IFN701: Investigation into Security of Mobile Apps Report
VerifiedAdded on 2022/10/17
|37
|9059
|259
Report
AI Summary
This report provides a comprehensive investigation into the security of mobile applications, addressing the growing importance of mobile technology in business and daily life. It explores the evolution of mobile applications, from standalone phones to smartphones and IoT devices, and highlights the increasing security risks associated with these technologies. The report delves into various aspects of mobile app security, including vulnerabilities, threats, and countermeasures, such as unit testing, system testing, and the implementation of security policies. It examines research questions related to the security of mobile applications, including the effectiveness of existing security measures, user awareness of security obligations, and the monitoring of security documents. The report also covers methodologies, including the Waterfall model, and discusses the need for continuous review and adaptation of security measures to address emerging threats. Furthermore, the report analyzes the risks associated with mobile apps, focusing on the Android platform, and offers recommendations for enhancing mobile app security, making this a valuable resource for understanding and mitigating the risks associated with mobile app usage.

Running Head: INVESTIGATION INTO SECURITY OF MOBILE APPS 1
An Investigation into the Security of Mobile Phone Communication Apps
Affiliate Institution
Professor’s Name
Student
Date
An Investigation into the Security of Mobile Phone Communication Apps
Affiliate Institution
Professor’s Name
Student
Date
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

INVESTIGATION INTO SECURITY OF MOBILE APPS 2
1.0 Abstract
Information technology is currently widely used all over the world. Technology has made
everything possible and more so has led to improved business standards. Most companies across
the globe have embraced the use of technology to improve their business productivity.
Technology is advancing at a higher rate such that mobile application which will help us to run
our business anywhere we are in have been developed. For this reason, we can manage our
businesses anywhere on the earth surface so long as we are connected to the internet.
Using mobile applications, we can communicate vividly with our customers and as well with our
company employees. Technology advances from a standalone mobile phone, and now we are in
the era of smartphones. With the use of mobile phones such as tablets, IPad, iPhone or
Smartphones, we can carry on with our usual businesses as if we are in office. Even while
transacting, everything is done over the internet. (Wang & Lau, n.d.)
Internet of Things (IoT) is a technology which has enabled us to manage our businesses
everywhere across the earth surface. Through the technology we are connected as one village
even if we are far from each other. The only thing which IoT has done is building trust that we
can do anything over the internet. (Velu, 2016)
In this project report, we will deal with security issues on the mobile application we are using to
transact our businesses. We will ask ourselves some questions before the implementation of this
project. The kind of questions includes; how secure are we to employ these mobile applications
technologies? Is the mobile application reliable to our day to day business processes? What are
the impacts and benefits of the mobile app to the business processes? Does the mobile
1.0 Abstract
Information technology is currently widely used all over the world. Technology has made
everything possible and more so has led to improved business standards. Most companies across
the globe have embraced the use of technology to improve their business productivity.
Technology is advancing at a higher rate such that mobile application which will help us to run
our business anywhere we are in have been developed. For this reason, we can manage our
businesses anywhere on the earth surface so long as we are connected to the internet.
Using mobile applications, we can communicate vividly with our customers and as well with our
company employees. Technology advances from a standalone mobile phone, and now we are in
the era of smartphones. With the use of mobile phones such as tablets, IPad, iPhone or
Smartphones, we can carry on with our usual businesses as if we are in office. Even while
transacting, everything is done over the internet. (Wang & Lau, n.d.)
Internet of Things (IoT) is a technology which has enabled us to manage our businesses
everywhere across the earth surface. Through the technology we are connected as one village
even if we are far from each other. The only thing which IoT has done is building trust that we
can do anything over the internet. (Velu, 2016)
In this project report, we will deal with security issues on the mobile application we are using to
transact our businesses. We will ask ourselves some questions before the implementation of this
project. The kind of questions includes; how secure are we to employ these mobile applications
technologies? Is the mobile application reliable to our day to day business processes? What are
the impacts and benefits of the mobile app to the business processes? Does the mobile

INVESTIGATION INTO SECURITY OF MOBILE APPS 3
application receive a positive response from the customers? At what cost does it incur to be
developed?
