Analyzing IoT Mobile Device Security: Architecture and Threats
VerifiedAdded on 2023/04/08
|6
|654
|383
Report
AI Summary
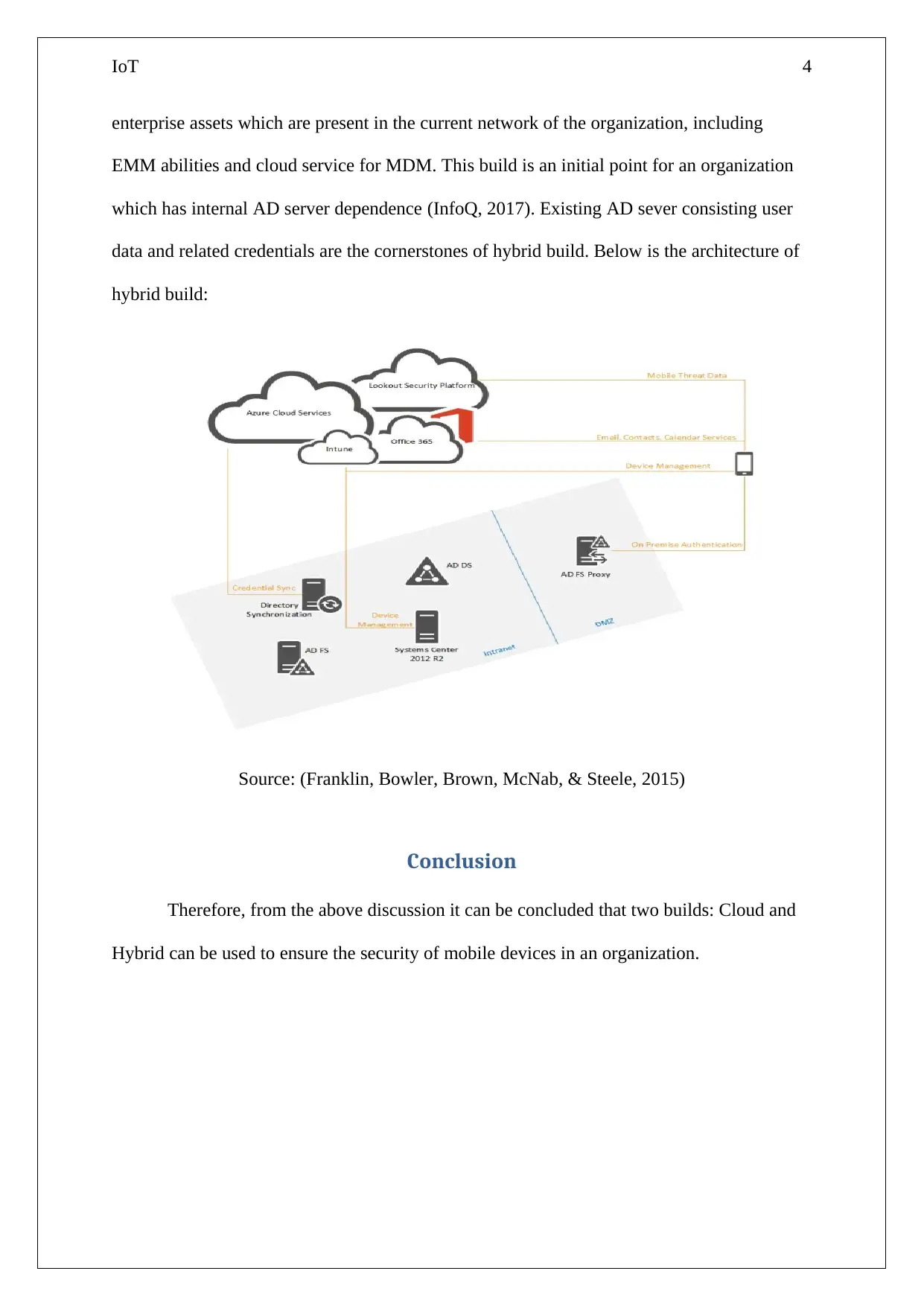
This report explores the security challenges and architectural considerations for mobile devices within the Internet of Things (IoT) ecosystem. It addresses management's concerns regarding the detailed documentation of IoT implementation, particularly in the context of asset tracking systems. The report examines key components of an IoT architecture, including generic sensing and actuating devices, IoT applications for data transformation, cloud/server infrastructure for data storage and processing, and gateway capabilities for data acquisition and communication. It further discusses two primary architectural models for securing mobile devices: cloud-based and hybrid. The cloud build architecture leverages cloud services for easy implementation and management, while the hybrid build architecture integrates cloud services with existing on-premises infrastructure, particularly Active Directory (AD) servers. The report concludes that both cloud and hybrid architectures offer viable solutions for ensuring the security of mobile devices within an organization's IoT environment.
1 out of 6












![[object Object]](/_next/static/media/star-bottom.7253800d.svg)