Security in the Internet of Things (IoT): Issues and Solutions
VerifiedAdded on 2020/02/24
|12
|2426
|306
Report
AI Summary
This report provides a critical review of the Internet of Things (IoT), exploring its security challenges and potential solutions. The report begins with an overview of the IoT, defining its core concepts and applications across various sectors such as healthcare, home automation, and retail. It then delves into the security issues that plague IoT devices, including insecure web interfaces, insufficient authentication, and the threat of hacking. The report highlights the importance of device status monitoring, end-to-end encryption, user education, and penetration testing as crucial security measures. Furthermore, it discusses technologies associated with the IoT, such as IoT analytics and distributed computing stream platforms, and their real-world applications. The report concludes by emphasizing the need for enhanced security measures to safeguard the growing number of interconnected devices and the sensitive data they generate.

Running head: INTERNET OF THINGS 1
Internet of Things (IOT): Security issues and solutions
Name:
Institution Affiliation:
Internet of Things (IOT): Security issues and solutions
Name:
Institution Affiliation:
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

INTERNET OF THINGS 2
Executive Summary
In this research it aims to provide a critical review on the aspect of internet of things. The world
is adapting this technology, therefore a need arises to understand it and what it could provide.
Additionally, this report will give an overview of the internet of things from the perspective of
security issues and how it has offered solutions to the businesses.
Executive Summary
In this research it aims to provide a critical review on the aspect of internet of things. The world
is adapting this technology, therefore a need arises to understand it and what it could provide.
Additionally, this report will give an overview of the internet of things from the perspective of
security issues and how it has offered solutions to the businesses.

INTERNET OF THINGS 3
Table of Contents
Introduction...............................................................................................................................................4
Overview of internet of things..................................................................................................................4
Applications of the internet of things.......................................................................................................5
Security issues and solution in IOT..........................................................................................................6
Security issues of IOT...............................................................................................................................6
Security solutions utilized in internet of things.......................................................................................7
Technologies associated with internet of things and application to real world.....................................8
Conclusion..................................................................................................................................................9
References.................................................................................................................................................10
Table of Contents
Introduction...............................................................................................................................................4
Overview of internet of things..................................................................................................................4
Applications of the internet of things.......................................................................................................5
Security issues and solution in IOT..........................................................................................................6
Security issues of IOT...............................................................................................................................6
Security solutions utilized in internet of things.......................................................................................7
Technologies associated with internet of things and application to real world.....................................8
Conclusion..................................................................................................................................................9
References.................................................................................................................................................10
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

INTERNET OF THINGS 4
Introduction
The world of technology has advanced tremendously over the past few years. Every day there is
launching of a given technology (Bonomi, Milito, Zhu & Addepalli, 2012). Among such
technology which has taken the world by storm is the internet off things (IOT). In this research it
aims to explore more on this topic of internet of things. Some of the research questions which
will be addressed are as follows;
What is regarded as the internet of things?
How are these issues being addressed?
What are some of the solutions that internet of things solved?
Which are some of technology which are used in internet of things?
Overview of internet of things
The internet of things is the sprawling set of technologies which uses the cases which have no
clear, definition. One of the workable frames of the internet of things is the use of the network-
connected devices that are embedded in the physical environment, in order to improve some of
the existing process or perhaps enable a new scenario which was not possible previously (Da Xu,
He & Li, 2014). Every individual uses a smart device which could be anything from that contain
an electronics, sensors, software that are connected to a network. The term internet of things in
this regards refers to the interconnection of all these things (Gubbi, Buyya, Marusic &
Palaniswami, 2013). Once they are launched online they are capable of collecting and
exchanging data without any human intervention. Recently, it has been observed that
technologies such as the internet of things have emerged due to internet of things technology.
Introduction
The world of technology has advanced tremendously over the past few years. Every day there is
launching of a given technology (Bonomi, Milito, Zhu & Addepalli, 2012). Among such
technology which has taken the world by storm is the internet off things (IOT). In this research it
aims to explore more on this topic of internet of things. Some of the research questions which
will be addressed are as follows;
What is regarded as the internet of things?
How are these issues being addressed?
What are some of the solutions that internet of things solved?
Which are some of technology which are used in internet of things?
Overview of internet of things
The internet of things is the sprawling set of technologies which uses the cases which have no
clear, definition. One of the workable frames of the internet of things is the use of the network-
connected devices that are embedded in the physical environment, in order to improve some of
the existing process or perhaps enable a new scenario which was not possible previously (Da Xu,
He & Li, 2014). Every individual uses a smart device which could be anything from that contain
an electronics, sensors, software that are connected to a network. The term internet of things in
this regards refers to the interconnection of all these things (Gubbi, Buyya, Marusic &
Palaniswami, 2013). Once they are launched online they are capable of collecting and
exchanging data without any human intervention. Recently, it has been observed that
technologies such as the internet of things have emerged due to internet of things technology.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

