Choosing Snort IDS: Implementation and Comparison Report
VerifiedAdded on 2020/04/13
|4
|708
|101
Report
AI Summary
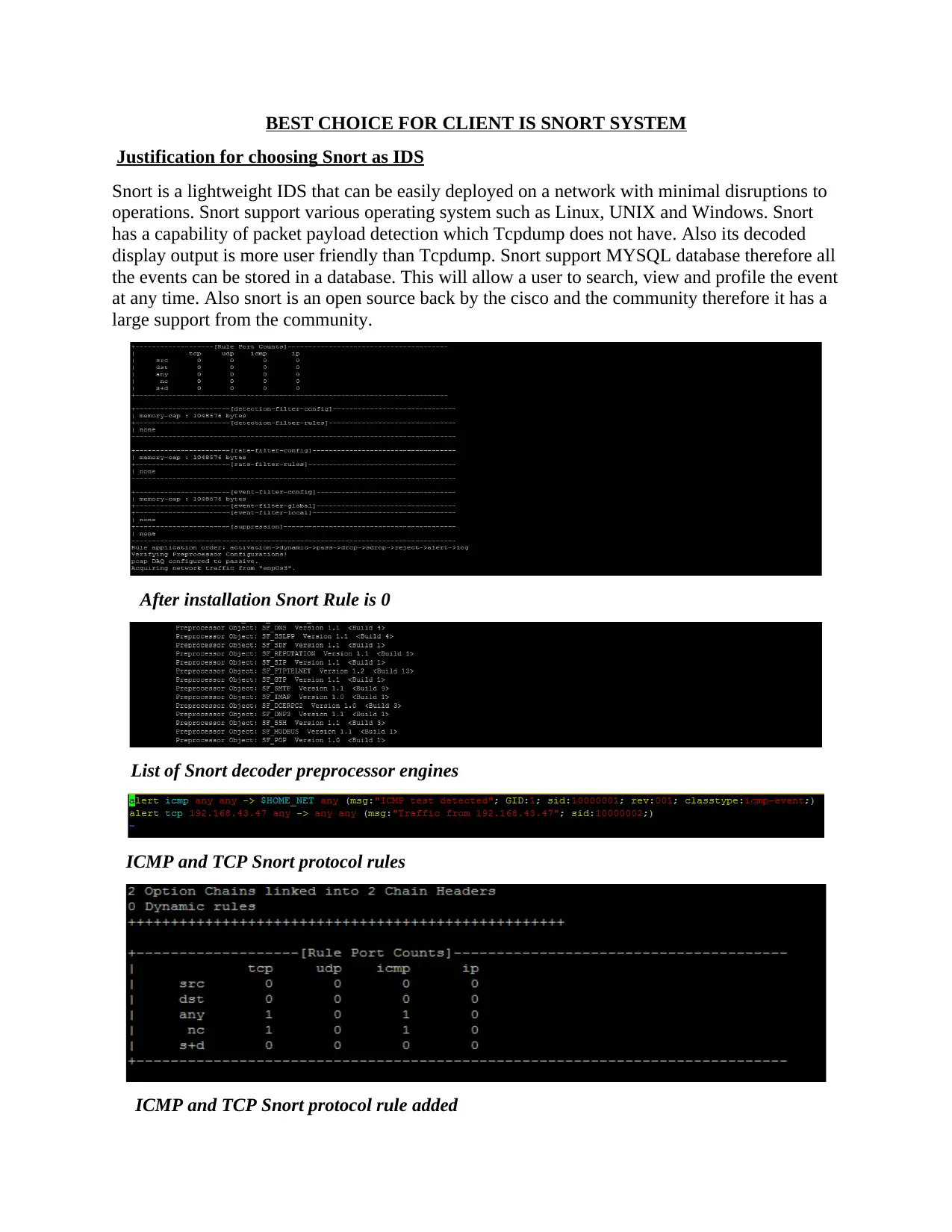
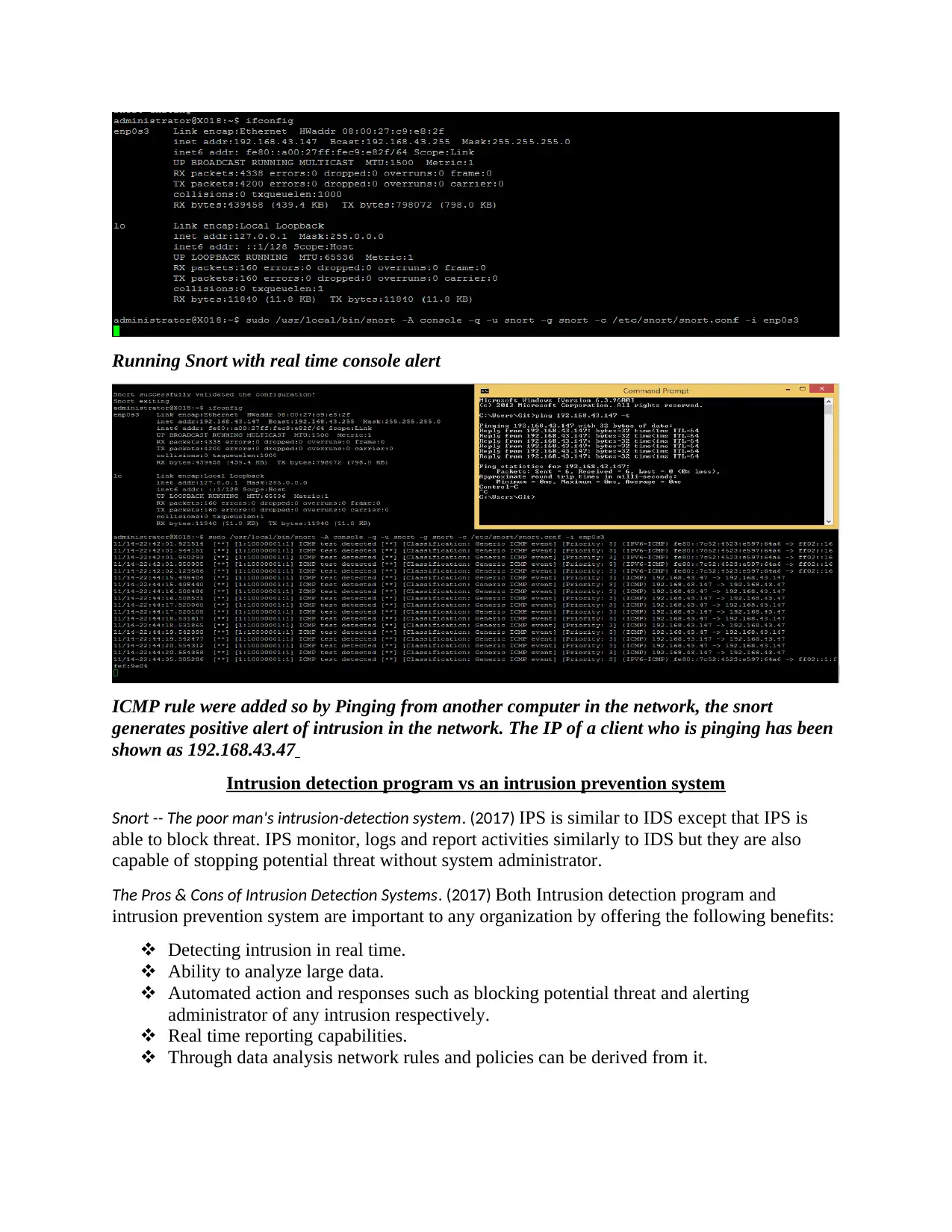
This report provides a comprehensive analysis of the Snort Intrusion Detection System (IDS), arguing for its selection as the best choice for a client. The justification for choosing Snort includes its lightweight nature, ease of deployment across various operating systems (Linux, UNIX, and Windows), and packet payload detection capabilities superior to Tcpdump. The report details the implementation of Snort, including rule configuration and real-time console alerts, demonstrating how ICMP rules generate intrusion alerts. It then differentiates between IDS and Intrusion Prevention Systems (IPS), outlining the pros and cons of each, and highlighting the benefits of both in detecting and preventing network intrusions. The report concludes by providing a list of references used for the analysis, supporting the arguments presented and offering further resources for the reader to explore the topic of network security and intrusion detection.
1 out of 4








![[object Object]](/_next/static/media/star-bottom.7253800d.svg)