MN503 Overview of Internetworking: Network Analysis and Plan
VerifiedAdded on 2023/06/08
|11
|2318
|192
Report
AI Summary
This report provides a comprehensive overview of computer networking, focusing on network requirement analysis and planning. It begins by defining computer networks and discussing the Standard Operating Procedures (SOP) in networking. The report then delves into human-centric design approaches, including the OSI and TCP/IP models, highlighting their functions and differences. It also explores present-day computer network technologies such as Routing Information Protocol (RIP), Interior Gateway Protocol (IGRP), Open Shortest Path First (OSPF), Enhanced Interior Gateway Routing Protocol (EIGRP), Border Gateway Protocol (BGP), and Intermediate System-to-Intermediate System (IS-IS). Furthermore, the report discusses future computer networks, including Software Defined Networking (SDN), cloud computing, intelligent networks, and the Internet of Things (IoT), emphasizing their potential impact on how humans work and communicate. The report concludes that the evolution of new technologies is changing human lives and enhancing their overall quality of life.

Running head: COMPUTER NETWORKING
Computer Networking
[Name of the Student]
[Name of the University]
[Author note]
Computer Networking
[Name of the Student]
[Name of the University]
[Author note]
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1COMPUTER NETWORKING
Table of Contents
Introduction:...............................................................................................................................2
Discussion:.................................................................................................................................2
Human-centric design approach:................................................................................................2
A brief discussion of the present-day technology of computer network...................................5
Discussion on future computer networks...................................................................................6
Conclusion..................................................................................................................................9
References:...............................................................................................................................10
Table of Contents
Introduction:...............................................................................................................................2
Discussion:.................................................................................................................................2
Human-centric design approach:................................................................................................2
A brief discussion of the present-day technology of computer network...................................5
Discussion on future computer networks...................................................................................6
Conclusion..................................................................................................................................9
References:...............................................................................................................................10

2COMPUTER NETWORKING
Introduction:
Computer network can be defined as the collection of computer systems along with
other computing hardware devices which are connected together by making use of the
communication channels. This connecting channels are associated with facilitating the
process of communication along with sharing the resources amongst numerous users. The
classification of the computer networks are generally done according to the characteristics
that they are having [1]. Computer networking is generally refers to the entire process by
which the computer network is created and used by depending upon the various kind of
hardware, protocol and software which includes the wired as well as the wireless technology.
This also includes the various application of theories from different technological fields
which includes the IT, science and computer or electrical engineering.
Discussion:
SOP or the Standard Operating Procedures present in the networking generally
requires the selecting materials which includes the cables and the networking hardware and is
initially associated with the establishment of the telecommunication protocols, hardware and
the software which are required. The advancement in multiple networking hardware
technologies are a result of the need for enhanced telecommunication and this hardware
mainly includes the hubs, switches, and routers.
Human-centric design approach:
The different human centric design approach are listed below:
OSI Model: The OSI model or the Open System Interconnection model is considered to
be the conceptual model which is associated with characterizing and standardizing the
communication functions present in the telecommunication or the computing system.
This is generally done regardless of the internal structure and the technology which
Introduction:
Computer network can be defined as the collection of computer systems along with
other computing hardware devices which are connected together by making use of the
communication channels. This connecting channels are associated with facilitating the
process of communication along with sharing the resources amongst numerous users. The
classification of the computer networks are generally done according to the characteristics
that they are having [1]. Computer networking is generally refers to the entire process by
which the computer network is created and used by depending upon the various kind of
hardware, protocol and software which includes the wired as well as the wireless technology.
This also includes the various application of theories from different technological fields
which includes the IT, science and computer or electrical engineering.
Discussion:
SOP or the Standard Operating Procedures present in the networking generally
requires the selecting materials which includes the cables and the networking hardware and is
initially associated with the establishment of the telecommunication protocols, hardware and
the software which are required. The advancement in multiple networking hardware
technologies are a result of the need for enhanced telecommunication and this hardware
mainly includes the hubs, switches, and routers.
Human-centric design approach:
The different human centric design approach are listed below:
OSI Model: The OSI model or the Open System Interconnection model is considered to
be the conceptual model which is associated with characterizing and standardizing the
communication functions present in the telecommunication or the computing system.
