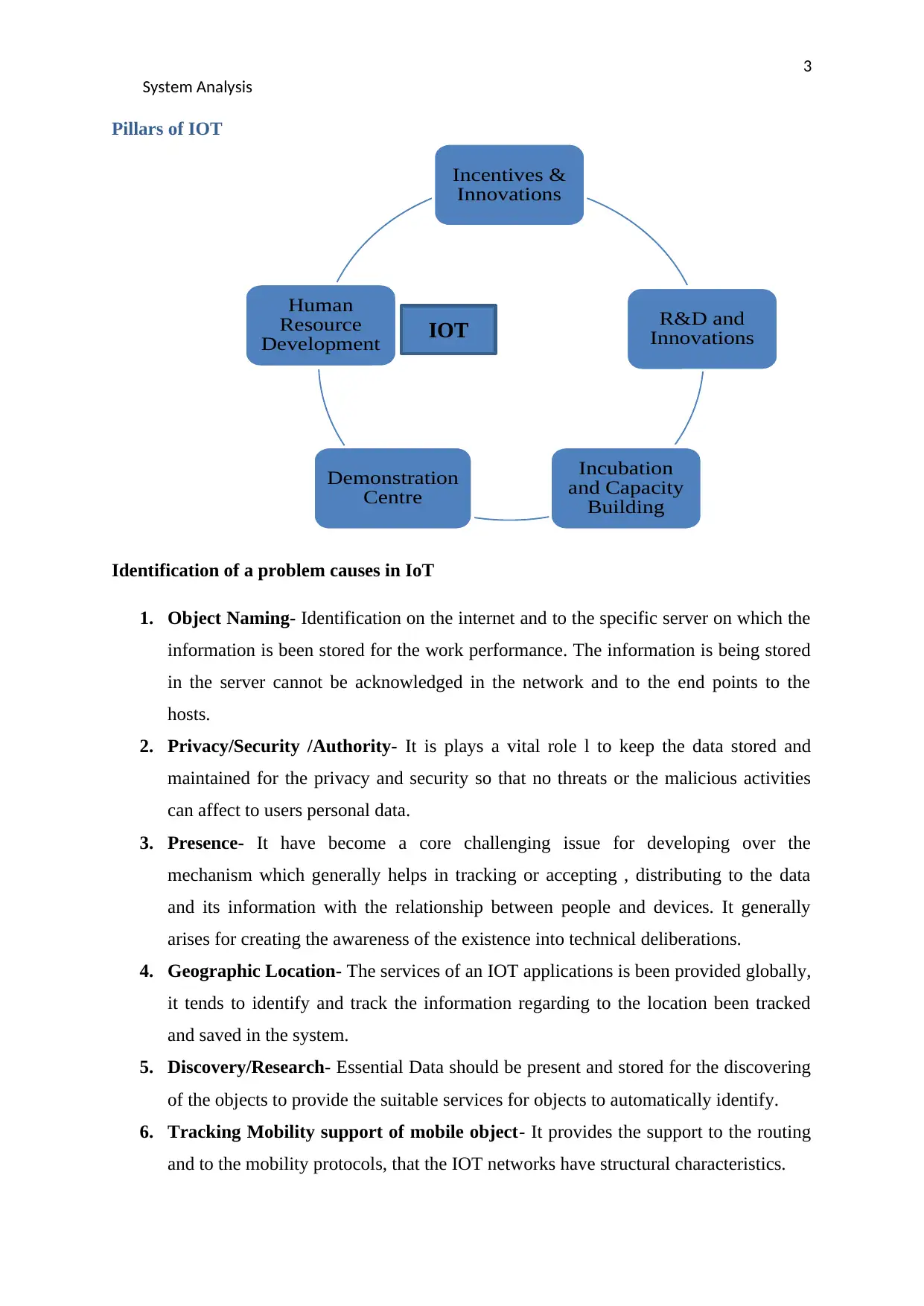
Pillars of IOT
Identification of a problem causes in IoT
1. Object Naming- Identification on the internet and to the specific server on which the
information is been stored for the work performance. The information is being stored
in the server cannot be acknowledged in the network and to the end points to the
hosts.
2. Privacy/Security /Authority- It is plays a vital role l to keep the data stored and
maintained for the privacy and security so that no threats or the malicious activities
can affect to users personal data.
3. Presence- It have become a core challenging issue for developing over the
mechanism which generally helps in tracking or accepting , distributing to the data
and its information with the relationship between people and devices. It generally
arises for creating the awareness of the existence into technical deliberations.
4. Geographic Location- The services of an IOT applications is been provided globally,
it tends to identify and track the information regarding to the location been tracked
and saved in the system.
5. Discovery/Research- Essential Data should be present and stored for the discovering
of the objects to provide the suitable services for objects to automatically identify.
