Survey on IoT Security: Applications, Threats, Solutions Analysis
VerifiedAdded on 2021/07/02
|24
|27021
|250
Report
AI Summary
This report presents a comprehensive survey on Internet of Things (IoT) security, examining various application areas, security threats, and solution architectures. It begins by highlighting the rapid growth of IoT and the increasing need for robust security measures. The report categorizes different IoT applications, such as smart cities, and discusses the specific security and privacy issues associated with each. It then delves into the sources of threats across different layers of IoT environments, emphasizing the challenges in securing IoT devices compared to traditional IT devices. The paper reviews existing and emerging technologies to enhance IoT security, including blockchain, fog computing, edge computing, and machine learning. These technologies are discussed in detail, along with their potential to improve trust and security in IoT applications. The survey also addresses open issues, challenges, and future research directions for developing secure IoT applications, providing recommendations for improving the IoT infrastructure to facilitate secure communications. The report concludes by emphasizing the critical need for security in all IoT deployments and the importance of addressing the identified challenges to ensure the successful and secure expansion of IoT applications.

This work is licensed under a Creative Commons Attribution 3.0 License. For more information, see http://creativecomm
This article has been accepted for publication in a future issue of this journal, but has not been fully edited. Content may change p
10.1109/ACCESS.2019.2924045, IEEE Access
Date of publication xxxx 00, 0000, date of current version xxxx 00, 0000.
Digital Object Identifier xxx
A Survey on IoT Security: Application
Areas, Security Threats, and Solution
Architectures
VIKAS HASSIJA 1, VINAY CHAMOLA2, VIKAS SAXENA 1, DIVYANSH JAIN 1, PRANAV
GOYAL 1 and BIPLAB SIKDAR3
1 Department of CSE and IT, Jaypee Institute of Information Technology, Noida, 201309 India (e-mail: {vikas.hassija, vikas.saxena}@jiit.ac.in), (e-mail:
{divyansh.bjain,pranav.goyal1297}@gmail.com)
2 Department of EEE, Birla Institute of Technology & Science (BITS), Pilani, Rajasthan 333031 India (e-mail: vinay.chamola@pilani.bits-pilani.ac.in)
3 Department of Electrical and Computer Engineering, National University of Singapore, 117583 Singapore (e-mail: bsikdar@nus.edu.sg)
Corresponding author:Vinay Chamola(e-mail: vinay.chamola@pilani.bits-pilani.ac.in).
ABSTRACT Internet of things (IoT) is the next era of communication. Using IoT, physical objects can
be empowered to create, receive and exchange data in a seamless manner. Various IoT applications focus
on automating different tasks and are trying to empower the inanimate physical objects to act without any
human intervention. The existing and upcoming IoT applications are highly promising to increase the level
of comfort, efficiency, and automation for the users. To be able to implement such a world in an ever
growing fashion requires high security, privacy, authentication, and recovery from attacks. In this regard, it
is imperative to make the required changes in the architecture of IoT applications for achieving end-to-end
secure IoT environments. In this paper, a detailed review of the security-related challenges and sources of
threat in IoT applications is presented. After discussing the security issues, various emerging and existing
technologies focused on achieving a high degree of trust in IoT applications are discussed. Four different
technologies: Blockchain, fog computing, edge computing, and machine learning to increase the level of
security in IoT are discussed.
INDEX TERMS IoT, IoT Security, Blockchain, Fog Computing, Edge Computing, Machine Learning, IoT
applications, Distributed Systems.
I. INTRODUCTION
THE pace of connecting physical devices around us to
the Internet is increasing rapidly. According to a recent
Gartner report, there will be around 8.4 billion connected
things worldwide in 2020. This number is expected to grow
to 20.4 billion by 2022 [1]. The use of IoT applications
is increasing in all parts of the world. The major driving
countries in this include western Europe, North America,
and China [1]. The number of machine to machine (M2M)
connections is expected to grow from 5.6 billion in 2016 to
27 billion in 2024 [1]. This leap in numbers itself declares
IoT to be one of the major upcoming markets that could form
a cornerstone of the expanding digital economy. The IoT
industry is expected to grow in terms of revenue from $892
billion in 2018 to $4 trillion by 2025 [2]. M2M connections
cover a broad range of applications like smart cities, smart
environment, smart grids, smart retail, smart farming, etc.
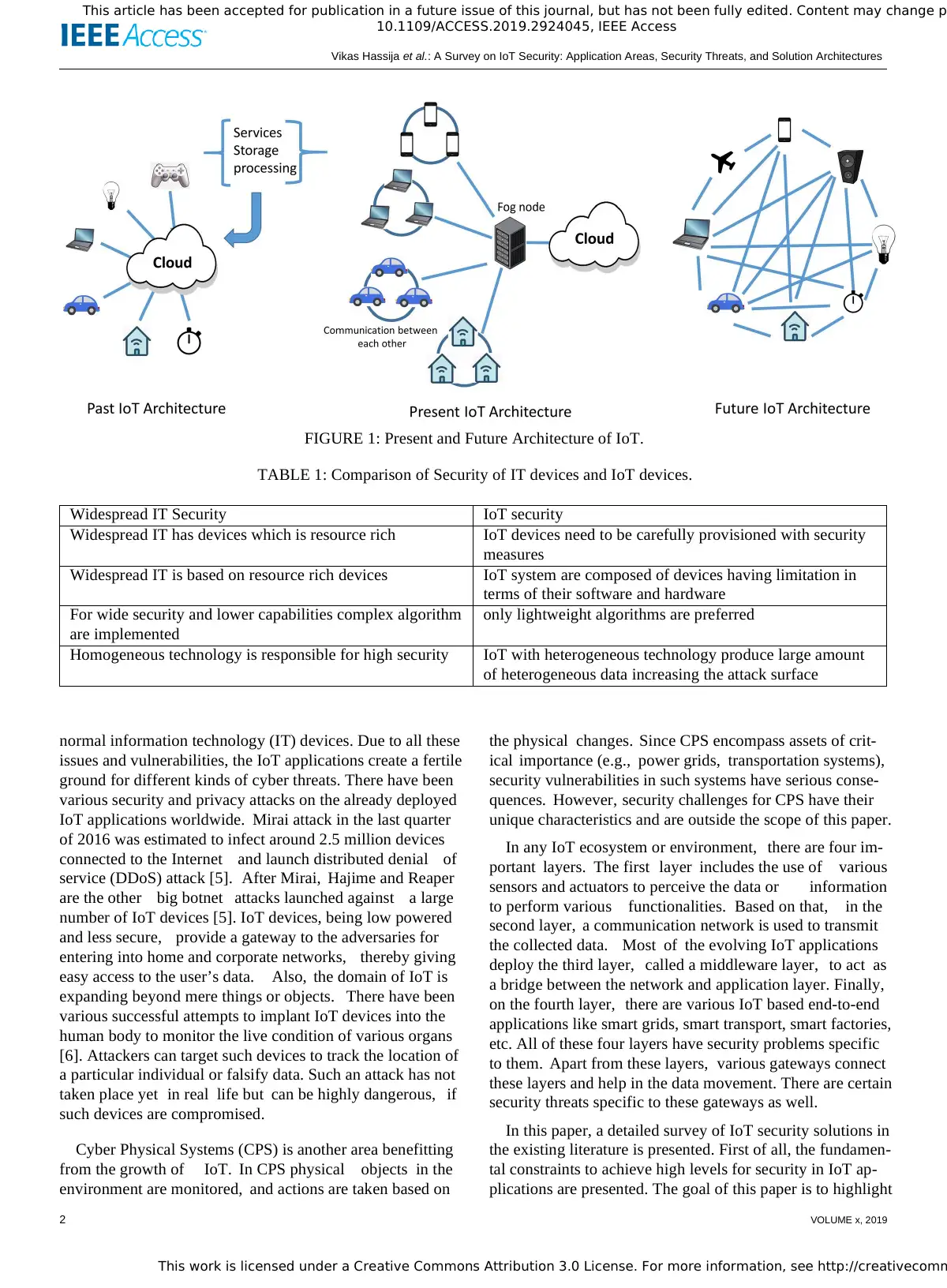
[3]. Figure 1 shows the past, present and future architecture
of IoT. In future, the devices are not only expected to be
connected to the Internet and other local devices but are also
expected to communicate with other devices on the Internet
directly. Apart from the devices or things being connected,
the concept of social IoT (SIoT) is also emerging. SIoT will
enable different social networking users to be connected to
the devices and users can share the devices over the Internet
[4].
With all this vast spectrum of IoT applications comes
the issue of security and privacy. Without a trusted and
interoperable IoT ecosystem, emerging IoT applications can-
not reach high demand and may lose all their potential.
Along with the security issues faced generally by the Inter-
net, cellular networks, and WSNs, IoT also has its special
security challenges such as privacy issues, authentication
issues, management issues, information storage and so on.
Table 1 summarizes various factors due to which securing
IoT environment is much more challenging than securing
VOLUME x, 2019 1
This article has been accepted for publication in a future issue of this journal, but has not been fully edited. Content may change p
10.1109/ACCESS.2019.2924045, IEEE Access
Date of publication xxxx 00, 0000, date of current version xxxx 00, 0000.
Digital Object Identifier xxx
A Survey on IoT Security: Application
Areas, Security Threats, and Solution
Architectures
VIKAS HASSIJA 1, VINAY CHAMOLA2, VIKAS SAXENA 1, DIVYANSH JAIN 1, PRANAV
GOYAL 1 and BIPLAB SIKDAR3
1 Department of CSE and IT, Jaypee Institute of Information Technology, Noida, 201309 India (e-mail: {vikas.hassija, vikas.saxena}@jiit.ac.in), (e-mail:
{divyansh.bjain,pranav.goyal1297}@gmail.com)
2 Department of EEE, Birla Institute of Technology & Science (BITS), Pilani, Rajasthan 333031 India (e-mail: vinay.chamola@pilani.bits-pilani.ac.in)
3 Department of Electrical and Computer Engineering, National University of Singapore, 117583 Singapore (e-mail: bsikdar@nus.edu.sg)
Corresponding author:Vinay Chamola(e-mail: vinay.chamola@pilani.bits-pilani.ac.in).
ABSTRACT Internet of things (IoT) is the next era of communication. Using IoT, physical objects can
be empowered to create, receive and exchange data in a seamless manner. Various IoT applications focus
on automating different tasks and are trying to empower the inanimate physical objects to act without any
human intervention. The existing and upcoming IoT applications are highly promising to increase the level
of comfort, efficiency, and automation for the users. To be able to implement such a world in an ever
growing fashion requires high security, privacy, authentication, and recovery from attacks. In this regard, it
is imperative to make the required changes in the architecture of IoT applications for achieving end-to-end
secure IoT environments. In this paper, a detailed review of the security-related challenges and sources of
threat in IoT applications is presented. After discussing the security issues, various emerging and existing
technologies focused on achieving a high degree of trust in IoT applications are discussed. Four different
technologies: Blockchain, fog computing, edge computing, and machine learning to increase the level of
security in IoT are discussed.
INDEX TERMS IoT, IoT Security, Blockchain, Fog Computing, Edge Computing, Machine Learning, IoT
applications, Distributed Systems.
I. INTRODUCTION
THE pace of connecting physical devices around us to
the Internet is increasing rapidly. According to a recent
Gartner report, there will be around 8.4 billion connected
things worldwide in 2020. This number is expected to grow
to 20.4 billion by 2022 [1]. The use of IoT applications
is increasing in all parts of the world. The major driving
countries in this include western Europe, North America,
and China [1]. The number of machine to machine (M2M)
connections is expected to grow from 5.6 billion in 2016 to
27 billion in 2024 [1]. This leap in numbers itself declares
IoT to be one of the major upcoming markets that could form
a cornerstone of the expanding digital economy. The IoT
industry is expected to grow in terms of revenue from $892
billion in 2018 to $4 trillion by 2025 [2]. M2M connections
cover a broad range of applications like smart cities, smart
environment, smart grids, smart retail, smart farming, etc.
[3]. Figure 1 shows the past, present and future architecture
of IoT. In future, the devices are not only expected to be
connected to the Internet and other local devices but are also
expected to communicate with other devices on the Internet
directly. Apart from the devices or things being connected,
the concept of social IoT (SIoT) is also emerging. SIoT will
enable different social networking users to be connected to
the devices and users can share the devices over the Internet
[4].
With all this vast spectrum of IoT applications comes
the issue of security and privacy. Without a trusted and
interoperable IoT ecosystem, emerging IoT applications can-
not reach high demand and may lose all their potential.
Along with the security issues faced generally by the Inter-
net, cellular networks, and WSNs, IoT also has its special
security challenges such as privacy issues, authentication
issues, management issues, information storage and so on.
Table 1 summarizes various factors due to which securing
IoT environment is much more challenging than securing
VOLUME x, 2019 1
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
This work is licensed under a Creative Commons Attribution 3.0 License. For more information, see http://creativecomm
This article has been accepted for publication in a future issue of this journal, but has not been fully edited. Content may change p
10.1109/ACCESS.2019.2924045, IEEE Access
Vikas Hassija et al.: A Survey on IoT Security: Application Areas, Security Threats, and Solution Architectures
FIGURE 1: Present and Future Architecture of IoT.
TABLE 1: Comparison of Security of IT devices and IoT devices.
