An Analysis of Internet of Things Security: Problems and Solutions
VerifiedAdded on 2020/03/07
|14
|3356
|407
Report
AI Summary
This report provides a detailed overview of Internet of Things (IoT) security, addressing the critical need for robust security measures in interconnected devices. It begins with an executive summary highlighting the core issue: data security in the IoT ecosystem. The report then explores the architecture and applications of IoT, emphasizing its growing prevalence in various sectors. It delves into the security problems, including data encryption, authentication, and hardware vulnerabilities, while also discussing the impact of these issues. Furthermore, the report proposes potential solutions, such as encrypted digital certificates, access controls, authentication protocols, firewalls, and regular software updates. The report concludes by stressing the importance of prioritizing security in the design and development of IoT devices, offering insights for developers to ensure data protection and user safety. The report is a valuable resource for understanding the current state of IoT security and the measures needed to mitigate risks.

Running head: INTERNET OF THINGS SECURITY
Internet of Things Security
Name of the Student
Name of the University
Author Note
Internet of Things Security
Name of the Student
Name of the University
Author Note
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1
INTERNET OF THINGS SECURITY
Executive summary
This report deals with the security measure Internet of Things offers to its users. The internet
of things is a futuristic technology, which mainly involves interconnection of the devices, and
the internet is proposed. With Internet of Things, the risk of losing data is there because of
the transmission of the data from one point to another, which can be referred to as the main
problem statement. The report further discusses about the different application area Internet
of Things is applied, the problems which are being faced and the potential solutions for the
problems being faced. To conclude this report it can be said that the use of Internet of Things
security should be the top priority for the organizations specializing in the Internet of Things
devices.
INTERNET OF THINGS SECURITY
Executive summary
This report deals with the security measure Internet of Things offers to its users. The internet
of things is a futuristic technology, which mainly involves interconnection of the devices, and
the internet is proposed. With Internet of Things, the risk of losing data is there because of
the transmission of the data from one point to another, which can be referred to as the main
problem statement. The report further discusses about the different application area Internet
of Things is applied, the problems which are being faced and the potential solutions for the
problems being faced. To conclude this report it can be said that the use of Internet of Things
security should be the top priority for the organizations specializing in the Internet of Things
devices.

2
INTERNET OF THINGS SECURITY
Table of Contents
Introduction................................................................................................................................3
Overview of Internet of Things..................................................................................................3
Application.................................................................................................................................4
Security Problems......................................................................................................................6
Security Solutions......................................................................................................................8
Conclusion..................................................................................................................................9
References................................................................................................................................11
INTERNET OF THINGS SECURITY
Table of Contents
Introduction................................................................................................................................3
Overview of Internet of Things..................................................................................................3
Application.................................................................................................................................4
Security Problems......................................................................................................................6
Security Solutions......................................................................................................................8
Conclusion..................................................................................................................................9
References................................................................................................................................11
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3
INTERNET OF THINGS SECURITY
Introduction
Internet of Things is a concept of device with the ability to collect information from
the world using sensors and applications and sharing them across the internet where there are
devices to process the collected data and utilize it when needed. The use of it devices has
recently seen a rise in production (Gubbi et al. 2013).
Internet of Things security is an area of concern related to the safeguarding of tee
device connected to the network. It involves the prevalence of objects or things to provide
them with unique identifiers and the ability to automatically transmit the data using a
network. The Internet of Things communication comprises of the embedded sensors, energy
grids, home appliances and wearable smart devices.
The report further discusses about the different application area Internet of Things is
applied, the problems, which are being faced, and the potential solutions for the problems
being faced.
Overview of Internet of Things
Using Internet of Things in the common world has several benefits. The devices can
be used to receive warning to the user’s phone and to detect danger from the nearby-analyzed
data. Using the technology in automobiles can cause them to park automatically using sensors
to look out for nearby cars. Tracking of shipments can be done easily using electronic tags
attached to the parcel (Tao et al. 2014). Tacking the habits and health of the user can detect
any disease or can be used to send out SOS signals during time of danger. Internet of Things
devices can also be used in business world to locate inventory shipments, save fuel by using
intelligent driving routes and mechanisms and to improve safety for the workers in hazardous
areas.
