Use of IoT in RFID System: A Capstone Project Plan and Proposal
VerifiedAdded on 2020/03/04
|16
|2848
|196
Project
AI Summary
This document outlines a capstone project plan and proposal investigating the integration of the Internet of Things (IoT) in Radio Frequency Identification (RFID) systems. It begins with an executive summary, rationale, and problem domain, emphasizing the need for IoT in RFID for automated identification and tracking. The project aims to explore the benefits, challenges, and ethical considerations of this integration, with a focus on a case study involving LEAPIN Digital Keys, an Australian organization. The methodology involves an online survey for data collection, following a post-positivist approach. The project plan includes detailed phases from initial research to data analysis and final thesis drafting, along with deliverables, a work breakdown structure (WBS), risk analysis, and a Gantt chart for project management. Ethical considerations, compliance requirements, and data analysis methods are also thoroughly addressed, ensuring the integrity and validity of the research. The project seeks to provide insights into the practical applications and implications of IoT in RFID systems.

Running head: USE OF IOT IN RFID SYSTEM
Use of IoT in RFID system
Name of the student:
Name of the university:
Author Note
Use of IoT in RFID system
Name of the student:
Name of the university:
Author Note
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1USE OF IOT IN RFID SYSTEM
Executive summary
The following study provides the rationale, problem domain, the purpose and justification.
Supervisor or sponsor recommendation regarding the use of IoT in RFID systems. It includes the
research questions, conceptual framework, and methods for research and system development, data
collection systems, ethical issues and data analysis.
Executive summary
The following study provides the rationale, problem domain, the purpose and justification.
Supervisor or sponsor recommendation regarding the use of IoT in RFID systems. It includes the
research questions, conceptual framework, and methods for research and system development, data
collection systems, ethical issues and data analysis.

2USE OF IOT IN RFID SYSTEM
Table of Contents
Introduction:..........................................................................................................................................4
Rationale, domain and research questions:............................................................................................4
Rationale:...........................................................................................................................................4
Problem domain:................................................................................................................................4
Purpose and justification:..................................................................................................................5
Sponsor or Supervisor recommendation:...........................................................................................5
Research Questions:...........................................................................................................................6
Conceptual or Theoretical Framework:.................................................................................................6
Methodology:.........................................................................................................................................7
Research and Systems Development method:...................................................................................8
Data collection methods:...................................................................................................................8
Ethical Issues:....................................................................................................................................8
Compliance Requirements:................................................................................................................9
Analysis of data:................................................................................................................................9
Project Plan:.......................................................................................................................................9
Deliverables:....................................................................................................................................10
WBS:................................................................................................................................................10
Risk analysis:...................................................................................................................................11
Duration:..........................................................................................................................................11
Gantt chart:......................................................................................................................................12
References:..........................................................................................................................................13
Table of Contents
Introduction:..........................................................................................................................................4
Rationale, domain and research questions:............................................................................................4
Rationale:...........................................................................................................................................4
Problem domain:................................................................................................................................4
Purpose and justification:..................................................................................................................5
Sponsor or Supervisor recommendation:...........................................................................................5
Research Questions:...........................................................................................................................6
Conceptual or Theoretical Framework:.................................................................................................6
Methodology:.........................................................................................................................................7
Research and Systems Development method:...................................................................................8
Data collection methods:...................................................................................................................8
Ethical Issues:....................................................................................................................................8
Compliance Requirements:................................................................................................................9
Analysis of data:................................................................................................................................9
Project Plan:.......................................................................................................................................9
Deliverables:....................................................................................................................................10
WBS:................................................................................................................................................10
Risk analysis:...................................................................................................................................11
Duration:..........................................................................................................................................11
Gantt chart:......................................................................................................................................12
References:..........................................................................................................................................13
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3USE OF IOT IN RFID SYSTEM
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

4USE OF IOT IN RFID SYSTEM
Introduction:
The RFID or “Radio Frequency Identification” devices are the wireless microchips that are
utilized to tag objects for the automated identification (Ip, 2014). The following study delivers the
insight of the use of IoT or “Internet of Things” in the RFID system developing an in-depth
“Capstone Project Plan and Proposal”.