This is generally done regardless of the internal structure and the technology which
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
3COMPUTER NETWORKING
underlies the telecommunication or computing system. The major goal of this OSI layer
includes the interoperability of the various kind of communication system by making use
of the standard protocols. This model is associated with partitioning the communication
system into abstract layer whereas the original version of this model consists of 7
different layers [2].
Seven layers Of the OSI model includes the following:
Layer Function
Application Layer This generally refers to the interface that is present between the
network and the application software which includes the
authentication service as well.
Presentation layer This layer mainly includes the format and operation of the data
and besides this it also includes the encryption as well
Session layer Associated with the maintenance and establishment of the end-to-
end bi-directional flow between the endpoints. Besides this the
layer is associated with managing the flow of transactions
Transport layer This is associated with provide different kind of services between
two host computers which also includes the establishment of
connection along with the termination, flow control, recovery of
errors and segmentation of the large data blocks into smaller parts
for transmission
Network layer This generally refers to the logical addressing, routing and
determination of the path
Data link layer This is associated with formatting the data into frames which are
appropriated for the transmission onto some physical medium.
This also defines the rules that are responsible for determination
underlies the telecommunication or computing system. The major goal of this OSI layer
includes the interoperability of the various kind of communication system by making use
of the standard protocols. This model is associated with partitioning the communication
system into abstract layer whereas the original version of this model consists of 7
different layers [2].
Seven layers Of the OSI model includes the following:
Layer Function
Application Layer This generally refers to the interface that is present between the
network and the application software which includes the
authentication service as well.
Presentation layer This layer mainly includes the format and operation of the data
and besides this it also includes the encryption as well
Session layer Associated with the maintenance and establishment of the end-to-
end bi-directional flow between the endpoints. Besides this the
layer is associated with managing the flow of transactions
Transport layer This is associated with provide different kind of services between
two host computers which also includes the establishment of
connection along with the termination, flow control, recovery of
errors and segmentation of the large data blocks into smaller parts
for transmission
Network layer This generally refers to the logical addressing, routing and
determination of the path
Data link layer This is associated with formatting the data into frames which are
appropriated for the transmission onto some physical medium.
This also defines the rules that are responsible for determination
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

4COMPUTER NETWORKING
of time when the medium can be used.
Physical layer This is associated with defining the electrical, optical, cabling
connectors and the procedural details that are generally required
for the purpose of transmitting the bits that are generally
represented as some form of energy which are passing over the
physical medium.
Table 1: Seven Layers of the OSI Model
TCP/IP Model: The TCP/IP model is generally considered to be a suite of communication
protocol which is generally used for the purpose of interconnecting the various network
devices that are present in the internet. This is also used as one of the communication
protocol for the private networks. The entire internet protocol suite or the set of rules and
procedures is termed as TCP/IP whereas some other things are also included in the suite
as well. This is associated with specifying the ways by which the data gets exchanged by
making use of the internet which is associated with providing an end-to-end
communication and is also responsible for the identifying the ways by which the data is to
be broken into packets, addressed, transmitted, routed and lastly received at the
destination [3].
The table provided below depicts the four major layer of the TCP/IP model:
Layer Function
Application Layer Associated with representing the data to the user and is also
responsible for controlling the dialogues.
Transport Layer Associated with supporting the communication that exists
between the diverse devices present across diverse networks.
Internet This is associated with determining the best path through the
of time when the medium can be used.
Physical layer This is associated with defining the electrical, optical, cabling
connectors and the procedural details that are generally required
for the purpose of transmitting the bits that are generally
represented as some form of energy which are passing over the
physical medium.
Table 1: Seven Layers of the OSI Model
TCP/IP Model: The TCP/IP model is generally considered to be a suite of communication
protocol which is generally used for the purpose of interconnecting the various network
devices that are present in the internet. This is also used as one of the communication
protocol for the private networks. The entire internet protocol suite or the set of rules and
procedures is termed as TCP/IP whereas some other things are also included in the suite
as well. This is associated with specifying the ways by which the data gets exchanged by
making use of the internet which is associated with providing an end-to-end
communication and is also responsible for the identifying the ways by which the data is to
be broken into packets, addressed, transmitted, routed and lastly received at the
destination [3].
