SBM4304 - IS Security and Risk Management: IoT Security Report
VerifiedAdded on 2022/08/22
|13
|3100
|44
Report
AI Summary
This report, prepared for SBM4304 (IS Security and Risk Management) at Asia Pacific International College, delves into the critical aspects of IoT security. It begins with an overview of IoT devices, their types, and applications, emphasizing their growing importance in daily life. The report then analyzes three recent IoT attacks, including Mirai botnet and Man-in-the-middle attacks, highlighting the vulnerabilities they exploit. It provides detailed countermeasures and formal security protection techniques for smart homes and industrial IoT, covering secured boot, mutual authentication, encryption, and security monitoring. Furthermore, the report explores two authentication protocols, including authentication based on certification (DTLS) and encryption-based authentication, assessing their strengths and limitations. The report concludes by summarizing the key challenges and the need for proactive security management in the rapidly evolving IoT landscape, emphasizing the importance of addressing security and privacy concerns to ensure the continued growth and adoption of IoT technologies.

Running head: INNOVATION AND TECHNOLOGIES
Innovation and Technologies: For SBM4304 IS Security and Risk
Management
Name of Student-
Name of University-
Author’s Note-
Innovation and Technologies: For SBM4304 IS Security and Risk
Management
Name of Student-
Name of University-
Author’s Note-
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1INNOVATION AND TECHNOLOGIES
Table of Contents
IoT devices, their types and applications.........................................................................................1
Three recent attacks on IoT devices................................................................................................3
Countermeasures and formal security protection techniques against the IoT attacks.....................4
Two Authentication protocols specifies to IT devices....................................................................6
Summary..........................................................................................................................................8
References......................................................................................................................................10
Table of Contents
IoT devices, their types and applications.........................................................................................1
Three recent attacks on IoT devices................................................................................................3
Countermeasures and formal security protection techniques against the IoT attacks.....................4
Two Authentication protocols specifies to IT devices....................................................................6
Summary..........................................................................................................................................8
References......................................................................................................................................10

2INNOVATION AND TECHNOLOGIES
IoT devices, their types and applications
Internet of Things devices are being used daily by humans and they are becoming an
important part of daily lives. IoT is an extension of the internet connection to some physical
devices and with everyday objects. The devices of IoT helps to communicate with embedded
internet connectivity, electronic devices and other hardware and they can be easily controlled and
monitor remotely (Siboni et al. 2019). The characteristics of IoT device is to produce vast
amount of data. These data can be used in applications of artificial intelligence and in machine
learning. IoT can be defined as network consisting of different physical objects and people who
are denoted as things. The main goal of IoT is to extend the connectivity of internet from
standard devices to dumb devices.
The components used in IoT are:
1. Lower power systems: These are less-battery consumption that includes high
performance factor that are used in the designing of electronic system.
2. Cloud computing: Information that are collected via IoT devices includes large amount
and they are stored on a storage server that is reliable. The data is processed and they are
analyzed to find out electrical faults and errors (Chifor et al. 2018).
3. Big data availability: The devices of IoT depends on sensors and real time data. As the
electronic devices are used in every field of life the usage of these data triggers a huge amount of
big data.
4. Network connection: For communicating there is need of internet connectivity with
each devices that has an IP address. The IoT devices are named uniquely so that they can be
identified.
IoT devices, their types and applications
Internet of Things devices are being used daily by humans and they are becoming an
important part of daily lives. IoT is an extension of the internet connection to some physical
devices and with everyday objects. The devices of IoT helps to communicate with embedded
internet connectivity, electronic devices and other hardware and they can be easily controlled and
monitor remotely (Siboni et al. 2019). The characteristics of IoT device is to produce vast
amount of data. These data can be used in applications of artificial intelligence and in machine
learning. IoT can be defined as network consisting of different physical objects and people who
are denoted as things. The main goal of IoT is to extend the connectivity of internet from
standard devices to dumb devices.
The components used in IoT are:
1. Lower power systems: These are less-battery consumption that includes high
performance factor that are used in the designing of electronic system.
2. Cloud computing: Information that are collected via IoT devices includes large amount
and they are stored on a storage server that is reliable. The data is processed and they are
analyzed to find out electrical faults and errors (Chifor et al. 2018).