Widespread IT Security IoT security
Widespread IT has devices which is resource rich IoT devices need to be carefully provisioned with security
measures
Widespread IT is based on resource rich devices IoT system are composed of devices having limitation in
terms of their software and hardware
For wide security and lower capabilities complex algorithm
are implemented
only lightweight algorithms are preferred
Homogeneous technology is responsible for high security IoT with heterogeneous technology produce large amount
of heterogeneous data increasing the attack surface
normal information technology (IT) devices. Due to all these
issues and vulnerabilities, the IoT applications create a fertile
ground for different kinds of cyber threats. There have been
various security and privacy attacks on the already deployed
IoT applications worldwide. Mirai attack in the last quarter
of 2016 was estimated to infect around 2.5 million devices
connected to the Internet and launch distributed denial of
service (DDoS) attack [5]. After Mirai, Hajime and Reaper
are the other big botnet attacks launched against a large
number of IoT devices [5]. IoT devices, being low powered
and less secure, provide a gateway to the adversaries for
entering into home and corporate networks, thereby giving
easy access to the user’s data. Also, the domain of IoT is
expanding beyond mere things or objects. There have been
various successful attempts to implant IoT devices into the
human body to monitor the live condition of various organs
[6]. Attackers can target such devices to track the location of
a particular individual or falsify data. Such an attack has not
taken place yet in real life but can be highly dangerous, if
such devices are compromised.
Cyber Physical Systems (CPS) is another area benefitting
from the growth of IoT. In CPS physical objects in the
environment are monitored, and actions are taken based on
the physical changes. Since CPS encompass assets of crit-
ical importance (e.g., power grids, transportation systems),
security vulnerabilities in such systems have serious conse-
quences. However, security challenges for CPS have their
unique characteristics and are outside the scope of this paper.
In any IoT ecosystem or environment, there are four im-
portant layers. The first layer includes the use of various
sensors and actuators to perceive the data or information
to perform various functionalities. Based on that, in the
second layer, a communication network is used to transmit
the collected data. Most of the evolving IoT applications
deploy the third layer, called a middleware layer, to act as
a bridge between the network and application layer. Finally,
on the fourth layer, there are various IoT based end-to-end
applications like smart grids, smart transport, smart factories,
etc. All of these four layers have security problems specific
to them. Apart from these layers, various gateways connect
these layers and help in the data movement. There are certain
security threats specific to these gateways as well.
In this paper, a detailed survey of IoT security solutions in
the existing literature is presented. First of all, the fundamen-
tal constraints to achieve high levels for security in IoT ap-
plications are presented. The goal of this paper is to highlight
2 VOLUME x, 2019
This article has been accepted for publication in a future issue of this journal, but has not been fully edited. Content may change p
10.1109/ACCESS.2019.2924045, IEEE Access
Vikas Hassija et al.: A Survey on IoT Security: Application Areas, Security Threats, and Solution Architectures
FIGURE 1: Present and Future Architecture of IoT.
TABLE 1: Comparison of Security of IT devices and IoT devices.
Widespread IT Security IoT security
Widespread IT has devices which is resource rich IoT devices need to be carefully provisioned with security
measures
Widespread IT is based on resource rich devices IoT system are composed of devices having limitation in
terms of their software and hardware
For wide security and lower capabilities complex algorithm
are implemented
only lightweight algorithms are preferred
Homogeneous technology is responsible for high security IoT with heterogeneous technology produce large amount
of heterogeneous data increasing the attack surface
normal information technology (IT) devices. Due to all these
issues and vulnerabilities, the IoT applications create a fertile
ground for different kinds of cyber threats. There have been
various security and privacy attacks on the already deployed
IoT applications worldwide. Mirai attack in the last quarter
of 2016 was estimated to infect around 2.5 million devices
connected to the Internet and launch distributed denial of
service (DDoS) attack [5]. After Mirai, Hajime and Reaper
are the other big botnet attacks launched against a large
number of IoT devices [5]. IoT devices, being low powered
and less secure, provide a gateway to the adversaries for
entering into home and corporate networks, thereby giving
easy access to the user’s data. Also, the domain of IoT is
expanding beyond mere things or objects. There have been
various successful attempts to implant IoT devices into the
human body to monitor the live condition of various organs
[6]. Attackers can target such devices to track the location of
a particular individual or falsify data. Such an attack has not
taken place yet in real life but can be highly dangerous, if
such devices are compromised.
Cyber Physical Systems (CPS) is another area benefitting
from the growth of IoT. In CPS physical objects in the
environment are monitored, and actions are taken based on
the physical changes. Since CPS encompass assets of crit-
ical importance (e.g., power grids, transportation systems),
security vulnerabilities in such systems have serious conse-
quences. However, security challenges for CPS have their
unique characteristics and are outside the scope of this paper.
In any IoT ecosystem or environment, there are four im-
portant layers. The first layer includes the use of various
sensors and actuators to perceive the data or information
to perform various functionalities. Based on that, in the
second layer, a communication network is used to transmit
the collected data. Most of the evolving IoT applications
deploy the third layer, called a middleware layer, to act as
a bridge between the network and application layer. Finally,
on the fourth layer, there are various IoT based end-to-end
applications like smart grids, smart transport, smart factories,
etc. All of these four layers have security problems specific
to them. Apart from these layers, various gateways connect
these layers and help in the data movement. There are certain
security threats specific to these gateways as well.
In this paper, a detailed survey of IoT security solutions in
the existing literature is presented. First of all, the fundamen-
tal constraints to achieve high levels for security in IoT ap-
plications are presented. The goal of this paper is to highlight
2 VOLUME x, 2019
This work is licensed under a Creative Commons Attribution 3.0 License. For more information, see http://creativecomm
This article has been accepted for publication in a future issue of this journal, but has not been fully edited. Content may change p
10.1109/ACCESS.2019.2924045, IEEE Access
Vikas Hassija et al.: A Survey on IoT Security: Application Areas, Security Threats, and Solution Architectures
the major existing and upcoming solutions for IoT security.
Specifically, the four major classes of IoT security solutions
namely: (1) blockchain based solutions; (2) fog computing
based solutions; (3) machine learning based solutions and
(4) edge computing based solutions are highlighted. Table 3
gives a list of acronyms related to IoT used in this paper.
A. RELATED SURVEYS AND OUR CONTRIBUTIONS
There are various existing surveys on IoT security and pri-
vacy issues. Yuchen et al. [10] have summarized various
security issues in IoT applications. Authors of [11] have dis-
cussed the security issues specific to location-based services
in IoT. The authors target the particular problems related to
localization and positioning of the IoT devices. Anne et al.
in [12] focus mainly on the security issues related to IoT
middleware and provide a detailed survey of related existing
protocols and their security issues. M. Guizani et al. in [14]
have surveyed various trust management techniques for IoT
along with their pros and cons. Security mechanisms for
IoT security such as software defined networking (SDN)
and network function virtualization (NFV) are discussed
in [13]. In [8] the authors have compared edge computing
with traditional cloud systems to secure IoT systems. Jie
Lin et al. in [9] have discussed the relationship between
IoT and fog computing. Some of the security issues related
to fog computing have also been discussed. Authors of [7]
have discussed vulnerabilities faced by IoT in brief. Table 2
summarizes the main contributions of the previous compre-
hensive surveys on IoT security. Although there are several
works in this direction, they are specific to certain limited
aspects of IoT. This calls the need for a detailed survey
on all the existing and upcoming security challenges in IoT
applications. This paper will help the reader to get a detailed
idea of the state-of-the-art in IoT security and will give them
a general understanding of the area. The main contributions
of this work are as follows:
1. A classification of different IoT applications and spe-
cific security and privacy issues related to those appli-
cations.
2. A detailed explanation of different threat sources in
different layers of IoT.
3. Detailed and realistic recommendations to improve the
IoT infrastructure to facilitate secure communications.
4. Review on the proposed countermeasures to the secu-
rity issues in IoT.
5. An assessment of the open issues, challenges and
future research directions for developing secure IoT
applications.
B. ORGANIZATION
The organization of the rest of the paper is as follows: Section
II describes various application areas of IoT where high
security is required. Section III discusses various sources of
threats in an IoT environment. In section IV various con-
straints and requirements to be considered while developing
a secure IoT application are reviewed. Four major IoT se-
curity approaches, i.e., blockchain, fog computing, machine
learning, and edge computing are presented in Section V,
VI, VII, and VIII, respectively. Section IX describes various
open issues, challenges and upcoming research opportunities
in IoT security and finally, Section X concludes the paper.
II. SECURITY CRITICAL APPLICATION AREAS OF IOT
Security is highly critical in almost all IoT applications that
have already been deployed or are in the process of deploy-
ment. The applications of IoT are increasing very rapidly
and penetrating most of the existing industries. Although
operators support these IoT applications through existing
networking technologies, several of these applications need
more stringent security support from technologies they use.
In this section various security critical IoT applications are
discussed.
1. Smart Cities: Smart cities involve extensive use of
emerging computation and communication resources
for increasing the overall quality of life of the people
[15]. It includes smart homes, smart traffic manage-
ment, smart disaster management, smart utilities, etc.
There is a push to make cities smarter, and govern-
ments worldwide are encouraging their development
through various incentives [16]. Although the use of
smart applications is intended to improve the overall
quality of life of the citizens, it comes with a threat
to the privacy of the citizens. Smart card services tend
to put the card details and purchase behavior of the
citizens at risk. Smart mobility applications may leak
the location traces of the users. There are applications
TABLE 2: Related Surveys on IoT Security
Year Author Contributions
2016 Arsalan Mosenia et al., [7] A brief discussion of vulnerabilities faced by the edge side layer of IoT
2017 Yu wei et al., [8] Survey on using Edge Computing to secure IoT
2017 Jie Lin ea al., [9] Discussion on relationship between IoT and Fog Computing
2017 Y yang et al., [10] A brief discussion on most relevant limitations of IoT devices
2017 L chen , S. Thombre et al., [11] security issues specific to location-based services in IoT
2017 A H Ngu, V. Metsis et al., [12] Security issues related to the IoT middle ware
2018 I Farris, T Taleb et al., [13] Security mechanism for IoT security like SDN and NFB
2019 Ikram Ud din, M. Guizani et al,. [14] Trust Management Techniques for Internet of Things
VOLUME x, 2019 3
This article has been accepted for publication in a future issue of this journal, but has not been fully edited. Content may change p
10.1109/ACCESS.2019.2924045, IEEE Access
Vikas Hassija et al.: A Survey on IoT Security: Application Areas, Security Threats, and Solution Architectures
the major existing and upcoming solutions for IoT security.
Specifically, the four major classes of IoT security solutions
namely: (1) blockchain based solutions; (2) fog computing
based solutions; (3) machine learning based solutions and
(4) edge computing based solutions are highlighted. Table 3
gives a list of acronyms related to IoT used in this paper.
A. RELATED SURVEYS AND OUR CONTRIBUTIONS
There are various existing surveys on IoT security and pri-
vacy issues. Yuchen et al. [10] have summarized various
security issues in IoT applications. Authors of [11] have dis-
cussed the security issues specific to location-based services
in IoT. The authors target the particular problems related to
localization and positioning of the IoT devices. Anne et al.
in [12] focus mainly on the security issues related to IoT
middleware and provide a detailed survey of related existing
protocols and their security issues. M. Guizani et al. in [14]
have surveyed various trust management techniques for IoT
along with their pros and cons. Security mechanisms for
IoT security such as software defined networking (SDN)
and network function virtualization (NFV) are discussed
in [13]. In [8] the authors have compared edge computing
with traditional cloud systems to secure IoT systems. Jie
Lin et al. in [9] have discussed the relationship between
IoT and fog computing. Some of the security issues related
to fog computing have also been discussed. Authors of [7]
have discussed vulnerabilities faced by IoT in brief. Table 2
summarizes the main contributions of the previous compre-
hensive surveys on IoT security. Although there are several
works in this direction, they are specific to certain limited
aspects of IoT. This calls the need for a detailed survey
on all the existing and upcoming security challenges in IoT
applications. This paper will help the reader to get a detailed
idea of the state-of-the-art in IoT security and will give them
a general understanding of the area. The main contributions
of this work are as follows:
1. A classification of different IoT applications and spe-
cific security and privacy issues related to those appli-
cations.
2. A detailed explanation of different threat sources in
different layers of IoT.
3. Detailed and realistic recommendations to improve the
IoT infrastructure to facilitate secure communications.
4. Review on the proposed countermeasures to the secu-
rity issues in IoT.
5. An assessment of the open issues, challenges and
future research directions for developing secure IoT
applications.
B. ORGANIZATION
The organization of the rest of the paper is as follows: Section
II describes various application areas of IoT where high
security is required. Section III discusses various sources of
threats in an IoT environment. In section IV various con-
straints and requirements to be considered while developing
a secure IoT application are reviewed. Four major IoT se-
curity approaches, i.e., blockchain, fog computing, machine
learning, and edge computing are presented in Section V,
VI, VII, and VIII, respectively. Section IX describes various
open issues, challenges and upcoming research opportunities
in IoT security and finally, Section X concludes the paper.
II. SECURITY CRITICAL APPLICATION AREAS OF IOT
Security is highly critical in almost all IoT applications that
have already been deployed or are in the process of deploy-
ment. The applications of IoT are increasing very rapidly
and penetrating most of the existing industries. Although
operators support these IoT applications through existing
networking technologies, several of these applications need
more stringent security support from technologies they use.
In this section various security critical IoT applications are
discussed.
1. Smart Cities: Smart cities involve extensive use of
emerging computation and communication resources
for increasing the overall quality of life of the people
[15]. It includes smart homes, smart traffic manage-
ment, smart disaster management, smart utilities, etc.
