Internetworking with TCP/IP: M2M Solutions Addressing and Protocols
VerifiedAdded on 2020/02/24
|14
|2377
|48
Report
AI Summary
This report provides a detailed analysis of internetworking with TCP/IP in the context of M2M (Machine-to-Machine) solutions. It begins with a detailed design of a simple addressing solution, covering IP addresses, subnet masks, and default gateways. The report then delves into subnetting calculations for different office departments, considering varying numbers of workstations and calculating appropriate subnet masks and ranges. The report also examines the implications of increasing the number of hosts per network beyond 1,024. Furthermore, it discusses network protocols in communication networks, including TCP, IP, and HTTP, along with the OSI model. The role and applications of network analyzers are also explored, including their functions in security, performance monitoring, and troubleshooting, with examples of network analyzer tools like GFI LanGuard, Microsoft Network Monitor, and NAST. The report concludes by highlighting the benefits of network analysis tools and recommending suitable tools for network analysis.

Running Head: INTERNETWORKING WITH TCP/IP
M2M Solutions Internetworking
[Student Names]
[Institution Name]
M2M Solutions Internetworking
[Student Names]
[Institution Name]
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

INTERNETWORKING WITH TCP/IP 2
TASK 1
a.The detailed design of a simple addressing solution
The configuration of the private or public Internet protocols in the computer systems
requires to set the ,IP addresses ,subnets masks, and the network defaults gateways.
Therefore while doing the configurations in any network system the IP networks are
partitioned into certain number of addresses which are divided into smaller subnets .
However for this case the M2M network system is divided into six sub networks
depending on the offices and the number of the computers to be installed in each network,
therefore the IP addressing is going to assist to link the various networks that will form large
M2M network systems .
In Ip addressing there are grouping of network classes staring from class A to class C
therefore the proposed network having IP address 10.0.0.0 is going to be split into smaller sub-
networks in order to accommodate all other offices and departments.
During the Ip addressing there will be use of the subnet masks, these masks will be useful
when it comes to the dividing of the IP address into two portions, the first portion will be used in
identification of the hosts computers while the next part identifies the hosts network .
IP addresses: Network and host.
The IP addresses can be referred to as the as the binary number which is made of 32 bits
that is able to uniquely identify the hosts devices like the computers ,printers ,telephones,
switches ,servers among others which are installed in a particular networks.
However they are represented in decimal formats as where the four different numbers
which are separated by the dots as xxx.xxx.xxx.xxx, the IP address is dived as host, network and
the subnetworks accordingly.
Subnet masks
TASK 1
a.The detailed design of a simple addressing solution
The configuration of the private or public Internet protocols in the computer systems
requires to set the ,IP addresses ,subnets masks, and the network defaults gateways.
Therefore while doing the configurations in any network system the IP networks are
partitioned into certain number of addresses which are divided into smaller subnets .
However for this case the M2M network system is divided into six sub networks
depending on the offices and the number of the computers to be installed in each network,
therefore the IP addressing is going to assist to link the various networks that will form large
M2M network systems .
In Ip addressing there are grouping of network classes staring from class A to class C
therefore the proposed network having IP address 10.0.0.0 is going to be split into smaller sub-
networks in order to accommodate all other offices and departments.
During the Ip addressing there will be use of the subnet masks, these masks will be useful
when it comes to the dividing of the IP address into two portions, the first portion will be used in
identification of the hosts computers while the next part identifies the hosts network .
IP addresses: Network and host.
The IP addresses can be referred to as the as the binary number which is made of 32 bits
that is able to uniquely identify the hosts devices like the computers ,printers ,telephones,
switches ,servers among others which are installed in a particular networks.
However they are represented in decimal formats as where the four different numbers
which are separated by the dots as xxx.xxx.xxx.xxx, the IP address is dived as host, network and
the subnetworks accordingly.
Subnet masks

INTERNETWORKING WITH TCP/IP 3
This is another part of the network that is ideally needed to enable the working of the
TCP/IP ,this helps the TCP/IP protocols determine incase the hosts computers or devices are
connected either locally or remotely in another network.
In the TCP/IP ,there are two parts which includes the networks and the hosts addresses
and they can keep on changing dynamically.
