A Novel Intrusion Detection System Based on PSO-FLN and KDD99
VerifiedAdded on 2022/09/26
|7
|6793
|26
Report
AI Summary
This paper introduces a novel intrusion detection system (IDS) named PSO-FLN, which combines a fast learning network (FLN) with particle swarm optimization (PSO). The system is designed to learn from examples and detect new attacks, leveraging the capabilities of artificial neural networks (ANNs) to reduce false positives and negatives. The model is evaluated using the KDD99 dataset and compared against various meta-heuristic algorithms for training extreme learning machines and FLN classifiers. The results demonstrate that PSO-FLN outperforms other learning approaches in terms of testing accuracy. The paper provides a comprehensive overview of the system, including its architecture, methodology, experimental setup, and performance evaluation. The study emphasizes the importance of feature construction and selection algorithms to improve the efficiency of the IDS and highlights the growing application of artificial intelligence in computer network security. The research also discusses the limitations of existing datasets and the need for more comprehensive data to train AI models effectively.

Received January 10, 2018, accepted March 18, 2018, date of publication March 27, 2018, date of current version April 25, 2018.
Digital Object Identifier 10.1109/ACCESS.2018.2820092
A New Intrusion Detection System Based
on Fast Learning Network and Particle
Swarm Optimization
MOHAMMED HASAN ALI 1, BAHAA ABBAS DAWOOD AL MOHAMMED2,
ALYANI ISMAIL2, (Member, IEEE), AND MOHAMAD FADLI ZOLKIPLI1
1Faculty of Computer Systems and Software Engineering, University Malaysia Pahang, Malaysia 26300
2Department of Computer and Communication Systems Engineering, Faculty of Engineering, Universiti Putra Malaysia, Malaysia 43400
Corresponding author: Mohammed Hasan Ali (mh180250@gmail.com)
ABSTRACTSupervised intrusion detection system is a system thathas the capability of learning from
examples about the previous attacks to detect new attacks.Using artificial neural network (ANN)-based
intrusion detection is promising for reducing the number of false negative or false positives, because ANN
has the capability of learning from actual examples. In this paper, a developed learning model for fast learn
network (FLN) based on particle swarm optimization (PSO) has been proposed and named as PSO-FLN.
The model has been applied to the problem of intrusion detection and validated based on the famous data
KDD99.Our developed model has been compared against a wide range of meta-heuristic algorithms for
training extreme learning machine and FLN classifier. PSO-FLN has outperformed other learning approache
in the testing accuracy of the learning.
INDEX TERMS Fast learning network,KDD Cup 99, intrusion detection system,particle swarm
optimization.
I. INTRODUCTION
In recent years, computer network security is a major concern
of computersociety due to the developmentof technolo-
gies and internet services at a rapid pace.Developments in
computer technology have enabled various new possibilities,
including the ability to remotely manage and control systems,
as well opening up a gateway to a multitude of information
through online sources.Organizational level cyber security
has consequently become a chief concern, Goodarzi et al. [1]
explored the problems faced by organizations in keeping their
information protected, available and reliable. This has created
the motivation for keeping systems secured from any external
system,program,or person aiming at breaking the security
line of the network.There are many tools and applications
developed to increase the security of the environments like
systems,networks and computers.Intrusion Detection Sys-
tem (IDS) is one of that tools that tries to protect the systems
from an intruder. IDS monitors the single machine or com-
puter network for intruder [2]. It is useful not only in detecting
successful intrusions, but also in monitoring attempts to break
security,which provides importantinformation fortimely
counter-measures [3].
The initial proposal to use intrusion detection in an att
to address misuses and networking attacks in computer
put forth by Denning [4] in 1987. The process is implem
by an intrusion detection system.Presently such systems
are widely available with variety [5],points outthe gen-
eral ineffectiveness and lack of sufficiency provided by t
present commercially available systems, this brings to li
the need for ongoing research on more dynamic intrusio
detection systems. In order to execute the process of int
detection,there is a need to identify ongoing or attempted
intrusions or attacks on the system or network, this iden
tion data include data collection, behavior classification,
reduction, and lastly reporting and response, this is refe
to, as ID [6].
The IDS attempted to determine whether monitored u
activity or network traffic is malicious. If a malicious atta
is detected,an alarm would be generated.Various differ-
ent techniquesare available forIDSs’ to distinguish an
attack,such as anomaly detection or signatures of attack
Green etal. [7] also pointout thatthe successof IDS
depends upon these techniques.One amongst the principal
factors governing the efficacy of the IDS is the quality of
VOLUME 6, 2018
2169-3536 2018 IEEE. Translations and content mining are permitted for academic research only.
Personal use is also permitted, but republication/redistribution requires IEEE permission.
See http://www.ieee.org/publications_standards/publications/rights/index.html for more information.
20255
Digital Object Identifier 10.1109/ACCESS.2018.2820092
A New Intrusion Detection System Based
on Fast Learning Network and Particle
Swarm Optimization
MOHAMMED HASAN ALI 1, BAHAA ABBAS DAWOOD AL MOHAMMED2,
ALYANI ISMAIL2, (Member, IEEE), AND MOHAMAD FADLI ZOLKIPLI1
1Faculty of Computer Systems and Software Engineering, University Malaysia Pahang, Malaysia 26300
2Department of Computer and Communication Systems Engineering, Faculty of Engineering, Universiti Putra Malaysia, Malaysia 43400
Corresponding author: Mohammed Hasan Ali (mh180250@gmail.com)
ABSTRACTSupervised intrusion detection system is a system thathas the capability of learning from
examples about the previous attacks to detect new attacks.Using artificial neural network (ANN)-based
intrusion detection is promising for reducing the number of false negative or false positives, because ANN
has the capability of learning from actual examples. In this paper, a developed learning model for fast learn
network (FLN) based on particle swarm optimization (PSO) has been proposed and named as PSO-FLN.
The model has been applied to the problem of intrusion detection and validated based on the famous data
KDD99.Our developed model has been compared against a wide range of meta-heuristic algorithms for
training extreme learning machine and FLN classifier. PSO-FLN has outperformed other learning approache
in the testing accuracy of the learning.
INDEX TERMS Fast learning network,KDD Cup 99, intrusion detection system,particle swarm
optimization.
I. INTRODUCTION
In recent years, computer network security is a major concern
of computersociety due to the developmentof technolo-
gies and internet services at a rapid pace.Developments in
computer technology have enabled various new possibilities,
including the ability to remotely manage and control systems,
as well opening up a gateway to a multitude of information
through online sources.Organizational level cyber security
has consequently become a chief concern, Goodarzi et al. [1]
explored the problems faced by organizations in keeping their
information protected, available and reliable. This has created
the motivation for keeping systems secured from any external
system,program,or person aiming at breaking the security
line of the network.There are many tools and applications
developed to increase the security of the environments like
systems,networks and computers.Intrusion Detection Sys-
tem (IDS) is one of that tools that tries to protect the systems
from an intruder. IDS monitors the single machine or com-
puter network for intruder [2]. It is useful not only in detecting
successful intrusions, but also in monitoring attempts to break
security,which provides importantinformation fortimely
counter-measures [3].
The initial proposal to use intrusion detection in an att
to address misuses and networking attacks in computer
put forth by Denning [4] in 1987. The process is implem
by an intrusion detection system.Presently such systems
are widely available with variety [5],points outthe gen-
eral ineffectiveness and lack of sufficiency provided by t
present commercially available systems, this brings to li
the need for ongoing research on more dynamic intrusio
detection systems. In order to execute the process of int
detection,there is a need to identify ongoing or attempted
intrusions or attacks on the system or network, this iden
tion data include data collection, behavior classification,
reduction, and lastly reporting and response, this is refe
to, as ID [6].
The IDS attempted to determine whether monitored u
activity or network traffic is malicious. If a malicious atta
is detected,an alarm would be generated.Various differ-
ent techniquesare available forIDSs’ to distinguish an
attack,such as anomaly detection or signatures of attack
Green etal. [7] also pointout thatthe successof IDS
depends upon these techniques.One amongst the principal
factors governing the efficacy of the IDS is the quality of
VOLUME 6, 2018
2169-3536 2018 IEEE. Translations and content mining are permitted for academic research only.
Personal use is also permitted, but republication/redistribution requires IEEE permission.
See http://www.ieee.org/publications_standards/publications/rights/index.html for more information.
20255
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

M. H. Ali et al.:New Intrusion Detection System Based on FLN and PSO
feature construction and feature selection algorithm. In order
to improve the overallefficiency of the IDS,a drop in the
number of applicable traffic features without incurring any
adverse effects on classification accuracy is required.