INTERNET OF THINGS 5
Applications of the internet of things
This technology has been used in all the industries ranging from use at home as well as other
field such as medicine, engineering and for operations in the business. Some of ways it has been
incorporated is as follows;
Health sector: when it comes to the health sector the world has encountered a high number of
individuals seeking the medical attention. The real issue arises when there is lack of enough
expertise in this sector (Gubbi, Buyya, Marusic & Palaniswami, 2013). However, to deal with
this issue the internet of things has incorporated system which are used in remote monitoring of
the patients especially in the diagnosis and the delivery of the correct medicine to the patients.
Another application of the internet of things is in home automation. Individuals are able to
connect all objects they have ranging from the appliances as well as the automobiles. When it
comes to the retail shop the internet of things has been used (Ntuli & Abu-Mahfouz, 2016).
Individuals today no longer use the bar codes when it comes to monitoring of the movement of
their goods (Jones, 2015). With the application such as radio frequency identification, the retail
shop owners have the capability of monitoring all their stock and get real time data which will be
essential when it comes to making of decisions (Jones, 2015). Additionally, the IOT has been
used in the industry automation, where the industries are automating most of their processes to
be able to improve on their efficiency. The manufacturing and the logistics sectors have also not
been left behind when it comes to acquiring this technology, especially in the use of the machine
to machine interaction as well as being able to track their goods while they are in transit. The use
of these technology has been possible through the use of the internet of things.
Applications of the internet of things
This technology has been used in all the industries ranging from use at home as well as other
field such as medicine, engineering and for operations in the business. Some of ways it has been
incorporated is as follows;
Health sector: when it comes to the health sector the world has encountered a high number of
individuals seeking the medical attention. The real issue arises when there is lack of enough
expertise in this sector (Gubbi, Buyya, Marusic & Palaniswami, 2013). However, to deal with
this issue the internet of things has incorporated system which are used in remote monitoring of
the patients especially in the diagnosis and the delivery of the correct medicine to the patients.
Another application of the internet of things is in home automation. Individuals are able to
connect all objects they have ranging from the appliances as well as the automobiles. When it
comes to the retail shop the internet of things has been used (Ntuli & Abu-Mahfouz, 2016).
Individuals today no longer use the bar codes when it comes to monitoring of the movement of
their goods (Jones, 2015). With the application such as radio frequency identification, the retail
shop owners have the capability of monitoring all their stock and get real time data which will be
essential when it comes to making of decisions (Jones, 2015). Additionally, the IOT has been
used in the industry automation, where the industries are automating most of their processes to
be able to improve on their efficiency. The manufacturing and the logistics sectors have also not
been left behind when it comes to acquiring this technology, especially in the use of the machine
to machine interaction as well as being able to track their goods while they are in transit. The use
of these technology has been possible through the use of the internet of things.

