Network Requirement Analysis and Plan for HiTech Telecommunications
VerifiedAdded on 2022/11/11
|14
|1457
|323
Homework Assignment
AI Summary
This assignment focuses on the network requirement analysis and plan for HiTech Telecommunications Company. It outlines the project scope, including incorporating organizational growth, dividing IP addresses for enhanced traffic capacity, ensuring network uptime, managing redundant links, and providing accurate data transfer. The project details both functional requirements, such as performance improvement, traffic management, and IP address allocation, and non-functional requirements, including surveys, feasibility studies, hardware requirements, and network topology identification. The network design strategy involves reviewing required services, usability, characteristics, and the deployment environment. It emphasizes error-free design through testing, security assessments, and user experience enhancement. The assignment includes network topology diagrams, switch configurations (VLAN, Trunking), router configurations (VLAN sub-interface, Access lists), and DHCP configurations. It provides guidelines for access point and server configurations, along with detailed network designs in Netsim and device configurations. References to relevant research papers are also included.

Running head: INTERNETWORKING TECHNOLOGIES
Assignment 2 - Network requirement analysis and plan
Name of the Student
Name of the University
Author’s Note
Assignment 2 - Network requirement analysis and plan
Name of the Student
Name of the University
Author’s Note
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1
INTERNETWORKING TECHNOLOGIES
Project Scope
The network design is provided for implementing network design for HiTech Telecommunications
Company. The project identifies the following scope for the project:
To incorporate growth of the organization into design of the network and adhering to
organizational structure for providing optimum design for the implementation of the
proposed network solution
Divide IP address into smaller module to enhance the traffic capacity of the network and
reliability of the network during high traffic flow over the network
to ensure that network bandwidth is not wasted while ensuring optimum performance of
the network
to design the proposed network in such a way that network uptime is high even during high
network traffic
to ensure proper management of the redundant links of the network to provide facility for
sending and receiving data with higher accuracy along with proper data transfer speed
to ensure that security of the network is proper through integration of proper security
measures with the network design
Project requirements
Functional Requirement
● Performance improvement through minimization of network jitters, data packet loss and
allocate network bandwidth accordingly
● Improving traffic management of the network
● Division of data packets and transfer data through allocation of various available
communication channels so that maximum bandwidth is allocated during data transfer for
making the data transfer faster and reliable
● Configure network in such a fashion so that new IP address is possible to allocate to the
existing network design
INTERNETWORKING TECHNOLOGIES
Project Scope
The network design is provided for implementing network design for HiTech Telecommunications
Company. The project identifies the following scope for the project:
To incorporate growth of the organization into design of the network and adhering to
organizational structure for providing optimum design for the implementation of the
proposed network solution
Divide IP address into smaller module to enhance the traffic capacity of the network and
reliability of the network during high traffic flow over the network
to ensure that network bandwidth is not wasted while ensuring optimum performance of
the network
to design the proposed network in such a way that network uptime is high even during high
network traffic
to ensure proper management of the redundant links of the network to provide facility for
sending and receiving data with higher accuracy along with proper data transfer speed
to ensure that security of the network is proper through integration of proper security
measures with the network design
Project requirements
Functional Requirement
● Performance improvement through minimization of network jitters, data packet loss and
allocate network bandwidth accordingly
● Improving traffic management of the network
● Division of data packets and transfer data through allocation of various available
communication channels so that maximum bandwidth is allocated during data transfer for
making the data transfer faster and reliable
● Configure network in such a fashion so that new IP address is possible to allocate to the
existing network design

2
INTERNETWORKING TECHNOLOGIES
● Create IP address plan and configure network in accordance with the IP plan
Non Functional Requirement
● To design and implement an in-depth survey involving employees and authorities of the
company for gathering requirements for the network design
● Prepare a feasibility study to review compatibility of the proposed network design and
identify any issues before the design is implemented
● Prepare a comprehensive hardware requirements for the network design and also prepare
an initial budget for the network design
● Prepare a detailed plan to install network devices and associated network equipment for
implanting the design for the organization
● Identification of network topology with reference to organizational structure and design
requirements
Network Design strategy
In order to design the network properly, various things such as required services, usability aspect of
the network, characteristics of the network design and environment for deploying the network and
network process need to review for designing the network. This will ensure that the design of the
network is consistent with organizational requirements. In order to ensure that the network design
is error free, testing of the network has to be done throughout the implementation of the network.
It will help in identifying any issue that might affect the performance of the network. Hence testing
process of network for identification of issues and resolve it is an important strategy for this network
design. It is not enough to ensure that the network performs better, security of the network is
something that requires detailed assessment hence it is important to review various network design
methods and then chose the appropriate solution that is consistent with the security applications of
the network. The designed network should not only met the design requirements and user
requirements, it should enhance the process too by offering enhanced user experience. In order to
do this, survey with the users of the network is conducted. The application of HiTech
Telecommunications is such that it requires to support high speed data transfer and for this network
uptime should be optimum for most of the time, especially when network traffic is high and during
INTERNETWORKING TECHNOLOGIES
● Create IP address plan and configure network in accordance with the IP plan
Non Functional Requirement
● To design and implement an in-depth survey involving employees and authorities of the
company for gathering requirements for the network design
● Prepare a feasibility study to review compatibility of the proposed network design and
identify any issues before the design is implemented
● Prepare a comprehensive hardware requirements for the network design and also prepare
an initial budget for the network design
● Prepare a detailed plan to install network devices and associated network equipment for
implanting the design for the organization
● Identification of network topology with reference to organizational structure and design
requirements
Network Design strategy
In order to design the network properly, various things such as required services, usability aspect of
the network, characteristics of the network design and environment for deploying the network and
network process need to review for designing the network. This will ensure that the design of the
network is consistent with organizational requirements. In order to ensure that the network design
is error free, testing of the network has to be done throughout the implementation of the network.
