An Investigation into Privacy Issues of IoT Devices and Networks
VerifiedAdded on 2023/03/17
|13
|3345
|59
Report
AI Summary
This report investigates the multifaceted privacy issues associated with the Internet of Things (IoT). It begins with an introduction highlighting the increasing use of IoT devices and the resulting security and privacy concerns, particularly device and physical security. The report poses critical research questions about the root causes of IoT security issues and potential solutions. A background study explores existing literature, citing various scholars who have discussed device security, data security, network security, operating system flaws, and server issues. The study identifies gaps in the literature, such as the impact of different security issues on IoT users. The report then outlines the research plan, including data collection from secondary resources and the use of peer-reviewed articles. A Gantt chart is included to detail the task and publication plans. The conclusion emphasizes the significance of the research in understanding IoT security and privacy challenges. The report also covers networking difficulties, protocol problems, and the privacy implications of technologies like face identification. It highlights the importance of corporate transparency and government regulations regarding IoT devices. The report aims to provide a comprehensive overview of IoT privacy issues and their potential impact on individuals and organizations.

Running head: PRIVACY ISSUES OF IOT
Privacy issues of IoT
Name of the Student
Name of the University
Author’s Note:
Privacy issues of IoT
Name of the Student
Name of the University
Author’s Note:
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1PRIVACY ISSUES OF IOT
Table of Contents
Introduction................................................................................................................................3
Background Study......................................................................................................................3
Aims and Significance.............................................................................................................10
Research Plan...........................................................................................................................10
Publication Plan...................................................................................................................11
Conclusion................................................................................................................................12
References................................................................................................................................13
Table of Contents
Introduction................................................................................................................................3
Background Study......................................................................................................................3
Aims and Significance.............................................................................................................10
Research Plan...........................................................................................................................10
Publication Plan...................................................................................................................11
Conclusion................................................................................................................................12
References................................................................................................................................13

2PRIVACY ISSUES OF IOT
Introduction
The increasing use of the IoT based devices has lots of privacy issues such as the
device security and physical security which is a big issues for most of the IoT users. The
primary research questions of the paper are presented as follows:
What are the reasons behind the security issues of IoT based devices?
How can be privacy issue be addressed?
Data will be collected from the secondary resources. The gaps in the collected
resources will be addressed as 30 peer review articles shall be argued in the same topic. The
ensuing section of this proposal will be discussing the background of the study presented the
opinion of numerous scholar who have stated their opinion about the selected topic. This
section will be ensue by a Gantt chart where the task plan and the publication plan will be
identified. This paper can be used for future researchers as it can successfully identify the
reason behind the security issues of IoT based devices.
Background Study
According to Abomhara (2015), there are different security issue allied with the use
of the IoT based devices which are used in our society as well as in commercial organizations
such as the device security and data security. The researcher of the paper provided a thorough
explanation of the physical security concerns of the IoT based devices. The impact of the
device security was highlighted in the paper in a professional manner. The investigator of the
paper helped in understanding the two different categories of data which are very much
vulnerable to the privacy issues of the IoT devices such as the ransomware (Lin at al. 2017).
This paper have numerous case studies which supports the discussions made in the paper, this
paper is very much reliable, but the paper have few limitations as well as it did not show the
Introduction
The increasing use of the IoT based devices has lots of privacy issues such as the
device security and physical security which is a big issues for most of the IoT users. The
primary research questions of the paper are presented as follows:
What are the reasons behind the security issues of IoT based devices?
How can be privacy issue be addressed?
Data will be collected from the secondary resources. The gaps in the collected
resources will be addressed as 30 peer review articles shall be argued in the same topic. The
ensuing section of this proposal will be discussing the background of the study presented the
opinion of numerous scholar who have stated their opinion about the selected topic. This
section will be ensue by a Gantt chart where the task plan and the publication plan will be
identified. This paper can be used for future researchers as it can successfully identify the
reason behind the security issues of IoT based devices.
