ITC542: Internetworking with TCP/IP - Addressing and Network Report
VerifiedAdded on 2021/04/21
|11
|1793
|84
Report
AI Summary
This report, prepared for ITC542 - Internetworking with TCP/IP, delves into key networking concepts. It begins with a comparison of the OSI and TCP/IP models, highlighting their architectures and functionalities. The report then presents subnet calculations for specific IP addresses, demonstrating practical application of IP addressing. It also explains the Address Resolution Protocol (ARP) and its purpose in mapping MAC addresses to IP addresses. The core of the report is a case study that addresses the implementation of a new network solution for a company with multiple branches. The case study includes network design, justification for the design choices, addressing solutions, and considerations for handling increased network traffic. The network design incorporates VLANs and EIGRP for improved performance and security. The report concludes with a discussion on the implications of increased host numbers per building and emphasizes the importance of network security and traffic management. Finally, the report includes a bibliography of relevant sources.

Running head: ITC542 - INTERNETWORKING WITH TCP/IP
ITC542 - Internetworking with TCP/IP
Assessment No
Assessment Title
Student Name & ID
Subject Name and Code
Student Email Address
ITC542 - Internetworking with TCP/IP
Assessment No
Assessment Title
Student Name & ID
Subject Name and Code
Student Email Address
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1
ITC542 - INTERNETWORKING WITH TCP/IP
Table of Contents
Question 1: Comparison of the OSI reference model with TCP/IP networking model..................2
Question 2:.......................................................................................................................................3
Hands on Project 2.3:.......................................................................................................3
Hands on Project 2.5:.......................................................................................................3
Question 3: Address Resolution Protocol and its Purpose..............................................................4
Question 4: Case Study Task...........................................................................................................5
Introduction......................................................................................................................5
Network design................................................................................................................6
Justification......................................................................................................................6
Addressing solution.........................................................................................................7
Host per network jumps over 1024 per building.............................................................8
Conclusion.......................................................................................................................9
Bibliography..................................................................................................................................10
ITC542 - INTERNETWORKING WITH TCP/IP
Table of Contents
Question 1: Comparison of the OSI reference model with TCP/IP networking model..................2
Question 2:.......................................................................................................................................3
Hands on Project 2.3:.......................................................................................................3
Hands on Project 2.5:.......................................................................................................3
Question 3: Address Resolution Protocol and its Purpose..............................................................4
Question 4: Case Study Task...........................................................................................................5
Introduction......................................................................................................................5
Network design................................................................................................................6
Justification......................................................................................................................6
Addressing solution.........................................................................................................7
Host per network jumps over 1024 per building.............................................................8
Conclusion.......................................................................................................................9
Bibliography..................................................................................................................................10

2
ITC542 - INTERNETWORKING WITH TCP/IP
Question 1: Comparison of the OSI reference model with TCP/IP networking
model
The TCP/IP model is the communication protocol that is used for connecting the hosts
with the internet. The OSI model is used as a gateway for communication with the end users and
thee network. The TCP/IP protocol is used by different application in the internet and it was
developed by the department of defense for allowing the devices to be connected with the
internet service. On the other hand the OSI model is developed by the International organization
for standards and it acts as a theoretical model (Edwards & Bramante, 2015). The OSI
model only finds its application as a reference model and it is developed based on the TCP/IP
model. There are four layers in the TCP/IP model while the OSI reference model have seven
layers. In case of reliability the OSI reference model is less reliable when compared with the
TCP/IP model because it is older. There are different boundaries and strict protocols followed by
the OSI reference model but the TCP/IP model only follows the basic guidelines for the
transmission of the data packets to the destination address over the network (Sinha et al., 2017).
The OSI reference model is the most useful when working and describing networks
because OSI model supports both the connection oriented and the connection less
communication protocol whereas the TCP/IP does not support the connection less
communication.
ITC542 - INTERNETWORKING WITH TCP/IP
Question 1: Comparison of the OSI reference model with TCP/IP networking
model
The TCP/IP model is the communication protocol that is used for connecting the hosts
with the internet. The OSI model is used as a gateway for communication with the end users and
thee network. The TCP/IP protocol is used by different application in the internet and it was
developed by the department of defense for allowing the devices to be connected with the
internet service. On the other hand the OSI model is developed by the International organization
for standards and it acts as a theoretical model (Edwards & Bramante, 2015). The OSI
model only finds its application as a reference model and it is developed based on the TCP/IP
model. There are four layers in the TCP/IP model while the OSI reference model have seven
layers. In case of reliability the OSI reference model is less reliable when compared with the
TCP/IP model because it is older. There are different boundaries and strict protocols followed by
the OSI reference model but the TCP/IP model only follows the basic guidelines for the
transmission of the data packets to the destination address over the network (Sinha et al., 2017).