In recenttimes,we have seen an exponentially great
increase in the employmentof ArtificialIntelligence (AI)
in a tremendously large and vastnumberof fields,such
as;computer vision,robotics,control,communication and
variousengineering fields.AI combined ofseveralsub
fields such as neural network, evolutionary searching, expert
systems,fuzzy systems,etc.Although a lotof researchers
prefer AI models with interpretability aspects such as heuris-
tically knowledge building based modelslike fuzzy sys-
tems, artificial neural networks ANN, which had no explicit
interpretability aspectis considered as more effective AI
models when learning scheme is feasible.This is due to
the power of capturing knowledge through examples pro-
vided to such models.This has created a strong motiva-
tion to researchers for building supervised learning models
to predictintrusion attacks based on collected data setof
examples of various attacks. There exists a very large num-
ber of methods,mostof which have been used for differ-
entintrusion-detection models to perform a diverse setof
importanttasks,some of these methods include;Machine
learning based,Hybrid ANN based and/or integrated tech-
niques.Additionally,as presented by Kiranyaz etal. [8],
there are hybrid data mining schemes,hierarchicalhybrid
intelligent system models, and ensemble learning approaches
all of which have gained popularity in the works reviewed.
The remainderof the presentwork is arranged as such;
we startin section 2 with related work.Section 3 talk
aboutthe data setKDD. Section 4 formulation problem.
Section 5 developed methodology.Section 6 resultsand
discussion.The conclusion and summary in this work in
section 7.
II. RELATED WORK
ArtificialNeuralNetworks(ANNs), from inputpatterns,
it can be approximate complex nonlinear mappings directly,
and hasbeen used in alot of applicationswith great
success [7]. Artificial Neural Networks (ANNs), given their
ability to approximate complex nonlinear mappings directly
from input patterns, have been frequently used in a variety of
applications with great success [9]. Based on gradient descent
algorithms training samples would be used to define the free
parameters of ANNs. Moreover, this reason for brings some
issues related to its localminima and the learning process
relatively became slow. Owing to these shortages, also train
ANNs could take much more time and have a suboptimal
solution [8]. For solving the above problems, it has been a hot
topic to reduce the computing iterations and simultaneously
decrease the training time [9]–[11]
In order to addressthe aforementionedproblems,
Huang et al.[12] propose the use of a new artificial neural
network,known as an Extreme Learning Machine (ELM).
ELM is defined as new learning approach for Single Hidden
Layer Feedforward Neural Network (SLFN), where random
value generation is used for the input weights and the b
hidden nodes without tuning, and where the output weig
are determined analytically.
Extreme learning machine as explored by (Huang etal.,
2004),avoidsseveraldisadvantagesof gradientdescent-
based learning algorithm for SLFNs. Research on the app
imation abilities of Feed-Forward Neural Networks (FFNN
focuses on two primary features:universalapproximation
on compactinputsets and approximation in a finite setof
training samples [12].Some generaladvantages ofELM
algorithms are; simple and robust implementation, tend
to converge with the shortest training error, and smalles
of weights, and generally good performance, with extrem
fastrunning.These amongstother help differentiate ELM
from the other SLFN algorithms.
The ELM algorithm is based on three steps training; fir
assigning random weights in the input-hidden layer, sec
calculating the output hidden layer matrix,and thirdly,cal-
culating the outputlayer weights based on Moore-Penrose
equation [11].Based on the idea ofELM, Li et al. [13]
proposed a novel Fast Learning Network (FLN). The FLN
a Double Parallel Forward Neural Network (DPFNN) [14],
which is essentially a parallelconnection ofa multilayer
FFNN, and an SLFN. The re-coded external information f
the hidden nodes, along with the external information it
directly from the input nodes is fed into the output node
the DFNN’s.Inputweights as wellas hidden layer biases
are generated in a random manner for FLN’s, but where
analytical approach, based on a least squares method is
to determine the weights of values for the connection be
the output layer and the input layer and the weights of v
for connecting the output node and the input. If a compa
is made between relating methods FLN, is capable of rea
ing a good general high speed performance, with impres
stability in mostscenarios,whilstrunning with a smaller
number of hidden units.
In orderto build an effective and reliable ANN based
intrusion-detection system,there isa high need to pro-
vide comprehensive data setfor teaching the ANN model.
Although several data sets exist within the literature for
a knowledge building,there is a significantchallenge that
needs to be addressed in this respect. More specifically,
of the dataset do not provide enough examples for teac
the models in an explicitway due to the less frequency of
some attacks.This has caused a concern on how to rely
on the available small examples of data of attacks in ord
to build generalizable knowledge forAI models to use it
in detecting similar non-stored attacks. An example for o
common dataset used for training models on intrusion a
is KDD99.
Although ELM approach of training for both SLFN and
FLN is quite easy and provides non-iterated learning for
model it has one important limitation. Actually, it is havi
an infinite number of degree of freedom to reach a class
fication result. In other words, there is no one determinis
20256 VOLUME 6, 2018
feature construction and feature selection algorithm. In order
to improve the overallefficiency of the IDS,a drop in the
number of applicable traffic features without incurring any
adverse effects on classification accuracy is required.
In recenttimes,we have seen an exponentially great
increase in the employmentof ArtificialIntelligence (AI)
in a tremendously large and vastnumberof fields,such
as;computer vision,robotics,control,communication and
variousengineering fields.AI combined ofseveralsub
fields such as neural network, evolutionary searching, expert
systems,fuzzy systems,etc.Although a lotof researchers
prefer AI models with interpretability aspects such as heuris-
tically knowledge building based modelslike fuzzy sys-
tems, artificial neural networks ANN, which had no explicit
interpretability aspectis considered as more effective AI
models when learning scheme is feasible.This is due to
the power of capturing knowledge through examples pro-
vided to such models.This has created a strong motiva-
tion to researchers for building supervised learning models
to predictintrusion attacks based on collected data setof
examples of various attacks. There exists a very large num-
ber of methods,mostof which have been used for differ-
entintrusion-detection models to perform a diverse setof
importanttasks,some of these methods include;Machine
learning based,Hybrid ANN based and/or integrated tech-
niques.Additionally,as presented by Kiranyaz etal. [8],
there are hybrid data mining schemes,hierarchicalhybrid
intelligent system models, and ensemble learning approaches
all of which have gained popularity in the works reviewed.
The remainderof the presentwork is arranged as such;
we startin section 2 with related work.Section 3 talk
aboutthe data setKDD. Section 4 formulation problem.
Section 5 developed methodology.Section 6 resultsand
discussion.The conclusion and summary in this work in
section 7.
II. RELATED WORK
ArtificialNeuralNetworks(ANNs), from inputpatterns,
it can be approximate complex nonlinear mappings directly,
and hasbeen used in alot of applicationswith great
success [7]. Artificial Neural Networks (ANNs), given their
ability to approximate complex nonlinear mappings directly
from input patterns, have been frequently used in a variety of
applications with great success [9]. Based on gradient descent
algorithms training samples would be used to define the free
parameters of ANNs. Moreover, this reason for brings some
issues related to its localminima and the learning process
relatively became slow. Owing to these shortages, also train
ANNs could take much more time and have a suboptimal
solution [8]. For solving the above problems, it has been a hot
topic to reduce the computing iterations and simultaneously
decrease the training time [9]–[11]
In order to addressthe aforementionedproblems,
Huang et al.[12] propose the use of a new artificial neural
network,known as an Extreme Learning Machine (ELM).
ELM is defined as new learning approach for Single Hidden
Layer Feedforward Neural Network (SLFN), where random
value generation is used for the input weights and the b
hidden nodes without tuning, and where the output weig
are determined analytically.
Extreme learning machine as explored by (Huang etal.,
2004),avoidsseveraldisadvantagesof gradientdescent-
based learning algorithm for SLFNs. Research on the app
imation abilities of Feed-Forward Neural Networks (FFNN
focuses on two primary features:universalapproximation
on compactinputsets and approximation in a finite setof
training samples [12].Some generaladvantages ofELM
algorithms are; simple and robust implementation, tend
to converge with the shortest training error, and smalles
of weights, and generally good performance, with extrem
fastrunning.These amongstother help differentiate ELM
from the other SLFN algorithms.
The ELM algorithm is based on three steps training; fir
assigning random weights in the input-hidden layer, sec
calculating the output hidden layer matrix,and thirdly,cal-
culating the outputlayer weights based on Moore-Penrose
equation [11].Based on the idea ofELM, Li et al. [13]
proposed a novel Fast Learning Network (FLN). The FLN
a Double Parallel Forward Neural Network (DPFNN) [14],
which is essentially a parallelconnection ofa multilayer
FFNN, and an SLFN. The re-coded external information f
the hidden nodes, along with the external information it
directly from the input nodes is fed into the output node
the DFNN’s.Inputweights as wellas hidden layer biases
are generated in a random manner for FLN’s, but where
analytical approach, based on a least squares method is
to determine the weights of values for the connection be
the output layer and the input layer and the weights of v
for connecting the output node and the input. If a compa
is made between relating methods FLN, is capable of rea
ing a good general high speed performance, with impres
stability in mostscenarios,whilstrunning with a smaller
number of hidden units.
In orderto build an effective and reliable ANN based
intrusion-detection system,there isa high need to pro-
vide comprehensive data setfor teaching the ANN model.
Although several data sets exist within the literature for
a knowledge building,there is a significantchallenge that
needs to be addressed in this respect. More specifically,
of the dataset do not provide enough examples for teac
the models in an explicitway due to the less frequency of
some attacks.This has caused a concern on how to rely
on the available small examples of data of attacks in ord
to build generalizable knowledge forAI models to use it
in detecting similar non-stored attacks. An example for o
common dataset used for training models on intrusion a
is KDD99.