INTERNET OF THINGS SECURITY
Introduction
Internet of Things is a concept of device with the ability to collect information from
the world using sensors and applications and sharing them across the internet where there are
devices to process the collected data and utilize it when needed. The use of it devices has
recently seen a rise in production (Gubbi et al. 2013).
Internet of Things security is an area of concern related to the safeguarding of tee
device connected to the network. It involves the prevalence of objects or things to provide
them with unique identifiers and the ability to automatically transmit the data using a
network. The Internet of Things communication comprises of the embedded sensors, energy
grids, home appliances and wearable smart devices.
The report further discusses about the different application area Internet of Things is
applied, the problems, which are being faced, and the potential solutions for the problems
being faced.
Overview of Internet of Things
Using Internet of Things in the common world has several benefits. The devices can
be used to receive warning to the user’s phone and to detect danger from the nearby-analyzed
data. Using the technology in automobiles can cause them to park automatically using sensors
to look out for nearby cars. Tracking of shipments can be done easily using electronic tags
attached to the parcel (Tao et al. 2014). Tacking the habits and health of the user can detect
any disease or can be used to send out SOS signals during time of danger. Internet of Things
devices can also be used in business world to locate inventory shipments, save fuel by using
intelligent driving routes and mechanisms and to improve safety for the workers in hazardous
areas.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
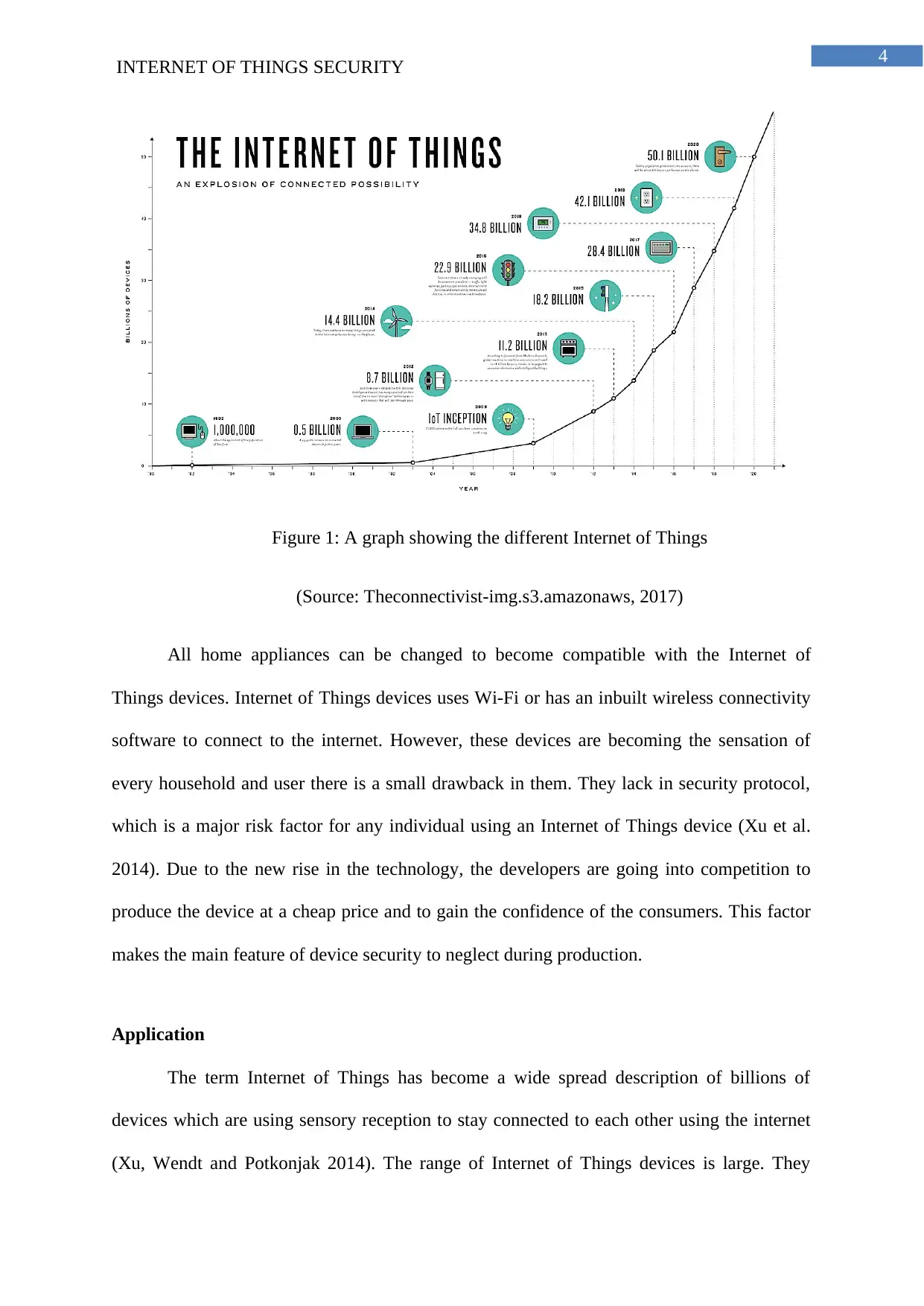
4
INTERNET OF THINGS SECURITY
Figure 1: A graph showing the different Internet of Things
(Source: Theconnectivist-img.s3.amazonaws, 2017)
All home appliances can be changed to become compatible with the Internet of
Things devices. Internet of Things devices uses Wi-Fi or has an inbuilt wireless connectivity
software to connect to the internet. However, these devices are becoming the sensation of
every household and user there is a small drawback in them. They lack in security protocol,
which is a major risk factor for any individual using an Internet of Things device (Xu et al.
2014). Due to the new rise in the technology, the developers are going into competition to
produce the device at a cheap price and to gain the confidence of the consumers. This factor
makes the main feature of device security to neglect during production.
Application
The term Internet of Things has become a wide spread description of billions of
devices which are using sensory reception to stay connected to each other using the internet
(Xu, Wendt and Potkonjak 2014). The range of Internet of Things devices is large. They