3. Big data availability: The devices of IoT depends on sensors and real time data. As the
electronic devices are used in every field of life the usage of these data triggers a huge amount of
big data.
4. Network connection: For communicating there is need of internet connectivity with
each devices that has an IP address. The IoT devices are named uniquely so that they can be
identified.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3INNOVATION AND TECHNOLOGIES
The applications of IoT devices are:
1. Smart Homes: These are the smart residential spaces and it can be predicted that these
SmartHomes are becoming as common devices like smartphones (D’Orazio, Choo and Yang
2016). The products of smart homes helps to save time, save energy as well as money.
2. Wearable: Wearable provides an explosive demand for marketers over world. The
devices of wearable are installed with the sensors and the software for designing such devices.
These helps to collected information about the users and process those information to have
essential insight for the users.
3. Connected cars: The vehicles has also been optimized with IoT to improve their
internal functions. The IoT has also been used in the in-car experience and the connected cars
can help to optimize the operations and maintenance of the passengers.
4. Industrial Internet: This is an industrial sector that has empowered engineering of
industries with sensors, big data and with software for creating brilliant machines. The features
and application of IoT are beautiful, investable and desirable.
5. Smart Cities: Smart city is another application of IoT that has powerfull application in
the world population. There are smart surveillance, water distribution and automated
transportation in the cities and all are connected to internet of things (Ho et al. 2016).
6. IoT in agriculture: IoT is used in agriculture as because the demand for food supply is
increasing at a high speed. Governments has played a vital role to help the farmers for using
advanced techniques and used research for increasing the production of foods.
Three recent attacks on IoT devices
The applications of IoT devices are:
1. Smart Homes: These are the smart residential spaces and it can be predicted that these
SmartHomes are becoming as common devices like smartphones (D’Orazio, Choo and Yang
2016). The products of smart homes helps to save time, save energy as well as money.
2. Wearable: Wearable provides an explosive demand for marketers over world. The
devices of wearable are installed with the sensors and the software for designing such devices.
These helps to collected information about the users and process those information to have
essential insight for the users.
