Report: Investigation of System Security Threats and Solutions
VerifiedAdded on 2021/05/31
|13
|2683
|119
Report
AI Summary
This report provides a comprehensive overview of computer security, addressing various aspects of system protection. It begins by introducing the concept of system security and its importance in safeguarding hardware, software, and data. The report explores different security threats, including both physical and non-physical risks, and discusses the role of virtual machines in enhancing security. It delves into virtual machine technologies, types, and their applications in creating secure environments. The investigation section outlines techniques such as ethical hacking and vulnerability scanning, along with tools used for forensic analysis, security, and system monitoring. The report includes a description of findings, specifically focusing on password recovery and system vulnerabilities, and provides references to relevant literature. Overall, the report offers valuable insights into computer security principles and practical approaches to system protection.

computer security
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Table of Contents
1. Introduction.......................................................................................................................................2
2. How to secure the system......................................................................................................................3
2.1 Security threats....................................................................................................................................3
2.2 Security systems of virtual machine...................................................................................................3
2.3 Virtual machine technologies..............................................................................................................4
2.4 Types of virtual machine.....................................................................................................................5
3. Investigation of the system security......................................................................................................6
3.1 Techniques...........................................................................................................................................6
3.2 Tools.....................................................................................................................................................6
4. Description of result..............................................................................................................................7
4.1 Investigation of finding the password................................................................................................8
References............................................................................................................................................10
1
1. Introduction.......................................................................................................................................2
2. How to secure the system......................................................................................................................3
2.1 Security threats....................................................................................................................................3
2.2 Security systems of virtual machine...................................................................................................3
2.3 Virtual machine technologies..............................................................................................................4
2.4 Types of virtual machine.....................................................................................................................5
3. Investigation of the system security......................................................................................................6
3.1 Techniques...........................................................................................................................................6
3.2 Tools.....................................................................................................................................................6
4. Description of result..............................................................................................................................7
4.1 Investigation of finding the password................................................................................................8
References............................................................................................................................................10
1

1. Introduction
The system becomes safety using system security. Using system security we can avoid
the threat attacks. Confidentiality of the system, integrity to the system, and also system
availability is provided by the system security. Three different types of components are used
such as hardware, software and data. Hardware means physical part of the computer memory,
Software is an interface, operating systems and browsers are the types of software. If you want
to protect the Hardware and software components the only way is using security control (Yeo,
2013).Two types of protections are available. One is technical and another one is physical
protection, these two protections are used to protect the virus. The protection to the
administration is provided by the security control. Security system is used to access the
information and it mainly used to avoid the threat and information loss and, many computer
systems are protected by this way. Two security systems are used.
Internet security
complete computer security
Malware is the kind of security risk is used to protect the malware and viruses and it
is a most popular security. The network security it is used to provide the solutions of the security
problems, these problems fully based on the network security .The computer system is used to
avoid the computer network problems. If you want to secure the network from the attackers then
we need to follow some steps, like auditing method and another one is mapping method, it
provide some additional details about the system structure, firewall, and also system devices.
This system shows the information about network connections. Some important affect is
auditing and it is used to develop performance, and provide best security system. The physical
threats are used in the smaller network. But in the big network maps are used. The computers are
connected with a network so it affected by viruses and worms based on the operating system and
the packages. Drivers use the latest version of anti-virus software to secure the password. VPN
connection is used to secure the password setting and also reduce the traffic, not only the
passwords the email is also be protected by this connection. We know that physical security
system is a crucial work. The firewall internet use this crucial work to protect the system from
viruses, and malware. The strong physical security like internet is used to protect the system
2
The system becomes safety using system security. Using system security we can avoid
the threat attacks. Confidentiality of the system, integrity to the system, and also system
availability is provided by the system security. Three different types of components are used
such as hardware, software and data. Hardware means physical part of the computer memory,
Software is an interface, operating systems and browsers are the types of software. If you want
to protect the Hardware and software components the only way is using security control (Yeo,
2013).Two types of protections are available. One is technical and another one is physical
protection, these two protections are used to protect the virus. The protection to the
administration is provided by the security control. Security system is used to access the
information and it mainly used to avoid the threat and information loss and, many computer
systems are protected by this way. Two security systems are used.
Internet security
complete computer security
Malware is the kind of security risk is used to protect the malware and viruses and it
is a most popular security. The network security it is used to provide the solutions of the security
problems, these problems fully based on the network security .The computer system is used to
avoid the computer network problems. If you want to secure the network from the attackers then
we need to follow some steps, like auditing method and another one is mapping method, it
provide some additional details about the system structure, firewall, and also system devices.
