ITC571 Emerging Tech & Innovations: IoT Cyber-Attack Prevention
VerifiedAdded on 2023/06/14
|24
|6375
|312
Annotated Bibliography
AI Summary
This annotated bibliography explores cyber-attack detection and prevention systems for IoT networks, focusing on the significance of securing IoT devices due to their widespread use. It discusses the originality of approaches, reviews literature on federated architectures and online sequential learning accelerators, and identifies research gaps related to increasing security implications. The aim is to analyze and detect cyber security attacks, with a qualitative research approach using secondary data from books and journals. The methodology emphasizes the importance of up-to-date information and comparison of expert perspectives. The research deliverables include documented outcomes, author reviews, work breakdown structure, and test cases for system accuracy. The work breakdown structure outlines the project plan for completing the research within the specified timescale.

Full Name
Student ID
Subject ITC571 – Emerging Technology and Innovations
Assignment No Annotated Bibliography
Due Date 20-April-2018
Lecturer’s Name
CYBER-ATTACKS DETECTION AND PREVENTION SYSTEMS FOR IOT NETWORKS
Your Name
Your Email
Student ID
Subject ITC571 – Emerging Technology and Innovations
Assignment No Annotated Bibliography
Due Date 20-April-2018
Lecturer’s Name
CYBER-ATTACKS DETECTION AND PREVENTION SYSTEMS FOR IOT NETWORKS
Your Name
Your Email
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Abstract
The particular technology is used over different areas as a solution of various problems like- IOT in Smart
homes, IOT in Smart Cities, IOT in Healthcare, IOT is smart retailing etc. Along with various benefits, it
also consists of some security issues that must be kept into consideration while talking about the use of IOT
devices. The proposed research is very much significant and interesting because today IOT is using in each
home and office in order to reduce human efforts and enhance the rate of productivity so its security is very
much important to consider as any of the issue in this can affect the overall working schedule of its users.
SDN based solution is provided under the research to detect the anonymous traffic over the network so that
it can be reported and blocked instantly. IOT is becoming the basic need of every individual and utilized in
different areas so its security architecture and requirements needs to be properly formulated in highly
efficient manner. A federated architecture approach is introduced under the research to manage and
maintain the security of internet of things. It is found that the proposed design architecture is highly able to
exchange data and devoted to deploy a federated identity based environment along with dynamic context
information. Protocol description and security management is still needs to be consider as per the usage of
crypto engines.
Key Words— Natural hazards, large flood events, flood risk assessment metrics, flood hazards
The particular technology is used over different areas as a solution of various problems like- IOT in Smart
homes, IOT in Smart Cities, IOT in Healthcare, IOT is smart retailing etc. Along with various benefits, it
also consists of some security issues that must be kept into consideration while talking about the use of IOT
devices. The proposed research is very much significant and interesting because today IOT is using in each
home and office in order to reduce human efforts and enhance the rate of productivity so its security is very
much important to consider as any of the issue in this can affect the overall working schedule of its users.
SDN based solution is provided under the research to detect the anonymous traffic over the network so that
it can be reported and blocked instantly. IOT is becoming the basic need of every individual and utilized in
different areas so its security architecture and requirements needs to be properly formulated in highly
efficient manner. A federated architecture approach is introduced under the research to manage and
maintain the security of internet of things. It is found that the proposed design architecture is highly able to
exchange data and devoted to deploy a federated identity based environment along with dynamic context
information. Protocol description and security management is still needs to be consider as per the usage of
crypto engines.
Key Words— Natural hazards, large flood events, flood risk assessment metrics, flood hazards

I. INTRODUCTION
Internet of Things is one of the technologies that is using at almost every area to reduce human efforts over
performing any of the task. IOT connects people with the things that are further connected with sensors or
software. IOT is changing the world and helping in making it digital. Each person can access its services
even sitting their homes with the help of strong internet connection as now IOT smoothen the life of each
individual. The particular technology is used over different areas as a solution of various problems like-
IOT in Smart homes, IOT in Smart Cities, IOT in Healthcare, IOT is smart retailing etc. Along with various
benefits, it also consists of some security issues that must be kept into consideration while talking about the
use of IOT devices. The following research is made to analyze, detect and prevent cyber-attacks over IOT
networks. SDN (Software Defined Networking) based solution is proposed under the research in order to
detection and prevents the cyber security issues over IOT networks in order to prevent its users from
various security implications (Lee, 2017).