3. Connected cars: The vehicles has also been optimized with IoT to improve their
internal functions. The IoT has also been used in the in-car experience and the connected cars
can help to optimize the operations and maintenance of the passengers.
4. Industrial Internet: This is an industrial sector that has empowered engineering of
industries with sensors, big data and with software for creating brilliant machines. The features
and application of IoT are beautiful, investable and desirable.
5. Smart Cities: Smart city is another application of IoT that has powerfull application in
the world population. There are smart surveillance, water distribution and automated
transportation in the cities and all are connected to internet of things (Ho et al. 2016).
6. IoT in agriculture: IoT is used in agriculture as because the demand for food supply is
increasing at a high speed. Governments has played a vital role to help the farmers for using
advanced techniques and used research for increasing the production of foods.
Three recent attacks on IoT devices
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
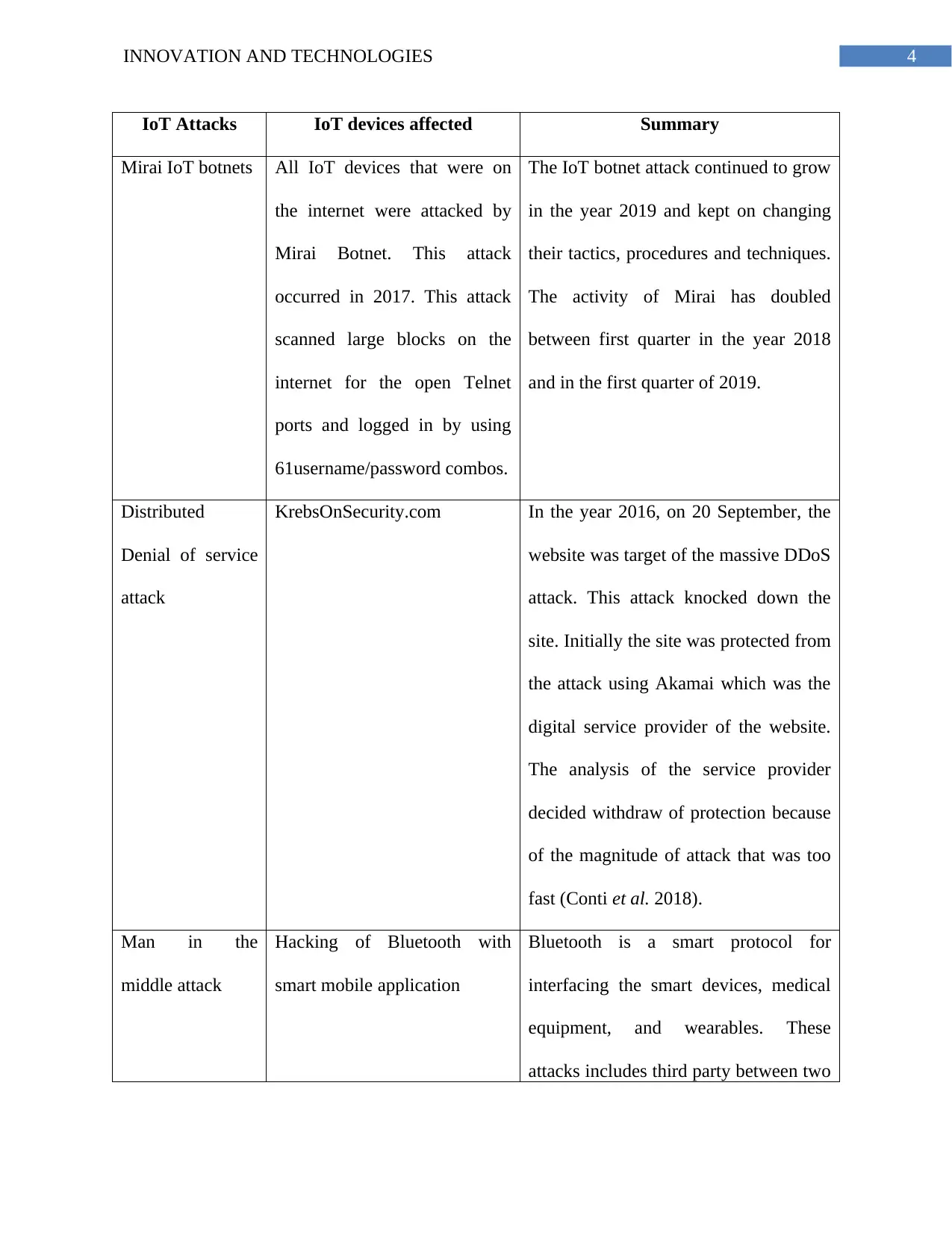
4INNOVATION AND TECHNOLOGIES
IoT Attacks IoT devices affected Summary
Mirai IoT botnets All IoT devices that were on
the internet were attacked by
Mirai Botnet. This attack
occurred in 2017. This attack
scanned large blocks on the
internet for the open Telnet
ports and logged in by using
61username/password combos.
The IoT botnet attack continued to grow
in the year 2019 and kept on changing
their tactics, procedures and techniques.
The activity of Mirai has doubled
between first quarter in the year 2018
and in the first quarter of 2019.
Distributed
Denial of service
attack
KrebsOnSecurity.com In the year 2016, on 20 September, the
website was target of the massive DDoS
attack. This attack knocked down the
site. Initially the site was protected from
the attack using Akamai which was the
digital service provider of the website.
The analysis of the service provider
decided withdraw of protection because
of the magnitude of attack that was too
fast (Conti et al. 2018).
Man in the
middle attack
Hacking of Bluetooth with
smart mobile application
Bluetooth is a smart protocol for
interfacing the smart devices, medical
equipment, and wearables. These
attacks includes third party between two
IoT Attacks IoT devices affected Summary
Mirai IoT botnets All IoT devices that were on
the internet were attacked by
Mirai Botnet. This attack
occurred in 2017. This attack
scanned large blocks on the
internet for the open Telnet
ports and logged in by using
61username/password combos.
The IoT botnet attack continued to grow
in the year 2019 and kept on changing
their tactics, procedures and techniques.
