Internet of Things & Cyber Security Research Report, May 2018
VerifiedAdded on 2021/05/27
|19
|5950
|53
Report
AI Summary
This research report delves into the complex world of Internet of Things (IoT) and its associated cyber security challenges. The report begins by defining IoT and highlighting its growing significance in various sectors, followed by an exploration of critical cyber security issues and threats. It covers device security limitations, authorization and authentication problems, the need for device updates, and the importance of secure communication. Data privacy and integrity issues, architectural security concerns, and data protection measures are also discussed. The report further examines data encryption challenges, identity management security, and scale management issues in IoT-cloud environments. It also addresses denial of service and distributed denial of service attacks. The report concludes with recommendations for countermeasures and solutions, covering device security, cloud security, and IoT security lifecycle management, making it a valuable resource for understanding and addressing the cyber security challenges inherent in the rapidly expanding IoT landscape.
qwertyuiopasdfghjklzxcvbnmqw
ertyuiopasdfghjklzxcvbnmqwert
yuiopasdfghjklzxcvbnmqwertyui
opasdfghjklzxcvbnmqwertyuiop
asdfghjklzxcvbnmqwertyuiopasd
fghjklzxcvbnmqwertyuiopasdfgh
jklzxcvbnmqwertyuiopasdfghjkl
zxcvbnmqwertyuiopasdfghjklzxc
vbnmqwertyuiopasdfghjklzxcvb
nmqwertyuiopasdfghjklzxcvbnm
qwertyuiopasdfghjklzxcvbnmqw
ertyuiopasdfghjklzxcvbnmqwert
yuiopasdfghjklzxcvbnmqwertyui
opasdfghjklzxcvbnmqwertyuiop
asdfghjklzxcvbnmqwertyuiopasd
fghjklzxcvbnmqwertyuiopasdfgh
jklzxcvbnmrtyuiopasdfghjklzxcv
Internet of Things (IoT) & Cyber Security
Research Work
5/16/2018
ertyuiopasdfghjklzxcvbnmqwert
yuiopasdfghjklzxcvbnmqwertyui
opasdfghjklzxcvbnmqwertyuiop
asdfghjklzxcvbnmqwertyuiopasd
fghjklzxcvbnmqwertyuiopasdfgh
jklzxcvbnmqwertyuiopasdfghjkl
zxcvbnmqwertyuiopasdfghjklzxc
vbnmqwertyuiopasdfghjklzxcvb
nmqwertyuiopasdfghjklzxcvbnm
qwertyuiopasdfghjklzxcvbnmqw
ertyuiopasdfghjklzxcvbnmqwert
yuiopasdfghjklzxcvbnmqwertyui
opasdfghjklzxcvbnmqwertyuiop
asdfghjklzxcvbnmqwertyuiopasd
fghjklzxcvbnmqwertyuiopasdfgh
jklzxcvbnmrtyuiopasdfghjklzxcv
Internet of Things (IoT) & Cyber Security
Research Work
5/16/2018
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Internet of Things & Cyber Security
Table of Contents
Introduction...........................................................................................................................................1
Significance of the Research..............................................................................................................2
Literature Review: Cyber Security Issues and Threats in IoT............................................................2
Device Security Issues...................................................................................................................2
Authorization & Authentication Issues..........................................................................................3
Device Updates for Security..........................................................................................................3
Secure Communication Issues.......................................................................................................4
Data Privacy & Integrity Issues.....................................................................................................4
Architectural Security Issues.........................................................................................................5
Data Protection Issues....................................................................................................................5
Data Encryption Issues..................................................................................................................5
Identity Management Security Issues............................................................................................6
Scale Management for IoT-Cloud..................................................................................................6
Denial of Service & Distributed Denial of Service Attacks...........................................................6
Limitations & Research Gap.................................................................................................................7
Aim of the Research..........................................................................................................................7
Materials & Methods.............................................................................................................................7
Results.................................................................................................................................................12
Discussion...........................................................................................................................................13
Set of Countermeasures & Solutions...............................................................................................13
Device Security...........................................................................................................................13
Securing the Cloud......................................................................................................................13
IoT Security Lifecycle Management............................................................................................14
Recommendations & Conclusion........................................................................................................14
References...........................................................................................................................................15
1
Table of Contents
Introduction...........................................................................................................................................1
Significance of the Research..............................................................................................................2
Literature Review: Cyber Security Issues and Threats in IoT............................................................2
Device Security Issues...................................................................................................................2
Authorization & Authentication Issues..........................................................................................3
Device Updates for Security..........................................................................................................3
Secure Communication Issues.......................................................................................................4
Data Privacy & Integrity Issues.....................................................................................................4
Architectural Security Issues.........................................................................................................5
Data Protection Issues....................................................................................................................5
Data Encryption Issues..................................................................................................................5
Identity Management Security Issues............................................................................................6
Scale Management for IoT-Cloud..................................................................................................6
Denial of Service & Distributed Denial of Service Attacks...........................................................6
Limitations & Research Gap.................................................................................................................7
Aim of the Research..........................................................................................................................7
Materials & Methods.............................................................................................................................7
Results.................................................................................................................................................12
Discussion...........................................................................................................................................13
Set of Countermeasures & Solutions...............................................................................................13
Device Security...........................................................................................................................13
Securing the Cloud......................................................................................................................13
IoT Security Lifecycle Management............................................................................................14
Recommendations & Conclusion........................................................................................................14
References...........................................................................................................................................15
1

Internet of Things & Cyber Security
Introduction
Internet of Things (IoT) is defined as the amalgamation and inter-connection of varied
components to allow them to achieve as specific goal. The components that may be involved
in an IoT application may include computer systems, databases, file servers, exchange mail
servers, sensors, networking equipment and peripherals, web servers, home appliances, and
many more. IoT is gaining immense popularity and is being implemented by numerous
industrial sectors. The business organizations are now trying to adapt to the technology to
offer the IoT services and applications to the customers. There are various sectors that can be
witnessed to be using IoT applications and technology, such as healthcare, banking,
entertainment, commercial, and many others.
IoT has provided several benefits to the users in terms of the intelligent components that
come together to give rise to smart applications. The overall connectivity of the components
has increased with the emergence of IoT. However, there is one prime concern that has been
seen in this area. There are cyber security issues that are observed in association with the IoT
technology and applications.
Significance of the Research
IoT has started to become a significant component in the business and personal activities that
are carried out by the users. The occurrence of cyber security attacks in association with the
IoT applications and technology bring in numerous disadvantages. These disadvantages and
drawbacks are primarily in terms of the exposure of the confidential, sensitive, and private
data sets. There are also legal obligations that the IoT vendors suffer from as a result of the
occurrence of security attack. The reputation of the vendor in the market deteriorates and so
does the customer trust and engagement (Botta, de Donato, Persico & Pescapé, 2015).