There is a push to make cities smarter, and govern-
ments worldwide are encouraging their development
through various incentives [16]. Although the use of
smart applications is intended to improve the overall
quality of life of the citizens, it comes with a threat
to the privacy of the citizens. Smart card services tend
to put the card details and purchase behavior of the
citizens at risk. Smart mobility applications may leak
the location traces of the users. There are applications
TABLE 2: Related Surveys on IoT Security
Year Author Contributions
2016 Arsalan Mosenia et al., [7] A brief discussion of vulnerabilities faced by the edge side layer of IoT
2017 Yu wei et al., [8] Survey on using Edge Computing to secure IoT
2017 Jie Lin ea al., [9] Discussion on relationship between IoT and Fog Computing
2017 Y yang et al., [10] A brief discussion on most relevant limitations of IoT devices
2017 L chen , S. Thombre et al., [11] security issues specific to location-based services in IoT
2017 A H Ngu, V. Metsis et al., [12] Security issues related to the IoT middle ware
2018 I Farris, T Taleb et al., [13] Security mechanism for IoT security like SDN and NFB
2019 Ikram Ud din, M. Guizani et al,. [14] Trust Management Techniques for Internet of Things
VOLUME x, 2019 3
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

This work is licensed under a Creative Commons Attribution 3.0 License. For more information, see http://creativecomm
This article has been accepted for publication in a future issue of this journal, but has not been fully edited. Content may change p
10.1109/ACCESS.2019.2924045, IEEE Access
Vikas Hassija et al.: A Survey on IoT Security: Application Areas, Security Threats, and Solution Architectures
TABLE 3: List of Acronyms
Notation Meaning
ABSI Adaptive Binary Splitting Inspection
AMI Advanced Metering Infrastructure
AMQP Advanced Message Queuing Protocol
APT Advanced Persistent Threat
CoAP Constrained Application Protocol
DAC Distributed Autonomous Corporation
DAOs Decentalized Autonomous Organizations
DDoS Distributed denial of service
GPS Global Positioning System
HAN Home Area Network
IIoT Industrial Internet of Things
IOE Internet of Everything
IoT Internet of Things
M2M Machine to Machine
MCC Mobile Cloud Computing
MEC Mobile Edge Computing
MLP Multi-Layer Perceptron
MQTT Message Queuing Telemetry Transport
NFC Near Field Communication
NFV Network Function Virtualization
P2P peer to peer
QoS Quality of Service
RFID Radio Frequency Identification
RSN RFID sensor Networks
SDN Software-Defined Networking
SHA Secure Hash Algorithm
SIoT Social Internet of Things
SMQTT Secure Message Queue Telemetry Transport
STD Security Trust and Decentralization
WSN Wireless Sensor Networks
XMPP Extensible Messaging and Presence Protocol
XSS cross-site scripting
using which parents can keep track of their child. How-
ever, if such applications are hacked, then the safety of
the child can come to risk.
2. Smart Environment: Smart environment includes
various IoT applications such as fire detection in
forests, monitoring the level of snow in high alti-
tude regions, preventing landslides, early detection of
earthquakes, pollution monitoring, etc. All these IoT
applications are closely related to the life of human
beings and animals in those areas. The government
agencies involved in such fields will also be relying on
the information from these IoT applications. Security
breaches and vulnerability in any area related to such
IoT applications can have serious consequences. In this
context, both false negatives and false positives can
lead to disastrous results for such IoT applications. For
example, if the application starts detecting earthquakes
falsely, then it will lead to monetary losses for the
government and businesses. On the other hand, if the
application is not able to predict the earthquake, then
it will lead to the loss of both property and life. There-
fore, smart environment applications have to be highly
precise, and security breaches and data tampering must
be avoided.
3. Smart Metering and Smart Grids: Smart metering
includes applications related to various measurements,
monitoring, and management. The most common ap-
plication of smart metering is smart grids, where the
electricity consumption is measured and monitored.
Smart metering may also be used to address the prob-
lem of electricity theft [17]. Other applications of smart
metering include monitoring of water, oil and gas
levels in storage tanks and cisterns. Smart meters are
also used to monitor and optimize the performance of
solar energy plants by dynamically changing the angle
of solar panels to harvest the maximum possible solar
energy. There also exist some IoT applications that use
smart meters to measure the water pressure in water
transport systems or to measure the weight of goods.
However, smart metering systems are vulnerable to
both physical and cyber-attacks as compared to analog
meters that can be tampered only by physical attacks.
Also, smart meters or advanced metering infrastruc-
ture (AMI) are intended to perform functions beyond
generic energy usage recording. In a smart home area
network (HAN) all electric equipment at home are con-
nected to smart meters and the information collected
from these equipments can be used for load and cost
management. Intentional intrusion in such communi-
cation systems by the consumer or an adversary may
modify the collected information, leading to monetary
loss for the service providers or consumers [18].
4. Security and Emergencies: Security and emergencies
is another important area where various IoT applica-
tions are being deployed. It includes applications such
as allowing only authorized people in restricted areas
etc. Another application in this domain is the detection
of leakage of hazardous gases in industrial areas or
areas around chemical factories. Radiation levels can
also be measured in the areas around nuclear power
reactors or cellular base stations and alerts can be
generated when the radiation level is high. There are
various buildings whose systems have sensitive data or
that house sensitive goods. Security applications can
be deployed to protect sensitive data and goods. IoT
applications that detect various liquids can also be used
to prevent corrosion and break downs in such sensitive
buildings. Security breaches in such applications can
also have various serious consequences. For example,
the criminals may try to enter the restricted areas by
attacking the vulnerabilities in such applications. Also,
false radiation level alarms can have serious immediate
and long term impacts. For example, if infants are
exposed to high levels of radiation, then it may lead
to serious life threatening diseases in long term.
4 VOLUME x, 2019
This article has been accepted for publication in a future issue of this journal, but has not been fully edited. Content may change p
10.1109/ACCESS.2019.2924045, IEEE Access
Vikas Hassija et al.: A Survey on IoT Security: Application Areas, Security Threats, and Solution Architectures
TABLE 3: List of Acronyms
Notation Meaning
ABSI Adaptive Binary Splitting Inspection
AMI Advanced Metering Infrastructure
AMQP Advanced Message Queuing Protocol
APT Advanced Persistent Threat
CoAP Constrained Application Protocol
DAC Distributed Autonomous Corporation
DAOs Decentalized Autonomous Organizations
DDoS Distributed denial of service
GPS Global Positioning System
HAN Home Area Network
IIoT Industrial Internet of Things
IOE Internet of Everything
IoT Internet of Things
M2M Machine to Machine
MCC Mobile Cloud Computing
MEC Mobile Edge Computing
MLP Multi-Layer Perceptron
MQTT Message Queuing Telemetry Transport
NFC Near Field Communication
NFV Network Function Virtualization
P2P peer to peer
QoS Quality of Service
RFID Radio Frequency Identification
RSN RFID sensor Networks
SDN Software-Defined Networking
SHA Secure Hash Algorithm
SIoT Social Internet of Things
SMQTT Secure Message Queue Telemetry Transport
STD Security Trust and Decentralization
WSN Wireless Sensor Networks
XMPP Extensible Messaging and Presence Protocol
XSS cross-site scripting
using which parents can keep track of their child. How-
ever, if such applications are hacked, then the safety of
the child can come to risk.
2. Smart Environment: Smart environment includes
various IoT applications such as fire detection in
forests, monitoring the level of snow in high alti-
tude regions, preventing landslides, early detection of
earthquakes, pollution monitoring, etc. All these IoT
applications are closely related to the life of human
beings and animals in those areas. The government
agencies involved in such fields will also be relying on
the information from these IoT applications. Security
breaches and vulnerability in any area related to such
IoT applications can have serious consequences. In this
context, both false negatives and false positives can
lead to disastrous results for such IoT applications. For
example, if the application starts detecting earthquakes
falsely, then it will lead to monetary losses for the
government and businesses. On the other hand, if the
application is not able to predict the earthquake, then
it will lead to the loss of both property and life. There-
fore, smart environment applications have to be highly
precise, and security breaches and data tampering must
be avoided.
3. Smart Metering and Smart Grids: Smart metering
includes applications related to various measurements,
monitoring, and management. The most common ap-
plication of smart metering is smart grids, where the
electricity consumption is measured and monitored.
Smart metering may also be used to address the prob-
lem of electricity theft [17]. Other applications of smart
metering include monitoring of water, oil and gas
levels in storage tanks and cisterns. Smart meters are
also used to monitor and optimize the performance of
solar energy plants by dynamically changing the angle
of solar panels to harvest the maximum possible solar
energy. There also exist some IoT applications that use
smart meters to measure the water pressure in water
transport systems or to measure the weight of goods.
However, smart metering systems are vulnerable to
both physical and cyber-attacks as compared to analog
meters that can be tampered only by physical attacks.
Also, smart meters or advanced metering infrastruc-
ture (AMI) are intended to perform functions beyond
generic energy usage recording. In a smart home area
network (HAN) all electric equipment at home are con-
nected to smart meters and the information collected
from these equipments can be used for load and cost
management. Intentional intrusion in such communi-
cation systems by the consumer or an adversary may
modify the collected information, leading to monetary
loss for the service providers or consumers [18].
4. Security and Emergencies: Security and emergencies
is another important area where various IoT applica-
tions are being deployed. It includes applications such
as allowing only authorized people in restricted areas
etc. Another application in this domain is the detection
of leakage of hazardous gases in industrial areas or
areas around chemical factories. Radiation levels can
also be measured in the areas around nuclear power
reactors or cellular base stations and alerts can be
generated when the radiation level is high. There are
various buildings whose systems have sensitive data or
that house sensitive goods. Security applications can
be deployed to protect sensitive data and goods. IoT
applications that detect various liquids can also be used
to prevent corrosion and break downs in such sensitive
buildings. Security breaches in such applications can
also have various serious consequences. For example,
the criminals may try to enter the restricted areas by
attacking the vulnerabilities in such applications. Also,
false radiation level alarms can have serious immediate
and long term impacts. For example, if infants are
exposed to high levels of radiation, then it may lead
to serious life threatening diseases in long term.
4 VOLUME x, 2019
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

This work is licensed under a Creative Commons Attribution 3.0 License. For more information, see http://creativecomm
This article has been accepted for publication in a future issue of this journal, but has not been fully edited. Content may change p
10.1109/ACCESS.2019.2924045, IEEE Access
Vikas Hassija et al.: A Survey on IoT Security: Application Areas, Security Threats, and Solution Architectures
5. Smart Retail: IoT applications are being extensively
used in the retail sector. Various applications have been
developed to monitor the storage conditions of the
goods as they move along the supply chain. IoT is also
being used to control the tracking of products in the
warehouses so that restocking can be done optimally.
Various intelligent shopping applications are also being
developed for assisting the customers based on their
preferences, habits, allergies to certain components,
etc. Mechanisms to provide the experience of online
shopping to offline retailers using augmented reality
techniques have also been developed. Various compa-
nies in retail have faced security issues in deploying
and using various IoT applications. Some of these com-
panies include Apple, Home Depot, JP Morgan Chase
and Sony [19]. Adversaries may try to compromise the
IoT applications associated with storage conditions of
the goods and may try to send wrong information about
the products to the users in order to increase the sale.
If security features are not implemented in smart retail,
attackers may steal debit and credit card information,
phone numbers, email-addresses, etc. of the customers
which can lead to monetary losses for the customers
and retailers.
6. Smart Agriculture and Animal Farming: Smart
agriculture includes monitoring soil moisture, control-
ling micro-climate conditions, selective irrigation in
dry zones, and controlling humidity and temperature.
Usage of such advanced features in agriculture can help
in achieving high yields and can save farmers from
monetary losses. Control of temperature and humidity
levels in various grain and vegetable production can
help in preventing fungus and other microbial contam-
inants. Controlling the climate conditions can also help
in increasing the vegetable and crop yield and quality.
Just like crop monitoring, there are IoT applications to
monitor the activities and the health condition of farm
animals by attaching sensors to the animals. If such
applications are compromised, then it may lead to the
theft of animals from the farm and adversaries may also
damage the crops.
7. Home Automation: Home automation is one of the
most widely used and deployed IoT applications. This
includes applications such as those for remotely con-
trolling electrical appliances to save energy, systems
deployed on windows and doors to detect intruders, etc.
Monitoring systems are being applied to track energy
and water supply consumption, and users are being ad-
vised to save cost and resources. Authors in [20] have
proposed the use of logic based security algorithms
to enhance security level in homes. Intrusions are de-
tected by comparing the user actions at key locations
of the home with normal behavior of the user in these
locations. However, attackers may gain unauthorized
access of the IoT devices in the home and try to harm
the users. For instance, cases of home burglaries have
FIGURE 2: Layers in IoT System.
increased rapidly after the deployment of various home
automation systems [20]. There have also been various
cases in the past where the adversaries try to analyze
the type and volume of Internet traffic to/from the smart
home for judging the behavior and presence of the
residents.
III. SOURCES OF SECURITY THREATS IN IOT
APPLICATIONS
As discussed in Section I, any IoT application can be divided
into four layers: (1) sensing layer; (2) network layer; (3) mid-
dleware layer; and (4) application layer. Each of these layers
in an IoT application uses diverse technologies that bring a
number of issues and security threats. Figure 2 shows various
technologies, devices, and applications at these four layers.