The table provided below depicts the four major layer of the TCP/IP model:
Layer Function
Application Layer Associated with representing the data to the user and is also
responsible for controlling the dialogues.
Transport Layer Associated with supporting the communication that exists
between the diverse devices present across diverse networks.
Internet This is associated with determining the best path through the

5COMPUTER NETWORKING
network
Network access This is associated with controlling the hardware devices and the
media that are responsible for making the network.
Table 2: Four Layers of the TCP/IP Model
Difference between TCP/IP Model and OSI Model
OSI MODEL TCP/IP MODEL
This model is consisting of 7 layers. This model is consisting of 4 layers
Layering is Strict which results in the layer
which are vertical in nature
Layering is Loose which results in the layer
which are vertical in nature
Associated with distinguishing service,
interface and protocol
Does not distinguish the service, interface
and protocol
Table 3: Difference between the TCP/IP Model and the OSI Model
A brief discussion of the present-day technology of computer network
The various type of Routing Protocols mainly includes the following:
Routing Information Protocols (RIP): This is generally considered to be the forceful
protocol type that is generally used by the LAN and the WAN. This type of protocol is
also considered as the interior gateway protocol which exists within the usage of the
distance vector algorithm.
Interior Gateway Protocol (IGRP): This is a Distance Vector Interior Gateway Protocol
that is used by the routers for the purpose of exchanging the data related to routing in a
system which is totally independent [4].
network
Network access This is associated with controlling the hardware devices and the
media that are responsible for making the network.
Table 2: Four Layers of the TCP/IP Model
Difference between TCP/IP Model and OSI Model
OSI MODEL TCP/IP MODEL
This model is consisting of 7 layers. This model is consisting of 4 layers
Layering is Strict which results in the layer
which are vertical in nature
Layering is Loose which results in the layer
which are vertical in nature
Associated with distinguishing service,
interface and protocol
Does not distinguish the service, interface
and protocol
Table 3: Difference between the TCP/IP Model and the OSI Model
A brief discussion of the present-day technology of computer network
The various type of Routing Protocols mainly includes the following:
Routing Information Protocols (RIP): This is generally considered to be the forceful
protocol type that is generally used by the LAN and the WAN. This type of protocol is
also considered as the interior gateway protocol which exists within the usage of the
distance vector algorithm.
Interior Gateway Protocol (IGRP): This is a Distance Vector Interior Gateway Protocol
that is used by the routers for the purpose of exchanging the data related to routing in a
system which is totally independent [4].
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

6COMPUTER NETWORKING
Open Shortest Path First (OSPF): This is one of the routing protocol which is generally
used by the IP. This can also be stated as the link state routing protocol which is present
in a group of interior gateway protocol. This type of protocol generally operates inside an
autonomous system is totally distinct.
Enhanced interior gateway routing protocol (EIGRP): This is routing protocol which is
dependent upon the original IGRP whereas it can defined as a Cisco proprietary routing
protocol. This can also be defined as a distance-vector routing protocol which is advance
within their optimization for the purpose of lessening the unsteadiness of the routing
which is incurred after the alteration topology along with the usage of the bandwidth and
the processing power of the router which is associated with supporting the enhanced
interior gateway routing protocol which would be associated with automatic reallocation
of the routing information to the IGRP neighbours by means of exchanging the 32bit
EIGRP metric to 24 bit IGRP metric [5].
Border Gateway Protocol (BGP): This can be considered to be the core routing protocol
present in the internet which are responsible for the maintenance of the table of internet
protocol network that are associated with authorizing the network reaching capability
existing between the AS. This is also expressed as the “Path Vector Protocol”.
Intermediate System-to-Intermediate System (IS-IS): This is the great protocol that is
generally used by the network devices for the purpose of determining the way that is best
for promoting the datagram from side to side a packet switch network and this process is
generally termed as routing [2].
Discussion on future computer networks
The use of various technologies helps a lot in developing the future computer
network. Some of eth examples of future computer network includes eth following:
Open Shortest Path First (OSPF): This is one of the routing protocol which is generally
used by the IP. This can also be stated as the link state routing protocol which is present
in a group of interior gateway protocol. This type of protocol generally operates inside an
autonomous system is totally distinct.