Although ELM approach of training for both SLFN and
FLN is quite easy and provides non-iterated learning for
model it has one important limitation. Actually, it is havi
an infinite number of degree of freedom to reach a class
fication result. In other words, there is no one determinis
20256 VOLUME 6, 2018

M. H. Ali et al.:New Intrusion Detection System Based on FLN and PSO
solution to train an SLFN network with basic ELM training.
Assuming that the possible weights of the input-hidden layer
connections are potential solution for training ELM, there are
certain values of set of solutions with more superiority if the
goal is to obtain best knowledge extraction from the data set.
We call the process of finding those solutions based upon an
extension of ELM a developed ELM. Our goal is to design a
learning mechanism based on two factors: the nature of the
data set,and the nature of the evaluation measures that are
aimed to be used for evaluating the learning mechanism or
algorithm.
III. DATA SET KDD99
ANN based intrusion detection has to be trained on selected
Dataset.In orderto demonstrate the effectiveness ofour
model, we choose the highest dataset in terms of citation to
the literature of intrusion KD99. Furthermore, we present the
different issue that is addressed in the literature.
A. OVERVIEW OF KD99
KDD Cup 99 is considered the most accepted research dataset
highly appropriate to benchmark performance [17], also notes
its use in comparing the effectiveness of various approaches
to Network Intrusion. KDD CUP 99 is built based on the data
captured in DARPA’98 IDS program [18].DARPA’98 con-
tains approximately 4GB of compressed raw (binary) tcp-
dump data.This contains roughly 7 weeks ofmonitored
network traffic. This data can consequently, be managed into
about 5 million linking records, each about 100 bytes. KDD
training data set consists of approximately 4,900,000 single
connection vectors each of which contains 41 features and
is labeled as either normal or an attack, [19], the attacks can
thereafter be categorized into exactly one of four, as detailed
below;
Denial Service of Attack (DoS): DOS is an attack which
essentially involves the resources are too busy to handle other
requests or the attacker making use of specific resources to an
extent that denied access for legitimate users.
User to Root Attack (U2R): It is a form of security exploita-
tion, whereby the attacker would gain access to a normal user
account, through conventional means, and thereafter proceed
to attempt root access to the system through the exploitation
of a vulnerability.
Remoteto Local Attack (R2L): this is when an
attackerattemptsaccessto a system overa network.
The attacker can only transmitdata packets over the net-
work,the attacker attempts to gain access to the machine,
by exploiting some vulnerability.
Probing Attack (Prob): It is when an attacker attempts to
acquire information from a network, for evading the systems,
security protocols.
Since 1999,a large number of researchers assessed their
IDS models using KDD Cup 99.This shows how KDD
Cup 99 has been a working benchmark data setfor over
15 years,and is stilleasily accessible and available today.
The objective of the KDD 99 IDS competition is to create a
standard data set for the surveying and evaluation of re
in intrusion detection, [15]. Researchers found some diffi
ties or hurdles in training with KDD99,Olusola et al.[16]
have analyzed the KDD 99 data set for selecting a releva
feature. They proposed that some features or attributes
notrelated to any attack,[17] they have taken 10% of the
whole data set to perform their analysis.
IV. FORMULATING THE PROBLEM
Intrusion detection based on ANN is built by using gathe
features aboutseveraltypes ofattacks.Usually,building
knowledge based on gathered data required sufficient a
of data with comprehensive nature.Unfortunately,in the
application of intrusion detection, it is not feasible to cre
sufficient knowledge for learning or at least balanced lea
between the different classes (refer to the problem desc
in KDD99 in the previous section). Therefore, learning al
rithm has to be carefully optimized according to the nat
the dataset. This leads us to investigate about how to id
the optimization parameters of the learning algorithm. I
work,the problem willbe formulated as an optimization
problem.More specifically,the problem is how to find the
optimalvalues of the hidden layer neurons in both SLFN,
and FLN in order to maintain highestaccuracy of testing.
Such problem is addressed in the literature as a heuristi
searching in the space of solutions considering the aim i
to minimize an objective function represents the accura
of the classification ofattacks.Mathematically,assuming
thatthe accuracy of the testing is the function f (x),where
x = (x1, x2, . . . xn) denotes the random selected different
weights of hidden layer network.Our problem is presented
in equation (1)
x∗ = argmax f
s.t.(x1, x2, . . . xn) ∈ [−1, 1]n (1)
V. DEVELOPED METHODOLOGY
This section presents the developed methodology forthis
research.Firstly,particle swarm optimization is PSO pre-
sented in section.Secondly,particle FastLearning Net-
work (FLN) presented in section.Thirdly,our adaption of
PSO to build FLN based training for IDS is presented in
section.
A. PARTICLE SWARM OPTIMIZATION
Particle Swarm Optimization (PSO)is a parallelevolu-
tionary computation technique developed by Mishra and
Sengupta [23]. The protocol has been developed based
social behavior metaphor. The PSO algorithm’s performa
is greatly influenced by the included tuning parameters,
referred to as the exploration– exploitation tradeoff: whe
exploration describes the ability to assess various region
the problem space to an attempt to pinpoint a good opt
preferably the global one. Exploitation describes the abi
to focus the search within near vicinity of a promising ca
date solution, to effectively and quickly locate the optim
VOLUME 6, 2018 20257
solution to train an SLFN network with basic ELM training.
Assuming that the possible weights of the input-hidden layer
connections are potential solution for training ELM, there are
certain values of set of solutions with more superiority if the
goal is to obtain best knowledge extraction from the data set.
We call the process of finding those solutions based upon an
extension of ELM a developed ELM. Our goal is to design a
learning mechanism based on two factors: the nature of the
data set,and the nature of the evaluation measures that are
aimed to be used for evaluating the learning mechanism or
algorithm.
III. DATA SET KDD99
ANN based intrusion detection has to be trained on selected
Dataset.In orderto demonstrate the effectiveness ofour
model, we choose the highest dataset in terms of citation to
the literature of intrusion KD99. Furthermore, we present the
different issue that is addressed in the literature.
A. OVERVIEW OF KD99
KDD Cup 99 is considered the most accepted research dataset
highly appropriate to benchmark performance [17], also notes
its use in comparing the effectiveness of various approaches
to Network Intrusion. KDD CUP 99 is built based on the data
captured in DARPA’98 IDS program [18].DARPA’98 con-
tains approximately 4GB of compressed raw (binary) tcp-
dump data.This contains roughly 7 weeks ofmonitored
network traffic. This data can consequently, be managed into
about 5 million linking records, each about 100 bytes. KDD
training data set consists of approximately 4,900,000 single
connection vectors each of which contains 41 features and
is labeled as either normal or an attack, [19], the attacks can
thereafter be categorized into exactly one of four, as detailed
below;
Denial Service of Attack (DoS): DOS is an attack which
essentially involves the resources are too busy to handle other
requests or the attacker making use of specific resources to an
extent that denied access for legitimate users.
User to Root Attack (U2R): It is a form of security exploita-
tion, whereby the attacker would gain access to a normal user
account, through conventional means, and thereafter proceed
to attempt root access to the system through the exploitation
of a vulnerability.
Remoteto Local Attack (R2L): this is when an
attackerattemptsaccessto a system overa network.
The attacker can only transmitdata packets over the net-
work,the attacker attempts to gain access to the machine,
by exploiting some vulnerability.
Probing Attack (Prob): It is when an attacker attempts to
acquire information from a network, for evading the systems,
security protocols.
Since 1999,a large number of researchers assessed their
IDS models using KDD Cup 99.This shows how KDD
Cup 99 has been a working benchmark data setfor over
15 years,and is stilleasily accessible and available today.
The objective of the KDD 99 IDS competition is to create a
standard data set for the surveying and evaluation of re
in intrusion detection, [15]. Researchers found some diffi
ties or hurdles in training with KDD99,Olusola et al.[16]
have analyzed the KDD 99 data set for selecting a releva
feature. They proposed that some features or attributes
notrelated to any attack,[17] they have taken 10% of the
whole data set to perform their analysis.
IV. FORMULATING THE PROBLEM
Intrusion detection based on ANN is built by using gathe
features aboutseveraltypes ofattacks.Usually,building
knowledge based on gathered data required sufficient a
of data with comprehensive nature.Unfortunately,in the
application of intrusion detection, it is not feasible to cre
sufficient knowledge for learning or at least balanced lea
between the different classes (refer to the problem desc
in KDD99 in the previous section). Therefore, learning al
rithm has to be carefully optimized according to the nat
the dataset. This leads us to investigate about how to id
the optimization parameters of the learning algorithm. I
work,the problem willbe formulated as an optimization
problem.More specifically,the problem is how to find the
optimalvalues of the hidden layer neurons in both SLFN,
and FLN in order to maintain highestaccuracy of testing.
