Anna University: Intrusion Detection for Blockchain-Based IoT Networks
VerifiedAdded on 2021/08/30
|5
|4213
|21
Report
AI Summary
This research paper introduces IDBIoT, an intrusion detection system designed for blockchain-based IoT networks. The system aims to secure IoT environments by detecting intruders using statistical significance while preventing Goldfinger attacks. The paper explores the architecture of IDBIoT, which leverages blockchain technology for decentralized data storage and intrusion detection. It details how each node monitors its peers, identifies anomalous behavior based on usage patterns, and reports malicious nodes. The study analyzes the probability of achieving consensus within the network and demonstrates the system's performance against Goldfinger attacks. The paper is structured into six sections, covering background information on blockchain and IoT issues, the proposed IDBIoT model, consensus probability analysis, performance evaluation, and conclusions with future scope. The proposed system addresses the security vulnerabilities inherent in IoT devices and the need for software solutions by utilizing blockchain's distributed data storage and enhanced security features. The IDBIoT system predicts abnormal behavior of the nodes by exploiting the usage pattern and reports the malicious nodes to other nodes in the network whereas the data with regular pattern get added to the existing chain if the data achieve consensus within the network. The system is designed to provide a trusted and secured environment using blockchain technology and intrusion detection system.

Intrusion Detector for Blockchain based
IoT Networks
1Gunasekaran Raja,2Aishwarya Ganapathisubramaniyan,3Gokul Anand and4Gowshika
Department of Computer Technology,Anna University,MIT Campus,Chennai.
1dr.r.gunasekaran@ieee.org,2aishwarya97.mit@gmail.com,3gokulanand205@gmail.com,
4gowshikaappavoo@gmail.com
Abstract—Internet of Things (IoT) is a fast growing technology
in the digitalised world where each device in the network inter-
connect and interact with other device to collect the information
and automate tasks.A lotof vulnerabilities are exposed in IoT
devices,which can be exploited to compromise the devices and
an infected device can disruptall other nodes in the network.
The severeness of the vulnerabilities can vary from launching a
Distributed Denial of Service (DDOS) attack to entirely draining
the batteriesof a heart pacemaker.Although IoT providers
constantly working on reducing the vulnerabilities,an Intrusion
Detection (ID)system can be builtto find, whether the nodes
are behaving abnormally or not.ID system can be built with a
centralized architecture, but compromising the centralized entity
can result in compromising the entire network.For storing data
and running ID system in a decentralized manner,blockchain
technology is executed to increase trust between the peers.With
this decentralized blockchain architecture each node will be able
to find out whether the peers in the group are malicious or not.
So, we propose a architecture,IDBIoT (Intrusion Detector for
Blockchain based IoT networks) for Intrusion detection in an IoT
environment, that mainly focuses on the securing the network by
detecting intruders, using statistical significance while preventing
Goldfinger attack.
Index Terms—IoT,Blockchain,Intrusion Detection,Statistical
Significance,Goldfinger Attack.
I. INTRODUCTION
IoT is a networkof interconnectedobjectsbuilt with
electronics,sensors,software and actuators.With increase in
popularity,it also suffers from security threats such as Man-
In-The-Middle (MITM) and Denial of Service (DoS) attacks.
Attackers are able to compromise IoT devices with known
vulnerabilities like insecure web interface,insecure network
services,insecure software or firmware and insufficient secu-
rity configurability, and with the help of a compromised node,
the entire network can be manipulated.IoT devices infected
with Miraimalware controlled online devices and used them
to launch distributed DDoS attacks [11].
With increase in growth ofIoT devices,the amountof
communication handled will increase exponentially. Also, each
affected node can actas a bottleneck and disruptthe entire
network [11].After Edward Snowden leaks,it is difficultfor
IoT adopters to trusttechnologicalpartners who,in general,
give device accessand controlto certain authorities(i.e.,
governments,manufacturersor service providers),allowing
them to collectand analyze userdata [10].Though the IoT
manufacturersare constantly working hard to reducethe
vulnerabilities, there is a need for software solutions to prev
the security threats.
Blockchain on the other hand provides distributed data sto
age and enhanced security for IoT networks. This facilitates
with decentralized storage,communication protocols,mining
hardware,addressmanagementand network administration
[10].The advantage of blockchain is that,once transactions
are recorded overriding the transaction is notpossible.Also
blockchain can be used to provide end-to-end secure autho-
rized access to IoT resources [20].With the deploymentof
blockchain enabled IoT network, all nodes in the network wi
be provided with the details oftheirpeers in the network.
As the usage of devices tend to follow patterns,we focus on
building a ID system, that will predict the abnormal behavio
of the nodes,by exploiting the usage pattern.
IDBIoT, intrusion detection system in blockchain based IoT
technology deployed in each device to monitortheirpeers
through periodically updated patterns from the learning mod
The node which send data with maliciousbehavioursare
reported to other nodes in the network whereas the data wit
regularpattern getadded to the existing chain ifthe data
achieve consensus within the network. IDBIoT sense intrusio
and protectthe Iotdevice and its data from severeness there
by providing secured IoT environment.
The purpose ofthis research paperis to provide trusted
and secured environmentusing blockchain technology and
intrusion detection system.The paper is structured as VI sec-
tions.Section II describes Blockchain,IoT issues,techniques
to detect anomalies,Goldfinger attack and Low powered IoT
devices.Section IIIproposes the intrusion detection system
modelin blockchain based IoT environment.Section IV de-
rives the propability of achieving consensus within the group
and among the groups,and relation among node size,group
size and consensus probability.Section V demonstrates the
performance againstGoldfinger attack.Section VI concludes
the challenges and future scope.
II. LITERATURE SURVEY
A. Blockchain
Blockchain is a kind of decentralized database, which keep
record ofevery transaction made on a network.Instead of
having a traditional central database like bank or governme
database,it has a ledger distributed over a network of nodes
328978-1-7281-0353-2/18/$31.00 ©2018 IEEE
IoT Networks
1Gunasekaran Raja,2Aishwarya Ganapathisubramaniyan,3Gokul Anand and4Gowshika
Department of Computer Technology,Anna University,MIT Campus,Chennai.