This system shows the information about network connections. Some important affect is
auditing and it is used to develop performance, and provide best security system. The physical
threats are used in the smaller network. But in the big network maps are used. The computers are
connected with a network so it affected by viruses and worms based on the operating system and
the packages. Drivers use the latest version of anti-virus software to secure the password. VPN
connection is used to secure the password setting and also reduce the traffic, not only the
passwords the email is also be protected by this connection. We know that physical security
system is a crucial work. The firewall internet use this crucial work to protect the system from
viruses, and malware. The strong physical security like internet is used to protect the system
2
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

from the attacker or hacker. For example the wireless router use open Ethernet port. All the
wireless routers are connected by the network.
The good security plan is built by the internet, so no one can access your system without
any authentication. So the hackers are eliminated by good security plan. So needed to build the
strong security plan.
For checking purpose two locks are used. In that one is door lock and another one is
cabinet lock. Ethernet is disconnected by this task. The router configuration and physical
switches are used for the security process.
2. How to secure the system
2.1 Security threats
System threat make an affect in the way of quality of data or hardware damage, the
natural sources are used for create a threats. The risks are available in the system and it is known
as security threat, and stealing computer resources is also the type of threat. The essential data is
stolen by the virus. Unauthorized access is also a kind of attack done by hackers. The data loss
and damages are done by hackers in the physical security system. Three different types of
physical threats are available such as internal threat, external and human threat. The internal
threats like files and hardware components are included .And the external threat is like the nature
attacks are possible. In this way the human stealing is reduced. The non-physical threats are also
the type of data loss and theft sensitive information. Anti-virus software is used to protect the
system from the non-physical threats. All the viruses and Trojans are avoided by the additional
storage (Inayatullah, 2013). Additional storage is known as to use pen drives or other devices
such as hard disk, adapter, etc. Secured password is the only way to protect system. There are
some intruders are used in the security services. So the above two threats are used in the physical
and non-physical causes of data loss.
2.2 Security systems of virtual machine
If you want to send the resources in secure manner the only way is we have to use the
virtual machine. Only one process is used for maintain the entire control of the virtual machine.
And computers are makes the virtual machine by the usage of one process. The security system
3
wireless routers are connected by the network.
The good security plan is built by the internet, so no one can access your system without
any authentication. So the hackers are eliminated by good security plan. So needed to build the
strong security plan.
For checking purpose two locks are used. In that one is door lock and another one is
cabinet lock. Ethernet is disconnected by this task. The router configuration and physical
switches are used for the security process.
2. How to secure the system
2.1 Security threats
System threat make an affect in the way of quality of data or hardware damage, the
natural sources are used for create a threats. The risks are available in the system and it is known
as security threat, and stealing computer resources is also the type of threat. The essential data is
stolen by the virus. Unauthorized access is also a kind of attack done by hackers. The data loss
and damages are done by hackers in the physical security system. Three different types of
physical threats are available such as internal threat, external and human threat. The internal
threats like files and hardware components are included .And the external threat is like the nature
attacks are possible. In this way the human stealing is reduced. The non-physical threats are also
the type of data loss and theft sensitive information. Anti-virus software is used to protect the
system from the non-physical threats. All the viruses and Trojans are avoided by the additional
storage (Inayatullah, 2013). Additional storage is known as to use pen drives or other devices
such as hard disk, adapter, etc. Secured password is the only way to protect system. There are
some intruders are used in the security services. So the above two threats are used in the physical
and non-physical causes of data loss.
2.2 Security systems of virtual machine
If you want to send the resources in secure manner the only way is we have to use the
virtual machine. Only one process is used for maintain the entire control of the virtual machine.
And computers are makes the virtual machine by the usage of one process. The security system
3
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

has two types. One is anti-virus detection system and another one is intrusion detection system.
The attacks are vulnerable by the security system (Jaiswal, 2013). No of processors are used in
every modern operating system, they are used to provide the imperfect of isolation process
between two different process.
Underlying software is used in the virtual machine. Using this software we can make the
raw devices such as easily and effectively. Each software has the own hardware for their
personal use. The physical computers are controlled by the software component, and also they
have an ability to manage the computers. The levels of isolation have two separate machines, and
the isolation process is located.
Different security applications were created by the virtual machine technology such as
intrusion detection algorithm, introspection, and honey farms. These are some kind of malicious
software.