INTERNET OF THINGS SECURITY
Figure 1: A graph showing the different Internet of Things
(Source: Theconnectivist-img.s3.amazonaws, 2017)
All home appliances can be changed to become compatible with the Internet of
Things devices. Internet of Things devices uses Wi-Fi or has an inbuilt wireless connectivity
software to connect to the internet. However, these devices are becoming the sensation of
every household and user there is a small drawback in them. They lack in security protocol,
which is a major risk factor for any individual using an Internet of Things device (Xu et al.
2014). Due to the new rise in the technology, the developers are going into competition to
produce the device at a cheap price and to gain the confidence of the consumers. This factor
makes the main feature of device security to neglect during production.
Application
The term Internet of Things has become a wide spread description of billions of
devices which are using sensory reception to stay connected to each other using the internet
(Xu, Wendt and Potkonjak 2014). The range of Internet of Things devices is large. They

5
INTERNET OF THINGS SECURITY
include wearable devices, to medical devices and even devices to control automobiles and
factories. The main drawback is that the users think that the devices they are using are safe,
but they lack the security feature, which should have been present. There has been a lot of
research done in order to see ton what extent does it require to hack the Internet of Things
devices. These can be taken control by hackers and be used in harmful ways to harm the user.
As the devices falling under the category of Internet of Things devices are small and use the
sensory and embedded system, they cannot be secured using the steps used to secure a
personal computer (Zhang et al. 2014). Keeping aside the security issues, which may arise, a
few of the applications of Internet of Things Security are given below:
Internet of Things network security: This application is used to secure the connection,
which is used to connect the Internet of Things devices to the internet. If the devices
cannot be secured easily then by securing the network they are connected to can help a
little in securing the Internet of Things devices (Zhang, Cho and Shieh 2015).
Internet of Things Authentication: There should be an ability to implement the use of
authentication of an Internet of Things device. There can be usage of a simple pin number
to using static passwords to authenticate the device. Additional security can be added by
using biometric and digital certificates of the devices being used. However, the method of
using an authentication process is for a human to enter the pin or password into the device
to gain access, but in the use of Internet of Things devices, they are all machine to
machine connected. There are no human interaction in between (Minoli, Sohraby and
Kouns 2017).