It will help in identifying any issue that might affect the performance of the network. Hence testing
process of network for identification of issues and resolve it is an important strategy for this network
design. It is not enough to ensure that the network performs better, security of the network is
something that requires detailed assessment hence it is important to review various network design
methods and then chose the appropriate solution that is consistent with the security applications of
the network. The designed network should not only met the design requirements and user
requirements, it should enhance the process too by offering enhanced user experience. In order to
do this, survey with the users of the network is conducted. The application of HiTech
Telecommunications is such that it requires to support high speed data transfer and for this network
uptime should be optimum for most of the time, especially when network traffic is high and during
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3
INTERNETWORKING TECHNOLOGIES
this time, the network should be stable and reliable as well as stability of network is important for
the business of the company. Hence proper bandwidth distribution is required in this context. When
traffic over the network is low the network should preserve most of the available network
bandwidth and this should be deployed during the high traffic network so that communication is not
affected. In order to secure the network devices and ensure security of the data stored in the sever
of the network, access control needs to be integrated with the network sever so that it is difficult to
access those data without proper authorization which has been a significant issue for the company.
This access control which offers better authorization and security control will be implemented for
each network device and sever for offering enhanced security of the network according to the
requirements of the organization. This strategy that is developed for designing the network will be
implemented for designing and deploying the proposed network solution will be followed in this
context.
Network Topology Diagram
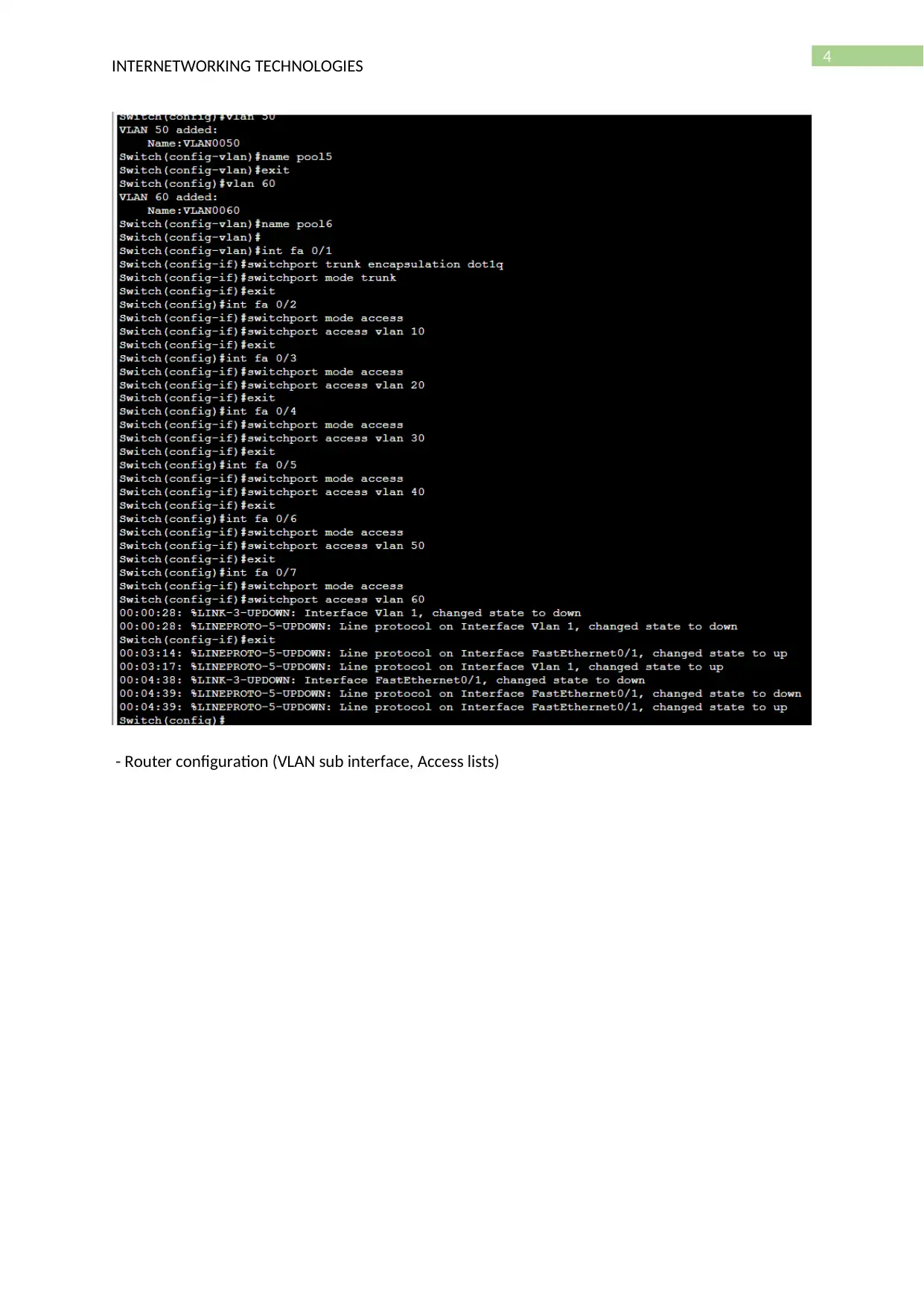
- Switch configuration (VLAN, Trunking)
INTERNETWORKING TECHNOLOGIES
this time, the network should be stable and reliable as well as stability of network is important for
the business of the company. Hence proper bandwidth distribution is required in this context. When
traffic over the network is low the network should preserve most of the available network
bandwidth and this should be deployed during the high traffic network so that communication is not
affected. In order to secure the network devices and ensure security of the data stored in the sever
of the network, access control needs to be integrated with the network sever so that it is difficult to
access those data without proper authorization which has been a significant issue for the company.