The study provides the rationale, problem domain, the purpose and justification and
supervisor or sponsor recommendation. Here an online survey is discussed to be done on the
employees of LEAPIN Digital Keys, a popular organization in Australia. It also includes the
research questions, conceptual framework, and methods for research and system development, data
collection systems, ethical issues and data analysis.
Rationale, domain and research questions:
Rationale:
The IoT proponents have been pointing towards the connected home as the utmost
application. The RFID has been an automated technology aiding computers and machines for
recognizing objects, recording the metadata and controlling the individual targets via the radio waves
(Amendola et al., 2014). Through connecting the RFID reader with the Internet’s terminal, the
readers are able to identify, monitor and track the object. These objects have been tagged in real
time, automatically and globally. This is the IoT. Thus RFID has been seen as the necessity for the
IoT.
Introduction:
The RFID or “Radio Frequency Identification” devices are the wireless microchips that are
utilized to tag objects for the automated identification (Ip, 2014). The following study delivers the
insight of the use of IoT or “Internet of Things” in the RFID system developing an in-depth
“Capstone Project Plan and Proposal”.
The study provides the rationale, problem domain, the purpose and justification and
supervisor or sponsor recommendation. Here an online survey is discussed to be done on the
employees of LEAPIN Digital Keys, a popular organization in Australia. It also includes the
research questions, conceptual framework, and methods for research and system development, data
collection systems, ethical issues and data analysis.
Rationale, domain and research questions:
Rationale:
The IoT proponents have been pointing towards the connected home as the utmost
application. The RFID has been an automated technology aiding computers and machines for
recognizing objects, recording the metadata and controlling the individual targets via the radio waves
(Amendola et al., 2014). Through connecting the RFID reader with the Internet’s terminal, the
readers are able to identify, monitor and track the object. These objects have been tagged in real
time, automatically and globally. This is the IoT. Thus RFID has been seen as the necessity for the
IoT.

5USE OF IOT IN RFID SYSTEM
Problem domain:
RFID have not been managing to become pervasive enough. There have been still various
challenges arising before IoT could develop and reach the maturity. The research results till now
have been feeding into the innovations. A series of components have been available that could be
exploited useful and developed by the market (Seo et al., 2017). However there have been still
various challenges regarding how the applications of IoT would be developed and deployed on the
support of research and innovation. The issues have been technical in nature and have been not leant
regarding the interoperability, discoverability, complex integration, reliability and security (Hua et
al., 2013). Moreover, standardization has been playing a vital role here. The other challenges have
been related to acceptability of the application of the IoT by the citizens and the users.
Purpose and justification:
The maturing RFID technology along with the falling expenses and the anticipation of the
integration of IoT has been assimilated. This has been for boosting both the expansion and adoption
of the current deployments (Naskar, Basu & Sen, 2017). The RFID has been exploding in terms of
growth. The integration of RFID with the IoT has been occurring gradually. The primary thing with
the IoT has been that it has been going to occur in a particular date. It has been growing till the
people make sense of their systems more effectively (Vikram, 2016). As they undergo trail
implementations, the adoption would increase.
Sponsor or Supervisor recommendation:
The sponsors must possess a tight setting of guidelines regarding sponsorship making them
clearly available. This must enhance the proposal that never gets matched clearly. The project must
also trip up the seekers of sponsorship who have not been interested in imparting their effort for
meeting the project needs. For the proposals and the request letters received, there could be areas
Problem domain:
RFID have not been managing to become pervasive enough. There have been still various
challenges arising before IoT could develop and reach the maturity. The research results till now
have been feeding into the innovations. A series of components have been available that could be
exploited useful and developed by the market (Seo et al., 2017). However there have been still
various challenges regarding how the applications of IoT would be developed and deployed on the
support of research and innovation. The issues have been technical in nature and have been not leant
regarding the interoperability, discoverability, complex integration, reliability and security (Hua et
al., 2013). Moreover, standardization has been playing a vital role here. The other challenges have
been related to acceptability of the application of the IoT by the citizens and the users.
