A Report on Internet of Things: Security Attacks and Protocols
VerifiedAdded on 2022/08/22
|12
|2759
|21
Report
AI Summary
This report provides a comprehensive analysis of Internet of Things (IoT) technology, focusing on security vulnerabilities and countermeasures. It begins by introducing the concept of IoT and its integration into everyday life, highlighting the increasing number of interconnected devices. The report then delves into various attacks on IoT devices, including the Mirai botnet, man-in-the-middle attacks, and SQL injection attacks, providing a comparative analysis of these incidents. Furthermore, it outlines several countermeasures to mitigate these threats, such as secure boot, mutual authentication, secure communication, and security monitoring. The report also discusses authentication protocols specific to IoT devices, including MA-PIMP and S2M, evaluating their strengths and weaknesses. The conclusion emphasizes the importance of addressing security concerns to ensure the safe and effective deployment of IoT technologies.

Running head: INTERNET OF THINGS
INTERNET OF THINGS
Name of student
Name of university
Author’s note:
INTERNET OF THINGS
Name of student
Name of university
Author’s note:
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1
INTERNET OF THINGS
Table of Contents
Introduction....................................................................................................................2
Discussion......................................................................................................................2
Comparison of recent attacks.....................................................................................4
Counter measures against the IoT attacks..................................................................6
Authentication protocol of IoT devices......................................................................7
Conclusion......................................................................................................................8
References......................................................................................................................9
INTERNET OF THINGS
Table of Contents
Introduction....................................................................................................................2
Discussion......................................................................................................................2
Comparison of recent attacks.....................................................................................4
Counter measures against the IoT attacks..................................................................6
Authentication protocol of IoT devices......................................................................7
Conclusion......................................................................................................................8
References......................................................................................................................9

2
INTERNET OF THINGS
Introduction
Presently, with the introduction of various Iot based technology, the people are
gaining the improved functionalities and features that were not available earlier. The IoT
technology is growing to be the vital section of everyday life and millions of IoT devices are
presently connected among one another that allows the collection of data using the wireless
technologies and could interoperate in the existing internet infrastructure. This report aims to
analyse the various IoT technology and analyse the attacks that are conducted on the various
IoT devices. Appropriate comparison of the variant of attacks on IoT devices have been
executed. The appropriate countermeasures against the attacks have been provided. A brief
discussion of the authentication protocols that are specific to the IoT devices have been
clearly briefed.
Discussion
The technology of Internet of Things mainly denotes to the kind of network for
connecting anything with the internet depending on the specified protocols through the
equipment of sensing information for conducting the information exchange as well as the
communication for achieving the smart recognitions, monitoring, tracing, as well as the
administration (Ray 2018). Concept of the IoT was provided by the member of the developer
of Radio Frequency Identification and it has grown to be significantly linked with practical
world due to the growth of the mobile devices, the implanted as well as the ubiquitous
communications, data analytics and the cloud computing. With the introduction of the IoT
technology, the billions of the objects could sense, communicate as well as share the
information, all of them interconnected over the private or the public Internet Protocol
networks. These kinds of interconnected objects have the functionality of constant collection,
analysis, as well as utilising the information for initiating any kind of actions, provide the
INTERNET OF THINGS
Introduction
Presently, with the introduction of various Iot based technology, the people are
gaining the improved functionalities and features that were not available earlier. The IoT
technology is growing to be the vital section of everyday life and millions of IoT devices are
presently connected among one another that allows the collection of data using the wireless
technologies and could interoperate in the existing internet infrastructure. This report aims to
analyse the various IoT technology and analyse the attacks that are conducted on the various
IoT devices. Appropriate comparison of the variant of attacks on IoT devices have been
executed. The appropriate countermeasures against the attacks have been provided. A brief
discussion of the authentication protocols that are specific to the IoT devices have been
clearly briefed.
