A Comprehensive Look at IoT Security, Privacy Issues and Trends 2017
VerifiedAdded on 2020/03/04
|9
|1402
|116
Report
AI Summary
This report provides an overview of Internet of Things (IoT) technology, focusing on the interconnection of physical devices and networks. It highlights the advantages of IoT, such as reduced costs, improved efficiency, and increased productivity. The report delves into privacy issues related to IoT design, data collection, and the use of cloud technology, emphasizing the importance of addressing vulnerabilities and unauthorized data access. It also discusses trends in IoT applications, including intelligence, architecture, and network complexity, and methodologies for device installation, configuration, and security testing. Furthermore, the report examines geo-encryption practices for securing IoT services, including cryptographic methods, password enforcement, TLS certificate validation, and protection against replay attacks. The conclusion emphasizes the need for periodic reviews of privacy and security concerns to enhance the efficiency and accuracy of IoT services.
Internet of Things
2017
2017
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Internet of Things
Contents
Internet of Things:.................................................................................................................................2
Privacy issues in IoT:............................................................................................................................2
Trends and Methodology:......................................................................................................................4
Methodology:........................................................................................................................................5
Geo encryptions of IoT:.........................................................................................................................5
Conclusion:............................................................................................................................................6
References:............................................................................................................................................7
1
Contents
Internet of Things:.................................................................................................................................2
Privacy issues in IoT:............................................................................................................................2
Trends and Methodology:......................................................................................................................4
Methodology:........................................................................................................................................5
Geo encryptions of IoT:.........................................................................................................................5
Conclusion:............................................................................................................................................6
References:............................................................................................................................................7
1

Internet of Things
Internet of Things:
The interconnection between the physical devices, buildings, vehicles, software, electronics,
sensors, actuators, and the connectivity network is called as Internet of things. The network
infrastructure is capable of controlling and sensing the IoT objects. It helps in improving
efficiency, accuracy, and reducing the human intervention. The applications of cyber physical
system are smart grid, smart homes, virtual power plant, smart cities, and intelligent
transportation. “The focus of IoT is providing machine to machine communication with the
help of variety of protocols, application, and domains” (Friess, 2013). The connectivity of
devices helps in collecting more data. IOT security methodology helps in in improving the
performance of the IoT analytics. The advantages of using IoT are that it helps in reducing
costs, improving the efficiency of the processes, helps in effective utilization of assets, and
increased productivity. “The connection between people, processes, and businesses helps in
smooth flow of information” (Lord, 2014).
Privacy issues in IoT:
The value services are provided by the IoT by improving quality of life and providing new
opportunities to the in the open market. The cloud technologies, big data paradigms wireless
sensor netwroks, peer to peer networks, and others are the technologies which are used for
leveraging the IOT system. “The use of wireless sensors in the IoT application raises the
problems like accessibility, accuracy, availability, and confidentiality” (Simon, 2017). In the
IoT environment the security problems are associated with data collection phase and
transmission, processing, and storage of data throughout the life cycle. Some of the privacy
issues are listed below:
Privacy issues related with the design of IoT.
In the process of tracking the threats
Preserving privacy from the middleware in the internet of things
Enhancing recovery from unconventional resources.
Privacy issues related to big data in IoT
Preserving privacy in data collection and mining methods
Responsibility and accountability
Privacy issues related to the use of cloud technology
Use of new cryptographic methods in IoT environment
2
Internet of Things:
The interconnection between the physical devices, buildings, vehicles, software, electronics,
sensors, actuators, and the connectivity network is called as Internet of things. The network
infrastructure is capable of controlling and sensing the IoT objects. It helps in improving
efficiency, accuracy, and reducing the human intervention. The applications of cyber physical
system are smart grid, smart homes, virtual power plant, smart cities, and intelligent
transportation. “The focus of IoT is providing machine to machine communication with the
help of variety of protocols, application, and domains” (Friess, 2013). The connectivity of
devices helps in collecting more data. IOT security methodology helps in in improving the
performance of the IoT analytics. The advantages of using IoT are that it helps in reducing
costs, improving the efficiency of the processes, helps in effective utilization of assets, and
increased productivity. “The connection between people, processes, and businesses helps in
smooth flow of information” (Lord, 2014).