However to determine those addresses one can use the subnet mask which is made of 32
bits which is represented with series of ones and also in number form, as in example below
11111111. 11111111.00000000.0000000 or 255.255.000.000, however the subnet mask is then
combined with the IP address as below example:
11000000.10101000.01111011.01111011----- 192.168.123.123 the IP address
11111111. 11111111.00000000.00000000-----255.255.000.000 the Subnet mask
Subnetting
The TCP/IP networks are also sliced more by the administrators of the respective
systems ,this is to ensure that the internet’s addressing schemes are reconciled with the
physically networking that is installed. However the different networks will be allocated a certain
number of addresses in order to fit his number of hosts.
For instance if a network requires 80 hosts the network can be assigned network address
192.168.123.0 which have ip addresses range from 192.168.123.1 up to 192.168.123.254 hence
all the hosts will be connected in the network.
Therefore below are the steps of calculating the addressing solution using utilizing
10.0.0.0 private IP address
Finance Office - 260 workstations
Solution:
For 260 workstations 260 hosts are required and is obtained as follows
This is another part of the network that is ideally needed to enable the working of the
TCP/IP ,this helps the TCP/IP protocols determine incase the hosts computers or devices are
connected either locally or remotely in another network.
In the TCP/IP ,there are two parts which includes the networks and the hosts addresses
and they can keep on changing dynamically.
However to determine those addresses one can use the subnet mask which is made of 32
bits which is represented with series of ones and also in number form, as in example below
11111111. 11111111.00000000.0000000 or 255.255.000.000, however the subnet mask is then
combined with the IP address as below example:
11000000.10101000.01111011.01111011----- 192.168.123.123 the IP address
11111111. 11111111.00000000.00000000-----255.255.000.000 the Subnet mask
Subnetting
The TCP/IP networks are also sliced more by the administrators of the respective
systems ,this is to ensure that the internet’s addressing schemes are reconciled with the
physically networking that is installed. However the different networks will be allocated a certain
number of addresses in order to fit his number of hosts.
For instance if a network requires 80 hosts the network can be assigned network address
192.168.123.0 which have ip addresses range from 192.168.123.1 up to 192.168.123.254 hence
all the hosts will be connected in the network.
Therefore below are the steps of calculating the addressing solution using utilizing
10.0.0.0 private IP address
Finance Office - 260 workstations
Solution:
For 260 workstations 260 hosts are required and is obtained as follows
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

INTERNETWORKING WITH TCP/IP 4
Hosts=2^h-2=260
2^h=260+2
2^h=262
Hence ,Host bits=9
Therefore value =8+8+8+8-9=23
Therefore subnet mask = 11111111.11111111.11111110.00000000 i.e 255.255.254.000
Block size = 2^9=512
The range for this will be 10.0.0.0/23 to 10.0.0.511/23 with 260 workstations.
Transport Office - 130 workstations
Solution:
For 130 workstations 130 hosts are required and is obtained as follows
Hosts=2^h-2=130
2^h=130+2
2^h=132
Hence ,Host bits=8
Therefore value =8+8+8+8-8=24
Therefore subnet mask = 11111111.11111111.11111111.00000000 i.e 255.255.255.000
Block size = 2^8=256
Hosts=2^h-2=260
2^h=260+2
2^h=262
Hence ,Host bits=9
Therefore value =8+8+8+8-9=23
Therefore subnet mask = 11111111.11111111.11111110.00000000 i.e 255.255.254.000
Block size = 2^9=512
The range for this will be 10.0.0.0/23 to 10.0.0.511/23 with 260 workstations.
Transport Office - 130 workstations
Solution:
For 130 workstations 130 hosts are required and is obtained as follows
Hosts=2^h-2=130
2^h=130+2
2^h=132
Hence ,Host bits=8
Therefore value =8+8+8+8-8=24
Therefore subnet mask = 11111111.11111111.11111111.00000000 i.e 255.255.255.000
Block size = 2^8=256
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

INTERNETWORKING WITH TCP/IP 5
The range for this will be 10.0.1.0/24 to 10.0.1.255/24 with 130 workstations.
Research Office - 120 workstations
Solution:
For 120 workstations 120 hosts are required and is obtained as follows
Hosts=2^h-2=120
2^h=120+2
2^h=122
Hence ,Host bits=7
Therefore value =8+8+8+8-7=25
Therefore subnet mask = 11111111.11111111.11111111.10000000 i.e 255.255.255.128
Block size = 2^7=128
The range for this will be 10.0.2.0/25 to 10.0.2.127/25 with 120 workstations.