Background Study
According to Abomhara (2015), there are different security issue allied with the use
of the IoT based devices which are used in our society as well as in commercial organizations
such as the device security and data security. The researcher of the paper provided a thorough
explanation of the physical security concerns of the IoT based devices. The impact of the
device security was highlighted in the paper in a professional manner. The investigator of the
paper helped in understanding the two different categories of data which are very much
vulnerable to the privacy issues of the IoT devices such as the ransomware (Lin at al. 2017).
This paper have numerous case studies which supports the discussions made in the paper, this
paper is very much reliable, but the paper have few limitations as well as it did not show the
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3PRIVACY ISSUES OF IOT
impact of the security related concerns on the IoT users. However, as stated by Alaba et al.
(2017), the prime issues which can have a direct impact on the users of IoT based devices is
the network security issues. The researcher of the paper stated that the device security is one
of the most negligible issues of the IoT based devices (Li et al. 2016). The most substantial
gains of this paper is that it helps in reflecting most of the probable network security issues
and the main limitation of the paper is that it does not highlights the impact of the network
security issues (Malina et al. 2016). Thus the literature gap between these two papers is both
of them have not discussed which of these issues have the maximum impact on the IoT users.
As mentioned by Alrawais et al. (2017), operating security issues is one of the most
important issues of most of the IoT based devices. The investigator of this resource stated
that the security issues of the IoT based devices arises mostly due to the flaws of the
operating system. The researcher of the paper highlighted that the data security issue of the
IoT based devices are mostly due to the flaws of their operating systems (Maple 2017). The
paper has both benefits as well as limitations. The most substantial advantage of the paper is
its identification of the operating security issues of the IoT devices which are increasingly
used in our society such as the temperature sensors which are connected to a network (Zhou
et al. 2017). The limitation of the paper it does not state the ways to reduce the threats
coming from the network security issues. At the same time Alur et al. (2016), declared that
the server issues of the IoT based devices is the main reason behind the security issues of the
IoT based devices. The investigator of this resource stated that the most of the network
security issues such as the DDoS occurs mainly due to the server security issues of the IoT
based devices (Li et al. 2018). This paper also has certain limitations as well. Most of the
discussions which are there in the paper are entirely in generalized manner. Thus, both
researchers of the paper contradicted in their opinion about the reason behind the security
issues of the IoT based devices.
impact of the security related concerns on the IoT users. However, as stated by Alaba et al.
(2017), the prime issues which can have a direct impact on the users of IoT based devices is
the network security issues. The researcher of the paper stated that the device security is one
of the most negligible issues of the IoT based devices (Li et al. 2016). The most substantial
gains of this paper is that it helps in reflecting most of the probable network security issues
and the main limitation of the paper is that it does not highlights the impact of the network
security issues (Malina et al. 2016). Thus the literature gap between these two papers is both
of them have not discussed which of these issues have the maximum impact on the IoT users.
As mentioned by Alrawais et al. (2017), operating security issues is one of the most
important issues of most of the IoT based devices. The investigator of this resource stated
that the security issues of the IoT based devices arises mostly due to the flaws of the
operating system. The researcher of the paper highlighted that the data security issue of the
IoT based devices are mostly due to the flaws of their operating systems (Maple 2017). The
paper has both benefits as well as limitations. The most substantial advantage of the paper is
its identification of the operating security issues of the IoT devices which are increasingly
used in our society such as the temperature sensors which are connected to a network (Zhou
et al. 2017). The limitation of the paper it does not state the ways to reduce the threats
coming from the network security issues. At the same time Alur et al. (2016), declared that
the server issues of the IoT based devices is the main reason behind the security issues of the
IoT based devices. The investigator of this resource stated that the most of the network
security issues such as the DDoS occurs mainly due to the server security issues of the IoT
based devices (Li et al. 2018). This paper also has certain limitations as well. Most of the
discussions which are there in the paper are entirely in generalized manner. Thus, both
researchers of the paper contradicted in their opinion about the reason behind the security
issues of the IoT based devices.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

4PRIVACY ISSUES OF IOT
As discussed by Andrea et al. (2015), privacy of the users of the IoT devices is a huge
concern for most of the IoT devices. The researcher of the paper stated that the security
breaches can have an undesirable impact on the security measures of the IoT devices (Sicari
et al. 2015). The paper suggested that most of the global manufacturing organization who are
actively manufacturing most of the IoT devices must be understand the networking security
threats of IoT devices. The importance of the cyber surveillance was highlighted in the paper
as well (Li et al. 2015). The investigator of the paper highlighted that corporate transparency
of the IoT devices are very much desired regarding the usage of the IoT derives both in
global commercial organizations as well as in our society. As deliberated by Andrea,
Chrysostomou, and Hadjichristofi (2015), there are numerous networking difficulties
connected with the IoT based devices used in business enterprises in terms of the
configuration issues, compatibility issues of between the devices and the configurations
(Thierer 2015). The researcher of the paper highlighted the different categories of
networking issues which can have a direct impact on the security of the IoT devices
(Mehmood et al. 2017). The prime contribution of the paper is that it helps in identifying the
networking difficulties of the IoT devices, at the same time the paper also have limitations as
well as it does not discusses the ways to address these networking difficulties (Yang et al.