Internet of Things encryption: Encryption of information stored on the device and the
ones being transmitted should be encrypted using proper methods. Even if the devices can
get hacked the hacker will be able to find encrypted information on the devices. The
INTERNET OF THINGS SECURITY
include wearable devices, to medical devices and even devices to control automobiles and
factories. The main drawback is that the users think that the devices they are using are safe,
but they lack the security feature, which should have been present. There has been a lot of
research done in order to see ton what extent does it require to hack the Internet of Things
devices. These can be taken control by hackers and be used in harmful ways to harm the user.
As the devices falling under the category of Internet of Things devices are small and use the
sensory and embedded system, they cannot be secured using the steps used to secure a
personal computer (Zhang et al. 2014). Keeping aside the security issues, which may arise, a
few of the applications of Internet of Things Security are given below:
Internet of Things network security: This application is used to secure the connection,
which is used to connect the Internet of Things devices to the internet. If the devices
cannot be secured easily then by securing the network they are connected to can help a
little in securing the Internet of Things devices (Zhang, Cho and Shieh 2015).
Internet of Things Authentication: There should be an ability to implement the use of
authentication of an Internet of Things device. There can be usage of a simple pin number
to using static passwords to authenticate the device. Additional security can be added by
using biometric and digital certificates of the devices being used. However, the method of
using an authentication process is for a human to enter the pin or password into the device
to gain access, but in the use of Internet of Things devices, they are all machine to
machine connected. There are no human interaction in between (Minoli, Sohraby and
Kouns 2017).
Internet of Things encryption: Encryption of information stored on the device and the
ones being transmitted should be encrypted using proper methods. Even if the devices can
get hacked the hacker will be able to find encrypted information on the devices. The
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

6
INTERNET OF THINGS SECURITY
information will require a lot of time before it can be decrypted, till then the information
will be of no use to the hacker.
Internet of Things security analysis of data: Collecting the information from the Internet
of Things devices can be used to do analytical data manipulation to understand the range
of data being dealt with. The information gathered can be used to develop machine-
learning programs and to be added to the collection of big data. Internet of Things
security analysts will now be required to detect the kind of attack the devices will face
(Riahi et al. 2013).
Internet of Things API security: Using procedures during the transmission of information
between the Internet of Things devices should be authenticated and authorized. API
security measures should be used to provide integrity to the data being collected and
transferred.
Security Problems
Information security should always be given top priority in case of electronics
devices. There hackers who are capable of extracting information from any type of devices.
There is a large area of application of the Internet of Things devices due to its implementation
scope and procedures. Though there are benefits to all kinds of technology, drawbacks follow
them closely (Sivaraman et al. 2015). Drawbacks of Internet of Things can be divided into
two parts: security issues and hardware security issues. They are discussed below:
Security Issues:
Security data encryption: There is a huge collection of data from Internet of Things
applications. Retrieving of data and processing the collected information is an essential
part of all Internet of Things applications. Most of the information is personal data 0f the
user thus it needs to be encrypted before saving them.
INTERNET OF THINGS SECURITY
information will require a lot of time before it can be decrypted, till then the information
will be of no use to the hacker.
Internet of Things security analysis of data: Collecting the information from the Internet
of Things devices can be used to do analytical data manipulation to understand the range
of data being dealt with. The information gathered can be used to develop machine-
learning programs and to be added to the collection of big data. Internet of Things
security analysts will now be required to detect the kind of attack the devices will face
(Riahi et al. 2013).
Internet of Things API security: Using procedures during the transmission of information
between the Internet of Things devices should be authenticated and authorized. API
security measures should be used to provide integrity to the data being collected and
transferred.
Security Problems
Information security should always be given top priority in case of electronics
devices. There hackers who are capable of extracting information from any type of devices.
