Detailed Report on Internetworking with TCP/IP Protocols
VerifiedAdded on 2022/09/09
|7
|1785
|24
Report
AI Summary
This report provides a comprehensive overview of internetworking with TCP/IP. It begins by establishing TCP/IP network architecture as the preferred communication model, highlighting its four layers: application, transport, internet, and network access, and discusses the protocols within each layer. The report delves into the functions of the internet layer, including packet transmission, routing, and error control, and examines the IPv4 header length and identification fields. It then analyzes specific IP addresses, differentiating between Class A and Class D addresses and their respective uses. Finally, the report provides a detailed network diagram illustrating the connectivity of various networks and routers, including Ethernet LANs and point-to-point WANs, and discusses network configuration and management. The report concludes by emphasizing the importance of proper internetworking device configuration for secure and efficient data transmission.
RUNNING HEAD: INTERNETWORKING WITH TCP/IP 0
Internetworking with TCP/IP
Report
Student name
Internetworking with TCP/IP
Report
Student name
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

INTERNETWORKING WITH TCP/IP 1
Answer: 1
TCP/IP network architecture has used for communication, which is the best network
model for communication. In addition, most of the firms have used this model for
communication (Dye, McDonald, & Rufi, 2007). It was based on the protocols, which have
performed better in communication. Moreover, it has four layers, which are an application,
transport, internet, and network access layer (Dye, McDonald, & Rufi, 2007). Most of the
protocols have used for better communication with each layer as per their functioning (Le, 2017).
The Internet layer has three main functions, which areas:
1. Transmitting packets: Internets layers have responsibly for the packet transmitting to
the data link layer, which is a huge work, as it is tough work in a network. It has used
a connection oriented and connectionless approaches for transmitting the packets
from one source to another. In addition, TCP/IP has involved these layers for many
functions. Address Resolution Protocol and Reverse Address Resolution Protocol
have used for managing packet transmission (Forouzan, 2007).
2. Routing: TCP/IP has selected this layer for the routing as well. In addition, users have
used this layer for routing packets in a network. It has used proper routing protocols
for routing packets in a network, such as RIP, EIGRP, and many others. Internet
Protocol has used for routing (Medhi & Ramasamy, 2017).
3. Error control: it is a necessary process in which different types of errors have
occurred in the network, which has corrected using the network layer. Most of the
errors have occurred because of fragmentation and reassemble. In addition, a
communication channel has created errors in the data, which is not good for the
receiver. Internet Control Message Protocol is used for error control (Mitchell, 2018).
The Internet layer is the third layer of this protocol architecture, which has provided
reliable data transfer with minimum errors. Moreover, this layer has provided various solutions
to basic services (Paquet, 2013). Moreover, Internet layer has used for managing all the packets.
Mostly, packets can be transformed using connection-oriented and connectionless approaches.
Moreover, network can be managed using internet layer, as IPv4 and IPv6 are used for
data packets. It has used for the particular routing and fragmentation. All the functions are
important for a network. Internet layer has created a proper routing table and information for
packets to travel in the network. All the nodes have used routing table for forwarding the packet
in a network.
Furthermore, most of the protocols have used for particular function, such as IP, ICMP,
ARP, RARP, and many more. All the protocols have some set of rules to communicate in a
network. IP is the most important protocol of this layer, as it has managed packet transmission in
a network.
Answer: 1
TCP/IP network architecture has used for communication, which is the best network
model for communication. In addition, most of the firms have used this model for
communication (Dye, McDonald, & Rufi, 2007). It was based on the protocols, which have
performed better in communication. Moreover, it has four layers, which are an application,
transport, internet, and network access layer (Dye, McDonald, & Rufi, 2007). Most of the
protocols have used for better communication with each layer as per their functioning (Le, 2017).
The Internet layer has three main functions, which areas:
1. Transmitting packets: Internets layers have responsibly for the packet transmitting to
the data link layer, which is a huge work, as it is tough work in a network. It has used
a connection oriented and connectionless approaches for transmitting the packets
from one source to another. In addition, TCP/IP has involved these layers for many
functions. Address Resolution Protocol and Reverse Address Resolution Protocol
have used for managing packet transmission (Forouzan, 2007).
2. Routing: TCP/IP has selected this layer for the routing as well. In addition, users have
used this layer for routing packets in a network. It has used proper routing protocols
for routing packets in a network, such as RIP, EIGRP, and many others. Internet
Protocol has used for routing (Medhi & Ramasamy, 2017).