2.3 Virtual machine technologies
Virtual machine also knows as the logical process. The virtual machine was affected by
the underlying computer programs. In virtual machine it uses some main frames for providing
the resources. Multiplexing and isolation are the two types of resources used in main frames
(Pektaş and Acarman, 2013). The virtual machine uses are increased as very fast because now a
days the scope of virtual machine is used in many places.
. VMM is used for display the sequence of actions. The individual virtual machines are
controlled by the virtual machine monitor. By the usage of virtual machine monitor the hardware
layers are run directly. Each operating system provides the set of virtual machine interface to use
the Virtual Machine Monitor.
Multiple virtual machines are executed in same time period. More over the multi-tasking
operation was performed. Types of operating systems are running in the same virtual machine
and these operating systems are known as guest operating system. Guest operating systems are
run by Guest applications.
4
The attacks are vulnerable by the security system (Jaiswal, 2013). No of processors are used in
every modern operating system, they are used to provide the imperfect of isolation process
between two different process.
Underlying software is used in the virtual machine. Using this software we can make the
raw devices such as easily and effectively. Each software has the own hardware for their
personal use. The physical computers are controlled by the software component, and also they
have an ability to manage the computers. The levels of isolation have two separate machines, and
the isolation process is located.
Different security applications were created by the virtual machine technology such as
intrusion detection algorithm, introspection, and honey farms. These are some kind of malicious
software.
2.3 Virtual machine technologies
Virtual machine also knows as the logical process. The virtual machine was affected by
the underlying computer programs. In virtual machine it uses some main frames for providing
the resources. Multiplexing and isolation are the two types of resources used in main frames
(Pektaş and Acarman, 2013). The virtual machine uses are increased as very fast because now a
days the scope of virtual machine is used in many places.
. VMM is used for display the sequence of actions. The individual virtual machines are
controlled by the virtual machine monitor. By the usage of virtual machine monitor the hardware
layers are run directly. Each operating system provides the set of virtual machine interface to use
the Virtual Machine Monitor.
Multiple virtual machines are executed in same time period. More over the multi-tasking
operation was performed. Types of operating systems are running in the same virtual machine
and these operating systems are known as guest operating system. Guest operating systems are
run by Guest applications.
4
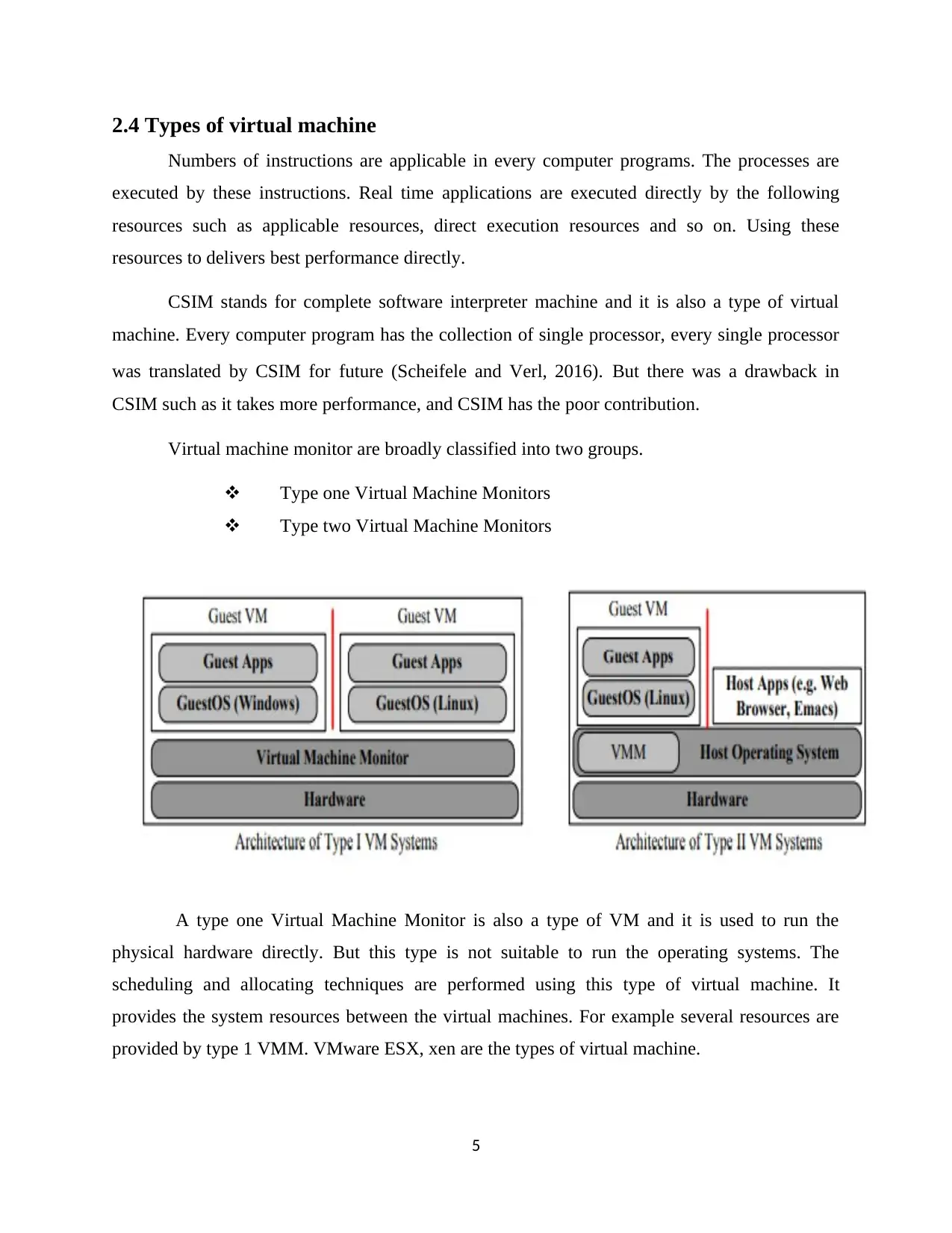
2.4 Types of virtual machine
Numbers of instructions are applicable in every computer programs. The processes are
executed by these instructions. Real time applications are executed directly by the following
resources such as applicable resources, direct execution resources and so on. Using these
resources to delivers best performance directly.
CSIM stands for complete software interpreter machine and it is also a type of virtual
