IoT Security Application Project Blog & Progress Report, August 2017
VerifiedAdded on 2020/03/13
|7
|1215
|161
Project
AI Summary
This document presents an IoT Security Application project, encompassing a blog and a progress report. The project addresses the security challenges within IoT applications, including network security, database security, and device security. The blog section introduces the concept of IoT and its associated security risks, such as data breaches, denial-of-service attacks, and device theft. It emphasizes the need for an integrated security solution, including network monitoring, intrusion detection, access control, and anti-malware tools. The progress report details the project's milestones, including the creation of a project plan, application design, and source code development. It highlights the technical and planning issues encountered and their solutions. The references provide sources on IoT security vulnerabilities, threats, and attacks.

IoT Security Application
Project Blog & Progress Report
8/18/2017
Project Blog & Progress Report
8/18/2017
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

IoT Security Application
Table of Contents
IoT Security Application – Project Blog......................................................................................................3
Progress Report...........................................................................................................................................4
References...................................................................................................................................................7
Table of Contents
IoT Security Application – Project Blog......................................................................................................3
Progress Report...........................................................................................................................................4
References...................................................................................................................................................7

IoT Security Application
IoT Security Application – Project Blog
Internet of Things (IoT) is a discipline that involves the amalgamation of a variety of devices and
networks to achieve a common set of goals and objectives. There is an involvement of numerous
devices in the applications that are based on IoT such as computing devices, small and large
electrical appliances, and mobile devices and may more. The IoT applications are being used in
the business sectors and industries all across the globe. There are certain security issues that are
associated with these applications and solutions.
The reason behind the occurrence of the security events and occurrences is because of the
involvement of varied devices and networks in the applications. This leads to the presence of a
number of access points which allow the attackers to gain an easy entry to the application. The
security risks and threats such as network security attacks, attacks on the database of the
application and the threats to the devices are associated with these IoT applications. There are
many solutions that have been developed in order to overcome the security attacks. However, the
organizations need to integrate a number of different security solutions to resolve, detect, prevent
and control these security risks and threats (Abomhara, 2015). Some of the common issues in
association with the IoT application include the breaching of data and information. The
malicious entities find it easy to breach into the application and its components that have an
adverse impact on the privacy and confidentiality of the application information. Many of the
denial of service and flooding attacks are also executed on the application so that the availability
of the application is hampered and the customer experience that is earned on the application is
deteriorated. Many of the malware have been developed to cause damage to the information and
data that is associated with the application (Bertino, 2016). There are also many threats that are
associated with the devices that are involved in the application. These devices may get lost or the
attackers may steal the devices from the device owners to have a negative impact on the
application security.
It is necessary to come up with an integrated solution comprising of different security
mechanisms and protocols to control the security threats and attacks. IoT security application has
therefore been proposed to be developed and deployed to provide an integrated IoT security
solution. The solution will include the network security controls such as network monitoring
IoT Security Application – Project Blog
Internet of Things (IoT) is a discipline that involves the amalgamation of a variety of devices and
networks to achieve a common set of goals and objectives. There is an involvement of numerous
devices in the applications that are based on IoT such as computing devices, small and large
electrical appliances, and mobile devices and may more. The IoT applications are being used in
the business sectors and industries all across the globe. There are certain security issues that are
associated with these applications and solutions.
The reason behind the occurrence of the security events and occurrences is because of the
involvement of varied devices and networks in the applications. This leads to the presence of a
number of access points which allow the attackers to gain an easy entry to the application. The
security risks and threats such as network security attacks, attacks on the database of the
application and the threats to the devices are associated with these IoT applications. There are
many solutions that have been developed in order to overcome the security attacks. However, the
organizations need to integrate a number of different security solutions to resolve, detect, prevent
and control these security risks and threats (Abomhara, 2015). Some of the common issues in
association with the IoT application include the breaching of data and information. The
malicious entities find it easy to breach into the application and its components that have an
adverse impact on the privacy and confidentiality of the application information. Many of the
denial of service and flooding attacks are also executed on the application so that the availability
of the application is hampered and the customer experience that is earned on the application is
deteriorated. Many of the malware have been developed to cause damage to the information and
data that is associated with the application (Bertino, 2016). There are also many threats that are
associated with the devices that are involved in the application. These devices may get lost or the
attackers may steal the devices from the device owners to have a negative impact on the
application security.