Privacy issues in IoT:
The value services are provided by the IoT by improving quality of life and providing new
opportunities to the in the open market. The cloud technologies, big data paradigms wireless
sensor netwroks, peer to peer networks, and others are the technologies which are used for
leveraging the IOT system. “The use of wireless sensors in the IoT application raises the
problems like accessibility, accuracy, availability, and confidentiality” (Simon, 2017). In the
IoT environment the security problems are associated with data collection phase and
transmission, processing, and storage of data throughout the life cycle. Some of the privacy
issues are listed below:
Privacy issues related with the design of IoT.
In the process of tracking the threats
Preserving privacy from the middleware in the internet of things
Enhancing recovery from unconventional resources.
Privacy issues related to big data in IoT
Preserving privacy in data collection and mining methods
Responsibility and accountability
Privacy issues related to the use of cloud technology
Use of new cryptographic methods in IoT environment
2
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Internet of Things
Anonymization of IoT technology
In the development of proactive privacy model
Compliance with ethical and legal standards for IoT devices.
Unauthorised accessing of data
Internet is equipped with threat and vulnerabilities
Machine to machine interaction
Contract information with M2M
Availability of information
Unauthorised accessing of services
Changes in the information used for communication
Attacks of viruses and malwares
Network security
Code resources management
Operator replacement
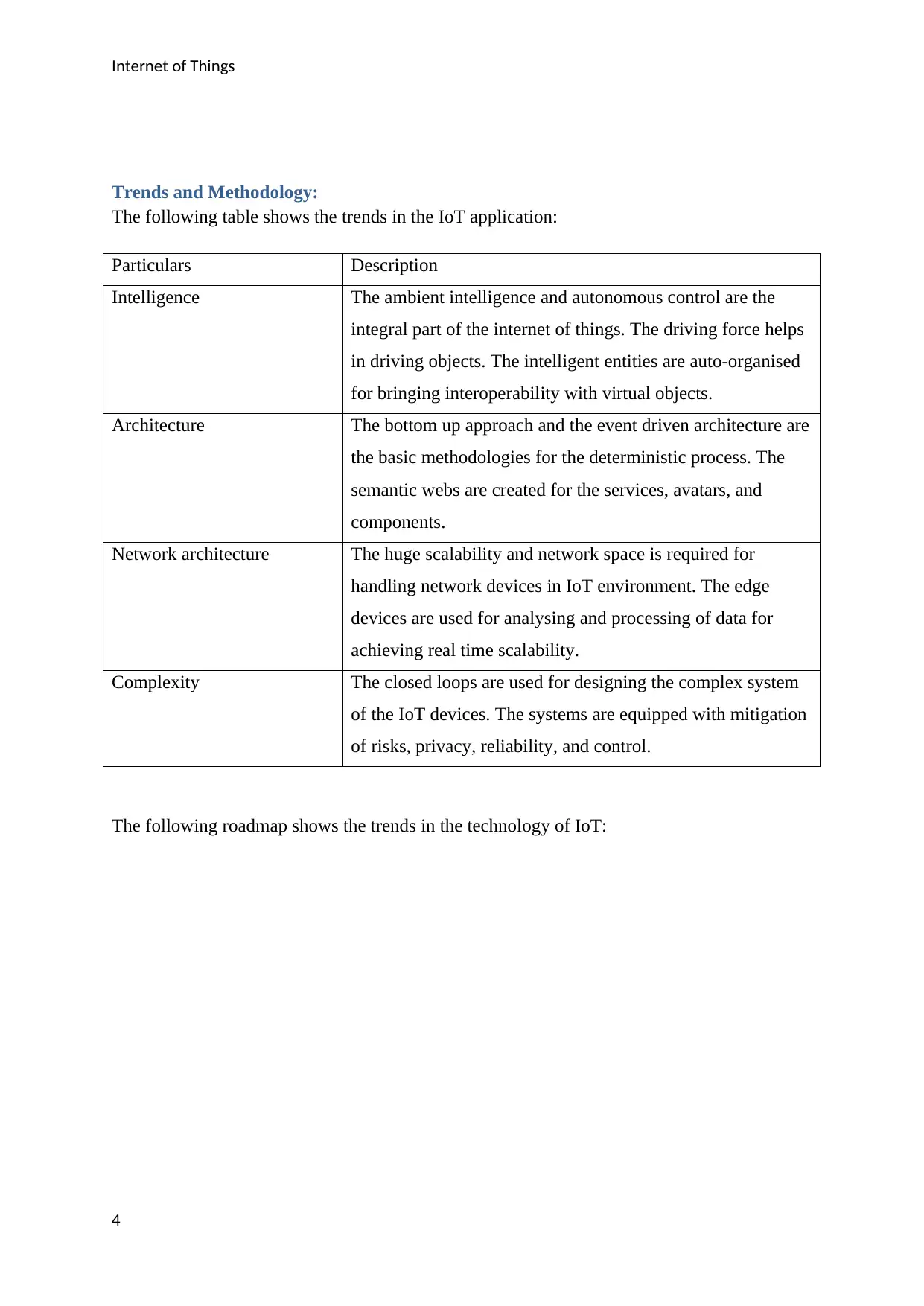
The following diagram gives the clear description of security concern for the IoT:
3
Anonymization of IoT technology
In the development of proactive privacy model
Compliance with ethical and legal standards for IoT devices.
Unauthorised accessing of data
Internet is equipped with threat and vulnerabilities
Machine to machine interaction
Contract information with M2M
Availability of information
Unauthorised accessing of services
Changes in the information used for communication
Attacks of viruses and malwares
Network security
Code resources management
Operator replacement
The following diagram gives the clear description of security concern for the IoT:
3
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
Internet of Things
Trends and Methodology:
The following table shows the trends in the IoT application:
Particulars Description
Intelligence The ambient intelligence and autonomous control are the
integral part of the internet of things. The driving force helps
in driving objects. The intelligent entities are auto-organised
for bringing interoperability with virtual objects.
Architecture The bottom up approach and the event driven architecture are
the basic methodologies for the deterministic process. The
semantic webs are created for the services, avatars, and
components.
Network architecture The huge scalability and network space is required for
handling network devices in IoT environment. The edge
devices are used for analysing and processing of data for
achieving real time scalability.
Complexity The closed loops are used for designing the complex system
of the IoT devices. The systems are equipped with mitigation
of risks, privacy, reliability, and control.
The following roadmap shows the trends in the technology of IoT:
4
Trends and Methodology:
The following table shows the trends in the IoT application:
Particulars Description
Intelligence The ambient intelligence and autonomous control are the
integral part of the internet of things. The driving force helps
in driving objects. The intelligent entities are auto-organised
for bringing interoperability with virtual objects.
Architecture The bottom up approach and the event driven architecture are
the basic methodologies for the deterministic process. The
semantic webs are created for the services, avatars, and
components.
Network architecture The huge scalability and network space is required for
handling network devices in IoT environment. The edge
devices are used for analysing and processing of data for
achieving real time scalability.
Complexity The closed loops are used for designing the complex system
of the IoT devices. The systems are equipped with mitigation
of risks, privacy, reliability, and control.
The following roadmap shows the trends in the technology of IoT:
4
Internet of Things
Methodology:
The installation and the configuration of devices are governed by the documentation. The
monitoring and testing of devices helps in predicting vulnerabilities within the devices. The
devices are tested separately. “The security of the communication is directed by reverse
engineering methods. The unauthorised access of data in the cloud environment should be
checked by running active test” (Rosa, 2015). The back-end cloud services are associated
with the monitoring of traffic to assess devices security.