INTERNET OF THINGS 6
Security issues and solution in IOT
According to Gartner (2013) he oversees a world where there are more than twenty six billion
devices which have been connected to the internet by the year 2020. Moreover, some researcher
have taken this number to a high level of fifty billion devices in the same period (Rivera & van
der Meulen, 2013). This is a scary trend considering the rise of the hacking problems which have
been exhibited across the globe (Jones, 2015). Nevertheless, there would be a large volume of
data which will be generated every second, still the world has yet to bring technology to process
such volume of data in an efficient manner (Jones, 2015). Below are some of the security issues
which have been encountered as a result in use of internet of things.
Security issues of IOT
The current technology entails one to secure the servers, personal computers as well as other
devices employing latest security protocols and practices (Jones, 2015). Nonetheless, the security
of internet of things can be hard to maintain considering it uses bi-directional communication
whose security is still developing. Some of the security issues which faces internet of things are
as follows;
One of the issue is the insecure web interfaces. This is one of the top ten vulnerability which has
been outlined by the open web Application security project (Jones, 2015). This threat is found I
the web interfaces which are found in all the internet of things devices.
The second issue is insufficient authentication. This usually occurs when an application permits
an attacker to access sensitive information or perhaps functionality without proper authenticate,
such as accessing the controls of the admin by going to the admin directory without having to log
in (Wortmann & Flüchter, 2015). Therefore, when the devices allows user to login with a lame
Security issues and solution in IOT
According to Gartner (2013) he oversees a world where there are more than twenty six billion
devices which have been connected to the internet by the year 2020. Moreover, some researcher
have taken this number to a high level of fifty billion devices in the same period (Rivera & van
der Meulen, 2013). This is a scary trend considering the rise of the hacking problems which have
been exhibited across the globe (Jones, 2015). Nevertheless, there would be a large volume of
data which will be generated every second, still the world has yet to bring technology to process
such volume of data in an efficient manner (Jones, 2015). Below are some of the security issues
which have been encountered as a result in use of internet of things.
Security issues of IOT
The current technology entails one to secure the servers, personal computers as well as other
devices employing latest security protocols and practices (Jones, 2015). Nonetheless, the security
of internet of things can be hard to maintain considering it uses bi-directional communication
whose security is still developing. Some of the security issues which faces internet of things are
as follows;
One of the issue is the insecure web interfaces. This is one of the top ten vulnerability which has
been outlined by the open web Application security project (Jones, 2015). This threat is found I
the web interfaces which are found in all the internet of things devices.
The second issue is insufficient authentication. This usually occurs when an application permits
an attacker to access sensitive information or perhaps functionality without proper authenticate,
such as accessing the controls of the admin by going to the admin directory without having to log
in (Wortmann & Flüchter, 2015). Therefore, when the devices allows user to login with a lame
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

INTERNET OF THINGS 7
password or password which are not secure enough it could be possible for the attacker to have
an access.
Hacking: this refers to the issue related to the ransomware, the distributed Denial attack or
perhaps an identity theft. The issue in regards to this security concern is that some devices are
important and in the event they are tampered with there could be catastrophic effects such as the
health monitoring system (Wortmann & Flüchter, 2015). Moreover, the information which is
contained there could be used for malicious activities by the cyber criminals.
Security solutions utilized in internet of things
There are various solutions which could be put in place to ensure there is security in the internet
of things technology, these are as follows;
Device status monitoring: each device which has been connected to the internet need to be
monitored more frequently (Wortmann & Flüchter, 2015). In the event the device goes offline,
the user should be in a position to know immediately and have measures in place to stop the flow
of data and be able to identify the sudden changes on its status (Wortmann & Flüchter, 2015). A
practical example of this is on the smart TV, in the event it goes offline this could mean that
there is someone who has tampered with it or perhaps there is issues of internet outage (Jones,
2015). The internet of things metadata tracking programs could be utilized in such as a situation.
End to end encryption: to be in a position to enable there is an end to end security, there is need
to employ technology such as the Advanced Encryption standard which is integrated with the
existing standards (Tan & Wang, 2010). The use of such technology could ensure that only the
devices which have an encryption keys are capable of transmitting as well as decrypting data
from the source of the devices.
password or password which are not secure enough it could be possible for the attacker to have
an access.
Hacking: this refers to the issue related to the ransomware, the distributed Denial attack or
perhaps an identity theft. The issue in regards to this security concern is that some devices are
important and in the event they are tampered with there could be catastrophic effects such as the
health monitoring system (Wortmann & Flüchter, 2015). Moreover, the information which is
contained there could be used for malicious activities by the cyber criminals.
Security solutions utilized in internet of things
There are various solutions which could be put in place to ensure there is security in the internet
of things technology, these are as follows;
Device status monitoring: each device which has been connected to the internet need to be
monitored more frequently (Wortmann & Flüchter, 2015). In the event the device goes offline,
the user should be in a position to know immediately and have measures in place to stop the flow
of data and be able to identify the sudden changes on its status (Wortmann & Flüchter, 2015). A
practical example of this is on the smart TV, in the event it goes offline this could mean that
there is someone who has tampered with it or perhaps there is issues of internet outage (Jones,
2015). The internet of things metadata tracking programs could be utilized in such as a situation.
End to end encryption: to be in a position to enable there is an end to end security, there is need
to employ technology such as the Advanced Encryption standard which is integrated with the
existing standards (Tan & Wang, 2010). The use of such technology could ensure that only the
devices which have an encryption keys are capable of transmitting as well as decrypting data
from the source of the devices.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