The research explores the several cyber security issues that are associated with IoT and is
significant as it is necessary to have this information so that the measures to control and
prevent these issues may be developed (Wang, Bi & Xu, 2014).
2
Introduction
Internet of Things (IoT) is defined as the amalgamation and inter-connection of varied
components to allow them to achieve as specific goal. The components that may be involved
in an IoT application may include computer systems, databases, file servers, exchange mail
servers, sensors, networking equipment and peripherals, web servers, home appliances, and
many more. IoT is gaining immense popularity and is being implemented by numerous
industrial sectors. The business organizations are now trying to adapt to the technology to
offer the IoT services and applications to the customers. There are various sectors that can be
witnessed to be using IoT applications and technology, such as healthcare, banking,
entertainment, commercial, and many others.
IoT has provided several benefits to the users in terms of the intelligent components that
come together to give rise to smart applications. The overall connectivity of the components
has increased with the emergence of IoT. However, there is one prime concern that has been
seen in this area. There are cyber security issues that are observed in association with the IoT
technology and applications.
Significance of the Research
IoT has started to become a significant component in the business and personal activities that
are carried out by the users. The occurrence of cyber security attacks in association with the
IoT applications and technology bring in numerous disadvantages. These disadvantages and
drawbacks are primarily in terms of the exposure of the confidential, sensitive, and private
data sets. There are also legal obligations that the IoT vendors suffer from as a result of the
occurrence of security attack. The reputation of the vendor in the market deteriorates and so
does the customer trust and engagement (Botta, de Donato, Persico & Pescapé, 2015).
The research explores the several cyber security issues that are associated with IoT and is
significant as it is necessary to have this information so that the measures to control and
prevent these issues may be developed (Wang, Bi & Xu, 2014).
2
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Internet of Things & Cyber Security
Literature Review: Cyber Security Issues and Threats in IoT
Device Security Issues
There are various limitations and constraints that are applied on the devices that are
associated with the IoT applications. These limitations are in terms of the data storage limits
along with the processing capabilities that may be allowed on the device. It is also required
for the devices to always operate on the power saver modes whenever they may be running
on the batteries. As a result, the application of encryption algorithms and processes become
troublesome on these devices. The tasks that are associated with encrypting or decrypting the
data sets may not be quick to carry out the safe and secure transmission of the data sets.
There are various other forms of security attacks that may also take place, such as power
analysis attacks, side channel attacks, and so on. There are physical security risks that are also
associated with the IoT applications in terms of loss of device. For example, smart parking
IoT application is being widely used. The Smartphone of the user comprises of the location
and parking details of the vehicle. If the attacker succeeds in capturing the Smartphone of the
user then the security of the user as well as that of the vehicle may get compromised.
Authorization & Authentication Issues
The primary reason behind the occurrence of cyber security issues in IoT applications is the
enhanced number of access points that are present in these applications. There are a lot many
access points that lead to increase in the failure points as well. All of these access points
cannot be secured with a generalised authentication and authorization scheme that leads to
the presence of security loopholes (Duncan & Whittington, 2012). Due to the presence of so
many access points, there may be chances that one of these may utilize weaker password or
improper access control. Such vulnerabilities may then be utilized by the malevolent entities
to give shape to the security attacks.
For example, there are home automation systems that have been designed on the basis of IoT
technology and are being used by numerous users. There are a lot of components involved in
the application, such as Smartphones of the house owners, computer systems, routers, home
appliances, electronic gadgets, and many more. The use of poor access control in any of these
components may compromise the overall security (Yousuf, Mahmoud, Aloul & Zualkernan,
2015).
3
Literature Review: Cyber Security Issues and Threats in IoT
Device Security Issues
There are various limitations and constraints that are applied on the devices that are
associated with the IoT applications. These limitations are in terms of the data storage limits
along with the processing capabilities that may be allowed on the device. It is also required
for the devices to always operate on the power saver modes whenever they may be running
on the batteries. As a result, the application of encryption algorithms and processes become
troublesome on these devices. The tasks that are associated with encrypting or decrypting the
data sets may not be quick to carry out the safe and secure transmission of the data sets.
There are various other forms of security attacks that may also take place, such as power
analysis attacks, side channel attacks, and so on. There are physical security risks that are also
associated with the IoT applications in terms of loss of device. For example, smart parking
IoT application is being widely used. The Smartphone of the user comprises of the location
and parking details of the vehicle. If the attacker succeeds in capturing the Smartphone of the
user then the security of the user as well as that of the vehicle may get compromised.
Authorization & Authentication Issues
The primary reason behind the occurrence of cyber security issues in IoT applications is the
enhanced number of access points that are present in these applications. There are a lot many
access points that lead to increase in the failure points as well. All of these access points
cannot be secured with a generalised authentication and authorization scheme that leads to
the presence of security loopholes (Duncan & Whittington, 2012). Due to the presence of so
many access points, there may be chances that one of these may utilize weaker password or
improper access control. Such vulnerabilities may then be utilized by the malevolent entities
to give shape to the security attacks.
For example, there are home automation systems that have been designed on the basis of IoT
technology and are being used by numerous users. There are a lot of components involved in
the application, such as Smartphones of the house owners, computer systems, routers, home
appliances, electronic gadgets, and many more. The use of poor access control in any of these
components may compromise the overall security (Yousuf, Mahmoud, Aloul & Zualkernan,
2015).
3
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Internet of Things & Cyber Security
Device Updates for Security
The IoT devices and components that are involved in any of the IoT application shall be
updated on a regular basis. These updates shall focus upon security patches as there are newer
forms of security risks and attacks that are being developed with each passing day. There are
scenarios wherein the IoT vendors delay the launch of such updates. Also, the launch of the
updates by respective device company and owners is also essential and the syncing of the two
becomes a problem. This leads to the ability to the attackers to target specific security
vulnerabilities to give shape to the security attacks (Ali, Khan & Zomaya, 2016). The
installation of the updates and patches also demands downtime which may vary from one
device to the other. The downtime required for certain devices may be longer which may lead
to disengagement of the users. For example, in case of the IoT-based healthcare applications,
there are smart wearables and other devices involved in the application. The presence of
security vulnerability in any of these components may bring in increased security risks and
attacks.
Secure Communication Issues
Communication among the IoT components is essential in any of the IoT application. It is
because the applications will not be able to function correctly if they fail to interact with each
other as per the requirements. As a result, these communications and transmission
mechanisms shall be secure and safe (Pan & McElhannon, 2017). The majority of the
communication activities and messages that are transmitted to and from the IoT devices are
not secure. It is because these messages are not encrypted which enhances the possibility of a
security attack on the same. The cyber security data leakages and data breaches are often
witnessed as a result of the same.