Discussion
The technology of Internet of Things mainly denotes to the kind of network for
connecting anything with the internet depending on the specified protocols through the
equipment of sensing information for conducting the information exchange as well as the
communication for achieving the smart recognitions, monitoring, tracing, as well as the
administration (Ray 2018). Concept of the IoT was provided by the member of the developer
of Radio Frequency Identification and it has grown to be significantly linked with practical
world due to the growth of the mobile devices, the implanted as well as the ubiquitous
communications, data analytics and the cloud computing. With the introduction of the IoT
technology, the billions of the objects could sense, communicate as well as share the
information, all of them interconnected over the private or the public Internet Protocol
networks. These kinds of interconnected objects have the functionality of constant collection,
analysis, as well as utilising the information for initiating any kind of actions, provide the
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3
INTERNET OF THINGS
wealth of information for executing planning, management, and the decision making. The
Internet of Things technology has also been perceived as network of various physical objects
(Jeschke et al. 2017). The internet is not solely the network of various computers, but it
presently has grown into the network of various devices of various kinds as well as sizes,
smart phones, the home appliances, the vehicles, cameras, building, that all are connected and
are constantly communicating and sharing the information on the basis of the stipulated
protocols for achieving the smart reorganisations, tracing, positioning, safe & Control, and
even the personal online monitoring in real time, online upgrade, administration and the
process control. The internet of things also denotes to common idea of the things, specifically
the daily objects, that have been made recognisable, readable, addressable, locatable using the
devices of information sensing that works through the internet without depending on the
means of communication (Li et al. 2018). The everyday objects involves not solely all the
electronic devices that are presently encountered by the people or even all the products of the
extensive technological development but also the things that are not considered commonly to
be electronic. Internet of things is presently viewed as the revolution of internet technology.
The objects makes themselves significantly recognisable as well as obtain the intelligence by
the development or even enabling the context associated decisions with the help of the
communication of information among themselves. The devices have been provided with the
functionality of accessing the information which have been collected by the other things or
even they could be modules of the complex services (Dastjerdi and Buyya 2016). This
particular transition has been found to be concomitant with emergence of the capabilities of
cloud computing as well as the transformation of Internet towards the IPv6 with the
unrestricted capacity of addressing. Internet of things has been considered to be the
worldwide infrastructure for ensuring the information security, allowing the progressive
services by the interconnection of the things on the basis of the existing as well as the
INTERNET OF THINGS
wealth of information for executing planning, management, and the decision making. The
Internet of Things technology has also been perceived as network of various physical objects
(Jeschke et al. 2017). The internet is not solely the network of various computers, but it
presently has grown into the network of various devices of various kinds as well as sizes,
smart phones, the home appliances, the vehicles, cameras, building, that all are connected and
are constantly communicating and sharing the information on the basis of the stipulated
protocols for achieving the smart reorganisations, tracing, positioning, safe & Control, and
even the personal online monitoring in real time, online upgrade, administration and the
process control. The internet of things also denotes to common idea of the things, specifically
the daily objects, that have been made recognisable, readable, addressable, locatable using the
devices of information sensing that works through the internet without depending on the
means of communication (Li et al. 2018). The everyday objects involves not solely all the
electronic devices that are presently encountered by the people or even all the products of the
extensive technological development but also the things that are not considered commonly to
be electronic. Internet of things is presently viewed as the revolution of internet technology.
The objects makes themselves significantly recognisable as well as obtain the intelligence by
the development or even enabling the context associated decisions with the help of the
communication of information among themselves. The devices have been provided with the
functionality of accessing the information which have been collected by the other things or
even they could be modules of the complex services (Dastjerdi and Buyya 2016). This
particular transition has been found to be concomitant with emergence of the capabilities of
cloud computing as well as the transformation of Internet towards the IPv6 with the
unrestricted capacity of addressing. Internet of things has been considered to be the
worldwide infrastructure for ensuring the information security, allowing the progressive
services by the interconnection of the things on the basis of the existing as well as the
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

4
INTERNET OF THINGS
evolving information that are interoperable and the communication technologies (Christidis
and Devetsikiotis 2016).