1dr.r.gunasekaran@ieee.org,2aishwarya97.mit@gmail.com,3gokulanand205@gmail.com,
4gowshikaappavoo@gmail.com
Abstract—Internet of Things (IoT) is a fast growing technology
in the digitalised world where each device in the network inter-
connect and interact with other device to collect the information
and automate tasks.A lotof vulnerabilities are exposed in IoT
devices,which can be exploited to compromise the devices and
an infected device can disruptall other nodes in the network.
The severeness of the vulnerabilities can vary from launching a
Distributed Denial of Service (DDOS) attack to entirely draining
the batteriesof a heart pacemaker.Although IoT providers
constantly working on reducing the vulnerabilities,an Intrusion
Detection (ID)system can be builtto find, whether the nodes
are behaving abnormally or not.ID system can be built with a
centralized architecture, but compromising the centralized entity
can result in compromising the entire network.For storing data
and running ID system in a decentralized manner,blockchain
technology is executed to increase trust between the peers.With
this decentralized blockchain architecture each node will be able
to find out whether the peers in the group are malicious or not.
So, we propose a architecture,IDBIoT (Intrusion Detector for
Blockchain based IoT networks) for Intrusion detection in an IoT
environment, that mainly focuses on the securing the network by
detecting intruders, using statistical significance while preventing
Goldfinger attack.
Index Terms—IoT,Blockchain,Intrusion Detection,Statistical
Significance,Goldfinger Attack.
I. INTRODUCTION
IoT is a networkof interconnectedobjectsbuilt with
electronics,sensors,software and actuators.With increase in
popularity,it also suffers from security threats such as Man-
In-The-Middle (MITM) and Denial of Service (DoS) attacks.
Attackers are able to compromise IoT devices with known
vulnerabilities like insecure web interface,insecure network
services,insecure software or firmware and insufficient secu-
rity configurability, and with the help of a compromised node,
the entire network can be manipulated.IoT devices infected
with Miraimalware controlled online devices and used them
to launch distributed DDoS attacks [11].
With increase in growth ofIoT devices,the amountof
communication handled will increase exponentially. Also, each
affected node can actas a bottleneck and disruptthe entire
network [11].After Edward Snowden leaks,it is difficultfor
IoT adopters to trusttechnologicalpartners who,in general,
give device accessand controlto certain authorities(i.e.,
governments,manufacturersor service providers),allowing
them to collectand analyze userdata [10].Though the IoT
manufacturersare constantly working hard to reducethe
vulnerabilities, there is a need for software solutions to prev
the security threats.
Blockchain on the other hand provides distributed data sto
age and enhanced security for IoT networks. This facilitates
with decentralized storage,communication protocols,mining
hardware,addressmanagementand network administration
[10].The advantage of blockchain is that,once transactions
are recorded overriding the transaction is notpossible.Also
blockchain can be used to provide end-to-end secure autho-
rized access to IoT resources [20].With the deploymentof
blockchain enabled IoT network, all nodes in the network wi
be provided with the details oftheirpeers in the network.
As the usage of devices tend to follow patterns,we focus on
building a ID system, that will predict the abnormal behavio
of the nodes,by exploiting the usage pattern.
IDBIoT, intrusion detection system in blockchain based IoT
technology deployed in each device to monitortheirpeers
through periodically updated patterns from the learning mod
The node which send data with maliciousbehavioursare
reported to other nodes in the network whereas the data wit
regularpattern getadded to the existing chain ifthe data
achieve consensus within the network. IDBIoT sense intrusio
and protectthe Iotdevice and its data from severeness there
by providing secured IoT environment.
The purpose ofthis research paperis to provide trusted
and secured environmentusing blockchain technology and
intrusion detection system.The paper is structured as VI sec-
tions.Section II describes Blockchain,IoT issues,techniques
to detect anomalies,Goldfinger attack and Low powered IoT
devices.Section IIIproposes the intrusion detection system
modelin blockchain based IoT environment.Section IV de-
rives the propability of achieving consensus within the group
and among the groups,and relation among node size,group
size and consensus probability.Section V demonstrates the
performance againstGoldfinger attack.Section VI concludes
the challenges and future scope.
II. LITERATURE SURVEY
A. Blockchain
Blockchain is a kind of decentralized database, which keep
record ofevery transaction made on a network.Instead of
having a traditional central database like bank or governme
database,it has a ledger distributed over a network of nodes
328978-1-7281-0353-2/18/$31.00 ©2018 IEEE
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

[12].In otherwords,a blockchain isa data structure that
creates a immutable record of events in a distributed network
[7]. Although blockchain is used in decentralized networks,
in [17] a random group mining approach isdiscussed.In
[19],blockchain is used in recommender systems to improve
performance.
B. Issues in IoT Network
Issues in IoT network that are addressed by blockchain are
[10],
• Cloud server’s costand capacity -Blockchain’s decen-
tralized architecture removes the need for a server.
• Deficientarchitecture - Validity of a device’s identity is
verified, transactions are signed and verified cryptograph-
ically.
• Serverdowntimeand unavailability ofservices- No
single pointof failure:Identicalrecords are maintained
by the distributed network.
• Manipulation - Attacker can’tdisruptthe records unless
he owns more computational power in the network.
C. Intrusion Detection
The authors in [1], detects anomaly using mean and standard
deviation ofthe pastdata.If the new datafalls beyond
the confidence range (i.e)mean ± standard deviation the
data is said to be anomalous.If the usage ofthe resources
goesbelow the normalusage,it is not considered asan
anomalous situation for our use case. Data points are clustered
based on similarity to find anomalies.The advantage of this
unsupervised clustering results in no need for a training data
set.A network based intrusion detection is also deployed to
detectthe anomalies,thatuses the originalnetwork packet
as the data source.Network based IDS usually monitors and
analyzes all communication services over the network using a
network adapter running in a random mode.
In [2] intrusion detection is based on density, cluster centers
and Nearest Neighbors.First,clustering is used to obtain dis-
tances and density based on network data to form a new feature
vectorwith low dimension.k-NearestNeighborclassifieris
developed based on the new feature vectors,and the labelis
the outputclass ofdata.Clustering on training setaims to
obtain the cluster center, the nearest neighbors of each sample
point,and the local density of each sample point.