Data Privacy & Integrity Issues
There are also cloud platforms used in the IoT applications for communication, transmission,
and storage purposes. The data sets are stored and processed using the cloud databases and
networks. In such cases, the data privacy norms and principles that are used to monitor the
sensitive and confidential information sets are separated from the data payloads associated
with IoT (Sahmim & Gharsellaoui, 2017). It may become necessary to eliminate the
unwanted pieces of data so that adherence to the regulatory principles and policies is not
adversely impacted. The involvement of varied IoT components along with the usage of
cloud platforms and mechanisms leads to an increase in the number and types of privacy
issues.
4
Device Updates for Security
The IoT devices and components that are involved in any of the IoT application shall be
updated on a regular basis. These updates shall focus upon security patches as there are newer
forms of security risks and attacks that are being developed with each passing day. There are
scenarios wherein the IoT vendors delay the launch of such updates. Also, the launch of the
updates by respective device company and owners is also essential and the syncing of the two
becomes a problem. This leads to the ability to the attackers to target specific security
vulnerabilities to give shape to the security attacks (Ali, Khan & Zomaya, 2016). The
installation of the updates and patches also demands downtime which may vary from one
device to the other. The downtime required for certain devices may be longer which may lead
to disengagement of the users. For example, in case of the IoT-based healthcare applications,
there are smart wearables and other devices involved in the application. The presence of
security vulnerability in any of these components may bring in increased security risks and
attacks.
Secure Communication Issues
Communication among the IoT components is essential in any of the IoT application. It is
because the applications will not be able to function correctly if they fail to interact with each
other as per the requirements. As a result, these communications and transmission
mechanisms shall be secure and safe (Pan & McElhannon, 2017). The majority of the
communication activities and messages that are transmitted to and from the IoT devices are
not secure. It is because these messages are not encrypted which enhances the possibility of a
security attack on the same. The cyber security data leakages and data breaches are often
witnessed as a result of the same.
Data Privacy & Integrity Issues
There are also cloud platforms used in the IoT applications for communication, transmission,
and storage purposes. The data sets are stored and processed using the cloud databases and
networks. In such cases, the data privacy norms and principles that are used to monitor the
sensitive and confidential information sets are separated from the data payloads associated
with IoT (Sahmim & Gharsellaoui, 2017). It may become necessary to eliminate the
unwanted pieces of data so that adherence to the regulatory principles and policies is not
adversely impacted. The involvement of varied IoT components along with the usage of
cloud platforms and mechanisms leads to an increase in the number and types of privacy
issues.
4

Internet of Things & Cyber Security
Malware attacks are one of the most common types of cyber security attacks that take place
on the IoT applications using cloud platforms and other attacking agents. There are various
forms of malware that have been developed by the attackers, such as worms Logic Bombs,
Trojan Horses, viruses, ransomware, and many more. Integrity issues are also a common
sight with the IoT applications are there may be unauthorized alteration of the media contents
or the messages that may take place. For example, in the case of the office automation
system, there is a lot of sensitive information that is associated with this IoT application. The
malware attacks on such an application lead to the compromise of the privacy of the entire
organization.
Architectural Security Issues
Architecture of the IoT application may also contribute in the occurrence of security risks and
attacks. There are cloud platforms and architectures that are also used in an IoT application.
These may be private, public, or hybrid cloud. There are sensitive, private, public,
confidential, internal, and other data sets that are involved in an IoT application. The cloud
architecture and the data category must match with each other (Ezema, Abdullah & Mohd,
2018). For example, transmission of the confidential data sets using cloud architecture as
public may lead to the enhanced probability of the security attacks. Such architectural
mistakes and issues lead to the occurrence of security threats and attacks (Bhabad & Bagade,
2015).
Data Protection Issues
The IoT vendors and service providers provide the users with the specific security measures
and protocols that are integrated in the application. It is done to make sure that the user data
and information is always kept protected from any sorts of cyber security attacks and risks.
However, it is also necessary to maintain the multi-tenancy and resource sharing abilities in
the application (Vurukonda, 2016). The IoT architecture and design is therefore based on the
economies of scale that lead to increased probability of the occurrence of the security risks
and attacks.
There are certain predefined settings that come along with the IoT applications that are
handed over to the users. The vendors at times obtain the complete data access to the
application in advance without letting the users know about the same. The protection and
confidentiality of the data sets may be affected as a result (Puliafito, Celesti, Villari & Fazio,
2015).
5
Malware attacks are one of the most common types of cyber security attacks that take place
on the IoT applications using cloud platforms and other attacking agents. There are various
forms of malware that have been developed by the attackers, such as worms Logic Bombs,
Trojan Horses, viruses, ransomware, and many more. Integrity issues are also a common
sight with the IoT applications are there may be unauthorized alteration of the media contents
or the messages that may take place. For example, in the case of the office automation
system, there is a lot of sensitive information that is associated with this IoT application. The
malware attacks on such an application lead to the compromise of the privacy of the entire
organization.
Architectural Security Issues
Architecture of the IoT application may also contribute in the occurrence of security risks and
attacks. There are cloud platforms and architectures that are also used in an IoT application.
These may be private, public, or hybrid cloud. There are sensitive, private, public,
confidential, internal, and other data sets that are involved in an IoT application. The cloud
architecture and the data category must match with each other (Ezema, Abdullah & Mohd,
2018). For example, transmission of the confidential data sets using cloud architecture as
public may lead to the enhanced probability of the security attacks. Such architectural
mistakes and issues lead to the occurrence of security threats and attacks (Bhabad & Bagade,
2015).
Data Protection Issues
The IoT vendors and service providers provide the users with the specific security measures
and protocols that are integrated in the application. It is done to make sure that the user data
and information is always kept protected from any sorts of cyber security attacks and risks.
However, it is also necessary to maintain the multi-tenancy and resource sharing abilities in
the application (Vurukonda, 2016). The IoT architecture and design is therefore based on the
economies of scale that lead to increased probability of the occurrence of the security risks
and attacks.
There are certain predefined settings that come along with the IoT applications that are
handed over to the users. The vendors at times obtain the complete data access to the
application in advance without letting the users know about the same. The protection and
confidentiality of the data sets may be affected as a result (Puliafito, Celesti, Villari & Fazio,
2015).
5
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Internet of Things & Cyber Security
Data Encryption Issues
There are varied components and devices that are present in an IoT application. This leads to
the need to manage the several keys for enhanced security and protection. Due to the
involvement of varied sets of data with different structures and massive volumes along with
the varied components in the application, the management of the keys become a complex
process (Kamalakannan & Tamilselvan, 2016). For example, in the IoT applications that
make use of any of the location-based service, the data sets are acquired from the location
sensors that are involved. These may dynamically change as per the change in location
(Zhou, Cao, Dong & Vasilakos, 2017). When the nature of the change is authorised, it may
become essential to revoke all the security keys involved and issue fresh keys for maintaining
security and privacy.