machine. Every computer program has the collection of single processor, every single processor
was translated by CSIM for future (Scheifele and Verl, 2016). But there was a drawback in
CSIM such as it takes more performance, and CSIM has the poor contribution.
Virtual machine monitor are broadly classified into two groups.
Type one Virtual Machine Monitors
Type two Virtual Machine Monitors
A type one Virtual Machine Monitor is also a type of VM and it is used to run the
physical hardware directly. But this type is not suitable to run the operating systems. The
scheduling and allocating techniques are performed using this type of virtual machine. It
provides the system resources between the virtual machines. For example several resources are
provided by type 1 VMM. VMware ESX, xen are the types of virtual machine.
5
Numbers of instructions are applicable in every computer programs. The processes are
executed by these instructions. Real time applications are executed directly by the following
resources such as applicable resources, direct execution resources and so on. Using these
resources to delivers best performance directly.
CSIM stands for complete software interpreter machine and it is also a type of virtual
machine. Every computer program has the collection of single processor, every single processor
was translated by CSIM for future (Scheifele and Verl, 2016). But there was a drawback in
CSIM such as it takes more performance, and CSIM has the poor contribution.
Virtual machine monitor are broadly classified into two groups.
Type one Virtual Machine Monitors
Type two Virtual Machine Monitors
A type one Virtual Machine Monitor is also a type of VM and it is used to run the
physical hardware directly. But this type is not suitable to run the operating systems. The
scheduling and allocating techniques are performed using this type of virtual machine. It
provides the system resources between the virtual machines. For example several resources are
provided by type 1 VMM. VMware ESX, xen are the types of virtual machine.
5
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

The normal operating systems are used in Type 2 VMM. This operating system is used to
control the real time hardware systems. Host operating system is the best example for type 2
VMM. The host operating system was produced in type 2 VMM. The virtual machine knowledge
was not considered. Host operating system is known as ordinary operating system. Next type is
Guest operating system is also a type of operating system and it is used to refer the host
operating system. The host operating systems is present in the VMM 2.
Some resources are available in Types 2 VMM. VMware GSX, UML, and FAUma-chine are
the kind of resources used by type 2 VMM. UML is a well-defined OS. It must present the type
one Virtual Machine Monitor.
Compare the type one Virtual Machine Monitor and type two Virtual Machine Monitor, the
type 2 VMM is a heavy weighted virtual machine monitor. For this reason type 1 VMM was
most secured compared to type 2 VMM. So many places use the type 1 VMM because it
provides a better security
3. Investigation of the system security
3.1 Techniques
The following techniques shows the details about the testing process of security.
First one is Cross site scripting, Cross site testing is done by the following operations.