Such problem is addressed in the literature as a heuristi
searching in the space of solutions considering the aim i
to minimize an objective function represents the accura
of the classification ofattacks.Mathematically,assuming
thatthe accuracy of the testing is the function f (x),where
x = (x1, x2, . . . xn) denotes the random selected different
weights of hidden layer network.Our problem is presented
in equation (1)
x∗ = argmax f
s.t.(x1, x2, . . . xn) ∈ [−1, 1]n (1)
V. DEVELOPED METHODOLOGY
This section presents the developed methodology forthis
research.Firstly,particle swarm optimization is PSO pre-
sented in section.Secondly,particle FastLearning Net-
work (FLN) presented in section.Thirdly,our adaption of
PSO to build FLN based training for IDS is presented in
section.
A. PARTICLE SWARM OPTIMIZATION
Particle Swarm Optimization (PSO)is a parallelevolu-
tionary computation technique developed by Mishra and
Sengupta [23]. The protocol has been developed based
social behavior metaphor. The PSO algorithm’s performa
is greatly influenced by the included tuning parameters,
referred to as the exploration– exploitation tradeoff: whe
exploration describes the ability to assess various region
the problem space to an attempt to pinpoint a good opt
preferably the global one. Exploitation describes the abi
to focus the search within near vicinity of a promising ca
date solution, to effectively and quickly locate the optim
VOLUME 6, 2018 20257
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
M. H. Ali et al.:New Intrusion Detection System Based on FLN and PSO
Despite recent research efforts, the selection of the algorithm
parameters remains empirical to a large extent [18].
The objective function ofPSO algorithm used to eval-
uate its solutions,and operates upon the resultantfitness
values.
Each particlesavesits position,composedof the
candidatesolution and its evaluatesfitness,and its
velocity [19].PSO algorithm has been used in many appli-
cations to solve many problems [20]–[24].
The modifications of the position and velocity are a pro-
cess for seeking optimal solution at each iteration using as
following:
vi(k + 1) = wvik + c1r1(xbest, local − xi)
+c2r2(xbest, global − xi) (2)
xi(k + 1) = xk + v(k + 1) (3)
The velocity and position of each particle are represented
as the vectors vk = (vk1, . . . , vkd) and xi = (xi1, . . . , xid)
respectively. In (2) x vectors are representing the best local
and best global positions. c1 and c2 are acceleration factors
known as cognitive and socialparameters.r1 and r2 are
random number between 0 and 1. k is the iteration index. w is
the inertia weight parameter [25]. And update xi for particle
using (3).
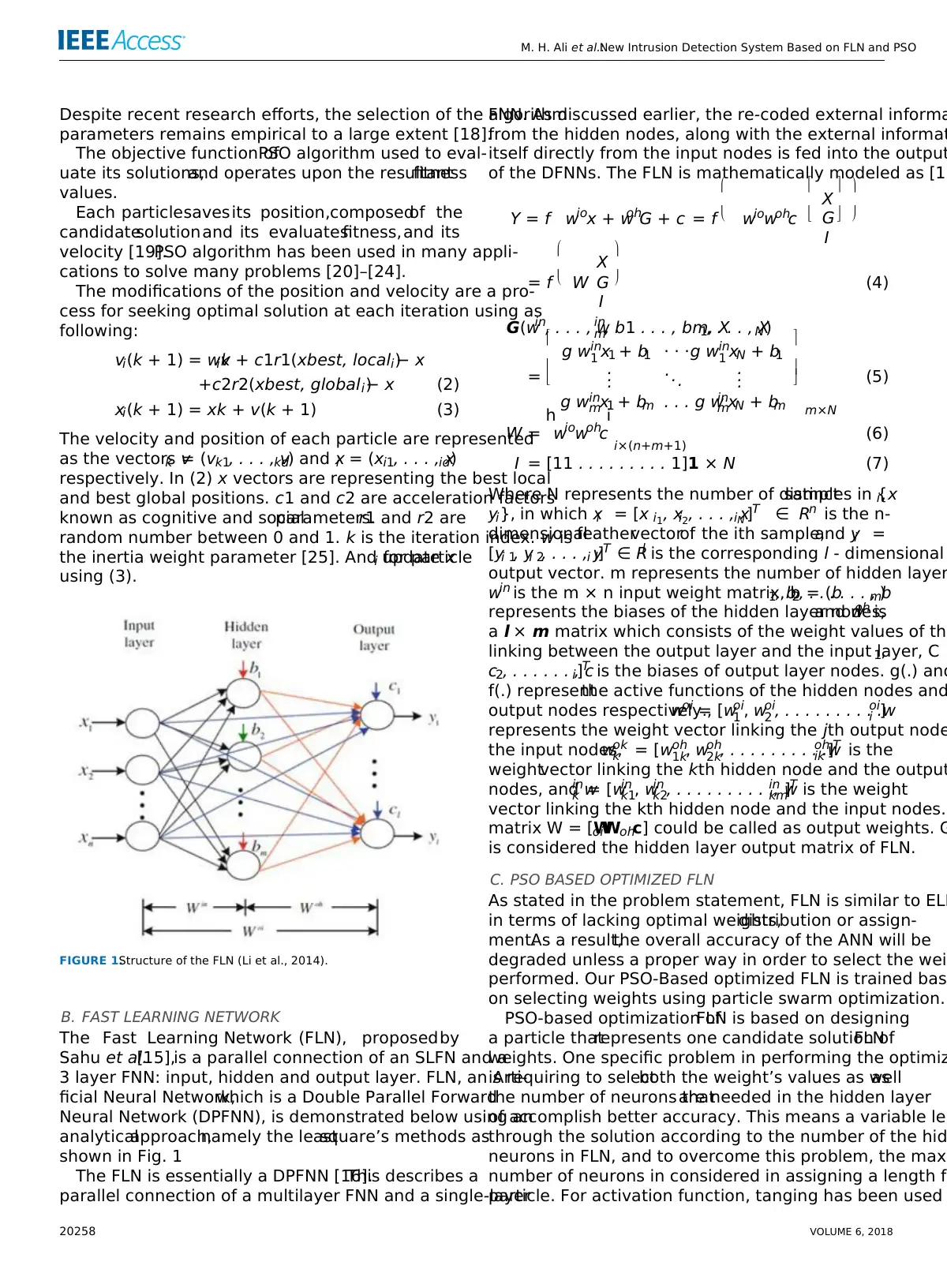
FIGURE 1.Structure of the FLN (Li et al., 2014).
B. FAST LEARNING NETWORK
The Fast Learning Network (FLN), proposedby
Sahu et al.[15],is a parallel connection of an SLFN and a
3 layer FNN: input, hidden and output layer. FLN, an Arti-
ficial Neural Network,which is a Double Parallel Forward
Neural Network (DPFNN), is demonstrated below using an
analyticalapproach,namely the leastsquare’s methods as
shown in Fig. 1
The FLN is essentially a DPFNN [16].This describes a
parallel connection of a multilayer FNN and a single-layer
FNN. As discussed earlier, the re-coded external informa
from the hidden nodes, along with the external informat
itself directly from the input nodes is fed into the output
of the DFNNs. The FLN is mathematically modeled as [15
Y = f wiox + wohG + c = f
wiowohc
X
G
I
= f
W
X
G
I
(4)
G(win, . . . , win
m, b1 . . . , bm, X1, . . . , XN )
=
g win
1 x1 + b1 · · ·g win
1 xN + b1
... ... ...
g win
mx1 + bm . . . g win
mxN + bm
m×N
(5)
W =
h
wiowohc
i
i×(n+m+1) (6)
I = [11 . . . . . . . . . 1]1 × N (7)
Where N represents the number of distinctsamples in {xi,
yi}, in which xi = [x i1, xi2, . . . , xiN ]T ∈ Rn is the n-
dimensionalfeathervectorof the ith sample,and yi =
[yi 1, yi 2, . . . , yi l]T ∈ Rl is the corresponding l - dimensional
output vector. m represents the number of hidden layer
win is the m × n input weight matrix, b = (b1, b2, . . . . . . , bm)
represents the biases of the hidden layer nodes,and woh is
a l × m matrix which consists of the weight values of the
linking between the output layer and the input layer, C =1,
c2, . . . . . . , ci]T is the biases of output layer nodes. g(.) and
f(.) representthe active functions of the hidden nodes and
output nodes respectively.,woi = [woi
1 , woi
2 , . . . . . . . . . .woi
i ]
represents the weight vector linking the jth output node
the input nodes,wok
k = [woh
1k, woh
2k, . . . . . . . . . .woh
ik ]T is the
weightvector linking the kth hidden node and the output
nodes, and win
k = [win
k1, win
k2, . . . . . . . . . ., win
km]T is the weight
vector linking the kth hidden node and the input nodes.
matrix W = [WoiWohc] could be called as output weights. G
is considered the hidden layer output matrix of FLN.
C. PSO BASED OPTIMIZED FLN
As stated in the problem statement, FLN is similar to ELM
in terms of lacking optimal weights,distribution or assign-
ment.As a result,the overall accuracy of the ANN will be
degraded unless a proper way in order to select the weig
performed. Our PSO-Based optimized FLN is trained base
on selecting weights using particle swarm optimization.