2017). However, as mentioned by Arias et al. (2015), there are numerous privacy issues
connected with the IoT watches which are used in our society in terms of the location settings
(Mendez, Papapanagiotou and Yang 2017). The compromise of the location settings can have
an undesirable impact on the users of the IoT devices. This paper also have few advantages
and disadvantages, the prime benefit of the paper is that it helps in identifying the privacy
issues coming from the IoT smart watches in terms of the location settings (Lee et al. 2015).
The main constraint of the paper is that it does not discusses the risk mitigation step to
resolve the above stated privacy issue (Weinberg et al. 2015). The research gap which can be
As discussed by Andrea et al. (2015), privacy of the users of the IoT devices is a huge
concern for most of the IoT devices. The researcher of the paper stated that the security
breaches can have an undesirable impact on the security measures of the IoT devices (Sicari
et al. 2015). The paper suggested that most of the global manufacturing organization who are
actively manufacturing most of the IoT devices must be understand the networking security
threats of IoT devices. The importance of the cyber surveillance was highlighted in the paper
as well (Li et al. 2015). The investigator of the paper highlighted that corporate transparency
of the IoT devices are very much desired regarding the usage of the IoT derives both in
global commercial organizations as well as in our society. As deliberated by Andrea,
Chrysostomou, and Hadjichristofi (2015), there are numerous networking difficulties
connected with the IoT based devices used in business enterprises in terms of the
configuration issues, compatibility issues of between the devices and the configurations
(Thierer 2015). The researcher of the paper highlighted the different categories of
networking issues which can have a direct impact on the security of the IoT devices
(Mehmood et al. 2017). The prime contribution of the paper is that it helps in identifying the
networking difficulties of the IoT devices, at the same time the paper also have limitations as
well as it does not discusses the ways to address these networking difficulties (Yang et al.
2017). However, as mentioned by Arias et al. (2015), there are numerous privacy issues
connected with the IoT watches which are used in our society in terms of the location settings
(Mendez, Papapanagiotou and Yang 2017). The compromise of the location settings can have
an undesirable impact on the users of the IoT devices. This paper also have few advantages
and disadvantages, the prime benefit of the paper is that it helps in identifying the privacy
issues coming from the IoT smart watches in terms of the location settings (Lee et al. 2015).
The main constraint of the paper is that it does not discusses the risk mitigation step to
resolve the above stated privacy issue (Weinberg et al. 2015). The research gap which can be

5PRIVACY ISSUES OF IOT
identified from the above paper is that it does not discuss the ways to address the threats
coming from the networking issues as well as location settings.
As discussed by Borgohain, Kumar and Sanyal (2015), there are security concerns in
terms of the protocol problems which are faced by most of the IoT systems. The investigator
of the journal mentioned that the protocol issues comes mainly from the IoT devices which
are extensively used most of the manufacturing industries (Kumar, Veale and Srivastava
2016). The researchers of the paper stated that the security issues comes mainly due to the
secure vulnerabilities of the organizational network (Sfar et al. 2018). The researchers of the
paper stated that malicious activities can have a huge impact on the business growth of the
global Corporations as they uses high-end IoT devices in their business environment (Dorri,
Kanhere and Jurda 2016). The most significant benefit of the paper it identifies the protocol
issues of the IoT devices (Sadeghi, Wachsmann, and Waidner 2015). At the same time, it can
also be said that the paper have lot of limitations as well as the discussion of the paper are not
supported by case study.
