IoT Assignment: Cables, Privacy, Modes, and Nielsen's Law
VerifiedAdded on 2020/02/24
|10
|1739
|52
Homework Assignment
AI Summary
This assignment explores various facets of the Internet of Things (IoT). It begins by discussing the concept of a 'no user interface' and its implications for security. It then delves into the specifications and categories of different types of cables used in IoT, including twisted pair, coaxial, and fiber optic cables, along with their advantages, disadvantages, and applications. The assignment also includes a summarized table of advantages, disadvantages, and applications of various IoT devices such as sensors, RFID tags, and video tracking. Furthermore, it addresses privacy and security issues related to IoT company products, emphasizing the importance of data minimization and security testing. It also explains blocking mode and publish/subscribe paradigms. Finally, it touches upon Nielsen's Law and its implications for IoT, discussing the expected growth of user bandwidth and sensor technology.

Running Head: INTERNET OF THINGS
INTERNET OF THINGS
Name of the Student
Name of the University
INTERNET OF THINGS
Name of the Student
Name of the University
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1INTERNET OF THINGS
Table of Contents
Question 1............................................................................................................................2
Question 2............................................................................................................................3
Question 3............................................................................................................................5
Question 4............................................................................................................................7
Question 5............................................................................................................................7
Question 6............................................................................................................................9
References..........................................................................................................................10
Table of Contents
Question 1............................................................................................................................2
Question 2............................................................................................................................3
Question 3............................................................................................................................5
Question 4............................................................................................................................7
Question 5............................................................................................................................7
Question 6............................................................................................................................9
References..........................................................................................................................10

2INTERNET OF THINGS
Assignment 2
Question 1
The statement “The best interface for the system is no user interface” can be ideally
related to the elimination of the interface that are directly related to the users. This technique is
initially done during the implementation of the aspects of technology by eliminating the user
interface. The main role is played by the security system of the organization as well as for the
benefit of the citizens. The most crucial is to identify the challenges regarding the security
system of the organization, ensuring the availability and continuity prospective along with the
provision of the services that are already been or will be served by the Internet of Things. The
main purpose is to avoid the interruptions and operations that are associated with potential
failure.
This kind of approaches can be used for elimination of various processes during the
interfacing schedule. The non-user interface can be directly beneficial as there are fewer steps
involved in the process and this may result in decreasing the time related aspects are well. The
concept can be justified by the following example:
Example 1: RFID code readers and backend servers have the communication channels
which has been assumed from the previous cases studies. However there are some problems
which has been considered as potential risk in the field of concern for the transactions in the field
of ATM. Thus the implementation of the RFID in this field has been found to be helpful in terms
of future perspective (Mulani & Pingle, 2016).
Example 2: By taking an example of a remote control device that has been installed in
mobile phone like an app by which the car can be accessed from anywhere near or far. This
Assignment 2
Question 1
The statement “The best interface for the system is no user interface” can be ideally
related to the elimination of the interface that are directly related to the users. This technique is
initially done during the implementation of the aspects of technology by eliminating the user
interface. The main role is played by the security system of the organization as well as for the
benefit of the citizens. The most crucial is to identify the challenges regarding the security
system of the organization, ensuring the availability and continuity prospective along with the
provision of the services that are already been or will be served by the Internet of Things. The
main purpose is to avoid the interruptions and operations that are associated with potential
failure.
This kind of approaches can be used for elimination of various processes during the
interfacing schedule. The non-user interface can be directly beneficial as there are fewer steps
involved in the process and this may result in decreasing the time related aspects are well. The
concept can be justified by the following example:
Example 1: RFID code readers and backend servers have the communication channels
which has been assumed from the previous cases studies. However there are some problems
which has been considered as potential risk in the field of concern for the transactions in the field
of ATM. Thus the implementation of the RFID in this field has been found to be helpful in terms
of future perspective (Mulani & Pingle, 2016).
Example 2: By taking an example of a remote control device that has been installed in
mobile phone like an app by which the car can be accessed from anywhere near or far. This
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
3INTERNET OF THINGS
Android app can be installed by the user, which has to be downloaded first and then accessed by
user name and password and other security steps.