Sales Office - 40 workstations
Solution:
For 40 workstations 40 hosts are required and is obtained as follows
Hosts=2^h-2=40
2^h=40+2
2^h=42
The range for this will be 10.0.1.0/24 to 10.0.1.255/24 with 130 workstations.
Research Office - 120 workstations
Solution:
For 120 workstations 120 hosts are required and is obtained as follows
Hosts=2^h-2=120
2^h=120+2
2^h=122
Hence ,Host bits=7
Therefore value =8+8+8+8-7=25
Therefore subnet mask = 11111111.11111111.11111111.10000000 i.e 255.255.255.128
Block size = 2^7=128
The range for this will be 10.0.2.0/25 to 10.0.2.127/25 with 120 workstations.
Sales Office - 40 workstations
Solution:
For 40 workstations 40 hosts are required and is obtained as follows
Hosts=2^h-2=40
2^h=40+2
2^h=42

INTERNETWORKING WITH TCP/IP 6
Hence ,Host bits=6
Therefore value =8+8+8+8-6=26
Therefore subnet mask = 11111111.11111111.11111111.11000000 i.e 255.255.255.192
Block size = 2^6=64
The range for this will be 10.0.3.0/26 to 10.0.3.63/26 with 40 workstations.
Information technology - 520 workstations
Solution:
For 520 workstations 520 hosts are required and is obtained as follows
Hosts=2^h-2=520
2^h=520+2
2^h=520
Hence ,Host bits=10
Therefore value =8+8+8+8-10=22
Therefore subnet mask = 11111111.11111111.11111111.11000000 i.e 255.255.252.000
Block size = 2^10=1024
The range for this will be 10.0.4.0/22 to 10.0.4.1023/22 with 520 workstations.
Head Office - 60 workstations
Hence ,Host bits=6
Therefore value =8+8+8+8-6=26
Therefore subnet mask = 11111111.11111111.11111111.11000000 i.e 255.255.255.192
Block size = 2^6=64
The range for this will be 10.0.3.0/26 to 10.0.3.63/26 with 40 workstations.
Information technology - 520 workstations
Solution:
For 520 workstations 520 hosts are required and is obtained as follows
Hosts=2^h-2=520
2^h=520+2
2^h=520
Hence ,Host bits=10
Therefore value =8+8+8+8-10=22
Therefore subnet mask = 11111111.11111111.11111111.11000000 i.e 255.255.252.000
Block size = 2^10=1024
The range for this will be 10.0.4.0/22 to 10.0.4.1023/22 with 520 workstations.
Head Office - 60 workstations
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

INTERNETWORKING WITH TCP/IP 7
Solution:
For 60 workstations 60 hosts are required and is obtained as follows
Hosts=2^h-2=60
2^h=60+2
2^h=62
Hence ,Host bits=6
Therefore value =8+8+8+8-6=26
Therefore subnet mask = 11111111.11111111.11111111.11000000 i.e 255.255.255.192
Block size = 2^6=64
The range for this will be 10.0.5.0/26 to 10.0.5.64/26 with 60 workstations.
b. what happens to design if the number of hosts per network jumps to over
1,024 per building.
Incase number of hosts per network rises over 1024 it will be hard to be accommodated
however to accommodate those hosts in that network one needs to expand mask up to /21 this
will however enable accommodation of up to 2046 hosts and this address issue of rise of host
beyond 1024.
TASK 2
protocol in communication networks and the role of network analyzers.
Protocol in communication networks
The information technology embarrasses use of protocols which is a given sets of rule
that is used by the network devices to communicate with each other ,however it is used as a
facilitator of communications between the network nodes and devices.
Solution:
For 60 workstations 60 hosts are required and is obtained as follows
Hosts=2^h-2=60
2^h=60+2
2^h=62
Hence ,Host bits=6
Therefore value =8+8+8+8-6=26
Therefore subnet mask = 11111111.11111111.11111111.11000000 i.e 255.255.255.192
Block size = 2^6=64
The range for this will be 10.0.5.0/26 to 10.0.5.64/26 with 60 workstations.
b. what happens to design if the number of hosts per network jumps to over
1,024 per building.