Enhanced interior gateway routing protocol (EIGRP): This is routing protocol which is
dependent upon the original IGRP whereas it can defined as a Cisco proprietary routing
protocol. This can also be defined as a distance-vector routing protocol which is advance
within their optimization for the purpose of lessening the unsteadiness of the routing
which is incurred after the alteration topology along with the usage of the bandwidth and
the processing power of the router which is associated with supporting the enhanced
interior gateway routing protocol which would be associated with automatic reallocation
of the routing information to the IGRP neighbours by means of exchanging the 32bit
EIGRP metric to 24 bit IGRP metric [5].
Border Gateway Protocol (BGP): This can be considered to be the core routing protocol
present in the internet which are responsible for the maintenance of the table of internet
protocol network that are associated with authorizing the network reaching capability
existing between the AS. This is also expressed as the “Path Vector Protocol”.
Intermediate System-to-Intermediate System (IS-IS): This is the great protocol that is
generally used by the network devices for the purpose of determining the way that is best
for promoting the datagram from side to side a packet switch network and this process is
generally termed as routing [2].
Discussion on future computer networks
The use of various technologies helps a lot in developing the future computer
network. Some of eth examples of future computer network includes eth following:
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
7COMPUTER NETWORKING
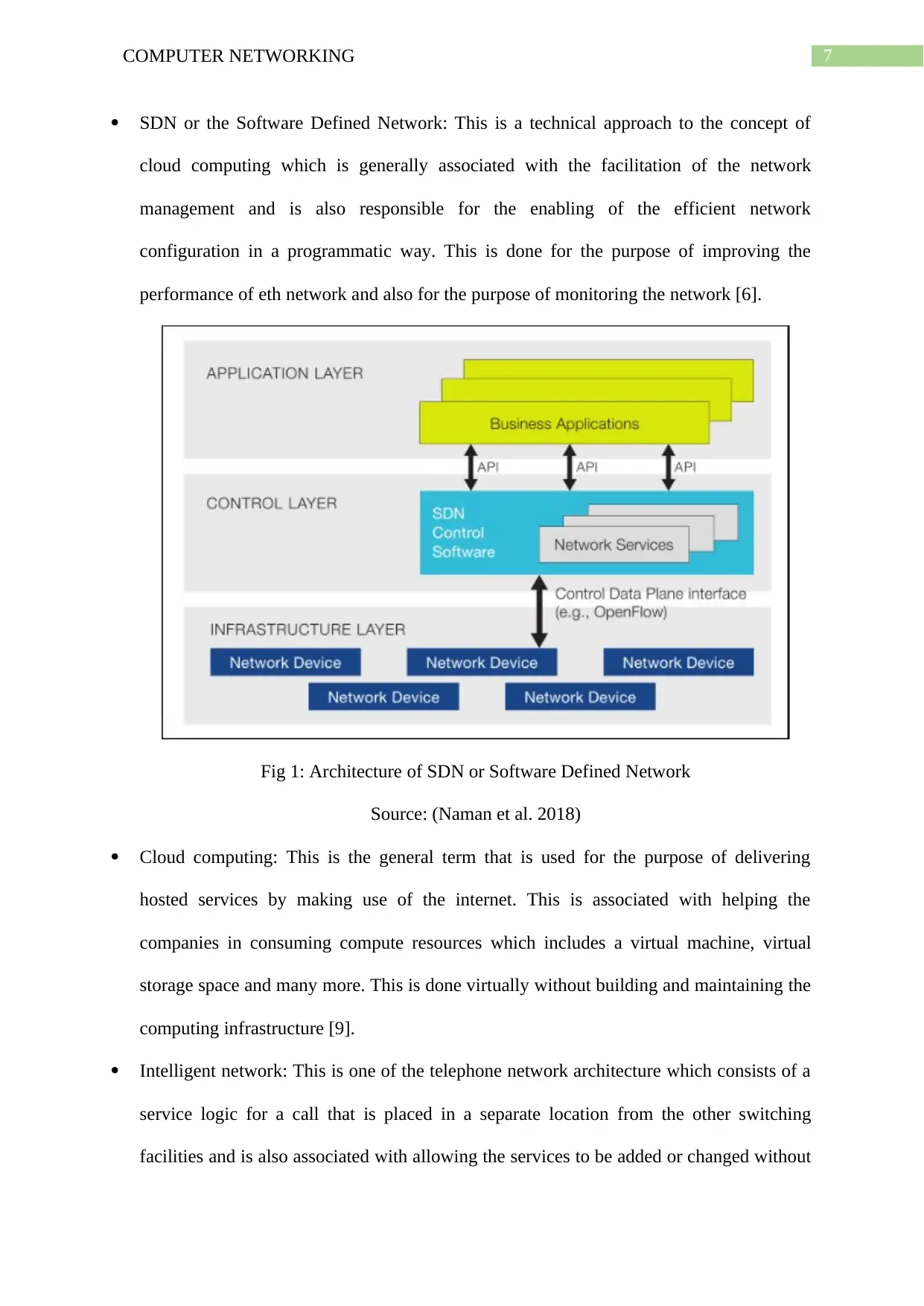
SDN or the Software Defined Network: This is a technical approach to the concept of
cloud computing which is generally associated with the facilitation of the network
management and is also responsible for the enabling of the efficient network
configuration in a programmatic way. This is done for the purpose of improving the
performance of eth network and also for the purpose of monitoring the network [6].