The activity of Mirai has doubled
between first quarter in the year 2018
and in the first quarter of 2019.
Distributed
Denial of service
attack
KrebsOnSecurity.com In the year 2016, on 20 September, the
website was target of the massive DDoS
attack. This attack knocked down the
site. Initially the site was protected from
the attack using Akamai which was the
digital service provider of the website.
The analysis of the service provider
decided withdraw of protection because
of the magnitude of attack that was too
fast (Conti et al. 2018).
Man in the
middle attack
Hacking of Bluetooth with
smart mobile application
Bluetooth is a smart protocol for
interfacing the smart devices, medical
equipment, and wearables. These
attacks includes third party between two

5INNOVATION AND TECHNOLOGIES
networked devices and helps to store
sensitive data that are stored. These
attacks takes place when network has no
security and has weak network.
Countermeasures and formal security protection techniques against the IoT
attacks
1. For securing the smart homes, the countermeasure that are to be taken explained
below:
Secured Boot: There are secure code signing techniques those are used in secure boot.
This helps in ensuring that the device can execute the code generated of device or some other
trusted party. Secure boots helps in preventing hackers to replace the firmware with some
malicious versions and can prevent attacks.
Mutual authentication: When a home device gets connected with a network, there
should be authentication before receiving or before transmitting the data (Bertino and Islam
2017). This helps in data originating from legitimate device and that does not includes fraudulent
source. The cryptographic algorithms actually includes symmetric keys as well as asymmetric
key s that are used for two way authentication.
Secure communication of including encryption: Protection of data in the transit
between the device and with the service infrastructure (Yang et al. 2017). Encryption helps to
ensure secure decryption helps in accessing the transmitted data.
networked devices and helps to store
sensitive data that are stored. These
attacks takes place when network has no
security and has weak network.
Countermeasures and formal security protection techniques against the IoT
attacks
1. For securing the smart homes, the countermeasure that are to be taken explained
below:
Secured Boot: There are secure code signing techniques those are used in secure boot.
This helps in ensuring that the device can execute the code generated of device or some other
trusted party. Secure boots helps in preventing hackers to replace the firmware with some
malicious versions and can prevent attacks.
Mutual authentication: When a home device gets connected with a network, there
should be authentication before receiving or before transmitting the data (Bertino and Islam
2017). This helps in data originating from legitimate device and that does not includes fraudulent
source. The cryptographic algorithms actually includes symmetric keys as well as asymmetric
key s that are used for two way authentication.
Secure communication of including encryption: Protection of data in the transit
between the device and with the service infrastructure (Yang et al. 2017). Encryption helps to
ensure secure decryption helps in accessing the transmitted data.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

6INNOVATION AND TECHNOLOGIES
Security monitoring: Capturing the data for the overall system includes endpoint
devices and includes traffic that are connected with each other. Data is analyzed for detecting the
possible security violations and includes system threats. When the attack is detected, broad range
of actions are to be formulated for the context in the security policy that are to be executed.
Secure lifecycle management: The features included in lifecycle management helps
service providers and helps in controlling the security aspects for the IoT devices when they are
in operation (Ambrosin et al. 2016). The key replacement in the cyber disaster recovery. This
ensures that there is minimal service disruption.
2. For securing the industrial IoT, the countermeasure that are to be taken are:
Include firmware integrity and secured boot: The secure boot helps to utilize the
cryptographic code with signing the techniques and helps to ensure the device for executing the
code that is generated by the device and includes some other trusted third party. But all the IIoT
chips are not equipped for the capabilities of secured boots. In such cases, it become important to
make sure that the devices can establish a communication only with authorized services.
Mutual Authentication: In the industries, when actuator connects with the network and
that should include authentication before receiving the data or transmitting them (Alaba et al.
2017). Mutual authentication helps ensuring that data originates from the legitimate device and
not from some other source. There is secure as well as mutual authentication which must prove
the identity with each other and helps to protect them against some malicious attacks.
End to end encryption: There are secured communication capabilities that helps to
protect the data that comes between the device and the service infrastructure. Device encryption
helps in ensuring that with secret decryption the transmitted data can be accessed.