Section 1: Significance of the research
The selected research area is very much important to consider because it consists of large number of users
all around the world and any of the security issue in-between IOT device can affect large number of
community people. The proposed research is very much significant and interesting because today IOT is
using in each home and office in order to reduce human efforts and enhance the rate of productivity so its
security is very much important to consider as any of the issue in this can affect the overall working
schedule of its users.
Internet of Things is one of the technologies that is using at almost every area to reduce human efforts over
performing any of the task. IOT connects people with the things that are further connected with sensors or
software. IOT is changing the world and helping in making it digital. Each person can access its services
even sitting their homes with the help of strong internet connection as now IOT smoothen the life of each
individual. The particular technology is used over different areas as a solution of various problems like-
IOT in Smart homes, IOT in Smart Cities, IOT in Healthcare, IOT is smart retailing etc. Along with various
benefits, it also consists of some security issues that must be kept into consideration while talking about the
use of IOT devices. The following research is made to analyze, detect and prevent cyber-attacks over IOT
networks. SDN (Software Defined Networking) based solution is proposed under the research in order to
detection and prevents the cyber security issues over IOT networks in order to prevent its users from
various security implications (Lee, 2017).
Section 1: Significance of the research
The selected research area is very much important to consider because it consists of large number of users
all around the world and any of the security issue in-between IOT device can affect large number of
community people. The proposed research is very much significant and interesting because today IOT is
using in each home and office in order to reduce human efforts and enhance the rate of productivity so its
security is very much important to consider as any of the issue in this can affect the overall working
schedule of its users.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Section 2: How original is the approach?
The selected research area is very much important to consider because it consists of large number of users
all around the world and any of the security issue in-between IOT device can affect large number of
community people. The proposed research is very much significant and interesting because today IOT is
using in each home and office in order to reduce human efforts and enhance the rate of productivity so its
security is very much important to consider as any of the issue in this can affect the overall working
schedule of its users (Joseph Muniz, 2018).
Section 3-4: Literature review in the area what you are working
Internet of Things works as a connector that is responsible for connecting different things with each other
with the help of sensors, software and internet connection. IOT is becoming the basic need of every
individual and utilized in different areas so its security architecture and requirements needs to be properly
formulated in highly efficient manner. A federated architecture approach is introduced under the research to
manage and maintain the security of internet of things. It is found that the proposed design architecture is
highly able to exchange data and devoted to deploy a federated identity based environment along with
dynamic context information. Protocol description and security management is still needs to be consider as
per the usage of crypto engines (Martin C. Libicki, 2015).
IOT is deploying in different buildings and homes and its deployment results in high level of comfort
ability along with high rate of energy efficiency but along with such positive points it also consists of
various cyber-attacks and issues like- network intrusions through linked IOT devices. Traditional software
based security systems are not beneficial over here due to low latency and power requirements for securing
The selected research area is very much important to consider because it consists of large number of users
all around the world and any of the security issue in-between IOT device can affect large number of
community people. The proposed research is very much significant and interesting because today IOT is
using in each home and office in order to reduce human efforts and enhance the rate of productivity so its
security is very much important to consider as any of the issue in this can affect the overall working
schedule of its users (Joseph Muniz, 2018).
Section 3-4: Literature review in the area what you are working
Internet of Things works as a connector that is responsible for connecting different things with each other
with the help of sensors, software and internet connection. IOT is becoming the basic need of every
individual and utilized in different areas so its security architecture and requirements needs to be properly
formulated in highly efficient manner. A federated architecture approach is introduced under the research to
manage and maintain the security of internet of things. It is found that the proposed design architecture is
highly able to exchange data and devoted to deploy a federated identity based environment along with
dynamic context information. Protocol description and security management is still needs to be consider as
per the usage of crypto engines (Martin C. Libicki, 2015).
IOT is deploying in different buildings and homes and its deployment results in high level of comfort
ability along with high rate of energy efficiency but along with such positive points it also consists of
various cyber-attacks and issues like- network intrusions through linked IOT devices. Traditional software
based security systems are not beneficial over here due to low latency and power requirements for securing
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

IOT network. Online sequential learning accelerator is proposed under the research for detecting the
intrusion over IOT networks which measure low and fast power NIDS based on the design of software and
hardware along with sequential learning to adopt new threats. Some of the future work is still pending like-
investigation of detection speed with deeper neural networks and consideration of memory constraints for
more energy efficiency and accuracy (C. Analide, 2017).