Purpose and justification:
The maturing RFID technology along with the falling expenses and the anticipation of the
integration of IoT has been assimilated. This has been for boosting both the expansion and adoption
of the current deployments (Naskar, Basu & Sen, 2017). The RFID has been exploding in terms of
growth. The integration of RFID with the IoT has been occurring gradually. The primary thing with
the IoT has been that it has been going to occur in a particular date. It has been growing till the
people make sense of their systems more effectively (Vikram, 2016). As they undergo trail
implementations, the adoption would increase.
Sponsor or Supervisor recommendation:
The sponsors must possess a tight setting of guidelines regarding sponsorship making them
clearly available. This must enhance the proposal that never gets matched clearly. The project must
also trip up the seekers of sponsorship who have not been interested in imparting their effort for
meeting the project needs. For the proposals and the request letters received, there could be areas
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

6USE OF IOT IN RFID SYSTEM
where it might be unclear that the project has not been prepared according to guidelines, or wrong
for the technology. The sponsorship managers must stop the reading there and send email for
resubmitting the more proper proposal customized to their needs.
Research Questions:
The research questions for the proposal should include the following:
1. What have been the barriers to implement RFID in today’s world?
2. Are there any concerns regarding the privacy of the clients?
3. Has the technology been seemed to be secure enough?
4. Has the RFID been bringing sufficient benefits?
5. Has the standardization proceeded enough?
6. Are there any doubts regarding the maturity of this technology?
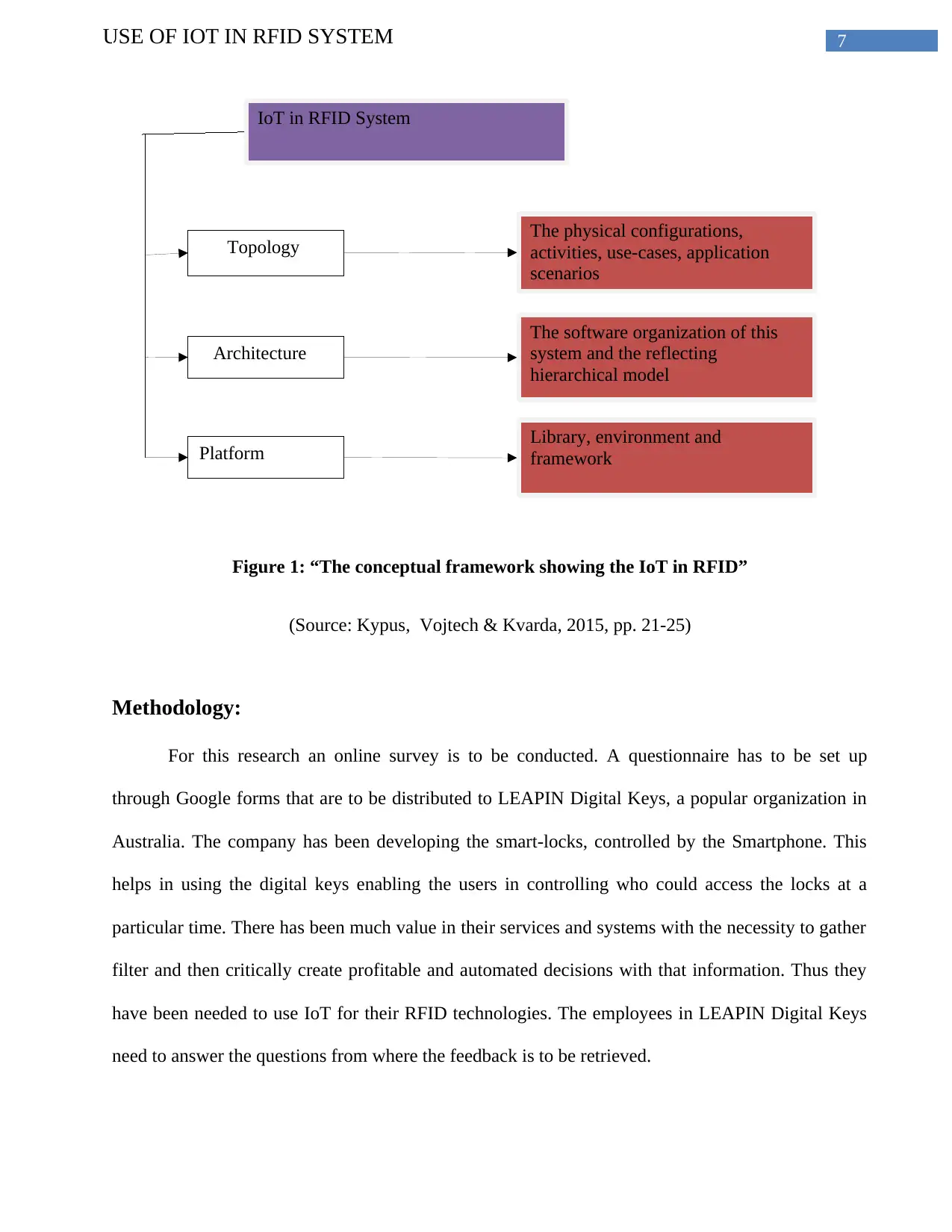
Conceptual or Theoretical Framework:
The following diagram illustrates the framework that has been joining the concepts of
implementation of IoT in RFID systems. First of all the organizations need to develop and improve
their information systems. The information system has been complemented by the RFID provided by
the IoT that has been structured in three levels. They are the topology, architecture and platform.