Security monitoring: Capturing the data for the overall system includes endpoint
devices and includes traffic that are connected with each other. Data is analyzed for detecting the
possible security violations and includes system threats. When the attack is detected, broad range
of actions are to be formulated for the context in the security policy that are to be executed.
Secure lifecycle management: The features included in lifecycle management helps
service providers and helps in controlling the security aspects for the IoT devices when they are
in operation (Ambrosin et al. 2016). The key replacement in the cyber disaster recovery. This
ensures that there is minimal service disruption.
2. For securing the industrial IoT, the countermeasure that are to be taken are:
Include firmware integrity and secured boot: The secure boot helps to utilize the
cryptographic code with signing the techniques and helps to ensure the device for executing the
code that is generated by the device and includes some other trusted third party. But all the IIoT
chips are not equipped for the capabilities of secured boots. In such cases, it become important to
make sure that the devices can establish a communication only with authorized services.
Mutual Authentication: In the industries, when actuator connects with the network and
that should include authentication before receiving the data or transmitting them (Alaba et al.
2017). Mutual authentication helps ensuring that data originates from the legitimate device and
not from some other source. There is secure as well as mutual authentication which must prove
the identity with each other and helps to protect them against some malicious attacks.
End to end encryption: There are secured communication capabilities that helps to
protect the data that comes between the device and the service infrastructure. Device encryption
helps in ensuring that with secret decryption the transmitted data can be accessed.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7INNOVATION AND TECHNOLOGIES
Security analysis and monitoring: There should be security monitoring that helps to
capture the data for the overall state in industries that includes endpoints devices and includes
connectivity traffic (Taylor, Reilly and Lempereur 2017). The data are then analyzed for
detecting the possible with security violations and includes potential threats for system. After
detection, there should be wide range of actions for the overall systems to include security
policy.
Two Authentication protocols specifies to IT devices
Two authentication protocols included in IT devices includes:
1. Authentication based on Certification: The protocol of DTLS (Datagram Transport
Layer Security) is existing standard. Two way protocol for authenticating security scheme for the
IoT are based on the DTLS and basically use RSA asymmetric encryption and also includes
X.509 certification. Certification includes electronic document that is used for identifying some
individual, server, the company and the other entities that are included for devices that used. The
certificate includes recognized proof that states the personal identity of the person. The scheme
of authentication with certification includes eight handshake algorithm that helps to establish the
session (Chifor et al. 2019). For implementing this particular scheme, there should be a higher
cost of consumption and should include large storage space that are required for constraining the
resources from the sensing devices.
The authentication protocol that is used in IoT devices includes certificate that are
distributed in different IoT environments. There is an ECC (Elliptic Curve Cryptography) that
helps in consuming less computing resources that are related to the RSA algorithm. This protocol
helps to consume less resources computing that are associated with the IoT environments (Li, Da
Security analysis and monitoring: There should be security monitoring that helps to
capture the data for the overall state in industries that includes endpoints devices and includes
connectivity traffic (Taylor, Reilly and Lempereur 2017). The data are then analyzed for
detecting the possible with security violations and includes potential threats for system. After
detection, there should be wide range of actions for the overall systems to include security
policy.
Two Authentication protocols specifies to IT devices
Two authentication protocols included in IT devices includes:
1. Authentication based on Certification: The protocol of DTLS (Datagram Transport
Layer Security) is existing standard. Two way protocol for authenticating security scheme for the
IoT are based on the DTLS and basically use RSA asymmetric encryption and also includes
X.509 certification. Certification includes electronic document that is used for identifying some
individual, server, the company and the other entities that are included for devices that used. The
certificate includes recognized proof that states the personal identity of the person. The scheme
of authentication with certification includes eight handshake algorithm that helps to establish the
session (Chifor et al. 2019). For implementing this particular scheme, there should be a higher
cost of consumption and should include large storage space that are required for constraining the
resources from the sensing devices.
The authentication protocol that is used in IoT devices includes certificate that are
distributed in different IoT environments. There is an ECC (Elliptic Curve Cryptography) that
helps in consuming less computing resources that are related to the RSA algorithm. This protocol
helps to consume less resources computing that are associated with the IoT environments (Li, Da

8INNOVATION AND TECHNOLOGIES
Xu and Zhao 2018). There are certificates that helps to accomplish the authentication process
with end to end protocol. The IoT devices includes protocol that uses implicit certificates for
accomplishing authentication. There are two phases of authentication in the IoT environments.