It is necessary to come up with an integrated solution comprising of different security
mechanisms and protocols to control the security threats and attacks. IoT security application has
therefore been proposed to be developed and deployed to provide an integrated IoT security
solution. The solution will include the network security controls such as network monitoring
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
IoT Security Application
tools and network based intrusion detection and prevention systems. These tools will
automatically detect the activities that are carried on the networks and any attempt by the
intruders to enter the networking channels. Also, the IoT security solution must comprise of the
solutions to the database security. The advanced access control along with two-factor
authentication will be included in the application to enhance the database related security. Other
measures such as secure monitoring and control, maintenance of the logs and anti-denial and
anti-malware tools will be included in the application to provide an integrated solution. The
solution shall also have automated tracking and monitoring tools present in it. These tools will be
of great aid in case of stealing or loss of the devices (Zolanvari, 2016).
Technology is an important aspect that has provided the users all across the globe with the ability
to execute a number of operations and processes with much ease and simplicity. In case of the
IoT applications, there is a large set of transformation that has been introduced for the home and
business users. However, there are certain security issues that are associated with these tools and
applications that shall be targeted and resolved. These issues have a direct impact on the
information properties such as integrity, confidentiality and availability of the information. It
also leads to loss of the organization reputation and deterioration of the customer satisfaction
level (Marsan, 2015).
IoT security application is an initiative that has been taken in order to make sure that such
negative impacts are not resulted. It is an integrated solution that will also be extremely cost-
effective in nature. The implementation of standalone security solutions proves to be extremely
costly for the organizations. The integrated set overcome such issues and will also easily detect
and prevent the security risks and attacks in association with the IoT applications.
Progress Report
Name: Student Name
Project Title: IoT Security Application
Week No: 1 Date: 18th August
2017
Planning
Milestone Planned Actual Comment
tools and network based intrusion detection and prevention systems. These tools will
automatically detect the activities that are carried on the networks and any attempt by the
intruders to enter the networking channels. Also, the IoT security solution must comprise of the
solutions to the database security. The advanced access control along with two-factor
authentication will be included in the application to enhance the database related security. Other
measures such as secure monitoring and control, maintenance of the logs and anti-denial and
anti-malware tools will be included in the application to provide an integrated solution. The
solution shall also have automated tracking and monitoring tools present in it. These tools will be
of great aid in case of stealing or loss of the devices (Zolanvari, 2016).
Technology is an important aspect that has provided the users all across the globe with the ability
to execute a number of operations and processes with much ease and simplicity. In case of the
IoT applications, there is a large set of transformation that has been introduced for the home and
business users. However, there are certain security issues that are associated with these tools and
applications that shall be targeted and resolved. These issues have a direct impact on the
information properties such as integrity, confidentiality and availability of the information. It
also leads to loss of the organization reputation and deterioration of the customer satisfaction
level (Marsan, 2015).
IoT security application is an initiative that has been taken in order to make sure that such
negative impacts are not resulted. It is an integrated solution that will also be extremely cost-
effective in nature. The implementation of standalone security solutions proves to be extremely
costly for the organizations. The integrated set overcome such issues and will also easily detect
and prevent the security risks and attacks in association with the IoT applications.