This section discusses various possible security threats in
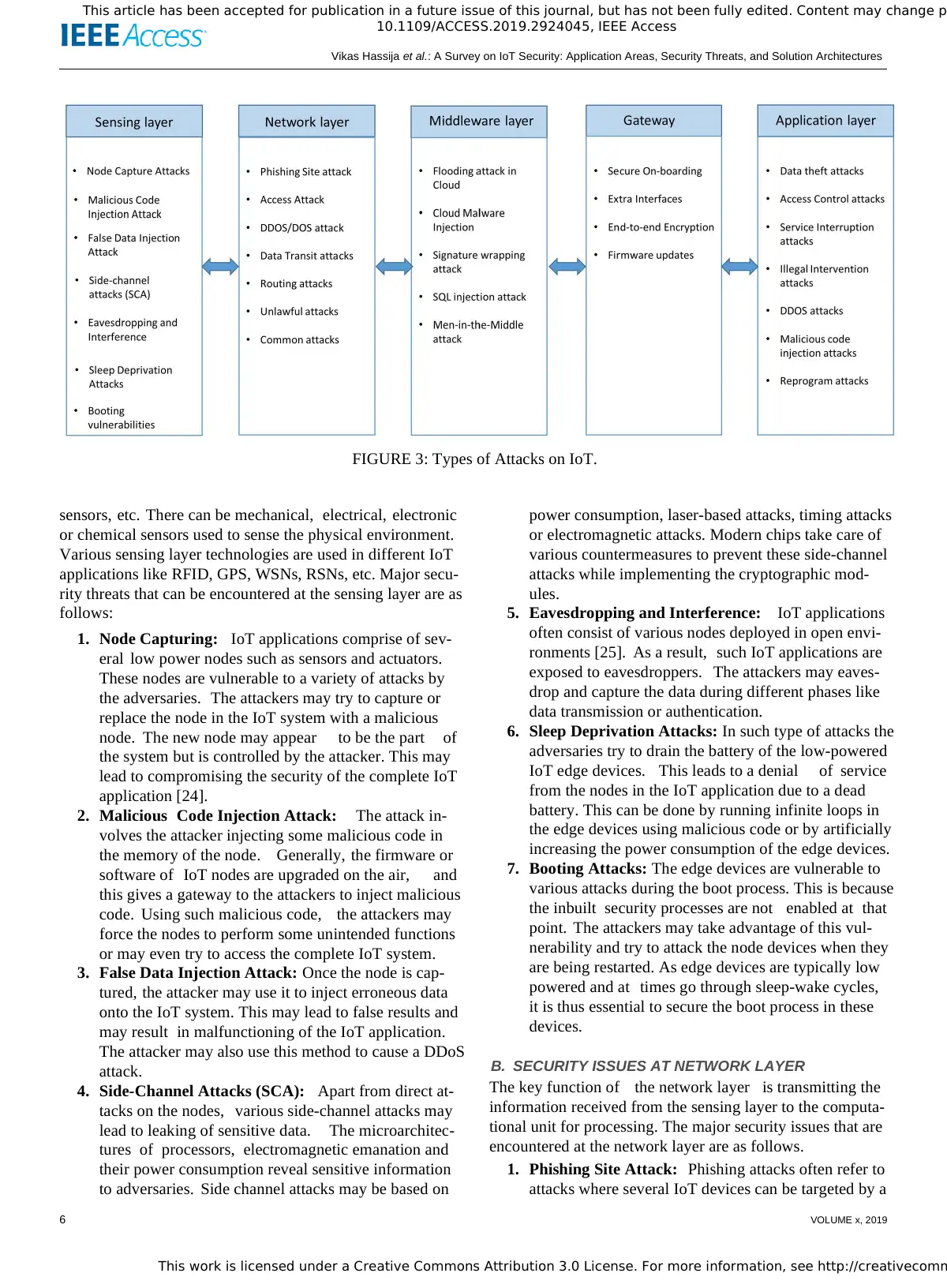
IoT applications for these four layers. Figure 3 shows the
possible attacks on these four layers. The special security
issues associated with the gateways that connect these layers
are also discussed in this section.
A. SECURITY ISSUES AT SENSING LAYER
The sensing layer mainly deals with physical IoT sensors and
actuators. Sensors sense the physical phenomenon happening
around them [21]–[23]. Actuators, on the other hand, perform
a certain action on the physical environment, based on the
sensed data. There are various kinds of sensors for sens-
ing different kinds of data, e.g., ultrasonic sensors, camera
sensors, smoke detection sensors, temperature and humidity
VOLUME x, 2019 5
This article has been accepted for publication in a future issue of this journal, but has not been fully edited. Content may change p
10.1109/ACCESS.2019.2924045, IEEE Access
Vikas Hassija et al.: A Survey on IoT Security: Application Areas, Security Threats, and Solution Architectures
5. Smart Retail: IoT applications are being extensively
used in the retail sector. Various applications have been
developed to monitor the storage conditions of the
goods as they move along the supply chain. IoT is also
being used to control the tracking of products in the
warehouses so that restocking can be done optimally.
Various intelligent shopping applications are also being
developed for assisting the customers based on their
preferences, habits, allergies to certain components,
etc. Mechanisms to provide the experience of online
shopping to offline retailers using augmented reality
techniques have also been developed. Various compa-
nies in retail have faced security issues in deploying
and using various IoT applications. Some of these com-
panies include Apple, Home Depot, JP Morgan Chase
and Sony [19]. Adversaries may try to compromise the
IoT applications associated with storage conditions of
the goods and may try to send wrong information about
the products to the users in order to increase the sale.
If security features are not implemented in smart retail,
attackers may steal debit and credit card information,
phone numbers, email-addresses, etc. of the customers
which can lead to monetary losses for the customers
and retailers.
6. Smart Agriculture and Animal Farming: Smart
agriculture includes monitoring soil moisture, control-
ling micro-climate conditions, selective irrigation in
dry zones, and controlling humidity and temperature.
Usage of such advanced features in agriculture can help
in achieving high yields and can save farmers from
monetary losses. Control of temperature and humidity
levels in various grain and vegetable production can
help in preventing fungus and other microbial contam-
inants. Controlling the climate conditions can also help
in increasing the vegetable and crop yield and quality.
Just like crop monitoring, there are IoT applications to
monitor the activities and the health condition of farm
animals by attaching sensors to the animals. If such
applications are compromised, then it may lead to the
theft of animals from the farm and adversaries may also
damage the crops.
7. Home Automation: Home automation is one of the
most widely used and deployed IoT applications. This
includes applications such as those for remotely con-
trolling electrical appliances to save energy, systems
deployed on windows and doors to detect intruders, etc.
Monitoring systems are being applied to track energy
and water supply consumption, and users are being ad-
vised to save cost and resources. Authors in [20] have
proposed the use of logic based security algorithms
to enhance security level in homes. Intrusions are de-
tected by comparing the user actions at key locations
of the home with normal behavior of the user in these
locations. However, attackers may gain unauthorized
access of the IoT devices in the home and try to harm
the users. For instance, cases of home burglaries have
FIGURE 2: Layers in IoT System.
increased rapidly after the deployment of various home
automation systems [20]. There have also been various
cases in the past where the adversaries try to analyze
the type and volume of Internet traffic to/from the smart
home for judging the behavior and presence of the
residents.
III. SOURCES OF SECURITY THREATS IN IOT
APPLICATIONS
As discussed in Section I, any IoT application can be divided
into four layers: (1) sensing layer; (2) network layer; (3) mid-
dleware layer; and (4) application layer. Each of these layers
in an IoT application uses diverse technologies that bring a
number of issues and security threats. Figure 2 shows various
technologies, devices, and applications at these four layers.
This section discusses various possible security threats in
IoT applications for these four layers. Figure 3 shows the
possible attacks on these four layers. The special security
issues associated with the gateways that connect these layers
are also discussed in this section.
A. SECURITY ISSUES AT SENSING LAYER
The sensing layer mainly deals with physical IoT sensors and
actuators. Sensors sense the physical phenomenon happening
around them [21]–[23]. Actuators, on the other hand, perform
a certain action on the physical environment, based on the
sensed data. There are various kinds of sensors for sens-
ing different kinds of data, e.g., ultrasonic sensors, camera
sensors, smoke detection sensors, temperature and humidity
VOLUME x, 2019 5
This work is licensed under a Creative Commons Attribution 3.0 License. For more information, see http://creativecomm
This article has been accepted for publication in a future issue of this journal, but has not been fully edited. Content may change p
10.1109/ACCESS.2019.2924045, IEEE Access
Vikas Hassija et al.: A Survey on IoT Security: Application Areas, Security Threats, and Solution Architectures
FIGURE 3: Types of Attacks on IoT.
sensors, etc. There can be mechanical, electrical, electronic
or chemical sensors used to sense the physical environment.
Various sensing layer technologies are used in different IoT
applications like RFID, GPS, WSNs, RSNs, etc. Major secu-
rity threats that can be encountered at the sensing layer are as
follows:
1. Node Capturing: IoT applications comprise of sev-
eral low power nodes such as sensors and actuators.
These nodes are vulnerable to a variety of attacks by
the adversaries. The attackers may try to capture or
replace the node in the IoT system with a malicious
node. The new node may appear to be the part of
the system but is controlled by the attacker. This may
lead to compromising the security of the complete IoT
application [24].
2. Malicious Code Injection Attack: The attack in-
volves the attacker injecting some malicious code in
the memory of the node. Generally, the firmware or
software of IoT nodes are upgraded on the air, and
this gives a gateway to the attackers to inject malicious
code. Using such malicious code, the attackers may
force the nodes to perform some unintended functions
or may even try to access the complete IoT system.
3. False Data Injection Attack: Once the node is cap-
tured, the attacker may use it to inject erroneous data
onto the IoT system. This may lead to false results and
may result in malfunctioning of the IoT application.
The attacker may also use this method to cause a DDoS
attack.
4. Side-Channel Attacks (SCA): Apart from direct at-
tacks on the nodes, various side-channel attacks may
lead to leaking of sensitive data. The microarchitec-
tures of processors, electromagnetic emanation and
their power consumption reveal sensitive information
to adversaries. Side channel attacks may be based on
power consumption, laser-based attacks, timing attacks
or electromagnetic attacks. Modern chips take care of
various countermeasures to prevent these side-channel
attacks while implementing the cryptographic mod-
ules.
5. Eavesdropping and Interference: IoT applications
often consist of various nodes deployed in open envi-
ronments [25]. As a result, such IoT applications are
exposed to eavesdroppers. The attackers may eaves-
drop and capture the data during different phases like
data transmission or authentication.
6. Sleep Deprivation Attacks: In such type of attacks the
adversaries try to drain the battery of the low-powered
IoT edge devices. This leads to a denial of service
from the nodes in the IoT application due to a dead
battery. This can be done by running infinite loops in
the edge devices using malicious code or by artificially
increasing the power consumption of the edge devices.
7. Booting Attacks: The edge devices are vulnerable to
various attacks during the boot process. This is because
the inbuilt security processes are not enabled at that
point. The attackers may take advantage of this vul-
nerability and try to attack the node devices when they
are being restarted. As edge devices are typically low
powered and at times go through sleep-wake cycles,
it is thus essential to secure the boot process in these
devices.
B. SECURITY ISSUES AT NETWORK LAYER
The key function of the network layer is transmitting the
information received from the sensing layer to the computa-
tional unit for processing. The major security issues that are
encountered at the network layer are as follows.
1. Phishing Site Attack: Phishing attacks often refer to
attacks where several IoT devices can be targeted by a
6 VOLUME x, 2019
This article has been accepted for publication in a future issue of this journal, but has not been fully edited. Content may change p
10.1109/ACCESS.2019.2924045, IEEE Access
Vikas Hassija et al.: A Survey on IoT Security: Application Areas, Security Threats, and Solution Architectures
FIGURE 3: Types of Attacks on IoT.
sensors, etc. There can be mechanical, electrical, electronic
or chemical sensors used to sense the physical environment.
Various sensing layer technologies are used in different IoT
applications like RFID, GPS, WSNs, RSNs, etc. Major secu-
rity threats that can be encountered at the sensing layer are as
follows:
1. Node Capturing: IoT applications comprise of sev-
eral low power nodes such as sensors and actuators.
These nodes are vulnerable to a variety of attacks by
the adversaries. The attackers may try to capture or
replace the node in the IoT system with a malicious
node. The new node may appear to be the part of
the system but is controlled by the attacker. This may
lead to compromising the security of the complete IoT
application [24].
2. Malicious Code Injection Attack: The attack in-
volves the attacker injecting some malicious code in
the memory of the node. Generally, the firmware or
software of IoT nodes are upgraded on the air, and
this gives a gateway to the attackers to inject malicious
code. Using such malicious code, the attackers may
force the nodes to perform some unintended functions
or may even try to access the complete IoT system.
3. False Data Injection Attack: Once the node is cap-
tured, the attacker may use it to inject erroneous data
onto the IoT system. This may lead to false results and
may result in malfunctioning of the IoT application.
The attacker may also use this method to cause a DDoS
attack.
4. Side-Channel Attacks (SCA): Apart from direct at-
tacks on the nodes, various side-channel attacks may
lead to leaking of sensitive data. The microarchitec-
tures of processors, electromagnetic emanation and
their power consumption reveal sensitive information
to adversaries. Side channel attacks may be based on
power consumption, laser-based attacks, timing attacks
or electromagnetic attacks. Modern chips take care of
various countermeasures to prevent these side-channel
attacks while implementing the cryptographic mod-
ules.
5. Eavesdropping and Interference: IoT applications
often consist of various nodes deployed in open envi-
ronments [25]. As a result, such IoT applications are
exposed to eavesdroppers. The attackers may eaves-
drop and capture the data during different phases like
data transmission or authentication.
6. Sleep Deprivation Attacks: In such type of attacks the
adversaries try to drain the battery of the low-powered
IoT edge devices. This leads to a denial of service
from the nodes in the IoT application due to a dead
battery. This can be done by running infinite loops in
the edge devices using malicious code or by artificially
increasing the power consumption of the edge devices.