The OSI reference model is the most useful when working and describing networks
because OSI model supports both the connection oriented and the connection less
communication protocol whereas the TCP/IP does not support the connection less
communication.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
3
ITC542 - INTERNETWORKING WITH TCP/IP
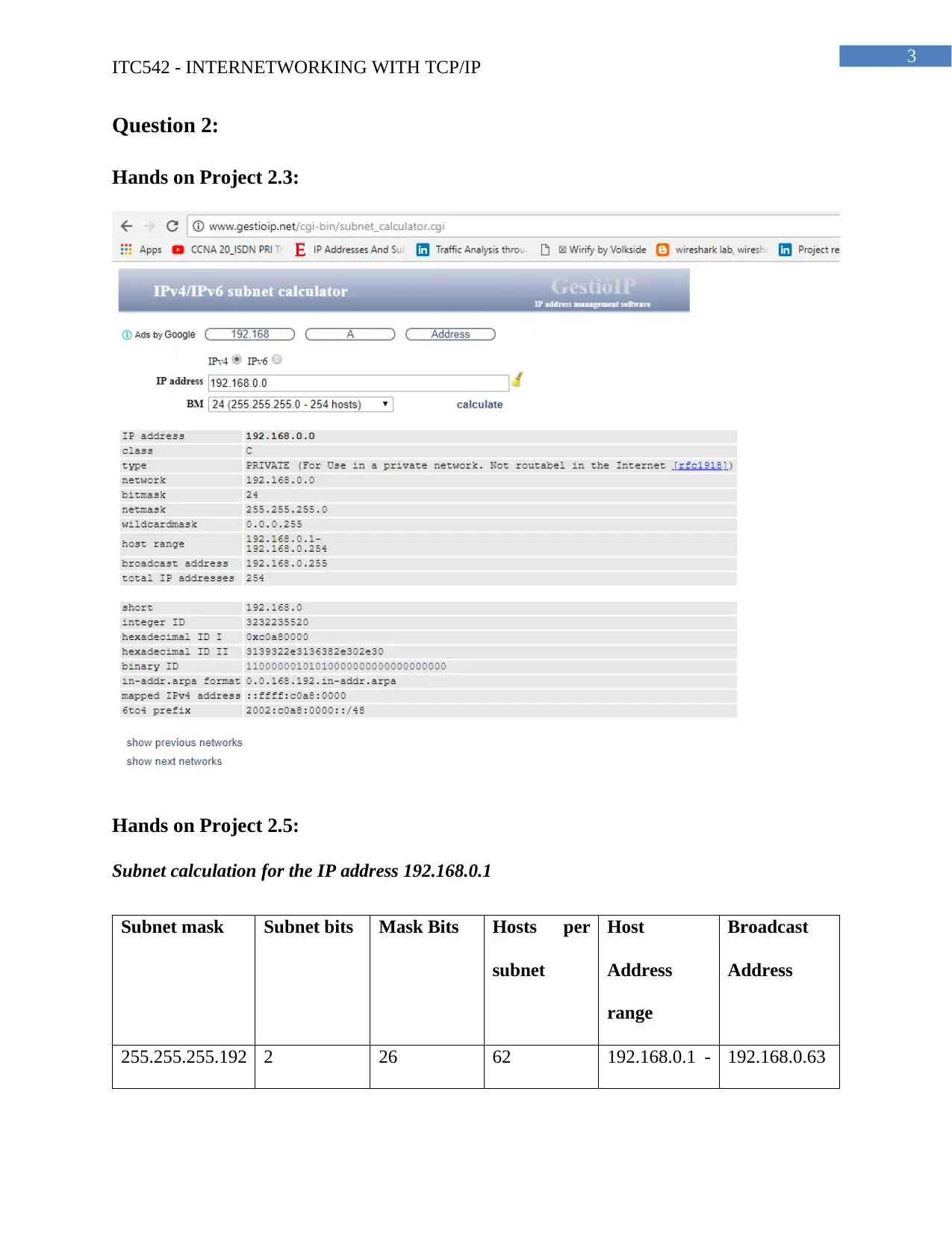
Question 2:
Hands on Project 2.3:
Hands on Project 2.5:
Subnet calculation for the IP address 192.168.0.1
Subnet mask Subnet bits Mask Bits Hosts per
subnet
Host
Address
range
Broadcast
Address
255.255.255.192 2 26 62 192.168.0.1 - 192.168.0.63
ITC542 - INTERNETWORKING WITH TCP/IP
Question 2:
Hands on Project 2.3:
Hands on Project 2.5:
Subnet calculation for the IP address 192.168.0.1
Subnet mask Subnet bits Mask Bits Hosts per
subnet
Host
Address
range
Broadcast
Address
255.255.255.192 2 26 62 192.168.0.1 - 192.168.0.63
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
4
ITC542 - INTERNETWORKING WITH TCP/IP
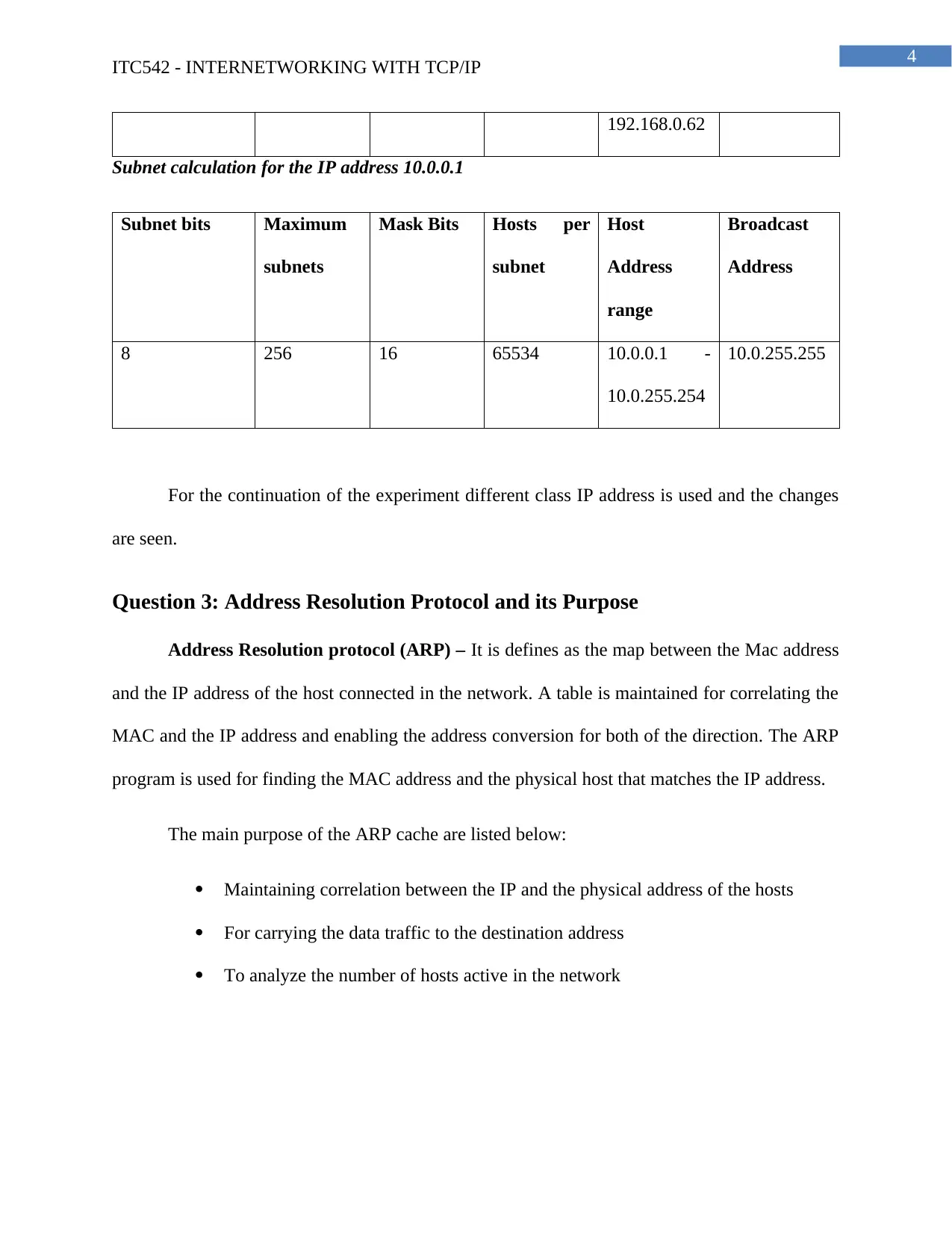
192.168.0.62
Subnet calculation for the IP address 10.0.0.1
Subnet bits Maximum
subnets
Mask Bits Hosts per
subnet
Host
Address
range
Broadcast
Address
8 256 16 65534 10.0.0.1 -
10.0.255.254
10.0.255.255
For the continuation of the experiment different class IP address is used and the changes
are seen.
