INFS 5115 Security Principles: Analyzing and Mitigating IoT Threats
VerifiedAdded on 2023/04/03
|10
|865
|302
Presentation
AI Summary
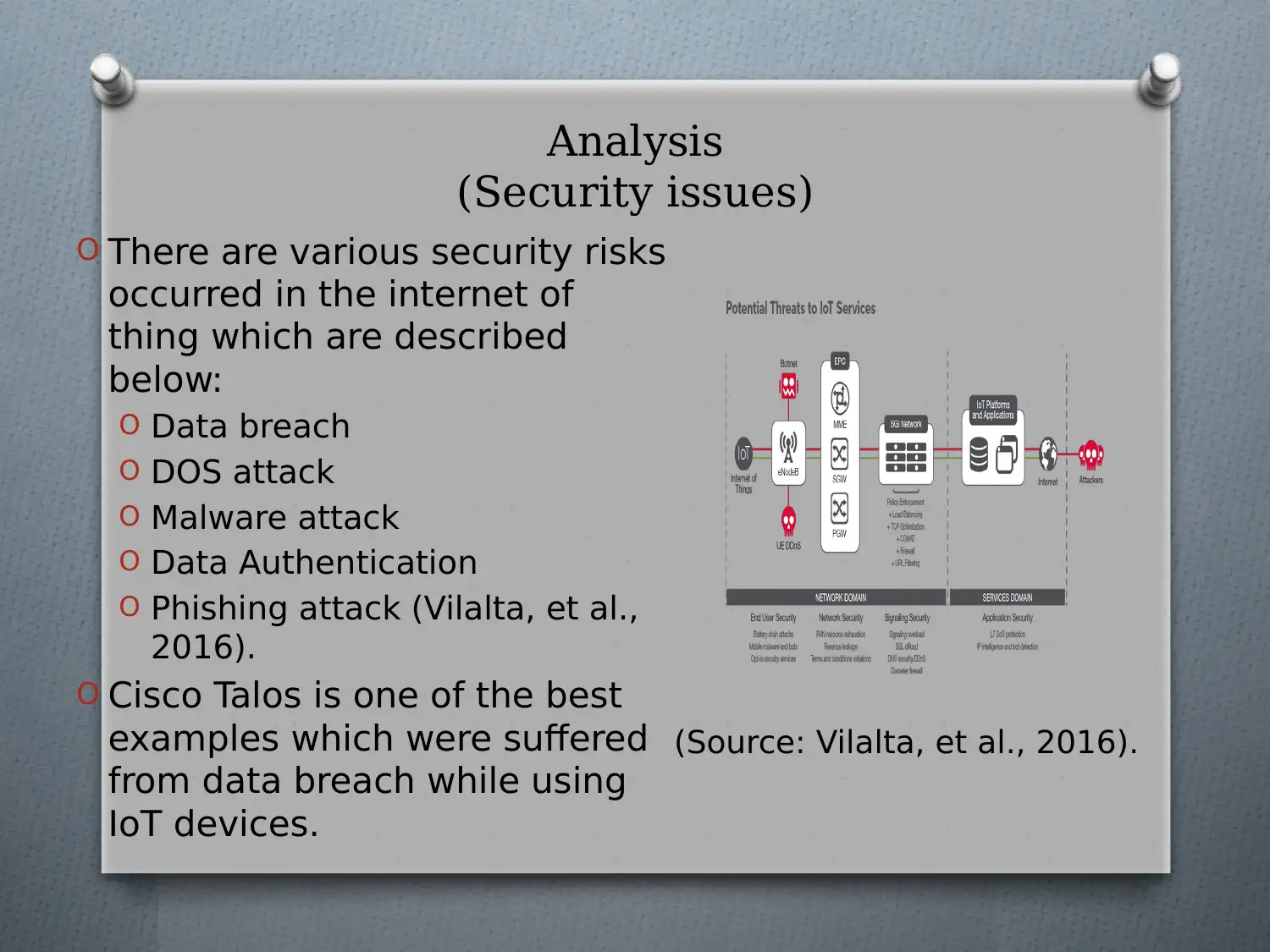
This presentation provides an overview of Internet of Things (IoT) security, defining IoT as an ecosystem of linked physical devices accessible via the internet. It explores the security issues associated with IoT, focusing on security threats such as data breaches, Denial of Service (DoS) attacks, and malware attacks, and evaluates mitigation techniques. The analysis highlights that security is a major concern for consumers, with vulnerabilities arising from unauthorized servers and inadequate security measures. Recommendations for mitigating security problems include using authentic networks, prioritizing data security, developing security policies, regularly updating software, avoiding third-party applications, adopting firewalls and antiviruses, and implementing encryption techniques. The presentation concludes that addressing security vulnerabilities and using authorized networks are crucial for enhancing IoT security, recommending that organizations like Cisco Talos prioritize security and develop comprehensive privacy plans. Desklib is a platform where students can find similar solved assignments and study resources.
1 out of 10















![[object Object]](/_next/static/media/star-bottom.7253800d.svg)