There is a large area of application of the Internet of Things devices due to its implementation
scope and procedures. Though there are benefits to all kinds of technology, drawbacks follow
them closely (Sivaraman et al. 2015). Drawbacks of Internet of Things can be divided into
two parts: security issues and hardware security issues. They are discussed below:
Security Issues:
Security data encryption: There is a huge collection of data from Internet of Things
applications. Retrieving of data and processing the collected information is an essential
part of all Internet of Things applications. Most of the information is personal data 0f the
user thus it needs to be encrypted before saving them.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7
INTERNET OF THINGS SECURITY
Data authentication: After the encryption of the information collected, there can still be a
chance that the device has been hacked from the inside. In this case, there needs to be the
implementation of data authentication from the source it is coming from. All commands
coming to the device should have authentication keys before executing the device (Sfar et
al. 2017).
Side channel issues: Apart from the above two problems there is always a side channel
which can be violated on the device. If the hacker can get access to the time, temperature
controller of the device they can violate the device using the side channel.
Hardware Security Issues:
Range of devices: range of working of the Internet of Things devices should be
determined correctly before implementing the application.
Capacity and latency: capacity and latency of all Internet of Things devices should be
increased which increases the efficiency of working of the devices.
Manufacturability test: Testing the device once the device has been manufactured to
ensure the devices work as to its specifications (Medwed 2016).
INTERNET OF THINGS SECURITY
Data authentication: After the encryption of the information collected, there can still be a
chance that the device has been hacked from the inside. In this case, there needs to be the
implementation of data authentication from the source it is coming from. All commands
coming to the device should have authentication keys before executing the device (Sfar et
al. 2017).
Side channel issues: Apart from the above two problems there is always a side channel
which can be violated on the device. If the hacker can get access to the time, temperature
controller of the device they can violate the device using the side channel.
Hardware Security Issues:
Range of devices: range of working of the Internet of Things devices should be
determined correctly before implementing the application.
Capacity and latency: capacity and latency of all Internet of Things devices should be
increased which increases the efficiency of working of the devices.
Manufacturability test: Testing the device once the device has been manufactured to
ensure the devices work as to its specifications (Medwed 2016).

8
INTERNET OF THINGS SECURITY
Figure 2: The Gartner hype cycle in 2011 showing the Internet of Things on the top
(Source: Iotsecurityfoundation.org, 2017)
There are many different vendors and developers of the Internet of Things devices,
which cause no single platform usage. Different developers use different platforms to
implement their devices. This has made no single platform to stand out in the crowd (Cai et
al. 2017). Due to such lack of security measures in the device, there is a high chance that the
device can be hacked at any time without the user even knowing about it. This is of huge risk.
Cars and health devices using Internet of Things once if it is hacked can cause death like
situations. The hacker can implement the device to work in any kind of situation and stop the
device from working (Pacheco and Hariri 2016).
Security Solutions
Internet of Things technologies are still new to the market (Aman, Chua and Sikdar
2016). There needs to be vigorous testing of security and hardware that needs to be done on
the devices before saying that they are reliable for the consumers to use. Before working on
any device there should be thorough research done on the topic to point out what are the
drawbacks, which needs to be addressed. This would help the developers to assess the
amount of work that needs to be done on the device before releasing it to the consumers.
Threats should be assessed correctly as the devices are cheap thus the developers pay small
attention to the point of security. This should not be the suitable process of development of
electronic devices, which are targeted for storing personal information and can be easily
hacked. Security should be the top most priority during the designing of any device (Tuna et
al. 2017). The developers can follow the following to ensure that they can produce a secured
device for the consumers:
INTERNET OF THINGS SECURITY
Figure 2: The Gartner hype cycle in 2011 showing the Internet of Things on the top
(Source: Iotsecurityfoundation.org, 2017)
There are many different vendors and developers of the Internet of Things devices,
which cause no single platform usage. Different developers use different platforms to
implement their devices. This has made no single platform to stand out in the crowd (Cai et
al. 2017). Due to such lack of security measures in the device, there is a high chance that the
device can be hacked at any time without the user even knowing about it. This is of huge risk.
Cars and health devices using Internet of Things once if it is hacked can cause death like
situations. The hacker can implement the device to work in any kind of situation and stop the
device from working (Pacheco and Hariri 2016).