The authorsin [3] proposesa game theoretic approach
for anomaly detection.In this approach,a setof players are
considered representing either an IDS agent or an attacker. The
IDS player, builds a rule related to each new attack’s signature.
The gaming is divided into static game and dynamic game. In
static game,once a playerdecides his strategy,it can’tbe
changed. However,the decision can be changed in a dynamic
game.
In [5] a distributed fog computing technique is used for
intrusion detection.For decreasing the response time,Ex-
treme Machine Learning,a fastlearning algorithm is used.
The sigmoid function provides betteraccuracy and training
time when compared with sine and RadialBasisFunction
(RBF) activation function. To identify malicious nodes within
IoT networks,authors in [6]and [4]employed a Bayesian
based intrusion detection mechanism in which all packets ar
assumed to be independent,irrespective of their origin.
D. Goldfinger attack in Blockchain
The bitcoin is a peer to peer payment network that operat
on cryptographic protocol.Bitcoin transactions are recorded
into distributed database known asthe blockchain through
consensusand Proofof Work (PoW)mechanisms[18].A
clientin Bitcoin network is able to achieve double spending
attack,if he is able to spend same bitcoins in two different
transactions.A varientof double spending attack is >50%
attack or Goldfinger attack. In this attack, an individual mine
has more than 50% of the computing power of the network
under his control.The probability of >50% attack in Bitcoin
network is very low as it is a very large network.[8].
But IoT networks contains less nodes relative to the Bitcoi
network.If an attacker is able to compromise more than 50%
of the node withoutan abnormalbehavior,then the attacker
will be able to control the entire network.
E. Low-powered IoT devices
In [9],alternative way to implementa public ledger over-
coming the limits ofIoT device constraints is discussed.A
chain is builtusing SHA-256 of length k.This chain is used
to record allthe activities.The value k limits the maximum
size ofthe chunk thatmustbe verified before validating a
given message.Also Etherium can be used as a DB server
by utilizing the existing IoT platform servercalled Mobius
[16].For resource constrained IoT devices to interactwith
blockchain,AlkylVM, a split-virtualmachine based imple-
mentation isdiscussed [13].Each IoT node would run an
instance ofthe VirtualMachine,thatwould allow the node
to access and process it’s own blockchain. A proof of concep
to enable low-power,resource-constrained IoT end-devices
accessing a blockchain-based infrastructure, an IoT gateway
configured as a blockchain node and an event-based messa
ing mechanism in [14].Publisher-Subscriber mechanism with
intermediate servers is found to be efficient for computation
power consuming technologies such as blockchain [15].
III. IDBI OT
In blockchain network,beforeadding anew block to
existing chain ofblocks,each node called as miners in the
network has to solve a mathematical puzzle to prove that th
are valid miners. Usually the puzzle will be like to find a has
value satisfying specified constraints.The energy spenton
solving the puzzle can be spent on computations that secure
the network.
In IDBIoT, each node maintains past records of data stored
in the blockchain.This data contain the information about
nodes in the network,like public key of the nodes,resource
requested by the nodes and the time when the requestwas
made. Data over a long period are gathered together to form
pattern. Every node in the network will monitor their peers b
matching their pattern with the learning model pattern.If the
329
creates a immutable record of events in a distributed network
[7]. Although blockchain is used in decentralized networks,
in [17] a random group mining approach isdiscussed.In
[19],blockchain is used in recommender systems to improve
performance.
B. Issues in IoT Network
Issues in IoT network that are addressed by blockchain are
[10],
• Cloud server’s costand capacity -Blockchain’s decen-
tralized architecture removes the need for a server.
• Deficientarchitecture - Validity of a device’s identity is
verified, transactions are signed and verified cryptograph-
ically.
• Serverdowntimeand unavailability ofservices- No
single pointof failure:Identicalrecords are maintained
by the distributed network.
• Manipulation - Attacker can’tdisruptthe records unless
he owns more computational power in the network.
C. Intrusion Detection
The authors in [1], detects anomaly using mean and standard
deviation ofthe pastdata.If the new datafalls beyond
the confidence range (i.e)mean ± standard deviation the
data is said to be anomalous.If the usage ofthe resources
goesbelow the normalusage,it is not considered asan
anomalous situation for our use case. Data points are clustered
based on similarity to find anomalies.The advantage of this
unsupervised clustering results in no need for a training data
set.A network based intrusion detection is also deployed to
detectthe anomalies,thatuses the originalnetwork packet
as the data source.Network based IDS usually monitors and
analyzes all communication services over the network using a
network adapter running in a random mode.
In [2] intrusion detection is based on density, cluster centers
and Nearest Neighbors.First,clustering is used to obtain dis-
tances and density based on network data to form a new feature
vectorwith low dimension.k-NearestNeighborclassifieris
developed based on the new feature vectors,and the labelis
the outputclass ofdata.Clustering on training setaims to
obtain the cluster center, the nearest neighbors of each sample
point,and the local density of each sample point.
The authorsin [3] proposesa game theoretic approach
for anomaly detection.In this approach,a setof players are
considered representing either an IDS agent or an attacker. The
IDS player, builds a rule related to each new attack’s signature.
The gaming is divided into static game and dynamic game. In
static game,once a playerdecides his strategy,it can’tbe
changed. However,the decision can be changed in a dynamic
game.
In [5] a distributed fog computing technique is used for
intrusion detection.For decreasing the response time,Ex-
treme Machine Learning,a fastlearning algorithm is used.
The sigmoid function provides betteraccuracy and training
time when compared with sine and RadialBasisFunction
(RBF) activation function. To identify malicious nodes within
IoT networks,authors in [6]and [4]employed a Bayesian
based intrusion detection mechanism in which all packets ar
assumed to be independent,irrespective of their origin.
D. Goldfinger attack in Blockchain
The bitcoin is a peer to peer payment network that operat
on cryptographic protocol.Bitcoin transactions are recorded
into distributed database known asthe blockchain through
consensusand Proofof Work (PoW)mechanisms[18].A
clientin Bitcoin network is able to achieve double spending
attack,if he is able to spend same bitcoins in two different
transactions.A varientof double spending attack is >50%
attack or Goldfinger attack. In this attack, an individual mine
has more than 50% of the computing power of the network
under his control.The probability of >50% attack in Bitcoin
network is very low as it is a very large network.[8].
