Internet of Things: Communication, Security, and Design Principles
VerifiedAdded on 2020/03/02
|10
|2368
|189
Homework Assignment
AI Summary
This assignment delves into various aspects of the Internet of Things (IoT). It begins by examining the concept of a "no UI" interface and provides examples. The assignment then compares different types of network cables (twisted pair, coaxial, and fiber optic) across bandwidth, distance, cost, and security, including specific examples. Furthermore, it contrasts three information gathering technologies: sensors, RFID, and video tracking, analyzing their advantages, disadvantages, and applications. The assignment explores security and privacy concerns within the IoT context. It also presents a problem involving command/response versus publish/subscribe communication models, calculating potential time savings. Finally, the assignment concludes with a discussion of Nielsen's Law, its relationship to Moore's Law, and implications for the IoT. The document also contains a detailed reference section.

Internet of Things
Submitted By
Course
Professor
Date
Submitted By 1
Submitted By
Course
Professor
Date
Submitted By 1
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

What does the statement "the best interface for a system is no User Interface"? When
might this apply and provide two examples.
User experience (UX) or human-to-machine cooperation is exceptionally critical for the
achievement of IoT. The main focus of IoT UX rule is meeting the fundamental requirements for
the utilization of an item or an administration without disturbance or trouble. Overengineering or
including excessively insight into items can blowback and be counterproductive. UIs that are
frustrating to utilize and ease back to separate significant data can prompt client abandonment.
Eg: A toaster exists to make toast. In any case, if we overengineer with a lot of data, switches
and alternatives, we make building items that are annoying to the point that our clients won't
have any desire to utilize them. Usability is considered as the best prerequisite for any electronic
framework. Eg: Apple's iPhone versus rival devices with a similar usefulness. Clients will pay
more for simple to utilize devices, and sensors are no exemptions. Consequently, the best UI is
"no UI" when sensors are required to work without anyone else's input once they are associated.
(Rayes, A. & Salam, S., 2017).
Compare the bandwidth, distance, interference rating, cost and security of a) twisted pair
cable, b) coaxial cable and 3) fibre optic cable. Use current data, give specific details for at
least 3 types of cable within each category, these should have different specifications, rather
than simply different brands of the same type.
Twisting Pair Cable - Twisted pair cable can be used for communications in telephone as well
as in Ethernet networks. A couple of wires frames a circuit that can transmit information. The
sets are twisted to give the protection against crosstalk, the commotion produced by adjoining
sets. When there is flow of current in the wire, a small magnetic field is created in the wire.
When two wires are put very close to each other, their attractive fields are the correct inverse of
Submitted By 2
might this apply and provide two examples.
User experience (UX) or human-to-machine cooperation is exceptionally critical for the
achievement of IoT. The main focus of IoT UX rule is meeting the fundamental requirements for
the utilization of an item or an administration without disturbance or trouble. Overengineering or
including excessively insight into items can blowback and be counterproductive. UIs that are
frustrating to utilize and ease back to separate significant data can prompt client abandonment.
Eg: A toaster exists to make toast. In any case, if we overengineer with a lot of data, switches
and alternatives, we make building items that are annoying to the point that our clients won't
have any desire to utilize them. Usability is considered as the best prerequisite for any electronic
framework. Eg: Apple's iPhone versus rival devices with a similar usefulness. Clients will pay
more for simple to utilize devices, and sensors are no exemptions. Consequently, the best UI is
"no UI" when sensors are required to work without anyone else's input once they are associated.
(Rayes, A. & Salam, S., 2017).
Compare the bandwidth, distance, interference rating, cost and security of a) twisted pair
cable, b) coaxial cable and 3) fibre optic cable. Use current data, give specific details for at
least 3 types of cable within each category, these should have different specifications, rather
than simply different brands of the same type.
Twisting Pair Cable - Twisted pair cable can be used for communications in telephone as well
as in Ethernet networks. A couple of wires frames a circuit that can transmit information. The
sets are twisted to give the protection against crosstalk, the commotion produced by adjoining
sets. When there is flow of current in the wire, a small magnetic field is created in the wire.
When two wires are put very close to each other, their attractive fields are the correct inverse of
Submitted By 2

each other. Hence, these magnetic field cancel each other. Utilizing cancelation together with
twisting wires, link designers can successfully give self-protecting to wire pairs inside the
network system. The speed and throughput of twisted pair cables ranges from 10 – 1000 Mbps.