Identity Management Security Issues
The users of any of the IoT applications carry out the major set of interactions with the
tenant’s application. It may be hosted by a cloud vendor or service provider. There are also
many other points that shall be considered in the IoT application because of the constraints
involved with the same (Wahab, Ahmad, Muhammad & Ali, 2017). Adherence to the
security protocols and measures is also essential and significant and often comes up as one of
the prime constraints. It may also be necessary to send the pieces of information to multiple
destinations at the same time. The process of transmission for each of these cases is important
to make sure that secure communication and transmission is made possible (Maple, 2017).
Scale Management for IoT-Cloud
The number of clients and third parties that are involved in the IoT applications are also huge.
This is because there are various components present in an IoT application. The data sets
involved also have varied volumes, velocity, and structures. It is required for the application
to securely manage and maintain the varied loads on the data sets along with the security of
the same. The inefficiencies in scalability management may bring up the availability issues
and also deterioration of quality in the application services (Tari, Yi, Premarathne, Bertok &
Khalil, 2015).
It is necessary for the IoT applications to maintain the logs for every component that is
involved. It is one of the significant aspects involved in maintaining the security as these logs
may be studied and reviewed to come up with the attacking patterns and trends. However, the
log maintenance is complex in case of IoT. There may be adverse implication on the
6
Data Encryption Issues
There are varied components and devices that are present in an IoT application. This leads to
the need to manage the several keys for enhanced security and protection. Due to the
involvement of varied sets of data with different structures and massive volumes along with
the varied components in the application, the management of the keys become a complex
process (Kamalakannan & Tamilselvan, 2016). For example, in the IoT applications that
make use of any of the location-based service, the data sets are acquired from the location
sensors that are involved. These may dynamically change as per the change in location
(Zhou, Cao, Dong & Vasilakos, 2017). When the nature of the change is authorised, it may
become essential to revoke all the security keys involved and issue fresh keys for maintaining
security and privacy.
Identity Management Security Issues
The users of any of the IoT applications carry out the major set of interactions with the
tenant’s application. It may be hosted by a cloud vendor or service provider. There are also
many other points that shall be considered in the IoT application because of the constraints
involved with the same (Wahab, Ahmad, Muhammad & Ali, 2017). Adherence to the
security protocols and measures is also essential and significant and often comes up as one of
the prime constraints. It may also be necessary to send the pieces of information to multiple
destinations at the same time. The process of transmission for each of these cases is important
to make sure that secure communication and transmission is made possible (Maple, 2017).
Scale Management for IoT-Cloud
The number of clients and third parties that are involved in the IoT applications are also huge.
This is because there are various components present in an IoT application. The data sets
involved also have varied volumes, velocity, and structures. It is required for the application
to securely manage and maintain the varied loads on the data sets along with the security of
the same. The inefficiencies in scalability management may bring up the availability issues
and also deterioration of quality in the application services (Tari, Yi, Premarathne, Bertok &
Khalil, 2015).
It is necessary for the IoT applications to maintain the logs for every component that is
involved. It is one of the significant aspects involved in maintaining the security as these logs
may be studied and reviewed to come up with the attacking patterns and trends. However, the
log maintenance is complex in case of IoT. There may be adverse implication on the
6
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Internet of Things & Cyber Security
integrity, privacy, confidentiality, and availability of the information and data sets (Bokefode,
Bhise, Satarkar & Modani, 2016).
Denial of Service & Distributed Denial of Service Attacks
There are multiple network connections that are associated with the IoT applications and
services. These connections are mainly because of the presence of a lot of components and
devices. The malevolent entities may launch abundant network traffic as garbage data that
may impact the availability of the services and application access. These are termed as denial
of service and distributed denial of service attacks. These forms of attacks may have adverse
impacts on the user trust and engagement (Mahjabin, 2017). For example, if a connected car
or smart retail application suffers from the denial of service attacks, then the users will not be
able to carry out the desired tasks which may deteriorate the trust. In the case of connected
health applications, the impact may be worse.
Limitations & Research Gap
The major set of the security issues and threats that have been discussed and listed in the
research work in the past primarily focus on the cloud-related or device-related security
issues. However, with the advent of technology, there are newer attacking mediums and
agents that are being explored by the attackers and are being used to give shape to the
security risks and attacks. Some of the key technologies that are now being amalgamated
with IoT include artificial intelligence, machine learning, data analytics, data warehousing,
and many others. There are specific concerns that are associated with each of these
technologies and it may take a newer shape with the involvement of the technology with IoT.
The research should have covered this aspect as well. It is necessary to throw light on these
lesser researched areas as the need to control and prevent the cyber security risks in IoT is
becoming urgent.
Aim of the Research
The aim of the research work is to qualitatively research and analyse the various cyber
security risks and issues that are present in the case of IoT and to describe the same along
with the control measures that may be used to put a check on these attacks.
7
integrity, privacy, confidentiality, and availability of the information and data sets (Bokefode,
Bhise, Satarkar & Modani, 2016).
Denial of Service & Distributed Denial of Service Attacks
There are multiple network connections that are associated with the IoT applications and
services. These connections are mainly because of the presence of a lot of components and
devices. The malevolent entities may launch abundant network traffic as garbage data that
may impact the availability of the services and application access. These are termed as denial
of service and distributed denial of service attacks. These forms of attacks may have adverse
impacts on the user trust and engagement (Mahjabin, 2017). For example, if a connected car
or smart retail application suffers from the denial of service attacks, then the users will not be
able to carry out the desired tasks which may deteriorate the trust. In the case of connected
health applications, the impact may be worse.
Limitations & Research Gap
The major set of the security issues and threats that have been discussed and listed in the
research work in the past primarily focus on the cloud-related or device-related security
issues. However, with the advent of technology, there are newer attacking mediums and
agents that are being explored by the attackers and are being used to give shape to the
security risks and attacks. Some of the key technologies that are now being amalgamated
with IoT include artificial intelligence, machine learning, data analytics, data warehousing,
and many others. There are specific concerns that are associated with each of these
technologies and it may take a newer shape with the involvement of the technology with IoT.
The research should have covered this aspect as well. It is necessary to throw light on these
lesser researched areas as the need to control and prevent the cyber security risks in IoT is
becoming urgent.
Aim of the Research
The aim of the research work is to qualitatively research and analyse the various cyber
security risks and issues that are present in the case of IoT and to describe the same along
with the control measures that may be used to put a check on these attacks.
7
Internet of Things & Cyber Security
Materials & Methods
The method of research that was adopted in this case was qualitative method. It was
necessary to collect information and data sets for the research purpose to make sure that the
necessary information was available to understand the various forms of cyber security risks
and attacks in association with IoT.
The following data collection methods were used in the process.
Domain Analysis: The domain that was involved in the research work focussed upon
the technologies as Internet of Things (IoT), cyber systems and information sets, and
cloud computing. These domains were analysed in the application areas of IoT, such
as healthcare, manufacturing, retail, agriculture, automobiles, and many more.