Internet of Things inter-connects smart homes, buildings and cities along with connecting things
with mobile and computer devices. IOT also connects gas, electric grids, automobiles, airplanes and water
networks. IOT based security framework is introduced under the research for the smart cyber
infrastructures. A general threat model is also proposed under the research that will help in getting proper
protection from various cyber-attacks. It is found that ABA-IDS (Anomaly Behavior Analysis- Intrusion
Detection System) can help in detecting and classifying wide range of attacks over IOT sensors.
Internet of things can be said as the networking of various physical devices. IOT consists of large
number of users all around the world so its various security measurements are important to consider. The
research is made on examining the growth rate of IOT based Ransom ware in order to detect and control it
by making use of commands and blacklisting technique. Ransom ware attacks statistics are also analyzed
under the report to understand the requirements more effectively. The proposed model observes the traffic
over TCP/IP (Transmission control protocol / Internet protocol) with the help of Web Proxy server and then
extraction is made for the header of TCP/IP (C. Analide, 2017).
Section 5: Research gap
With the increased use of internet of things in regular life of individuals, various security implications are
occurring over it. IOT devices are becoming the target of various cyber-attacks and it becomes necessary to
overcome all those risks before their occurrence because IOT is using by almost 76% percent users all
around the world and any of the issue in it can affect large amount of its users all around the world. SDN
intrusion over IOT networks which measure low and fast power NIDS based on the design of software and
hardware along with sequential learning to adopt new threats. Some of the future work is still pending like-
investigation of detection speed with deeper neural networks and consideration of memory constraints for
more energy efficiency and accuracy (C. Analide, 2017).
Internet of Things inter-connects smart homes, buildings and cities along with connecting things
with mobile and computer devices. IOT also connects gas, electric grids, automobiles, airplanes and water
networks. IOT based security framework is introduced under the research for the smart cyber
infrastructures. A general threat model is also proposed under the research that will help in getting proper
protection from various cyber-attacks. It is found that ABA-IDS (Anomaly Behavior Analysis- Intrusion
Detection System) can help in detecting and classifying wide range of attacks over IOT sensors.
Internet of things can be said as the networking of various physical devices. IOT consists of large
number of users all around the world so its various security measurements are important to consider. The
research is made on examining the growth rate of IOT based Ransom ware in order to detect and control it
by making use of commands and blacklisting technique. Ransom ware attacks statistics are also analyzed
under the report to understand the requirements more effectively. The proposed model observes the traffic
over TCP/IP (Transmission control protocol / Internet protocol) with the help of Web Proxy server and then
extraction is made for the header of TCP/IP (C. Analide, 2017).
Section 5: Research gap
With the increased use of internet of things in regular life of individuals, various security implications are
occurring over it. IOT devices are becoming the target of various cyber-attacks and it becomes necessary to
overcome all those risks before their occurrence because IOT is using by almost 76% percent users all
around the world and any of the issue in it can affect large amount of its users all around the world. SDN

(Software Defined Networking) approach is used under the research to data an information that resides and
stores under IOT devices that makes use of software, sensors or internet connection (Lee, 2017).
Section 6: Aim of your research
The aim of overall research is to analyze the number of cyber security attacks over IOT networks in order
to detect them to prevent the users of IOT from its various security issues. The objective is to make the
technology more secure for its users all around the world as there are 75% of users which are utilizing the
benefits of IOT in different areas and in different modes (Nik Bessis, 2012).
II. MATERIAL & METHODS
This research seeks to establish answers and solutions to the challenge of cyber-attacks over IOT networks.
In order to meets its objectives, the research thus seeks to establish a system that can be used to prevent
cyber-attacks on internet of things network systems. Following the nature of this research, qualitative
research approach will be deployed in finding and meting the aims and objectives of the research question.
The nature of this research is such that it needs to explore into depth cyber-attack problems in internet of
things network systems. An extensive comprehension of the nature of the attacks and thereby making
proposals on the probable solutions is thus deemed fit and most accurate way of going about this research.
Secondary data would be appropriate for this research. Secondary data is data that was collected and
organized by another individual other than the user. Sources of secondary data include information from
books, peer reviewed journals and publications. There is a lot of information, guidelines and proposals
made by preceding scholars and experts in the field of information technology that if are properly reviewed
would prove useful in establishing the solutions to cyber-attacks on internet of things systems. A benefit
that comes with secondary data is the availability of a lot of preliminary work done and the data is normally
in very organized forms for example printed or electronic formats making it easy to extract the required
stores under IOT devices that makes use of software, sensors or internet connection (Lee, 2017).