The distance between node and hub can be approximately 100 meters to 328 feet. Exposed
cabling can be dangerous, so it is covered with protected material. The protected cable would be
resistant to any electrical attractive obstruction created from the power link situated in a similar
pathway. Being nominal cost, it is being used to great extent.
Eg: Common types of Unshielded Twist Pair (UTP) are:
Category1 – It is used for telephone communication but not good for transmitting data.
Category2 – It is used to transmit data with a speed of 4Mbps.
Category3 – It is used in 10BASE –T networks. Its bandwidth is 10Mbps. (Cisco Systems, Inc.,
2003).
Coaxial Cable - Coaxial cable seems to be like the link used to deliver the TV signals. A strong
center copper wire keeps running down the center of the link. Around that strong center copper
wire is a layer of protection, and covering that protection is metal thwart, which shields against
electromagnetic interference. A last layer of protection covers the plaited wire. The transmission
capacity for coaxial cable is 10 Mbps. The most extreme length of cable is 2 feet or less. Its price
range from $30 to $50 for 300 meters.
Hard Line Coaxial cable – It is used for high signal strength applications having radio
transmitters. It is mainly preferred for heavy signal transmission due to its thickness.
Submitted By 3
twisting wires, link designers can successfully give self-protecting to wire pairs inside the
network system. The speed and throughput of twisted pair cables ranges from 10 – 1000 Mbps.
The distance between node and hub can be approximately 100 meters to 328 feet. Exposed
cabling can be dangerous, so it is covered with protected material. The protected cable would be
resistant to any electrical attractive obstruction created from the power link situated in a similar
pathway. Being nominal cost, it is being used to great extent.
Eg: Common types of Unshielded Twist Pair (UTP) are:
Category1 – It is used for telephone communication but not good for transmitting data.
Category2 – It is used to transmit data with a speed of 4Mbps.
Category3 – It is used in 10BASE –T networks. Its bandwidth is 10Mbps. (Cisco Systems, Inc.,
2003).
Coaxial Cable - Coaxial cable seems to be like the link used to deliver the TV signals. A strong
center copper wire keeps running down the center of the link. Around that strong center copper
wire is a layer of protection, and covering that protection is metal thwart, which shields against
electromagnetic interference. A last layer of protection covers the plaited wire. The transmission
capacity for coaxial cable is 10 Mbps. The most extreme length of cable is 2 feet or less. Its price
range from $30 to $50 for 300 meters.
Hard Line Coaxial cable – It is used for high signal strength applications having radio
transmitters. It is mainly preferred for heavy signal transmission due to its thickness.
Submitted By 3
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

RG-6 Coaxial Cables – It is used for high definition signals like cable TV or any other signal.
(Thomas, J., 2017).
Thick coaxial cables - Thick coaxial link is also known as thicknet. 10Base5 alludes to the
details for thick coaxial link that delivers Ethernet signals. The 5 alludes to the greatest fragment
length being 500 meters. Thick coaxial link has an additional shielded plastic cover that helps
keep dampness far from the inside conductor. This settles on thick coaxial an incredible decision
when running longer lengths in a linear bus network. One weakness of thick coaxial is that it
doesn't twist effortlessly and is hard to install. (Dr. Winkelman, R., 2013).
Fiber Optic Cable - Fiber optic cable deliver communication signals utilizing pulses of light
produced by small lasers or light-emanating diodes (LEDs). Fiber links evaluated at 10 Gbps, 40
Gbps and even 100 Gbps are standard. Fiber is less vulnerable to impedance. A customary
system link requires exceptional protecting to protect it from electromagnetic obstruction. While
this protecting causes, it is not adequate to counteract impedance when many links are hung
together in closeness to each other. It cost $6 per feet. (Mitchell, B., 2017).
Single Fiber Optic Cable - Single Mode link is a single stand (most applications utilize 2 fibers)
of glass fiber with a distance across of 8.3 to 10 microns that has one method of transmission.
Single Modem fiber is utilized as a part of numerous applications where information is sent at
multi-frequency (WDM Wave-Division-Multiplexing) so just a single link is required. Single-
mode fiber gives a higher distance than multimode, yet it additionally costs more.
Multi-Mode Cable - Multi-Mode link has small diameter with a typical diameter in the 50-to-
100 micron for the light carry component (in the US the most widely recognized size is 62.5um).
Multimode fiber gives you high transfer speed of 10 to 100MBS - Gigabit to 275m to 2km over
Submitted By 4
(Thomas, J., 2017).