Comparison of recent attacks
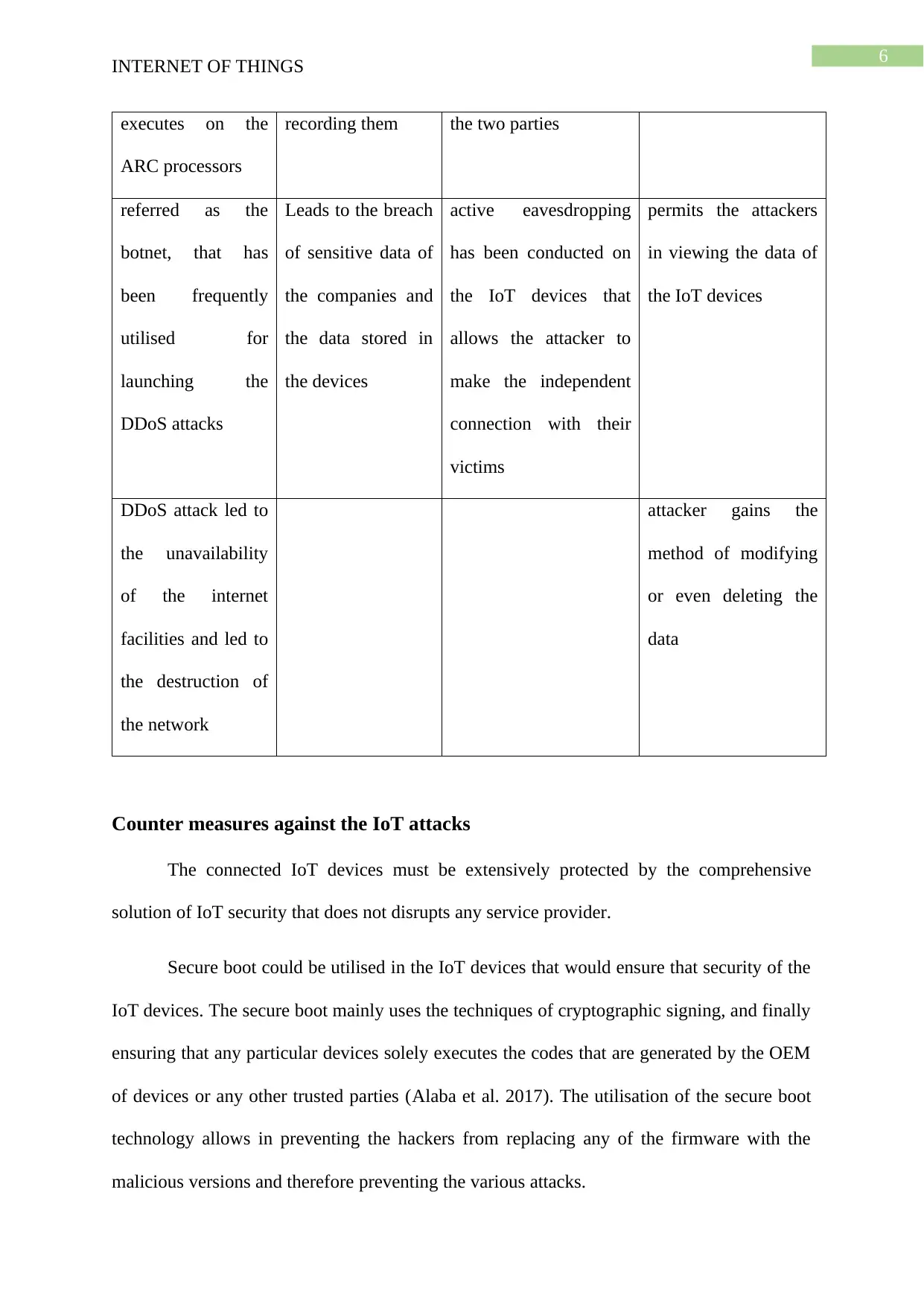
Mirai botnet: On October 12, 2016 significantly huge distributed denial of the
services attack led to the loss of internet services on the US east coast. Mirai botnet is the
malware that is being used for infecting the smart devices which executes on the ARC
processors, transforming them into the network of the remotely controlled bots or the
zombies. This kind of network of the bots have been referred as the botnet, that has been
frequently utilised for launching the DDoS attacks. The DDoS attack led to the unavailability
of the internet facilities and led to the destruction of the network of various organisations
(Bertino and Islam 2017).