Question 2
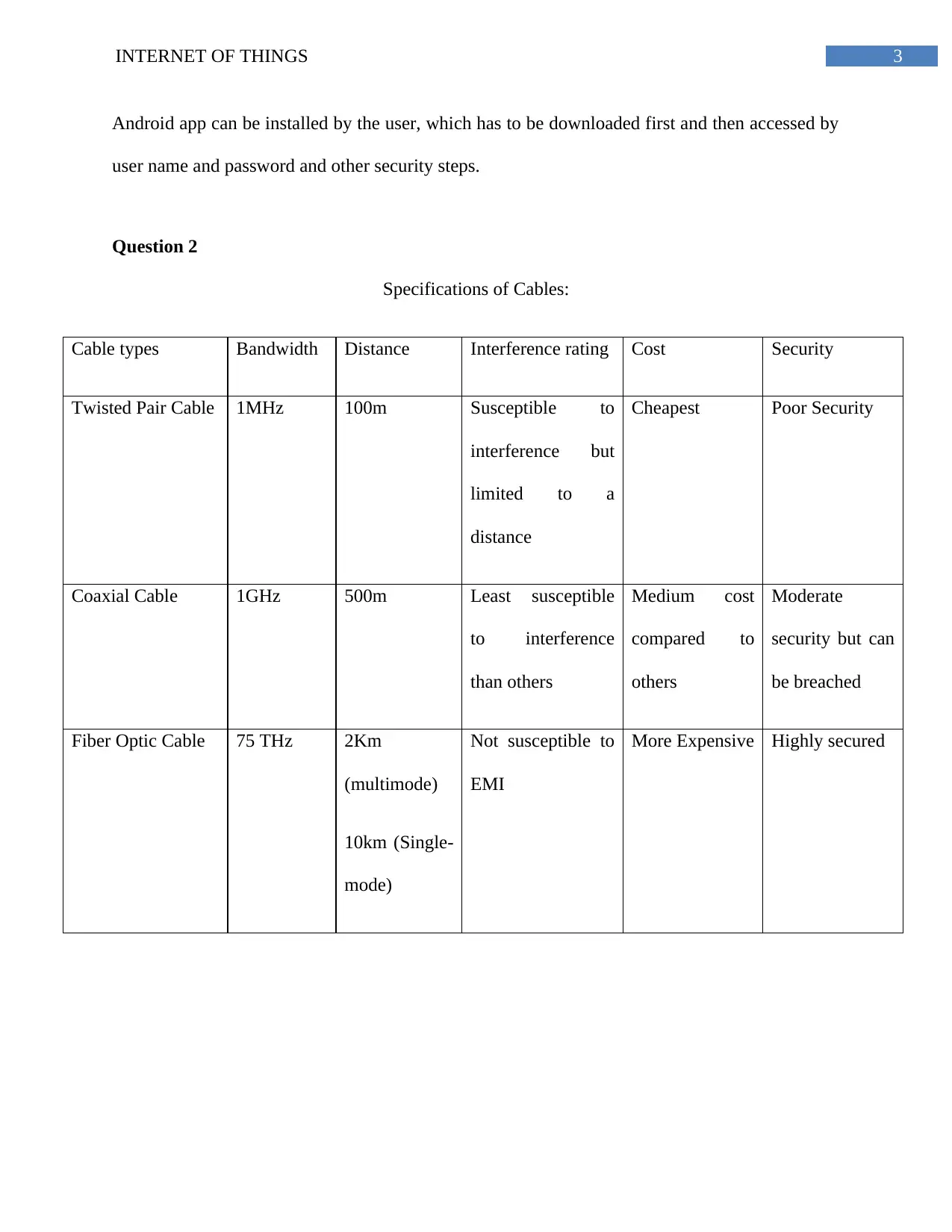
Specifications of Cables:
Cable types Bandwidth Distance Interference rating Cost Security
Twisted Pair Cable 1MHz 100m Susceptible to
interference but
limited to a
distance
Cheapest Poor Security
Coaxial Cable 1GHz 500m Least susceptible
to interference
than others
Medium cost
compared to
others
Moderate
security but can
be breached
Fiber Optic Cable 75 THz 2Km
(multimode)
10km (Single-
mode)
Not susceptible to
EMI
More Expensive Highly secured
Android app can be installed by the user, which has to be downloaded first and then accessed by
user name and password and other security steps.