6. Tracking Mobility support of mobile object- It provides the support to the routing
and to the mobility protocols, that the IOT networks have structural characteristics.
Incentives &
Innovations
R&D and
Innovations
Incubation
and Capacity
Building
Demonstration
Centre
Human
Resource
Development IOT
System Analysis
Pillars of IOT
Identification of a problem causes in IoT
1. Object Naming- Identification on the internet and to the specific server on which the
information is been stored for the work performance. The information is being stored
in the server cannot be acknowledged in the network and to the end points to the
hosts.
2. Privacy/Security /Authority- It is plays a vital role l to keep the data stored and
maintained for the privacy and security so that no threats or the malicious activities
can affect to users personal data.
3. Presence- It have become a core challenging issue for developing over the
mechanism which generally helps in tracking or accepting , distributing to the data
and its information with the relationship between people and devices. It generally
arises for creating the awareness of the existence into technical deliberations.
4. Geographic Location- The services of an IOT applications is been provided globally,
it tends to identify and track the information regarding to the location been tracked
and saved in the system.
5. Discovery/Research- Essential Data should be present and stored for the discovering
of the objects to provide the suitable services for objects to automatically identify.
6. Tracking Mobility support of mobile object- It provides the support to the routing
and to the mobility protocols, that the IOT networks have structural characteristics.
Incentives &
Innovations
R&D and
Innovations
Incubation
and Capacity
Building
Demonstration
Centre
Human
Resource
Development IOT
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

4
System Analysis
7. Data Processing/ computing- IOT technology ensures in providing the support to the
various applications and information present should be available for transferring the
objects operating under the varied perspectives instead of the humans involvement.
8. Global Connectivity- It provides the global connectivity to end to end
communications. It tends and ensures to the huge number of IP addresses in order to
individually identify each object. For considering the global interoperability, IoT is
considered for connecting to the smart objects and to the latest technology and its
software’s (Jing et al., 2014).
Why IoT?
The main concept of IoT is it generally develops to the networks being formed on a large
scale having the sensor nodes. It is used for integrating to the various kinds of networks for
communication and usability on the devices.
1. It provides the dynamic control in the internet world and in daily life.
2. It improves the utilization of resources ratios.
3. It emphasis on the building a mutual relationships between the human and nature.
4. Formatting an intellectual entity by integrating the human society and to the physical
systems.
5. Internetworking and universal transport.
6. Usability and accessibility of the resources.
7. It acts as an integration of the technology (Li & Da Xu, 2017).
Limitations of IoT
IoT has the limitations due to certain extent.
1. Interoperability and standardization of the technology
2. Legal Mechanisms
3. Technical Limitation in some cases.
4. It has the connectivity problem regarding to all the part of the customers using the
smart cards, big schemes in smart cities etc.
5. It involves the forms and design of the products and services and the analytics tools
used for dealing with the massive data.
6. Killing of applications which basically needed to control the things from the data
which is being collected and analysing of the data (Roman et al., 2013).
System Analysis
7. Data Processing/ computing- IOT technology ensures in providing the support to the
various applications and information present should be available for transferring the
objects operating under the varied perspectives instead of the humans involvement.
8. Global Connectivity- It provides the global connectivity to end to end
communications. It tends and ensures to the huge number of IP addresses in order to
individually identify each object. For considering the global interoperability, IoT is
considered for connecting to the smart objects and to the latest technology and its
software’s (Jing et al., 2014).
Why IoT?
The main concept of IoT is it generally develops to the networks being formed on a large
scale having the sensor nodes. It is used for integrating to the various kinds of networks for
communication and usability on the devices.
1. It provides the dynamic control in the internet world and in daily life.
2. It improves the utilization of resources ratios.
3. It emphasis on the building a mutual relationships between the human and nature.
4. Formatting an intellectual entity by integrating the human society and to the physical
systems.
5. Internetworking and universal transport.
6. Usability and accessibility of the resources.
7. It acts as an integration of the technology (Li & Da Xu, 2017).
Limitations of IoT
IoT has the limitations due to certain extent.
1. Interoperability and standardization of the technology
2. Legal Mechanisms
3. Technical Limitation in some cases.
4. It has the connectivity problem regarding to all the part of the customers using the
smart cards, big schemes in smart cities etc.
5. It involves the forms and design of the products and services and the analytics tools
used for dealing with the massive data.
6. Killing of applications which basically needed to control the things from the data
which is being collected and analysing of the data (Roman et al., 2013).