They are Apostrophe Greater Less than sign than sign. Second one is Ethical hacking, and also it
contains several techniques like Password cracking, Penetration testing, Risk assessment
Security auditing, Security scanning SQL injection, and the SQL injection testing is done by
following operations such as Apostrophes Commas Brackets Quotation mark, Vulnerability
scanning Posture assessment, and Buffer overflow testing
3.2 Tools
Following tools are used to protect the system in a proper manner. Normally different
types of tools are used to this security purpose.
Forensic tool
6
control the real time hardware systems. Host operating system is the best example for type 2
VMM. The host operating system was produced in type 2 VMM. The virtual machine knowledge
was not considered. Host operating system is known as ordinary operating system. Next type is
Guest operating system is also a type of operating system and it is used to refer the host
operating system. The host operating systems is present in the VMM 2.
Some resources are available in Types 2 VMM. VMware GSX, UML, and FAUma-chine are
the kind of resources used by type 2 VMM. UML is a well-defined OS. It must present the type
one Virtual Machine Monitor.
Compare the type one Virtual Machine Monitor and type two Virtual Machine Monitor, the
type 2 VMM is a heavy weighted virtual machine monitor. For this reason type 1 VMM was
most secured compared to type 2 VMM. So many places use the type 1 VMM because it
provides a better security
3. Investigation of the system security
3.1 Techniques
The following techniques shows the details about the testing process of security.
First one is Cross site scripting, Cross site testing is done by the following operations.
They are Apostrophe Greater Less than sign than sign. Second one is Ethical hacking, and also it
contains several techniques like Password cracking, Penetration testing, Risk assessment
Security auditing, Security scanning SQL injection, and the SQL injection testing is done by
following operations such as Apostrophes Commas Brackets Quotation mark, Vulnerability
scanning Posture assessment, and Buffer overflow testing
3.2 Tools
Following tools are used to protect the system in a proper manner. Normally different
types of tools are used to this security purpose.