As mentioned by Hu et al. (2017), there are security issues with face identification
techniques of the IoT based systems, these issues can have a huge financial impact in global
business organizations. The researcher of the paper stated that these security concerns can
have undesirable impact on both the employees as well as for the management team of
business organizations (Whitmore, Agarwal and Da 2015). The investigator also highlighted
about the stringent government regulations on most of the IoT devices which are used in the
production rooms of the business enterprises. The paper has both advantages as well as
disadvantages (Kolias et al. 2016). The main advantage of the paper is that it helps in
identifying the impact the privacy issues in global organizations (Stojkoska and Trivodaliev
2017). The research gap which can be identified from the above papers is it does not
identified from the above paper is that it does not discuss the ways to address the threats
coming from the networking issues as well as location settings.
As discussed by Borgohain, Kumar and Sanyal (2015), there are security concerns in
terms of the protocol problems which are faced by most of the IoT systems. The investigator
of the journal mentioned that the protocol issues comes mainly from the IoT devices which
are extensively used most of the manufacturing industries (Kumar, Veale and Srivastava
2016). The researchers of the paper stated that the security issues comes mainly due to the
secure vulnerabilities of the organizational network (Sfar et al. 2018). The researchers of the
paper stated that malicious activities can have a huge impact on the business growth of the
global Corporations as they uses high-end IoT devices in their business environment (Dorri,
Kanhere and Jurda 2016). The most significant benefit of the paper it identifies the protocol
issues of the IoT devices (Sadeghi, Wachsmann, and Waidner 2015). At the same time, it can
also be said that the paper have lot of limitations as well as the discussion of the paper are not
supported by case study.
As mentioned by Hu et al. (2017), there are security issues with face identification
techniques of the IoT based systems, these issues can have a huge financial impact in global
business organizations. The researcher of the paper stated that these security concerns can
have undesirable impact on both the employees as well as for the management team of
business organizations (Whitmore, Agarwal and Da 2015). The investigator also highlighted
about the stringent government regulations on most of the IoT devices which are used in the
production rooms of the business enterprises. The paper has both advantages as well as
disadvantages (Kolias et al. 2016). The main advantage of the paper is that it helps in
identifying the impact the privacy issues in global organizations (Stojkoska and Trivodaliev
2017). The research gap which can be identified from the above papers is it does not
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
6PRIVACY ISSUES OF IOT
highlights the ways to address the protocol problems of the IoT devices at the same it can
also be said that security measures taken by the corporate organizations to deal with the
security threats were also not considered in these papers.
Aims and Significance
The overall objective of this research proposal is to focus on the safety and the
privacy challenges of IoT. All the specific safety concerns of IoT will be considered in the
paper.