After discussing the questions, the problem is given a solution to ensure that all the requirements
have been achieved. (Thuraisingham, 2001) The project team members will have to use these
research questions to clearly understand the customer requirements and how secure will be the
system after the solution have been provided. Finally, detectives which will help to detect these
threats will be established so that the threats will be blocked before harming the system.
application receive a positive response from the customers? At what cost does it incur to be
developed?
After discussing the questions, the problem is given a solution to ensure that all the requirements
have been achieved. (Thuraisingham, 2001) The project team members will have to use these
research questions to clearly understand the customer requirements and how secure will be the
system after the solution have been provided. Finally, detectives which will help to detect these
threats will be established so that the threats will be blocked before harming the system.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

INVESTIGATION INTO SECURITY OF MOBILE APPS 4
Table of Contents
1.0 Abstract.................................................................................................................................................2
2.0 Introduction...........................................................................................................................................6
2.1 The purpose of the Research.............................................................................................................7
2.2 Research Scope..................................................................................................................................8
2.1 Project Background............................................................................................................................8
2.2 Research Questions...........................................................................................................................9
3.0 Literature review.................................................................................................................................11
4.0 Methodology.......................................................................................................................................12
4.1 Waterfall Model...............................................................................................................................13
4.1.0 Project Planning........................................................................................................................13
4.1.1 Requirements definition...........................................................................................................14
4.1.2 System design...........................................................................................................................14
Design view of how weekly report will be done................................................................................15
4.1.3 Research development process................................................................................................15
4.1.4 Integration and Testing.............................................................................................................15
4.1.5 Installation and Acceptance......................................................................................................15
4.1 Work Break-Down Structure and Weekly Plan................................................................................16
4.1.6 Communication Plan.....................................................................................................................17
5.0 Literature Review Results....................................................................................................................18
5.1 Mobile application...........................................................................................................................18
5.2 Mobile application system vulnerabilities.......................................................................................19
5.3 Mobile Application Testing Method................................................................................................20
5.4 Mobile Application Approval or Rejection.......................................................................................21
5.5 Risks and threats model...................................................................................................................23
5.6 Results Analysis...............................................................................................................................25
5.7 Tools and Services used...................................................................................................................26
6.0 Discussion............................................................................................................................................27
6.1.0 Source Code Testing.....................................................................................................................27
6.2.0 Correctness Testing Method.........................................................................................................28
6.2.0 Managing and Un-mapping Mobile Applications..........................................................................29
6.3.0 Limitation of Approving or Rejecting the Mobile Apps.................................................................30
Table of Contents
1.0 Abstract.................................................................................................................................................2
2.0 Introduction...........................................................................................................................................6
2.1 The purpose of the Research.............................................................................................................7
2.2 Research Scope..................................................................................................................................8
2.1 Project Background............................................................................................................................8
2.2 Research Questions...........................................................................................................................9
3.0 Literature review.................................................................................................................................11
4.0 Methodology.......................................................................................................................................12
4.1 Waterfall Model...............................................................................................................................13
4.1.0 Project Planning........................................................................................................................13
4.1.1 Requirements definition...........................................................................................................14
4.1.2 System design...........................................................................................................................14
Design view of how weekly report will be done................................................................................15
4.1.3 Research development process................................................................................................15
4.1.4 Integration and Testing.............................................................................................................15
4.1.5 Installation and Acceptance......................................................................................................15
4.1 Work Break-Down Structure and Weekly Plan................................................................................16
4.1.6 Communication Plan.....................................................................................................................17
5.0 Literature Review Results....................................................................................................................18
5.1 Mobile application...........................................................................................................................18
5.2 Mobile application system vulnerabilities.......................................................................................19
5.3 Mobile Application Testing Method................................................................................................20
5.4 Mobile Application Approval or Rejection.......................................................................................21
5.5 Risks and threats model...................................................................................................................23
5.6 Results Analysis...............................................................................................................................25
5.7 Tools and Services used...................................................................................................................26
6.0 Discussion............................................................................................................................................27
6.1.0 Source Code Testing.....................................................................................................................27
6.2.0 Correctness Testing Method.........................................................................................................28
6.2.0 Managing and Un-mapping Mobile Applications..........................................................................29
6.3.0 Limitation of Approving or Rejecting the Mobile Apps.................................................................30
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

INVESTIGATION INTO SECURITY OF MOBILE APPS 5
7.0 Reflection of the research...................................................................................................................31
Conclusion.................................................................................................................................................34
References.................................................................................................................................................36
7.0 Reflection of the research...................................................................................................................31
Conclusion.................................................................................................................................................34
References.................................................................................................................................................36

INVESTIGATION INTO SECURITY OF MOBILE APPS 6
2.0 Introduction
Mobile communication is currently the most rapidly growing technology as the world is
targeting every work will in the near future be done at the palm of your hand. The current market
trend for mobile application technologies such as android applications, apple store for IPhone
and many more to name but few are rapidly growing at an alarming rate. As we can witness that
within a short period of time after the release of the handy cell phones, smartphones, tablets,
iPhone and iPad came into being. This is evidence in the sense that mobile technology is
constantly changing over time. (Thuraisingham, 2001)
The change is growing faster because it has caught the warm in the market where every person is
in high demand for it. When the internet was embedded on mobile devices, so many people gain
a higher preference for purchasing a mobile device rather than buying a desktop or laptop
computer. Smartphones this day serve so many transactions, including online payments.