Various incidents including the connected cameras as well as the devices in the hotels
as well as Airbnbs spurred the privacy concerns around 2019, that involved the major flaw in
the in-room Tapia robots of the hotels that were used as the replacement of the human staff
who were found to be significantly inefficient (Stojkoska and Trivodaliev 2017). Replacing
the humans with the robots helped the organisation to provide the improved services to the
customers all time but the vulnerability led to the major attacks in the system of the
companies. In the associated incident, Airbnb came under the fire around 2019 where the
guests reported the hidden connected camera that are were used for recording them in the
houses of Airbnb.
Several companies and people have faced the man-in-the-middle attack on the IoT
devices that have led to the breach of huge amount of data (Botta et al. 2016). The man-in-
the-middle attack could be considered as the kind of attack where any attacker could secretly
relay as well as possibly alter the communications among the two parties who consider that
INTERNET OF THINGS
evolving information that are interoperable and the communication technologies (Christidis
and Devetsikiotis 2016).
Comparison of recent attacks
Mirai botnet: On October 12, 2016 significantly huge distributed denial of the
services attack led to the loss of internet services on the US east coast. Mirai botnet is the
malware that is being used for infecting the smart devices which executes on the ARC
processors, transforming them into the network of the remotely controlled bots or the
zombies. This kind of network of the bots have been referred as the botnet, that has been
frequently utilised for launching the DDoS attacks. The DDoS attack led to the unavailability
of the internet facilities and led to the destruction of the network of various organisations
(Bertino and Islam 2017).
Various incidents including the connected cameras as well as the devices in the hotels
as well as Airbnbs spurred the privacy concerns around 2019, that involved the major flaw in
the in-room Tapia robots of the hotels that were used as the replacement of the human staff
who were found to be significantly inefficient (Stojkoska and Trivodaliev 2017). Replacing
the humans with the robots helped the organisation to provide the improved services to the
customers all time but the vulnerability led to the major attacks in the system of the
companies. In the associated incident, Airbnb came under the fire around 2019 where the
guests reported the hidden connected camera that are were used for recording them in the
houses of Airbnb.
Several companies and people have faced the man-in-the-middle attack on the IoT
devices that have led to the breach of huge amount of data (Botta et al. 2016). The man-in-
the-middle attack could be considered as the kind of attack where any attacker could secretly
relay as well as possibly alter the communications among the two parties who consider that

5
INTERNET OF THINGS
they are only communicating among one another. The active eavesdropping has been
conducted on the IoT devices that allows the attacker to make the autonomous connection
with their victims and relaying the messages among them for making them perceive that they
are talking to one another over the private connection but factually, the complete
conversation is being controlled by attacker.
Some of the IoT devices have been discovered to be significantly vulnerable to the
SQL injection attacks. The SQL injection could be considered as the vulnerability in the web
security that permits the attackers in interfering with various queries that is made by the
application to the database. It commonly permits the attackers in viewing the data of the IoT
devices that the attackers are not authorised to see (Sethi and Sarangi 2017). It mainly
includes the data that are belonging to the other users, or any of the data that is being
accessed by the application. The attacker gains the method of modifying or even deleting the
data that has been stored in the company database.