Geo encryptions of IoT:
The encryption practices which are used for securing the IoT services are:
Allowing cryptographic methodology:
Test: Does the communication can be protected by strong cryptographic methods?
Impact: The authentication credentials are required for allowing encrypted communication in
protecting data in the transition process.
Requirement of cryptography:
Test: Does the user required to use cryptography for using the IOT services?
5
Methodology:
The installation and the configuration of devices are governed by the documentation. The
monitoring and testing of devices helps in predicting vulnerabilities within the devices. The
devices are tested separately. “The security of the communication is directed by reverse
engineering methods. The unauthorised access of data in the cloud environment should be
checked by running active test” (Rosa, 2015). The back-end cloud services are associated
with the monitoring of traffic to assess devices security.
Geo encryptions of IoT:
The encryption practices which are used for securing the IoT services are:
Allowing cryptographic methodology:
Test: Does the communication can be protected by strong cryptographic methods?
Impact: The authentication credentials are required for allowing encrypted communication in
protecting data in the transition process.
Requirement of cryptography:
Test: Does the user required to use cryptography for using the IOT services?
5
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Internet of Things
Impact: The strong cryptography methods helps in reducing the change of data leakage. It
also helps in overcoming the problem of weaknesses of the network and user error.
Enforcement of using strong passwords:
Test: Password strength guidelines should be followed by the user in creating passwords:
Impact: “The cost of attacking can be increased by using strong passwords because the
attacker has to use brute force or other algorithms for attacking” (Cognizant Report, 2017).
The cracking of passwords requires more effort and time.
TLS certificate validation:
Test: The TLS certificates should be used for validation
Impact: The man in the middle attack arises due to the improper validation certificates. With
the use of TLS certificate the problem of man in the middle attack can be resolved
Authentication provided to Device to service:
Test: Strong authentication mechanism should be used by the devices:
Impact: “The failure of device give rise to vulnerabilities. The communication session should
be maintained between the devices and services” (Morchan, 2014).
Protection provided to sensitive data
Test: The control services should use encryption methodology for carrying out
communication
Impact: “The sensitivity of the data requires adequate protection from the passive observers”
(Arockiam, 2016). The passive observer looks for the flow of network traffic. It requires the
encryption methodologies.
Replay attacks should be protected:
Test: The adequate protection should be planned against the replay of attacks
Impact: Sometimes the protocols are not well designed to protect the data from attack. “The
weaknesses of the attack should remove for protecting the devices from unauthorised access
6
Impact: The strong cryptography methods helps in reducing the change of data leakage. It
also helps in overcoming the problem of weaknesses of the network and user error.
Enforcement of using strong passwords:
Test: Password strength guidelines should be followed by the user in creating passwords:
Impact: “The cost of attacking can be increased by using strong passwords because the
attacker has to use brute force or other algorithms for attacking” (Cognizant Report, 2017).
The cracking of passwords requires more effort and time.
TLS certificate validation:
Test: The TLS certificates should be used for validation
Impact: The man in the middle attack arises due to the improper validation certificates. With
the use of TLS certificate the problem of man in the middle attack can be resolved
Authentication provided to Device to service:
Test: Strong authentication mechanism should be used by the devices:
Impact: “The failure of device give rise to vulnerabilities. The communication session should
be maintained between the devices and services” (Morchan, 2014).
Protection provided to sensitive data
Test: The control services should use encryption methodology for carrying out
communication
Impact: “The sensitivity of the data requires adequate protection from the passive observers”
(Arockiam, 2016). The passive observer looks for the flow of network traffic. It requires the
encryption methodologies.
Replay attacks should be protected:
Test: The adequate protection should be planned against the replay of attacks
Impact: Sometimes the protocols are not well designed to protect the data from attack. “The
weaknesses of the attack should remove for protecting the devices from unauthorised access
6
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Internet of Things
in the future” (Kumar, 2014). The debugging of the interface should be periodically
performed to check the efficiency of the protocol.