7. Booting Attacks: The edge devices are vulnerable to
various attacks during the boot process. This is because
the inbuilt security processes are not enabled at that
point. The attackers may take advantage of this vul-
nerability and try to attack the node devices when they
are being restarted. As edge devices are typically low
powered and at times go through sleep-wake cycles,
it is thus essential to secure the boot process in these
devices.
B. SECURITY ISSUES AT NETWORK LAYER
The key function of the network layer is transmitting the
information received from the sensing layer to the computa-
tional unit for processing. The major security issues that are
encountered at the network layer are as follows.
1. Phishing Site Attack: Phishing attacks often refer to
attacks where several IoT devices can be targeted by a
6 VOLUME x, 2019
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

This work is licensed under a Creative Commons Attribution 3.0 License. For more information, see http://creativecomm
This article has been accepted for publication in a future issue of this journal, but has not been fully edited. Content may change p
10.1109/ACCESS.2019.2924045, IEEE Access
Vikas Hassija et al.: A Survey on IoT Security: Application Areas, Security Threats, and Solution Architectures
minimal effort put by the attacker. The attackers expect
that at least few of the devices will become a victim of
the attack. There is a possibility of encountering phish-
ing sites in the course of users visiting web pages on
the Internet. Once the user’s account and password are
compromised, the whole IoT environment being used
by the user becomes vulnerable to cyber attacks. The
network layer in IoT is highly vulnerable to phishing
sites attacks [26].
2. Access Attack: Access attack is also referred to as ad-
vanced persistent threat (APT). This is a type of attack
in which an unauthorized person or an adversary gains
access to the IoT network. The attacker can continue
to stay in the network undetected for a long duration.
The purpose or intention of this kind of attack is to
steal valuable data or information, rather than to cause
damage to the network. IoT applications continuously
receive and transfer valuable data and are therefore
highly vulnerable to such attacks [27].
3. DDoS/DoS Attack: In this kind of attacks, the attacker
floods the target servers with a large number of un-
wanted requests. This incapacitates the target server,
thereby disrupting services to genuine users. If there
are multiple sources used by the attacker to flood the
target server, then such an attack is termed as DDoS
or distributed denial of service attack. Such attacks are
not specific to IoT applications, but due to the hetero-
geneity and complexity of IoT networks, the network
layer of the IoT is prone to such attacks. Many IoT
devices in IoT applications are not strongly configured,
and thus become easy gateways for attackers to launch
DDoS attacks on the target servers. The Mirai botnet
attack as discussed in Section I used this vulnerability
and blocked various servers by constantly propagating
requests to the weakly configured IoT devices [28].
4. Data Transit Attacks: IoT applications deal with a
lot of data storage and exchange. Data is valuable, and
therefore it is always the target of hackers and other ad-
versaries. Data that is stored in the local servers or the
cloud has a security risk, but the data that is in transit
or is moving from one location to another is even more
vulnerable to cyber attacks. In IoT applications, there
is a lot of data movement between sensors, actuators,
cloud, etc. Different connection technologies are used
in such data movements, and therefore IoT applications
are susceptible to data breaches.
5. Routing Attacks: In such attacks, malicious nodes
in an IoT application may try to redirect the routing
paths during data transit. Sinkhole attacks are a specific
kind of routing attack in which an adversary advertises
an artificial shortest routing path and attracts nodes to
route traffic through it. A worm-hole attack is another
attack which can become serious security threat if
combined with other attacks such as sinkhole attacks.
A warm-hole is an out of band connection between two
nodes for fast packet transfer. An attacker can create a
warm-hole between a compromised node and a device
on the internet and try to bypass the basic security
protocols in an IoT application.
C. SECURITY ISSUES AT MIDDLEWARE LAYER
The role of the middleware in IoT is to create an abstraction
layer between the network layer and the application layer.
Middleware can also provide powerful computing and stor-
age capabilities [29]. This layer provides APIs to fulfill the
demands of the application layer. Middleware layer includes
brokers, persistent data stores, queuing systems, machine
learning, etc. Although the middleware layer is useful to
provide a reliable and robust IoT application, it is also sus-
ceptible to various attacks. These attacks can take control
of the entire IoT application by infecting the middleware.
Database security and cloud security are other main security
challenges in the middleware layer. Various possible attacks
in the middleware layer are discussed as follows.
1. Man-in-the-Middle Attack: The MQTT protocol
uses publish-subscribe model of communication be-
tween clients and subscribers using the MQTT bro-
ker, which effectively acts as a proxy. This helps in
decoupling the publishing and the subscribing clients
from each other and messages can be sent without the
knowledge of the destination. If the attacker can con-
trol the broker and become a man-in-the-middle, then
he/she can get complete control of all communication
without any knowledge of the clients.
2. SQL Injection Attack: MIddleware is also suscep-
tible to SQL Injection (SQLi) attacks. In such at-
tacks, attacker can embed malicious SQL statements
in a program [30], [31]. Then, the attackers can obtain
private data of any user and can even alter records
in the database [32]. Open Web Application Security
Project (OWASP) has listed SQLi as a top threat to web
security in their OWASP top 10 2018 document [33].
3. Signature Wrapping Attack: In the web services
used in the middleware, XML signatures are used [34].
In a signature wrapping attack, the attacker breaks
the signature algorithm and can execute opera-
tions or modify eavesdropped message by exploit-
ing vulnerabilities in SOAP (Simple Object Access
Protocol) [35].
4. Cloud Malware Injection: In cloud malware injec-
tion, the attacker can obtain control, inject malicious
code or can inject a virtual machine into the cloud.
The attacker pretends to be a valid service by trying
to create a virtual machine instance or a malicious
service module. In this way, the attacker can obtain
access to service requests of the victim’s service and
can capture sensitive data which can be modified as per
the instance.
5. Flooding Attack in Cloud: This attack works almost
the same as DoS attack in the cloud and affects the
quality of service (QoS). For depleting cloud resources,
the attackers continuously send multiple requests to a
VOLUME x, 2019 7
This article has been accepted for publication in a future issue of this journal, but has not been fully edited. Content may change p
10.1109/ACCESS.2019.2924045, IEEE Access
Vikas Hassija et al.: A Survey on IoT Security: Application Areas, Security Threats, and Solution Architectures
minimal effort put by the attacker. The attackers expect
that at least few of the devices will become a victim of
the attack. There is a possibility of encountering phish-
ing sites in the course of users visiting web pages on
the Internet. Once the user’s account and password are
compromised, the whole IoT environment being used
by the user becomes vulnerable to cyber attacks. The
network layer in IoT is highly vulnerable to phishing
sites attacks [26].
2. Access Attack: Access attack is also referred to as ad-
vanced persistent threat (APT). This is a type of attack
in which an unauthorized person or an adversary gains
access to the IoT network. The attacker can continue
to stay in the network undetected for a long duration.
The purpose or intention of this kind of attack is to
steal valuable data or information, rather than to cause
damage to the network. IoT applications continuously
receive and transfer valuable data and are therefore
highly vulnerable to such attacks [27].
3. DDoS/DoS Attack: In this kind of attacks, the attacker
floods the target servers with a large number of un-
wanted requests. This incapacitates the target server,
thereby disrupting services to genuine users. If there
are multiple sources used by the attacker to flood the
target server, then such an attack is termed as DDoS
or distributed denial of service attack. Such attacks are
not specific to IoT applications, but due to the hetero-
geneity and complexity of IoT networks, the network
layer of the IoT is prone to such attacks. Many IoT
devices in IoT applications are not strongly configured,
and thus become easy gateways for attackers to launch
DDoS attacks on the target servers. The Mirai botnet
attack as discussed in Section I used this vulnerability
and blocked various servers by constantly propagating
requests to the weakly configured IoT devices [28].
4. Data Transit Attacks: IoT applications deal with a
lot of data storage and exchange. Data is valuable, and
therefore it is always the target of hackers and other ad-
versaries. Data that is stored in the local servers or the
cloud has a security risk, but the data that is in transit
or is moving from one location to another is even more
vulnerable to cyber attacks. In IoT applications, there
is a lot of data movement between sensors, actuators,
cloud, etc. Different connection technologies are used
in such data movements, and therefore IoT applications
are susceptible to data breaches.
5. Routing Attacks: In such attacks, malicious nodes
in an IoT application may try to redirect the routing
paths during data transit. Sinkhole attacks are a specific
kind of routing attack in which an adversary advertises
an artificial shortest routing path and attracts nodes to
route traffic through it. A worm-hole attack is another
attack which can become serious security threat if
combined with other attacks such as sinkhole attacks.
A warm-hole is an out of band connection between two
nodes for fast packet transfer. An attacker can create a
warm-hole between a compromised node and a device
on the internet and try to bypass the basic security
protocols in an IoT application.
C. SECURITY ISSUES AT MIDDLEWARE LAYER
The role of the middleware in IoT is to create an abstraction
layer between the network layer and the application layer.
Middleware can also provide powerful computing and stor-
age capabilities [29]. This layer provides APIs to fulfill the
demands of the application layer. Middleware layer includes
brokers, persistent data stores, queuing systems, machine
learning, etc. Although the middleware layer is useful to
provide a reliable and robust IoT application, it is also sus-
ceptible to various attacks. These attacks can take control
of the entire IoT application by infecting the middleware.
Database security and cloud security are other main security
challenges in the middleware layer. Various possible attacks
in the middleware layer are discussed as follows.
1. Man-in-the-Middle Attack: The MQTT protocol
uses publish-subscribe model of communication be-
tween clients and subscribers using the MQTT bro-
ker, which effectively acts as a proxy. This helps in
decoupling the publishing and the subscribing clients
from each other and messages can be sent without the
knowledge of the destination. If the attacker can con-
trol the broker and become a man-in-the-middle, then
he/she can get complete control of all communication
without any knowledge of the clients.
2. SQL Injection Attack: MIddleware is also suscep-
tible to SQL Injection (SQLi) attacks. In such at-
tacks, attacker can embed malicious SQL statements
in a program [30], [31]. Then, the attackers can obtain
private data of any user and can even alter records
in the database [32]. Open Web Application Security
Project (OWASP) has listed SQLi as a top threat to web
security in their OWASP top 10 2018 document [33].
3. Signature Wrapping Attack: In the web services
used in the middleware, XML signatures are used [34].
In a signature wrapping attack, the attacker breaks
the signature algorithm and can execute opera-
tions or modify eavesdropped message by exploit-
ing vulnerabilities in SOAP (Simple Object Access
Protocol) [35].
4. Cloud Malware Injection: In cloud malware injec-
tion, the attacker can obtain control, inject malicious
code or can inject a virtual machine into the cloud.
The attacker pretends to be a valid service by trying
to create a virtual machine instance or a malicious
service module. In this way, the attacker can obtain
access to service requests of the victim’s service and
can capture sensitive data which can be modified as per
the instance.
5. Flooding Attack in Cloud: This attack works almost
the same as DoS attack in the cloud and affects the
quality of service (QoS). For depleting cloud resources,
the attackers continuously send multiple requests to a
VOLUME x, 2019 7
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

This work is licensed under a Creative Commons Attribution 3.0 License. For more information, see http://creativecomm
This article has been accepted for publication in a future issue of this journal, but has not been fully edited. Content may change p
10.1109/ACCESS.2019.2924045, IEEE Access
Vikas Hassija et al.: A Survey on IoT Security: Application Areas, Security Threats, and Solution Architectures
service. These attacks can have a big impact on cloud
systems by increasing the load on the cloud servers.
D. SECURITY ISSUES AT GATEWAYS
Gateway is a broad layer that has an important role in con-
necting multiple devices, people, things and cloud services.
Gateways also help in providing hardware and software
solutions for IoT devices. Gateways are used for decrypting
and encrypting IoT data and translating protocols for com-
munication between different layers [36]. IoT systems today
are heterogeneous including LoraWan, ZigBee, Z-Wave and
TCP/IP stacks with many gateways in between. Some of the
security challenges for IoT gateway are discussed below.
1. Secure On-boarding: When a new device or sensor is
installed in an IoT system, it is imperative to protect
encryption keys. Gateways act as an intermediary be-
tween the new devices and the managing services, and
all the keys pass through the gateways. The gateways
are susceptible to man-in-the-middle attacks and eaves-
dropping to capture the encryption keys, especially
during the on-boarding process.
2. Extra Interfaces: Minimizing the attack surface is an
important strategy that needs to be kept in mind while
installing the IoT devices [37]. Only the necessary
interfaces and protocols should be implemented by
an IoT gateway manufacturer. Some of the services
and functionalities should be restricted for end-users to
avoid backdoor authentication or information breach.
3. End-to-End Encryption: True end-to-end application
layer security is required to ensure the confidentiality
of the data [38]. The application should not let anyone
other than the unique recipient to decrypt the encrypted
messages. Although Zigbee and Zwave protocols sup-
port encryption, this is not end-to-end encryption, be-
cause, in order to translate the information from one
protocol to another, the gateways are required to de-
crypt and re-encrypt the messages. This decryption at
the gateway level makes the data susceptible to data
breaches.
4. Firmware updates: Most IoT devices are resource
constrained, and therefore they do not have an user
interface or the computation power to download and
install the firmware updates. Generally, gateways are
used to download and apply the firmware updates.
The current and new version of the firmware should
be recorded, and validity of the signatures should be
checked for secure firmware updates.
E. SECURITY ISSUES AT APPLICATION LAYER
The application layer directly deals with and provides ser-
vices to the end users. IoT applications like smart homes,
smart meters, smart cities, smart grids, etc. lie in this layer.