Question 3: Address Resolution Protocol and its Purpose
Address Resolution protocol (ARP) – It is defines as the map between the Mac address
and the IP address of the host connected in the network. A table is maintained for correlating the
MAC and the IP address and enabling the address conversion for both of the direction. The ARP
program is used for finding the MAC address and the physical host that matches the IP address.
The main purpose of the ARP cache are listed below:
Maintaining correlation between the IP and the physical address of the hosts
For carrying the data traffic to the destination address
To analyze the number of hosts active in the network
ITC542 - INTERNETWORKING WITH TCP/IP
192.168.0.62
Subnet calculation for the IP address 10.0.0.1
Subnet bits Maximum
subnets
Mask Bits Hosts per
subnet
Host
Address
range
Broadcast
Address
8 256 16 65534 10.0.0.1 -
10.0.255.254
10.0.255.255
For the continuation of the experiment different class IP address is used and the changes
are seen.
Question 3: Address Resolution Protocol and its Purpose
Address Resolution protocol (ARP) – It is defines as the map between the Mac address
and the IP address of the host connected in the network. A table is maintained for correlating the
MAC and the IP address and enabling the address conversion for both of the direction. The ARP
program is used for finding the MAC address and the physical host that matches the IP address.
The main purpose of the ARP cache are listed below:
Maintaining correlation between the IP and the physical address of the hosts
For carrying the data traffic to the destination address
To analyze the number of hosts active in the network

5
ITC542 - INTERNETWORKING WITH TCP/IP
Question 4: Case Study Task
Introduction
There is a requirement of the Foreshore IT solution to implement a new network solution
for its company such that the users of each of the branches can communicate with the other
branches. The company uses the class A network address 10.0.0.0 for connecting the six offices
located in different location of Adelaide. The network is subnetted for reducing the wastage of
the IP address and increase the security and efficiency of the network solution. A report is
created for the organization with the network address plan and the details of the IP address and
subnet used for configuring the interface of the hardware device. An estimation is created listing
the resource and the hardware required for the development of the network infrastructure. The
proposed network solution is designed for 1200 hosts connected across different subnets for each
of the office network.
ITC542 - INTERNETWORKING WITH TCP/IP
Question 4: Case Study Task
Introduction
There is a requirement of the Foreshore IT solution to implement a new network solution
for its company such that the users of each of the branches can communicate with the other