This access control which offers better authorization and security control will be implemented for
each network device and sever for offering enhanced security of the network according to the
requirements of the organization. This strategy that is developed for designing the network will be
implemented for designing and deploying the proposed network solution will be followed in this
context.
Network Topology Diagram
- Switch configuration (VLAN, Trunking)
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
4
INTERNETWORKING TECHNOLOGIES
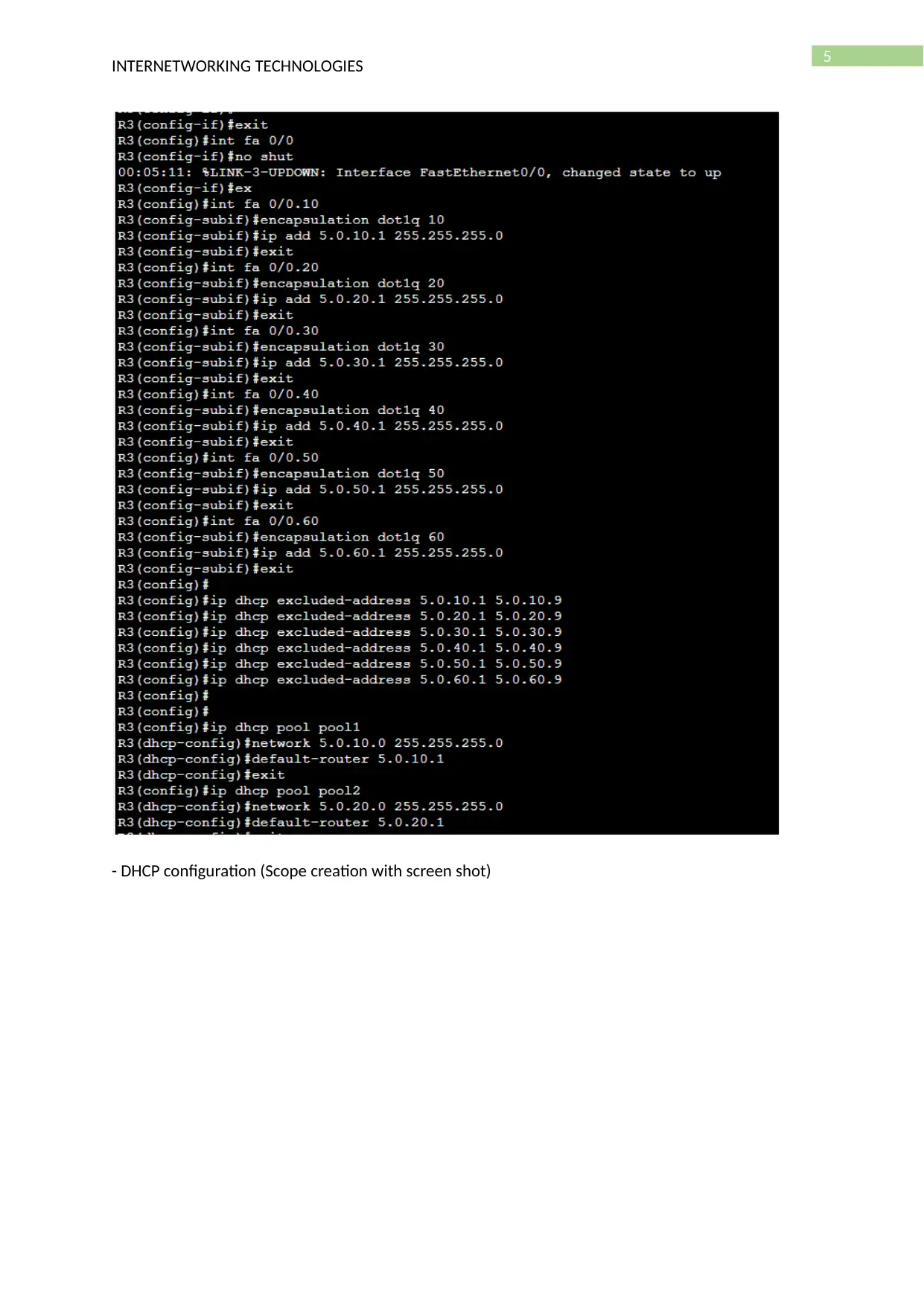
- Router configuration (VLAN sub interface, Access lists)
INTERNETWORKING TECHNOLOGIES
- Router configuration (VLAN sub interface, Access lists)
5
INTERNETWORKING TECHNOLOGIES
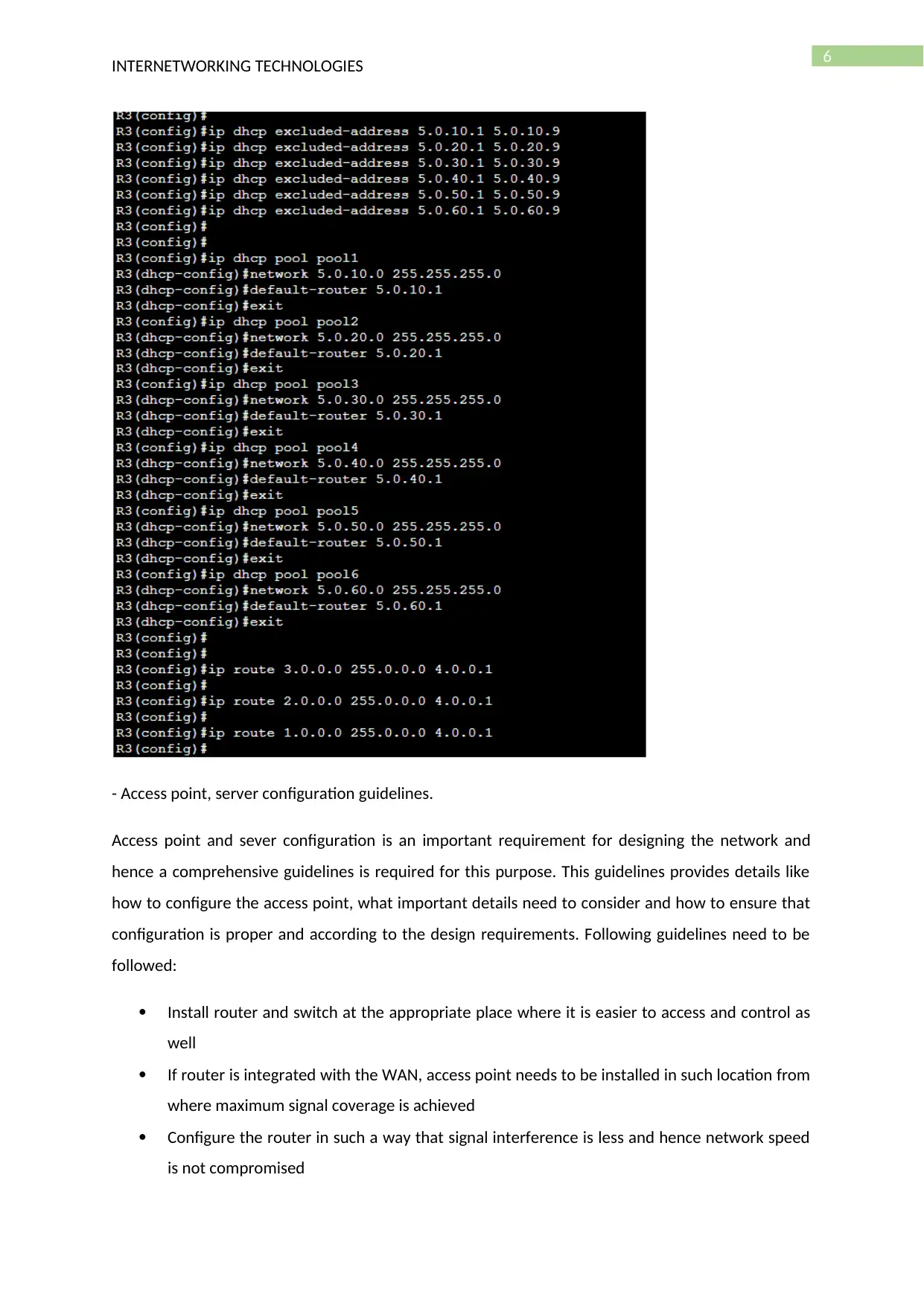
- DHCP configuration (Scope creation with screen shot)
INTERNETWORKING TECHNOLOGIES
- DHCP configuration (Scope creation with screen shot)
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
6
INTERNETWORKING TECHNOLOGIES
- Access point, server configuration guidelines.
Access point and sever configuration is an important requirement for designing the network and
hence a comprehensive guidelines is required for this purpose. This guidelines provides details like
how to configure the access point, what important details need to consider and how to ensure that
configuration is proper and according to the design requirements. Following guidelines need to be
followed:
Install router and switch at the appropriate place where it is easier to access and control as
well
If router is integrated with the WAN, access point needs to be installed in such location from
where maximum signal coverage is achieved
Configure the router in such a way that signal interference is less and hence network speed
is not compromised
INTERNETWORKING TECHNOLOGIES
- Access point, server configuration guidelines.