Fig 1: Architecture of SDN or Software Defined Network
Source: (Naman et al. 2018)
Cloud computing: This is the general term that is used for the purpose of delivering
hosted services by making use of the internet. This is associated with helping the
companies in consuming compute resources which includes a virtual machine, virtual
storage space and many more. This is done virtually without building and maintaining the
computing infrastructure [9].
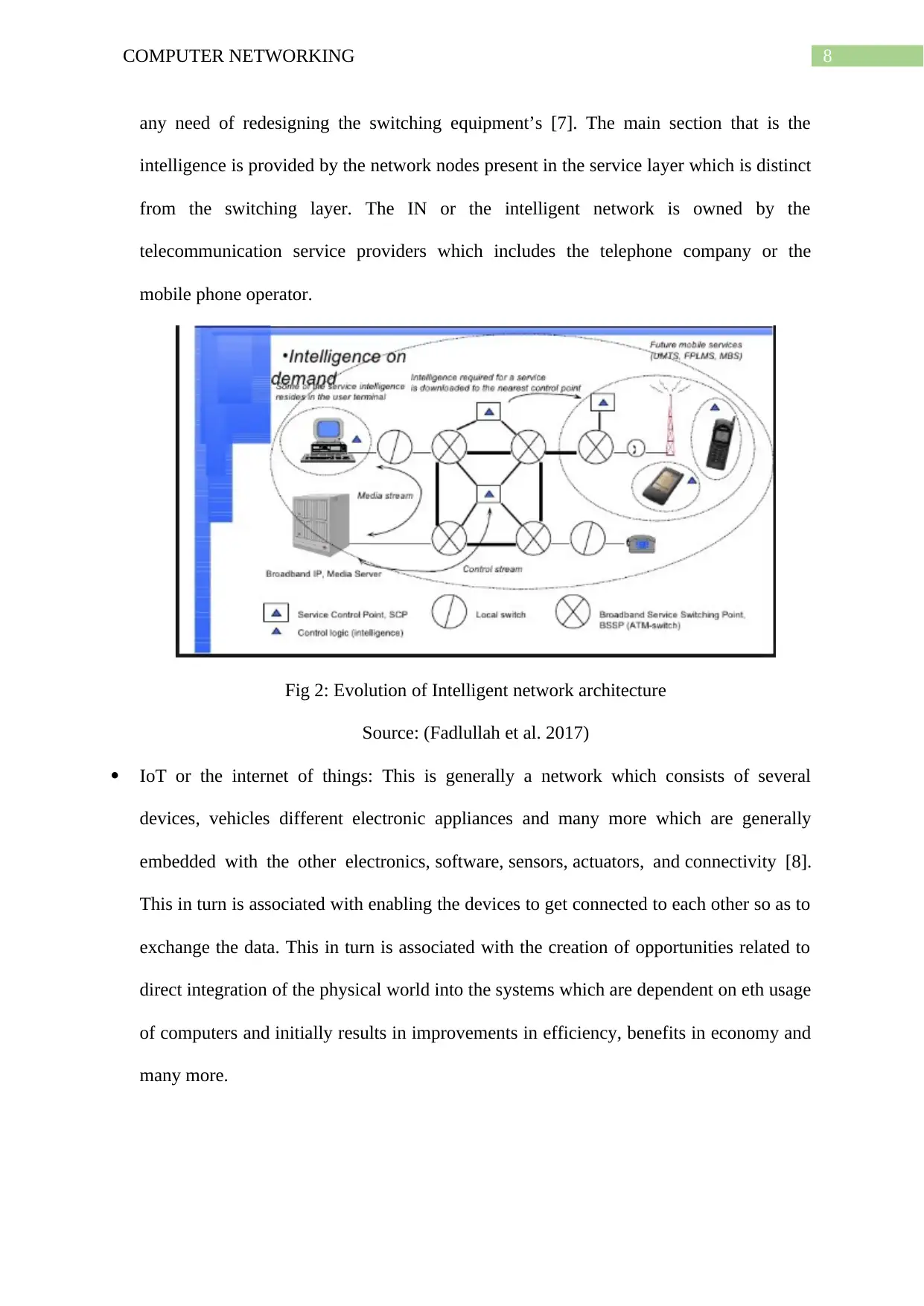
Intelligent network: This is one of the telephone network architecture which consists of a
service logic for a call that is placed in a separate location from the other switching
facilities and is also associated with allowing the services to be added or changed without
SDN or the Software Defined Network: This is a technical approach to the concept of
cloud computing which is generally associated with the facilitation of the network
management and is also responsible for the enabling of the efficient network
configuration in a programmatic way. This is done for the purpose of improving the
performance of eth network and also for the purpose of monitoring the network [6].
Fig 1: Architecture of SDN or Software Defined Network
Source: (Naman et al. 2018)
Cloud computing: This is the general term that is used for the purpose of delivering
hosted services by making use of the internet. This is associated with helping the
companies in consuming compute resources which includes a virtual machine, virtual
storage space and many more. This is done virtually without building and maintaining the
computing infrastructure [9].
Intelligent network: This is one of the telephone network architecture which consists of a
service logic for a call that is placed in a separate location from the other switching
facilities and is also associated with allowing the services to be added or changed without
8COMPUTER NETWORKING
any need of redesigning the switching equipment’s [7]. The main section that is the
intelligence is provided by the network nodes present in the service layer which is distinct
from the switching layer. The IN or the intelligent network is owned by the
telecommunication service providers which includes the telephone company or the
mobile phone operator.
Fig 2: Evolution of Intelligent network architecture
Source: (Fadlullah et al. 2017)
IoT or the internet of things: This is generally a network which consists of several