Thick coaxial cables - Thick coaxial link is also known as thicknet. 10Base5 alludes to the
details for thick coaxial link that delivers Ethernet signals. The 5 alludes to the greatest fragment
length being 500 meters. Thick coaxial link has an additional shielded plastic cover that helps
keep dampness far from the inside conductor. This settles on thick coaxial an incredible decision
when running longer lengths in a linear bus network. One weakness of thick coaxial is that it
doesn't twist effortlessly and is hard to install. (Dr. Winkelman, R., 2013).
Fiber Optic Cable - Fiber optic cable deliver communication signals utilizing pulses of light
produced by small lasers or light-emanating diodes (LEDs). Fiber links evaluated at 10 Gbps, 40
Gbps and even 100 Gbps are standard. Fiber is less vulnerable to impedance. A customary
system link requires exceptional protecting to protect it from electromagnetic obstruction. While
this protecting causes, it is not adequate to counteract impedance when many links are hung
together in closeness to each other. It cost $6 per feet. (Mitchell, B., 2017).
Single Fiber Optic Cable - Single Mode link is a single stand (most applications utilize 2 fibers)
of glass fiber with a distance across of 8.3 to 10 microns that has one method of transmission.
Single Modem fiber is utilized as a part of numerous applications where information is sent at
multi-frequency (WDM Wave-Division-Multiplexing) so just a single link is required. Single-
mode fiber gives a higher distance than multimode, yet it additionally costs more.
Multi-Mode Cable - Multi-Mode link has small diameter with a typical diameter in the 50-to-
100 micron for the light carry component (in the US the most widely recognized size is 62.5um).
Multimode fiber gives you high transfer speed of 10 to 100MBS - Gigabit to 275m to 2km over
Submitted By 4
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
medium distance. Light waves are scattered into various ways, or modes, as they go through the
link normally 850 or 1300nm. Multimode fiber diameter across are 50, 62.5, and 100
micrometers. (MacChesney, J., n.d).
Step Index - They are generally cheap as well as they have the greatest scope of center diameter
across: fundamentally from 50 μm up to 2 mm. The material might be plastic, fluid or glass.
(Ovejabiennera, 2009).
The three common ways to obtain information from IoT devices are sensors, RFID and
Video tracking. Compare the three technologies by addressing the advantages,
disadvantages, key requirements for the things. Provide two applications of each.
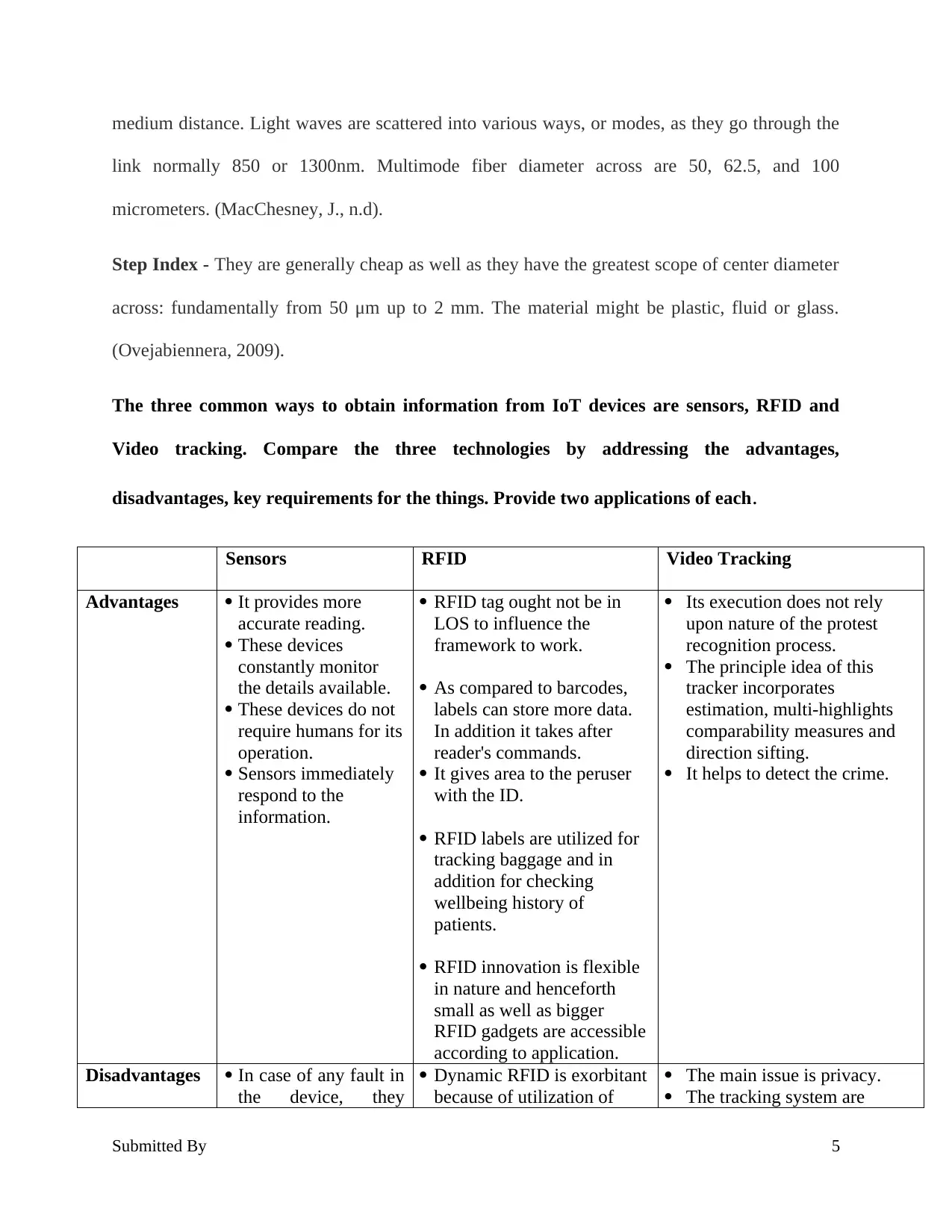
Sensors RFID Video Tracking