Interviews: There were interview sessions organized with the IoT vendors, service
providers, and the users of these services. The interviews were carried out by
preparing the interview questions for each of the groups and then the prepared
questions were asked during the sessions. The information provided by each of these
groups were then analysed using the automated tools and platforms.
Observations: There are numerous IoT applications that are already in use. These
applications were observed to understand the various forms of cyber security attacks
that took place on the applications. The form of attack, reason behind the occurrence
of these attacks, and likewise was observed.
Surveys: There have been a lot of cases of cyber-attacks and compromises in
association with the IoT applications and platforms. There were surveys that were
conducted to understand the details of these attacks in terms of impacts and
consequences, response strategy that was used, associated parties impacted by the
attack, and likewise.
Group discussions & Brainstorming sessions: There were also varied groups that were
invited to discuss the IoT applications and the involvement & role of cyber security in
the same.
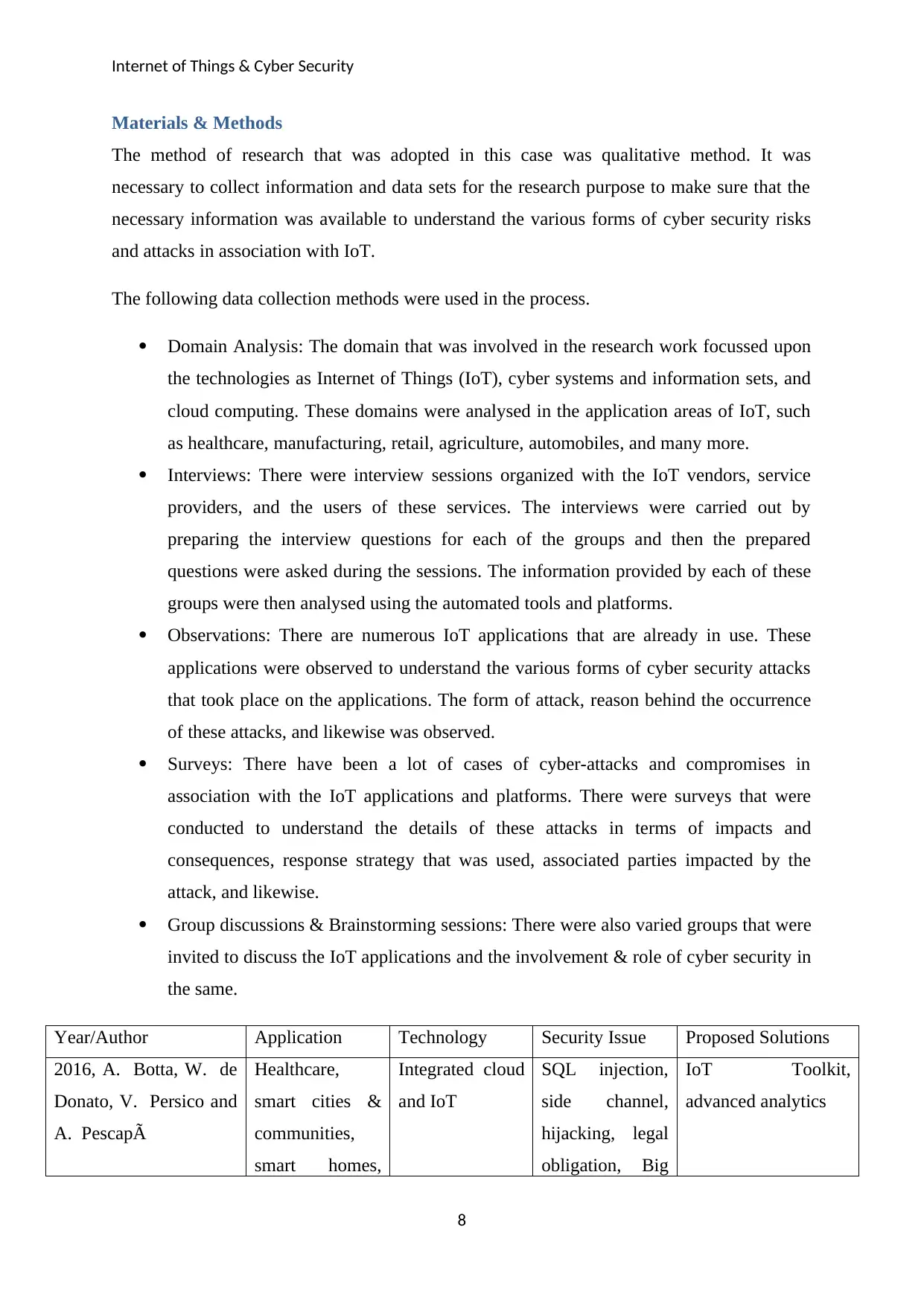
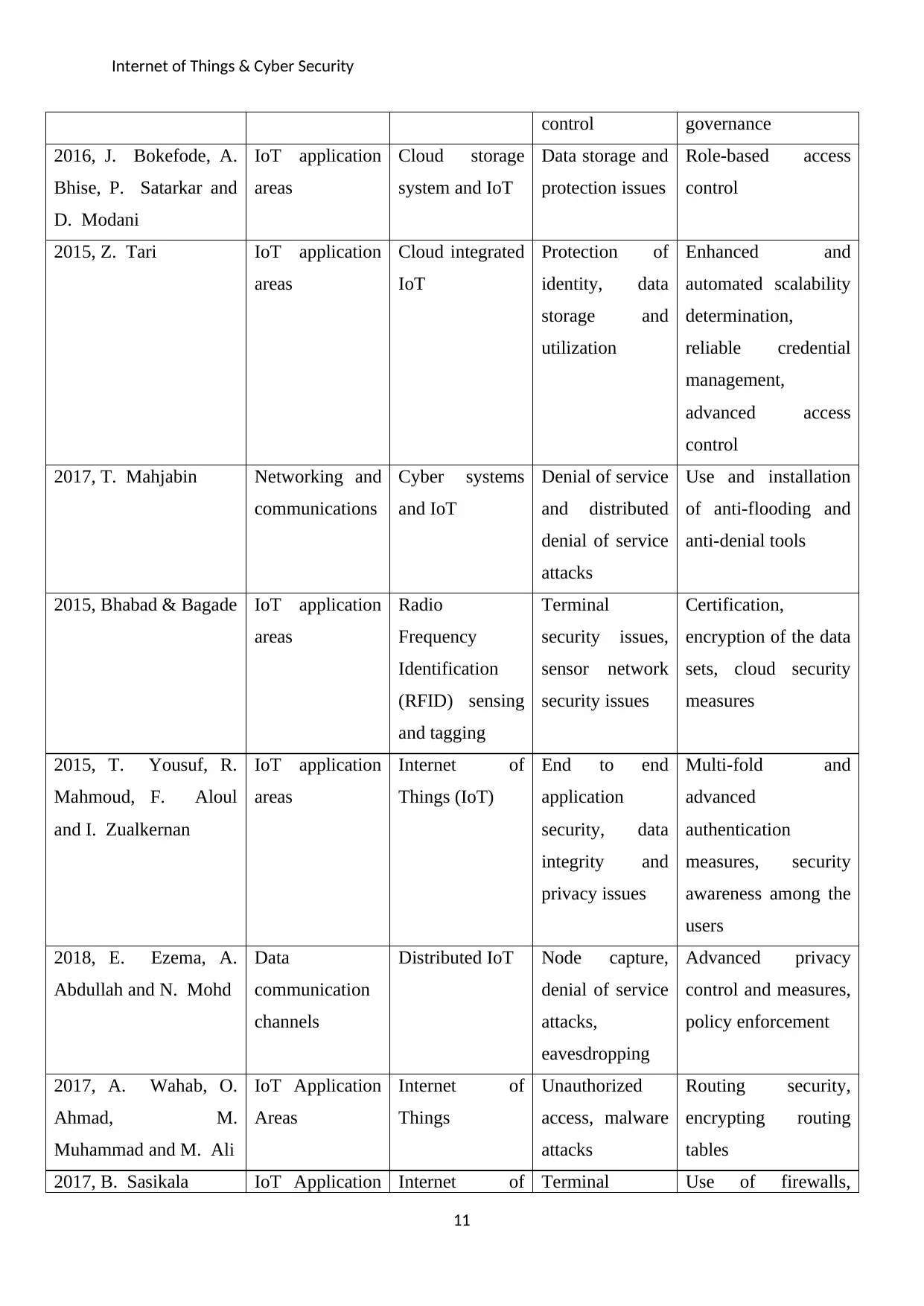
Year/Author Application Technology Security Issue Proposed Solutions
2016, A. Botta, W. de
Donato, V. Persico and
A. PescapÃ
Healthcare,
smart cities &
communities,
smart homes,
Integrated cloud
and IoT
SQL injection,
side channel,
hijacking, legal
obligation, Big
IoT Toolkit,
advanced analytics
8
Materials & Methods
The method of research that was adopted in this case was qualitative method. It was
necessary to collect information and data sets for the research purpose to make sure that the
necessary information was available to understand the various forms of cyber security risks
and attacks in association with IoT.
The following data collection methods were used in the process.
Domain Analysis: The domain that was involved in the research work focussed upon
the technologies as Internet of Things (IoT), cyber systems and information sets, and
cloud computing. These domains were analysed in the application areas of IoT, such
as healthcare, manufacturing, retail, agriculture, automobiles, and many more.
Interviews: There were interview sessions organized with the IoT vendors, service