But IoT networks contains less nodes relative to the Bitcoi
network.If an attacker is able to compromise more than 50%
of the node withoutan abnormalbehavior,then the attacker
will be able to control the entire network.
E. Low-powered IoT devices
In [9],alternative way to implementa public ledger over-
coming the limits ofIoT device constraints is discussed.A
chain is builtusing SHA-256 of length k.This chain is used
to record allthe activities.The value k limits the maximum
size ofthe chunk thatmustbe verified before validating a
given message.Also Etherium can be used as a DB server
by utilizing the existing IoT platform servercalled Mobius
[16].For resource constrained IoT devices to interactwith
blockchain,AlkylVM, a split-virtualmachine based imple-
mentation isdiscussed [13].Each IoT node would run an
instance ofthe VirtualMachine,thatwould allow the node
to access and process it’s own blockchain. A proof of concep
to enable low-power,resource-constrained IoT end-devices
accessing a blockchain-based infrastructure, an IoT gateway
configured as a blockchain node and an event-based messa
ing mechanism in [14].Publisher-Subscriber mechanism with
intermediate servers is found to be efficient for computation
power consuming technologies such as blockchain [15].
III. IDBI OT
In blockchain network,beforeadding anew block to
existing chain ofblocks,each node called as miners in the
network has to solve a mathematical puzzle to prove that th
are valid miners. Usually the puzzle will be like to find a has
value satisfying specified constraints.The energy spenton
solving the puzzle can be spent on computations that secure
the network.
In IDBIoT, each node maintains past records of data stored
in the blockchain.This data contain the information about
nodes in the network,like public key of the nodes,resource
requested by the nodes and the time when the requestwas
made. Data over a long period are gathered together to form
pattern. Every node in the network will monitor their peers b
matching their pattern with the learning model pattern.If the
329
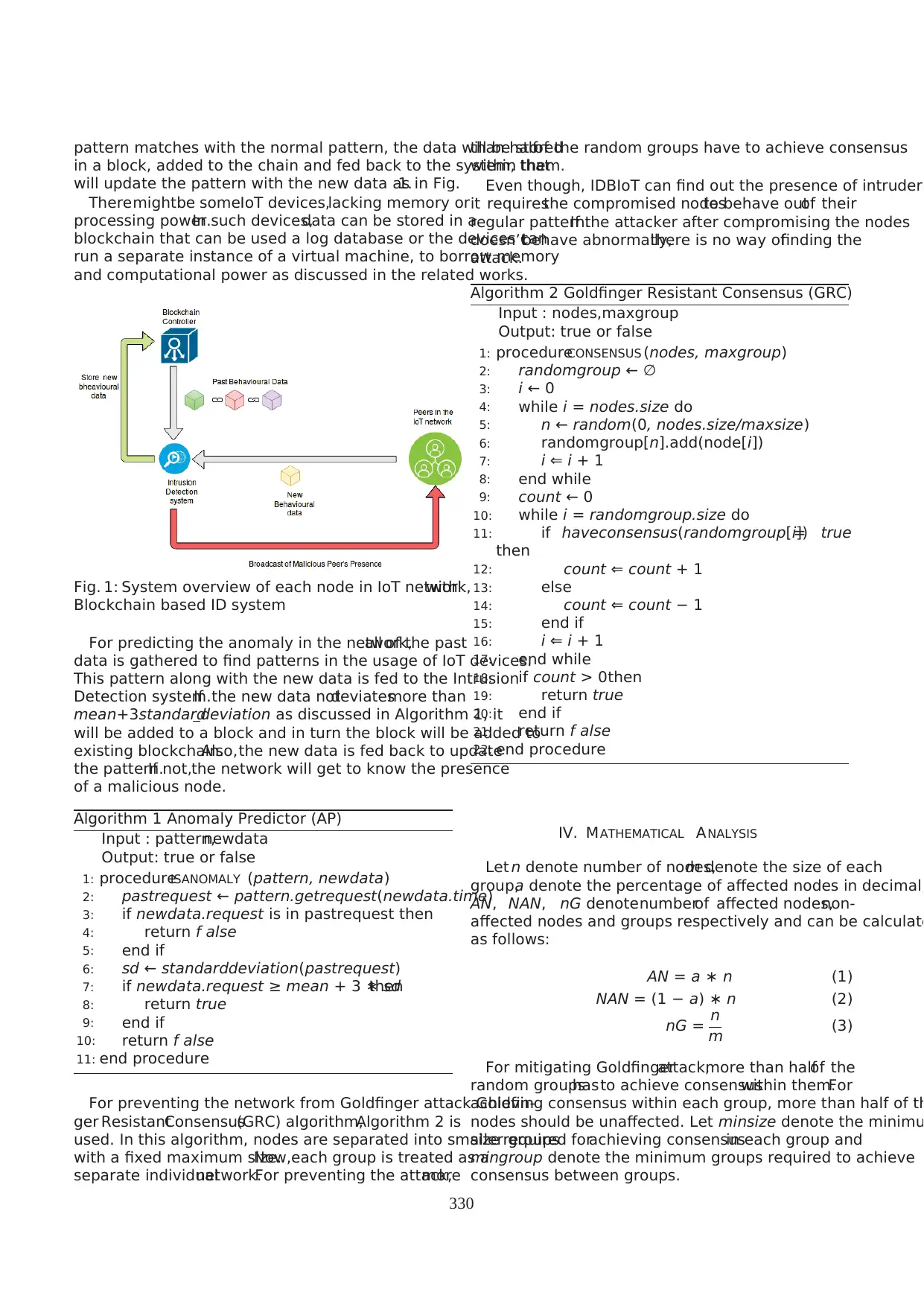
pattern matches with the normal pattern, the data will be stored
in a block, added to the chain and fed back to the system, that
will update the pattern with the new data as in Fig.1.
Theremightbe someIoT devices,lacking memory or
processing power.In such devices,data can be stored in a
blockchain that can be used a log database or the devices can
run a separate instance of a virtual machine, to borrow memory
and computational power as discussed in the related works.
Fig. 1: System overview of each node in IoT network,with
Blockchain based ID system
For predicting the anomaly in the network,all of the past
data is gathered to find patterns in the usage of IoT devices.