Mirai botnet Spoofing attack man-in-the-middle
attack
SQL injection attack
huge distributed
denial of the
services attack led
to the loss of
internet services
major flaw in the
in-room Tapia
robots of the hotels
led to the breach of
huge amount of data
vulnerability in the
web security
Mirai botnet is the
malware that is
being used for
infecting the smart
devices that
guests reported the
hidden connected
camera that are
were used for
attacker could secretly
relay as well as possibly
alter the
communications among
permits the attackers
in interfering with
various queries
INTERNET OF THINGS
they are only communicating among one another. The active eavesdropping has been
conducted on the IoT devices that allows the attacker to make the autonomous connection
with their victims and relaying the messages among them for making them perceive that they
are talking to one another over the private connection but factually, the complete
conversation is being controlled by attacker.
Some of the IoT devices have been discovered to be significantly vulnerable to the
SQL injection attacks. The SQL injection could be considered as the vulnerability in the web
security that permits the attackers in interfering with various queries that is made by the
application to the database. It commonly permits the attackers in viewing the data of the IoT
devices that the attackers are not authorised to see (Sethi and Sarangi 2017). It mainly
includes the data that are belonging to the other users, or any of the data that is being
accessed by the application. The attacker gains the method of modifying or even deleting the
data that has been stored in the company database.
Mirai botnet Spoofing attack man-in-the-middle
attack
SQL injection attack
huge distributed
denial of the
services attack led
to the loss of
internet services
major flaw in the
in-room Tapia
robots of the hotels
led to the breach of
huge amount of data
vulnerability in the
web security
Mirai botnet is the
malware that is
being used for
infecting the smart
devices that
guests reported the
hidden connected
camera that are
were used for
attacker could secretly
relay as well as possibly
alter the
communications among
permits the attackers
in interfering with
various queries
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
6
INTERNET OF THINGS
executes on the
ARC processors
recording them the two parties
referred as the
botnet, that has
been frequently
utilised for
launching the
DDoS attacks
Leads to the breach
of sensitive data of
the companies and
the data stored in
the devices
active eavesdropping
has been conducted on
the IoT devices that
allows the attacker to
make the independent
connection with their
victims
permits the attackers
in viewing the data of
the IoT devices
DDoS attack led to
the unavailability
of the internet
facilities and led to
the destruction of
the network
attacker gains the
method of modifying
or even deleting the
data
Counter measures against the IoT attacks
The connected IoT devices must be extensively protected by the comprehensive
solution of IoT security that does not disrupts any service provider.
Secure boot could be utilised in the IoT devices that would ensure that security of the
IoT devices. The secure boot mainly uses the techniques of cryptographic signing, and finally
ensuring that any particular devices solely executes the codes that are generated by the OEM
of devices or any other trusted parties (Alaba et al. 2017). The utilisation of the secure boot
technology allows in preventing the hackers from replacing any of the firmware with the
malicious versions and therefore preventing the various attacks.
INTERNET OF THINGS
executes on the
ARC processors
recording them the two parties
referred as the
botnet, that has
been frequently
utilised for
launching the
DDoS attacks
Leads to the breach
of sensitive data of
the companies and
the data stored in
the devices
active eavesdropping
has been conducted on
the IoT devices that
allows the attacker to
make the independent
connection with their
victims
permits the attackers
in viewing the data of
the IoT devices
DDoS attack led to
the unavailability
of the internet
facilities and led to
the destruction of
the network
attacker gains the
method of modifying
or even deleting the
data
Counter measures against the IoT attacks
The connected IoT devices must be extensively protected by the comprehensive
solution of IoT security that does not disrupts any service provider.