providers, and the users of these services. The interviews were carried out by
preparing the interview questions for each of the groups and then the prepared
questions were asked during the sessions. The information provided by each of these
groups were then analysed using the automated tools and platforms.
Observations: There are numerous IoT applications that are already in use. These
applications were observed to understand the various forms of cyber security attacks
that took place on the applications. The form of attack, reason behind the occurrence
of these attacks, and likewise was observed.
Surveys: There have been a lot of cases of cyber-attacks and compromises in
association with the IoT applications and platforms. There were surveys that were
conducted to understand the details of these attacks in terms of impacts and
consequences, response strategy that was used, associated parties impacted by the
attack, and likewise.
Group discussions & Brainstorming sessions: There were also varied groups that were
invited to discuss the IoT applications and the involvement & role of cyber security in
the same.
Year/Author Application Technology Security Issue Proposed Solutions
2016, A. Botta, W. de
Donato, V. Persico and
A. PescapÃ
Healthcare,
smart cities &
communities,
smart homes,
Integrated cloud
and IoT
SQL injection,
side channel,
hijacking, legal
obligation, Big
IoT Toolkit,
advanced analytics
8
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
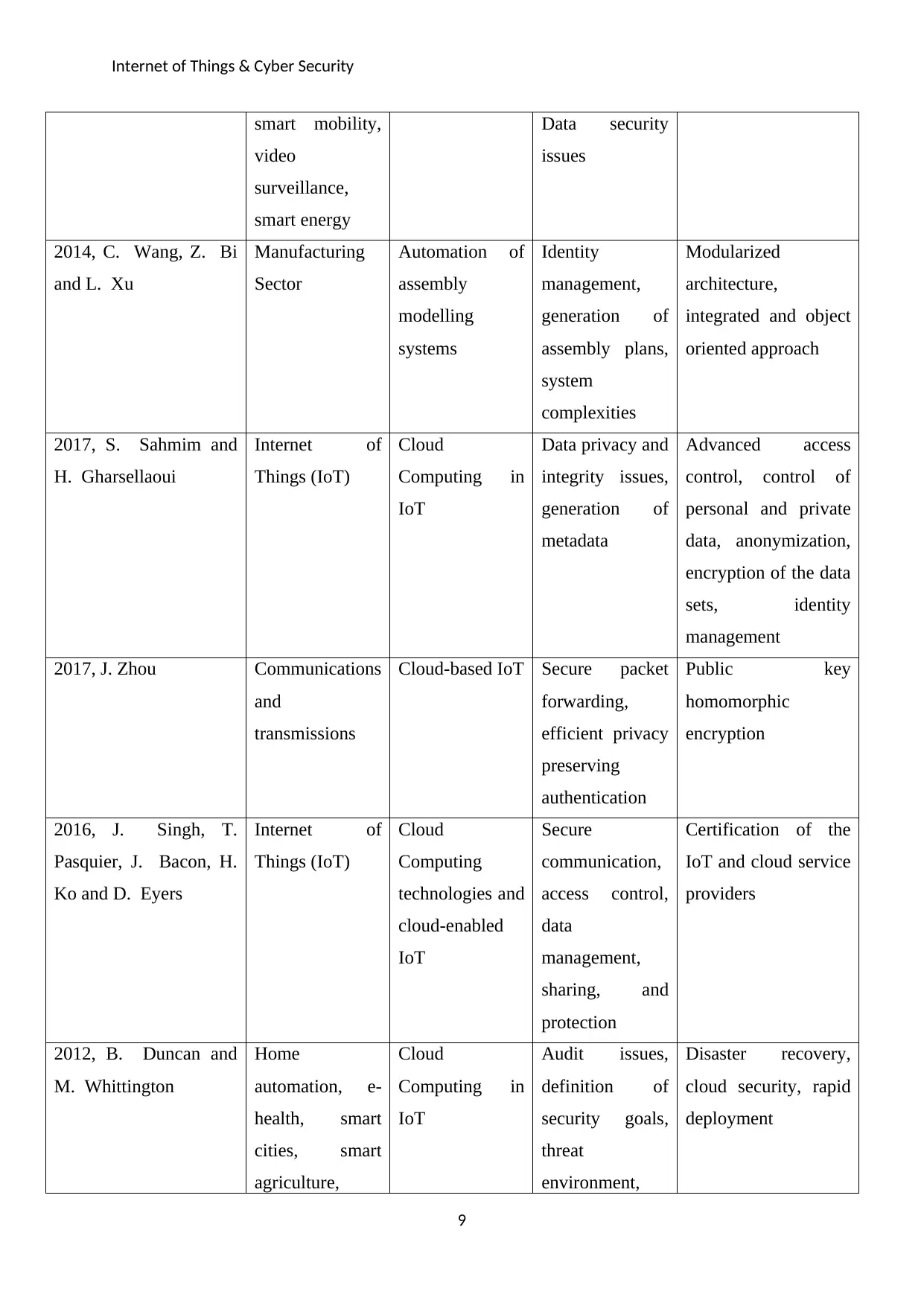
Internet of Things & Cyber Security
smart mobility,
video
surveillance,
smart energy
Data security
issues
2014, C. Wang, Z. Bi
and L. Xu
Manufacturing
Sector
Automation of
assembly
modelling
systems
Identity
management,
generation of
assembly plans,
system
complexities
Modularized
architecture,
integrated and object
oriented approach
2017, S. Sahmim and
H. Gharsellaoui
Internet of
Things (IoT)
Cloud
Computing in
IoT
Data privacy and
integrity issues,
generation of
metadata
Advanced access
control, control of
personal and private
data, anonymization,
encryption of the data
sets, identity
management
2017, J. Zhou Communications
and
transmissions
Cloud-based IoT Secure packet
forwarding,
efficient privacy
preserving
authentication
Public key
homomorphic
encryption
2016, J. Singh, T.