One is registration phase, and the other is authentication phase.
2. Encryption based Authentication: This authentication includes one-time password
phase that is used for authentication for the IoT infrastructures. This protocols helps to adopt the
IBE ECC (Identity Based Elliptic Curve Cryptography) for providing lightweight for
establishing end to end authentication between the IoT devices. This would help to establish the
authentication more secured (Safkhani and Bagheri 2017). The main advantage of this protocol
includes sensing the devices that does not include extra storage that are used for storing the keys
for the scheme includes in OTP. If the devices of IoT requires frequent communication, they
should request the central cloud for generating OTP. This helps to communicate all the devices
that need to spend more time for establishing the session. The protocol that are used in the
authentication includes TCGA scheme that mainly uses a cryptography algorithm that includes
Paillier Threshold Cryptography.
3. Non-encryption based authentication: This authentication technique does not include
certification technique or any other encryption operation. This is a proposed approach that is
being used in the IoT devices that includes distributed IoT architecture (Marktscheffel et al.
2016). This particular scheme mainly uses hash functions as well as bitwise operations for
constructing lightweight mechanism of authentication. These schemes are used with sequence
numbers as well as random numbers for generating alias identity in the IoT device.
Summary
Xu and Zhao 2018). There are certificates that helps to accomplish the authentication process
with end to end protocol. The IoT devices includes protocol that uses implicit certificates for
accomplishing authentication. There are two phases of authentication in the IoT environments.
One is registration phase, and the other is authentication phase.
2. Encryption based Authentication: This authentication includes one-time password
phase that is used for authentication for the IoT infrastructures. This protocols helps to adopt the
IBE ECC (Identity Based Elliptic Curve Cryptography) for providing lightweight for
establishing end to end authentication between the IoT devices. This would help to establish the
authentication more secured (Safkhani and Bagheri 2017). The main advantage of this protocol
includes sensing the devices that does not include extra storage that are used for storing the keys
for the scheme includes in OTP. If the devices of IoT requires frequent communication, they
should request the central cloud for generating OTP. This helps to communicate all the devices
that need to spend more time for establishing the session. The protocol that are used in the
authentication includes TCGA scheme that mainly uses a cryptography algorithm that includes
Paillier Threshold Cryptography.
3. Non-encryption based authentication: This authentication technique does not include
certification technique or any other encryption operation. This is a proposed approach that is
being used in the IoT devices that includes distributed IoT architecture (Marktscheffel et al.
2016). This particular scheme mainly uses hash functions as well as bitwise operations for
constructing lightweight mechanism of authentication. These schemes are used with sequence
numbers as well as random numbers for generating alias identity in the IoT device.
Summary
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

9INNOVATION AND TECHNOLOGIES
As per the report above, there are many challenges that are faced by IoT devices and
those security is to be ensured in the IoT devices. There is security management, securing the
law and the regulation of security in the project, includes requirement analysis and many other
security approaches that are to be ensured in the IoT devices. The domain of IoT is emerging and
includes significant interest and will draw interest of many people in the coming years. Security
and the privacy of the IoT devices is the main issue and those are to be addressed in the project
(Li et al. 2017). Users face challenges in the environment in handling the security of the IoT
devices. Analyzing security solution in the IoT devices is necessary as because those devices are
to be managed properly by the users.
IoT devices needs to make network more less secure and those needed to be addressed
and connected to other devices for the secure network that does not includes IT understanding
some other set of rules in the devices network. The user needs to understand that what the IoT
device needs to be smart and interoperate with other devices that are included in the software.
The designers of the IoT devices needs to think that is the devices are not being securely
authenticated, then they will lead to data breach resulting in large amount of data. It is also stated
that is the device of IoT is in filtered, then the data that are included in the devices can be
exposed and the hacckers get the opportunity to get access to the back end application server
(Chikouche, Cayrel and Boidje 2019). This paper emphasized the main data security breach that
occurred in the last year with the IoT devices and have highlighted those issues. This report also
has discussed counter measures that can be taken or that has been taken to mitigate those issues
with IoT devices.