branches. The company uses the class A network address 10.0.0.0 for connecting the six offices
located in different location of Adelaide. The network is subnetted for reducing the wastage of
the IP address and increase the security and efficiency of the network solution. A report is
created for the organization with the network address plan and the details of the IP address and
subnet used for configuring the interface of the hardware device. An estimation is created listing
the resource and the hardware required for the development of the network infrastructure. The
proposed network solution is designed for 1200 hosts connected across different subnets for each
of the office network.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
6
ITC542 - INTERNETWORKING WITH TCP/IP
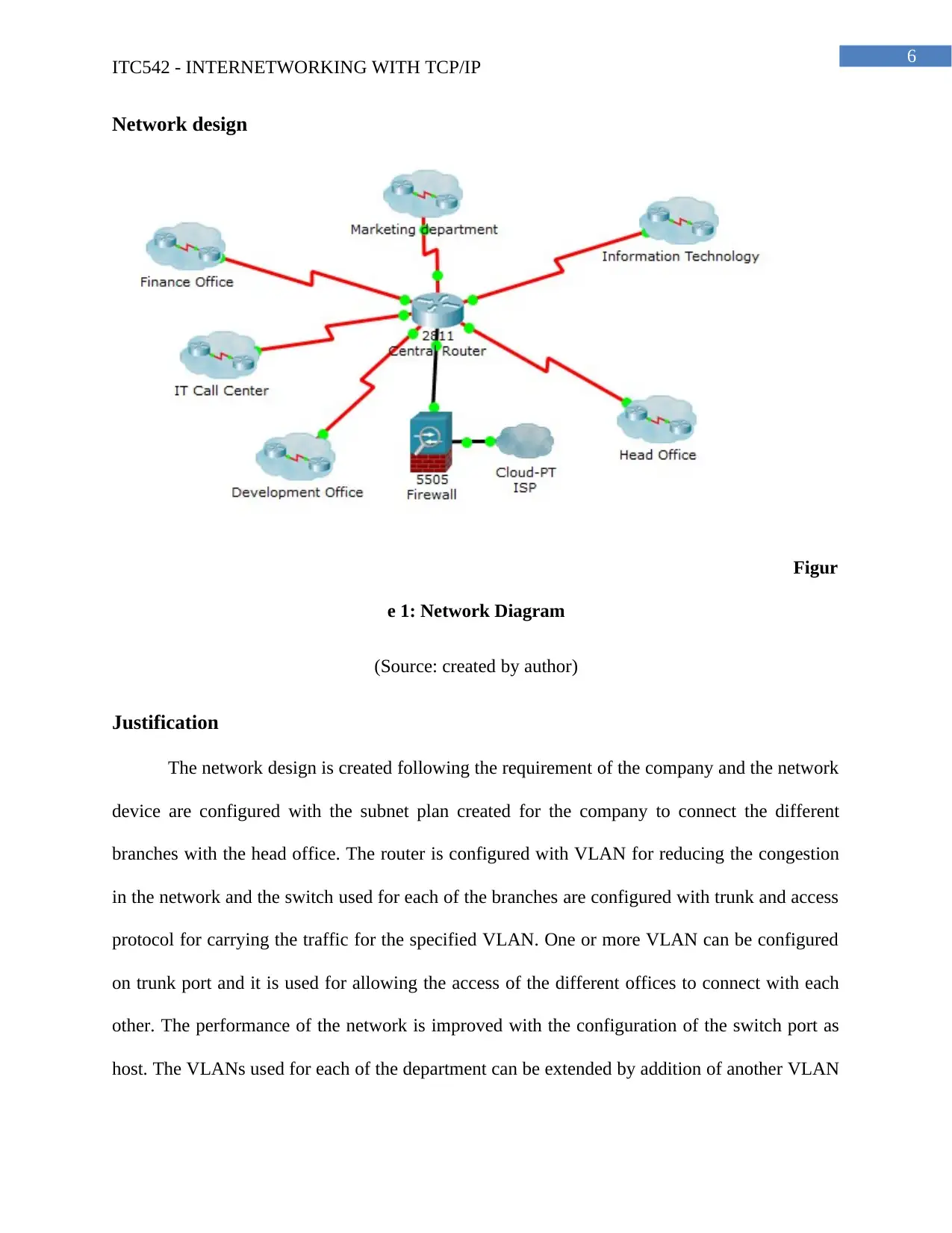
Network design
Figur
e 1: Network Diagram
(Source: created by author)
Justification
The network design is created following the requirement of the company and the network
device are configured with the subnet plan created for the company to connect the different
branches with the head office. The router is configured with VLAN for reducing the congestion
in the network and the switch used for each of the branches are configured with trunk and access
protocol for carrying the traffic for the specified VLAN. One or more VLAN can be configured
on trunk port and it is used for allowing the access of the different offices to connect with each
other. The performance of the network is improved with the configuration of the switch port as
host. The VLANs used for each of the department can be extended by addition of another VLAN
ITC542 - INTERNETWORKING WITH TCP/IP
Network design
Figur
e 1: Network Diagram
(Source: created by author)
Justification
The network design is created following the requirement of the company and the network
device are configured with the subnet plan created for the company to connect the different
branches with the head office. The router is configured with VLAN for reducing the congestion
in the network and the switch used for each of the branches are configured with trunk and access
protocol for carrying the traffic for the specified VLAN. One or more VLAN can be configured
on trunk port and it is used for allowing the access of the different offices to connect with each
other. The performance of the network is improved with the configuration of the switch port as
host. The VLANs used for each of the department can be extended by addition of another VLAN
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
7
ITC542 - INTERNETWORKING WITH TCP/IP
and the traffic can be separated for reducing the traffic and increasing the efficiency of the
network. The switch is also configured with spanning tree and the default VLAN is removed
from the spanning tree list such that it cannot be used for communication and the traffic in the
network can be controlled.