How Mobile Application works
2.0 Introduction
Mobile communication is currently the most rapidly growing technology as the world is
targeting every work will in the near future be done at the palm of your hand. The current market
trend for mobile application technologies such as android applications, apple store for IPhone
and many more to name but few are rapidly growing at an alarming rate. As we can witness that
within a short period of time after the release of the handy cell phones, smartphones, tablets,
iPhone and iPad came into being. This is evidence in the sense that mobile technology is
constantly changing over time. (Thuraisingham, 2001)
The change is growing faster because it has caught the warm in the market where every person is
in high demand for it. When the internet was embedded on mobile devices, so many people gain
a higher preference for purchasing a mobile device rather than buying a desktop or laptop
computer. Smartphones this day serve so many transactions, including online payments.
How Mobile Application works
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

INVESTIGATION INTO SECURITY OF MOBILE APPS 7
This report explains various issues which we may encounter with the use of the mobile
application and the countermeasures we can use to control them. (Mukherjea, n.d.) An
investigation will be carried out to check whether the use of mobile application technology to
transact our business is safe or not.
The most crucial aspect of the implementation of technology is security. Developing a mobile
application without considering its security is a waste of time as a resource. We can ensure that
the mobile application is secure enough by employing various techniques such as unit testing or
system testing. Unit testing is a technique done by programmers during the development stage of
the application, while system testing is done after the development process by testers. This kind
of exercise will help to ensure that the programs we will be deploying for first use are safe and
secure. Also, developing mobile applications is not like in the past. The mobile phone is also
changing their compatibility features like 2G, 3G, 4G and currently we are migrating to the fifth-
generation (5G), WPS Wi-Fi security settings, Bluetooth and NFC. All these are the mobile
application technologies to enhance the security and the functionality of mobile devices. (Makan,
2013) This is in conjunction with the internet of things, and that is the reason why we are
regarding them as an IoT device.
Day in day out, we hear of cases of system hacking. This means that these mobile applications
are not secure at all. This project will expound more on these threats that are affecting our mobile
application systems.
2.1 The purpose of the Research
This record characterizes a mobile application checking process and gives direction in planning
and actualizing an application security process, creating security prerequisites for mobile
applications, recognizing suitable instruments for testing mobile applications and deciding
This report explains various issues which we may encounter with the use of the mobile
application and the countermeasures we can use to control them. (Mukherjea, n.d.) An
investigation will be carried out to check whether the use of mobile application technology to
transact our business is safe or not.
The most crucial aspect of the implementation of technology is security. Developing a mobile
application without considering its security is a waste of time as a resource. We can ensure that
the mobile application is secure enough by employing various techniques such as unit testing or
system testing. Unit testing is a technique done by programmers during the development stage of
the application, while system testing is done after the development process by testers. This kind
of exercise will help to ensure that the programs we will be deploying for first use are safe and
secure. Also, developing mobile applications is not like in the past. The mobile phone is also
changing their compatibility features like 2G, 3G, 4G and currently we are migrating to the fifth-
generation (5G), WPS Wi-Fi security settings, Bluetooth and NFC. All these are the mobile
application technologies to enhance the security and the functionality of mobile devices. (Makan,
2013) This is in conjunction with the internet of things, and that is the reason why we are
regarding them as an IoT device.
Day in day out, we hear of cases of system hacking. This means that these mobile applications
are not secure at all. This project will expound more on these threats that are affecting our mobile
application systems.