3. Error control: it is a necessary process in which different types of errors have
occurred in the network, which has corrected using the network layer. Most of the
errors have occurred because of fragmentation and reassemble. In addition, a
communication channel has created errors in the data, which is not good for the
receiver. Internet Control Message Protocol is used for error control (Mitchell, 2018).
The Internet layer is the third layer of this protocol architecture, which has provided
reliable data transfer with minimum errors. Moreover, this layer has provided various solutions
to basic services (Paquet, 2013). Moreover, Internet layer has used for managing all the packets.
Mostly, packets can be transformed using connection-oriented and connectionless approaches.
Moreover, network can be managed using internet layer, as IPv4 and IPv6 are used for
data packets. It has used for the particular routing and fragmentation. All the functions are
important for a network. Internet layer has created a proper routing table and information for
packets to travel in the network. All the nodes have used routing table for forwarding the packet
in a network.
Furthermore, most of the protocols have used for particular function, such as IP, ICMP,
ARP, RARP, and many more. All the protocols have some set of rules to communicate in a
network. IP is the most important protocol of this layer, as it has managed packet transmission in
a network.

INTERNETWORKING WITH TCP/IP 2
Answer: 2
IPv4 Header Length field
Internet Protocol Version 4 has used different fields to transmit data in a network. Header
length field has used for identification of length of the header, which is necessary to know about
the size of the packet. Moreover, it has used 4-bits to express the length of the packet. It has used
multiple of 5 bits, as the minimum size of IPv4 will be 20 bytes and the maximum will be 60
bytes (Hogg, 2017).
Identification field
IPv4 has used an identification field for the error control in the function of fragmentation
and reassembly of message segments of a packet, which has used for minimizing the errors in the
network. Most of the packets have sent in the network, but in some cases, packets have
fragmented in the datagrams because of the size of the packets (Rao, 2018). Thus, each packet
has divided into various parts, which can be sent in the network. The identification field has used
for segments identification. The receiver can find the same ID of all the segments of a single
paper. 16-bits have used for the identification of a segment of a particular packet (Techdonut,
2018).
Answer: 3
227.12.14.87: This address belongs to class D, which has used for multicasting. It is a
special class, which has used for forwarding a message to multiple clients at the same time. Most
of the organization has used class D addresses for multicasting in their groups (Certiology,
2018). The message has gone to selected users form a big list in a single time. It does not use a
subnet mask for multicasting. It has used for special wireless communication and cable-TV
(Tanenbaum, 2014).
14.23.120.8: This address belongs to class A, which has used for the large-scale network
in a huge organization, such as Google, IBM, Microsoft, and many others. It can manage 16
million users in a single network. Most of the large-scale network has used class an address, as
they have used a large number of hosts in their different departments. The default subnet mask of
this class is 255.0.0.0 (Sunshine, 2013).
Answer: 4
In this case, all the routers have placed between different networks, as shown in the
below figure. All the devices have connected with the router and LAN and WAN.
Answer: 2
IPv4 Header Length field
Internet Protocol Version 4 has used different fields to transmit data in a network. Header
length field has used for identification of length of the header, which is necessary to know about
the size of the packet. Moreover, it has used 4-bits to express the length of the packet. It has used
multiple of 5 bits, as the minimum size of IPv4 will be 20 bytes and the maximum will be 60
bytes (Hogg, 2017).
Identification field
IPv4 has used an identification field for the error control in the function of fragmentation
and reassembly of message segments of a packet, which has used for minimizing the errors in the
network. Most of the packets have sent in the network, but in some cases, packets have
fragmented in the datagrams because of the size of the packets (Rao, 2018). Thus, each packet
has divided into various parts, which can be sent in the network. The identification field has used
for segments identification. The receiver can find the same ID of all the segments of a single
paper. 16-bits have used for the identification of a segment of a particular packet (Techdonut,
2018).
Answer: 3
227.12.14.87: This address belongs to class D, which has used for multicasting. It is a
special class, which has used for forwarding a message to multiple clients at the same time. Most
of the organization has used class D addresses for multicasting in their groups (Certiology,
2018). The message has gone to selected users form a big list in a single time. It does not use a
subnet mask for multicasting. It has used for special wireless communication and cable-TV
(Tanenbaum, 2014).