Question 2
Specifications of Cables:
Cable types Bandwidth Distance Interference rating Cost Security
Twisted Pair Cable 1MHz 100m Susceptible to
interference but
limited to a
distance
Cheapest Poor Security
Coaxial Cable 1GHz 500m Least susceptible
to interference
than others
Medium cost
compared to
others
Moderate
security but can
be breached
Fiber Optic Cable 75 THz 2Km
(multimode)
10km (Single-
mode)
Not susceptible to
EMI
More Expensive Highly secured
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
4INTERNET OF THINGS
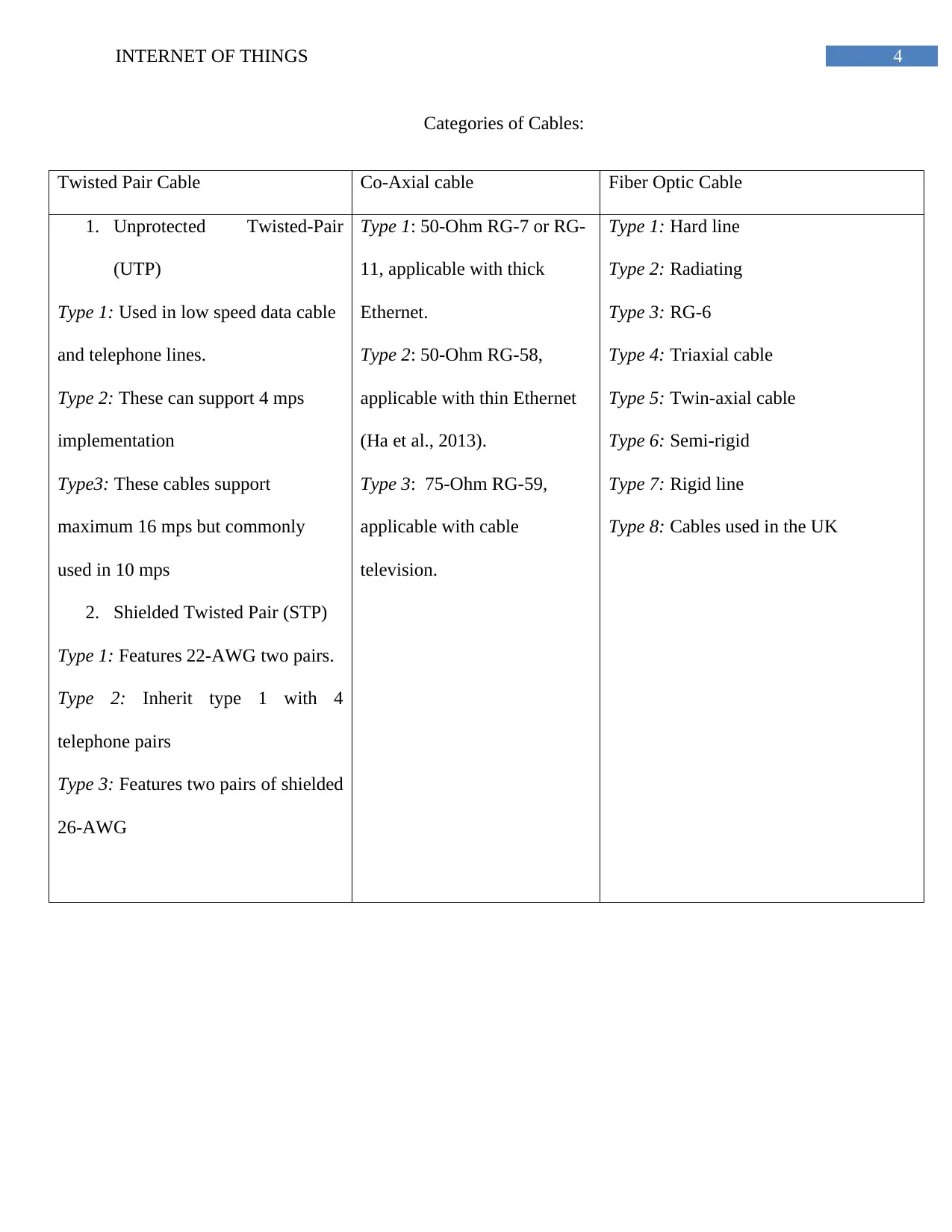
Categories of Cables:
Twisted Pair Cable Co-Axial cable Fiber Optic Cable
1. Unprotected Twisted-Pair
(UTP)
Type 1: Used in low speed data cable
and telephone lines.