Advantages It provides more
accurate reading.
These devices
constantly monitor
the details available.
These devices do not
require humans for its
operation.
Sensors immediately
respond to the
information.
RFID tag ought not be in
LOS to influence the
framework to work.
As compared to barcodes,
labels can store more data.
In addition it takes after
reader's commands.
It gives area to the peruser
with the ID.
RFID labels are utilized for
tracking baggage and in
addition for checking
wellbeing history of
patients.
RFID innovation is flexible
in nature and henceforth
small as well as bigger
RFID gadgets are accessible
according to application.
Its execution does not rely
upon nature of the protest
recognition process.
The principle idea of this
tracker incorporates
estimation, multi-highlights
comparability measures and
direction sifting.
It helps to detect the crime.
Disadvantages In case of any fault in
the device, they
Dynamic RFID is exorbitant
because of utilization of
The main issue is privacy.
The tracking system are
Submitted By 5
link normally 850 or 1300nm. Multimode fiber diameter across are 50, 62.5, and 100
micrometers. (MacChesney, J., n.d).
Step Index - They are generally cheap as well as they have the greatest scope of center diameter
across: fundamentally from 50 μm up to 2 mm. The material might be plastic, fluid or glass.
(Ovejabiennera, 2009).
The three common ways to obtain information from IoT devices are sensors, RFID and
Video tracking. Compare the three technologies by addressing the advantages,
disadvantages, key requirements for the things. Provide two applications of each.
Sensors RFID Video Tracking
Advantages It provides more
accurate reading.
These devices
constantly monitor
the details available.
These devices do not
require humans for its
operation.
Sensors immediately
respond to the
information.
RFID tag ought not be in
LOS to influence the
framework to work.
As compared to barcodes,
labels can store more data.
In addition it takes after
reader's commands.
It gives area to the peruser
with the ID.
RFID labels are utilized for
tracking baggage and in
addition for checking
wellbeing history of
patients.
RFID innovation is flexible
in nature and henceforth
small as well as bigger
RFID gadgets are accessible
according to application.
Its execution does not rely
upon nature of the protest
recognition process.
The principle idea of this
tracker incorporates
estimation, multi-highlights
comparability measures and
direction sifting.
It helps to detect the crime.
Disadvantages In case of any fault in
the device, they
Dynamic RFID is exorbitant
because of utilization of
The main issue is privacy.