Section 6: Aim of your research
The aim of overall research is to analyze the number of cyber security attacks over IOT networks in order
to detect them to prevent the users of IOT from its various security issues. The objective is to make the
technology more secure for its users all around the world as there are 75% of users which are utilizing the
benefits of IOT in different areas and in different modes (Nik Bessis, 2012).
II. MATERIAL & METHODS
This research seeks to establish answers and solutions to the challenge of cyber-attacks over IOT networks.
In order to meets its objectives, the research thus seeks to establish a system that can be used to prevent
cyber-attacks on internet of things network systems. Following the nature of this research, qualitative
research approach will be deployed in finding and meting the aims and objectives of the research question.
The nature of this research is such that it needs to explore into depth cyber-attack problems in internet of
things network systems. An extensive comprehension of the nature of the attacks and thereby making
proposals on the probable solutions is thus deemed fit and most accurate way of going about this research.
Secondary data would be appropriate for this research. Secondary data is data that was collected and
organized by another individual other than the user. Sources of secondary data include information from
books, peer reviewed journals and publications. There is a lot of information, guidelines and proposals
made by preceding scholars and experts in the field of information technology that if are properly reviewed
would prove useful in establishing the solutions to cyber-attacks on internet of things systems. A benefit
that comes with secondary data is the availability of a lot of preliminary work done and the data is normally
in very organized forms for example printed or electronic formats making it easy to extract the required
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

information. Accessibility of this data is as well less of a challenge as the data be availed to the public
knowledge through the use of the various forms of the media.
As a result of the exposure of information from secondary sources to the public, it attracts higher
legitimacy levels and can be used to verify primary data. Through the unlimited range of information
available from the various sources of secondary data, making comparison is highly enhanced. It will thus
be possible for the researcher to compare information and perspectives of the various experts. In so doing, a
solid and concrete solution to the research question will be established. While extracting data from the
secondary sources, it will be of essence to ensure that the most relevant and up to date information
considered. In as much as there might be a lot of information available from various scholars and
researchers that would be helpful in answering the research question, the most up to date data tend to be
more useful as they address the issues that exist in the contemporary society.
knowledge through the use of the various forms of the media.
As a result of the exposure of information from secondary sources to the public, it attracts higher
legitimacy levels and can be used to verify primary data. Through the unlimited range of information
available from the various sources of secondary data, making comparison is highly enhanced. It will thus
be possible for the researcher to compare information and perspectives of the various experts. In so doing, a
solid and concrete solution to the research question will be established. While extracting data from the
secondary sources, it will be of essence to ensure that the most relevant and up to date information
considered. In as much as there might be a lot of information available from various scholars and
researchers that would be helpful in answering the research question, the most up to date data tend to be
more useful as they address the issues that exist in the contemporary society.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

8
EMERGING TECHNOLOGIES AND INNOVATIONS
DISCUSSION
RESEARCH PROPOSAL
A. Deliverables
Following are the deliverables of proposed research proposal that needs to be put under the
lights-
The documents regarding expected outcomes will be delivered at the end of the research.
Reviews of different authors will be documented properly for the purpose of effective
delivery.
Work breakdown structure will be delivered in order to verify that the results are
delivered or time or not.
The test cases are prepared in order to verify the accuracy of the system and then
documented properly (Brooks, 2017).