This pattern along with the new data is fed to the Intrusion
Detection system.If the new data notdeviatesmore than
mean+3standarddeviation as discussed in Algorithm 1, it
will be added to a block and in turn the block will be added to
existing blockchain.Also,the new data is fed back to update
the pattern.If not,the network will get to know the presence
of a malicious node.
Algorithm 1 Anomaly Predictor (AP)
Input : pattern,newdata
Output: true or false
1: procedureISANOMALY (pattern, newdata)
2: pastrequest ← pattern.getrequest(newdata.time)
3: if newdata.request is in pastrequest then
4: return f alse
5: end if
6: sd ← standarddeviation(pastrequest)
7: if newdata.request ≥ mean + 3 ∗ sdthen
8: return true
9: end if
10: return f alse
11: end procedure
For preventing the network from Goldfinger attack Goldfin-
ger ResistantConsensus(GRC) algorithm,Algorithm 2 is
used. In this algorithm, nodes are separated into smaller groups
with a fixed maximum size.Now,each group is treated as a
separate individualnetwork.For preventing the attack,more
than halfof the random groups have to achieve consensus
within them.
Even though, IDBIoT can find out the presence of intruders
it requiresthe compromised nodesto behave outof their
regular pattern.If the attacker after compromising the nodes
doesn’tbehave abnormally,there is no way offinding the
attack.
Algorithm 2 Goldfinger Resistant Consensus (GRC)
Input : nodes,maxgroup
Output: true or false
1: procedureCONSENSUS (nodes, maxgroup)
2: randomgroup ← ∅
3: i ← 0
4: while i = nodes.size do
5: n ← random(0, nodes.size/maxsize)
6: randomgroup[n].add(node[i])
7: i ⇐ i + 1
8: end while
9: count ← 0
10: while i = randomgroup.size do
11: if haveconsensus(randomgroup[i])= true
then
12: count ⇐ count + 1
13: else
14: count ⇐ count − 1
15: end if
16: i ⇐ i + 1
17: end while
18: if count > 0then
19: return true
20: end if
21: return f alse
22: end procedure
IV. MATHEMATICAL ANALYSIS
Let n denote number of nodes,m denote the size of each
group,a denote the percentage of affected nodes in decimal,
AN, NAN, nG denotenumberof affected nodes,non-
affected nodes and groups respectively and can be calculate
as follows:
AN = a ∗ n (1)
NAN = (1 − a) ∗ n (2)
nG = n
m (3)
For mitigating Goldfingerattack,more than halfof the
random groupshasto achieve consensuswithin them.For
achieving consensus within each group, more than half of th
nodes should be unaffected. Let minsize denote the minimu
size required forachieving consensusin each group and
mingroup denote the minimum groups required to achieve
consensus between groups.
330
in a block, added to the chain and fed back to the system, that
will update the pattern with the new data as in Fig.1.
Theremightbe someIoT devices,lacking memory or
processing power.In such devices,data can be stored in a
blockchain that can be used a log database or the devices can
run a separate instance of a virtual machine, to borrow memory
and computational power as discussed in the related works.
Fig. 1: System overview of each node in IoT network,with
Blockchain based ID system
For predicting the anomaly in the network,all of the past
data is gathered to find patterns in the usage of IoT devices.
This pattern along with the new data is fed to the Intrusion
Detection system.If the new data notdeviatesmore than
mean+3standarddeviation as discussed in Algorithm 1, it
will be added to a block and in turn the block will be added to
existing blockchain.Also,the new data is fed back to update
the pattern.If not,the network will get to know the presence
of a malicious node.
Algorithm 1 Anomaly Predictor (AP)
Input : pattern,newdata
Output: true or false
1: procedureISANOMALY (pattern, newdata)
2: pastrequest ← pattern.getrequest(newdata.time)
3: if newdata.request is in pastrequest then
4: return f alse
5: end if
6: sd ← standarddeviation(pastrequest)
7: if newdata.request ≥ mean + 3 ∗ sdthen
8: return true
9: end if
10: return f alse
11: end procedure
For preventing the network from Goldfinger attack Goldfin-
ger ResistantConsensus(GRC) algorithm,Algorithm 2 is
used. In this algorithm, nodes are separated into smaller groups
with a fixed maximum size.Now,each group is treated as a
separate individualnetwork.For preventing the attack,more
than halfof the random groups have to achieve consensus
within them.
Even though, IDBIoT can find out the presence of intruders
it requiresthe compromised nodesto behave outof their
regular pattern.If the attacker after compromising the nodes
doesn’tbehave abnormally,there is no way offinding the
attack.
Algorithm 2 Goldfinger Resistant Consensus (GRC)
Input : nodes,maxgroup
Output: true or false
1: procedureCONSENSUS (nodes, maxgroup)
2: randomgroup ← ∅
3: i ← 0
4: while i = nodes.size do
5: n ← random(0, nodes.size/maxsize)
6: randomgroup[n].add(node[i])
7: i ⇐ i + 1
8: end while
9: count ← 0
10: while i = randomgroup.size do
11: if haveconsensus(randomgroup[i])= true
then
12: count ⇐ count + 1
13: else
14: count ⇐ count − 1
15: end if
16: i ⇐ i + 1
17: end while
18: if count > 0then
19: return true
20: end if
21: return f alse
22: end procedure
IV. MATHEMATICAL ANALYSIS
Let n denote number of nodes,m denote the size of each
group,a denote the percentage of affected nodes in decimal,
AN, NAN, nG denotenumberof affected nodes,non-
affected nodes and groups respectively and can be calculate
as follows:
AN = a ∗ n (1)
NAN = (1 − a) ∗ n (2)
nG = n
m (3)
For mitigating Goldfingerattack,more than halfof the
random groupshasto achieve consensuswithin them.For
achieving consensus within each group, more than half of th
nodes should be unaffected. Let minsize denote the minimu
size required forachieving consensusin each group and
mingroup denote the minimum groups required to achieve
consensus between groups.