Secure boot could be utilised in the IoT devices that would ensure that security of the
IoT devices. The secure boot mainly uses the techniques of cryptographic signing, and finally
ensuring that any particular devices solely executes the codes that are generated by the OEM
of devices or any other trusted parties (Alaba et al. 2017). The utilisation of the secure boot
technology allows in preventing the hackers from replacing any of the firmware with the
malicious versions and therefore preventing the various attacks.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7
INTERNET OF THINGS
Mutual authentication is another security measure that has been suggested to use in
the IoT devices. Each time any IoT device is connecting to any network, it must be properly
authenticated before receiving or even transmitting any data. It would help in ensuring that all
the data develops from the authentic devices and not from any fraudulent sources. The
cryptographic algorithms including the symmetric keys or the asymmetric keys could be
easily used for ensuring the proper two way authentication.
Securing the communication among the various devices could be considered as the
countermeasure for the IoT attacks. The protection of the data in transmission among the
device as well as the service infrastructure is necessary to prevent any hacker from gaining
the access to the cloud of the devices (Kshetri 2017). The proper use of the encryption
guarantees that the people who possess the secret decryption key could easily access the
transferred data and no other unauthorised user could access the data that is being
transmitted.
The proper security monitoring and analysis could be deployed as the countermeasure
for preventing the attacks on the IoT devices (Wang et al. 2017). The capturing of data is
done from the IoT devices that includes the various endpoint devices as well as the traffic of
connectivity. The analysis of this data is done for detecting the possible violations in the
security or the potential threats in the systems. As soon as this is detected, the vast range of
appropriate actions are deduced and overall system security policy must be executed.
Authentication protocol of IoT devices
There are various authentication protocols that are being used in the IoT devices. The
MA-PIMP is one kind of authentication protocol that is being used for securing the
communication among the connected vehicles. On the basic of the phase of authentication, as
well as the mobile router revocation, the MA-PIMP could accomplish significantly less cost
INTERNET OF THINGS
Mutual authentication is another security measure that has been suggested to use in
the IoT devices. Each time any IoT device is connecting to any network, it must be properly
authenticated before receiving or even transmitting any data. It would help in ensuring that all
the data develops from the authentic devices and not from any fraudulent sources. The
cryptographic algorithms including the symmetric keys or the asymmetric keys could be
easily used for ensuring the proper two way authentication.
Securing the communication among the various devices could be considered as the
countermeasure for the IoT attacks. The protection of the data in transmission among the
device as well as the service infrastructure is necessary to prevent any hacker from gaining
the access to the cloud of the devices (Kshetri 2017). The proper use of the encryption
guarantees that the people who possess the secret decryption key could easily access the
transferred data and no other unauthorised user could access the data that is being
transmitted.
The proper security monitoring and analysis could be deployed as the countermeasure
for preventing the attacks on the IoT devices (Wang et al. 2017). The capturing of data is
done from the IoT devices that includes the various endpoint devices as well as the traffic of
connectivity. The analysis of this data is done for detecting the possible violations in the
security or the potential threats in the systems. As soon as this is detected, the vast range of
appropriate actions are deduced and overall system security policy must be executed.
Authentication protocol of IoT devices
There are various authentication protocols that are being used in the IoT devices. The
MA-PIMP is one kind of authentication protocol that is being used for securing the
communication among the connected vehicles. On the basic of the phase of authentication, as
well as the mobile router revocation, the MA-PIMP could accomplish significantly less cost

8
INTERNET OF THINGS
of location update as compared to the scheme as well as handover delay is significantly lower
than scheme. The MA-PIMP could help in achieving the mutual authentication alongside the
authentication attacks nonetheless privacy preserving has not been yet analysed as associated
to the GLARM scheme (Lin et al. 2017).
Another protocol that is being used by the IoT devices as the authentication protocol
is the S2M protocol. S2M protocol mainly utilises the three major phases, namely, the audio-
handshake stage, the varied signal generation stage and the feature extraction as well as the
storage phase (Gilchrist 2016). The S2M could achieve significantly variable distance
authentication as well as the detection of any active attack with the help of acoustic hardware
fingerprints. The S2M has been considered to be effective in the terms of significantly lower
rates of error as compared to the DISWn, PLTEA and the LDLTS but performance of these
methods in the terms of extensive privacy preservation has not been yet analysed, specifically
in the terms of the GLARM scheme.