Addressing solution
Network Address: 10.0.0.0/21
Number of IP address available for the network: 2046
Required number of IP address: 1130
Number of IP address available in the subnet: 2036
Subnet Name Neede
d Size
Allocate
d Size
Mas
k
Dec Mask Addre
ss
Assignabl
e Range
Broadcas
t
Head_Office 60 62 /26 255.255.25
5.192
10.0.7.
128
10.0.7.129
-
10.0.7.190
10.0.7.19
1
Finance_office 260 510 /23 255.255.25
4.0
10.0.4.
0
10.0.4.1 -
10.0.5.254
10.0.5.25
5
IT_Call
Centre
520 1022 /22 255.255.25
2.0
10.0.0.
0
10.0.0.1 -
10.0.3.254
10.0.3.25
5
ITC542 - INTERNETWORKING WITH TCP/IP
and the traffic can be separated for reducing the traffic and increasing the efficiency of the
network. The switch is also configured with spanning tree and the default VLAN is removed
from the spanning tree list such that it cannot be used for communication and the traffic in the
network can be controlled.
Addressing solution
Network Address: 10.0.0.0/21
Number of IP address available for the network: 2046
Required number of IP address: 1130
Number of IP address available in the subnet: 2036
Subnet Name Neede
d Size
Allocate
d Size
Mas
k
Dec Mask Addre
ss
Assignabl
e Range
Broadcas
t
Head_Office 60 62 /26 255.255.25
5.192
10.0.7.
128
10.0.7.129
-
10.0.7.190
10.0.7.19
1
Finance_office 260 510 /23 255.255.25
4.0
10.0.4.
0
10.0.4.1 -
10.0.5.254
10.0.5.25
5
IT_Call
Centre
520 1022 /22 255.255.25
2.0
10.0.0.
0
10.0.0.1 -
10.0.3.254
10.0.3.25
5
8
ITC542 - INTERNETWORKING WITH TCP/IP
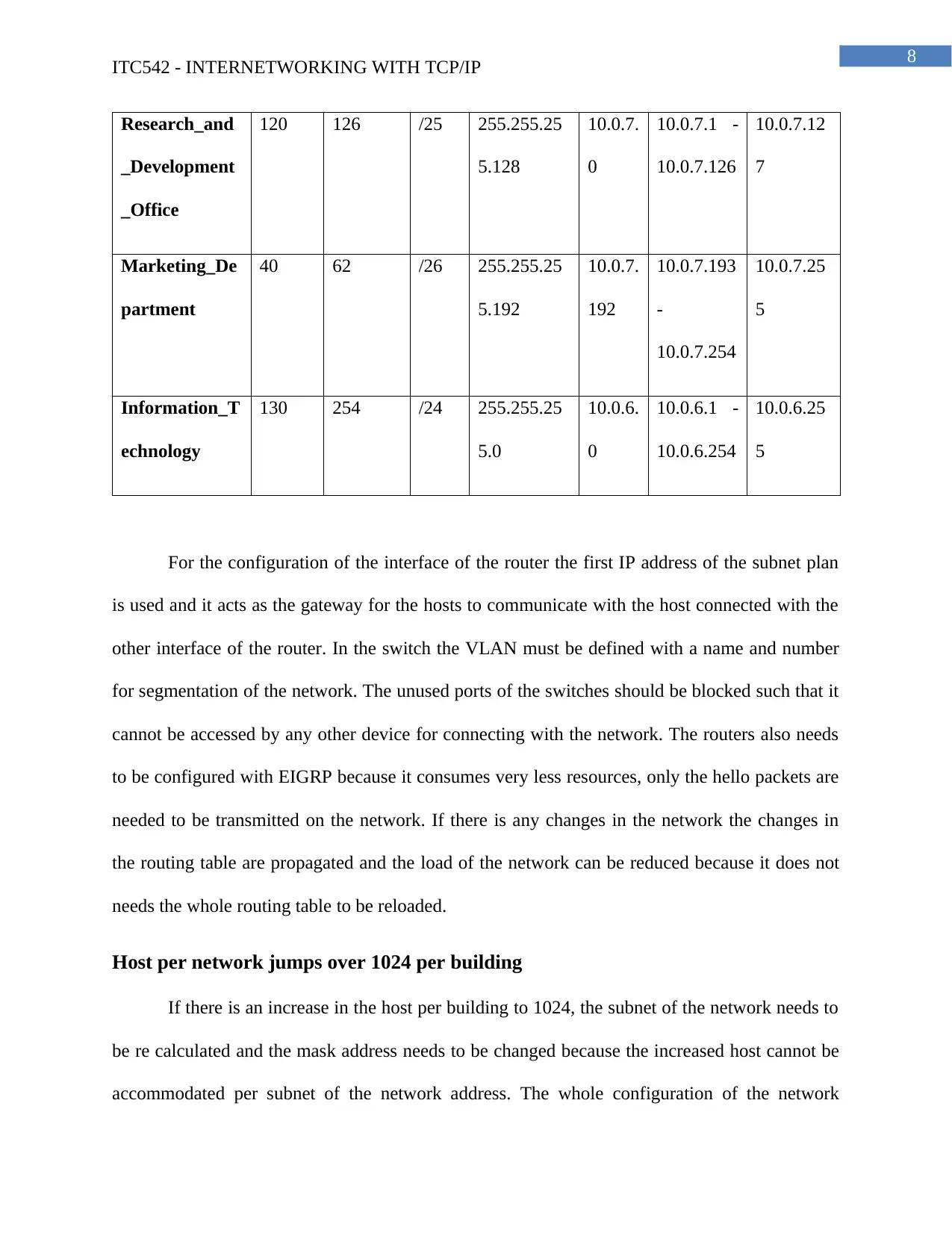
Research_and
_Development
_Office
120 126 /25 255.255.25
5.128
10.0.7.
0
10.0.7.1 -
10.0.7.126
10.0.7.12
7
Marketing_De
partment
40 62 /26 255.255.25
5.192
10.0.7.
192
10.0.7.193
-
10.0.7.254
10.0.7.25
5
Information_T
echnology
130 254 /24 255.255.25
5.0
10.0.6.
0
10.0.6.1 -
10.0.6.254
10.0.6.25
5
For the configuration of the interface of the router the first IP address of the subnet plan
is used and it acts as the gateway for the hosts to communicate with the host connected with the
other interface of the router. In the switch the VLAN must be defined with a name and number
for segmentation of the network. The unused ports of the switches should be blocked such that it
cannot be accessed by any other device for connecting with the network. The routers also needs
to be configured with EIGRP because it consumes very less resources, only the hello packets are