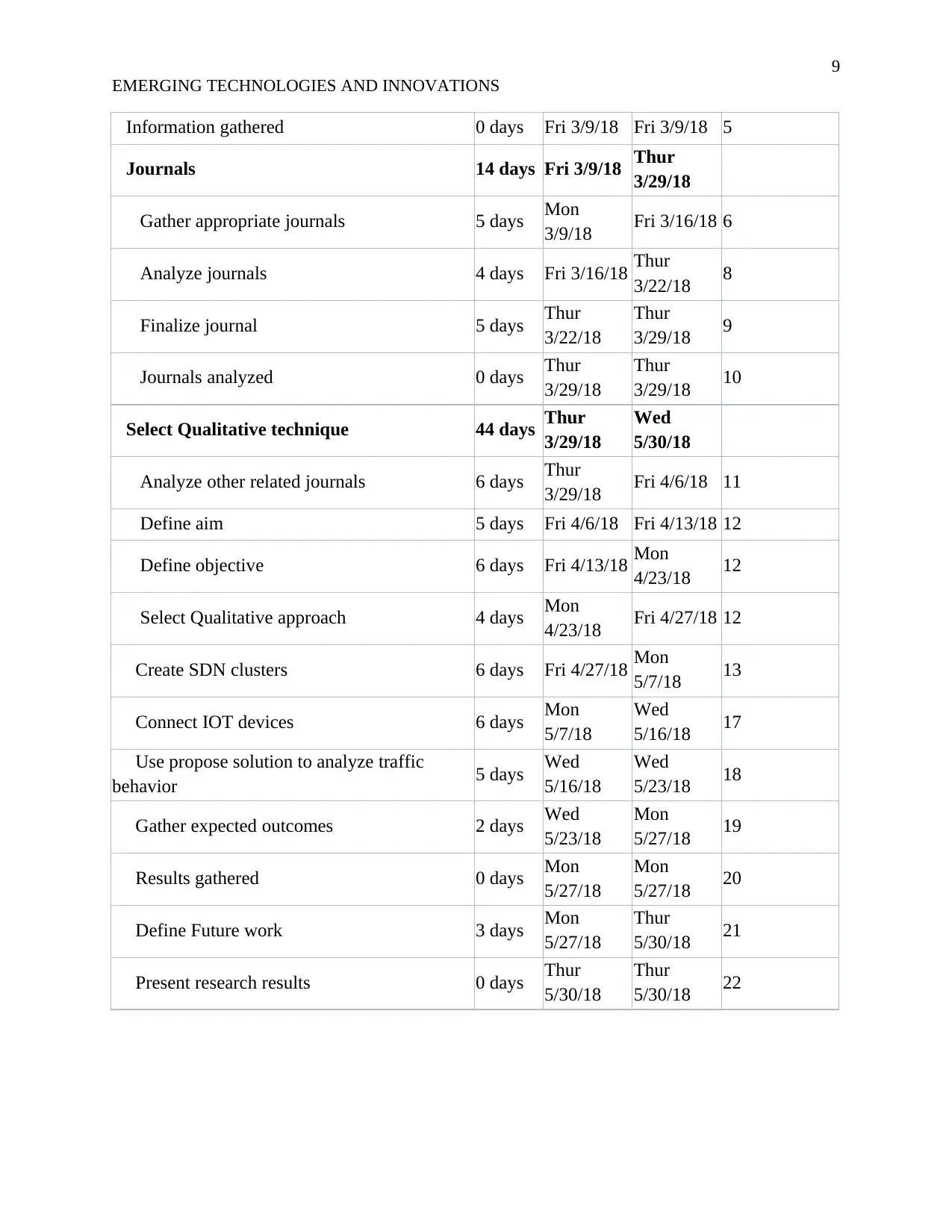
B. Work Breakdown Structure
Following figure consists of work breakdown structure that is designed to complete the
project within the specified timescale. It’s like a project plan that needs to be followed properly
in order to get the resultant outcome at the end of the research.
Task Name Duration Start Finish Predecessors
Cyber-attacks detection and prevention
systems for IOT networks 77 days Mon
2/26/18
Wed
5/30/18
Information collection 13 days Thu
2/26/18 Fri 3/9/18
Gather required info 5 days Mon
2/26/18 Fri 3/2/18
Gather facts 4 days Fri 3/2/18 Tue 3/6/18 3
Prepare Research question 4 days Tue 3/6/18 Fri 3/9/18 4
EMERGING TECHNOLOGIES AND INNOVATIONS
DISCUSSION
RESEARCH PROPOSAL
A. Deliverables
Following are the deliverables of proposed research proposal that needs to be put under the
lights-
The documents regarding expected outcomes will be delivered at the end of the research.
Reviews of different authors will be documented properly for the purpose of effective
delivery.
Work breakdown structure will be delivered in order to verify that the results are
delivered or time or not.
The test cases are prepared in order to verify the accuracy of the system and then
documented properly (Brooks, 2017).
B. Work Breakdown Structure
Following figure consists of work breakdown structure that is designed to complete the
project within the specified timescale. It’s like a project plan that needs to be followed properly
in order to get the resultant outcome at the end of the research.