Forensic tool
6
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
Security tool
Admin tool
Monitoring tool
In forensic tool it includes number of objectives. Using these objectives the forensic tools
are used in effective manner. In that NTO Log is very powerful, and also it known as network
wide backup tool, LServers –it is fully based on net BIOS name dumper, NPList- it is used to
perform the NT network process dumper, NTODrv- NT network driver/service dumpers are
produced by this objective. Security tools are classified into three types, such as LAN guard
network scanner, Del guest, Sechole3
4. Description of result
Two or more operating systems use virtual machine for execute. The widgetsInc file
implementation showed below window.
Step 1-login window
7
Admin tool
Monitoring tool
In forensic tool it includes number of objectives. Using these objectives the forensic tools
are used in effective manner. In that NTO Log is very powerful, and also it known as network
wide backup tool, LServers –it is fully based on net BIOS name dumper, NPList- it is used to
perform the NT network process dumper, NTODrv- NT network driver/service dumpers are
produced by this objective. Security tools are classified into three types, such as LAN guard
network scanner, Del guest, Sechole3
4. Description of result
Two or more operating systems use virtual machine for execute. The widgetsInc file
implementation showed below window.
Step 1-login window
7
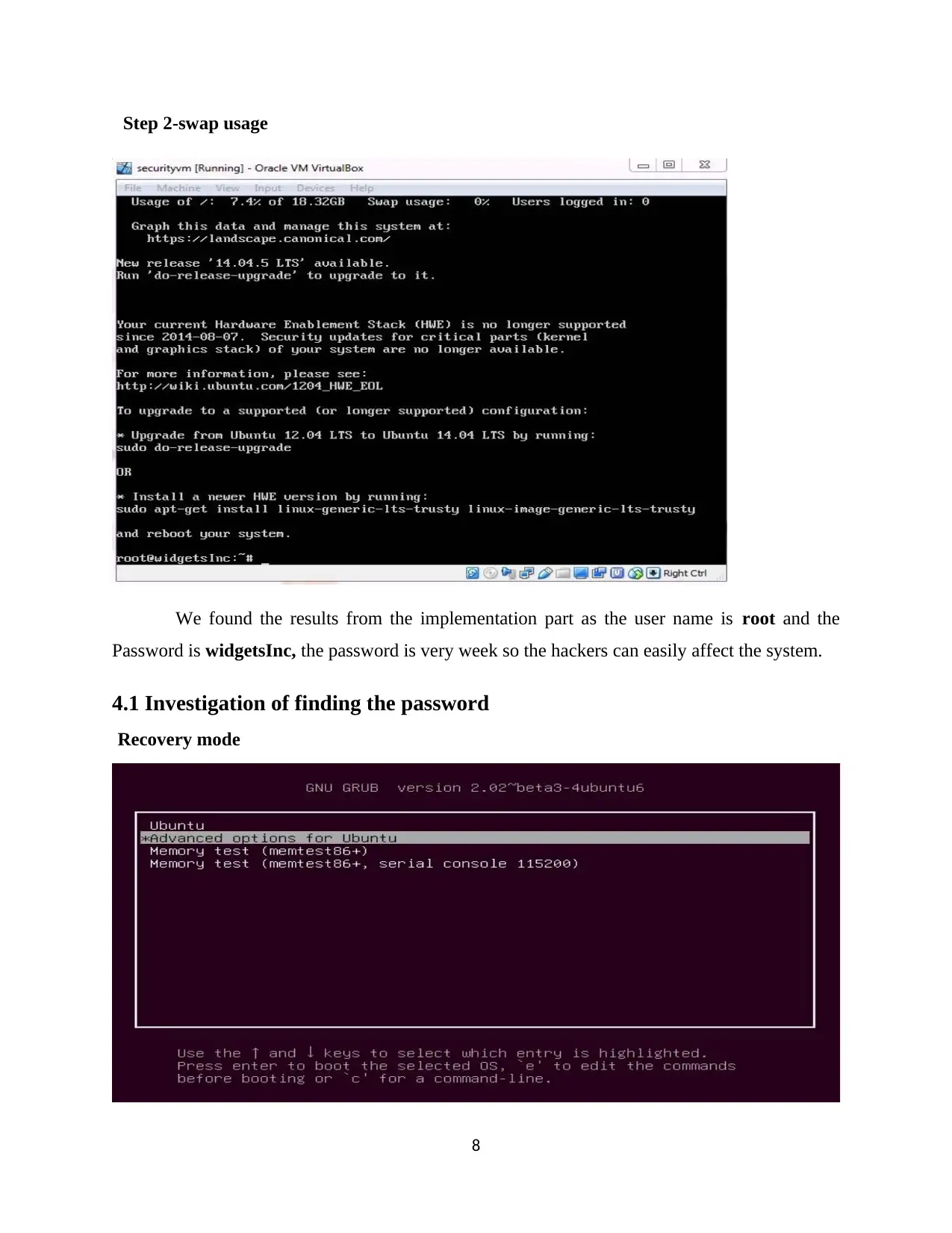
Step 2-swap usage
We found the results from the implementation part as the user name is root and the
Password is widgetsInc, the password is very week so the hackers can easily affect the system.
4.1 Investigation of finding the password
Recovery mode
8
We found the results from the implementation part as the user name is root and the
Password is widgetsInc, the password is very week so the hackers can easily affect the system.
4.1 Investigation of finding the password
Recovery mode
8
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
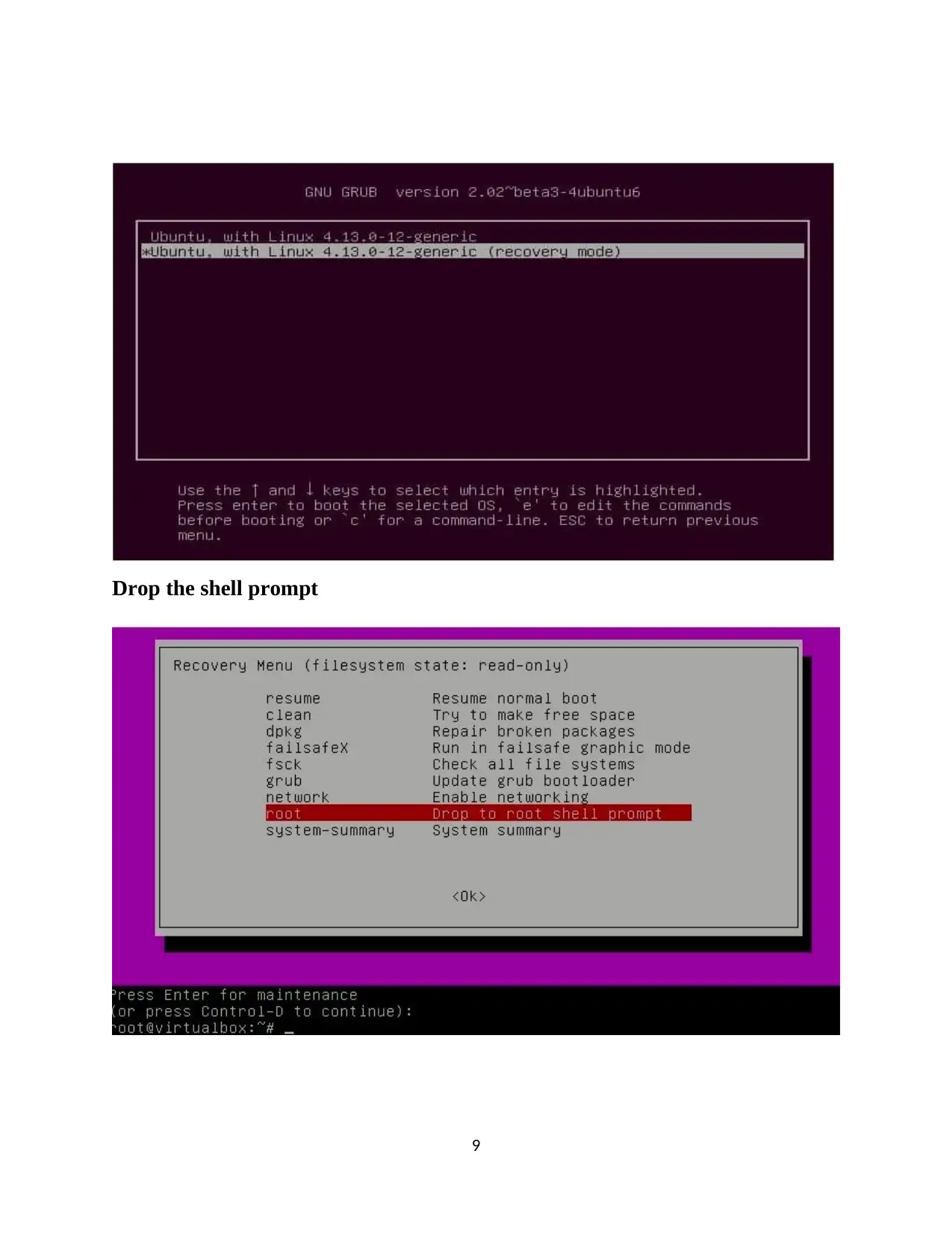
Drop the shell prompt
9
9
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

References
Bagaryakov, A. (2012). Innovational security in the system of a region's economic