devices, vehicles different electronic appliances and many more which are generally
embedded with the other electronics, software, sensors, actuators, and connectivity [8].
This in turn is associated with enabling the devices to get connected to each other so as to
exchange the data. This in turn is associated with the creation of opportunities related to
direct integration of the physical world into the systems which are dependent on eth usage
of computers and initially results in improvements in efficiency, benefits in economy and
many more.
any need of redesigning the switching equipment’s [7]. The main section that is the
intelligence is provided by the network nodes present in the service layer which is distinct
from the switching layer. The IN or the intelligent network is owned by the
telecommunication service providers which includes the telephone company or the
mobile phone operator.
Fig 2: Evolution of Intelligent network architecture
Source: (Fadlullah et al. 2017)
IoT or the internet of things: This is generally a network which consists of several
devices, vehicles different electronic appliances and many more which are generally
embedded with the other electronics, software, sensors, actuators, and connectivity [8].
This in turn is associated with enabling the devices to get connected to each other so as to
exchange the data. This in turn is associated with the creation of opportunities related to
direct integration of the physical world into the systems which are dependent on eth usage
of computers and initially results in improvements in efficiency, benefits in economy and
many more.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

9COMPUTER NETWORKING
Fig 3: Different types of Electronic devices connected with one another
Source: (Lee and Lee 2015)
Conclusion
The report helps in concluding to the fact that the old concept of network has totally
changed and the new concepts and protocols are associated with changing the ways in which
the humans work, communicate and many more. This had been forging in a powerful way
into areas of human lives in such ways which has ever been expected. Along with the
evolution of new technologies the lives of human would be changing gradually and they
would live an enhanced life. It can be considered that most of the digital networking's current
technologies are not associated with cutting the edge, but are rather considered to be the
protocols and standards which are conceived at digital networking age.