Progress Report
Name: Student Name
Project Title: IoT Security Application
Week No: 1 Date: 18th August
2017
Planning
Milestone Planned Actual Comment
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
IoT Security Application
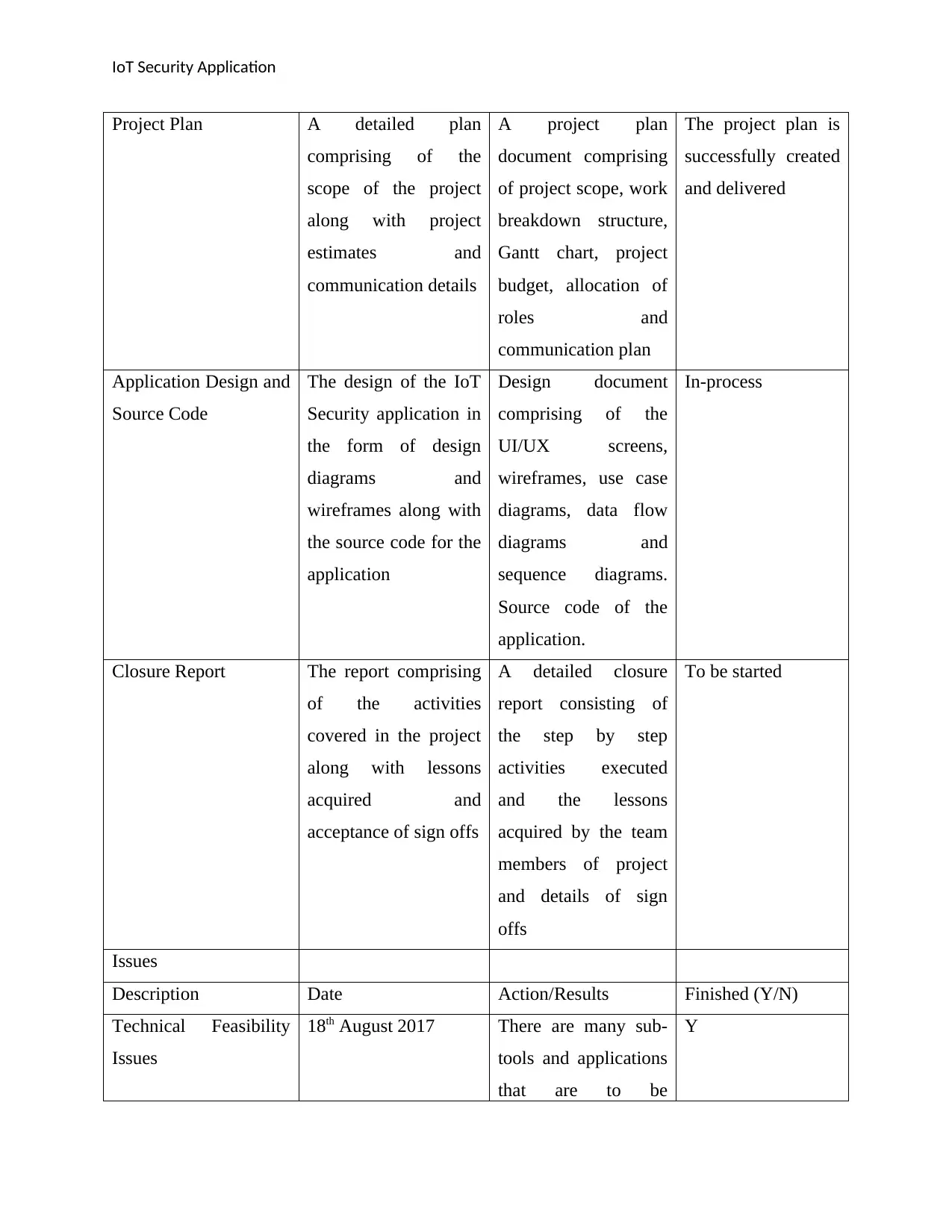
Project Plan A detailed plan
comprising of the
scope of the project
along with project
estimates and
communication details
A project plan
document comprising
of project scope, work
breakdown structure,
Gantt chart, project
budget, allocation of
roles and
communication plan
The project plan is
successfully created
and delivered
Application Design and
Source Code
The design of the IoT
Security application in
the form of design
diagrams and
wireframes along with
the source code for the
application
Design document
comprising of the
UI/UX screens,
wireframes, use case
diagrams, data flow
diagrams and
sequence diagrams.