Access point and sever configuration is an important requirement for designing the network and
hence a comprehensive guidelines is required for this purpose. This guidelines provides details like
how to configure the access point, what important details need to consider and how to ensure that
configuration is proper and according to the design requirements. Following guidelines need to be
followed:
Install router and switch at the appropriate place where it is easier to access and control as
well
If router is integrated with the WAN, access point needs to be installed in such location from
where maximum signal coverage is achieved
Configure the router in such a way that signal interference is less and hence network speed
is not compromised
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
7
INTERNETWORKING TECHNOLOGIES
Ensure that the access point provides connection to all the wireless devices that are
integrated with the network
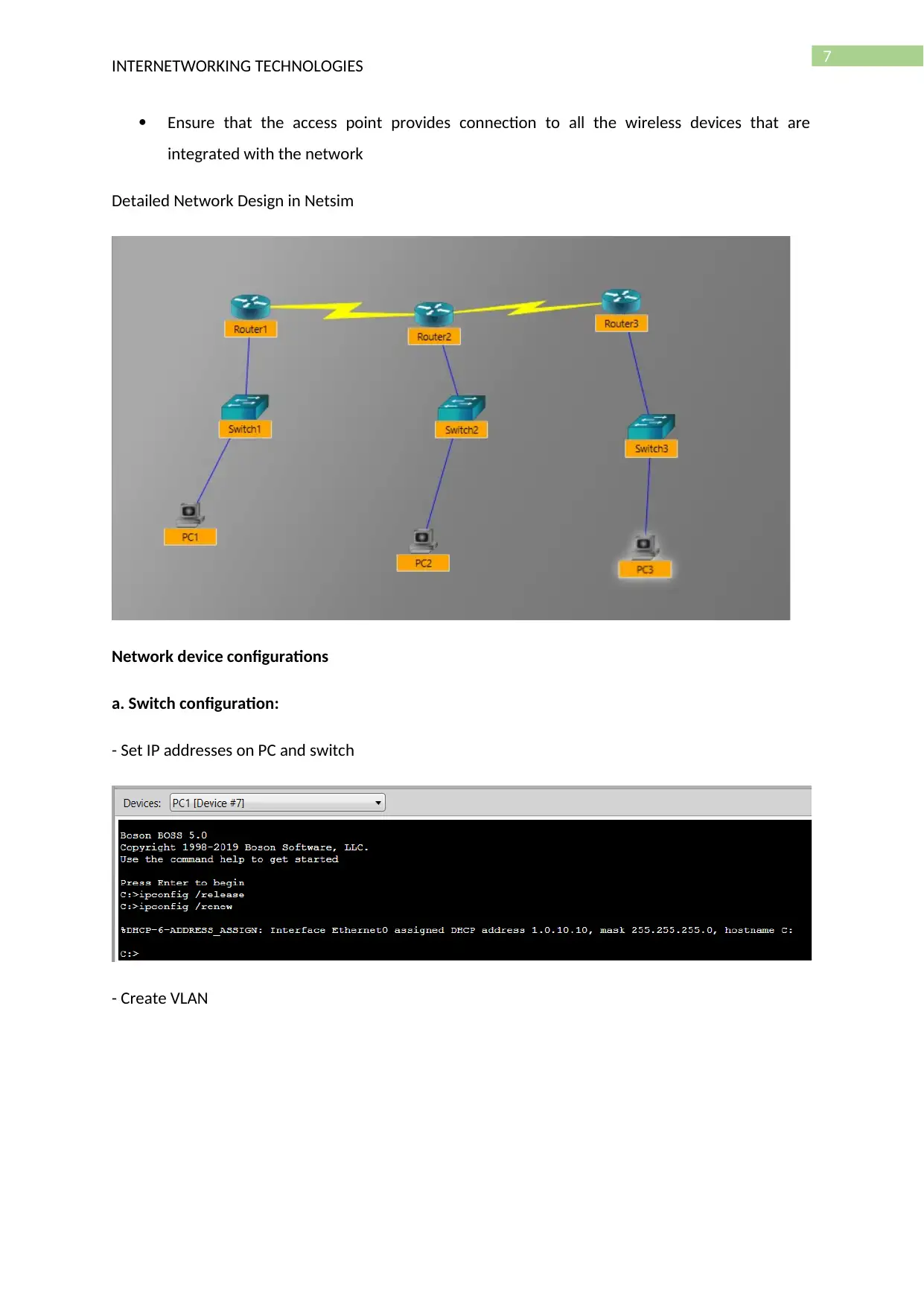
Detailed Network Design in Netsim
Network device configurations
a. Switch configuration:
- Set IP addresses on PC and switch
- Create VLAN
INTERNETWORKING TECHNOLOGIES
Ensure that the access point provides connection to all the wireless devices that are
integrated with the network
Detailed Network Design in Netsim
Network device configurations
a. Switch configuration:
- Set IP addresses on PC and switch
- Create VLAN
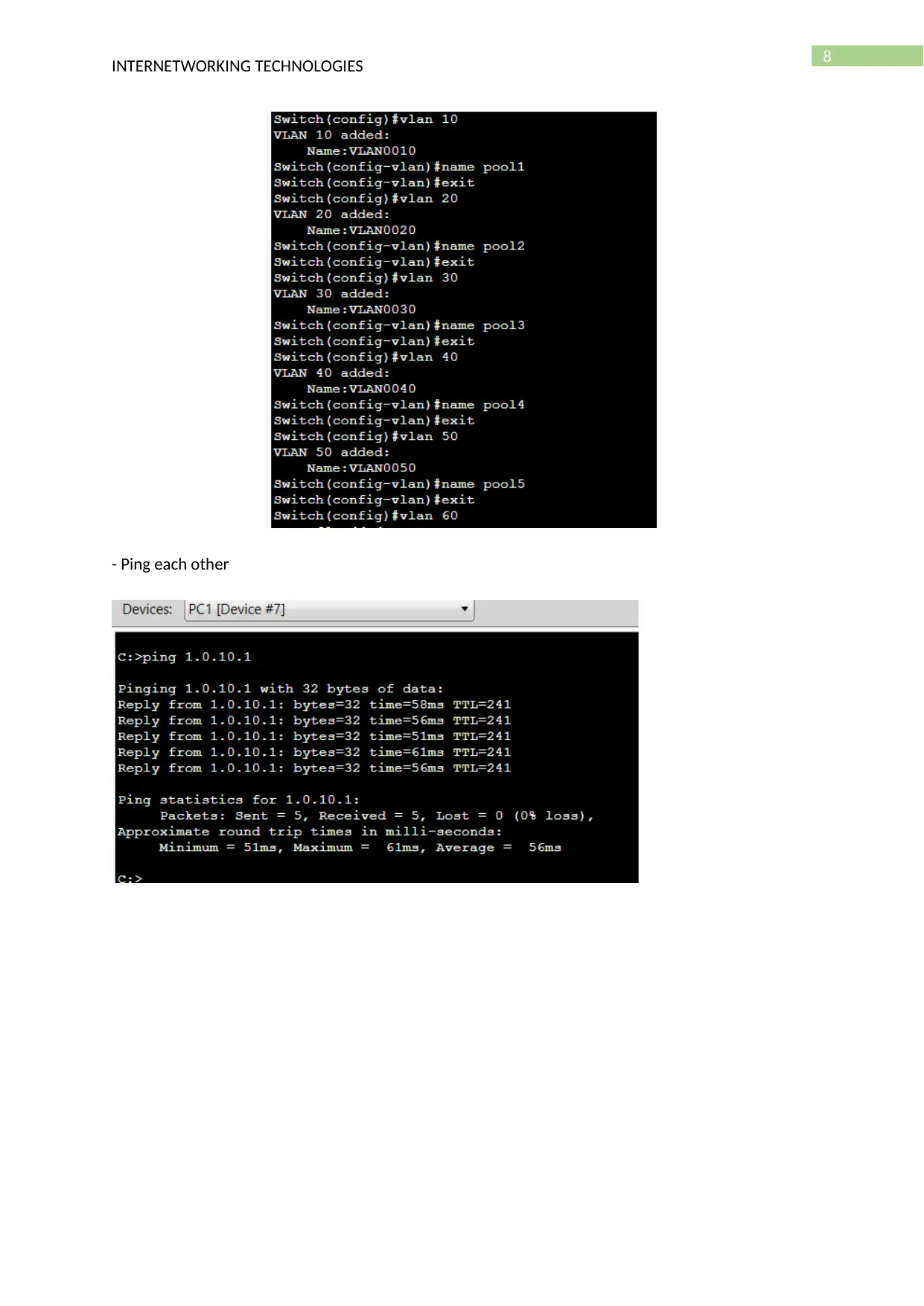
8
INTERNETWORKING TECHNOLOGIES