where it might be unclear that the project has not been prepared according to guidelines, or wrong
for the technology. The sponsorship managers must stop the reading there and send email for
resubmitting the more proper proposal customized to their needs.
Research Questions:
The research questions for the proposal should include the following:
1. What have been the barriers to implement RFID in today’s world?
2. Are there any concerns regarding the privacy of the clients?
3. Has the technology been seemed to be secure enough?
4. Has the RFID been bringing sufficient benefits?
5. Has the standardization proceeded enough?
6. Are there any doubts regarding the maturity of this technology?
Conceptual or Theoretical Framework:
The following diagram illustrates the framework that has been joining the concepts of
implementation of IoT in RFID systems. First of all the organizations need to develop and improve
their information systems. The information system has been complemented by the RFID provided by
the IoT that has been structured in three levels. They are the topology, architecture and platform.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
7USE OF IOT IN RFID SYSTEM
IoT in RFID System
Topology
Architecture
Platform
The physical configurations,
activities, use-cases, application
scenarios
The software organization of this
system and the reflecting
hierarchical model
Library, environment and
framework
Figure 1: “The conceptual framework showing the IoT in RFID”
(Source: Kypus, Vojtech & Kvarda, 2015, pp. 21-25)
Methodology:
For this research an online survey is to be conducted. A questionnaire has to be set up
through Google forms that are to be distributed to LEAPIN Digital Keys, a popular organization in
Australia. The company has been developing the smart-locks, controlled by the Smartphone. This
helps in using the digital keys enabling the users in controlling who could access the locks at a
particular time. There has been much value in their services and systems with the necessity to gather
filter and then critically create profitable and automated decisions with that information. Thus they
have been needed to use IoT for their RFID technologies. The employees in LEAPIN Digital Keys
need to answer the questions from where the feedback is to be retrieved.
IoT in RFID System
Topology
Architecture
Platform
The physical configurations,
activities, use-cases, application
scenarios
The software organization of this
system and the reflecting
hierarchical model
Library, environment and
framework
Figure 1: “The conceptual framework showing the IoT in RFID”
(Source: Kypus, Vojtech & Kvarda, 2015, pp. 21-25)
Methodology:
For this research an online survey is to be conducted. A questionnaire has to be set up
through Google forms that are to be distributed to LEAPIN Digital Keys, a popular organization in
Australia. The company has been developing the smart-locks, controlled by the Smartphone. This
helps in using the digital keys enabling the users in controlling who could access the locks at a
particular time. There has been much value in their services and systems with the necessity to gather
filter and then critically create profitable and automated decisions with that information. Thus they
have been needed to use IoT for their RFID technologies. The employees in LEAPIN Digital Keys
need to answer the questions from where the feedback is to be retrieved.

8USE OF IOT IN RFID SYSTEM
Research and Systems Development method:
The research and system development method to be followed must fall roughly under the
post-positivist school. This must include the quantitative data analysis. This would help to examine
the deductive hypothesis that is to be refined over the course of collection, analyzing and interpreting
the research data.