2.1 The purpose of the Research
This record characterizes a mobile application checking process and gives direction in planning
and actualizing an application security process, creating security prerequisites for mobile
applications, recognizing suitable instruments for testing mobile applications and deciding
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
INVESTIGATION INTO SECURITY OF MOBILE APPS 8
whether a handy application is satisfactory for arrangement on an association's cell phones. An
outline of methods usually utilized by programming confirmation experts is given, including
techniques for testing for discrete mobile application vulnerabilities and misconfigurations
identified with mobile application software. (Hoog, 2011)
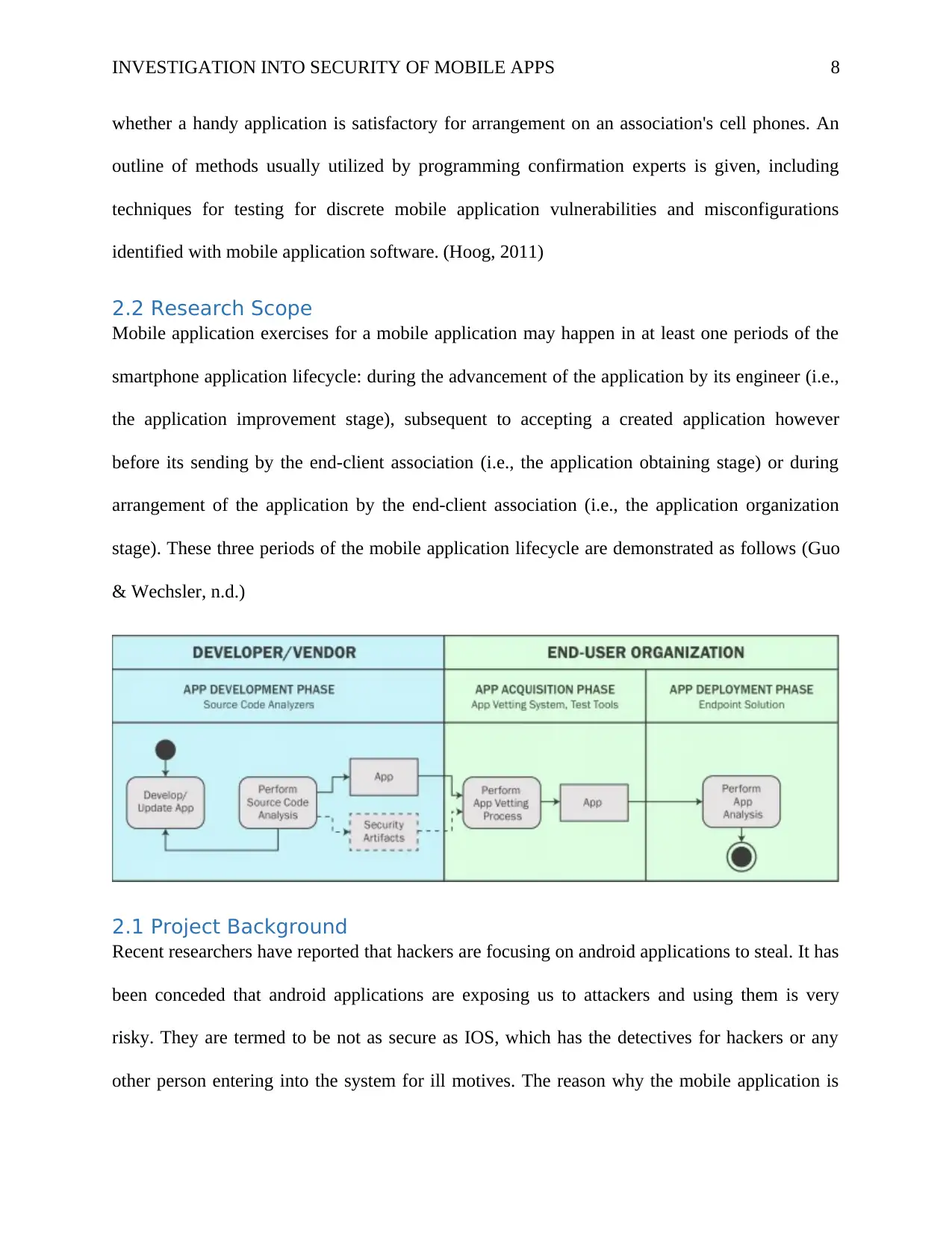
2.2 Research Scope
Mobile application exercises for a mobile application may happen in at least one periods of the
smartphone application lifecycle: during the advancement of the application by its engineer (i.e.,
the application improvement stage), subsequent to accepting a created application however
before its sending by the end-client association (i.e., the application obtaining stage) or during
arrangement of the application by the end-client association (i.e., the application organization
stage). These three periods of the mobile application lifecycle are demonstrated as follows (Guo
& Wechsler, n.d.)