PSO-based optimization ofFLN is based on designing
a particle thatrepresents one candidate solution ofFLN
weights. One specific problem in performing the optimiz
is requiring to selectboth the weight’s values as wellas
the number of neurons thatare needed in the hidden layer
of accomplish better accuracy. This means a variable len
through the solution according to the number of the hid
neurons in FLN, and to overcome this problem, the maxi
number of neurons in considered in assigning a length fo
particle. For activation function, tanging has been used
20258 VOLUME 6, 2018
Despite recent research efforts, the selection of the algorithm
parameters remains empirical to a large extent [18].
The objective function ofPSO algorithm used to eval-
uate its solutions,and operates upon the resultantfitness
values.
Each particlesavesits position,composedof the
candidatesolution and its evaluatesfitness,and its
velocity [19].PSO algorithm has been used in many appli-
cations to solve many problems [20]–[24].
The modifications of the position and velocity are a pro-
cess for seeking optimal solution at each iteration using as
following:
vi(k + 1) = wvik + c1r1(xbest, local − xi)
+c2r2(xbest, global − xi) (2)
xi(k + 1) = xk + v(k + 1) (3)
The velocity and position of each particle are represented
as the vectors vk = (vk1, . . . , vkd) and xi = (xi1, . . . , xid)
respectively. In (2) x vectors are representing the best local
and best global positions. c1 and c2 are acceleration factors
known as cognitive and socialparameters.r1 and r2 are
random number between 0 and 1. k is the iteration index. w is
the inertia weight parameter [25]. And update xi for particle
using (3).
FIGURE 1.Structure of the FLN (Li et al., 2014).
B. FAST LEARNING NETWORK
The Fast Learning Network (FLN), proposedby
Sahu et al.[15],is a parallel connection of an SLFN and a
3 layer FNN: input, hidden and output layer. FLN, an Arti-
ficial Neural Network,which is a Double Parallel Forward
Neural Network (DPFNN), is demonstrated below using an
analyticalapproach,namely the leastsquare’s methods as
shown in Fig. 1
The FLN is essentially a DPFNN [16].This describes a
parallel connection of a multilayer FNN and a single-layer
FNN. As discussed earlier, the re-coded external informa
from the hidden nodes, along with the external informat
itself directly from the input nodes is fed into the output
of the DFNNs. The FLN is mathematically modeled as [15
Y = f wiox + wohG + c = f
wiowohc
X
G
I
= f
W
X
G
I
(4)
G(win, . . . , win
m, b1 . . . , bm, X1, . . . , XN )
=
g win
1 x1 + b1 · · ·g win
1 xN + b1
... ... ...
g win
mx1 + bm . . . g win
mxN + bm
m×N
(5)
W =
h
wiowohc
i
i×(n+m+1) (6)
I = [11 . . . . . . . . . 1]1 × N (7)
Where N represents the number of distinctsamples in {xi,
yi}, in which xi = [x i1, xi2, . . . , xiN ]T ∈ Rn is the n-
dimensionalfeathervectorof the ith sample,and yi =
[yi 1, yi 2, . . . , yi l]T ∈ Rl is the corresponding l - dimensional
output vector. m represents the number of hidden layer
win is the m × n input weight matrix, b = (b1, b2, . . . . . . , bm)
represents the biases of the hidden layer nodes,and woh is
a l × m matrix which consists of the weight values of the
linking between the output layer and the input layer, C =1,
c2, . . . . . . , ci]T is the biases of output layer nodes. g(.) and
f(.) representthe active functions of the hidden nodes and
output nodes respectively.,woi = [woi
1 , woi
2 , . . . . . . . . . .woi
i ]
represents the weight vector linking the jth output node
the input nodes,wok
k = [woh
1k, woh
2k, . . . . . . . . . .woh
ik ]T is the
weightvector linking the kth hidden node and the output
nodes, and win
k = [win
k1, win
k2, . . . . . . . . . ., win
km]T is the weight
vector linking the kth hidden node and the input nodes.
matrix W = [WoiWohc] could be called as output weights. G
is considered the hidden layer output matrix of FLN.
C. PSO BASED OPTIMIZED FLN
As stated in the problem statement, FLN is similar to ELM
in terms of lacking optimal weights,distribution or assign-
ment.As a result,the overall accuracy of the ANN will be
degraded unless a proper way in order to select the weig
performed. Our PSO-Based optimized FLN is trained base
on selecting weights using particle swarm optimization.
PSO-based optimization ofFLN is based on designing
a particle thatrepresents one candidate solution ofFLN
weights. One specific problem in performing the optimiz
is requiring to selectboth the weight’s values as wellas
the number of neurons thatare needed in the hidden layer
of accomplish better accuracy. This means a variable len
through the solution according to the number of the hid
neurons in FLN, and to overcome this problem, the maxi
number of neurons in considered in assigning a length fo
particle. For activation function, tanging has been used
20258 VOLUME 6, 2018
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
M. H. Ali et al.:New Intrusion Detection System Based on FLN and PSO
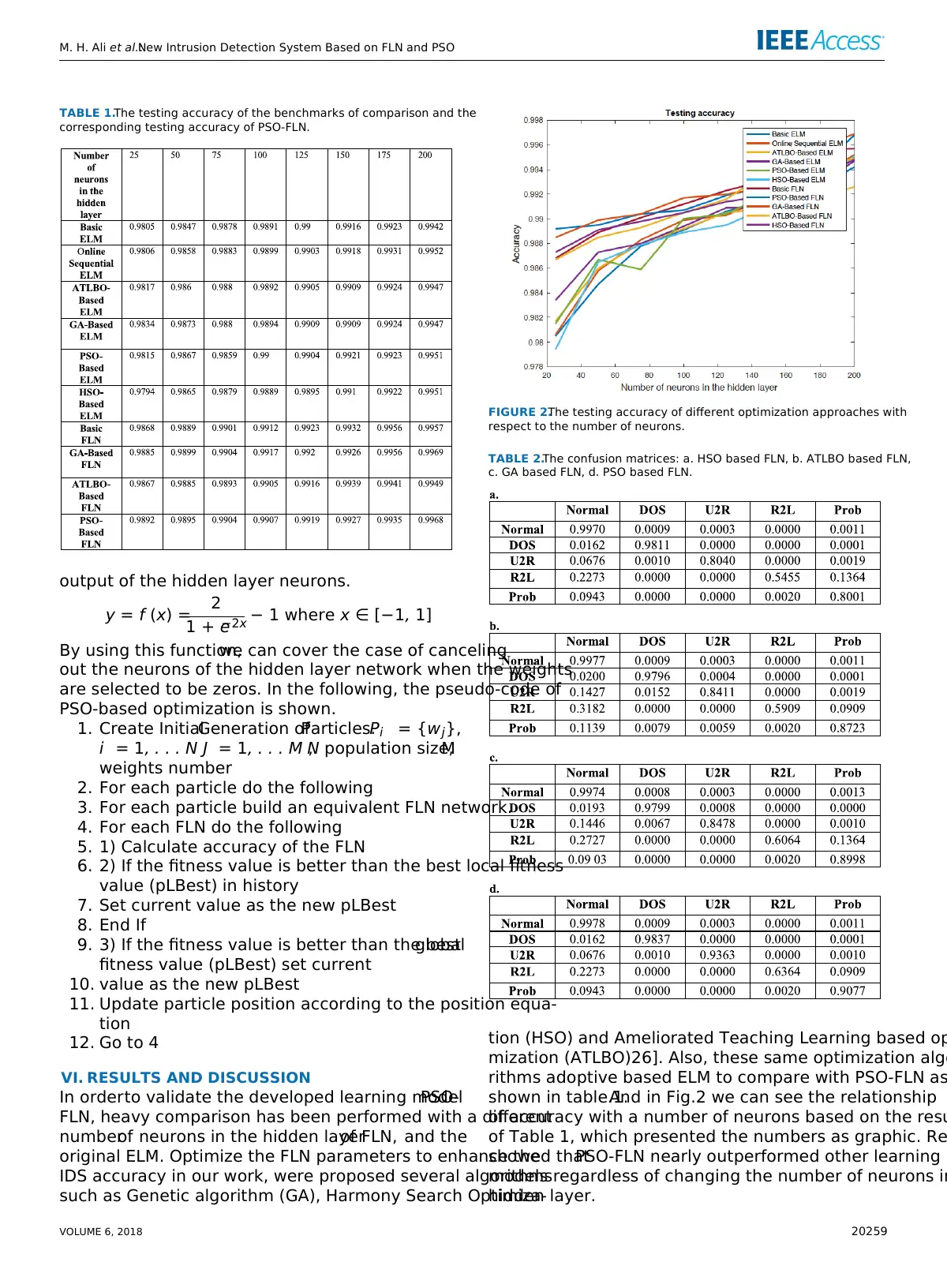
TABLE 1.The testing accuracy of the benchmarks of comparison and the
corresponding testing accuracy of PSO-FLN.
output of the hidden layer neurons.
y = f (x) = 2
1 + e−2x − 1 where x ∈ [−1, 1]
By using this function,we can cover the case of canceling
out the neurons of the hidden layer network when the weights
are selected to be zeros. In the following, the pseudo-code of
PSO-based optimization is shown.