Task Name Duration Start Finish Predecessors
Cyber-attacks detection and prevention
systems for IOT networks 77 days Mon
2/26/18
Wed
5/30/18
Information collection 13 days Thu
2/26/18 Fri 3/9/18
Gather required info 5 days Mon
2/26/18 Fri 3/2/18
Gather facts 4 days Fri 3/2/18 Tue 3/6/18 3
Prepare Research question 4 days Tue 3/6/18 Fri 3/9/18 4
9
EMERGING TECHNOLOGIES AND INNOVATIONS
Information gathered 0 days Fri 3/9/18 Fri 3/9/18 5
Journals 14 days Fri 3/9/18 Thur
3/29/18
Gather appropriate journals 5 days Mon
3/9/18 Fri 3/16/18 6
Analyze journals 4 days Fri 3/16/18 Thur
3/22/18 8
Finalize journal 5 days Thur
3/22/18
Thur
3/29/18 9
Journals analyzed 0 days Thur
3/29/18
Thur
3/29/18 10
Select Qualitative technique 44 days Thur
3/29/18
Wed
5/30/18
Analyze other related journals 6 days Thur
3/29/18 Fri 4/6/18 11
Define aim 5 days Fri 4/6/18 Fri 4/13/18 12
Define objective 6 days Fri 4/13/18 Mon
4/23/18 12
Select Qualitative approach 4 days Mon
4/23/18 Fri 4/27/18 12
Create SDN clusters 6 days Fri 4/27/18 Mon
5/7/18 13
Connect IOT devices 6 days Mon
5/7/18
Wed
5/16/18 17
Use propose solution to analyze traffic
behavior 5 days Wed
5/16/18
Wed
5/23/18 18
Gather expected outcomes 2 days Wed
5/23/18
Mon
5/27/18 19
Results gathered 0 days Mon
5/27/18
Mon
5/27/18 20
Define Future work 3 days Mon
5/27/18
Thur
5/30/18 21
Present research results 0 days Thur
5/30/18
Thur
5/30/18 22
EMERGING TECHNOLOGIES AND INNOVATIONS
Information gathered 0 days Fri 3/9/18 Fri 3/9/18 5
Journals 14 days Fri 3/9/18 Thur
3/29/18
Gather appropriate journals 5 days Mon
3/9/18 Fri 3/16/18 6
Analyze journals 4 days Fri 3/16/18 Thur
3/22/18 8
Finalize journal 5 days Thur
3/22/18
Thur
3/29/18 9
Journals analyzed 0 days Thur
3/29/18
Thur
3/29/18 10
Select Qualitative technique 44 days Thur
3/29/18
Wed
5/30/18
Analyze other related journals 6 days Thur
3/29/18 Fri 4/6/18 11
Define aim 5 days Fri 4/6/18 Fri 4/13/18 12
Define objective 6 days Fri 4/13/18 Mon
4/23/18 12
Select Qualitative approach 4 days Mon
4/23/18 Fri 4/27/18 12
Create SDN clusters 6 days Fri 4/27/18 Mon
5/7/18 13
Connect IOT devices 6 days Mon
5/7/18
Wed
5/16/18 17
Use propose solution to analyze traffic
behavior 5 days Wed
5/16/18
Wed
5/23/18 18
Gather expected outcomes 2 days Wed
5/23/18
Mon
5/27/18 19
Results gathered 0 days Mon
5/27/18
Mon
5/27/18 20
Define Future work 3 days Mon
5/27/18
Thur
5/30/18 21
Present research results 0 days Thur
5/30/18
Thur
5/30/18 22
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

10
EMERGING TECHNOLOGIES AND INNOVATIONS
C. Risk analysis
Risk of time can occur if the research and its sub-modules will not get completed within
the provided time constraints so each module needs to be completed within the time
limits.
Risk of content quality can occur if the used content will be copied from other sources or
of no use and meaning so the quality of the content must be insured firstly (Ayala, 2016).
Risk of end result can occur if the resultant outcome of the research will not match with
the expected outcome decided at the time of designing the research plan so each module
must be matched with the planned module and it’s working (Isafiade, 2016).
D. Duration
The overall project will get completed within the specified time duration of 77 days and
ensures the quality of the research. The overall research is started on (22/03/2018) and will get
completed on (07/06/2018).