Conclusion
Therefore, it could be concluded from the above discussion that the introduction of
the various IoT devices has led to the simplification of various functions of the present world
but there are some issues that are required to be considered for ensuring the proper use of this
technology. The technology of Internet of Things mainly denotes to the kind of network for
connecting anything with internet depending on the stipulated protocols through the
equipment of information sensing for conducting the information exchange as well as the
communication for achieving the smart recognitions, monitoring, tracing, as well as the
administration. Mirai botnet is the malware that is being used for infecting the smart devices
that executes on the ARC processors, turning them into the network of remotely controlled
INTERNET OF THINGS
of location update as compared to the scheme as well as handover delay is significantly lower
than scheme. The MA-PIMP could help in achieving the mutual authentication alongside the
authentication attacks nonetheless privacy preserving has not been yet analysed as associated
to the GLARM scheme (Lin et al. 2017).
Another protocol that is being used by the IoT devices as the authentication protocol
is the S2M protocol. S2M protocol mainly utilises the three major phases, namely, the audio-
handshake stage, the varied signal generation stage and the feature extraction as well as the
storage phase (Gilchrist 2016). The S2M could achieve significantly variable distance
authentication as well as the detection of any active attack with the help of acoustic hardware
fingerprints. The S2M has been considered to be effective in the terms of significantly lower
rates of error as compared to the DISWn, PLTEA and the LDLTS but performance of these
methods in the terms of extensive privacy preservation has not been yet analysed, specifically
in the terms of the GLARM scheme.
Conclusion
Therefore, it could be concluded from the above discussion that the introduction of
the various IoT devices has led to the simplification of various functions of the present world
but there are some issues that are required to be considered for ensuring the proper use of this
technology. The technology of Internet of Things mainly denotes to the kind of network for
connecting anything with internet depending on the stipulated protocols through the
equipment of information sensing for conducting the information exchange as well as the
communication for achieving the smart recognitions, monitoring, tracing, as well as the
administration. Mirai botnet is the malware that is being used for infecting the smart devices
that executes on the ARC processors, turning them into the network of remotely controlled
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

9
INTERNET OF THINGS
bots or the zombies. Mutual authentication is another security measure that has been
suggested to use in the IoT devices.
INTERNET OF THINGS
bots or the zombies. Mutual authentication is another security measure that has been
suggested to use in the IoT devices.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

10
INTERNET OF THINGS
References
Alaba, F.A., Othman, M., Hashem, I.A.T. and Alotaibi, F., 2017. Internet of Things security:
A survey. Journal of Network and Computer Applications, 88, pp.10-28.
Bertino, E. and Islam, N., 2017. Botnets and internet of things security. Computer, 50(2),
pp.76-79.
Botta, A., De Donato, W., Persico, V. and Pescapé, A., 2016. Integration of cloud computing
and internet of things: a survey. Future generation computer systems, 56, pp.684-700.
Christidis, K. and Devetsikiotis, M., 2016. Blockchains and smart contracts for the internet of
things. Ieee Access, 4, pp.2292-2303.
Dastjerdi, A.V. and Buyya, R., 2016. Fog computing: Helping the Internet of Things realize
its potential. Computer, 49(8), pp.112-116.
Gilchrist, A., 2016. Industry 4.0: the industrial internet of things. Apress.
Jeschke, S., Brecher, C., Meisen, T., Özdemir, D. and Eschert, T., 2017. Industrial internet of
things and cyber manufacturing systems. In Industrial internet of things (pp. 3-19). Springer,
Cham.
Kshetri, N., 2017. Can blockchain strengthen the internet of things?. IT professional, 19(4),
pp.68-72.