As per the report above, there are many challenges that are faced by IoT devices and
those security is to be ensured in the IoT devices. There is security management, securing the
law and the regulation of security in the project, includes requirement analysis and many other
security approaches that are to be ensured in the IoT devices. The domain of IoT is emerging and
includes significant interest and will draw interest of many people in the coming years. Security
and the privacy of the IoT devices is the main issue and those are to be addressed in the project
(Li et al. 2017). Users face challenges in the environment in handling the security of the IoT
devices. Analyzing security solution in the IoT devices is necessary as because those devices are
to be managed properly by the users.
IoT devices needs to make network more less secure and those needed to be addressed
and connected to other devices for the secure network that does not includes IT understanding
some other set of rules in the devices network. The user needs to understand that what the IoT
device needs to be smart and interoperate with other devices that are included in the software.
The designers of the IoT devices needs to think that is the devices are not being securely
authenticated, then they will lead to data breach resulting in large amount of data. It is also stated
that is the device of IoT is in filtered, then the data that are included in the devices can be
exposed and the hacckers get the opportunity to get access to the back end application server
(Chikouche, Cayrel and Boidje 2019). This paper emphasized the main data security breach that
occurred in the last year with the IoT devices and have highlighted those issues. This report also
has discussed counter measures that can be taken or that has been taken to mitigate those issues
with IoT devices.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

10INNOVATION AND TECHNOLOGIES
References
Alaba, F.A., Othman, M., Hashem, I.A.T. and Alotaibi, F., 2017. Internet of Things security: A
survey. Journal of Network and Computer Applications, 88, pp.10-28.
Ambrosin, M., Anzanpour, A., Conti, M., Dargahi, T., Moosavi, S.R., Rahmani, A.M. and
Liljeberg, P., 2016. On the feasibility of attribute-based encryption on internet of things
devices. IEEE Micro, 36(6), pp.25-35.
Bertino, E. and Islam, N., 2017. Botnets and internet of things security. Computer, 50(2), pp.76-
79.
Chifor, B.C., Arseni, S.C., Matei, I. and Bica, I., 2019, May. Security-Oriented Framework for
Internet of Things Smart-Home Applications. In 2019 22nd International Conference on Control
Systems and Computer Science (CSCS) (pp. 146-153). IEEE.
Chifor, B.C., Bica, I., Patriciu, V.V. and Pop, F., 2018. A security authorization scheme for
smart home Internet of Things devices. Future Generation Computer Systems, 86, pp.740-749.
Chikouche, N., Cayrel, P.L. and Boidje, B.O., 2019. A privacy-preserving code-based
authentication protocol for Internet of Things. The Journal of Supercomputing, 75(12), pp.8231-
8261.
Conti, M., Dehghantanha, A., Franke, K. and Watson, S., 2018. Internet of Things security and
forensics: Challenges and opportunities.
D’Orazio, C.J., Choo, K.K.R. and Yang, L.T., 2016. Data exfiltration from Internet of Things
devices: iOS devices as case studies. IEEE Internet of Things Journal, 4(2), pp.524-535.
References
Alaba, F.A., Othman, M., Hashem, I.A.T. and Alotaibi, F., 2017. Internet of Things security: A
survey. Journal of Network and Computer Applications, 88, pp.10-28.
Ambrosin, M., Anzanpour, A., Conti, M., Dargahi, T., Moosavi, S.R., Rahmani, A.M. and
Liljeberg, P., 2016. On the feasibility of attribute-based encryption on internet of things
devices. IEEE Micro, 36(6), pp.25-35.
Bertino, E. and Islam, N., 2017. Botnets and internet of things security. Computer, 50(2), pp.76-
79.
Chifor, B.C., Arseni, S.C., Matei, I. and Bica, I., 2019, May. Security-Oriented Framework for
Internet of Things Smart-Home Applications. In 2019 22nd International Conference on Control
Systems and Computer Science (CSCS) (pp. 146-153). IEEE.
Chifor, B.C., Bica, I., Patriciu, V.V. and Pop, F., 2018. A security authorization scheme for
smart home Internet of Things devices. Future Generation Computer Systems, 86, pp.740-749.