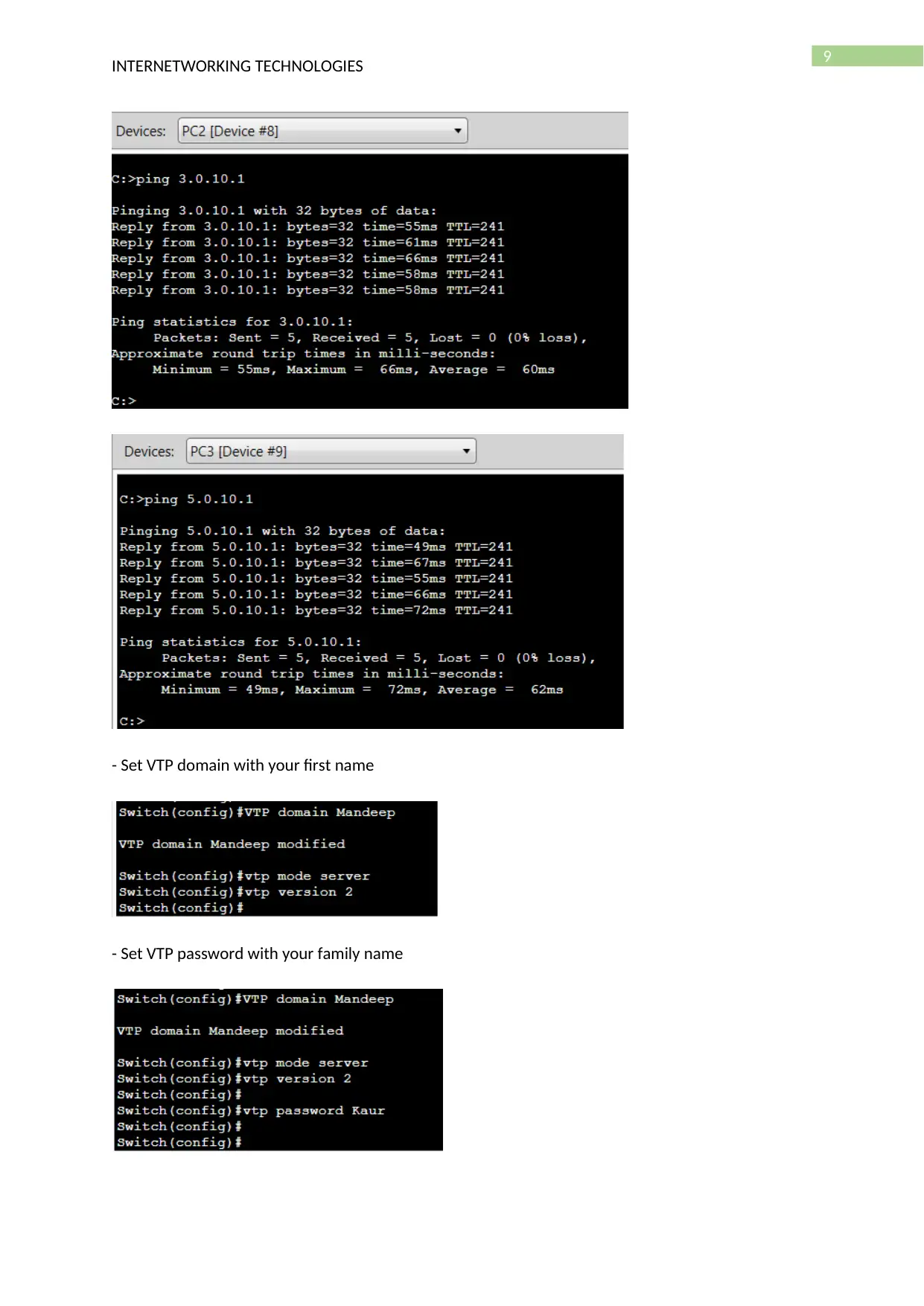
- Ping each other
INTERNETWORKING TECHNOLOGIES
- Ping each other
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
9
INTERNETWORKING TECHNOLOGIES
- Set VTP domain with your first name
- Set VTP password with your family name
INTERNETWORKING TECHNOLOGIES
- Set VTP domain with your first name
- Set VTP password with your family name
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
10
INTERNETWORKING TECHNOLOGIES
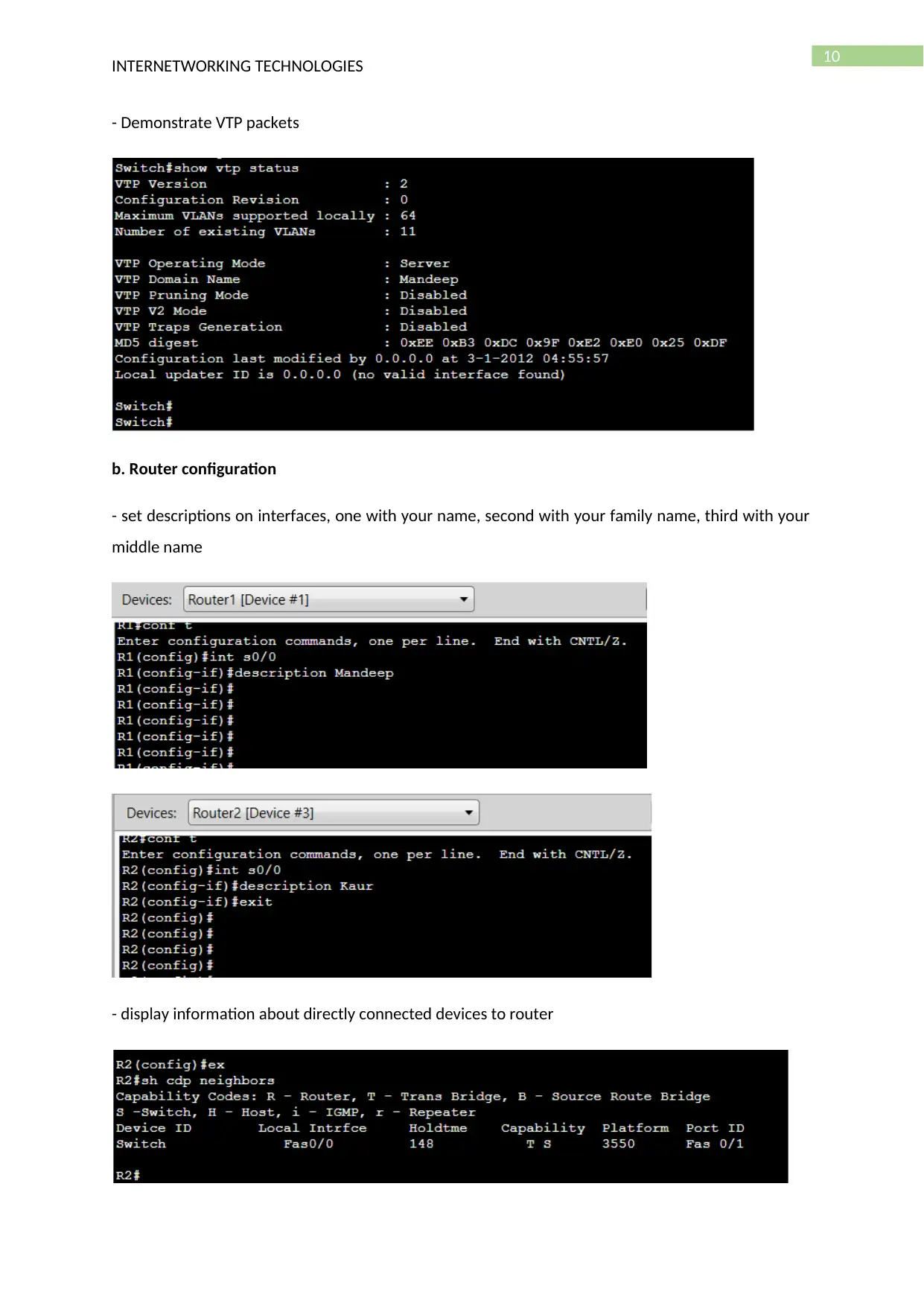
- Demonstrate VTP packets
b. Router configuration
- set descriptions on interfaces, one with your name, second with your family name, third with your
middle name
- display information about directly connected devices to router