14.23.120.8: This address belongs to class A, which has used for the large-scale network
in a huge organization, such as Google, IBM, Microsoft, and many others. It can manage 16
million users in a single network. Most of the large-scale network has used class an address, as
they have used a large number of hosts in their different departments. The default subnet mask of
this class is 255.0.0.0 (Sunshine, 2013).
Answer: 4
In this case, all the routers have placed between different networks, as shown in the
below figure. All the devices have connected with the router and LAN and WAN.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
INTERNETWORKING WITH TCP/IP 3
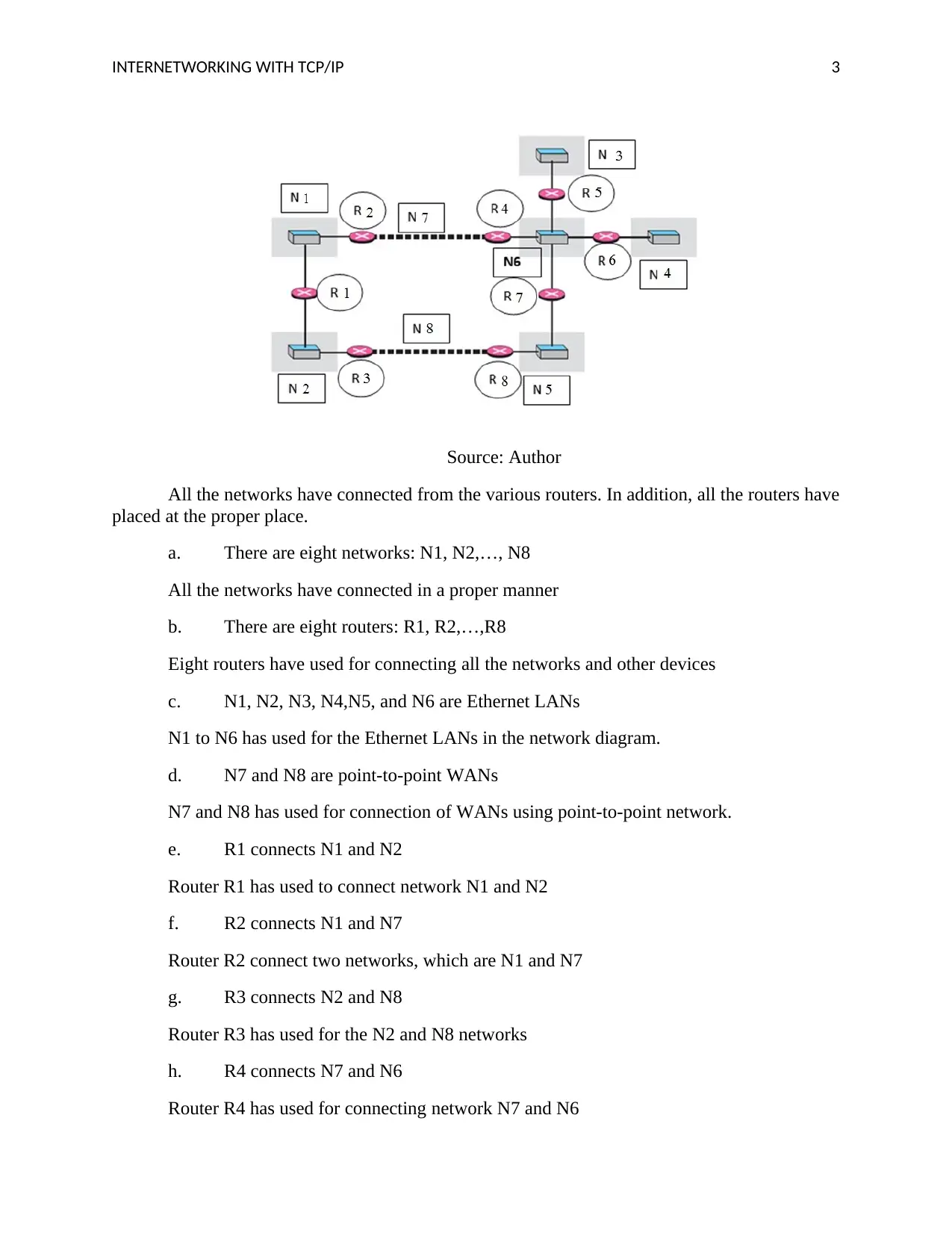
Source: Author
All the networks have connected from the various routers. In addition, all the routers have
placed at the proper place.