Chikouche, N., Cayrel, P.L. and Boidje, B.O., 2019. A privacy-preserving code-based
authentication protocol for Internet of Things. The Journal of Supercomputing, 75(12), pp.8231-
8261.
Conti, M., Dehghantanha, A., Franke, K. and Watson, S., 2018. Internet of Things security and
forensics: Challenges and opportunities.
D’Orazio, C.J., Choo, K.K.R. and Yang, L.T., 2016. Data exfiltration from Internet of Things
devices: iOS devices as case studies. IEEE Internet of Things Journal, 4(2), pp.524-535.

11INNOVATION AND TECHNOLOGIES
Ho, G., Leung, D., Mishra, P., Hosseini, A., Song, D. and Wagner, D., 2016, May. Smart locks:
Lessons for securing commodity internet of things devices. In Proceedings of the 11th ACM on
Asia conference on computer and communications security (pp. 461-472).
Li, S., Da Xu, L. and Zhao, S., 2018. 5G Internet of Things: A survey. Journal of Industrial
Information Integration, 10, pp.1-9.
Li, X., Peng, J., Niu, J., Wu, F., Liao, J. and Choo, K.K.R., 2017. A robust and energy efficient
authentication protocol for industrial internet of things. IEEE Internet of Things Journal, 5(3),
pp.1606-1615.
Marktscheffel, T., Gottschlich, W., Popp, W., Werli, P., Fink, S.D., Bilzhause, A. and de Meer,
H., 2016, June. QR code based mutual authentication protocol for Internet of Things. In 2016
IEEE 17th International Symposium on A World of Wireless, Mobile and Multimedia Networks
(WoWMoM) (pp. 1-6). IEEE.
Safkhani, M. and Bagheri, N., 2017. Passive secret disclosure attack on an ultralightweight
authentication protocol for internet of things. The Journal of Supercomputing, 73(8), pp.3579-
3585.
Siboni, S., Sachidananda, V., Meidan, Y., Bohadana, M., Mathov, Y., Bhairav, S., Shabtai, A.
and Elovici, Y., 2019. Security testbed for Internet-of-Things devices. IEEE Transactions on
Reliability, 68(1), pp.23-44.
Taylor, M., Reilly, D. and Lempereur, B., 2017. An access control management protocol for
Internet of Things devices. Network Security, 2017(7), pp.11-17.
Ho, G., Leung, D., Mishra, P., Hosseini, A., Song, D. and Wagner, D., 2016, May. Smart locks:
Lessons for securing commodity internet of things devices. In Proceedings of the 11th ACM on
Asia conference on computer and communications security (pp. 461-472).
Li, S., Da Xu, L. and Zhao, S., 2018. 5G Internet of Things: A survey. Journal of Industrial
Information Integration, 10, pp.1-9.
Li, X., Peng, J., Niu, J., Wu, F., Liao, J. and Choo, K.K.R., 2017. A robust and energy efficient
authentication protocol for industrial internet of things. IEEE Internet of Things Journal, 5(3),
pp.1606-1615.
Marktscheffel, T., Gottschlich, W., Popp, W., Werli, P., Fink, S.D., Bilzhause, A. and de Meer,
H., 2016, June. QR code based mutual authentication protocol for Internet of Things. In 2016
IEEE 17th International Symposium on A World of Wireless, Mobile and Multimedia Networks
(WoWMoM) (pp. 1-6). IEEE.
Safkhani, M. and Bagheri, N., 2017. Passive secret disclosure attack on an ultralightweight
authentication protocol for internet of things. The Journal of Supercomputing, 73(8), pp.3579-
3585.
Siboni, S., Sachidananda, V., Meidan, Y., Bohadana, M., Mathov, Y., Bhairav, S., Shabtai, A.
and Elovici, Y., 2019. Security testbed for Internet-of-Things devices. IEEE Transactions on
Reliability, 68(1), pp.23-44.
Taylor, M., Reilly, D. and Lempereur, B., 2017. An access control management protocol for
Internet of Things devices. Network Security, 2017(7), pp.11-17.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 13
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.