330
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
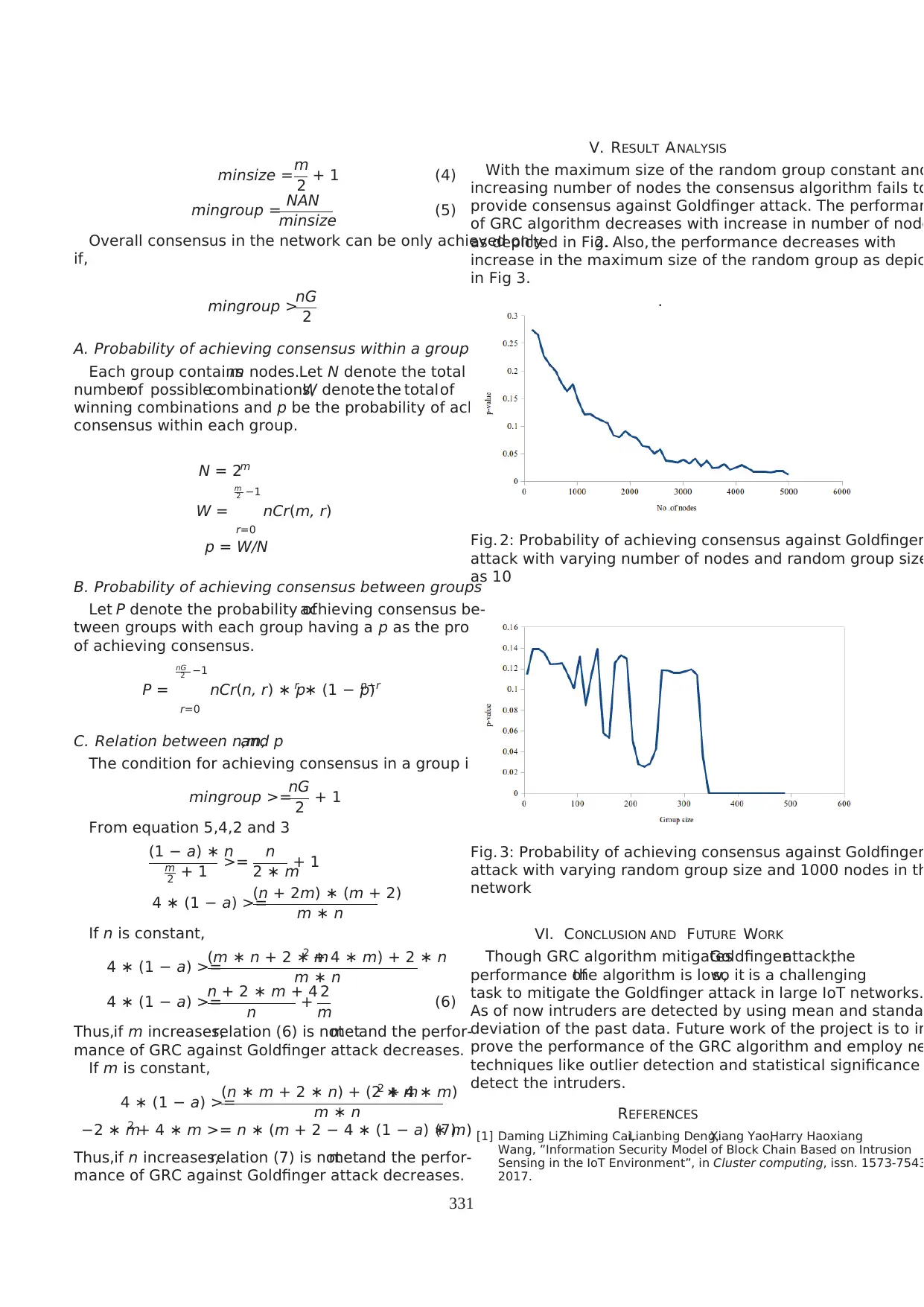
minsize =m
2 + 1 (4)
mingroup = NAN
minsize (5)
Overall consensus in the network can be only achieved only
if,
mingroup >nG
2
A. Probability of achieving consensus within a group
Each group containsm nodes.Let N denote the total
numberof possiblecombinations,W denote the totalof
winning combinations and p be the probability of achieving
consensus within each group.
N = 2m
W =
m
2 −1
r=0
nCr(m, r)
p = W/N
B. Probability of achieving consensus between groups
Let P denote the probability ofachieving consensus be-
tween groups with each group having a p as the probability
of achieving consensus.
P =
nG
2 −1
r=0
nCr(n, r) ∗ pr ∗ (1 − p)n−r
C. Relation between n,m,and p
The condition for achieving consensus in a group is,
mingroup >=
nG
2 + 1
From equation 5,4,2 and 3
(1 − a) ∗ n
m
2 + 1 >= n
2 ∗ m
+ 1
4 ∗ (1 − a) >=
(n + 2m) ∗ (m + 2)
m ∗ n
If n is constant,
4 ∗ (1 − a) >=
(m ∗ n + 2 ∗ m2 + 4 ∗ m) + 2 ∗ n
m ∗ n
4 ∗ (1 − a) >=
n + 2 ∗ m + 4
n + 2
m (6)
Thus,if m increases,relation (6) is notmetand the perfor-
mance of GRC against Goldfinger attack decreases.
If m is constant,
4 ∗ (1 − a) >=
(n ∗ m + 2 ∗ n) + (2 ∗ m2 + 4 ∗ m)
m ∗ n
−2 ∗ m2 + 4 ∗ m >= n ∗ (m + 2 − 4 ∗ (1 − a) ∗ m)(7)
Thus,if n increases,relation (7) is notmetand the perfor-
mance of GRC against Goldfinger attack decreases.
V. RESULT ANALYSIS
With the maximum size of the random group constant and
increasing number of nodes the consensus algorithm fails to
provide consensus against Goldfinger attack. The performan
of GRC algorithm decreases with increase in number of node
as depicted in Fig.2. Also, the performance decreases with
increase in the maximum size of the random group as depic
in Fig 3.
.
Fig. 2: Probability of achieving consensus against Goldfinger
attack with varying number of nodes and random group size
as 10
Fig. 3: Probability of achieving consensus against Goldfinger
attack with varying random group size and 1000 nodes in th
network
VI. CONCLUSION AND FUTURE WORK
Though GRC algorithm mitigatesGoldfingerattack,the
performance ofthe algorithm is low,so it is a challenging
task to mitigate the Goldfinger attack in large IoT networks.