Pasquier, J. Bacon, H.
Ko and D. Eyers
Internet of
Things (IoT)
Cloud
Computing
technologies and
cloud-enabled
IoT
Secure
communication,
access control,
data
management,
sharing, and
protection
Certification of the
IoT and cloud service
providers
2012, B. Duncan and
M. Whittington
Home
automation, e-
health, smart
cities, smart
agriculture,
Cloud
Computing in
IoT
Audit issues,
definition of
security goals,
threat
environment,
Disaster recovery,
cloud security, rapid
deployment
9
smart mobility,
video
surveillance,
smart energy
Data security
issues
2014, C. Wang, Z. Bi
and L. Xu
Manufacturing
Sector
Automation of
assembly
modelling
systems
Identity
management,
generation of
assembly plans,
system
complexities
Modularized
architecture,
integrated and object
oriented approach
2017, S. Sahmim and
H. Gharsellaoui
Internet of
Things (IoT)
Cloud
Computing in
IoT
Data privacy and
integrity issues,
generation of
metadata
Advanced access
control, control of
personal and private
data, anonymization,
encryption of the data
sets, identity
management
2017, J. Zhou Communications
and
transmissions
Cloud-based IoT Secure packet
forwarding,
efficient privacy
preserving
authentication
Public key
homomorphic
encryption
2016, J. Singh, T.
Pasquier, J. Bacon, H.
Ko and D. Eyers
Internet of
Things (IoT)
Cloud
Computing
technologies and
cloud-enabled
IoT
Secure
communication,
access control,
data
management,
sharing, and
protection
Certification of the
IoT and cloud service
providers
2012, B. Duncan and
M. Whittington
Home
automation, e-
health, smart
cities, smart
agriculture,
Cloud
Computing in
IoT
Audit issues,
definition of
security goals,
threat
environment,
Disaster recovery,
cloud security, rapid
deployment
9
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
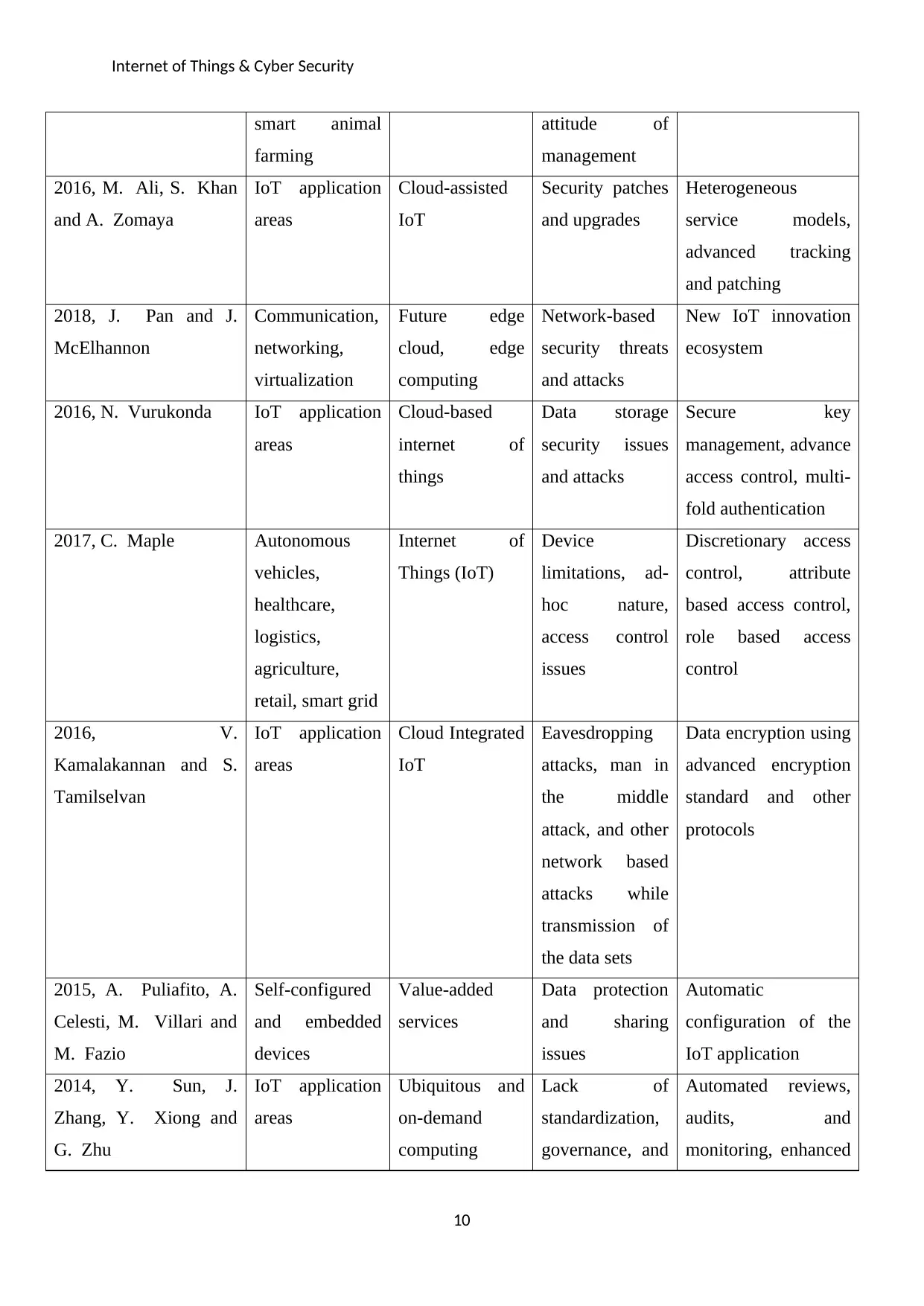
Internet of Things & Cyber Security
smart animal
farming
attitude of
management
2016, M. Ali, S. Khan
and A. Zomaya
IoT application
areas
Cloud-assisted
IoT
Security patches
and upgrades
Heterogeneous
service models,
advanced tracking
and patching
2018, J. Pan and J.