Data collection methods:
For the proposal the quantitative data collection method is to be followed. For this an online
questionnaire is to be created as discussed above. These data must deal with the values, numbers and
quantities. This would make them measurable. In this way they have been generally expressed in
number format. Examples of quantitative data include the duration, price amount sixe and length.
The usage of statistics for generating and then subsequently assessing the kind of data would ass
credibility and the credence to it. Hence, quantitative data has been recognized to be more objective
and reliable.
Ethical Issues:
The ethical issues must consider that any research participant must not be subjected to any
kind of harm in any manner. The respect for dignity of the research participants must be prioritized.
Complete consent must be retrieved from the participants before the study. The privacy protection of
the research participants must be ensured. Enough level of the research data confidentiality must be
assured. The anonymity of the company and the individuals in this research is to be assured. Any
deception or any kind of exaggeration regarding the objectives and aims of the research should be
avoided. The affiliations of any kind, sources of the funding and the possible conflicts of the
interests should be declared. Any type of communication regarding the research must be done with
Research and Systems Development method:
The research and system development method to be followed must fall roughly under the
post-positivist school. This must include the quantitative data analysis. This would help to examine
the deductive hypothesis that is to be refined over the course of collection, analyzing and interpreting
the research data.
Data collection methods:
For the proposal the quantitative data collection method is to be followed. For this an online
questionnaire is to be created as discussed above. These data must deal with the values, numbers and
quantities. This would make them measurable. In this way they have been generally expressed in
number format. Examples of quantitative data include the duration, price amount sixe and length.
The usage of statistics for generating and then subsequently assessing the kind of data would ass
credibility and the credence to it. Hence, quantitative data has been recognized to be more objective
and reliable.
Ethical Issues:
The ethical issues must consider that any research participant must not be subjected to any
kind of harm in any manner. The respect for dignity of the research participants must be prioritized.
Complete consent must be retrieved from the participants before the study. The privacy protection of
the research participants must be ensured. Enough level of the research data confidentiality must be
assured. The anonymity of the company and the individuals in this research is to be assured. Any
deception or any kind of exaggeration regarding the objectives and aims of the research should be
avoided. The affiliations of any kind, sources of the funding and the possible conflicts of the
interests should be declared. Any type of communication regarding the research must be done with
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

9USE OF IOT IN RFID SYSTEM
transparency and honesty. Lastly any kind of misleading information and denotation of the findings
of the primary data in biased manner should be avoided.
Compliance Requirements:
It must be kept in mind that every registration for the project has been up to date. The project
approach must be renewed as any types of feedbacks are needed to be retrieved from the particular
company. The privacy of the participants must be secured by the complying with the governmental,
state and national privacy laws. Before starting the project a legal advice is to be seeking from the
specialist advisers and the solicitors.
Analysis of data:
It has been simpler to create any online survey and distribute that to the participants.
However the analyzing of the outcomes has been a tricky job. There have been four primary
methods to gather the responses. The data types to confront while analyzing the outcomes of the
survey are ratio data, interval data, ordinal data and categorical data.
Project Plan:
The first phase of the research would be the research in the statement of the use of IoT in
RFID technology along with establishing the research methodology and completing administrative
requirements with defining few initial and general hypotheses. Next there must be technology and
literature review establishing a more in depth definition of use of IoT in RFID, the conceptual
framework and the variable affecting the analysis and the interpretation of the research problem. In
the next phase the research must generate and collect the data using the quantitative methods. Lastly
the data retrieved and gathered in the last phase must be assessed and interpreted. It must be found
out whether the operational and general hypothesis is supported or refuted. On the basis of the
transparency and honesty. Lastly any kind of misleading information and denotation of the findings
of the primary data in biased manner should be avoided.
Compliance Requirements:
It must be kept in mind that every registration for the project has been up to date. The project
approach must be renewed as any types of feedbacks are needed to be retrieved from the particular
company. The privacy of the participants must be secured by the complying with the governmental,
state and national privacy laws. Before starting the project a legal advice is to be seeking from the
specialist advisers and the solicitors.
Analysis of data:
It has been simpler to create any online survey and distribute that to the participants.
However the analyzing of the outcomes has been a tricky job. There have been four primary
methods to gather the responses. The data types to confront while analyzing the outcomes of the
survey are ratio data, interval data, ordinal data and categorical data.