INTERNET OF THINGS 8
Another way could be through education of the users: According to research it has been known
that one of the main causes of security attack of these devices has been because most individuals
do not know how to set up the devices well (Weber & Weber, 2010). It is important to educate
the users on the possible threats and ways of keeping them secure and how they could reduce
attacks.
End to end penetration testing: this test is usually undertaken to identify any kind of
vulnerabilities which could exists in the internet of things devices interface and the appropriate
solutions which can be applied to minimize these risks (Weber & Weber, 2010).
The ban on the Open Inbound ports in devices: previously, there were ports which were initially
used for communication between the devices (Xia, Yang, Wang & Vinel, 2012). The major
concern with them is that they demand to be left open, this could create a vulnerability for the
attackers who are able to gain access. When one does not use these ports, and alternatively uses
the outbound connections, the devices remain secure.
Technologies associated with internet of things and application to real world
One of the technology is the Internet of things analytics; these technology tend to generate a lot
of volume of data every second, therefore there is need for the systems to analyse on this data
and provide useful data for making decisions (Xia, Yang, Wang & Vinel, 2012). An example of
this is the health monitoring system which monitors the activities of a person and communicate
any changes which is exhibited. Another technology is the distributed computing stream
platforms (DCSP) (Xia, Yang, Wang & Vinel, 2012). These technology have capability of
processing high rate of data stream which is provided by the internet of things devices in
performing tasks for example identification of the pattern and the real time analytics. Many
business could utilize such technology when they want to predict the market.
Another way could be through education of the users: According to research it has been known
that one of the main causes of security attack of these devices has been because most individuals
do not know how to set up the devices well (Weber & Weber, 2010). It is important to educate
the users on the possible threats and ways of keeping them secure and how they could reduce
attacks.
End to end penetration testing: this test is usually undertaken to identify any kind of
vulnerabilities which could exists in the internet of things devices interface and the appropriate
solutions which can be applied to minimize these risks (Weber & Weber, 2010).
The ban on the Open Inbound ports in devices: previously, there were ports which were initially
used for communication between the devices (Xia, Yang, Wang & Vinel, 2012). The major
concern with them is that they demand to be left open, this could create a vulnerability for the
attackers who are able to gain access. When one does not use these ports, and alternatively uses
the outbound connections, the devices remain secure.
Technologies associated with internet of things and application to real world
One of the technology is the Internet of things analytics; these technology tend to generate a lot
of volume of data every second, therefore there is need for the systems to analyse on this data
and provide useful data for making decisions (Xia, Yang, Wang & Vinel, 2012). An example of
this is the health monitoring system which monitors the activities of a person and communicate
any changes which is exhibited. Another technology is the distributed computing stream
platforms (DCSP) (Xia, Yang, Wang & Vinel, 2012). These technology have capability of
processing high rate of data stream which is provided by the internet of things devices in
performing tasks for example identification of the pattern and the real time analytics. Many
business could utilize such technology when they want to predict the market.