a. There are eight networks: N1, N2,…, N8
All the networks have connected in a proper manner
b. There are eight routers: R1, R2,…,R8
Eight routers have used for connecting all the networks and other devices
c. N1, N2, N3, N4,N5, and N6 are Ethernet LANs
N1 to N6 has used for the Ethernet LANs in the network diagram.
d. N7 and N8 are point-to-point WANs
N7 and N8 has used for connection of WANs using point-to-point network.
e. R1 connects N1 and N2
Router R1 has used to connect network N1 and N2
f. R2 connects N1 and N7
Router R2 connect two networks, which are N1 and N7
g. R3 connects N2 and N8
Router R3 has used for the N2 and N8 networks
h. R4 connects N7 and N6
Router R4 has used for connecting network N7 and N6
Source: Author
All the networks have connected from the various routers. In addition, all the routers have
placed at the proper place.
a. There are eight networks: N1, N2,…, N8
All the networks have connected in a proper manner
b. There are eight routers: R1, R2,…,R8
Eight routers have used for connecting all the networks and other devices
c. N1, N2, N3, N4,N5, and N6 are Ethernet LANs
N1 to N6 has used for the Ethernet LANs in the network diagram.
d. N7 and N8 are point-to-point WANs
N7 and N8 has used for connection of WANs using point-to-point network.
e. R1 connects N1 and N2
Router R1 has used to connect network N1 and N2
f. R2 connects N1 and N7
Router R2 connect two networks, which are N1 and N7
g. R3 connects N2 and N8
Router R3 has used for the N2 and N8 networks
h. R4 connects N7 and N6
Router R4 has used for connecting network N7 and N6
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

INTERNETWORKING WITH TCP/IP 4
i. R5 connects N6 and N3
Router R5 has used for connecting network N6 and N3 networks
j. R6 connects N6 and N4
Router R5 connects two networks, which are N6 and N4 networks
k. R7 connects N6 and N5
Router R7 has used for connecting network N6 and N5
l. R8 connects N8 and N5
Router R8 has used for connecting networks N8 and N5
Most of the devices have used proper configuration for connecting all the devices. It is
necessary to manage all the things using all the processes.
Moreover, point-to-point wireless LAN has used for connecting various wireless devices,
such as mobile phones, laptops, and other devices. In addition, the above network diagram has
shown all the connectivity of networks. Most of the network has connected using routers for
better routing and switching. Besides, Layer- 3 switches can be used for the connection as well.
Furthermore, most of the network has used for basic services. Thus, this whole network has
connected in a proper manner as well as fully secured and connected. It can be managed using
mounting and controlling (Huston, 2016).
Furthermore, N1, N2, N3, N4, N5, and N6 has used as a transient network and N7 and
N8 has used as a subnetworks. Most of the networks have used for communication and
transmission of data. Therefore, internetworking devices has used in a proper manner, such as
router, switch, and many others.
i. R5 connects N6 and N3
Router R5 has used for connecting network N6 and N3 networks
j. R6 connects N6 and N4
Router R5 connects two networks, which are N6 and N4 networks
k. R7 connects N6 and N5
Router R7 has used for connecting network N6 and N5
l. R8 connects N8 and N5
Router R8 has used for connecting networks N8 and N5
Most of the devices have used proper configuration for connecting all the devices. It is
necessary to manage all the things using all the processes.
Moreover, point-to-point wireless LAN has used for connecting various wireless devices,
such as mobile phones, laptops, and other devices. In addition, the above network diagram has
shown all the connectivity of networks. Most of the network has connected using routers for
better routing and switching. Besides, Layer- 3 switches can be used for the connection as well.
Furthermore, most of the network has used for basic services. Thus, this whole network has
connected in a proper manner as well as fully secured and connected. It can be managed using
mounting and controlling (Huston, 2016).
Furthermore, N1, N2, N3, N4, N5, and N6 has used as a transient network and N7 and
N8 has used as a subnetworks. Most of the networks have used for communication and
transmission of data. Therefore, internetworking devices has used in a proper manner, such as
router, switch, and many others.

INTERNETWORKING WITH TCP/IP 5
References
Certiology. (2018). Network Devices:. Retrieved November 2, 2019, from Certiology:
http://www.certiology.com/computing/computer-networking/network-devices.html
Dye, M., McDonald, R., & Rufi, A. (2007). Network Fundamentals, CCNA Exploration
Companion Guide. Indianapolis, USA: Cisco press.