5
System Analysis
Security Issues of IoT
The internet of things has been widely spread for its implementation scope. However the
lethargic growth and the poor development of the IoT security have results in arising of the
several issues. IoT security issues are certainly a biggest reality for developing of the IoT
applications. In the security issues IoT application security plays the vital role in testing of
the frameworks. IoT poses the risks to the data and files saved in the system, privacy issues
and safety measures should be taken. It helps in creating the making the application secured
and to have the proof regarding to the attacks and enabling of the devices and the applications
that highlights the top security concerns. There are several security and privacy issues that are
being faced and arising in the development of IoT (Sfar et al., 2017).
The four major and critical issues in IoT are:
1. IoT Security in Data Encryption- Internet of things collect the tons of the data
the data is being retrieved from the several sites and for this it is essential to
maintain and to protect the data from the encryption. For example to provide the
location, it should only be shown to the customer or to the concerned user and no
one else.
2. IoT security in Data Authentication- It provides the successful encryption
format for the data being changed and sometimes the data is been hacked while
communication of the devices for this security is being compromised.
3. IoT Security side Channel attacks - Accessibility to the authentication services
and encryption of the data will leave the scope for opening for the side attacks or
to the malicious activities.
4. Hardware Issues – IoT is the biggest issues in terms of hardware because of its
modern architecture which creates the difficulty in accessing to the new
technology and to the complex designs which is a bigger challenge to be accepted
in the field of IoT.
IoT Security challenges and solutions to overcome from the issues:
In today’s scenario IoT plays a vital role in implementing the various tools and
technologies for developing of the various applications. It majorly helps in creating
and developing of the various different applications for the different platforms. The
main Key challenges to overcome from the issues being raised in an IoT are:
System Analysis
Security Issues of IoT
The internet of things has been widely spread for its implementation scope. However the
lethargic growth and the poor development of the IoT security have results in arising of the
several issues. IoT security issues are certainly a biggest reality for developing of the IoT
applications. In the security issues IoT application security plays the vital role in testing of
the frameworks. IoT poses the risks to the data and files saved in the system, privacy issues
and safety measures should be taken. It helps in creating the making the application secured
and to have the proof regarding to the attacks and enabling of the devices and the applications
that highlights the top security concerns. There are several security and privacy issues that are
being faced and arising in the development of IoT (Sfar et al., 2017).
The four major and critical issues in IoT are:
1. IoT Security in Data Encryption- Internet of things collect the tons of the data
the data is being retrieved from the several sites and for this it is essential to
maintain and to protect the data from the encryption. For example to provide the
location, it should only be shown to the customer or to the concerned user and no
one else.
2. IoT security in Data Authentication- It provides the successful encryption
format for the data being changed and sometimes the data is been hacked while
communication of the devices for this security is being compromised.
3. IoT Security side Channel attacks - Accessibility to the authentication services
and encryption of the data will leave the scope for opening for the side attacks or
to the malicious activities.
4. Hardware Issues – IoT is the biggest issues in terms of hardware because of its
modern architecture which creates the difficulty in accessing to the new
technology and to the complex designs which is a bigger challenge to be accepted
in the field of IoT.
IoT Security challenges and solutions to overcome from the issues:
In today’s scenario IoT plays a vital role in implementing the various tools and
technologies for developing of the various applications. It majorly helps in creating
and developing of the various different applications for the different platforms. The
main Key challenges to overcome from the issues being raised in an IoT are:
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

6
System Analysis
1. Device Range- It provides the facility for covering the whole network of the
IoT. It should be very specific in terms of range metrics and for the
applications and devices.
2. Latency and Capacity- It helps in handling in the speed and to the total time
taken for transferring of the data. It is essential before transferring; the data
should be checked thoroughly.
3. Manufacturability Test- It helps in building the IoT from scratching of the
data and developing of the various applications.
4. Flexible Infrastructure- It provides the internal and the cloud infrastructure
for the development of the IoT requirement.
5. Digital Certification- It provides and serves the certification as the main
foundation of IoT network security for establishing and interacting with
authenticated services.
6. Security Design and Professional Services- It helps in providing the security
to the users and helps in ensuring and developing the focus from the beginning
to the end in designing and implementation.
7. Data and System Integrity- It provides the confirmation regarding to the
configuration of the messages and keeping the information saved that the
message is not been changed (Zhu et al., 2010).
Conclusion
The IoT future is getting enhanced day by day and the development of the IoT is being
boosted in the digital market while providing and ensuring to maintain the security and the
appropriate protection provided to the customers. Most of the technology advancement
which is truly needed for making the enhancement in the manufacturing of the agencies of
that have already being implemented on the legal and social security fields. The IoT is
emerging into the global and to the International market and its architecture for providing and
delivering the best services to the users in the near future.
System Analysis
1. Device Range- It provides the facility for covering the whole network of the
IoT. It should be very specific in terms of range metrics and for the
applications and devices.