Type 2: These can support 4 mps
implementation
Type3: These cables support
maximum 16 mps but commonly
used in 10 mps
2. Shielded Twisted Pair (STP)
Type 1: Features 22-AWG two pairs.
Type 2: Inherit type 1 with 4
telephone pairs
Type 3: Features two pairs of shielded
26-AWG
Type 1: 50-Ohm RG-7 or RG-
11, applicable with thick
Ethernet.
Type 2: 50-Ohm RG-58,
applicable with thin Ethernet
(Ha et al., 2013).
Type 3: 75-Ohm RG-59,
applicable with cable
television.
Type 1: Hard line
Type 2: Radiating
Type 3: RG-6
Type 4: Triaxial cable
Type 5: Twin-axial cable
Type 6: Semi-rigid
Type 7: Rigid line
Type 8: Cables used in the UK
Categories of Cables:
Twisted Pair Cable Co-Axial cable Fiber Optic Cable
1. Unprotected Twisted-Pair
(UTP)
Type 1: Used in low speed data cable
and telephone lines.
Type 2: These can support 4 mps
implementation
Type3: These cables support
maximum 16 mps but commonly
used in 10 mps
2. Shielded Twisted Pair (STP)
Type 1: Features 22-AWG two pairs.
Type 2: Inherit type 1 with 4
telephone pairs
Type 3: Features two pairs of shielded
26-AWG
Type 1: 50-Ohm RG-7 or RG-
11, applicable with thick
Ethernet.
Type 2: 50-Ohm RG-58,
applicable with thin Ethernet
(Ha et al., 2013).
Type 3: 75-Ohm RG-59,
applicable with cable
television.
Type 1: Hard line
Type 2: Radiating
Type 3: RG-6
Type 4: Triaxial cable
Type 5: Twin-axial cable
Type 6: Semi-rigid
Type 7: Rigid line
Type 8: Cables used in the UK
5INTERNET OF THINGS
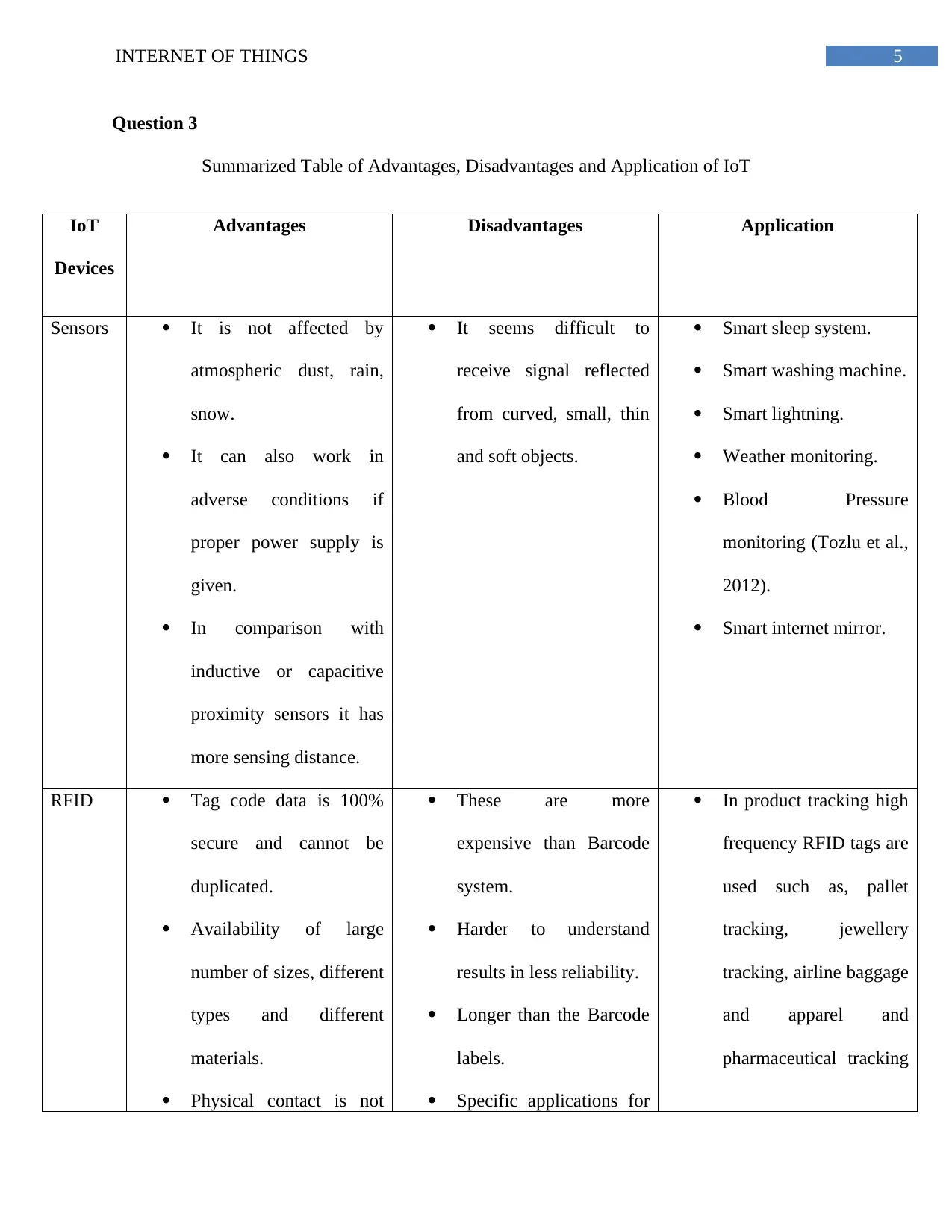
Question 3
Summarized Table of Advantages, Disadvantages and Application of IoT
IoT
Devices
Advantages Disadvantages Application
Sensors It is not affected by
atmospheric dust, rain,
snow.
It can also work in
adverse conditions if