Li, S., Da Xu, L. and Zhao, S., 2018. 5G Internet of Things: A survey. Journal of Industrial
Information Integration, 10, pp.1-9.
Lin, J., Yu, W., Zhang, N., Yang, X., Zhang, H. and Zhao, W., 2017. A survey on internet of
things: Architecture, enabling technologies, security and privacy, and applications. IEEE
Internet of Things Journal, 4(5), pp.1125-1142.
INTERNET OF THINGS
References
Alaba, F.A., Othman, M., Hashem, I.A.T. and Alotaibi, F., 2017. Internet of Things security:
A survey. Journal of Network and Computer Applications, 88, pp.10-28.
Bertino, E. and Islam, N., 2017. Botnets and internet of things security. Computer, 50(2),
pp.76-79.
Botta, A., De Donato, W., Persico, V. and Pescapé, A., 2016. Integration of cloud computing
and internet of things: a survey. Future generation computer systems, 56, pp.684-700.
Christidis, K. and Devetsikiotis, M., 2016. Blockchains and smart contracts for the internet of
things. Ieee Access, 4, pp.2292-2303.
Dastjerdi, A.V. and Buyya, R., 2016. Fog computing: Helping the Internet of Things realize
its potential. Computer, 49(8), pp.112-116.
Gilchrist, A., 2016. Industry 4.0: the industrial internet of things. Apress.
Jeschke, S., Brecher, C., Meisen, T., Özdemir, D. and Eschert, T., 2017. Industrial internet of
things and cyber manufacturing systems. In Industrial internet of things (pp. 3-19). Springer,
Cham.
Kshetri, N., 2017. Can blockchain strengthen the internet of things?. IT professional, 19(4),
pp.68-72.
Li, S., Da Xu, L. and Zhao, S., 2018. 5G Internet of Things: A survey. Journal of Industrial
Information Integration, 10, pp.1-9.
Lin, J., Yu, W., Zhang, N., Yang, X., Zhang, H. and Zhao, W., 2017. A survey on internet of
things: Architecture, enabling technologies, security and privacy, and applications. IEEE
Internet of Things Journal, 4(5), pp.1125-1142.

11
INTERNET OF THINGS
Ray, P.P., 2018. A survey on Internet of Things architectures. Journal of King Saud
University-Computer and Information Sciences, 30(3), pp.291-319.
Sethi, P. and Sarangi, S.R., 2017. Internet of things: architectures, protocols, and
applications. Journal of Electrical and Computer Engineering, 2017.
Stojkoska, B.L.R. and Trivodaliev, K.V., 2017. A review of Internet of Things for smart
home: Challenges and solutions. Journal of Cleaner Production, 140, pp.1454-1464.
Wang, Y.P.E., Lin, X., Adhikary, A., Grovlen, A., Sui, Y., Blankenship, Y., Bergman, J. and
Razaghi, H.S., 2017. A primer on 3GPP narrowband Internet of Things. IEEE
Communications Magazine, 55(3), pp.117-123.
INTERNET OF THINGS
Ray, P.P., 2018. A survey on Internet of Things architectures. Journal of King Saud
University-Computer and Information Sciences, 30(3), pp.291-319.
Sethi, P. and Sarangi, S.R., 2017. Internet of things: architectures, protocols, and
applications. Journal of Electrical and Computer Engineering, 2017.
Stojkoska, B.L.R. and Trivodaliev, K.V., 2017. A review of Internet of Things for smart
home: Challenges and solutions. Journal of Cleaner Production, 140, pp.1454-1464.
Wang, Y.P.E., Lin, X., Adhikary, A., Grovlen, A., Sui, Y., Blankenship, Y., Bergman, J. and
Razaghi, H.S., 2017. A primer on 3GPP narrowband Internet of Things. IEEE
Communications Magazine, 55(3), pp.117-123.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 12
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.