Incase number of hosts per network rises over 1024 it will be hard to be accommodated
however to accommodate those hosts in that network one needs to expand mask up to /21 this
will however enable accommodation of up to 2046 hosts and this address issue of rise of host
beyond 1024.
TASK 2
protocol in communication networks and the role of network analyzers.
Protocol in communication networks
The information technology embarrasses use of protocols which is a given sets of rule
that is used by the network devices to communicate with each other ,however it is used as a
facilitator of communications between the network nodes and devices.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

INTERNETWORKING WITH TCP/IP 8
In various communications stages of telecommunications in the protocol stages ,there are
some protocols that are used transmit data between the hardware and the application software in
the network.
There is a model that is standardized named as open system interconnection which has
various layers and are recognized in the international standards.
Below are some examples of internet protocols:
Transmissions Control Protocols (TCP), this use rules to send message to other points of
internet inform of packets.
Internet Protocols (IP),this is the one that use a rule on sending or receiving of message at
the internet addresses level.
Hypertext Transfer Protocols (HTTP) this has a rule to use with a similar application
remotely over the internet.
Other type of protocols includes Borders Gateway Protocols (BGP) and Dynamic Hosts
Configurations Protocols (DHCP) among others which also have their set of rule to
communicate.
The OSI layers of protocols are divided into different layers which ranges from layer 7 to
layer 1 ,however each layer is associated with a unique properties ,these layers are used by the
network devices to communicate and are divided into seven categories as discussed below:
7th Layer: The application layer. This is the layer where the two communicating devices are
established and together with capacities of networks ,however the contents is created , sent and
opened at this layer.
6th Layer: The presentation layer. This is the layer that form part of operating systems and it is
able to do conversion of the data from digital format to analog and from analog to digital format.
5th Layer: The session layer. This is layer that controls the communication where it creates
connections incase it is broken or interrupted.
In various communications stages of telecommunications in the protocol stages ,there are
some protocols that are used transmit data between the hardware and the application software in
the network.
There is a model that is standardized named as open system interconnection which has
various layers and are recognized in the international standards.
Below are some examples of internet protocols:
Transmissions Control Protocols (TCP), this use rules to send message to other points of
internet inform of packets.
Internet Protocols (IP),this is the one that use a rule on sending or receiving of message at
the internet addresses level.
Hypertext Transfer Protocols (HTTP) this has a rule to use with a similar application
remotely over the internet.
Other type of protocols includes Borders Gateway Protocols (BGP) and Dynamic Hosts
Configurations Protocols (DHCP) among others which also have their set of rule to
communicate.
The OSI layers of protocols are divided into different layers which ranges from layer 7 to
layer 1 ,however each layer is associated with a unique properties ,these layers are used by the
network devices to communicate and are divided into seven categories as discussed below:
7th Layer: The application layer. This is the layer where the two communicating devices are
established and together with capacities of networks ,however the contents is created , sent and
opened at this layer.
6th Layer: The presentation layer. This is the layer that form part of operating systems and it is
able to do conversion of the data from digital format to analog and from analog to digital format.
5th Layer: The session layer. This is layer that controls the communication where it creates
connections incase it is broken or interrupted.

INTERNETWORKING WITH TCP/IP 9
4th Layer: The transport layer. This is the layer that is used to control the movement of packets
over network ,delivers packets, detecting and eliminating errors when packet reach the
destination .
3rd Layer: The network layer. This is the layer that is used to determine the packets address and
also routes the data packets this is the IP of the network.
2nd Layer: The data-link layer. This is the layer that provides the link over the physical
networks and converts the packets to frame of networks ,however it is divided into two
categories including logical links controls layers and the media access controls layer this is
enabled by use of the Ethernet cables.
1st Layer: The physical layer. This layer is used to transmit the streams of bits over the network
in form of electric ,radios or optical signals, this give the necessary hardware for transmission.
Roles of analysers
The network analyzers is the made of computer hardware and application programs ,or
some devices ,however it get installed in a given networks or computers systems to prevent and
control the hacking activity or any malicious activities to be done (Cory, 2015).
.
This tool is used to support the service given by the computer firewall and anti-viruses
software , the tool is installed and it can have the following uses:
Updating the administrator on the statistical information regarding the activities done in
the networks.