needed to be transmitted on the network. If there is any changes in the network the changes in
the routing table are propagated and the load of the network can be reduced because it does not
needs the whole routing table to be reloaded.
Host per network jumps over 1024 per building
If there is an increase in the host per building to 1024, the subnet of the network needs to
be re calculated and the mask address needs to be changed because the increased host cannot be
accommodated per subnet of the network address. The whole configuration of the network
ITC542 - INTERNETWORKING WITH TCP/IP
Research_and
_Development
_Office
120 126 /25 255.255.25
5.128
10.0.7.
0
10.0.7.1 -
10.0.7.126
10.0.7.12
7
Marketing_De
partment
40 62 /26 255.255.25
5.192
10.0.7.
192
10.0.7.193
-
10.0.7.254
10.0.7.25
5
Information_T
echnology
130 254 /24 255.255.25
5.0
10.0.6.
0
10.0.6.1 -
10.0.6.254
10.0.6.25
5
For the configuration of the interface of the router the first IP address of the subnet plan
is used and it acts as the gateway for the hosts to communicate with the host connected with the
other interface of the router. In the switch the VLAN must be defined with a name and number
for segmentation of the network. The unused ports of the switches should be blocked such that it
cannot be accessed by any other device for connecting with the network. The routers also needs
to be configured with EIGRP because it consumes very less resources, only the hello packets are
needed to be transmitted on the network. If there is any changes in the network the changes in
the routing table are propagated and the load of the network can be reduced because it does not
needs the whole routing table to be reloaded.
Host per network jumps over 1024 per building
If there is an increase in the host per building to 1024, the subnet of the network needs to
be re calculated and the mask address needs to be changed because the increased host cannot be
accommodated per subnet of the network address. The whole configuration of the network
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

9
ITC542 - INTERNETWORKING WITH TCP/IP
should be done from the scratch because the default gateway address and the range allocated for
the DHCP pool should also be changed. The change in the router configuration with the new
address plan can handle the new changes in the network.