proper power supply is
given.
In comparison with
inductive or capacitive
proximity sensors it has
more sensing distance.
It seems difficult to
receive signal reflected
from curved, small, thin
and soft objects.
Smart sleep system.
Smart washing machine.
Smart lightning.
Weather monitoring.
Blood Pressure
monitoring (Tozlu et al.,
2012).
Smart internet mirror.
RFID Tag code data is 100%
secure and cannot be
duplicated.
Availability of large
number of sizes, different
types and different
materials.
Physical contact is not
These are more
expensive than Barcode
system.
Harder to understand
results in less reliability.
Longer than the Barcode
labels.
Specific applications for
In product tracking high
frequency RFID tags are
used such as, pallet
tracking, jewellery
tracking, airline baggage
and apparel and
pharmaceutical tracking
Question 3
Summarized Table of Advantages, Disadvantages and Application of IoT
IoT
Devices
Advantages Disadvantages Application
Sensors It is not affected by
atmospheric dust, rain,
snow.
It can also work in
adverse conditions if
proper power supply is
given.
In comparison with
inductive or capacitive
proximity sensors it has
more sensing distance.
It seems difficult to
receive signal reflected
from curved, small, thin
and soft objects.
Smart sleep system.
Smart washing machine.
Smart lightning.
Weather monitoring.
Blood Pressure
monitoring (Tozlu et al.,
2012).
Smart internet mirror.
RFID Tag code data is 100%
secure and cannot be
duplicated.
Availability of large
number of sizes, different
types and different
materials.
Physical contact is not
These are more
expensive than Barcode
system.
Harder to understand
results in less reliability.
Longer than the Barcode
labels.