This layer has specific security issues that are not present
in other layers, such as data theft and privacy issues. The
security issues in this layer are also specific to different
applications. Many IoT applications also consist of a sub-
layer between the network layer and application layer, usu-
ally termed as an application support layer or middleware
layer. The support layer supports various business services
and helps in intelligent resource allocation and computation.
Major security issues encountered by the application layer
are discussed below.
1. Data Thefts: IoT applications deal with lot of critical
and private data. The data in transit is even more
vulnerable to attacks than data at rest, and in IoT
applications, there is a lot of data movement. The users
will be reluctant to register their private data on IoT
applications if these applications are vulnerable to data
theft attacks. Data encryption, data isolation, user and
network authentication, privacy management, etc. are
some of the techniques and protocols being used to
secure IoT applications against data thefts.
2. Access Control Attacks: Access control is authoriza-
tion mechanism that allows only legitimate users or
processes to access the data or account. Access control
attack is a critical attack in IoT applications because
once the access is compromised, then the complete IoT
application becomes vulnerable to attacks.
3. Service Interruption Attacks: These attacks are also
referred to as illegal interruption attacks or DDoS
attacks in existing literature. There have been various
instances of such attacks on IoT applications. Such
attacks deprive legitimate users from using the services
of IoT applications by artificially making the servers or
network too busy to respond.
4. Malicious Code Injection Attacks: Attackers gener-
ally go for the easiest or simplest method they can use
to break into a system or network. If the system is
vulnerable to malicious scripts and misdirections due
to insufficient code checks, then that would be the first
entry point that an attacker would choose. Generally,
attackers use XSS (cross-site scripting) to inject some
malicious script into an otherwise trusted website. A
successful XSS attack can result in the hijacking of an
IoT account and can paralyze the IoT system.
5. Sniffing Attacks: The attackers may use sniffer appli-
cations to monitor the network traffic in IoT applica-
tions. This may allow the attacker to gain access to
confidential user data if there are not enough security
protocols implemented to prevent it [39].
6. Reprogram Attacks: If the programming process is
not protected, then the attackers can try to reprogram
the IoT objects remotely. This may lead to the hijack-
ing of the IoT network [40].
IV. IMPROVEMENTS AND ENHANCEMENTS REQUIRED
FOR UPCOMING IOT APPLICATIONS
Personal computers (PC) and smartphones have a number
of security features built into them, e.g., firewalls, anti-
virus softwares, address space randomization, etc. These
safety shields are, in general, missing in various IoT devices
8 VOLUME x, 2019
This article has been accepted for publication in a future issue of this journal, but has not been fully edited. Content may change p
10.1109/ACCESS.2019.2924045, IEEE Access
Vikas Hassija et al.: A Survey on IoT Security: Application Areas, Security Threats, and Solution Architectures
service. These attacks can have a big impact on cloud
systems by increasing the load on the cloud servers.
D. SECURITY ISSUES AT GATEWAYS
Gateway is a broad layer that has an important role in con-
necting multiple devices, people, things and cloud services.
Gateways also help in providing hardware and software
solutions for IoT devices. Gateways are used for decrypting
and encrypting IoT data and translating protocols for com-
munication between different layers [36]. IoT systems today
are heterogeneous including LoraWan, ZigBee, Z-Wave and
TCP/IP stacks with many gateways in between. Some of the
security challenges for IoT gateway are discussed below.
1. Secure On-boarding: When a new device or sensor is
installed in an IoT system, it is imperative to protect
encryption keys. Gateways act as an intermediary be-
tween the new devices and the managing services, and
all the keys pass through the gateways. The gateways
are susceptible to man-in-the-middle attacks and eaves-
dropping to capture the encryption keys, especially
during the on-boarding process.
2. Extra Interfaces: Minimizing the attack surface is an
important strategy that needs to be kept in mind while
installing the IoT devices [37]. Only the necessary
interfaces and protocols should be implemented by
an IoT gateway manufacturer. Some of the services
and functionalities should be restricted for end-users to
avoid backdoor authentication or information breach.
3. End-to-End Encryption: True end-to-end application
layer security is required to ensure the confidentiality
of the data [38]. The application should not let anyone
other than the unique recipient to decrypt the encrypted
messages. Although Zigbee and Zwave protocols sup-
port encryption, this is not end-to-end encryption, be-
cause, in order to translate the information from one
protocol to another, the gateways are required to de-
crypt and re-encrypt the messages. This decryption at
the gateway level makes the data susceptible to data
breaches.
4. Firmware updates: Most IoT devices are resource
constrained, and therefore they do not have an user
interface or the computation power to download and
install the firmware updates. Generally, gateways are
used to download and apply the firmware updates.
The current and new version of the firmware should
be recorded, and validity of the signatures should be
checked for secure firmware updates.
E. SECURITY ISSUES AT APPLICATION LAYER
The application layer directly deals with and provides ser-
vices to the end users. IoT applications like smart homes,
smart meters, smart cities, smart grids, etc. lie in this layer.
This layer has specific security issues that are not present
in other layers, such as data theft and privacy issues. The
security issues in this layer are also specific to different
applications. Many IoT applications also consist of a sub-
layer between the network layer and application layer, usu-
ally termed as an application support layer or middleware
layer. The support layer supports various business services
and helps in intelligent resource allocation and computation.
Major security issues encountered by the application layer
are discussed below.
1. Data Thefts: IoT applications deal with lot of critical
and private data. The data in transit is even more
vulnerable to attacks than data at rest, and in IoT
applications, there is a lot of data movement. The users
will be reluctant to register their private data on IoT
applications if these applications are vulnerable to data
theft attacks. Data encryption, data isolation, user and
network authentication, privacy management, etc. are
some of the techniques and protocols being used to
secure IoT applications against data thefts.
2. Access Control Attacks: Access control is authoriza-
tion mechanism that allows only legitimate users or
processes to access the data or account. Access control
attack is a critical attack in IoT applications because
once the access is compromised, then the complete IoT
application becomes vulnerable to attacks.
3. Service Interruption Attacks: These attacks are also
referred to as illegal interruption attacks or DDoS
attacks in existing literature. There have been various
instances of such attacks on IoT applications. Such
attacks deprive legitimate users from using the services
of IoT applications by artificially making the servers or
network too busy to respond.
4. Malicious Code Injection Attacks: Attackers gener-
ally go for the easiest or simplest method they can use
to break into a system or network. If the system is
vulnerable to malicious scripts and misdirections due
to insufficient code checks, then that would be the first
entry point that an attacker would choose. Generally,
attackers use XSS (cross-site scripting) to inject some
malicious script into an otherwise trusted website. A
successful XSS attack can result in the hijacking of an
IoT account and can paralyze the IoT system.
5. Sniffing Attacks: The attackers may use sniffer appli-
cations to monitor the network traffic in IoT applica-
tions. This may allow the attacker to gain access to
confidential user data if there are not enough security
protocols implemented to prevent it [39].
6. Reprogram Attacks: If the programming process is
not protected, then the attackers can try to reprogram
the IoT objects remotely. This may lead to the hijack-
ing of the IoT network [40].
IV. IMPROVEMENTS AND ENHANCEMENTS REQUIRED
FOR UPCOMING IOT APPLICATIONS
Personal computers (PC) and smartphones have a number
of security features built into them, e.g., firewalls, anti-
virus softwares, address space randomization, etc. These
safety shields are, in general, missing in various IoT devices
8 VOLUME x, 2019

This work is licensed under a Creative Commons Attribution 3.0 License. For more information, see http://creativecomm
This article has been accepted for publication in a future issue of this journal, but has not been fully edited. Content may change p
10.1109/ACCESS.2019.2924045, IEEE Access
Vikas Hassija et al.: A Survey on IoT Security: Application Areas, Security Threats, and Solution Architectures
FIGURE 4: Research papers addressing IoT security using various security techniques.
that are already in the market. There are various security
challenges that the IoT applications are facing currently. A
well-defined framework and standard for an end-to-end IoT
application is not yet available. An IoT application is not a
standalone application, and it is an assembled product which
includes work from many individuals and industries. At every
layer starting from sensing to the application, several diverse
products and technologies are being used. These include a
large number of sensors and actuators at the edge nodes.
There are multiple communication standards like cellular
network, WiFi, IEEE 802.15.4, Insteon, dash7, Bluetooth,
etc. A handshake mechanism is required between all these
standards. Apart from this, various connectivity technologies
are being used at different levels in the same IoT application
like Zigbee, 6LOWPAN, wireless HART, Z-Wave, ISA100,
Bluetooth, NFC, RFID, etc. Over and above this, the generic
HTTP protocol cannot be used in the application layer. HTTP
is not suitable for resource-constrained environments because
it is heavy-weight and thus incurs a large parsing overhead.
Therefore, at the application layer also there are many alter-
nate protocols that have been deployed for IoT environments.
Some of them are MQTT, SMQTT, CoAP, XMPP, AMQP,
M3DA, JavascriptIoT, etc.
Due to the intense diversity of protocols, technologies,
and devices in an IoT application, the significant trade-offs
are between cost effectiveness, security, reliability, privacy,
coverage, latency, etc. If one metric for improvement is
optimized, it may result in the degradation of other metric.
For example, imposing too many security checks and proto-
cols in all data transactions in IoT applications may end up
increasing the cost and latency of the application, thereby,
making it unsuitable for the users.
A typical IoT application consists of a big chain of
connected devices, technologies, domains, and geographies.
Even if one of the device or technology or their combination
is left weak, then that may be the cause of a security threat
for the entire application. The chain is considered to be as
strong as the weakest link. There has been a large increase
in the number of weak links in IoT applications recently. For
example, even basic IoT applications such as smart bulbs and
smart door locks can be used as a weak link in a smart home
IoT application to extract the user’s WiFi password [41] and
[42].
The large number of IoT devices being deployed around
the world to make it smart generates a large amount of en-
vironment and user-related data. A lot of private information
can be inferred from this data, and that can be another cause
of threat for an individual and society at large [7]. As a result,
significant improvements and enhancements in the current
IoT application structure and framework are required to make
it reliable, secure and robust. In this regard:
1. Rigorous penetration testing for IoT devices is nec-
essary to quantify the level of risk involved in de-
ploying these devices in different applications. Based
on the risk involved, a priority list can be made and
the devices can be deployed appropriately in different
VOLUME x, 2019 9
This article has been accepted for publication in a future issue of this journal, but has not been fully edited. Content may change p
10.1109/ACCESS.2019.2924045, IEEE Access
Vikas Hassija et al.: A Survey on IoT Security: Application Areas, Security Threats, and Solution Architectures
FIGURE 4: Research papers addressing IoT security using various security techniques.
that are already in the market. There are various security
challenges that the IoT applications are facing currently. A
well-defined framework and standard for an end-to-end IoT
application is not yet available. An IoT application is not a
standalone application, and it is an assembled product which
includes work from many individuals and industries. At every
layer starting from sensing to the application, several diverse
products and technologies are being used. These include a
large number of sensors and actuators at the edge nodes.
There are multiple communication standards like cellular
network, WiFi, IEEE 802.15.4, Insteon, dash7, Bluetooth,
etc. A handshake mechanism is required between all these
standards. Apart from this, various connectivity technologies
are being used at different levels in the same IoT application
like Zigbee, 6LOWPAN, wireless HART, Z-Wave, ISA100,
Bluetooth, NFC, RFID, etc. Over and above this, the generic
HTTP protocol cannot be used in the application layer. HTTP
is not suitable for resource-constrained environments because
it is heavy-weight and thus incurs a large parsing overhead.
Therefore, at the application layer also there are many alter-
nate protocols that have been deployed for IoT environments.
Some of them are MQTT, SMQTT, CoAP, XMPP, AMQP,
M3DA, JavascriptIoT, etc.
Due to the intense diversity of protocols, technologies,
and devices in an IoT application, the significant trade-offs
are between cost effectiveness, security, reliability, privacy,
coverage, latency, etc. If one metric for improvement is
optimized, it may result in the degradation of other metric.
For example, imposing too many security checks and proto-
cols in all data transactions in IoT applications may end up
increasing the cost and latency of the application, thereby,
making it unsuitable for the users.
A typical IoT application consists of a big chain of
connected devices, technologies, domains, and geographies.
Even if one of the device or technology or their combination
is left weak, then that may be the cause of a security threat
for the entire application. The chain is considered to be as
strong as the weakest link. There has been a large increase
in the number of weak links in IoT applications recently. For
example, even basic IoT applications such as smart bulbs and
smart door locks can be used as a weak link in a smart home
IoT application to extract the user’s WiFi password [41] and
[42].
The large number of IoT devices being deployed around
the world to make it smart generates a large amount of en-
vironment and user-related data. A lot of private information
can be inferred from this data, and that can be another cause
of threat for an individual and society at large [7]. As a result,
significant improvements and enhancements in the current
IoT application structure and framework are required to make
it reliable, secure and robust. In this regard:
1. Rigorous penetration testing for IoT devices is nec-
essary to quantify the level of risk involved in de-
ploying these devices in different applications. Based
on the risk involved, a priority list can be made and
the devices can be deployed appropriately in different
VOLUME x, 2019 9
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

This work is licensed under a Creative Commons Attribution 3.0 License. For more information, see http://creativecomm
This article has been accepted for publication in a future issue of this journal, but has not been fully edited. Content may change p
10.1109/ACCESS.2019.2924045, IEEE Access
Vikas Hassija et al.: A Survey on IoT Security: Application Areas, Security Threats, and Solution Architectures
applications.
2. Encryption techniques are being used in IoT system at
different layers and protocols. However, there are var-
ious levels of encrypt, decrypt, and re-encrypt cycles
in the complete system. These cycles make the system
vulnerable to attacks. End to end encryption would be
a promising solution to prevent different attacks.