1. Create InitialGeneration ofParticles.Pi = {wj},
i = 1, . . . N J = 1, . . . M ,N population size,M
weights number
2. For each particle do the following
3. For each particle build an equivalent FLN network.
4. For each FLN do the following
5. 1) Calculate accuracy of the FLN
6. 2) If the fitness value is better than the best local fitness
value (pLBest) in history
7. Set current value as the new pLBest
8. End If
9. 3) If the fitness value is better than the bestglobal
fitness value (pLBest) set current
10. value as the new pLBest
11. Update particle position according to the position equa-
tion
12. Go to 4
VI. RESULTS AND DISCUSSION
In orderto validate the developed learning modelPSO-
FLN, heavy comparison has been performed with a different
numberof neurons in the hidden layerof FLN, and the
original ELM. Optimize the FLN parameters to enhance the
IDS accuracy in our work, were proposed several algorithms
such as Genetic algorithm (GA), Harmony Search Optimiza-
FIGURE 2.The testing accuracy of different optimization approaches with
respect to the number of neurons.
TABLE 2.The confusion matrices: a. HSO based FLN, b. ATLBO based FLN,
c. GA based FLN, d. PSO based FLN.
tion (HSO) and Ameliorated Teaching Learning based op
mization (ATLBO)26]. Also, these same optimization algo
rithms adoptive based ELM to compare with PSO-FLN as
shown in table.1.And in Fig.2 we can see the relationship
of accuracy with a number of neurons based on the resu
of Table 1, which presented the numbers as graphic. Re
showed thatPSO-FLN nearly outperformed other learning
models regardless of changing the number of neurons in
hidden layer.
VOLUME 6, 2018 20259
TABLE 1.The testing accuracy of the benchmarks of comparison and the
corresponding testing accuracy of PSO-FLN.
output of the hidden layer neurons.
y = f (x) = 2
1 + e−2x − 1 where x ∈ [−1, 1]
By using this function,we can cover the case of canceling
out the neurons of the hidden layer network when the weights
are selected to be zeros. In the following, the pseudo-code of
PSO-based optimization is shown.
1. Create InitialGeneration ofParticles.Pi = {wj},
i = 1, . . . N J = 1, . . . M ,N population size,M
weights number
2. For each particle do the following
3. For each particle build an equivalent FLN network.
4. For each FLN do the following
5. 1) Calculate accuracy of the FLN
6. 2) If the fitness value is better than the best local fitness
value (pLBest) in history
7. Set current value as the new pLBest
8. End If
9. 3) If the fitness value is better than the bestglobal
fitness value (pLBest) set current
10. value as the new pLBest
11. Update particle position according to the position equa-
tion
12. Go to 4
VI. RESULTS AND DISCUSSION
In orderto validate the developed learning modelPSO-
FLN, heavy comparison has been performed with a different
numberof neurons in the hidden layerof FLN, and the
original ELM. Optimize the FLN parameters to enhance the
IDS accuracy in our work, were proposed several algorithms
such as Genetic algorithm (GA), Harmony Search Optimiza-
FIGURE 2.The testing accuracy of different optimization approaches with
respect to the number of neurons.
TABLE 2.The confusion matrices: a. HSO based FLN, b. ATLBO based FLN,
c. GA based FLN, d. PSO based FLN.
tion (HSO) and Ameliorated Teaching Learning based op
mization (ATLBO)26]. Also, these same optimization algo
rithms adoptive based ELM to compare with PSO-FLN as
shown in table.1.And in Fig.2 we can see the relationship
of accuracy with a number of neurons based on the resu
of Table 1, which presented the numbers as graphic. Re
showed thatPSO-FLN nearly outperformed other learning
models regardless of changing the number of neurons in
hidden layer.
VOLUME 6, 2018 20259

M. H. Ali et al.:New Intrusion Detection System Based on FLN and PSO
Table.1 show that the increase of the hidden neuron’s num-
ber linked to an increase the accuracy. For more details of the
performance,the table (2) shows the confusion matrices of
the testing results in all cases of optimize based on FLN with
specified the hidden number of neurons 25. Our analysis with
the confusion matrix results can be stated as follows.Class
number 4, which represents R2L attack, has obtained lower
accuracy comparing with other classes.This is due to the
limited amount of training data in this class comparing with
other classes. However, there is an obvious trend of improving
accuracy with the increase to the number of neurons in the
hidden layer.
The optimization algorithmswereused based on the
defaultsituation ofit. Firstly,we used HSO parameters
setas the Harmony Memory (HM) = 50,Harmony Mem-
ory Considering Rate (HMCR)= 0.7 and Pitch Adjusting
Rate (PAR)= 0.35.Secondly,for ATLBO, the number of
learners = 50.Thirdly,the ga function from GA toolbox
as in [27].Fourthly,for PSO parameters formulae such as
c1 = c2 = 1.42,w = 0.75 and number of particles = 50.
As for parameters that share for all the optimization models,
number of iterations = 100, training data = 72788 × 40 and
testing data = 72798 × 40.
VII. CONCLUSION AND SUMMARY
In this article,the problem of intrusion detection has been
presented and different approaches of solving were discussed.
Using ANN based intrusion detection is more promising for
reducing the numberof wrong negative orfalse positives
because ANN has the capability oflearning from actual
examples.A developed learning modelfor FLN based on
particle swarm optimization has been proposed and named
as PSO-FLN. The model has been applied to the problem of
intrusion detection and validated based on the famous dataset
KDD99. Our developed model has been compared against the
wide range of meta-heuristic algorithms for training ELM,
and FLN classifier.It can be concluded that our developed
PSO-FLN has outperformed otherlearning approaches in
the testing accuracy of the learning. Another finding is that
the accuracy has increased for allmodels with increasing
the number of hidden neurons in the ANN Future work is to
counter the problem of less accuracy for a certain number of
class because of the limited available amount of training data
for such class.
REFERENCES
[1] B. G. Goodarzi,H. Jazayeri,and S.Fateri,‘‘Intrusion detection system
in computer network using hybrid algorithms(SVM and ABC),’’ J.Adv.
Comput. Res., vol. 5, no. 4, pp. 43–52, 2014.
[2] S. K. Gautam and H.Om, ‘‘Computationalneuralnetwork regression
model for host based intrusion detection system,’’ Perspectives Sci., vol. 8,
pp. 93–95, Sep. 2016.
[3] F. A. Anifowose and S. I. Eludiora, ‘‘Application of artificial intelligence
in network intrusion detection,’’ World Appl.Programm.,vol.2, no.3,
pp. 158–166, 2012.
[4] D. E. Denning,‘‘An intrusion-detection model,’’in Proc.IEEE Symp.
Secur. Priv., vol. 2. Apr. 2012, pp. 118–131.
[5] M. S. Hoque,M. A. Mukit,M. A. N. Bikas,and M.S. Hoque,‘‘An
implementation of intrusion detection system using genetic algorithm
Int. J. Netw. Secur. Appl., vol. 4, no. 2, pp. 109–120, 2012.
[6] J. Frank,‘‘Artificialintelligence and intrusion detection:Currentand
future directions,’’ in Proc.17th Nat.Comput.Secur.Conf.,Baltimore,
MD, USA, Oct. 1994. [Online]. Available:https://scholar.google.
com/scholar?hl=en&as_sdt=0%2C5&q=A.+D.+O.+D.+Dabt–c-%2C+
‘‘Arti+cial+Intelligence+and+Intrusion+Detection?%3A+Current+an
Future+Directions+1+Problems+in+Intrusion+Detection+2+Arti+ci
Intelligence+Methods%2C’’+Expert+Syst.%2C+pp.+1-12%2C+1994
btnG=
[7] M. Green,U. Ekelund,L. Edenbrandt,J. Björk, J. L. Forberg,and
M. Ohlsson,‘‘Exploring new possibilitiesfor case-based explanation
of artificialneuralnetwork ensembles,’’NeuralNetw.,vol. 22, no. 1,
pp. 75–81, 2009.
[8] S. Kiranyaz, T. Ince, A. Yildirim, and M. Gabbouj, ‘‘Evolutionary artifi-
cial neural networks by multi-dimensional particle swarm optimizatio
Neural Netw., vol. 22, no. 10, pp. 1448–1462, 2009.
[9] T. W. S. Chow, J. Y. F. Yam, and S. Y. Cho, ‘‘Fast training algorithm for
feedforward neural networks: Application to crowd estimation at und
ground stations,’’ Artif. Intell. Eng., vol. 13, no. 3, pp. 301–307, 1999.
[10] G.-B. Huang,X. Ding, and H. Zhou,‘‘Optimization method based
extreme learning machine for classification,’’ Neurocomputing,vol. 74,
pp. 155–163, Dec. 2010.
[11] G.-B. Huang,Q.-Y. Zhu,and C.-K.Siew,‘‘Extreme learning machine:
Theory and applications,’’Neurocomputing,vol. 70, nos. 1–3,
pp. 489–501, 2006.
[12] G.-B. Huang,Q.-Y. Zhu,and C.-K.Siew,‘‘Extreme learning machine:
A new learning scheme of feedforward neural networks,’’ in Proc. IEE
Int. Joint Conf. Neural Netw., vol. 2. Jul. 2004, pp. 985–990.