Specific applications for
In product tracking high
frequency RFID tags are
used such as, pallet
tracking, jewellery
tracking, airline baggage
and apparel and
pharmaceutical tracking
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
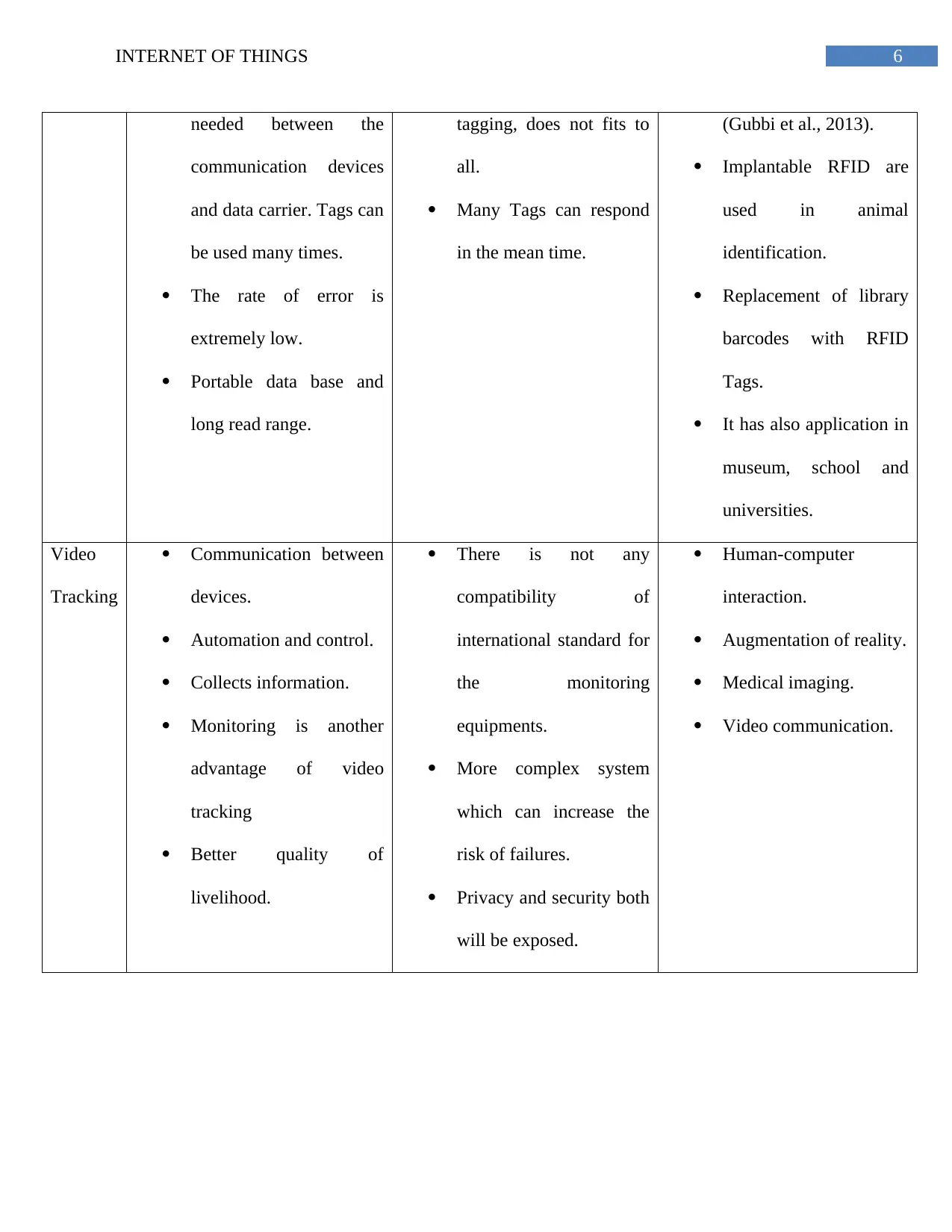
6INTERNET OF THINGS
needed between the
communication devices
and data carrier. Tags can
be used many times.
The rate of error is
extremely low.
Portable data base and
long read range.
tagging, does not fits to
all.
Many Tags can respond
in the mean time.
(Gubbi et al., 2013).
Implantable RFID are
used in animal
identification.
Replacement of library
barcodes with RFID
Tags.
It has also application in
museum, school and
universities.
Video
Tracking
Communication between
devices.
Automation and control.
Collects information.
Monitoring is another
advantage of video
tracking
Better quality of
livelihood.
There is not any
compatibility of
international standard for
the monitoring
equipments.
More complex system
which can increase the
risk of failures.
Privacy and security both
will be exposed.
Human-computer
interaction.
Augmentation of reality.
Medical imaging.
Video communication.
needed between the
communication devices
and data carrier. Tags can
be used many times.
The rate of error is
extremely low.
Portable data base and
long read range.
tagging, does not fits to
all.
Many Tags can respond
in the mean time.
(Gubbi et al., 2013).
Implantable RFID are
used in animal
identification.
Replacement of library
barcodes with RFID
Tags.