The tracking system are
Submitted By 5
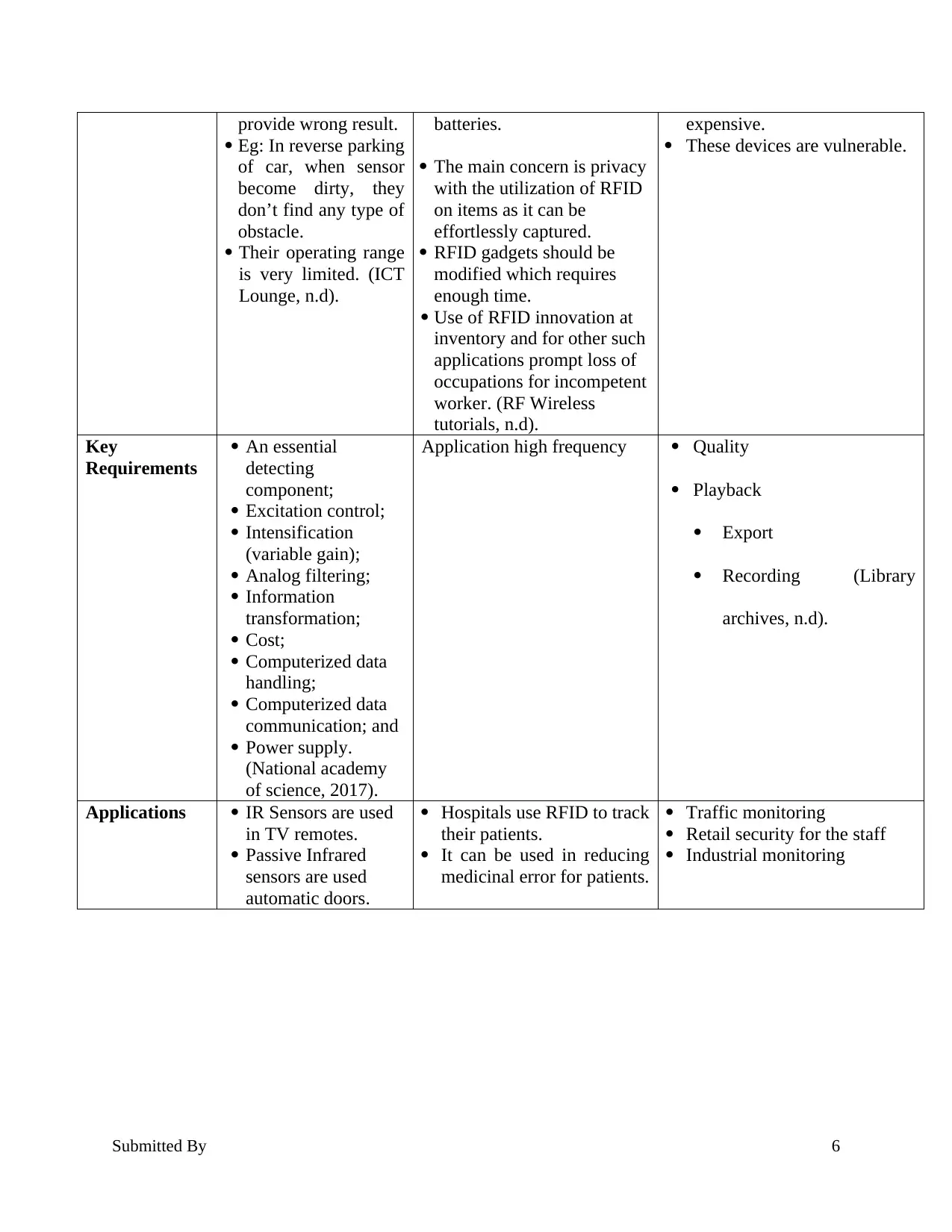
provide wrong result.
Eg: In reverse parking
of car, when sensor
become dirty, they
don’t find any type of
obstacle.
Their operating range
is very limited. (ICT
Lounge, n.d).
batteries.
The main concern is privacy
with the utilization of RFID
on items as it can be
effortlessly captured.
RFID gadgets should be
modified which requires
enough time.
Use of RFID innovation at
inventory and for other such
applications prompt loss of
occupations for incompetent
worker. (RF Wireless
tutorials, n.d).
expensive.
These devices are vulnerable.
Key
Requirements
An essential
detecting
component;
Excitation control;
Intensification
(variable gain);
Analog filtering;
Information
transformation;
Cost;
Computerized data
handling;
Computerized data
communication; and
Power supply.
(National academy
of science, 2017).
Application high frequency Quality
Playback
Export
Recording (Library
archives, n.d).
Applications IR Sensors are used
in TV remotes.
Passive Infrared
sensors are used
automatic doors.
Hospitals use RFID to track
their patients.
It can be used in reducing
medicinal error for patients.