2.1 Project Background
Recent researchers have reported that hackers are focusing on android applications to steal. It has
been conceded that android applications are exposing us to attackers and using them is very
risky. They are termed to be not as secure as IOS, which has the detectives for hackers or any
other person entering into the system for ill motives. The reason why the mobile application is
whether a handy application is satisfactory for arrangement on an association's cell phones. An
outline of methods usually utilized by programming confirmation experts is given, including
techniques for testing for discrete mobile application vulnerabilities and misconfigurations
identified with mobile application software. (Hoog, 2011)
2.2 Research Scope
Mobile application exercises for a mobile application may happen in at least one periods of the
smartphone application lifecycle: during the advancement of the application by its engineer (i.e.,
the application improvement stage), subsequent to accepting a created application however
before its sending by the end-client association (i.e., the application obtaining stage) or during
arrangement of the application by the end-client association (i.e., the application organization
stage). These three periods of the mobile application lifecycle are demonstrated as follows (Guo
& Wechsler, n.d.)
2.1 Project Background
Recent researchers have reported that hackers are focusing on android applications to steal. It has
been conceded that android applications are exposing us to attackers and using them is very
risky. They are termed to be not as secure as IOS, which has the detectives for hackers or any
other person entering into the system for ill motives. The reason why the mobile application is

INVESTIGATION INTO SECURITY OF MOBILE APPS 9
becoming a target is that the users are very many. (Chandra, 2009) This means that the system
has a complexity of users, making it more vulnerable to the attackers.
Android application systems for android phone are prone to expose us to spyware programs
which hackers usually use them to steal from our systems. So android must be dealt with in-
depth so that its security features can be improved.
2.2 Research Questions
What policies, guidelines and procedures have been established to ensure that our mobile
applications are secure?
The risk analysis report design by our team of security experts will have to indicate all the
possible procedures and policies established so that it can help us in ensuring that our mobile
applications are totally secure. We are in tandem that our mobile application software, especially
android application, are exposing us to be insecure. (Abraham & Dalziel, n.d.) A number of
people regularly experience a lack of IT security by getting conned over the mobile systems
ending up losing their money or any other property.
Policies and guidelines will help the users to protect the integrity of the company by following
the right procedure while using mobile applications. Every organization will have to set up IT
policies and regulation through which every user has to follow at its latter. (Abraham & Dalziel,
n.d.)
Do the existing security policy/procedures/guidelines adequately state what is allowed or
not allowed to do?
The audit team will be considering the already set rules and procedures which are currently in
use in regards to mobile application procedures of use. In a company, users are trained and given
becoming a target is that the users are very many. (Chandra, 2009) This means that the system
has a complexity of users, making it more vulnerable to the attackers.
Android application systems for android phone are prone to expose us to spyware programs
which hackers usually use them to steal from our systems. So android must be dealt with in-
depth so that its security features can be improved.
2.2 Research Questions
What policies, guidelines and procedures have been established to ensure that our mobile
applications are secure?
The risk analysis report design by our team of security experts will have to indicate all the
possible procedures and policies established so that it can help us in ensuring that our mobile
applications are totally secure. We are in tandem that our mobile application software, especially
android application, are exposing us to be insecure. (Abraham & Dalziel, n.d.) A number of
people regularly experience a lack of IT security by getting conned over the mobile systems
ending up losing their money or any other property.
Policies and guidelines will help the users to protect the integrity of the company by following
the right procedure while using mobile applications. Every organization will have to set up IT
policies and regulation through which every user has to follow at its latter. (Abraham & Dalziel,
n.d.)
Do the existing security policy/procedures/guidelines adequately state what is allowed or
not allowed to do?