2. Latency and Capacity- It helps in handling in the speed and to the total time
taken for transferring of the data. It is essential before transferring; the data
should be checked thoroughly.
3. Manufacturability Test- It helps in building the IoT from scratching of the
data and developing of the various applications.
4. Flexible Infrastructure- It provides the internal and the cloud infrastructure
for the development of the IoT requirement.
5. Digital Certification- It provides and serves the certification as the main
foundation of IoT network security for establishing and interacting with
authenticated services.
6. Security Design and Professional Services- It helps in providing the security
to the users and helps in ensuring and developing the focus from the beginning
to the end in designing and implementation.
7. Data and System Integrity- It provides the confirmation regarding to the
configuration of the messages and keeping the information saved that the
message is not been changed (Zhu et al., 2010).
Conclusion
The IoT future is getting enhanced day by day and the development of the IoT is being
boosted in the digital market while providing and ensuring to maintain the security and the
appropriate protection provided to the customers. Most of the technology advancement
which is truly needed for making the enhancement in the manufacturing of the agencies of
that have already being implemented on the legal and social security fields. The IoT is
emerging into the global and to the International market and its architecture for providing and
delivering the best services to the users in the near future.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7
System Analysis
References
Gatsis, K., & Pappas, G. J. (2017, April). Wireless Control for the IoT: Power, Spectrum, and
Security Challenges. In Proceedings of the Second International Conference on
Internet-of-Things Design and Implementation (pp. 341-342). ACM.
Gubbi, J., Buyya, R., Marusic, S., & Palaniswami, M. (2013). Internet of Things (IoT): A
vision, architectural elements, and future directions. Future generation computer
systems, 29(7), 1645-1660.
Heer, T., Garcia-Morchon, O., Hummen, R., Keoh, S. L., Kumar, S. S., & Wehrle, K. (2011).
Security Challenges in the IP-based Internet of Things. Wireless Personal
Communications, 61(3), 527-542.
Jing, Q., Vasilakos, A. V., Wan, J., Lu, J., & Qiu, D. (2014). Security of the internet of
things: Perspectives and challenges. Wireless Networks, 20(8), 2481-2501.
Li, S., & Da Xu, L. (2017). Securing the Internet of Things. Syngress.
Roman, R., Zhou, J., & Lopez, J. (2013). On the features and challenges of security and
privacy in distributed internet of things. Computer Networks, 57(10), 2266-2279.
Sfar, A., Chtourou, Z., Natalizio, E., & Challal, Y. (2017). A systemic and cognitive vision
for IoT security: a case study of military live simulation and security challenges.
In International Conference on Smart, Monitored and Controlled Cities SM2C’17.
Zhu, Q., Wang, R., Chen, Q., Liu, Y., & Qin, W. (2010, December). Iot gateway:
Bridgingwireless sensor networks into internet of things. In Embedded and
Ubiquitous Computing (EUC), 2010 IEEE/IFIP 8th International Conference on (pp.
347-352). IEEE.
System Analysis
References
Gatsis, K., & Pappas, G. J. (2017, April). Wireless Control for the IoT: Power, Spectrum, and
Security Challenges. In Proceedings of the Second International Conference on
Internet-of-Things Design and Implementation (pp. 341-342). ACM.
Gubbi, J., Buyya, R., Marusic, S., & Palaniswami, M. (2013). Internet of Things (IoT): A
vision, architectural elements, and future directions. Future generation computer
systems, 29(7), 1645-1660.
Heer, T., Garcia-Morchon, O., Hummen, R., Keoh, S. L., Kumar, S. S., & Wehrle, K. (2011).
Security Challenges in the IP-based Internet of Things. Wireless Personal
Communications, 61(3), 527-542.
Jing, Q., Vasilakos, A. V., Wan, J., Lu, J., & Qiu, D. (2014). Security of the internet of
things: Perspectives and challenges. Wireless Networks, 20(8), 2481-2501.
Li, S., & Da Xu, L. (2017). Securing the Internet of Things. Syngress.
Roman, R., Zhou, J., & Lopez, J. (2013). On the features and challenges of security and
privacy in distributed internet of things. Computer Networks, 57(10), 2266-2279.
Sfar, A., Chtourou, Z., Natalizio, E., & Challal, Y. (2017). A systemic and cognitive vision
for IoT security: a case study of military live simulation and security challenges.
In International Conference on Smart, Monitored and Controlled Cities SM2C’17.
Zhu, Q., Wang, R., Chen, Q., Liu, Y., & Qin, W. (2010, December). Iot gateway:
Bridgingwireless sensor networks into internet of things. In Embedded and
Ubiquitous Computing (EUC), 2010 IEEE/IFIP 8th International Conference on (pp.
347-352). IEEE.
1 out of 8
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