INTERNETWORKING TECHNOLOGIES
- Demonstrate VTP packets
b. Router configuration
- set descriptions on interfaces, one with your name, second with your family name, third with your
middle name
- display information about directly connected devices to router
11
INTERNETWORKING TECHNOLOGIES
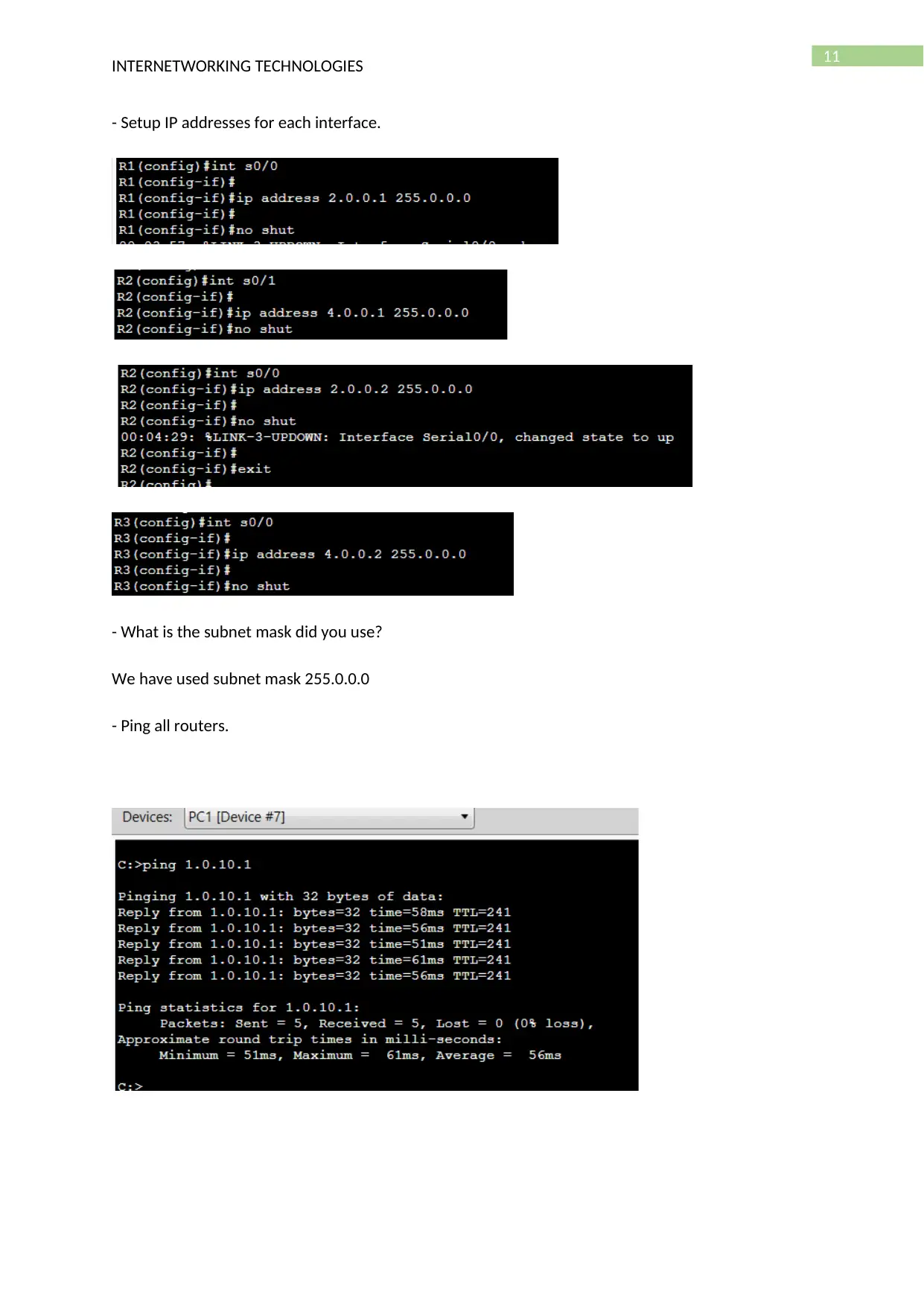
- Setup IP addresses for each interface.
- What is the subnet mask did you use?
We have used subnet mask 255.0.0.0
- Ping all routers.
INTERNETWORKING TECHNOLOGIES
- Setup IP addresses for each interface.
- What is the subnet mask did you use?
We have used subnet mask 255.0.0.0
- Ping all routers.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 14
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.