Security Solutions
Internet of Things technologies are still new to the market (Aman, Chua and Sikdar
2016). There needs to be vigorous testing of security and hardware that needs to be done on
the devices before saying that they are reliable for the consumers to use. Before working on
any device there should be thorough research done on the topic to point out what are the
drawbacks, which needs to be addressed. This would help the developers to assess the
amount of work that needs to be done on the device before releasing it to the consumers.
Threats should be assessed correctly as the devices are cheap thus the developers pay small
attention to the point of security. This should not be the suitable process of development of
electronic devices, which are targeted for storing personal information and can be easily
hacked. Security should be the top most priority during the designing of any device (Tuna et
al. 2017). The developers can follow the following to ensure that they can produce a secured
device for the consumers:
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

9
INTERNET OF THINGS SECURITY
There should be an encrypted digital certificate, which would authorize the device when it
is first powered up. The software, which has the correct authentication certificate, will
only be able to access the device when it has been installed (Wurm et al. 2016).
To limit the use of the device components there should be access controls installed into
the system. They should also be kept at certain limit of usage. The resources should not
be allowed to be used by the application to its full limit. Only the minimum amount of
limitations should be allowed for thee resources.
The device once connected to the internet should authenticate itself using a certificate
before they start transmitting and receiving the data from the internet.
There should be firewall installed on the device to have the ability to monitor the packets,
which are being transmitted and received over the internet (Li and Da Xu 2017).
Updates and patches of the software’s should be delivered to the device without using
excessive resources, which might compromise the safety of the device.
To implement the best security measure the developers can design interoperable and
standard security system, which not only stops hacking of the device but also records the
hacking attempt on the device. The developers of the system should have periodic routine
software updates sent to the Internet of Things devices to patch up the security measures of
the device. Using encrypted methods for the use of data transmission should be implemented
into the devices. This would help the device to keep the device safe from data theft (Li,
Tryfonas and Li 2016).
Conclusion
To conclude this report it can be said that the use of Internet of Things security should
be the top priority for the organizations specializing in the Internet of Things devices.
Discussion about the different applications of the security measures which the producers can
INTERNET OF THINGS SECURITY
There should be an encrypted digital certificate, which would authorize the device when it
is first powered up. The software, which has the correct authentication certificate, will
only be able to access the device when it has been installed (Wurm et al. 2016).
To limit the use of the device components there should be access controls installed into
the system. They should also be kept at certain limit of usage. The resources should not
be allowed to be used by the application to its full limit. Only the minimum amount of
limitations should be allowed for thee resources.
The device once connected to the internet should authenticate itself using a certificate
before they start transmitting and receiving the data from the internet.
There should be firewall installed on the device to have the ability to monitor the packets,
which are being transmitted and received over the internet (Li and Da Xu 2017).
Updates and patches of the software’s should be delivered to the device without using
excessive resources, which might compromise the safety of the device.
To implement the best security measure the developers can design interoperable and
standard security system, which not only stops hacking of the device but also records the
hacking attempt on the device. The developers of the system should have periodic routine
software updates sent to the Internet of Things devices to patch up the security measures of
the device. Using encrypted methods for the use of data transmission should be implemented
into the devices. This would help the device to keep the device safe from data theft (Li,
Tryfonas and Li 2016).
Conclusion
To conclude this report it can be said that the use of Internet of Things security should
be the top priority for the organizations specializing in the Internet of Things devices.
Discussion about the different applications of the security measures which the producers can
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

10
INTERNET OF THINGS SECURITY
use to apply security to the Internet of Things devices shows that even if the devices lack the
security measures there can be security addition to the various methods the devices are
connected to the other devices. The report also discusses about the different problems and the
possible solutions, which can be used by the organizations to counter, measure them.
Avoiding the problems and to provide the best possible measure should be the top most
priority of the organizations providing Internet of Things devices. The developers should
assess the security blind spots of the use of Internet of Things. The devices are not being used
at such a large scale due to the lack in security measure and due to certain legal issue, which
pertain to the fact of sharing personal information over the internet.
INTERNET OF THINGS SECURITY
use to apply security to the Internet of Things devices shows that even if the devices lack the
security measures there can be security addition to the various methods the devices are
connected to the other devices. The report also discusses about the different problems and the
possible solutions, which can be used by the organizations to counter, measure them.