INTERNET OF THINGS 9
Conclusion
Currently, the world is opening to the possibilities of the internet of things. Each day devices are
being developed and are being connected to the internet. There are many benefits which have
been gained as a result of this interconnection. Nevertheless, as highlighted in the research, this
has been brought about by many challenges on the devices. The problem ranges from data theft,
which are getting worse every day. The world therefore needs to focus more on how to improve
the security of the internet of things devices.
Conclusion
Currently, the world is opening to the possibilities of the internet of things. Each day devices are
being developed and are being connected to the internet. There are many benefits which have
been gained as a result of this interconnection. Nevertheless, as highlighted in the research, this
has been brought about by many challenges on the devices. The problem ranges from data theft,
which are getting worse every day. The world therefore needs to focus more on how to improve
the security of the internet of things devices.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

INTERNET OF THINGS 10
References
Bonomi, F., Milito, R., Zhu, J., & Addepalli, S. (2012, August). Fog computing and its role in
the internet of things. In Proceedings of the first edition of the MCC workshop on Mobile
cloud computing (pp. 13-16). ACM.
Da Xu, L., He, W., & Li, S. (2014). Internet of things in industries: A survey. IEEE Transactions
on industrial informatics, 10(4), 2233-2243.
Gubbi, J., Buyya, R., Marusic, S., & Palaniswami, M. (2013). Internet of Things (IoT): A vision,
architectural elements, and future directions. Future generation computer systems, 29(7),
1645-1660.
Jones, L. K. (2015). The insecurity of things: How to manage the internet of things (Doctoral
dissertation, Utica College).
Ntuli, N., & Abu-Mahfouz, A. (2016). A simple security architecture for smart water
management system. Procedia Computer Science, 83, 1164-1169.
Rivera, J., & van der Meulen, R. (2013). Gartner says the internet of things installed base will
grow to 26 billion units by 2020. Stamford, conn., December, 12.
Tan, L., & Wang, N. (2010, August). Future internet: The internet of things. In Advanced
Computer Theory and Engineering (ICACTE), 2010 3rd International Conference on
(Vol. 5, pp. V5-376). IEEE.
Weber, R. H., & Weber, R. (2010). Internet of things (Vol. 12). New York, NY, USA:: Springer.
Wortmann, F., & Flüchter, K. (2015). Internet of things. Business & Information Systems
Engineering, 57(3), 221-224.
Xia, F., Yang, L. T., Wang, L., & Vinel, A. (2012). Internet of things. International Journal of
Communication Systems, 25(9), 1101.
Zanella, A., Bui, N., Castellani, A., Vangelista, L., & Zorzi, M. (2014). Internet of things for
smart cities. IEEE Internet of Things journal, 1(1), 22-32.
References
Bonomi, F., Milito, R., Zhu, J., & Addepalli, S. (2012, August). Fog computing and its role in
the internet of things. In Proceedings of the first edition of the MCC workshop on Mobile
cloud computing (pp. 13-16). ACM.
Da Xu, L., He, W., & Li, S. (2014). Internet of things in industries: A survey. IEEE Transactions
on industrial informatics, 10(4), 2233-2243.
Gubbi, J., Buyya, R., Marusic, S., & Palaniswami, M. (2013). Internet of Things (IoT): A vision,
architectural elements, and future directions. Future generation computer systems, 29(7),
1645-1660.
Jones, L. K. (2015). The insecurity of things: How to manage the internet of things (Doctoral
dissertation, Utica College).
Ntuli, N., & Abu-Mahfouz, A. (2016). A simple security architecture for smart water
management system. Procedia Computer Science, 83, 1164-1169.
Rivera, J., & van der Meulen, R. (2013). Gartner says the internet of things installed base will
grow to 26 billion units by 2020. Stamford, conn., December, 12.
Tan, L., & Wang, N. (2010, August). Future internet: The internet of things. In Advanced
Computer Theory and Engineering (ICACTE), 2010 3rd International Conference on
(Vol. 5, pp. V5-376). IEEE.
Weber, R. H., & Weber, R. (2010). Internet of things (Vol. 12). New York, NY, USA:: Springer.
Wortmann, F., & Flüchter, K. (2015). Internet of things. Business & Information Systems
Engineering, 57(3), 221-224.
Xia, F., Yang, L. T., Wang, L., & Vinel, A. (2012). Internet of things. International Journal of
Communication Systems, 25(9), 1101.
Zanella, A., Bui, N., Castellani, A., Vangelista, L., & Zorzi, M. (2014). Internet of things for
smart cities. IEEE Internet of Things journal, 1(1), 22-32.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