Conclusion:
The IoT is the machine to machine technology which makes use of sensor and actuators to
develop a smart environment. The privacy and security concerns should be periodically
reviewed for increasing the efficiency and accuracy of the IOT services. The intelligent
connection between people, devices, and processes can be made with the help of IoT
services.
7
in the future” (Kumar, 2014). The debugging of the interface should be periodically
performed to check the efficiency of the protocol.
Conclusion:
The IoT is the machine to machine technology which makes use of sensor and actuators to
develop a smart environment. The privacy and security concerns should be periodically
reviewed for increasing the efficiency and accuracy of the IOT services. The intelligent
connection between people, devices, and processes can be made with the help of IoT
services.
7

Internet of Things
References:
Arockiam, L. (2016). A study of security issues and challenges in IoT. Retrieved from
http://www.ijesmr.com/doc/Archive-2016/November-2016/5.pdf
Cognizant Report. (2017). Safeguarding the internet of things. Retrieved from
https://www.cognizant.com/whitepapers/safeguarding-the-internet-of-things-
codex2465.pdf
Friess, P. (2013). Internet of things- converging technologies for smart environment.
Retrieved from
http://www.internet-of-things-research.eu/pdf/Converging_Technologies_for_Smart_
Environments_and_Integrated_Ecosystems_IERC_Book_Open_Access_2013.pdf
Kumar, S. (2014). A survey of internet of things: Security and privacy issues. Retrieved from
http://research.ijcaonline.org/volume90/number11/pxc3894454.pdf
Lord, S. (2014). The internet of things: An introduction to privacy issues. Retrieved from
https://www.priv.gc.ca/media/1808/iot_201602_e.pdf
Morchan, O. (2014). Privacy in the internet of things: Threats and challenges. Retrieved
from https://assets.documentcloud.org/documents/2822904/Ziegeldorf-Jan-Henrik-
Privacy-in-the-Internet-of.pdf
Rosa, T. (2015). The internet of things: Security research study. Retrieved from
https://www.veracode.com/sites/default/files/Resources/Whitepapers/internet-of-
things-whitepaper.pdf
Simon, T. (2017). Critical infrastructure and the internet of things. Retrieved from
https://www.cigionline.org/sites/default/files/documents/GCIG%20no.46_0.pdf
8
References:
Arockiam, L. (2016). A study of security issues and challenges in IoT. Retrieved from
http://www.ijesmr.com/doc/Archive-2016/November-2016/5.pdf
Cognizant Report. (2017). Safeguarding the internet of things. Retrieved from
https://www.cognizant.com/whitepapers/safeguarding-the-internet-of-things-
codex2465.pdf
Friess, P. (2013). Internet of things- converging technologies for smart environment.
Retrieved from
http://www.internet-of-things-research.eu/pdf/Converging_Technologies_for_Smart_
Environments_and_Integrated_Ecosystems_IERC_Book_Open_Access_2013.pdf
Kumar, S. (2014). A survey of internet of things: Security and privacy issues. Retrieved from
http://research.ijcaonline.org/volume90/number11/pxc3894454.pdf
Lord, S. (2014). The internet of things: An introduction to privacy issues. Retrieved from
https://www.priv.gc.ca/media/1808/iot_201602_e.pdf
Morchan, O. (2014). Privacy in the internet of things: Threats and challenges. Retrieved
from https://assets.documentcloud.org/documents/2822904/Ziegeldorf-Jan-Henrik-
Privacy-in-the-Internet-of.pdf
Rosa, T. (2015). The internet of things: Security research study. Retrieved from
https://www.veracode.com/sites/default/files/Resources/Whitepapers/internet-of-
things-whitepaper.pdf
Simon, T. (2017). Critical infrastructure and the internet of things. Retrieved from
https://www.cigionline.org/sites/default/files/documents/GCIG%20no.46_0.pdf
8
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 9
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