Traffic monitoring
Retail security for the staff
Industrial monitoring
Submitted By 6
Eg: In reverse parking
of car, when sensor
become dirty, they
don’t find any type of
obstacle.
Their operating range
is very limited. (ICT
Lounge, n.d).
batteries.
The main concern is privacy
with the utilization of RFID
on items as it can be
effortlessly captured.
RFID gadgets should be
modified which requires
enough time.
Use of RFID innovation at
inventory and for other such
applications prompt loss of
occupations for incompetent
worker. (RF Wireless
tutorials, n.d).
expensive.
These devices are vulnerable.
Key
Requirements
An essential
detecting
component;
Excitation control;
Intensification
(variable gain);
Analog filtering;
Information
transformation;
Cost;
Computerized data
handling;
Computerized data
communication; and
Power supply.
(National academy
of science, 2017).
Application high frequency Quality
Playback
Export
Recording (Library
archives, n.d).
Applications IR Sensors are used
in TV remotes.
Passive Infrared
sensors are used
automatic doors.
Hospitals use RFID to track
their patients.
It can be used in reducing
medicinal error for patients.
Traffic monitoring
Retail security for the staff
Industrial monitoring
Submitted By 6
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Discuss the issues associated with security and privacy in the context of the Internet of
Things.
Security Risks – 1. It enables unauthorized access and abuse of individual data;
(2) It encourages assaults on different frameworks; and
(3) It creates threat to the individual safety.
Privacy Concerns - Some of the privacy risks include the immediate collection of sensitive
individual data, for example, exact geolocation, financial accounting data, or wellbeing data –
hazards as of now introduced by customary Internet and versatile business. Others emerge from
the accumulation of individual data, propensities, areas, and physical conditions over time, which
may permit an element that has not gathered sensitive data to derive it. (FTC staff report, 2015).
An IoT water level monitoring application requires updates from a sensor periodically,
using the command/response paradigm. The application triggers a request every 1 s. The
round-trip propagation delay between the application and the sensor is 12 ms. On average
the sensor consumes 3 ms to process each request. The application consumes 2 ms to send
or receive any message. If the application blocks on every request to the sensor, how much
of its time budget can be saved by redesigning the application to use the publish/subscribe
communication model in lieu of the command/response approach?
If the application blocks on every request to the sensor, the time budget which can be saved by
redesigning the application can be 17ms for each request.
Describe Nielson's Law. How does it relate to Moore's Law? What are the implications for
the Internet of Thing?
Submitted By 7
Things.
Security Risks – 1. It enables unauthorized access and abuse of individual data;
(2) It encourages assaults on different frameworks; and
(3) It creates threat to the individual safety.
Privacy Concerns - Some of the privacy risks include the immediate collection of sensitive
individual data, for example, exact geolocation, financial accounting data, or wellbeing data –
hazards as of now introduced by customary Internet and versatile business. Others emerge from
the accumulation of individual data, propensities, areas, and physical conditions over time, which
may permit an element that has not gathered sensitive data to derive it. (FTC staff report, 2015).
An IoT water level monitoring application requires updates from a sensor periodically,
using the command/response paradigm. The application triggers a request every 1 s. The
round-trip propagation delay between the application and the sensor is 12 ms. On average
the sensor consumes 3 ms to process each request. The application consumes 2 ms to send
or receive any message. If the application blocks on every request to the sensor, how much
of its time budget can be saved by redesigning the application to use the publish/subscribe
communication model in lieu of the command/response approach?
If the application blocks on every request to the sensor, the time budget which can be saved by
redesigning the application can be 17ms for each request.
Describe Nielson's Law. How does it relate to Moore's Law? What are the implications for
the Internet of Thing?