The audit team will be considering the already set rules and procedures which are currently in
use in regards to mobile application procedures of use. In a company, users are trained and given
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

INVESTIGATION INTO SECURITY OF MOBILE APPS 10
instructions on what to do and not to do. IT risk management department will have to ensure that
the users are trained well in the issues related to security threats. They must be made aware of
various people who may use them to steal the company's property. They should get to know that
their passwords shall never be disclosed to anybody. (Abraham & Dalziel, n.d.)
Protecting the integrity of the system by the staff will enable a strong, secure environment to
carry out daily activities without trials from attackers and red had hackers. As we have seen that
mobile applications are the most affected systems when it comes to security breaches and
hacking. Also, users must be provided strictly with company phones with protected passwords
assigned to each staff. The passwords will be controlled from the main admin system to ensure
that the system integrity is maintained.
Are the users aware of the obligation with regard to the accepted company laws, security
policy and procedures before the access rights are given?
The report will find out if the mobile application users have been made aware of the guidelines
which must be followed keenly. The research team will be able to explain that in detail and what
are the possible consequences to be made in case the staff failed to adhere to the laws provided.
Therefore, in case there is no such guidelines, the team will provide them in the report so that the
management team can implement the same to ensure that the company is running smoothly. By
provisioning, these guidelines to the staff will help to mitigate stealing from the users themselves
However, there is a need in looking into external security as some experts may use some
software call spyware to intrude into the system and steal money or data. Remember the mobile
application has a user end which resides on a mobile phone, but the backend is in the powerful
instructions on what to do and not to do. IT risk management department will have to ensure that
the users are trained well in the issues related to security threats. They must be made aware of
various people who may use them to steal the company's property. They should get to know that
their passwords shall never be disclosed to anybody. (Abraham & Dalziel, n.d.)
Protecting the integrity of the system by the staff will enable a strong, secure environment to
carry out daily activities without trials from attackers and red had hackers. As we have seen that
mobile applications are the most affected systems when it comes to security breaches and
hacking. Also, users must be provided strictly with company phones with protected passwords
assigned to each staff. The passwords will be controlled from the main admin system to ensure
that the system integrity is maintained.
Are the users aware of the obligation with regard to the accepted company laws, security
policy and procedures before the access rights are given?
The report will find out if the mobile application users have been made aware of the guidelines
which must be followed keenly. The research team will be able to explain that in detail and what
are the possible consequences to be made in case the staff failed to adhere to the laws provided.
Therefore, in case there is no such guidelines, the team will provide them in the report so that the
management team can implement the same to ensure that the company is running smoothly. By
provisioning, these guidelines to the staff will help to mitigate stealing from the users themselves
However, there is a need in looking into external security as some experts may use some
software call spyware to intrude into the system and steal money or data. Remember the mobile
application has a user end which resides on a mobile phone, but the backend is in the powerful
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

INVESTIGATION INTO SECURITY OF MOBILE APPS 11
computer server. Most mobile application stores its data over the cloud. Cloud computing is a
technology we shall not rely on that much when it comes to security.
Are there any monitoring and review processes concerning these security documents?
In this research, we will look into the monitoring and review processes where other researchers
are carrying out a similar project. In this regard, references on the same will be made and check
if the findings are similar in one way or another.
Are these security documents regularly reviewed to address the threats that emerged from
new technologies?
The report also will be reviewing the different emerging technologies and the threats emerging in
the field of the mobile application. The report will explain the threats emerging and the possible
breaches which cause these threats to enter into our systems without us noticing them. Preventive
measures are considered and documented to allow users to get to know each type of attack and
how it occurs. (Siegrist, Earle & Gutscher, 2010)
3.0 Literature review
The accompanying paper is writing research on the topic of Mobile Security threats and
beaches. The point has been picked because of the ascent in mobile applications and the deficient
ascent in the theme of security in those applications. The reasons why this paper was written is
that cell phones such as tablet and PDAs, which run a versatile Operating System (OS). These
mobile phones are explicitly Android (Google), IOS (Apple), or BlackBerry OS (RIM).
(Raczkowski, 2017) While it is essential to take note of these terms, this research writing is
centred principally on Android OS security vulnerabilities. Polymorphic is characterized as
malware that changes to be to at some degree, not quite the same as the one preceding. The
computer server. Most mobile application stores its data over the cloud. Cloud computing is a
technology we shall not rely on that much when it comes to security.
Are there any monitoring and review processes concerning these security documents?