Testing of anti viruses programs and identification of possible vulnerability.
Detection of any abnormal levels of networks traffics.
Detection of abnormal character in a packet.
Determining the source and destination of packets.
Configuration of alarm for any able risk or threat.
Searching of strings of data in a given packet.
4th Layer: The transport layer. This is the layer that is used to control the movement of packets
over network ,delivers packets, detecting and eliminating errors when packet reach the
destination .
3rd Layer: The network layer. This is the layer that is used to determine the packets address and
also routes the data packets this is the IP of the network.
2nd Layer: The data-link layer. This is the layer that provides the link over the physical
networks and converts the packets to frame of networks ,however it is divided into two
categories including logical links controls layers and the media access controls layer this is
enabled by use of the Ethernet cables.
1st Layer: The physical layer. This layer is used to transmit the streams of bits over the network
in form of electric ,radios or optical signals, this give the necessary hardware for transmission.
Roles of analysers
The network analyzers is the made of computer hardware and application programs ,or
some devices ,however it get installed in a given networks or computers systems to prevent and
control the hacking activity or any malicious activities to be done (Cory, 2015).
.
This tool is used to support the service given by the computer firewall and anti-viruses
software , the tool is installed and it can have the following uses:
Updating the administrator on the statistical information regarding the activities done in
the networks.
Testing of anti viruses programs and identification of possible vulnerability.
Detection of any abnormal levels of networks traffics.
Detection of abnormal character in a packet.
