A Comprehensive Analysis of Security in the Internet of Things
VerifiedAdded on 2023/06/11
|12
|555
|406
Report
AI Summary
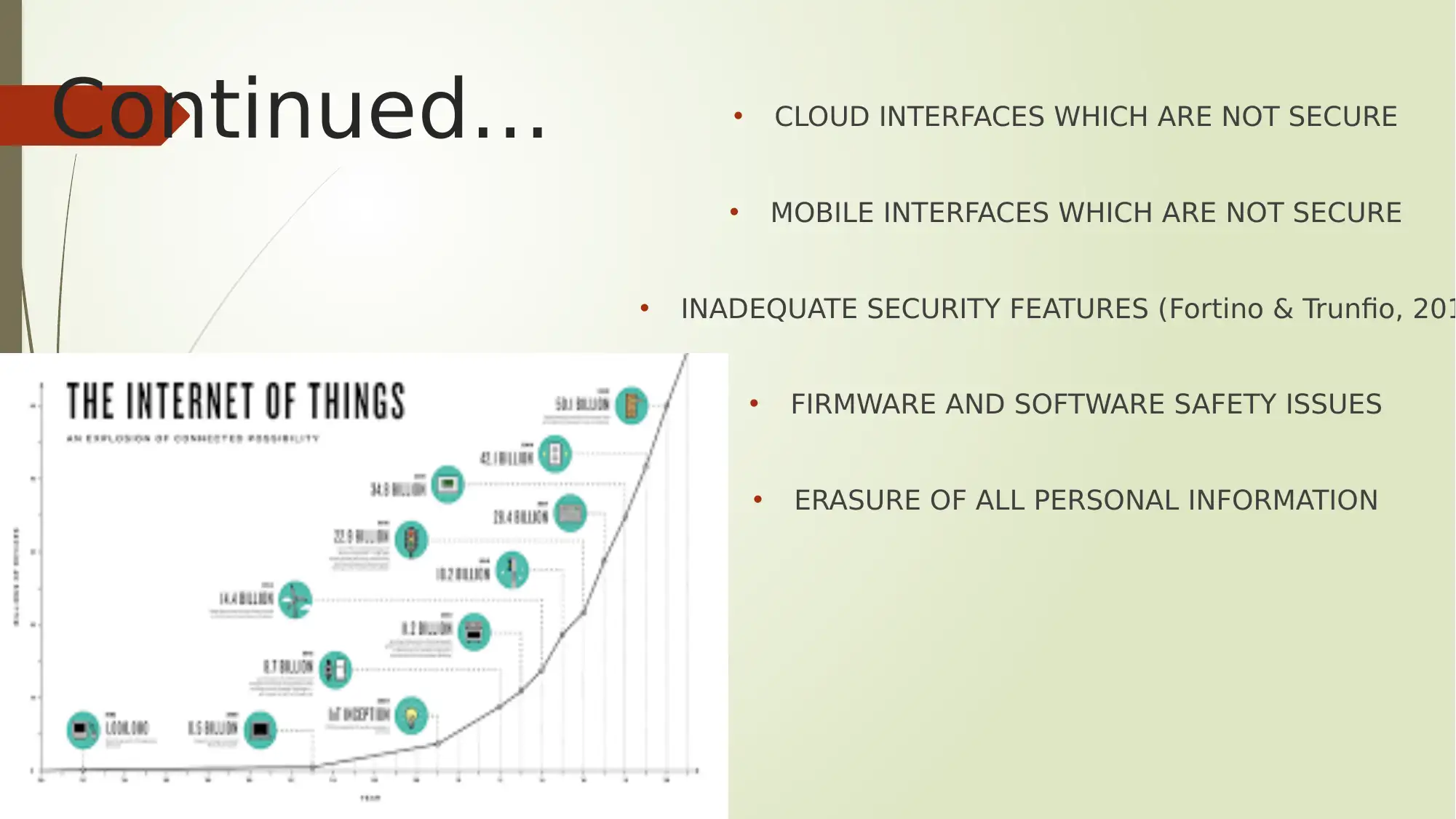
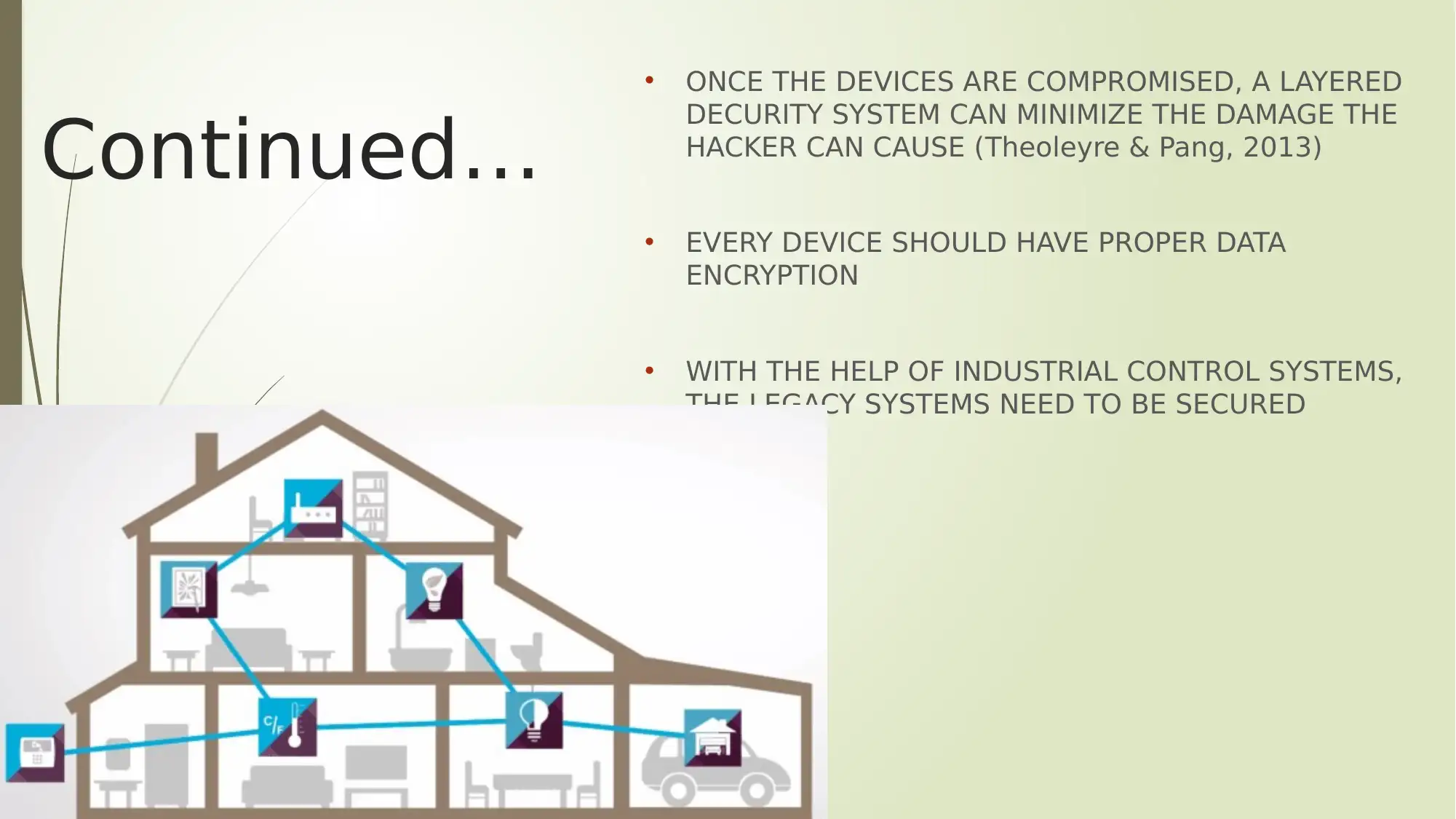
This report provides an overview of security issues and vulnerabilities within the Internet of Things (IoT), highlighting the interconnected network of computing devices and digital machines. It outlines various applications of IoT, including wearables, smart grids, connected cars, and smart cities, while also addressing critical security concerns such as limited device capabilities, prediction and detection inefficiencies, and vulnerability management challenges. The report emphasizes the importance of secure communication channels, regular updates, authentication, authorization, and securing applications across mobile, cloud, and web platforms. Research areas like smart gadgets, IoT applications, smart home automation, connected logistics, and blockchain integration are also explored. Key vulnerabilities discussed include improper authentication, exploitable web interfaces, insecure network services, inadequate transport encryption, and privacy concerns. Security measures such as using Trusted Platform Modules (TPM), Trusted Network Connect (TNC) standards, isolating infected devices, layered security systems, and data encryption are recommended to mitigate risks and secure legacy systems with industrial control systems. The report concludes with a list of references to support the information and analysis provided.
1 out of 12










![[object Object]](/_next/static/media/star-bottom.7253800d.svg)