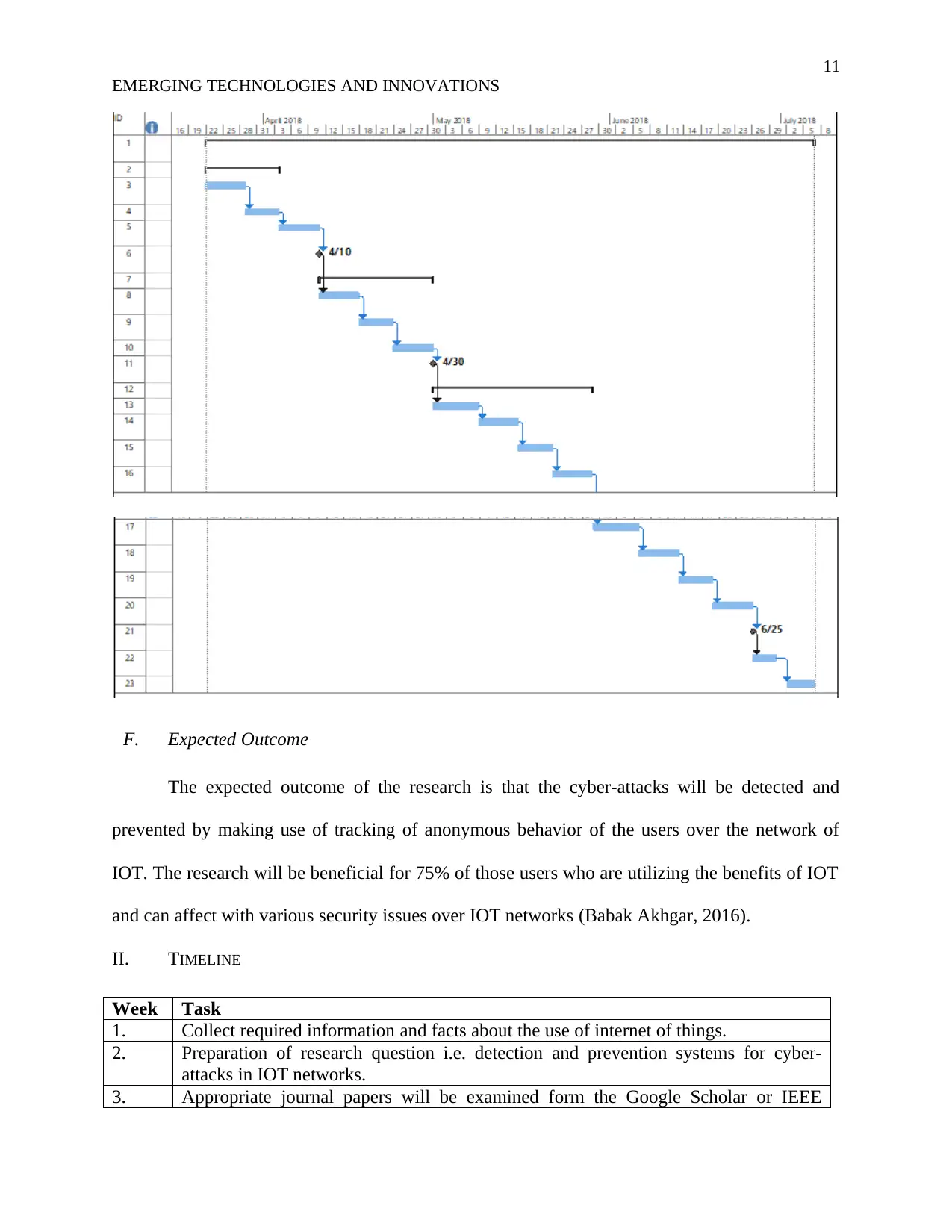
E. Gantt Chart
Following Gantt chart is the graphical representation of above mentioned work break
down structure which will help the research team to carry out their research in most effective
manner.
EMERGING TECHNOLOGIES AND INNOVATIONS
C. Risk analysis
Risk of time can occur if the research and its sub-modules will not get completed within
the provided time constraints so each module needs to be completed within the time
limits.
Risk of content quality can occur if the used content will be copied from other sources or
of no use and meaning so the quality of the content must be insured firstly (Ayala, 2016).
Risk of end result can occur if the resultant outcome of the research will not match with
the expected outcome decided at the time of designing the research plan so each module
must be matched with the planned module and it’s working (Isafiade, 2016).
D. Duration
The overall project will get completed within the specified time duration of 77 days and
ensures the quality of the research. The overall research is started on (22/03/2018) and will get
completed on (07/06/2018).
E. Gantt Chart
Following Gantt chart is the graphical representation of above mentioned work break
down structure which will help the research team to carry out their research in most effective
manner.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
11
EMERGING TECHNOLOGIES AND INNOVATIONS
F. Expected Outcome
The expected outcome of the research is that the cyber-attacks will be detected and
prevented by making use of tracking of anonymous behavior of the users over the network of
IOT. The research will be beneficial for 75% of those users who are utilizing the benefits of IOT
and can affect with various security issues over IOT networks (Babak Akhgar, 2016).