McElhannon
Communication,
networking,
virtualization
Future edge
cloud, edge
computing
Network-based
security threats
and attacks
New IoT innovation
ecosystem
2016, N. Vurukonda IoT application
areas
Cloud-based
internet of
things
Data storage
security issues
and attacks
Secure key
management, advance
access control, multi-
fold authentication
2017, C. Maple Autonomous
vehicles,
healthcare,
logistics,
agriculture,
retail, smart grid
Internet of
Things (IoT)
Device
limitations, ad-
hoc nature,
access control
issues
Discretionary access
control, attribute
based access control,
role based access
control
2016, V.
Kamalakannan and S.
Tamilselvan
IoT application
areas
Cloud Integrated
IoT
Eavesdropping
attacks, man in
the middle
attack, and other
network based
attacks while
transmission of
the data sets
Data encryption using
advanced encryption
standard and other
protocols
2015, A. Puliafito, A.
Celesti, M. Villari and
M. Fazio
Self-configured
and embedded
devices
Value-added
services
Data protection
and sharing
issues
Automatic
configuration of the
IoT application
2014, Y. Sun, J.
Zhang, Y. Xiong and
G. Zhu
IoT application
areas
Ubiquitous and
on-demand
computing
Lack of
standardization,
governance, and
Automated reviews,
audits, and
monitoring, enhanced
10
smart animal
farming
attitude of
management
2016, M. Ali, S. Khan
and A. Zomaya
IoT application
areas
Cloud-assisted
IoT
Security patches
and upgrades
Heterogeneous
service models,
advanced tracking
and patching
2018, J. Pan and J.
McElhannon
Communication,
networking,
virtualization
Future edge
cloud, edge
computing
Network-based
security threats
and attacks
New IoT innovation
ecosystem
2016, N. Vurukonda IoT application
areas
Cloud-based
internet of
things
Data storage
security issues
and attacks
Secure key
management, advance
access control, multi-
fold authentication
2017, C. Maple Autonomous
vehicles,
healthcare,
logistics,
agriculture,
retail, smart grid
Internet of
Things (IoT)
Device
limitations, ad-
hoc nature,
access control
issues
Discretionary access
control, attribute
based access control,
role based access
control
2016, V.
Kamalakannan and S.
Tamilselvan
IoT application
areas
Cloud Integrated
IoT
Eavesdropping
attacks, man in
the middle
attack, and other
network based
attacks while
transmission of
the data sets
Data encryption using
advanced encryption
standard and other
protocols
2015, A. Puliafito, A.
Celesti, M. Villari and
M. Fazio
Self-configured
and embedded
devices
Value-added
services
Data protection
and sharing
issues
Automatic
configuration of the
IoT application
2014, Y. Sun, J.
Zhang, Y. Xiong and
G. Zhu
IoT application
areas
Ubiquitous and
on-demand
computing
Lack of
standardization,
governance, and
Automated reviews,
audits, and
monitoring, enhanced
10
Internet of Things & Cyber Security
control governance
2016, J. Bokefode, A.
Bhise, P. Satarkar and
D. Modani
IoT application
areas
Cloud storage
system and IoT
Data storage and
protection issues
Role-based access
control
2015, Z. Tari IoT application
areas
Cloud integrated
IoT
Protection of
identity, data
storage and
utilization
Enhanced and
automated scalability
determination,
reliable credential
management,
advanced access
control
2017, T. Mahjabin Networking and
communications
Cyber systems
and IoT
Denial of service
and distributed
denial of service
attacks
Use and installation
of anti-flooding and
anti-denial tools
2015, Bhabad & Bagade IoT application
areas
Radio
Frequency
Identification
(RFID) sensing
and tagging
Terminal
security issues,
sensor network
security issues
Certification,
encryption of the data
sets, cloud security
measures
2015, T. Yousuf, R.
Mahmoud, F. Aloul
and I. Zualkernan
IoT application
areas
Internet of
Things (IoT)
End to end
application
security, data
integrity and
privacy issues
Multi-fold and
advanced
authentication
measures, security
awareness among the
users
2018, E. Ezema, A.
Abdullah and N. Mohd
Data
communication
channels
Distributed IoT Node capture,
denial of service
attacks,
eavesdropping
Advanced privacy
control and measures,
policy enforcement
2017, A. Wahab, O.
Ahmad, M.
Muhammad and M. Ali
IoT Application
Areas
Internet of
Things
Unauthorized
access, malware
attacks
Routing security,
encrypting routing
tables
2017, B. Sasikala IoT Application Internet of Terminal Use of firewalls,
11
control governance
2016, J. Bokefode, A.
Bhise, P. Satarkar and
D. Modani
IoT application
areas
Cloud storage
system and IoT
Data storage and
protection issues
Role-based access
control
2015, Z. Tari IoT application
areas
Cloud integrated
IoT
Protection of
identity, data
storage and
utilization
Enhanced and
automated scalability
determination,
reliable credential
management,
advanced access
control
2017, T. Mahjabin Networking and
communications
Cyber systems
and IoT
Denial of service
and distributed
denial of service
attacks
Use and installation
of anti-flooding and
anti-denial tools
2015, Bhabad & Bagade IoT application
areas
Radio
Frequency
Identification
(RFID) sensing
and tagging
Terminal
security issues,
sensor network
security issues
Certification,
encryption of the data
sets, cloud security
measures
2015, T. Yousuf, R.
Mahmoud, F. Aloul
and I. Zualkernan
IoT application
areas
Internet of
Things (IoT)
End to end
application
security, data
integrity and
privacy issues
Multi-fold and
advanced
authentication
measures, security
awareness among the
users
2018, E. Ezema, A.
Abdullah and N. Mohd
Data
communication
channels
Distributed IoT Node capture,
denial of service
attacks,
eavesdropping
Advanced privacy
control and measures,
policy enforcement
2017, A. Wahab, O.
Ahmad, M.
Muhammad and M. Ali
IoT Application
Areas
Internet of
Things
Unauthorized
access, malware
attacks
Routing security,
encrypting routing
tables
2017, B. Sasikala IoT Application Internet of Terminal Use of firewalls,
11
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 19
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