3. Authenticate-always protocols need to be imple-
mented. Whenever a device wants to interact with
another device, an authentication process should be
implemented. Digital certificates can be a promising
solution to provide seamless authentication with bound
identities that are tied to cryptographic protocols.
4. Any IoT security framework being implemented
should be tested and confirmed for scalability. The
security protocols should not be working only for a
limited set of users. The real threats start coming only
when the application becomes public and starts being
used widely in the public domain. Therefore, proper
strategy and planning are required.
5. A mechanism based on encryption techniques like
RSA, SHA256, or hash chains is required to secure the
user and environment data from being captured. IoT
devices need to be designed in a way that they can
transmit the sensed data in a secure and encrypted way.
This will help in gaining the trust of the individuals,
government agencies and industries in IoT applica-
tions.
6. Since the IoT devices and applications are growing
rapidly, an approach needs to be designed to handle
the cost and capacity constraints that are expected
to be encountered shortly. A paradigm shift from a
centralized approach to some decentralized approach
might be needed, where devices can automatically and
securely communicate with each other. This can help
in reducing the cost of managing the applications and
can reduce the issues of capacity constraints [43].
7. Since most of the IoT applications use cloud services
for data storage and retrieval, the risks caused by the
cloud should also be considered. Cloud is a public
platform used by multiple users and there may be
malicious users on the cloud who can be the cause of
threat for IoT related data. The data should be stored
as ciphertext in the cloud and the cloud should not
be allowed to decrypt any ciphertext. This can further
enhance data security and can save us from the generic
risks of using cloud services [44].
8. Apart from the challenges from outside entities, there
are various scenarios where the sensors in an IoT appli-
cation start collecting or sending erroneous data. These
errors might be easy to handle in case of a centralized
architecture but can become a bottleneck in case of an
autonomous decentralized architecture. Faulty reading
or transmitting of data can lead to undesirable results.
Thus, mechanism needs to be identified to validate the
data flow, especially in case of a distributed architec-
ture [45].
9. Since the ultimate goal of all IoT applications is to cre-
ate an autonomous system that needs minimum human
interventions, the use of some artificial intelligence
(AI) based techniques or algorithms to secure IoT
devices might be useful. This can help in reducing the
analysis and communication load on IoT environment
[46].
There are various techniques and approaches in the ex-
isting literature for securing IoT environments and applica-
tions. These solutions may be divided into four categories:
(1) blockchain based solutions; (2) fog computing based
solutions; (3) machine learning based solutions and (4) edge
computing based solutions. Figure 4 shows various works
in different domains that have used the above-mentioned
solutions for securing the IoT environments [47]–[97]. In the
following sections, these solutions are described in detail.
V. IOT SECURITY USING BLOCKCHAIN
Blockchain and IoT are important technologies that will
have a high impact on the IT and communication industry.
These two technologies focus on improving the overall trans-
parency, visibility, level of comfort and level of trust for the
users. The IoT devices provide real-time data from sensors
and blockchain provides the key for data security using a
distributed, decentralized and shared ledger [108].
The basic idea behind the blockchain is simple: it is a dis-
tributed ledger (also called replicated log files). The entries
in the blockchain are chronological and time-stamped. Each
entry in the ledger is tightly coupled with the previous entry
using cryptographic hash keys. A Merkle tree is used to store
the individual transactions and the root hash of the tree is
stored in the blockchain. In the figure, T 1, T 2, T 3, · · · , T n
represent the individual transactions. The transactions are
cryptographically hashed and stored on the leaf nodes of the
tree as Ha, Hb, Hcand so on. The hash of the child nodes
are concatenated and a new root hash is generated. The final
root hash (e.g., H1andH2) is stored on the blockchain. Just
the root hash can be verified in order to make sure that all
the transactions associated with that root hash are secure and
have not been tampered with. Even if a single transaction
is changed, all the hash values on that particular side of the
tree will change. The ledger maintainer or the miner verifies
the logs or transactions and generates a key that enables the
latest transaction to become the part of complete ledger. This
process makes the latest entries available to all the nodes in
the network. Due to the presence of cryptographic hash keys
in each block, it is too time-consuming and difficult for the
adversaries to tamper with the blocks [109].
The miners do not have any personal interest in the trans-
actions, and they are mining just to earn their incentives. The
miners do not know the identity of the owners of the transac-
tions. Over and above, there are multiple miners working on
the same set of transactions, and there is a strong competition
between them to add the transactions to the blockchain. All
these unique features empower the blockchain to be a strong,
10 VOLUME x, 2019
This article has been accepted for publication in a future issue of this journal, but has not been fully edited. Content may change p
10.1109/ACCESS.2019.2924045, IEEE Access
Vikas Hassija et al.: A Survey on IoT Security: Application Areas, Security Threats, and Solution Architectures
applications.
2. Encryption techniques are being used in IoT system at
different layers and protocols. However, there are var-
ious levels of encrypt, decrypt, and re-encrypt cycles
in the complete system. These cycles make the system
vulnerable to attacks. End to end encryption would be
a promising solution to prevent different attacks.
3. Authenticate-always protocols need to be imple-
mented. Whenever a device wants to interact with
another device, an authentication process should be
implemented. Digital certificates can be a promising
solution to provide seamless authentication with bound
identities that are tied to cryptographic protocols.
4. Any IoT security framework being implemented
should be tested and confirmed for scalability. The
security protocols should not be working only for a
limited set of users. The real threats start coming only
when the application becomes public and starts being
used widely in the public domain. Therefore, proper
strategy and planning are required.
5. A mechanism based on encryption techniques like
RSA, SHA256, or hash chains is required to secure the
user and environment data from being captured. IoT
devices need to be designed in a way that they can
transmit the sensed data in a secure and encrypted way.
This will help in gaining the trust of the individuals,
government agencies and industries in IoT applica-
tions.
6. Since the IoT devices and applications are growing
rapidly, an approach needs to be designed to handle
the cost and capacity constraints that are expected
to be encountered shortly. A paradigm shift from a
centralized approach to some decentralized approach
might be needed, where devices can automatically and
securely communicate with each other. This can help
in reducing the cost of managing the applications and
can reduce the issues of capacity constraints [43].
7. Since most of the IoT applications use cloud services
for data storage and retrieval, the risks caused by the
cloud should also be considered. Cloud is a public
platform used by multiple users and there may be
malicious users on the cloud who can be the cause of
threat for IoT related data. The data should be stored
as ciphertext in the cloud and the cloud should not
be allowed to decrypt any ciphertext. This can further
enhance data security and can save us from the generic
risks of using cloud services [44].
8. Apart from the challenges from outside entities, there
are various scenarios where the sensors in an IoT appli-
cation start collecting or sending erroneous data. These
errors might be easy to handle in case of a centralized
architecture but can become a bottleneck in case of an
autonomous decentralized architecture. Faulty reading
or transmitting of data can lead to undesirable results.
Thus, mechanism needs to be identified to validate the
data flow, especially in case of a distributed architec-
ture [45].
9. Since the ultimate goal of all IoT applications is to cre-
ate an autonomous system that needs minimum human
interventions, the use of some artificial intelligence
(AI) based techniques or algorithms to secure IoT
devices might be useful. This can help in reducing the
analysis and communication load on IoT environment
[46].
There are various techniques and approaches in the ex-
isting literature for securing IoT environments and applica-
tions. These solutions may be divided into four categories:
(1) blockchain based solutions; (2) fog computing based
solutions; (3) machine learning based solutions and (4) edge
computing based solutions. Figure 4 shows various works
in different domains that have used the above-mentioned
solutions for securing the IoT environments [47]–[97]. In the
following sections, these solutions are described in detail.
V. IOT SECURITY USING BLOCKCHAIN
Blockchain and IoT are important technologies that will
have a high impact on the IT and communication industry.
These two technologies focus on improving the overall trans-
parency, visibility, level of comfort and level of trust for the
users. The IoT devices provide real-time data from sensors
and blockchain provides the key for data security using a
distributed, decentralized and shared ledger [108].
The basic idea behind the blockchain is simple: it is a dis-
tributed ledger (also called replicated log files). The entries
in the blockchain are chronological and time-stamped. Each
entry in the ledger is tightly coupled with the previous entry
using cryptographic hash keys. A Merkle tree is used to store
the individual transactions and the root hash of the tree is
stored in the blockchain. In the figure, T 1, T 2, T 3, · · · , T n
represent the individual transactions. The transactions are
cryptographically hashed and stored on the leaf nodes of the
tree as Ha, Hb, Hcand so on. The hash of the child nodes
are concatenated and a new root hash is generated. The final
root hash (e.g., H1andH2) is stored on the blockchain. Just
the root hash can be verified in order to make sure that all
the transactions associated with that root hash are secure and
have not been tampered with. Even if a single transaction
is changed, all the hash values on that particular side of the
tree will change. The ledger maintainer or the miner verifies
the logs or transactions and generates a key that enables the
latest transaction to become the part of complete ledger. This
process makes the latest entries available to all the nodes in
the network. Due to the presence of cryptographic hash keys
in each block, it is too time-consuming and difficult for the
adversaries to tamper with the blocks [109].
The miners do not have any personal interest in the trans-
actions, and they are mining just to earn their incentives. The
miners do not know the identity of the owners of the transac-
tions. Over and above, there are multiple miners working on
the same set of transactions, and there is a strong competition
between them to add the transactions to the blockchain. All
these unique features empower the blockchain to be a strong,
10 VOLUME x, 2019
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
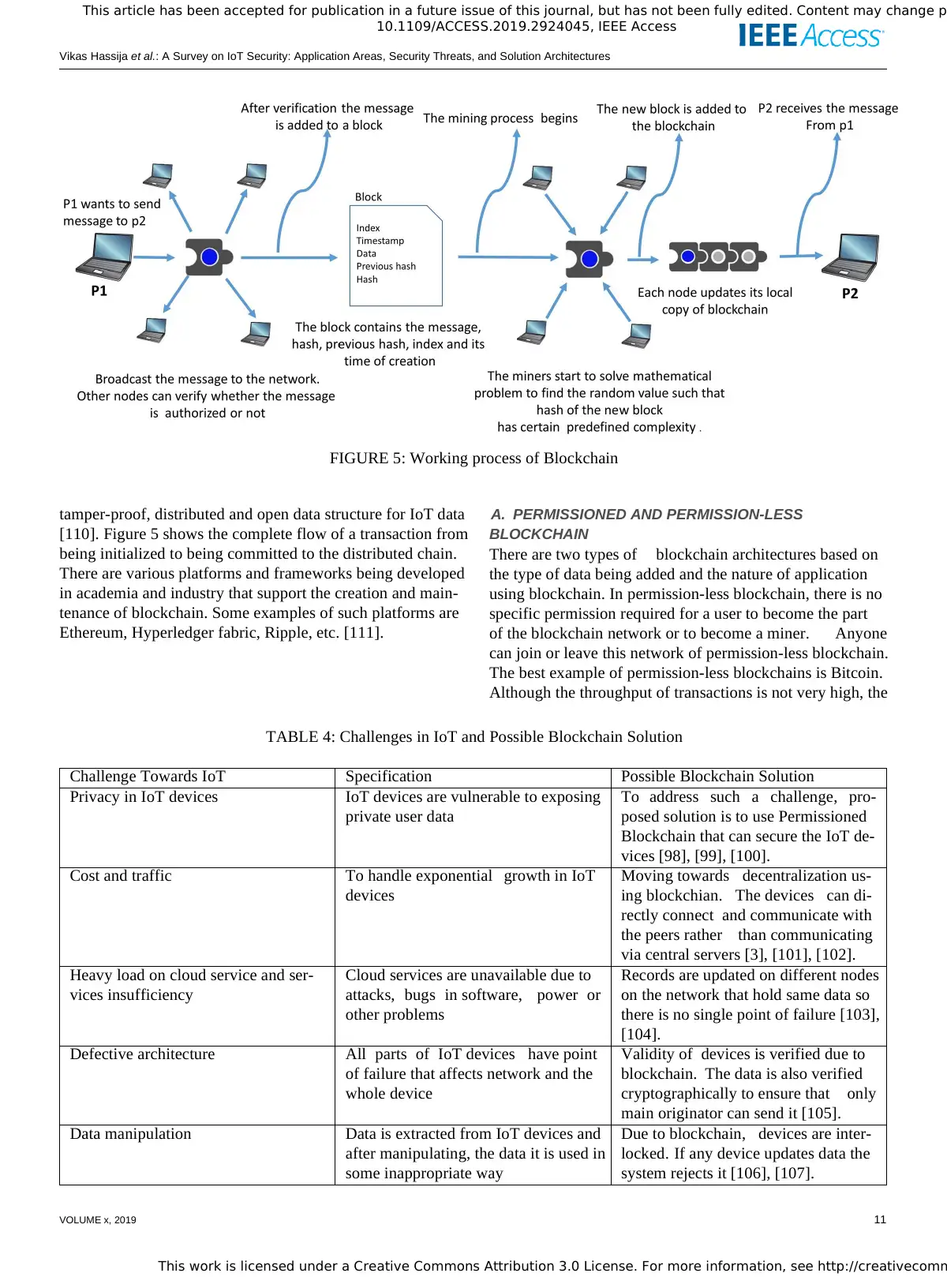
This work is licensed under a Creative Commons Attribution 3.0 License. For more information, see http://creativecomm
This article has been accepted for publication in a future issue of this journal, but has not been fully edited. Content may change p
10.1109/ACCESS.2019.2924045, IEEE Access
Vikas Hassija et al.: A Survey on IoT Security: Application Areas, Security Threats, and Solution Architectures
FIGURE 5: Working process of Blockchain
tamper-proof, distributed and open data structure for IoT data
[110]. Figure 5 shows the complete flow of a transaction from
being initialized to being committed to the distributed chain.