Source code of the
application.
In-process
Closure Report The report comprising
of the activities
covered in the project
along with lessons
acquired and
acceptance of sign offs
A detailed closure
report consisting of
the step by step
activities executed
and the lessons
acquired by the team
members of project
and details of sign
offs
To be started
Issues
Description Date Action/Results Finished (Y/N)
Technical Feasibility
Issues
18th August 2017 There are many sub-
tools and applications
that are to be
Y
Project Plan A detailed plan
comprising of the
scope of the project
along with project
estimates and
communication details
A project plan
document comprising
of project scope, work
breakdown structure,
Gantt chart, project
budget, allocation of
roles and
communication plan
The project plan is
successfully created
and delivered
Application Design and
Source Code
The design of the IoT
Security application in
the form of design
diagrams and
wireframes along with
the source code for the
application
Design document
comprising of the
UI/UX screens,
wireframes, use case
diagrams, data flow
diagrams and
sequence diagrams.
Source code of the
application.
In-process
Closure Report The report comprising
of the activities
covered in the project
along with lessons
acquired and
acceptance of sign offs
A detailed closure
report consisting of
the step by step
activities executed
and the lessons
acquired by the team
members of project
and details of sign
offs
To be started
Issues
Description Date Action/Results Finished (Y/N)
Technical Feasibility
Issues
18th August 2017 There are many sub-
tools and applications
that are to be
Y
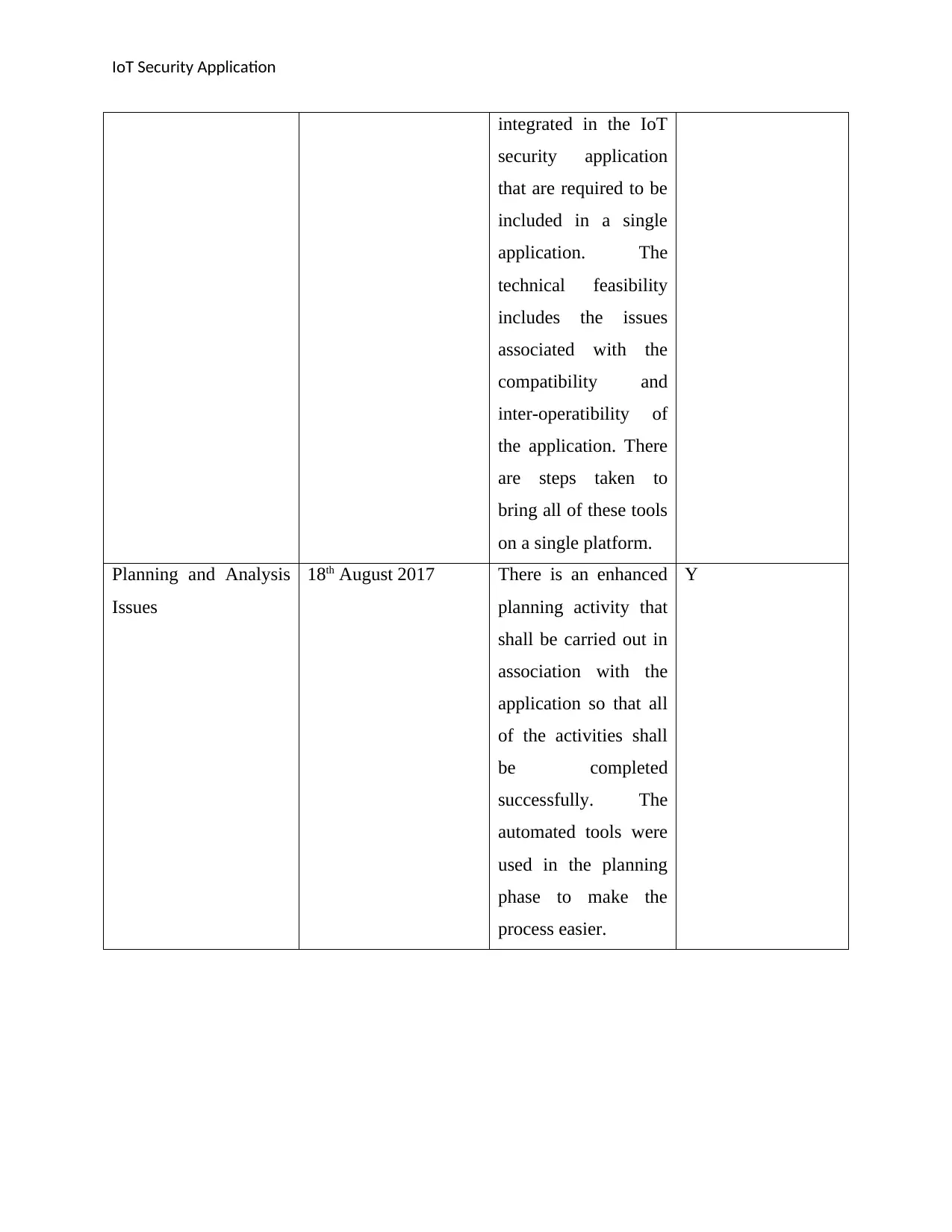
IoT Security Application
integrated in the IoT
security application
that are required to be
included in a single
application. The
technical feasibility
includes the issues
associated with the
compatibility and
inter-operatibility of
the application. There
are steps taken to
bring all of these tools
on a single platform.
Planning and Analysis
Issues
18th August 2017 There is an enhanced
planning activity that
shall be carried out in
association with the
application so that all
of the activities shall
be completed
successfully. The