Determining the source and destination of packets.
Configuration of alarm for any able risk or threat.
Searching of strings of data in a given packet.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
INTERNETWORKING WITH TCP/IP 10
Monitoring of bandwidths utilized over a given period of time.
Creation of plug-ins of a specified type of application.
Displaying of statistical data in a panel which is users friendly.
Network analyzer tools analysis.
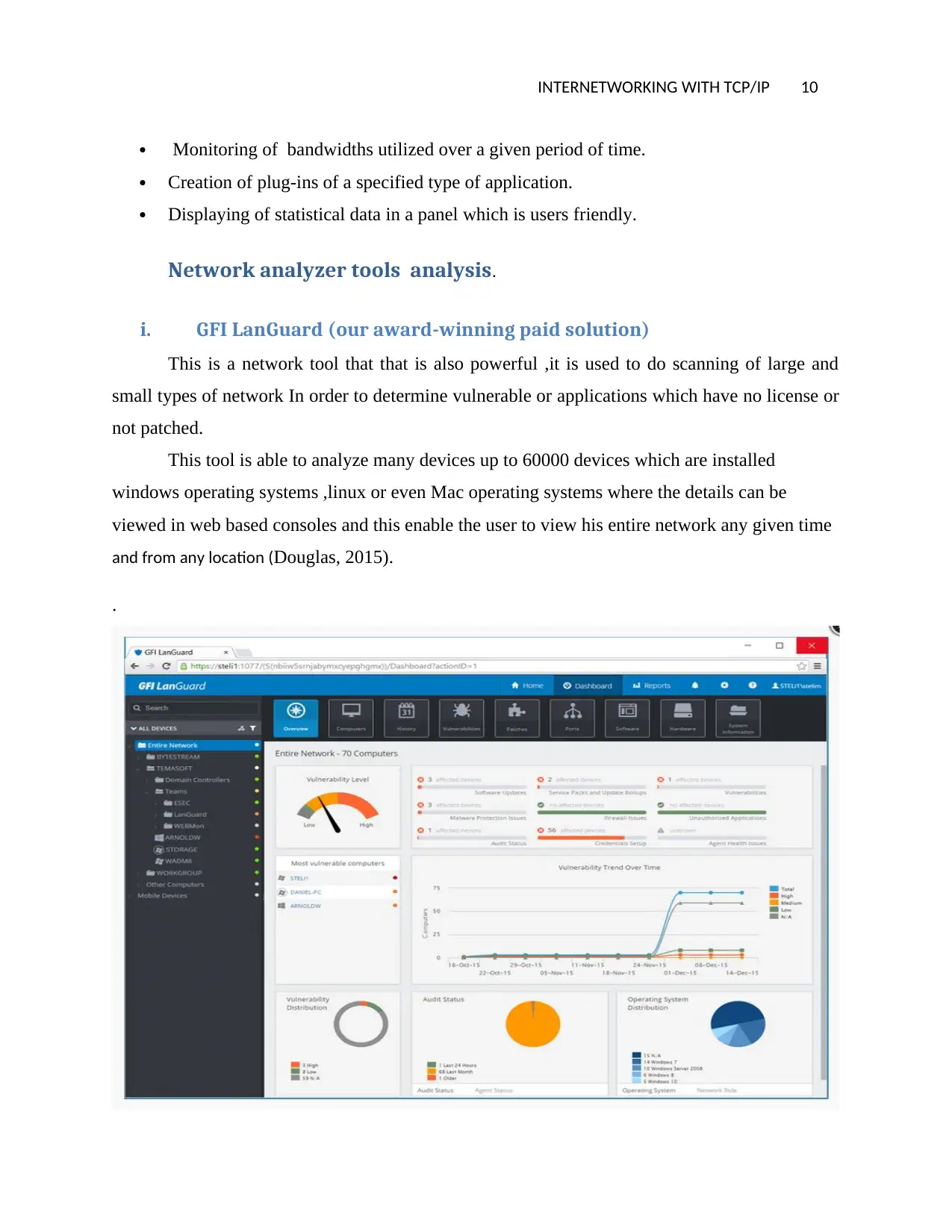
i. GFI LanGuard (our award-winning paid solution)
This is a network tool that that is also powerful ,it is used to do scanning of large and
small types of network In order to determine vulnerable or applications which have no license or
not patched.
This tool is able to analyze many devices up to 60000 devices which are installed
windows operating systems ,linux or even Mac operating systems where the details can be
viewed in web based consoles and this enable the user to view his entire network any given time
and from any location (Douglas, 2015).
.
Monitoring of bandwidths utilized over a given period of time.
Creation of plug-ins of a specified type of application.
Displaying of statistical data in a panel which is users friendly.
Network analyzer tools analysis.
i. GFI LanGuard (our award-winning paid solution)
This is a network tool that that is also powerful ,it is used to do scanning of large and
small types of network In order to determine vulnerable or applications which have no license or
not patched.
This tool is able to analyze many devices up to 60000 devices which are installed
windows operating systems ,linux or even Mac operating systems where the details can be
viewed in web based consoles and this enable the user to view his entire network any given time
and from any location (Douglas, 2015).
.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
INTERNETWORKING WITH TCP/IP 11