There are various platforms and frameworks being developed
in academia and industry that support the creation and main-
tenance of blockchain. Some examples of such platforms are
Ethereum, Hyperledger fabric, Ripple, etc. [111].
A. PERMISSIONED AND PERMISSION-LESS
BLOCKCHAIN
There are two types of blockchain architectures based on
the type of data being added and the nature of application
using blockchain. In permission-less blockchain, there is no
specific permission required for a user to become the part
of the blockchain network or to become a miner. Anyone
can join or leave this network of permission-less blockchain.
The best example of permission-less blockchains is Bitcoin.
Although the throughput of transactions is not very high, the
TABLE 4: Challenges in IoT and Possible Blockchain Solution
Challenge Towards IoT Specification Possible Blockchain Solution
Privacy in IoT devices IoT devices are vulnerable to exposing
private user data
To address such a challenge, pro-
posed solution is to use Permissioned
Blockchain that can secure the IoT de-
vices [98], [99], [100].
Cost and traffic To handle exponential growth in IoT
devices
Moving towards decentralization us-
ing blockchian. The devices can di-
rectly connect and communicate with
the peers rather than communicating
via central servers [3], [101], [102].
Heavy load on cloud service and ser-
vices insufficiency
Cloud services are unavailable due to
attacks, bugs in software, power or
other problems
Records are updated on different nodes
on the network that hold same data so
there is no single point of failure [103],
[104].
Defective architecture All parts of IoT devices have point
of failure that affects network and the
whole device
Validity of devices is verified due to
blockchain. The data is also verified
cryptographically to ensure that only
main originator can send it [105].
Data manipulation Data is extracted from IoT devices and
after manipulating, the data it is used in
some inappropriate way
Due to blockchain, devices are inter-
locked. If any device updates data the
system rejects it [106], [107].
VOLUME x, 2019 11
This article has been accepted for publication in a future issue of this journal, but has not been fully edited. Content may change p
10.1109/ACCESS.2019.2924045, IEEE Access
Vikas Hassija et al.: A Survey on IoT Security: Application Areas, Security Threats, and Solution Architectures
FIGURE 5: Working process of Blockchain
tamper-proof, distributed and open data structure for IoT data
[110]. Figure 5 shows the complete flow of a transaction from
being initialized to being committed to the distributed chain.
There are various platforms and frameworks being developed
in academia and industry that support the creation and main-
tenance of blockchain. Some examples of such platforms are
Ethereum, Hyperledger fabric, Ripple, etc. [111].
A. PERMISSIONED AND PERMISSION-LESS
BLOCKCHAIN
There are two types of blockchain architectures based on
the type of data being added and the nature of application
using blockchain. In permission-less blockchain, there is no
specific permission required for a user to become the part
of the blockchain network or to become a miner. Anyone
can join or leave this network of permission-less blockchain.
The best example of permission-less blockchains is Bitcoin.
Although the throughput of transactions is not very high, the
TABLE 4: Challenges in IoT and Possible Blockchain Solution
Challenge Towards IoT Specification Possible Blockchain Solution
Privacy in IoT devices IoT devices are vulnerable to exposing
private user data
To address such a challenge, pro-
posed solution is to use Permissioned
Blockchain that can secure the IoT de-
vices [98], [99], [100].
Cost and traffic To handle exponential growth in IoT
devices
Moving towards decentralization us-
ing blockchian. The devices can di-
rectly connect and communicate with
the peers rather than communicating
via central servers [3], [101], [102].
Heavy load on cloud service and ser-
vices insufficiency
Cloud services are unavailable due to
attacks, bugs in software, power or
other problems
Records are updated on different nodes
on the network that hold same data so
there is no single point of failure [103],
[104].
Defective architecture All parts of IoT devices have point
of failure that affects network and the
whole device
Validity of devices is verified due to
blockchain. The data is also verified
cryptographically to ensure that only
main originator can send it [105].
Data manipulation Data is extracted from IoT devices and
after manipulating, the data it is used in
some inappropriate way
Due to blockchain, devices are inter-
locked. If any device updates data the
system rejects it [106], [107].
VOLUME x, 2019 11
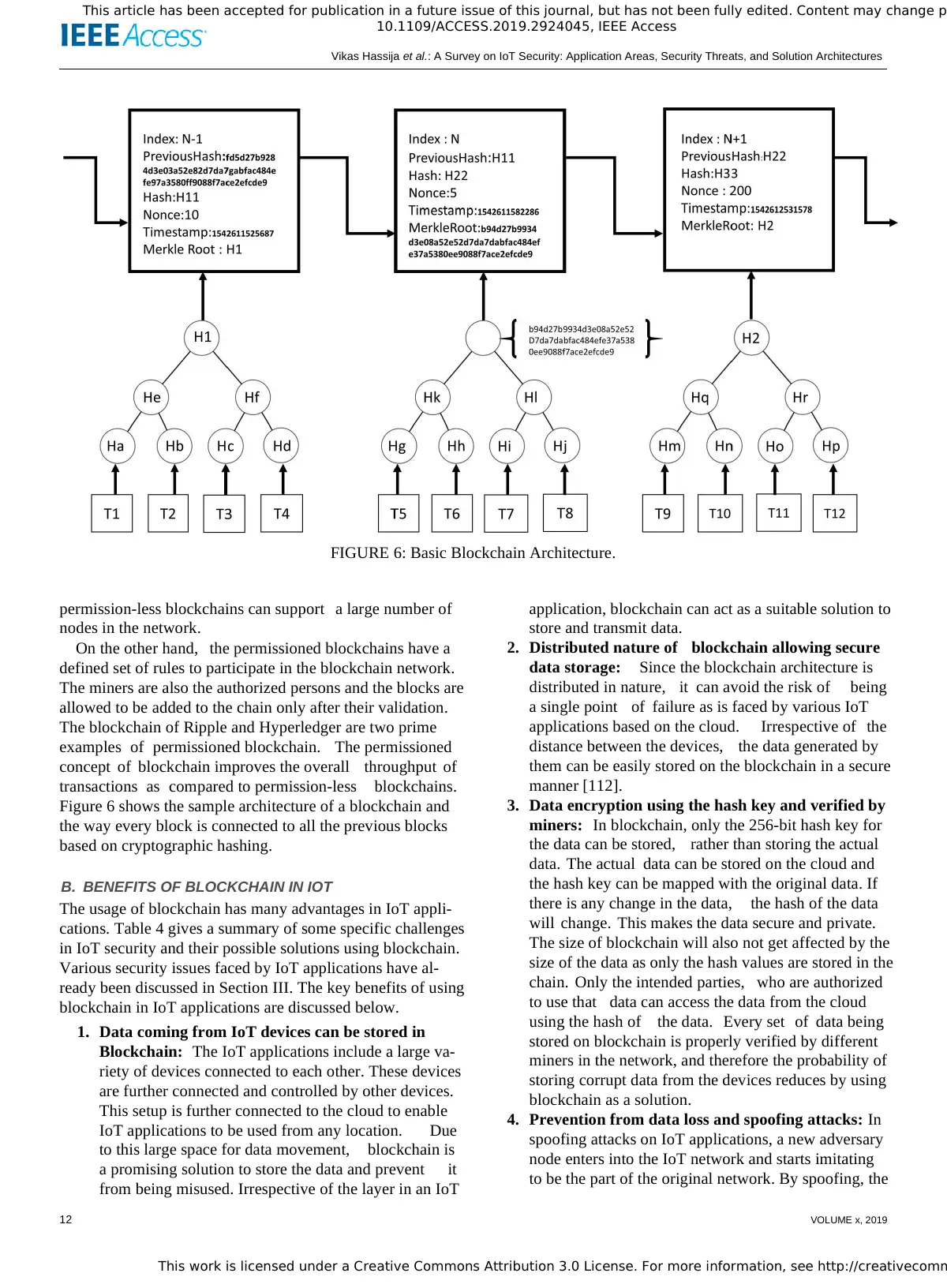
This work is licensed under a Creative Commons Attribution 3.0 License. For more information, see http://creativecomm
This article has been accepted for publication in a future issue of this journal, but has not been fully edited. Content may change p
10.1109/ACCESS.2019.2924045, IEEE Access
Vikas Hassija et al.: A Survey on IoT Security: Application Areas, Security Threats, and Solution Architectures
FIGURE 6: Basic Blockchain Architecture.
permission-less blockchains can support a large number of
nodes in the network.
On the other hand, the permissioned blockchains have a
defined set of rules to participate in the blockchain network.
The miners are also the authorized persons and the blocks are
allowed to be added to the chain only after their validation.
The blockchain of Ripple and Hyperledger are two prime
examples of permissioned blockchain. The permissioned
concept of blockchain improves the overall throughput of
transactions as compared to permission-less blockchains.
Figure 6 shows the sample architecture of a blockchain and
the way every block is connected to all the previous blocks
based on cryptographic hashing.
B. BENEFITS OF BLOCKCHAIN IN IOT
The usage of blockchain has many advantages in IoT appli-
cations. Table 4 gives a summary of some specific challenges
in IoT security and their possible solutions using blockchain.
Various security issues faced by IoT applications have al-
ready been discussed in Section III. The key benefits of using
blockchain in IoT applications are discussed below.
1. Data coming from IoT devices can be stored in
Blockchain: The IoT applications include a large va-
riety of devices connected to each other. These devices
are further connected and controlled by other devices.
This setup is further connected to the cloud to enable
IoT applications to be used from any location. Due
to this large space for data movement, blockchain is
a promising solution to store the data and prevent it
from being misused. Irrespective of the layer in an IoT
application, blockchain can act as a suitable solution to
store and transmit data.
2. Distributed nature of blockchain allowing secure
data storage: Since the blockchain architecture is
distributed in nature, it can avoid the risk of being
a single point of failure as is faced by various IoT
applications based on the cloud. Irrespective of the
distance between the devices, the data generated by
them can be easily stored on the blockchain in a secure
manner [112].
3. Data encryption using the hash key and verified by
miners: In blockchain, only the 256-bit hash key for
the data can be stored, rather than storing the actual
data. The actual data can be stored on the cloud and
the hash key can be mapped with the original data. If
there is any change in the data, the hash of the data
will change. This makes the data secure and private.
The size of blockchain will also not get affected by the
size of the data as only the hash values are stored in the
chain. Only the intended parties, who are authorized
to use that data can access the data from the cloud
using the hash of the data. Every set of data being
stored on blockchain is properly verified by different
miners in the network, and therefore the probability of
storing corrupt data from the devices reduces by using
blockchain as a solution.
4. Prevention from data loss and spoofing attacks: In
spoofing attacks on IoT applications, a new adversary
node enters into the IoT network and starts imitating
to be the part of the original network. By spoofing, the
12 VOLUME x, 2019
This article has been accepted for publication in a future issue of this journal, but has not been fully edited. Content may change p
10.1109/ACCESS.2019.2924045, IEEE Access
Vikas Hassija et al.: A Survey on IoT Security: Application Areas, Security Threats, and Solution Architectures
FIGURE 6: Basic Blockchain Architecture.
permission-less blockchains can support a large number of
nodes in the network.
On the other hand, the permissioned blockchains have a
defined set of rules to participate in the blockchain network.
The miners are also the authorized persons and the blocks are
allowed to be added to the chain only after their validation.
The blockchain of Ripple and Hyperledger are two prime
examples of permissioned blockchain. The permissioned
concept of blockchain improves the overall throughput of
transactions as compared to permission-less blockchains.
Figure 6 shows the sample architecture of a blockchain and
the way every block is connected to all the previous blocks
based on cryptographic hashing.
B. BENEFITS OF BLOCKCHAIN IN IOT
The usage of blockchain has many advantages in IoT appli-
cations. Table 4 gives a summary of some specific challenges
in IoT security and their possible solutions using blockchain.
Various security issues faced by IoT applications have al-
ready been discussed in Section III. The key benefits of using
blockchain in IoT applications are discussed below.
1. Data coming from IoT devices can be stored in
Blockchain: The IoT applications include a large va-
riety of devices connected to each other. These devices
are further connected and controlled by other devices.
This setup is further connected to the cloud to enable
IoT applications to be used from any location. Due
to this large space for data movement, blockchain is
a promising solution to store the data and prevent it
from being misused. Irrespective of the layer in an IoT
application, blockchain can act as a suitable solution to
store and transmit data.
2. Distributed nature of blockchain allowing secure
data storage: Since the blockchain architecture is
distributed in nature, it can avoid the risk of being
a single point of failure as is faced by various IoT
applications based on the cloud. Irrespective of the
distance between the devices, the data generated by
them can be easily stored on the blockchain in a secure
manner [112].
3. Data encryption using the hash key and verified by
miners: In blockchain, only the 256-bit hash key for
the data can be stored, rather than storing the actual
data. The actual data can be stored on the cloud and
the hash key can be mapped with the original data. If
there is any change in the data, the hash of the data
will change. This makes the data secure and private.
The size of blockchain will also not get affected by the
size of the data as only the hash values are stored in the
chain. Only the intended parties, who are authorized
to use that data can access the data from the cloud
using the hash of the data. Every set of data being
stored on blockchain is properly verified by different
miners in the network, and therefore the probability of
storing corrupt data from the devices reduces by using
blockchain as a solution.
4. Prevention from data loss and spoofing attacks: In
spoofing attacks on IoT applications, a new adversary
node enters into the IoT network and starts imitating
to be the part of the original network. By spoofing, the
12 VOLUME x, 2019
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 24
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.