automated tools were
used in the planning
phase to make the
process easier.
Y
integrated in the IoT
security application
that are required to be
included in a single
application. The
technical feasibility
includes the issues
associated with the
compatibility and
inter-operatibility of
the application. There
are steps taken to
bring all of these tools
on a single platform.
Planning and Analysis
Issues
18th August 2017 There is an enhanced
planning activity that
shall be carried out in
association with the
application so that all
of the activities shall
be completed
successfully. The
automated tools were
used in the planning
phase to make the
process easier.
Y
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

IoT Security Application
References
Abomhara, M. (2015). Cyber Security and the Internet of Things: Vulnerabilities, Threats,
Intruders and Attacks. Retrieved 18 August 2017, from
https://www.riverpublishers.com/journal/journal_articles/RP_Journal_2245-1439_414.pdf
Bertino, E. (2016). Data Security and Privacy in the IoT. Retrieved 18 August 2017, from
https://openproceedings.org/2016/conf/edbt/paper-a.pdf
Marsan, C. (2015). The Internet of Things: An Overview. Retrieved 18 August 2017, from
https://www.internetsociety.org/sites/default/files/ISOC-IoT-Overview-20151014_0.pdf
Zolanvari, M. (2016). IoT Security: A Survey. Retrieved 18 August 2017, from
https://www.cse.wustl.edu/~jain/cse570-15/ftp/iot_sec.pdf
References
Abomhara, M. (2015). Cyber Security and the Internet of Things: Vulnerabilities, Threats,
Intruders and Attacks. Retrieved 18 August 2017, from
https://www.riverpublishers.com/journal/journal_articles/RP_Journal_2245-1439_414.pdf
Bertino, E. (2016). Data Security and Privacy in the IoT. Retrieved 18 August 2017, from
https://openproceedings.org/2016/conf/edbt/paper-a.pdf
Marsan, C. (2015). The Internet of Things: An Overview. Retrieved 18 August 2017, from
https://www.internetsociety.org/sites/default/files/ISOC-IoT-Overview-20151014_0.pdf
Zolanvari, M. (2016). IoT Security: A Survey. Retrieved 18 August 2017, from
https://www.cse.wustl.edu/~jain/cse570-15/ftp/iot_sec.pdf
1 out of 7
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.