Avoiding the problems and to provide the best possible measure should be the top most
priority of the organizations providing Internet of Things devices. The developers should
assess the security blind spots of the use of Internet of Things. The devices are not being used
at such a large scale due to the lack in security measure and due to certain legal issue, which
pertain to the fact of sharing personal information over the internet.

11
INTERNET OF THINGS SECURITY
References
Aman, M.N., Chua, K.C. and Sikdar, B., 2016, May. Position Paper: Physical Unclonable
Functions for IoT Security. In Proceedings of the 2nd ACM International Workshop on IoT
Privacy, Trust, and Security (pp. 10-13). ACM.
Cai, H., Yun, T., Hester, J. and Venkatasubramanian, K.K., 2017, June. Deploying Data-
Driven Security Solutions on Resource-Constrained Wearable IoT Systems. In Distributed
Computing Systems Workshops (ICDCSW), 2017 IEEE 37th International Conference on
(pp. 199-204). IEEE.
Gubbi, J., Buyya, R., Marusic, S. and Palaniswami, M., 2013. Internet of Things (IoT): A
vision, architectural elements, and future directions. Future generation computer systems,
29(7), pp.1645-1660.
Iotsecurityfoundation.org. (2017). Reporting front row from the IoT Security Foundation
launch – IoT Security Foundation. [online] Available at:
https://iotsecurityfoundation.org/reporting-front-row-from-the-iot-security-foundation-
launch/ [Accessed 15 Aug. 2017].
Li, S. and Da Xu, L., 2017. Security in Enabling Technologies. Securing the Internet of
Things, p.109.
Li, S., Tryfonas, T. and Li, H., 2016. The internet of things: a security point of view. Internet
Research, 26(2), pp.337-359.
Medwed, M., 2016, October. Iot security challenges and ways forward. In Proceedings of the
6th International Workshop on Trustworthy Embedded Devices (pp. 55-55). ACM.
Minoli, D., Sohraby, K. and Kouns, J., 2017, January. IoT security (IoTSec) considerations,
requirements, and architectures. In Consumer Communications & Networking Conference
(CCNC), 2017 14th IEEE Annual(pp. 1006-1007). IEEE.
INTERNET OF THINGS SECURITY
References
Aman, M.N., Chua, K.C. and Sikdar, B., 2016, May. Position Paper: Physical Unclonable
Functions for IoT Security. In Proceedings of the 2nd ACM International Workshop on IoT
Privacy, Trust, and Security (pp. 10-13). ACM.
Cai, H., Yun, T., Hester, J. and Venkatasubramanian, K.K., 2017, June. Deploying Data-
Driven Security Solutions on Resource-Constrained Wearable IoT Systems. In Distributed
Computing Systems Workshops (ICDCSW), 2017 IEEE 37th International Conference on
(pp. 199-204). IEEE.
Gubbi, J., Buyya, R., Marusic, S. and Palaniswami, M., 2013. Internet of Things (IoT): A
vision, architectural elements, and future directions. Future generation computer systems,
29(7), pp.1645-1660.
Iotsecurityfoundation.org. (2017). Reporting front row from the IoT Security Foundation
launch – IoT Security Foundation. [online] Available at:
https://iotsecurityfoundation.org/reporting-front-row-from-the-iot-security-foundation-
launch/ [Accessed 15 Aug. 2017].
Li, S. and Da Xu, L., 2017. Security in Enabling Technologies. Securing the Internet of
Things, p.109.
Li, S., Tryfonas, T. and Li, H., 2016. The internet of things: a security point of view. Internet
Research, 26(2), pp.337-359.
Medwed, M., 2016, October. Iot security challenges and ways forward. In Proceedings of the
6th International Workshop on Trustworthy Embedded Devices (pp. 55-55). ACM.
Minoli, D., Sohraby, K. and Kouns, J., 2017, January. IoT security (IoTSec) considerations,
requirements, and architectures. In Consumer Communications & Networking Conference
(CCNC), 2017 14th IEEE Annual(pp. 1006-1007). IEEE.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 14
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