[13] G. Li, P. Niu, X. Duan,and X.Zhang,‘‘Fast learning network: A novel
artificial neural network with a fast learning speed,’’ Neural Comput.
vol. 24, nos. 7–8, pp. 1683–1695, 2014.
[14] J. Wang, W. Wu, Z. Li, and L. Li, ‘‘Convergence of gradient method for
double parallel feedforward neural network,’’ Int. J. Numer. Anal. Mod
vol. 8, no. 3, pp. 484–495, 2011.
[15] S. K. Sahu, S. Sarangi, and S. K. Jena, ‘‘A detail analysis on intrusion d
tion datasets,’’ in Proc. IEEE Int. Adv. Comput. Conf. (IACC), Feb. 201
pp. 1348–1353.
[16] A. A. Olusola, A. S. Oladele, and D. O. Abosede, ‘‘Analysis of KDD’99
intrusion detection datasetfor selection of relevance features,’’ in Proc.
World Congr. Eng. Comput. Sci., Jan. 2016, pp. 16–23.
[17] T.-S. Chou, J. Fan, S. Fan, and K. Makki, ‘‘Ensemble of machine learnin
algorithms for intrusion detection,’’ in Proc.IEEE Int. Conf.Syst.Man
Cybern., Oct. 2009, pp. 3976–3980.
[18] I. C. Trelea,‘‘The particle swarm optimization algorithm:Convergence
analysis and parameterselection,’’Inf. Process.Lett.,vol. 85, no. 6,
pp. 317–325, 2003.
[19] J. Blondin. Particle Swarm Optimization: A Tutorial. [Online]. Available
http://cs.armstrong.edu/saad/csci8100/pso_tutorial.pdf
[20] A. Sengupta,S. Bhadauria,and S.P. Mohanty,‘‘TL-HLS: Methodol-
ogy for low costhardware trojan security aware scheduling with opti-
mal loop unrolling factorduring high levelsynthesis,’’IEEE Trans.
Comput.-Aided Des.Integr.Circuits Syst.,vol. 36,no.4, pp.660–673,
Apr. 2017.
[21] V. K. Mishra and A. Sengupta, ‘‘Swarm-inspired exploration of archite
ture and unrolling factors for nested-loop-based application in archite
synthesis,’’ Electron. Lett., vol. 51, no. 2, pp. 157–159, 2015.
[22] A. Sengupta and S.Bhadauria,‘‘User power-delay budgetdriven PSO
based design space exploration of optimal k-cycle transient fault sec
datapath during high level synthesis,’’ in Proc.-Int. Symp. Qual. Elect
Des. (ISQED), Apr. 2015, pp. 289–292.
[23] V. K. Mishra and A. Sengupta, ‘‘MO-PSE: Adaptive multi-objective par
ticle swarm optimization based design space exploration in architect
synthesis forapplication specific processordesign,’’Adv.Eng.Softw.,
vol. 67, pp. 111–124, Jan. 2014.
[24] A. Senguptaand V. K. Mishra,‘‘Expertsystemswith applications
automated exploration of datapath and unrolling factor during power
Performance tradeoff in architecturalsynthesis using multi-dimensional
PSO algorithm,’’ Expert Syst. Appl., vol. 41, no. 10, pp. 4691–4703, 2
[25] Y. Shi and R. Eberhart, ‘‘A modified particle swarm optimizer,’’ in Pro
IEEE Int. Conf., May 1998, pp. 69–73.
20260 VOLUME 6, 2018
Table.1 show that the increase of the hidden neuron’s num-
ber linked to an increase the accuracy. For more details of the
performance,the table (2) shows the confusion matrices of
the testing results in all cases of optimize based on FLN with
specified the hidden number of neurons 25. Our analysis with
the confusion matrix results can be stated as follows.Class
number 4, which represents R2L attack, has obtained lower
accuracy comparing with other classes.This is due to the
limited amount of training data in this class comparing with
other classes. However, there is an obvious trend of improving
accuracy with the increase to the number of neurons in the
hidden layer.
The optimization algorithmswereused based on the
defaultsituation ofit. Firstly,we used HSO parameters
setas the Harmony Memory (HM) = 50,Harmony Mem-
ory Considering Rate (HMCR)= 0.7 and Pitch Adjusting
Rate (PAR)= 0.35.Secondly,for ATLBO, the number of
learners = 50.Thirdly,the ga function from GA toolbox
as in [27].Fourthly,for PSO parameters formulae such as
c1 = c2 = 1.42,w = 0.75 and number of particles = 50.
As for parameters that share for all the optimization models,
number of iterations = 100, training data = 72788 × 40 and
testing data = 72798 × 40.
VII. CONCLUSION AND SUMMARY
In this article,the problem of intrusion detection has been
presented and different approaches of solving were discussed.
Using ANN based intrusion detection is more promising for
reducing the numberof wrong negative orfalse positives
because ANN has the capability oflearning from actual
examples.A developed learning modelfor FLN based on
particle swarm optimization has been proposed and named
as PSO-FLN. The model has been applied to the problem of
intrusion detection and validated based on the famous dataset
KDD99. Our developed model has been compared against the
wide range of meta-heuristic algorithms for training ELM,
and FLN classifier.It can be concluded that our developed
PSO-FLN has outperformed otherlearning approaches in
the testing accuracy of the learning. Another finding is that
the accuracy has increased for allmodels with increasing
the number of hidden neurons in the ANN Future work is to
counter the problem of less accuracy for a certain number of
class because of the limited available amount of training data
for such class.
REFERENCES
[1] B. G. Goodarzi,H. Jazayeri,and S.Fateri,‘‘Intrusion detection system
in computer network using hybrid algorithms(SVM and ABC),’’ J.Adv.
Comput. Res., vol. 5, no. 4, pp. 43–52, 2014.
[2] S. K. Gautam and H.Om, ‘‘Computationalneuralnetwork regression
model for host based intrusion detection system,’’ Perspectives Sci., vol. 8,
pp. 93–95, Sep. 2016.
[3] F. A. Anifowose and S. I. Eludiora, ‘‘Application of artificial intelligence
in network intrusion detection,’’ World Appl.Programm.,vol.2, no.3,
pp. 158–166, 2012.
[4] D. E. Denning,‘‘An intrusion-detection model,’’in Proc.IEEE Symp.
Secur. Priv., vol. 2. Apr. 2012, pp. 118–131.
[5] M. S. Hoque,M. A. Mukit,M. A. N. Bikas,and M.S. Hoque,‘‘An
implementation of intrusion detection system using genetic algorithm
Int. J. Netw. Secur. Appl., vol. 4, no. 2, pp. 109–120, 2012.
[6] J. Frank,‘‘Artificialintelligence and intrusion detection:Currentand
future directions,’’ in Proc.17th Nat.Comput.Secur.Conf.,Baltimore,
MD, USA, Oct. 1994. [Online]. Available:https://scholar.google.
com/scholar?hl=en&as_sdt=0%2C5&q=A.+D.+O.+D.+Dabt–c-%2C+
‘‘Arti+cial+Intelligence+and+Intrusion+Detection?%3A+Current+an
Future+Directions+1+Problems+in+Intrusion+Detection+2+Arti+ci
Intelligence+Methods%2C’’+Expert+Syst.%2C+pp.+1-12%2C+1994
btnG=
[7] M. Green,U. Ekelund,L. Edenbrandt,J. Björk, J. L. Forberg,and
M. Ohlsson,‘‘Exploring new possibilitiesfor case-based explanation
of artificialneuralnetwork ensembles,’’NeuralNetw.,vol. 22, no. 1,
pp. 75–81, 2009.
[8] S. Kiranyaz, T. Ince, A. Yildirim, and M. Gabbouj, ‘‘Evolutionary artifi-
cial neural networks by multi-dimensional particle swarm optimizatio
Neural Netw., vol. 22, no. 10, pp. 1448–1462, 2009.
[9] T. W. S. Chow, J. Y. F. Yam, and S. Y. Cho, ‘‘Fast training algorithm for
feedforward neural networks: Application to crowd estimation at und
ground stations,’’ Artif. Intell. Eng., vol. 13, no. 3, pp. 301–307, 1999.
[10] G.-B. Huang,X. Ding, and H. Zhou,‘‘Optimization method based
extreme learning machine for classification,’’ Neurocomputing,vol. 74,
pp. 155–163, Dec. 2010.
[11] G.-B. Huang,Q.-Y. Zhu,and C.-K.Siew,‘‘Extreme learning machine:
Theory and applications,’’Neurocomputing,vol. 70, nos. 1–3,
pp. 489–501, 2006.
[12] G.-B. Huang,Q.-Y. Zhu,and C.-K.Siew,‘‘Extreme learning machine:
A new learning scheme of feedforward neural networks,’’ in Proc. IEE
Int. Joint Conf. Neural Netw., vol. 2. Jul. 2004, pp. 985–990.
[13] G. Li, P. Niu, X. Duan,and X.Zhang,‘‘Fast learning network: A novel
artificial neural network with a fast learning speed,’’ Neural Comput.
vol. 24, nos. 7–8, pp. 1683–1695, 2014.