security. Economy of Region, pp.302-305.
Byun, J. (2015). Privacy preserving smartcard-based authentication system with provable
security. Security and Communication Networks, 8(17), pp.3028-3044.
Mahawer, D. and Nagaraju, A. (2013). Metamorphic malware detection using base malware
identification approach. Security and Communication Networks, 7(11), pp.1719-1733.
N. Patil, D. (2016). Digital Forensic Analysis of Ubuntu File System. International Journal of
Cyber-Security and Digital Forensics, 5(4), pp.175-186.
Algorithm Based security System for Banknotes. (2018). International Journal of Recent Trends
in Engineering and Research, pp.231-242.
Khan, A. (2017). Virtual machine security. International Journal of Information and Computer
Security, 9(1/2), p.49.
Pektaş, A. and Acarman, T. (2013). A dynamic malware analyzer against virtual machine aware
malicious software. Security and Communication Networks, 7(12), pp.2245-225
Anitha, A. (2011). Network Security using Linux Intrusion Detection System. International
Journal of Research in Computer Science, 2(1), pp.33-38.
Babincev, I. and Vuletic, D. (2016). Web application security analysis using the Kali Linux
operating system. Vojnotehnicki glasnik, 64(2), pp.513-531.
Brucker, A. and Wolff, B. (2005). A verification approach to applied system
security. International Journal on Software Tools for Technology Transfer, 7(3), pp.233-247.
Cui, Y. and Zhang, Y. (2014). The Network Security Analysis of Linux Operating
System. Advanced Materials Research, 998-999, pp.1274-1277.
10
Bagaryakov, A. (2012). Innovational security in the system of a region's economic
security. Economy of Region, pp.302-305.
Byun, J. (2015). Privacy preserving smartcard-based authentication system with provable
security. Security and Communication Networks, 8(17), pp.3028-3044.
Mahawer, D. and Nagaraju, A. (2013). Metamorphic malware detection using base malware
identification approach. Security and Communication Networks, 7(11), pp.1719-1733.
N. Patil, D. (2016). Digital Forensic Analysis of Ubuntu File System. International Journal of
Cyber-Security and Digital Forensics, 5(4), pp.175-186.
Algorithm Based security System for Banknotes. (2018). International Journal of Recent Trends
in Engineering and Research, pp.231-242.