Forouzan, A. (2007). Data communications & networking (8th ed.). New Delhi: Tata McGraw-
Hill Education.
Hogg, S. (2017). IPv6 Addressing for Enterprises. Retrieved August 5, 2019, from
https://www.networkworld.com/article/3235384/ipv6-address-enterprises-how-to-easier-
than-ipv4.html
Huston, G. (2016, January 28). By Geoff Huston on 28 Jan 2016. Retrieved from
https://blog.apnic.net: https://blog.apnic.net/2016/01/28/evaluating-ipv4-and-ipv6-packet-
frangmentation/
Le, J. (2017, December 22). The 4-Layer Internet Model Network Engineers Need to Know.
Retrieved from https://medium.com: https://medium.com/@james_aka_yale/the-4-layer-
internet-model-network-engineers-need-to-know-e78432614a4f
Medhi, D., & Ramasamy, K. (2017). Network routing: algorithms, protocols, and architectures.
Morgan Kaufmann.
Mitchell, B. (2018, December 12). What Is Computer Networking? (lifewire) Retrieved January
16, 2019, from https://www.lifewire.com/what-is-computer-networking-816249
Paquet, C. (2013). Network Security Concepts and Policies. Retrieved november 2, 2019, from
http://www.ciscopress.com/articles/article.asp?p=1998559&seqNum=3
Rao, M. (2018, December 22). What is IPV4 Addressing? Retrieved from
https://www.includehelp.com: https://www.includehelp.com/computer-networks/ipv4-
addressing.aspx
Sunshine, C. (2013). Computer network architectures and protocols. New Jersy: Springer
Science & Business Media.
Tanenbaum, A. S. (2014). Computer networks. Harlow, Essex: Pearson.
Techdonut. (2018). Network management tasks. Retrieved November 2, 2019, from
https://www.techdonut.co.uk/buy-and-manage-it/regular-it-maintenance/network-
management-tasks
References
Certiology. (2018). Network Devices:. Retrieved November 2, 2019, from Certiology:
http://www.certiology.com/computing/computer-networking/network-devices.html
Dye, M., McDonald, R., & Rufi, A. (2007). Network Fundamentals, CCNA Exploration
Companion Guide. Indianapolis, USA: Cisco press.
Forouzan, A. (2007). Data communications & networking (8th ed.). New Delhi: Tata McGraw-
Hill Education.
Hogg, S. (2017). IPv6 Addressing for Enterprises. Retrieved August 5, 2019, from
https://www.networkworld.com/article/3235384/ipv6-address-enterprises-how-to-easier-
than-ipv4.html
Huston, G. (2016, January 28). By Geoff Huston on 28 Jan 2016. Retrieved from
https://blog.apnic.net: https://blog.apnic.net/2016/01/28/evaluating-ipv4-and-ipv6-packet-
frangmentation/
Le, J. (2017, December 22). The 4-Layer Internet Model Network Engineers Need to Know.
Retrieved from https://medium.com: https://medium.com/@james_aka_yale/the-4-layer-
internet-model-network-engineers-need-to-know-e78432614a4f
Medhi, D., & Ramasamy, K. (2017). Network routing: algorithms, protocols, and architectures.
Morgan Kaufmann.
Mitchell, B. (2018, December 12). What Is Computer Networking? (lifewire) Retrieved January
16, 2019, from https://www.lifewire.com/what-is-computer-networking-816249
Paquet, C. (2013). Network Security Concepts and Policies. Retrieved november 2, 2019, from
http://www.ciscopress.com/articles/article.asp?p=1998559&seqNum=3
Rao, M. (2018, December 22). What is IPV4 Addressing? Retrieved from
https://www.includehelp.com: https://www.includehelp.com/computer-networks/ipv4-
addressing.aspx
Sunshine, C. (2013). Computer network architectures and protocols. New Jersy: Springer
Science & Business Media.
Tanenbaum, A. S. (2014). Computer networks. Harlow, Essex: Pearson.
Techdonut. (2018). Network management tasks. Retrieved November 2, 2019, from
https://www.techdonut.co.uk/buy-and-manage-it/regular-it-maintenance/network-
management-tasks
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

INTERNETWORKING WITH TCP/IP 6
1 out of 7
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.