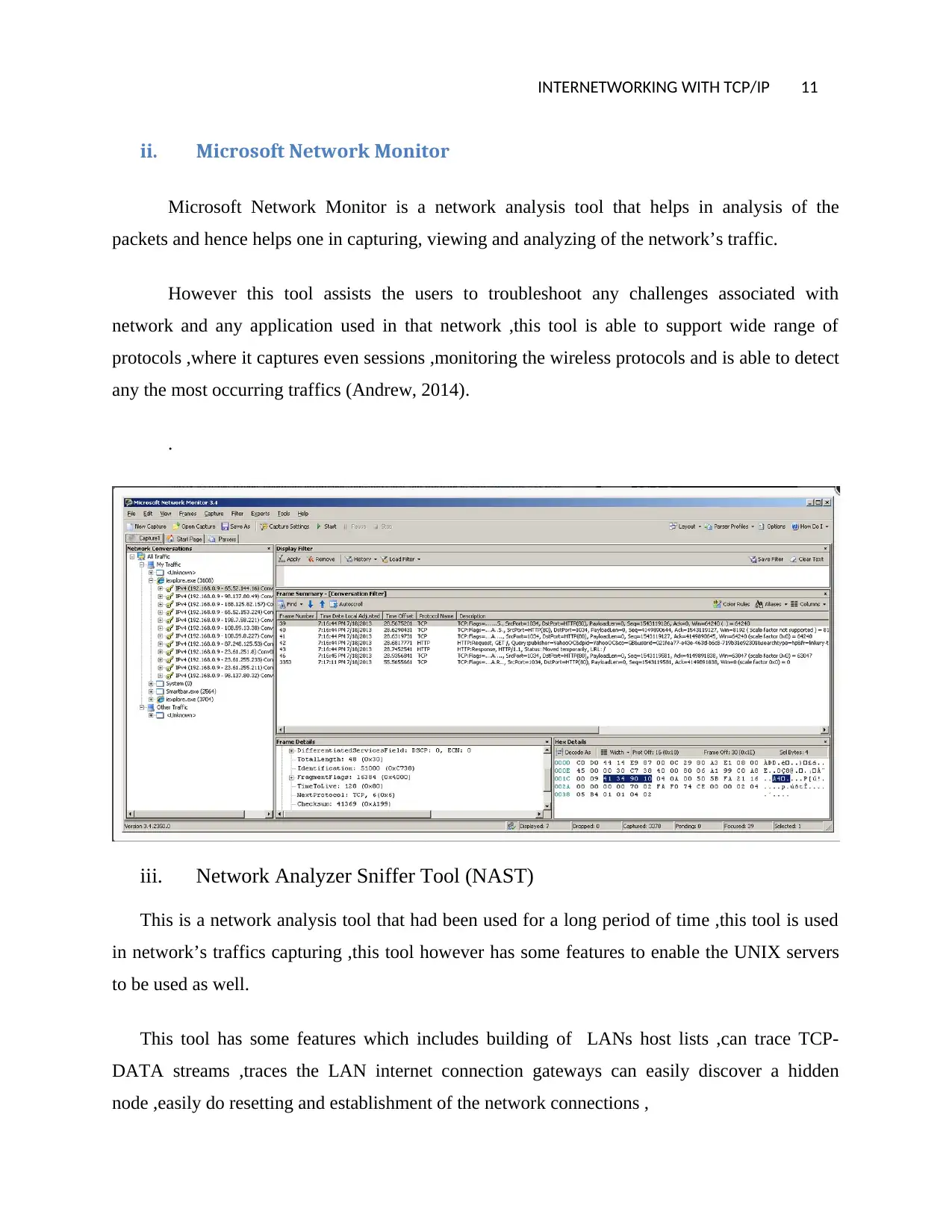
ii. Microsoft Network Monitor
Microsoft Network Monitor is a network analysis tool that helps in analysis of the
packets and hence helps one in capturing, viewing and analyzing of the network’s traffic.
However this tool assists the users to troubleshoot any challenges associated with
network and any application used in that network ,this tool is able to support wide range of
protocols ,where it captures even sessions ,monitoring the wireless protocols and is able to detect
any the most occurring traffics (Andrew, 2014).
.
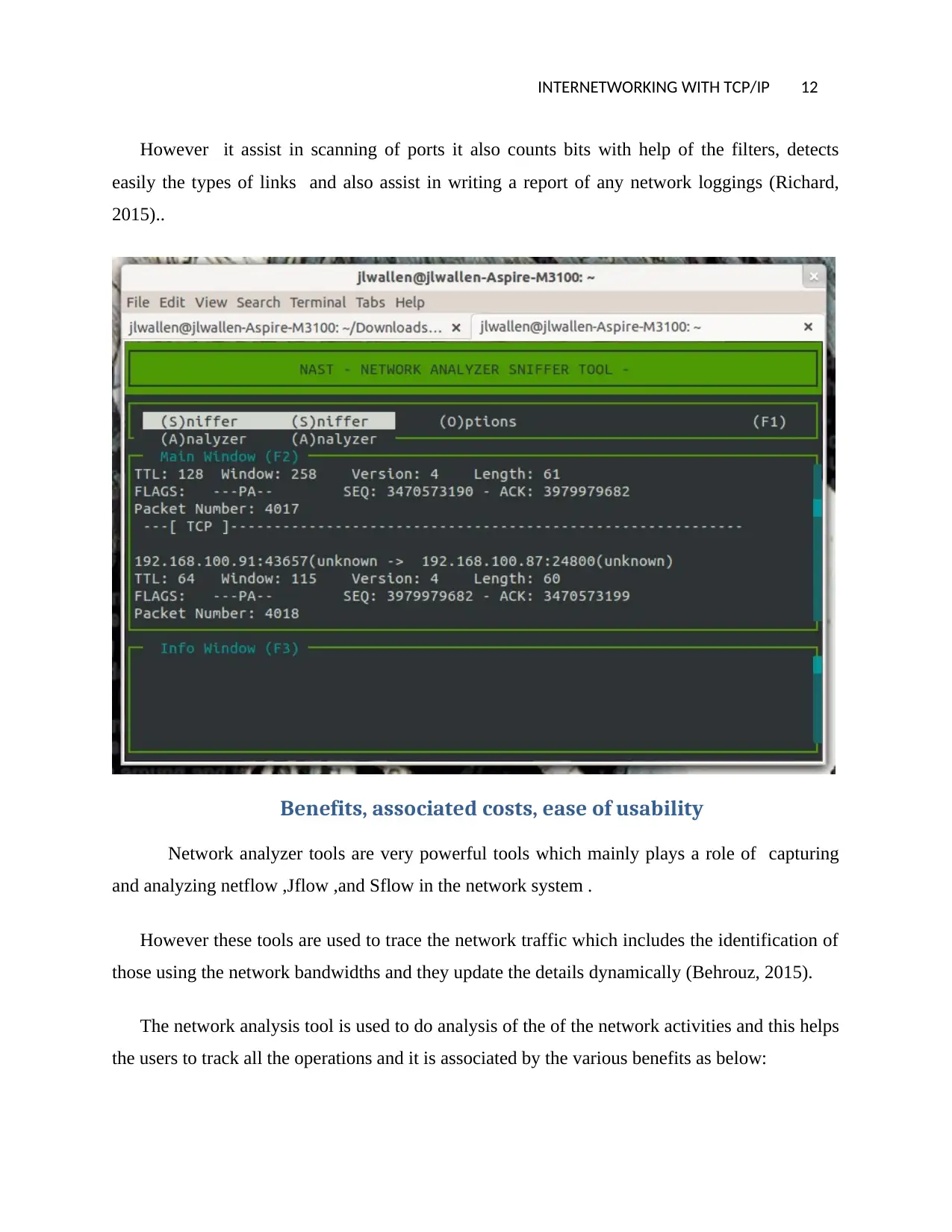
iii. Network Analyzer Sniffer Tool (NAST)
This is a network analysis tool that had been used for a long period of time ,this tool is used
in network’s traffics capturing ,this tool however has some features to enable the UNIX servers
to be used as well.
This tool has some features which includes building of LANs host lists ,can trace TCP-
DATA streams ,traces the LAN internet connection gateways can easily discover a hidden
node ,easily do resetting and establishment of the network connections ,
ii. Microsoft Network Monitor
Microsoft Network Monitor is a network analysis tool that helps in analysis of the
packets and hence helps one in capturing, viewing and analyzing of the network’s traffic.
However this tool assists the users to troubleshoot any challenges associated with
network and any application used in that network ,this tool is able to support wide range of
protocols ,where it captures even sessions ,monitoring the wireless protocols and is able to detect
any the most occurring traffics (Andrew, 2014).
.
iii. Network Analyzer Sniffer Tool (NAST)
This is a network analysis tool that had been used for a long period of time ,this tool is used
in network’s traffics capturing ,this tool however has some features to enable the UNIX servers
to be used as well.