It has also application in
museum, school and
universities.
Video
Tracking
Communication between
devices.
Automation and control.
Collects information.
Monitoring is another
advantage of video
tracking
Better quality of
livelihood.
There is not any
compatibility of
international standard for
the monitoring
equipments.
More complex system
which can increase the
risk of failures.
Privacy and security both
will be exposed.
Human-computer
interaction.
Augmentation of reality.
Medical imaging.
Video communication.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7INTERNET OF THINGS
Question 4
The privacy and security issues regarding IoT company products there are few things that should
be kept in company’s consideration. 1) Considering an assessment of privacy and security; 2) the
data collection and retain must be minimized; 3) the security measure must be tested before the
launch of the product (Kranz, 2016). Hence the company should build security into the devices at
the outset. The companies should train the employees good security service that can be provided
and retain the service provided which are capable of maintaining a secure service provider.
Question 5
Blocking Mode: In this mode, the operational request generated the end point would have
to wait in the order to get respond of its request made after the initialization of the end point
operation and its completion which involves long or may be termed as waiting point with respect
to the originator asynchronous massage would be received by the originator since it is a
synchronous.
Publish/Subscribe Paradigm: This refers to as the pub/sub which enables the
communication in order of unidirectional between the publishers with regards to the one
subscriber.
Question 4
The privacy and security issues regarding IoT company products there are few things that should
be kept in company’s consideration. 1) Considering an assessment of privacy and security; 2) the
data collection and retain must be minimized; 3) the security measure must be tested before the
launch of the product (Kranz, 2016). Hence the company should build security into the devices at
the outset. The companies should train the employees good security service that can be provided
and retain the service provided which are capable of maintaining a secure service provider.
Question 5
Blocking Mode: In this mode, the operational request generated the end point would have
to wait in the order to get respond of its request made after the initialization of the end point
operation and its completion which involves long or may be termed as waiting point with respect
to the originator asynchronous massage would be received by the originator since it is a
synchronous.
Publish/Subscribe Paradigm: This refers to as the pub/sub which enables the
communication in order of unidirectional between the publishers with regards to the one
subscriber.
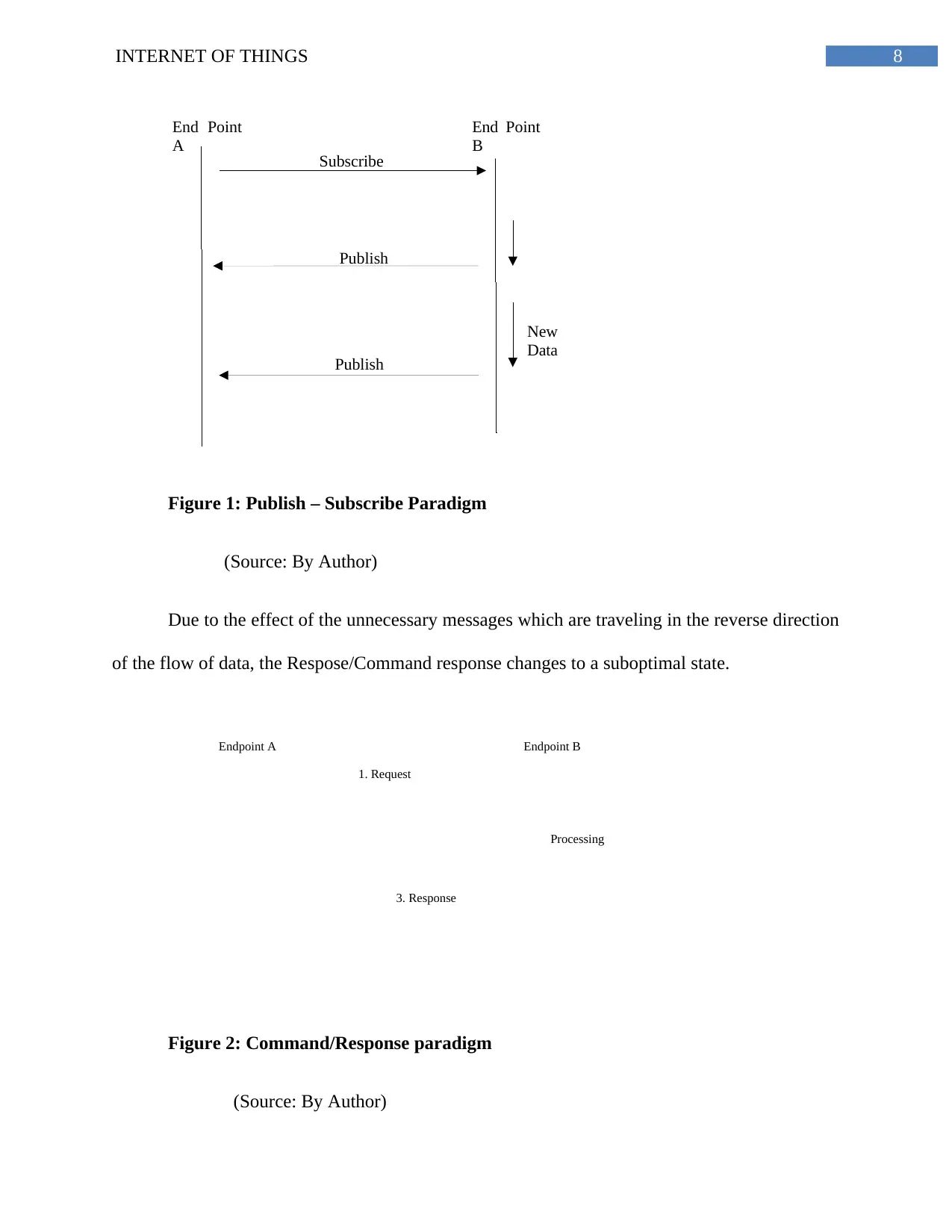
8INTERNET OF THINGS