As of now intruders are detected by using mean and standa
deviation of the past data. Future work of the project is to im
prove the performance of the GRC algorithm and employ ne
techniques like outlier detection and statistical significance
detect the intruders.
REFERENCES
[1] Daming Li,Zhiming Cai,Lianbing Deng,Xiang Yao,Harry Haoxiang
Wang, ”Information Security Model of Block Chain Based on Intrusion
Sensing in the IoT Environment”, in Cluster computing, issn. 1573-7543
2017.
331
2 + 1 (4)
mingroup = NAN
minsize (5)
Overall consensus in the network can be only achieved only
if,
mingroup >nG
2
A. Probability of achieving consensus within a group
Each group containsm nodes.Let N denote the total
numberof possiblecombinations,W denote the totalof
winning combinations and p be the probability of achieving
consensus within each group.
N = 2m
W =
m
2 −1
r=0
nCr(m, r)
p = W/N
B. Probability of achieving consensus between groups
Let P denote the probability ofachieving consensus be-
tween groups with each group having a p as the probability
of achieving consensus.
P =
nG
2 −1
r=0
nCr(n, r) ∗ pr ∗ (1 − p)n−r
C. Relation between n,m,and p
The condition for achieving consensus in a group is,
mingroup >=
nG
2 + 1
From equation 5,4,2 and 3
(1 − a) ∗ n
m
2 + 1 >= n
2 ∗ m
+ 1
4 ∗ (1 − a) >=
(n + 2m) ∗ (m + 2)
m ∗ n
If n is constant,
4 ∗ (1 − a) >=
(m ∗ n + 2 ∗ m2 + 4 ∗ m) + 2 ∗ n
m ∗ n
4 ∗ (1 − a) >=
n + 2 ∗ m + 4
n + 2
m (6)
Thus,if m increases,relation (6) is notmetand the perfor-
mance of GRC against Goldfinger attack decreases.
If m is constant,
4 ∗ (1 − a) >=
(n ∗ m + 2 ∗ n) + (2 ∗ m2 + 4 ∗ m)
m ∗ n
−2 ∗ m2 + 4 ∗ m >= n ∗ (m + 2 − 4 ∗ (1 − a) ∗ m)(7)
Thus,if n increases,relation (7) is notmetand the perfor-
mance of GRC against Goldfinger attack decreases.
V. RESULT ANALYSIS
With the maximum size of the random group constant and
increasing number of nodes the consensus algorithm fails to
provide consensus against Goldfinger attack. The performan
of GRC algorithm decreases with increase in number of node
as depicted in Fig.2. Also, the performance decreases with
increase in the maximum size of the random group as depic
in Fig 3.
.
Fig. 2: Probability of achieving consensus against Goldfinger
attack with varying number of nodes and random group size
as 10
Fig. 3: Probability of achieving consensus against Goldfinger
attack with varying random group size and 1000 nodes in th
network
VI. CONCLUSION AND FUTURE WORK
Though GRC algorithm mitigatesGoldfingerattack,the
performance ofthe algorithm is low,so it is a challenging
task to mitigate the Goldfinger attack in large IoT networks.
As of now intruders are detected by using mean and standa
deviation of the past data. Future work of the project is to im
prove the performance of the GRC algorithm and employ ne
techniques like outlier detection and statistical significance
detect the intruders.
REFERENCES
[1] Daming Li,Zhiming Cai,Lianbing Deng,Xiang Yao,Harry Haoxiang
Wang, ”Information Security Model of Block Chain Based on Intrusion
Sensing in the IoT Environment”, in Cluster computing, issn. 1573-7543
2017.
331
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

[2] Xiujuan Wang, Chenxi Zhang and Kangfeng Zheng, ”Intrusion detection
algorithm based on density,cluster centers,and nearestneighbors,” in
China Communications,vol.13,no.7, pp.24-31,Jul. 2016.
[3] H. Sedjelmaci, S. M. Senouci and T. Taleb, ”An Accurate Security Game
for Low-Resource IoT Devices,” in IEEE Transactions on Vehicular
Technology,vol.66,no.10,pp.9381-9393,Oct.2017.
[4] W. Meng,W. Li, C. Su,J. Zhou and R.Lu, ”Enhancing Trust Manage-
mentfor Wireless Intrusion Detection via Traffic Sampling in the Era
of Big Data,” in IEEE Access,vol.6, pp.7234-7243,2018.
[5] S. Prabavathy,K. Sundarakantham and S.M. Shalinie,”Design of
cognitive fog computing for intrusion detection in Internet of Things,” in
Journal of Communications and Networks,vol.20,no.3, pp.291-298,
Jun. 2018.
[6] W. Meng,”Intrusion Detection in the Era ofIoT: Building Trustvia
Traffic Filtering and Sampling,” in Computer,vol. 51,no.7, pp.36-43,
Jul. 2018.
[7] T. Aste,P. Tasca and T.Di Matteo,”Blockchain Technologies:The
Foreseeable Impact on Society and Industry,” in Computer, vol. 50, no.
9, pp.18-28,2017.
[8] M. Conti, S. K. E, C. Lal and S. Ruj, ”A Survey on Security and Privacy
Issues of Bitcoin,” in IEEE Communications Surveys and Tutorials.
[9] Francesco Buccafurri,Gianluca Lax,Serena Nicolazzo,and Antonino
Nocera,”Overcoming limits ofBlockchain forIoT Applications”,in
Proceedingsof the 12th InternationalConferenceon Availability,
Reliability and Security (ARES ’17).ACM, New York,NY,USA,2017.
[10] T. M. Fern´andez-Caram´es and P.Fraga-Lamas,”A Review on the Use
of Blockchain for the Internetof Things,” in IEEE Access,vol. 6, pp.
32979-33001,2018.
[11] N. Kshetri, ”Can Blockchain Strengthen the Internet of Things?,” in IT
Professional,vol.19,no.4, pp.68-72,2017.
[12] M. Singh,A. Singh and S.Kim, ”Blockchain:A game changerfor
securing IoT data,” inIEEE 4th World Forum on Internetof Things
(WF-IoT),Singapore,,pp.51-55,2018.