II. TIMELINE
Week Task
1. Collect required information and facts about the use of internet of things.
2. Preparation of research question i.e. detection and prevention systems for cyber-
attacks in IOT networks.
3. Appropriate journal papers will be examined form the Google Scholar or IEEE
EMERGING TECHNOLOGIES AND INNOVATIONS
F. Expected Outcome
The expected outcome of the research is that the cyber-attacks will be detected and
prevented by making use of tracking of anonymous behavior of the users over the network of
IOT. The research will be beneficial for 75% of those users who are utilizing the benefits of IOT
and can affect with various security issues over IOT networks (Babak Akhgar, 2016).
II. TIMELINE
Week Task
1. Collect required information and facts about the use of internet of things.
2. Preparation of research question i.e. detection and prevention systems for cyber-
attacks in IOT networks.
3. Appropriate journal papers will be examined form the Google Scholar or IEEE

12
EMERGING TECHNOLOGIES AND INNOVATIONS
explore.
4. Qualitative technique is utilized to carry on the research in well effective manner.
5. Five journal papers are examined properly in order to understand their findings and
research gap.
6. Aim and objective of the research will found and documented properly so that the
resultant outcomes can be as per the decided ones.
7. Qualitative approach will be used to carry forward the research in most efficient
manner.
8. SDN clusters will be made in order to proceed the proposed solution (Martin C.
Libicki, 2015).
9. The SDN clusters will be directed by the Master SDN cluster as Master SDN Cluster
will be responsible for the overall working of the proposed solution.
10. The IOT devices will be connect with SDN switches of each of the cluster.
11. Then anonymous traffic behavior will be detected with the help of proposed solution.
12. Then expected outcomes, future work and overall result of the research will be
documented properly.
CONCLUSION
The above research is made to propose a technique, method of system that can help in
detecting and protecting the cyber-security issues over IOT networks for the people who are
utilizing IOT in their daily life for getting essence in their day-to-day work. SDN based solution
is provided under the research to detect the anonymous traffic over the network so that it can be
reported and blocked instantly (Benny Mandler, 2016).
Annotated Bibliography
Ayala, L. (2016). Cybersecurity for Hospitals and Healthcare Facilities: A Guide to Detection
and Prevention. Alhambra: Apress.
Ayala's book provides insight into how to detect and avoid hacking of the medical equipment in
the hospitals and other healthcare facilities. This is following reports emerging that hackers are
of late, striking hospitals using ramsonware, which further block the staff from gaining access to
the patient records and scheduling appointments. These criminals end up asking for very hefty
EMERGING TECHNOLOGIES AND INNOVATIONS
explore.
4. Qualitative technique is utilized to carry on the research in well effective manner.
5. Five journal papers are examined properly in order to understand their findings and
research gap.
6. Aim and objective of the research will found and documented properly so that the
resultant outcomes can be as per the decided ones.
7. Qualitative approach will be used to carry forward the research in most efficient
manner.
8. SDN clusters will be made in order to proceed the proposed solution (Martin C.
Libicki, 2015).
9. The SDN clusters will be directed by the Master SDN cluster as Master SDN Cluster
will be responsible for the overall working of the proposed solution.
10. The IOT devices will be connect with SDN switches of each of the cluster.
11. Then anonymous traffic behavior will be detected with the help of proposed solution.
12. Then expected outcomes, future work and overall result of the research will be
documented properly.
CONCLUSION
The above research is made to propose a technique, method of system that can help in
detecting and protecting the cyber-security issues over IOT networks for the people who are
utilizing IOT in their daily life for getting essence in their day-to-day work. SDN based solution
is provided under the research to detect the anonymous traffic over the network so that it can be
reported and blocked instantly (Benny Mandler, 2016).
Annotated Bibliography
Ayala, L. (2016). Cybersecurity for Hospitals and Healthcare Facilities: A Guide to Detection
and Prevention. Alhambra: Apress.
Ayala's book provides insight into how to detect and avoid hacking of the medical equipment in
the hospitals and other healthcare facilities. This is following reports emerging that hackers are
of late, striking hospitals using ramsonware, which further block the staff from gaining access to
the patient records and scheduling appointments. These criminals end up asking for very hefty
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 24
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2025 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.