Publish
Publish
Subscribe
End Point
B
End Point
A
New
Data
Endpoint A Endpoint B
1. Request
3. Response
Processing
Figure 1: Publish – Subscribe Paradigm
(Source: By Author)
Due to the effect of the unnecessary messages which are traveling in the reverse direction
of the flow of data, the Respose/Command response changes to a suboptimal state.
Figure 2: Command/Response paradigm
(Source: By Author)
Publish
Publish
Subscribe
End Point
B
End Point
A
New
Data
Endpoint A Endpoint B
1. Request
3. Response
Processing
Figure 1: Publish – Subscribe Paradigm
(Source: By Author)
Due to the effect of the unnecessary messages which are traveling in the reverse direction
of the flow of data, the Respose/Command response changes to a suboptimal state.
Figure 2: Command/Response paradigm
(Source: By Author)
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

9INTERNET OF THINGS
Question 6
Nielson’s Law: User Bandwidth increases up to 60% every year which is less than
Moore’s Law related to speed of computer. This new law fits data from the time period of 1983
to 2016. Nielson’s Law which directly relates to internet bandwidth is states as, a high-end user’s
bandwidth connection speed grows by average 50% per year.
Nielson’s law is very similar to Moore’s law but more established than that. Moore stated
that “computer double in capabilities every 18 months”, which is related with 60% of annual
growth (Kumar et al., 2017).
Implication of Nelson’s law in IoT: In 2024, it has been expected that the use of sensor
technology will surpass through the “trillion sensor” which will help in the creation of data
streams virtually from every surrounding surfaces (Bonomi et al., 2017). Sensors will be soon
get embedded inside auto mobiles, residential houses and even in clothes. Microchips will
become a trend including body sensors or skin sensors
Question 6
Nielson’s Law: User Bandwidth increases up to 60% every year which is less than
Moore’s Law related to speed of computer. This new law fits data from the time period of 1983
to 2016. Nielson’s Law which directly relates to internet bandwidth is states as, a high-end user’s
bandwidth connection speed grows by average 50% per year.
Nielson’s law is very similar to Moore’s law but more established than that. Moore stated
that “computer double in capabilities every 18 months”, which is related with 60% of annual
growth (Kumar et al., 2017).
Implication of Nelson’s law in IoT: In 2024, it has been expected that the use of sensor
technology will surpass through the “trillion sensor” which will help in the creation of data
streams virtually from every surrounding surfaces (Bonomi et al., 2017). Sensors will be soon
get embedded inside auto mobiles, residential houses and even in clothes. Microchips will
become a trend including body sensors or skin sensors
1 out of 10
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2025 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