Submitted By 7
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
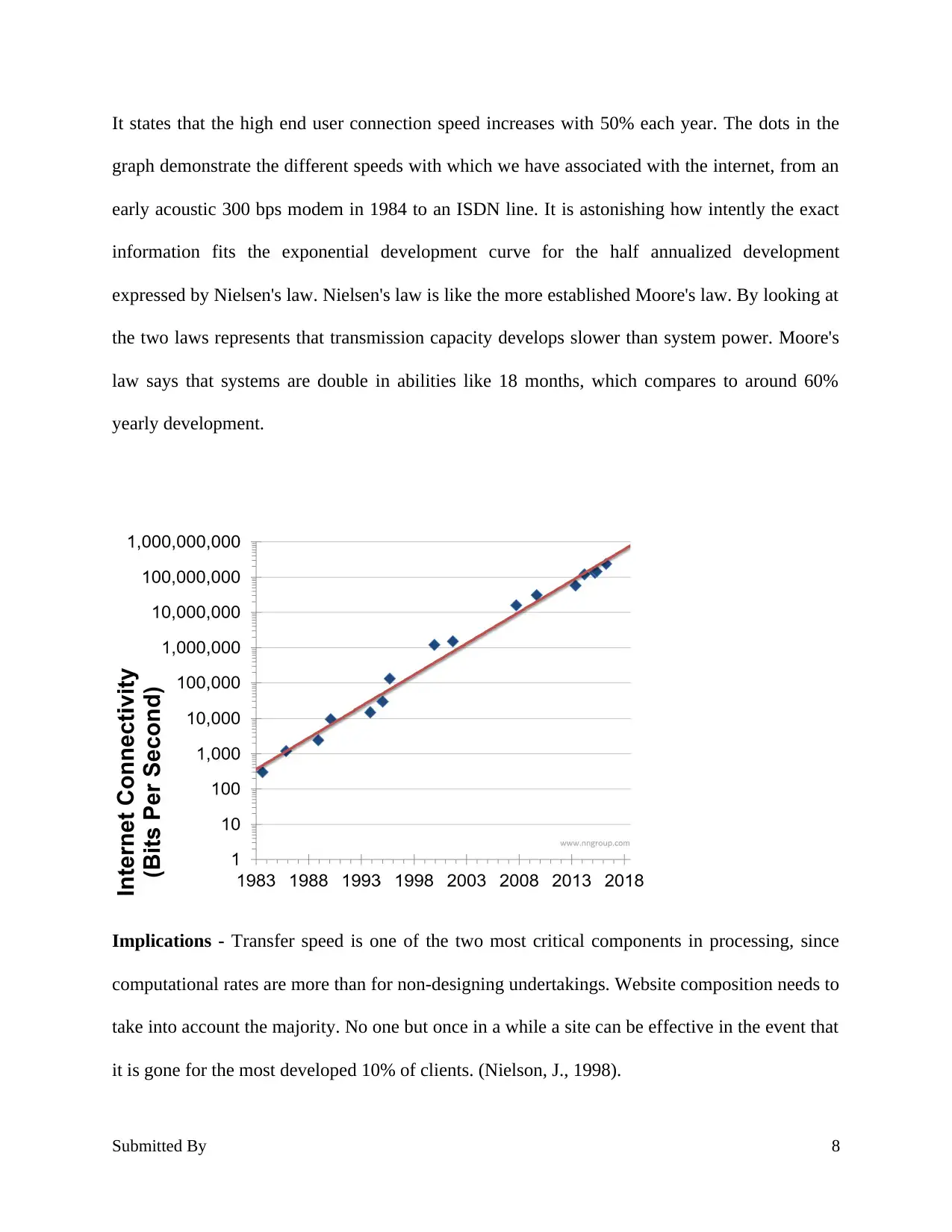
It states that the high end user connection speed increases with 50% each year. The dots in the
graph demonstrate the different speeds with which we have associated with the internet, from an
early acoustic 300 bps modem in 1984 to an ISDN line. It is astonishing how intently the exact
information fits the exponential development curve for the half annualized development
expressed by Nielsen's law. Nielsen's law is like the more established Moore's law. By looking at
the two laws represents that transmission capacity develops slower than system power. Moore's
law says that systems are double in abilities like 18 months, which compares to around 60%
yearly development.
Implications - Transfer speed is one of the two most critical components in processing, since
computational rates are more than for non-designing undertakings. Website composition needs to
take into account the majority. No one but once in a while a site can be effective in the event that
it is gone for the most developed 10% of clients. (Nielson, J., 1998).
Submitted By 8
graph demonstrate the different speeds with which we have associated with the internet, from an
early acoustic 300 bps modem in 1984 to an ISDN line. It is astonishing how intently the exact
information fits the exponential development curve for the half annualized development
expressed by Nielsen's law. Nielsen's law is like the more established Moore's law. By looking at
the two laws represents that transmission capacity develops slower than system power. Moore's
law says that systems are double in abilities like 18 months, which compares to around 60%
yearly development.
Implications - Transfer speed is one of the two most critical components in processing, since
computational rates are more than for non-designing undertakings. Website composition needs to
take into account the majority. No one but once in a while a site can be effective in the event that
it is gone for the most developed 10% of clients. (Nielson, J., 1998).