[14] J. Wang, W. Wu, Z. Li, and L. Li, ‘‘Convergence of gradient method for
double parallel feedforward neural network,’’ Int. J. Numer. Anal. Mod
vol. 8, no. 3, pp. 484–495, 2011.
[15] S. K. Sahu, S. Sarangi, and S. K. Jena, ‘‘A detail analysis on intrusion d
tion datasets,’’ in Proc. IEEE Int. Adv. Comput. Conf. (IACC), Feb. 201
pp. 1348–1353.
[16] A. A. Olusola, A. S. Oladele, and D. O. Abosede, ‘‘Analysis of KDD’99
intrusion detection datasetfor selection of relevance features,’’ in Proc.
World Congr. Eng. Comput. Sci., Jan. 2016, pp. 16–23.
[17] T.-S. Chou, J. Fan, S. Fan, and K. Makki, ‘‘Ensemble of machine learnin
algorithms for intrusion detection,’’ in Proc.IEEE Int. Conf.Syst.Man
Cybern., Oct. 2009, pp. 3976–3980.
[18] I. C. Trelea,‘‘The particle swarm optimization algorithm:Convergence
analysis and parameterselection,’’Inf. Process.Lett.,vol. 85, no. 6,
pp. 317–325, 2003.
[19] J. Blondin. Particle Swarm Optimization: A Tutorial. [Online]. Available
http://cs.armstrong.edu/saad/csci8100/pso_tutorial.pdf
[20] A. Sengupta,S. Bhadauria,and S.P. Mohanty,‘‘TL-HLS: Methodol-
ogy for low costhardware trojan security aware scheduling with opti-
mal loop unrolling factorduring high levelsynthesis,’’IEEE Trans.
Comput.-Aided Des.Integr.Circuits Syst.,vol. 36,no.4, pp.660–673,
Apr. 2017.
[21] V. K. Mishra and A. Sengupta, ‘‘Swarm-inspired exploration of archite
ture and unrolling factors for nested-loop-based application in archite
synthesis,’’ Electron. Lett., vol. 51, no. 2, pp. 157–159, 2015.
[22] A. Sengupta and S.Bhadauria,‘‘User power-delay budgetdriven PSO
based design space exploration of optimal k-cycle transient fault sec
datapath during high level synthesis,’’ in Proc.-Int. Symp. Qual. Elect
Des. (ISQED), Apr. 2015, pp. 289–292.
[23] V. K. Mishra and A. Sengupta, ‘‘MO-PSE: Adaptive multi-objective par
ticle swarm optimization based design space exploration in architect
synthesis forapplication specific processordesign,’’Adv.Eng.Softw.,
vol. 67, pp. 111–124, Jan. 2014.
[24] A. Senguptaand V. K. Mishra,‘‘Expertsystemswith applications
automated exploration of datapath and unrolling factor during power
Performance tradeoff in architecturalsynthesis using multi-dimensional
PSO algorithm,’’ Expert Syst. Appl., vol. 41, no. 10, pp. 4691–4703, 2
[25] Y. Shi and R. Eberhart, ‘‘A modified particle swarm optimizer,’’ in Pro
IEEE Int. Conf., May 1998, pp. 69–73.
20260 VOLUME 6, 2018
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

M. H. Ali et al.:New Intrusion Detection System Based on FLN and PSO
[26] G. Li, P. Niu, W. Zhang,and Y. Liu, ‘‘Model NOx emissionsby
leastsquares supportvector machine with tuning based on ameliorated
teachingŰlearning-based optimization,’’ Chemometrics Intell.Lab.Syst.,
vol. 126, pp. 11–20, Jul. 2013.
[27] J. Tvrdık,‘‘Competitive differentialevolution and genetic algorithm in
GA-DS toolbox,’’ Tech. Comput. Prague, Praha, Humusoft, vol. 1, no. 2,
pp. 99–106, 2006.
MOHAMMED HASAN ALI received the M.Sc.
degreein computersciencefrom Universiti
TeknikalMalaysia Melaka in 2014.He is cur-
rently pursuing the Ph.D.degree with Univer-
siti Malaysia Pahang.He is currently a Research
Assistant with Universiti Malaysia Pahang. He has
authored over 10 research peer review articles in
differentjournals and internationalconferences.
His currentresearch interestsinclude Android
security and network security.
BAHAA ABBAS DAWOOD AL MOHAMMED
was born ThiQar,Iraq,in 1989.He received the
B.Sc.degree in engineering from the Electrome-
chanical System Department, University of Tech-
nology Iraq,in 2011.He is currently pursuing
the master’s degree with the Communications and
Network Department,WirelessCommunication
Engineering Branch,UniversitiPutra Malaysia,
Malaysia. He is with the Department of Computer
and Communication Systems,Faculty ofEngi-
neering, Universiti Putra Malaysia.
ALYANI ISMAIL (M’17) received theB.Eng.
degree(Hons.) in electronicand informa-
tion engineeringfrom the University of
Huddersfield, U.K., in 2000, and the M.Sc. degree
in communication and computerand human-
centered systems engineering (major in commu-
nication)and thePh.D. degreein electronics
engineering (thesis:design if microwave waveg-
uides and filters formicromachining)from the
University ofBirmingham,U.K., in 2002 and
2006, respectively. She is currently a Lecturer with the Department of
puter and Communication Systems Engineering,Faculty of Engineering,
Universiti Putra Malaysia,Malaysia.She is a member of the International
Association of Engineers.
MOHAMAD FADLI ZOLKIPLI received the doc-
torate degree in computer science from Universiti
Sains Malaysia in 2012.He is currently a Senior
Lecturer with the Faculty of Computer Systems
and Software Engineering,UniversitiMalaysia
Pahang.His career in academia started when he
joined KUKTEM in 2002 as an academician. His
teaching expertise includes data communication
and networking,switching and routing,and net-
work security. He is currently active in supervising
research students of master and doctorate degrees. He has authored n
articles in the area ofcomputersystems and networking,especially in
security domain such as intrusion detection systems, malware analysis
cloud security. His research interests cover the broad area of digital se
As a part of the research community, he was also a reviewer for confer
and journals.
VOLUME 6, 2018 20261
[26] G. Li, P. Niu, W. Zhang,and Y. Liu, ‘‘Model NOx emissionsby
leastsquares supportvector machine with tuning based on ameliorated
teachingŰlearning-based optimization,’’ Chemometrics Intell.Lab.Syst.,
vol. 126, pp. 11–20, Jul. 2013.
[27] J. Tvrdık,‘‘Competitive differentialevolution and genetic algorithm in
GA-DS toolbox,’’ Tech. Comput. Prague, Praha, Humusoft, vol. 1, no. 2,
pp. 99–106, 2006.
MOHAMMED HASAN ALI received the M.Sc.
degreein computersciencefrom Universiti
TeknikalMalaysia Melaka in 2014.He is cur-
rently pursuing the Ph.D.degree with Univer-
siti Malaysia Pahang.He is currently a Research
Assistant with Universiti Malaysia Pahang. He has
authored over 10 research peer review articles in
differentjournals and internationalconferences.
His currentresearch interestsinclude Android
security and network security.
BAHAA ABBAS DAWOOD AL MOHAMMED
was born ThiQar,Iraq,in 1989.He received the
B.Sc.degree in engineering from the Electrome-
chanical System Department, University of Tech-
nology Iraq,in 2011.He is currently pursuing
the master’s degree with the Communications and
Network Department,WirelessCommunication
Engineering Branch,UniversitiPutra Malaysia,
Malaysia. He is with the Department of Computer
and Communication Systems,Faculty ofEngi-
neering, Universiti Putra Malaysia.
ALYANI ISMAIL (M’17) received theB.Eng.
degree(Hons.) in electronicand informa-
tion engineeringfrom the University of
Huddersfield, U.K., in 2000, and the M.Sc. degree
in communication and computerand human-
centered systems engineering (major in commu-
nication)and thePh.D. degreein electronics
engineering (thesis:design if microwave waveg-
uides and filters formicromachining)from the
University ofBirmingham,U.K., in 2002 and
2006, respectively. She is currently a Lecturer with the Department of
puter and Communication Systems Engineering,Faculty of Engineering,
Universiti Putra Malaysia,Malaysia.She is a member of the International
Association of Engineers.
MOHAMAD FADLI ZOLKIPLI received the doc-
torate degree in computer science from Universiti
Sains Malaysia in 2012.He is currently a Senior
Lecturer with the Faculty of Computer Systems
and Software Engineering,UniversitiMalaysia
Pahang.His career in academia started when he
joined KUKTEM in 2002 as an academician. His
teaching expertise includes data communication
and networking,switching and routing,and net-
work security. He is currently active in supervising
research students of master and doctorate degrees. He has authored n
articles in the area ofcomputersystems and networking,especially in
security domain such as intrusion detection systems, malware analysis
cloud security. His research interests cover the broad area of digital se
As a part of the research community, he was also a reviewer for confer
and journals.
VOLUME 6, 2018 20261
1 out of 7
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.