Fig 3: Different types of Electronic devices connected with one another
Source: (Lee and Lee 2015)
Conclusion
The report helps in concluding to the fact that the old concept of network has totally
changed and the new concepts and protocols are associated with changing the ways in which
the humans work, communicate and many more. This had been forging in a powerful way
into areas of human lives in such ways which has ever been expected. Along with the
evolution of new technologies the lives of human would be changing gradually and they
would live an enhanced life. It can be considered that most of the digital networking's current
technologies are not associated with cutting the edge, but are rather considered to be the
protocols and standards which are conceived at digital networking age.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

10COMPUTER NETWORKING
References:
[1.]S Yongjie, "Research on Communication Encryption Technology of Network
Security", Telecom Power Technology, 2014.
[2.]L Dong, Y Peng, "Network Security and Firewall Technology [C]", proceedings of
2010 3rd International Conference on Computer and Electrical Engineering (ICCEE
2010, no. 2, 2012.
[3.] W Xiaolin, "Study on Computer Network Antivirus Mechanism based on Antivirus
Software", Network Security Technology & Application, 2014.
[4.]D.L Mills, “Computer network time synchronization: the network time protocol on
earth and in space”. CRC Press, 2016.
[5.]B.K. Mishra and S.K Pandey, “Dynamic model of worm propagation in computer
network”, Applied mathematical modelling, 38(7-8), pp.2173-2179, 2014.
[6.]I Lee and K Lee, “The Internet of Things (IoT): Applications, investments, and
challenges for enterprises”, Business Horizons, 58(4), pp.431-440, 2015.
[7.]Z Fadlullah, F Tang, B Mao, N Kato, O Akashi, T Inoue, and K Mizutani, “State-of-
the-art deep learning: Evolving machine intelligence toward tomorrow’s intelligent
network traffic control systems”, IEEE Communications Surveys & Tutorials, 19(4),
pp.2432-2455, 2017.
[8.]A.T Naman, Y Wang, H.H Gharakheili, V Sivaraman, and D Taubman, “Responsive
high throughput congestion control for interactive applications over SDN-enabled
networks”, Computer Networks, 134, pp.152-166, 2018.
[9.]J.W Rittinghouse, and J.F Ransome, “Cloud computing: implementation,
management, and security”, CRC press, 2016.
References:
[1.]S Yongjie, "Research on Communication Encryption Technology of Network
Security", Telecom Power Technology, 2014.
[2.]L Dong, Y Peng, "Network Security and Firewall Technology [C]", proceedings of
2010 3rd International Conference on Computer and Electrical Engineering (ICCEE
2010, no. 2, 2012.
[3.] W Xiaolin, "Study on Computer Network Antivirus Mechanism based on Antivirus
Software", Network Security Technology & Application, 2014.
[4.]D.L Mills, “Computer network time synchronization: the network time protocol on
earth and in space”. CRC Press, 2016.
[5.]B.K. Mishra and S.K Pandey, “Dynamic model of worm propagation in computer
network”, Applied mathematical modelling, 38(7-8), pp.2173-2179, 2014.
[6.]I Lee and K Lee, “The Internet of Things (IoT): Applications, investments, and
challenges for enterprises”, Business Horizons, 58(4), pp.431-440, 2015.
[7.]Z Fadlullah, F Tang, B Mao, N Kato, O Akashi, T Inoue, and K Mizutani, “State-of-
the-art deep learning: Evolving machine intelligence toward tomorrow’s intelligent
network traffic control systems”, IEEE Communications Surveys & Tutorials, 19(4),
pp.2432-2455, 2017.
[8.]A.T Naman, Y Wang, H.H Gharakheili, V Sivaraman, and D Taubman, “Responsive
high throughput congestion control for interactive applications over SDN-enabled
networks”, Computer Networks, 134, pp.152-166, 2018.
[9.]J.W Rittinghouse, and J.F Ransome, “Cloud computing: implementation,
management, and security”, CRC press, 2016.
1 out of 11
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