In this research, we will look into the monitoring and review processes where other researchers
are carrying out a similar project. In this regard, references on the same will be made and check
if the findings are similar in one way or another.
Are these security documents regularly reviewed to address the threats that emerged from
new technologies?
The report also will be reviewing the different emerging technologies and the threats emerging in
the field of the mobile application. The report will explain the threats emerging and the possible
breaches which cause these threats to enter into our systems without us noticing them. Preventive
measures are considered and documented to allow users to get to know each type of attack and
how it occurs. (Siegrist, Earle & Gutscher, 2010)
3.0 Literature review
The accompanying paper is writing research on the topic of Mobile Security threats and
beaches. The point has been picked because of the ascent in mobile applications and the deficient
ascent in the theme of security in those applications. The reasons why this paper was written is
that cell phones such as tablet and PDAs, which run a versatile Operating System (OS). These
mobile phones are explicitly Android (Google), IOS (Apple), or BlackBerry OS (RIM).
(Raczkowski, 2017) While it is essential to take note of these terms, this research writing is
centred principally on Android OS security vulnerabilities. Polymorphic is characterized as
malware that changes to be to at some degree, not quite the same as the one preceding. The

INVESTIGATION INTO SECURITY OF MOBILE APPS 12
mechanized alterations in code don't adjust the malware's usefulness. However, they can render
traditional enemy of infection discovery innovation ineffectual against them. An attack vector is
most essentially depicted as the methodology used to ambush a particular innovation (I. e. away
is taken to bargain a framework). A botnet is a gathering of "zombies" which are remotely
controlled for pernicious or monetary benefits. A solitary botnet regularly contains hundreds or
thousands of gadgets. At the point when the expression "defenselessness" is being used inside
this paper, it is a shaky area which enables an assailant to diminish a framework's security.
(Merna & Al-Thani, 2011) A defenselessness happens when three components converge,
including a framework shortcoming or defect, aggressor access to the imperfection, an assailant
fitness to misuse the blemish.
The outcomes accommodation procedure starts after the last application endorsement/dismissal
report is finished by the approving authority and antiquities are set up for accommodation to the
mentioning source. These antiquities may incorporate the last endorsement/dismissal report, test
instrument reports and conceivably a carefully marked rendition of the application that
demonstrates the application has finished the application screening process. The utilization of an
advanced mark gives source verification and respectability insurance, bearing witness to that the
form of the dissected application is equivalent to the rendition that was at first submitted and was
definitely not intentionally adjusted.
4.0 Methodology
A method was chosen while the research was being carried out. Both qualitative and quantitative
research was conducted on the basis of organizing an interview to the relevant group of people.
The people who will be asked the questions are the current users of the mobile application.
Hence the approach which was used to design this report is the waterfall model. (Labbi, 2005) In
mechanized alterations in code don't adjust the malware's usefulness. However, they can render
traditional enemy of infection discovery innovation ineffectual against them. An attack vector is
most essentially depicted as the methodology used to ambush a particular innovation (I. e. away
is taken to bargain a framework). A botnet is a gathering of "zombies" which are remotely
controlled for pernicious or monetary benefits. A solitary botnet regularly contains hundreds or
thousands of gadgets. At the point when the expression "defenselessness" is being used inside
this paper, it is a shaky area which enables an assailant to diminish a framework's security.
(Merna & Al-Thani, 2011) A defenselessness happens when three components converge,
including a framework shortcoming or defect, aggressor access to the imperfection, an assailant
fitness to misuse the blemish.
The outcomes accommodation procedure starts after the last application endorsement/dismissal
report is finished by the approving authority and antiquities are set up for accommodation to the
mentioning source. These antiquities may incorporate the last endorsement/dismissal report, test
instrument reports and conceivably a carefully marked rendition of the application that
demonstrates the application has finished the application screening process. The utilization of an
advanced mark gives source verification and respectability insurance, bearing witness to that the
form of the dissected application is equivalent to the rendition that was at first submitted and was
definitely not intentionally adjusted.
4.0 Methodology
A method was chosen while the research was being carried out. Both qualitative and quantitative
research was conducted on the basis of organizing an interview to the relevant group of people.
The people who will be asked the questions are the current users of the mobile application.
Hence the approach which was used to design this report is the waterfall model. (Labbi, 2005) In
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 37
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