Conclusion
From the above report it can be concluded that the proposal of the new network solution
would benefit the organization to efficiently communicate with the remote branches of the
organization. The main focus for the security should be given on the resources and servers
installed in the central office of the organization and it should be secured from illegal access. The
documentation of the address plan is also important because it can be used as a reference for
configuring the interfaces of the hardware device used for connecting with the hosts located in
the branches. The traffic management is also necessary and the current network traffic should be
monitored by the network administrator for maintaining the security of the network and protect it
from different attacks.
ITC542 - INTERNETWORKING WITH TCP/IP
should be done from the scratch because the default gateway address and the range allocated for
the DHCP pool should also be changed. The change in the router configuration with the new
address plan can handle the new changes in the network.
Conclusion
From the above report it can be concluded that the proposal of the new network solution
would benefit the organization to efficiently communicate with the remote branches of the
organization. The main focus for the security should be given on the resources and servers
installed in the central office of the organization and it should be secured from illegal access. The
documentation of the address plan is also important because it can be used as a reference for
configuring the interfaces of the hardware device used for connecting with the hosts located in
the branches. The traffic management is also necessary and the current network traffic should be
monitored by the network administrator for maintaining the security of the network and protect it
from different attacks.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

10
ITC542 - INTERNETWORKING WITH TCP/IP
Bibliography
Edwards, J., & Bramante, R. (2015). Networking self-teaching guide: OSI, TCP/IP, LANs,
MANs, WANs, implementation, management, and maintenance. John Wiley & Sons.
Ferdoush, S., & Li, X. (2014). Wireless sensor network system design using Raspberry Pi and
Arduino for environmental monitoring applications. Procedia Computer Science, 34,
103-110.
Goralski, W. (2017). The illustrated network: how TCP/IP works in a modern network. Morgan
Kaufmann.
Kori, P., & Rai, S. S. (2016). ANALYSIS OF NETWORK SECURITY THREATS AND
VULNERABILITIES BY DEVELOPMENT & IMPLEMENTATION OF A SECURITY
NETWORK MONITORING SOLUTION. International Journal of Engineering,
Management & Medical Research (IJEMMR), 2(8).
Mahapatra, N., Sahu, N., Nanda, S., Kaur, G., & Prahar, M. (2017). Unit-3 Networking
Concepts.
Oppitz, M., & Tomsu, P. (2018). Networks for Sharing and Connecting. In Inventing the Cloud
Century (pp. 97-129). Springer, Cham.
Ozhiganova, M., Kostyukov, A., & Maslova, M. (2017, May). Functional model of firewall
application layer protection for WEB-Based information systems. In Industrial
Engineering, Applications and Manufacturing (ICIEAM), 2017 International Conference
on (pp. 1-5). IEEE.
ITC542 - INTERNETWORKING WITH TCP/IP
Bibliography
Edwards, J., & Bramante, R. (2015). Networking self-teaching guide: OSI, TCP/IP, LANs,
MANs, WANs, implementation, management, and maintenance. John Wiley & Sons.
Ferdoush, S., & Li, X. (2014). Wireless sensor network system design using Raspberry Pi and
Arduino for environmental monitoring applications. Procedia Computer Science, 34,
103-110.
Goralski, W. (2017). The illustrated network: how TCP/IP works in a modern network. Morgan
Kaufmann.
Kori, P., & Rai, S. S. (2016). ANALYSIS OF NETWORK SECURITY THREATS AND
VULNERABILITIES BY DEVELOPMENT & IMPLEMENTATION OF A SECURITY
NETWORK MONITORING SOLUTION. International Journal of Engineering,
Management & Medical Research (IJEMMR), 2(8).
Mahapatra, N., Sahu, N., Nanda, S., Kaur, G., & Prahar, M. (2017). Unit-3 Networking
Concepts.
Oppitz, M., & Tomsu, P. (2018). Networks for Sharing and Connecting. In Inventing the Cloud
Century (pp. 97-129). Springer, Cham.
Ozhiganova, M., Kostyukov, A., & Maslova, M. (2017, May). Functional model of firewall
application layer protection for WEB-Based information systems. In Industrial
Engineering, Applications and Manufacturing (ICIEAM), 2017 International Conference
on (pp. 1-5). IEEE.
1 out of 11
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.