Project Plan:
The first phase of the research would be the research in the statement of the use of IoT in
RFID technology along with establishing the research methodology and completing administrative
requirements with defining few initial and general hypotheses. Next there must be technology and
literature review establishing a more in depth definition of use of IoT in RFID, the conceptual
framework and the variable affecting the analysis and the interpretation of the research problem. In
the next phase the research must generate and collect the data using the quantitative methods. Lastly
the data retrieved and gathered in the last phase must be assessed and interpreted. It must be found
out whether the operational and general hypothesis is supported or refuted. On the basis of the
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

10USE OF IOT IN RFID SYSTEM
analysis the last thesis must be drafted. This should frame the research findings as some common
rules and principles.
Deliverables:
The study will obtain the clear quantification of the scopes at every part of the market and
supply chain. They must become aware of the performance of IoT in RFID, developing roadmaps
and the applicable market identity of them. IoT can use RFID for achieving the sharing and
exchange of data. This is an important means through the open network if computer systems.
The technical approaches for enhancing the RFID privacy must include the Pseudonym
rotation, Personal Simulator or Proxy for RFID, the “Blocker” Tag, Polite Blocking and
Cryptography.
The software codes include the UHF, HF, LF, 2.45GHz passive RFID and the Active RFID
Real Time Locating Systems (RTLS). Moreover the Ultra Wide Band (UWB), the Near Field
Communications (NFC), Cards, Battery Assisted Passive (BAP), Printed RFID, Chipless, RFID
Bluetooth and Zigbee should also be considered.
WBS:
Figure 2: “The required Work Breakdown Structure”
(Source: Created by Author)
analysis the last thesis must be drafted. This should frame the research findings as some common
rules and principles.
Deliverables:
The study will obtain the clear quantification of the scopes at every part of the market and
supply chain. They must become aware of the performance of IoT in RFID, developing roadmaps
and the applicable market identity of them. IoT can use RFID for achieving the sharing and
exchange of data. This is an important means through the open network if computer systems.
The technical approaches for enhancing the RFID privacy must include the Pseudonym
rotation, Personal Simulator or Proxy for RFID, the “Blocker” Tag, Polite Blocking and
Cryptography.
The software codes include the UHF, HF, LF, 2.45GHz passive RFID and the Active RFID
Real Time Locating Systems (RTLS). Moreover the Ultra Wide Band (UWB), the Near Field
Communications (NFC), Cards, Battery Assisted Passive (BAP), Printed RFID, Chipless, RFID
Bluetooth and Zigbee should also be considered.
WBS:
Figure 2: “The required Work Breakdown Structure”
(Source: Created by Author)
11USE OF IOT IN RFID SYSTEM
Risk analysis:
The risk analysis is demonstrated through the following table:
The sector of risks Possible ways to mitigate
Intelligence gathering:
This involves the gathering of data followed by
the risk assessment for identifying the assets
needed to be protected and their values.
The threats are to be defined and the adversary
types ate to be encountered.
Details of the participant:
This includes the location of the participant,
history, and other current protective measures.
A structured process is to follow undertaking
the survey from the key employees, insurance
assessors and crime prevention officers.
Site walk through, or the survey:
This involves the physical vulnerabilities,
present security measures and their conditions.
The process needs to account the people,
processes and the technologies needing the
integration to meet the aims.
Duration:
The task takes duration of about 65 days staring from the creation of survey form to
implementing the plan.
Risk analysis:
The risk analysis is demonstrated through the following table:
The sector of risks Possible ways to mitigate
Intelligence gathering:
This involves the gathering of data followed by
the risk assessment for identifying the assets
needed to be protected and their values.
The threats are to be defined and the adversary
types ate to be encountered.
Details of the participant:
This includes the location of the participant,
history, and other current protective measures.
A structured process is to follow undertaking
the survey from the key employees, insurance
assessors and crime prevention officers.
Site walk through, or the survey:
This involves the physical vulnerabilities,
present security measures and their conditions.
The process needs to account the people,
processes and the technologies needing the
integration to meet the aims.
Duration:
The task takes duration of about 65 days staring from the creation of survey form to
implementing the plan.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 16
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.