[13] J. Ellul and G. J. Pace, ”AlkylVM: A Virtual Machine for Smart Contract
Blockchain Connected Internetof Things,” in 9th IFIP International
Conference on New Technologies, Mobility and Security (NTMS), Paris,,
pp.1-4,2018.
[14] K. R. ¨Ozyılmaz and A.Yurdakul,”Work-in-progress:integrating low-
power IoT devices to a blockchain-based infrastructure,” in Internationa
Conference on Embedded Software (EMSOFT),Seoul,,pp.1-2,2017.
[15] N. Rifi, E. Rachkidi,N. Agoulmine and N.C. Taher,”Towards using
blockchain technology forIoT data access protection,” in IEEE 17th
International Conference on Ubiquitous Wireless Broadband (ICUWB),
Salamanca,,pp.1-5,2017.
[16] J. H. Jeon, K. Kim and J. Kim, ”Block chain based data security
enhanced IoT server platform,” International Conference on Information
Networking (ICOIN),Chiang Mai,2018,pp.941-944,2018.
[17] J.Bae and H.Lim, ”Random Mining Group Selection to Prevent51%
Attacks on Bitcoin,” in 48th Annual IEEE/IFIP International Conference
on Dependable Systemsand NetworksWorkshops(DSN-W),Luxem-
bourg City,pp.81-82,2018.
[18] S. Nakamoto,“Bitcoin: A peer-to-peer electronic cash system,” 2008.
[19] A. M. Saghiri, M. Vahdati, K. Gholizadeh, M. R. Meybodi, M. Dehghan
and H. Rashidi, ”A framework for cognitive Internet of Things based on
blockchain,” in 4th International Conference on Web Research (ICWR),
Tehran,,pp.138-143,2018.
[20] O. Alphand et al., ”IoTChain: A blockchain security architecture for the
Internet of Things,” in IEEE Wireless Communications and Networking
Conference (WCNC),Barcelona,,pp.1-6,2018.
332
algorithm based on density,cluster centers,and nearestneighbors,” in
China Communications,vol.13,no.7, pp.24-31,Jul. 2016.
[3] H. Sedjelmaci, S. M. Senouci and T. Taleb, ”An Accurate Security Game
for Low-Resource IoT Devices,” in IEEE Transactions on Vehicular
Technology,vol.66,no.10,pp.9381-9393,Oct.2017.
[4] W. Meng,W. Li, C. Su,J. Zhou and R.Lu, ”Enhancing Trust Manage-
mentfor Wireless Intrusion Detection via Traffic Sampling in the Era
of Big Data,” in IEEE Access,vol.6, pp.7234-7243,2018.
[5] S. Prabavathy,K. Sundarakantham and S.M. Shalinie,”Design of
cognitive fog computing for intrusion detection in Internet of Things,” in
Journal of Communications and Networks,vol.20,no.3, pp.291-298,
Jun. 2018.
[6] W. Meng,”Intrusion Detection in the Era ofIoT: Building Trustvia
Traffic Filtering and Sampling,” in Computer,vol. 51,no.7, pp.36-43,
Jul. 2018.
[7] T. Aste,P. Tasca and T.Di Matteo,”Blockchain Technologies:The
Foreseeable Impact on Society and Industry,” in Computer, vol. 50, no.
9, pp.18-28,2017.
[8] M. Conti, S. K. E, C. Lal and S. Ruj, ”A Survey on Security and Privacy
Issues of Bitcoin,” in IEEE Communications Surveys and Tutorials.
[9] Francesco Buccafurri,Gianluca Lax,Serena Nicolazzo,and Antonino
Nocera,”Overcoming limits ofBlockchain forIoT Applications”,in
Proceedingsof the 12th InternationalConferenceon Availability,
Reliability and Security (ARES ’17).ACM, New York,NY,USA,2017.
[10] T. M. Fern´andez-Caram´es and P.Fraga-Lamas,”A Review on the Use
of Blockchain for the Internetof Things,” in IEEE Access,vol. 6, pp.
32979-33001,2018.
[11] N. Kshetri, ”Can Blockchain Strengthen the Internet of Things?,” in IT
Professional,vol.19,no.4, pp.68-72,2017.
[12] M. Singh,A. Singh and S.Kim, ”Blockchain:A game changerfor
securing IoT data,” inIEEE 4th World Forum on Internetof Things
(WF-IoT),Singapore,,pp.51-55,2018.
[13] J. Ellul and G. J. Pace, ”AlkylVM: A Virtual Machine for Smart Contract
Blockchain Connected Internetof Things,” in 9th IFIP International
Conference on New Technologies, Mobility and Security (NTMS), Paris,,
pp.1-4,2018.
[14] K. R. ¨Ozyılmaz and A.Yurdakul,”Work-in-progress:integrating low-
power IoT devices to a blockchain-based infrastructure,” in Internationa
Conference on Embedded Software (EMSOFT),Seoul,,pp.1-2,2017.
[15] N. Rifi, E. Rachkidi,N. Agoulmine and N.C. Taher,”Towards using
blockchain technology forIoT data access protection,” in IEEE 17th
International Conference on Ubiquitous Wireless Broadband (ICUWB),
Salamanca,,pp.1-5,2017.
[16] J. H. Jeon, K. Kim and J. Kim, ”Block chain based data security
enhanced IoT server platform,” International Conference on Information
Networking (ICOIN),Chiang Mai,2018,pp.941-944,2018.
[17] J.Bae and H.Lim, ”Random Mining Group Selection to Prevent51%
Attacks on Bitcoin,” in 48th Annual IEEE/IFIP International Conference
on Dependable Systemsand NetworksWorkshops(DSN-W),Luxem-
bourg City,pp.81-82,2018.
[18] S. Nakamoto,“Bitcoin: A peer-to-peer electronic cash system,” 2008.
[19] A. M. Saghiri, M. Vahdati, K. Gholizadeh, M. R. Meybodi, M. Dehghan
and H. Rashidi, ”A framework for cognitive Internet of Things based on
blockchain,” in 4th International Conference on Web Research (ICWR),
Tehran,,pp.138-143,2018.
[20] O. Alphand et al., ”IoTChain: A blockchain security architecture for the
Internet of Things,” in IEEE Wireless Communications and Networking
Conference (WCNC),Barcelona,,pp.1-6,2018.
332
1 out of 5
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.