Submitted By 8

References
Advantages of RFID | Disadvantages of RFID. RF Wireless tutorials (n.d). Retrieved from -
http://www.rfwireless-world.com/Terminology/Advantages-and-Disadvantages-of-
RFID.html
CCNA: Network Media Types. Cisco Systems, Inc. (2003). Retrieved from -
http://www.ciscopress.com/articles/article.asp?p=31276
Dr. Winkelman, R. (2013). Chapter - 4 Cabling. Florida Center for Instructional Technology.
Retrieved from - https://fcit.usf.edu/network/chap4/chap4.htm
Internet of things - privacy & security in a connected world. FTC staff report (2015). Retrieved
from - https://www.ftc.gov/system/files/documents/reports/federal-trade-commission-
staff-report-november-2013-workshop-entitled-internet-things-privacy/150127iotrpt.pdf
Introduction to sensors. National academy of science (2017). Retrieved from -
https://www.nap.edu/read/4782/chapter/4#16
MacChesney, J. (n.d). The basics of fiber optic cable. Retrieved from -
http://www.arcelect.com/fibercable.htm
Mitchell, B. (2017). What Is a Fiber Optic Cable? Retrieved from -
https://www.lifewire.com/fiber-optic-cable-817874
Nielson, J. (1998). Nielsen's Law of Internet Bandwidth. Retrieved from -
https://www.nngroup.com/articles/law-of-bandwidth/
Operational requirements for CCTV systems. Library archives (n.d). Retrieved from -
http://www.dipolnet.com/operational_requirements_for_cctv_systems_bib702.htm
Submitted By 9
Advantages of RFID | Disadvantages of RFID. RF Wireless tutorials (n.d). Retrieved from -
http://www.rfwireless-world.com/Terminology/Advantages-and-Disadvantages-of-
RFID.html
CCNA: Network Media Types. Cisco Systems, Inc. (2003). Retrieved from -
http://www.ciscopress.com/articles/article.asp?p=31276
Dr. Winkelman, R. (2013). Chapter - 4 Cabling. Florida Center for Instructional Technology.
Retrieved from - https://fcit.usf.edu/network/chap4/chap4.htm
Internet of things - privacy & security in a connected world. FTC staff report (2015). Retrieved
from - https://www.ftc.gov/system/files/documents/reports/federal-trade-commission-
staff-report-november-2013-workshop-entitled-internet-things-privacy/150127iotrpt.pdf
Introduction to sensors. National academy of science (2017). Retrieved from -
https://www.nap.edu/read/4782/chapter/4#16
MacChesney, J. (n.d). The basics of fiber optic cable. Retrieved from -
http://www.arcelect.com/fibercable.htm
Mitchell, B. (2017). What Is a Fiber Optic Cable? Retrieved from -
https://www.lifewire.com/fiber-optic-cable-817874
Nielson, J. (1998). Nielsen's Law of Internet Bandwidth. Retrieved from -
https://www.nngroup.com/articles/law-of-bandwidth/
Operational requirements for CCTV systems. Library archives (n.d). Retrieved from -
http://www.dipolnet.com/operational_requirements_for_cctv_systems_bib702.htm
Submitted By 9
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Ovejabiennera (2009). Types of optical fibres. Retrieved from -
https://spectroscopy.wordpress.com/2009/04/19/types-of-optical-fibres/
Rayes, A. & Salam, S. (2017). Internet of Things From Hype to Reality: The Road to
Digitization. Supringer International Publishing AG - 2017.
Sensors. ICT Lounge (n.d). Retrieved from - https://www.ictlounge.com/html/sensors.htm
Thomas, J. (2017). Coaxial cables, Twisted Pair STP and UTP cables, Twisted Pair Cable
Categories (CAT). Retrieved from -
http://www.omnisecu.com/basic-networking/common-network-cable-types.php
Submitted By 10
https://spectroscopy.wordpress.com/2009/04/19/types-of-optical-fibres/
Rayes, A. & Salam, S. (2017). Internet of Things From Hype to Reality: The Road to
Digitization. Supringer International Publishing AG - 2017.
Sensors. ICT Lounge (n.d). Retrieved from - https://www.ictlounge.com/html/sensors.htm
Thomas, J. (2017). Coaxial cables, Twisted Pair STP and UTP cables, Twisted Pair Cable
Categories (CAT). Retrieved from -
http://www.omnisecu.com/basic-networking/common-network-cable-types.php
Submitted By 10
1 out of 10
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