This tool has some features which includes building of LANs host lists ,can trace TCP-
DATA streams ,traces the LAN internet connection gateways can easily discover a hidden
node ,easily do resetting and establishment of the network connections ,
INTERNETWORKING WITH TCP/IP 12
However it assist in scanning of ports it also counts bits with help of the filters, detects
easily the types of links and also assist in writing a report of any network loggings (Richard,
2015)..
Benefits, associated costs, ease of usability
Network analyzer tools are very powerful tools which mainly plays a role of capturing
and analyzing netflow ,Jflow ,and Sflow in the network system .
However these tools are used to trace the network traffic which includes the identification of
those using the network bandwidths and they update the details dynamically (Behrouz, 2015).
The network analysis tool is used to do analysis of the of the network activities and this helps
the users to track all the operations and it is associated by the various benefits as below:
However it assist in scanning of ports it also counts bits with help of the filters, detects
easily the types of links and also assist in writing a report of any network loggings (Richard,
2015)..
Benefits, associated costs, ease of usability
Network analyzer tools are very powerful tools which mainly plays a role of capturing
and analyzing netflow ,Jflow ,and Sflow in the network system .
However these tools are used to trace the network traffic which includes the identification of
those using the network bandwidths and they update the details dynamically (Behrouz, 2015).
The network analysis tool is used to do analysis of the of the network activities and this helps
the users to track all the operations and it is associated by the various benefits as below:
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 14
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.