Khan, A. (2017). Virtual machine security. International Journal of Information and Computer
Security, 9(1/2), p.49.
Pektaş, A. and Acarman, T. (2013). A dynamic malware analyzer against virtual machine aware
malicious software. Security and Communication Networks, 7(12), pp.2245-225
Anitha, A. (2011). Network Security using Linux Intrusion Detection System. International
Journal of Research in Computer Science, 2(1), pp.33-38.
Babincev, I. and Vuletic, D. (2016). Web application security analysis using the Kali Linux
operating system. Vojnotehnicki glasnik, 64(2), pp.513-531.
Brucker, A. and Wolff, B. (2005). A verification approach to applied system
security. International Journal on Software Tools for Technology Transfer, 7(3), pp.233-247.
Cui, Y. and Zhang, Y. (2014). The Network Security Analysis of Linux Operating
System. Advanced Materials Research, 998-999, pp.1274-1277.
10

Design and Implementation of Linux-based Integrated Security System(LISS) Using Open
Security Tools. (2004). The KIPS Transactions:PartC, 11C(4), pp.485-496.
Holm, H. and Afridi, K. (2015). An expert-based investigation of the Common Vulnerability
Scoring System. Computers & Security, 53, pp.18-30.
Huseyin, T. and Kerem, E. (2011). Password management diffuculties in system and network
management. Procedia Computer Science, 3, pp.801-804.
Mamman, A. and Zakaria, H. (2016). Spirituality and Ubuntu as the foundation for building
African institutions, organizations and leaders. Journal of Management, Spirituality & Religion,
13(3), pp.246-265.
Mangaliso, M. (2001). Building Competitive Advantage from Ubuntu: Management Lessons
from South Africa. SSRN Electronic Journal.
Mann, S. and Mitchell, E. (2001). Linux System Security: An Administrator's Guide to Open
Source Security Tools. EDPACS, 28(8), pp.1-3.
Wang, H., Zhu, H., Xue, P. and Zhu, X. (2018). The resin lens flaw feature extraction and
detection system based on data transmission security. Multimedia Tools and Applications.
Inayatullah, N. (2013). Pulling threats: Intimate systematicity in The Politics of Exile. Security
Dialogue, 44(4), pp.331-345.
Jaiswal, S. (2013). Enhancement in Elimination of Security Threats using Trusted Proactive
Routing. IOSR Journal of Computer Engineering, 9(3), pp.82-88..
Scheifele, S. and Verl, A. (2016). Automated Control System Generation Out of the Virtual
Machine. Procedia Technology, 26, pp.349-356.
Yeo, J. (2013). Using penetration testing to enhance your company's security. Computer Fraud
& Security, 2013(4), pp.17-20.
https://www.youtube.com/watch?v=33zxgEl6eTo
11
Security Tools. (2004). The KIPS Transactions:PartC, 11C(4), pp.485-496.
Holm, H. and Afridi, K. (2015). An expert-based investigation of the Common Vulnerability
Scoring System. Computers & Security, 53, pp.18-30.
Huseyin, T. and Kerem, E. (2011). Password management diffuculties in system and network
management. Procedia Computer Science, 3, pp.801-804.
Mamman, A. and Zakaria, H. (2016). Spirituality and Ubuntu as the foundation for building
African institutions, organizations and leaders. Journal of Management, Spirituality & Religion,
13(3), pp.246-265.
Mangaliso, M. (2001). Building Competitive Advantage from Ubuntu: Management Lessons
from South Africa. SSRN Electronic Journal.
Mann, S. and Mitchell, E. (2001). Linux System Security: An Administrator's Guide to Open
Source Security Tools. EDPACS, 28(8), pp.1-3.
Wang, H., Zhu, H., Xue, P. and Zhu, X. (2018). The resin lens flaw feature extraction and
detection system based on data transmission security. Multimedia Tools and Applications.
Inayatullah, N. (2013). Pulling threats: Intimate systematicity in The Politics of Exile. Security
Dialogue, 44(4), pp.331-345.
Jaiswal, S. (2013). Enhancement in Elimination of Security Threats using Trusted Proactive
Routing. IOSR Journal of Computer Engineering, 9(3), pp.82-88..
Scheifele, S. and Verl, A. (2016). Automated Control System Generation Out of the Virtual
Machine. Procedia Technology, 26, pp.349-356.
Yeo, J. (2013). Using penetration testing to enhance your company's security. Computer Fraud
& Security, 2013(4), pp.17-20.
https://www.youtube.com/watch?v=33zxgEl6eTo
11
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 13
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.