INTERNET OF THINGS 11
Glossary
IOT- internet of things
DCSP- Distributed computing stream platforms
Glossary
IOT- internet of things
DCSP- Distributed computing stream platforms
INTERNET OF THINGS 12
Appendices
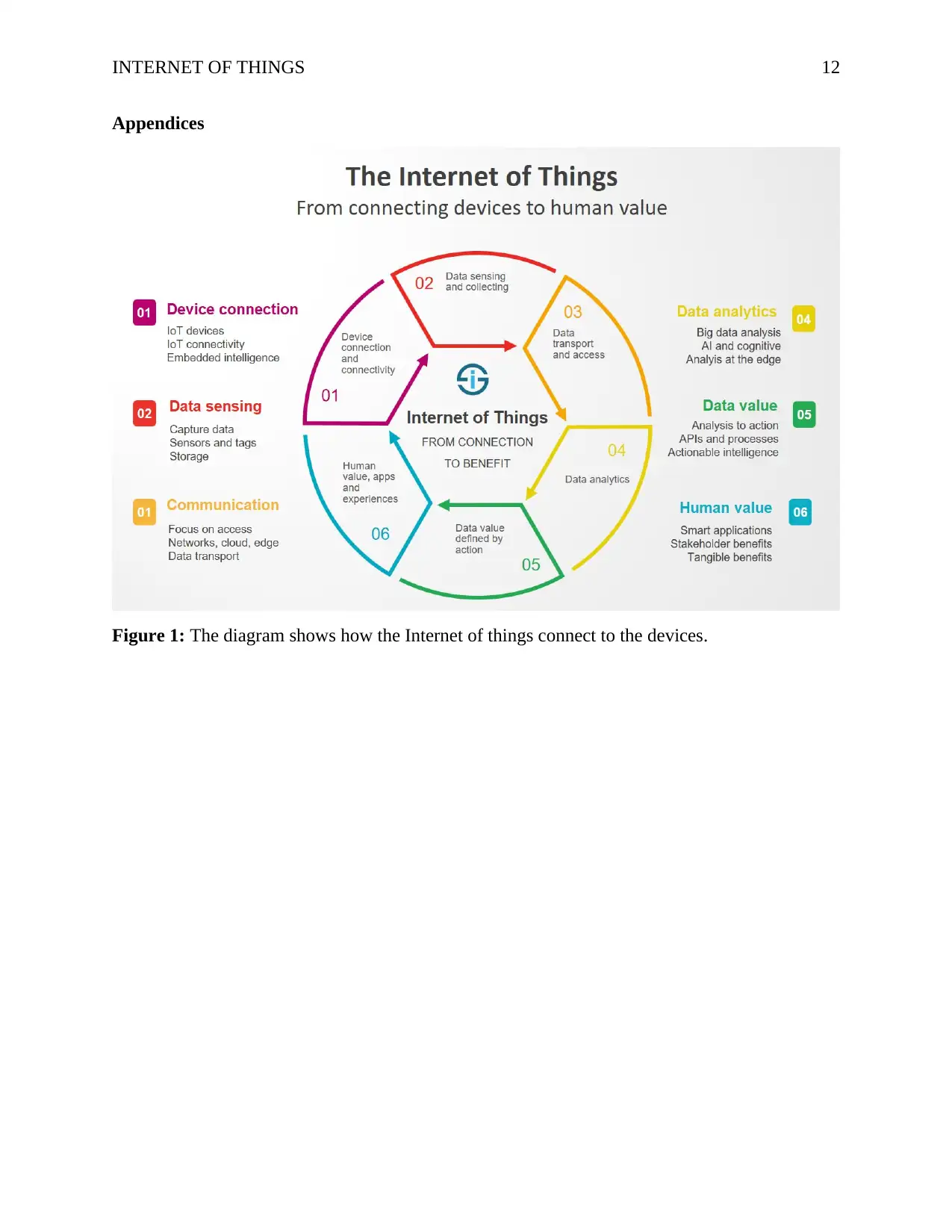
Figure 1: The diagram shows how the Internet of things connect to the devices.
Appendices
Figure 1: The diagram shows how the Internet of things connect to the devices.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 12
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.