Research Plan
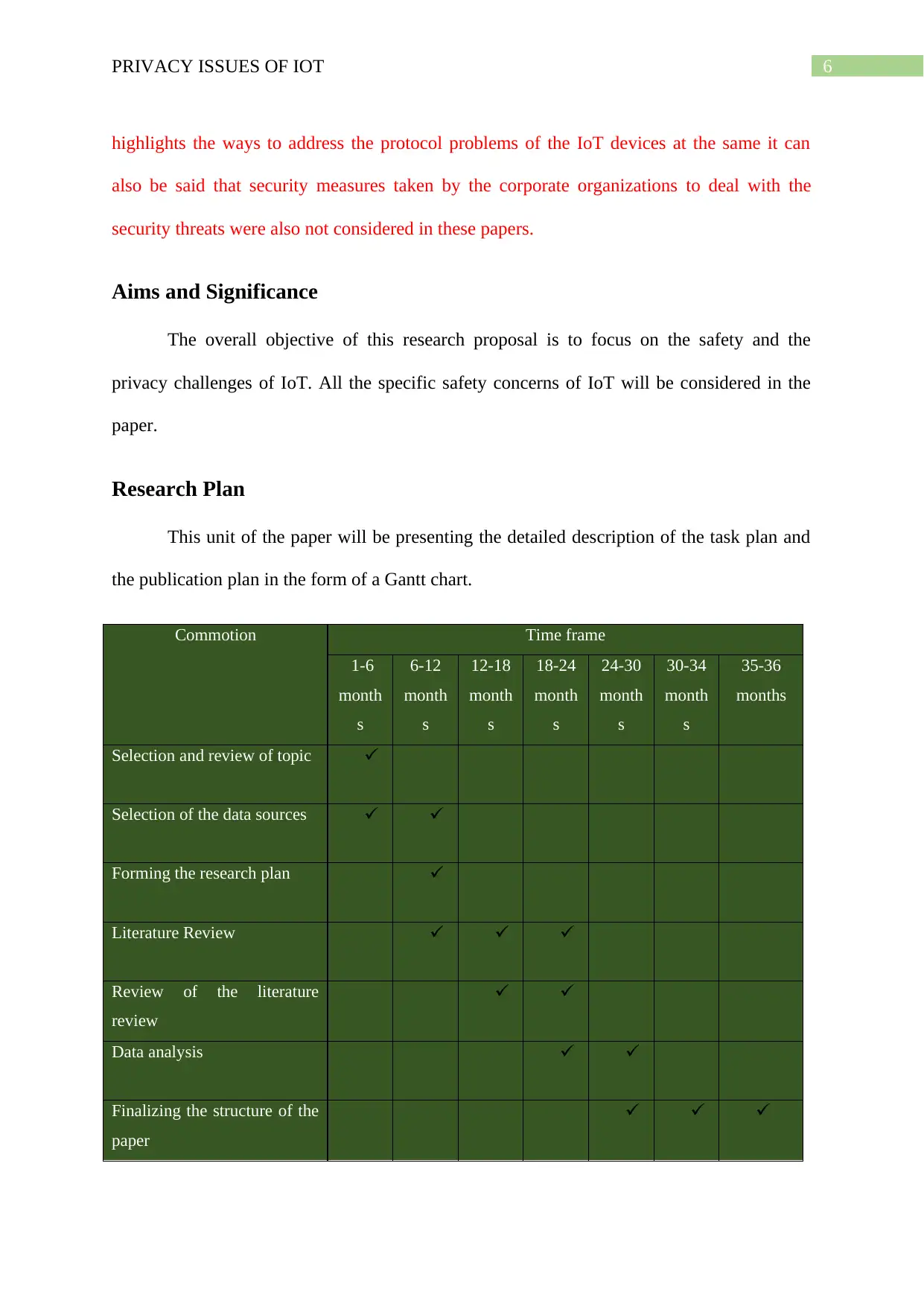
This unit of the paper will be presenting the detailed description of the task plan and
the publication plan in the form of a Gantt chart.
Commotion Time frame
1-6
month
s
6-12
month
s
12-18
month
s
18-24
month
s
24-30
month
s
30-34
month
s
35-36
months
Selection and review of topic
Selection of the data sources
Forming the research plan
Literature Review
Review of the literature
review
Data analysis
Finalizing the structure of the
paper
highlights the ways to address the protocol problems of the IoT devices at the same it can
also be said that security measures taken by the corporate organizations to deal with the
security threats were also not considered in these papers.
Aims and Significance
The overall objective of this research proposal is to focus on the safety and the
privacy challenges of IoT. All the specific safety concerns of IoT will be considered in the
paper.
Research Plan
This unit of the paper will be presenting the detailed description of the task plan and
the publication plan in the form of a Gantt chart.
Commotion Time frame
1-6
month
s
6-12
month
s
12-18
month
s
18-24
month
s
24-30
month
s
30-34
month
s
35-36
months
Selection and review of topic
Selection of the data sources
Forming the research plan
Literature Review
Review of the literature
review
Data analysis
Finalizing the structure of the
paper
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
7PRIVACY ISSUES OF IOT
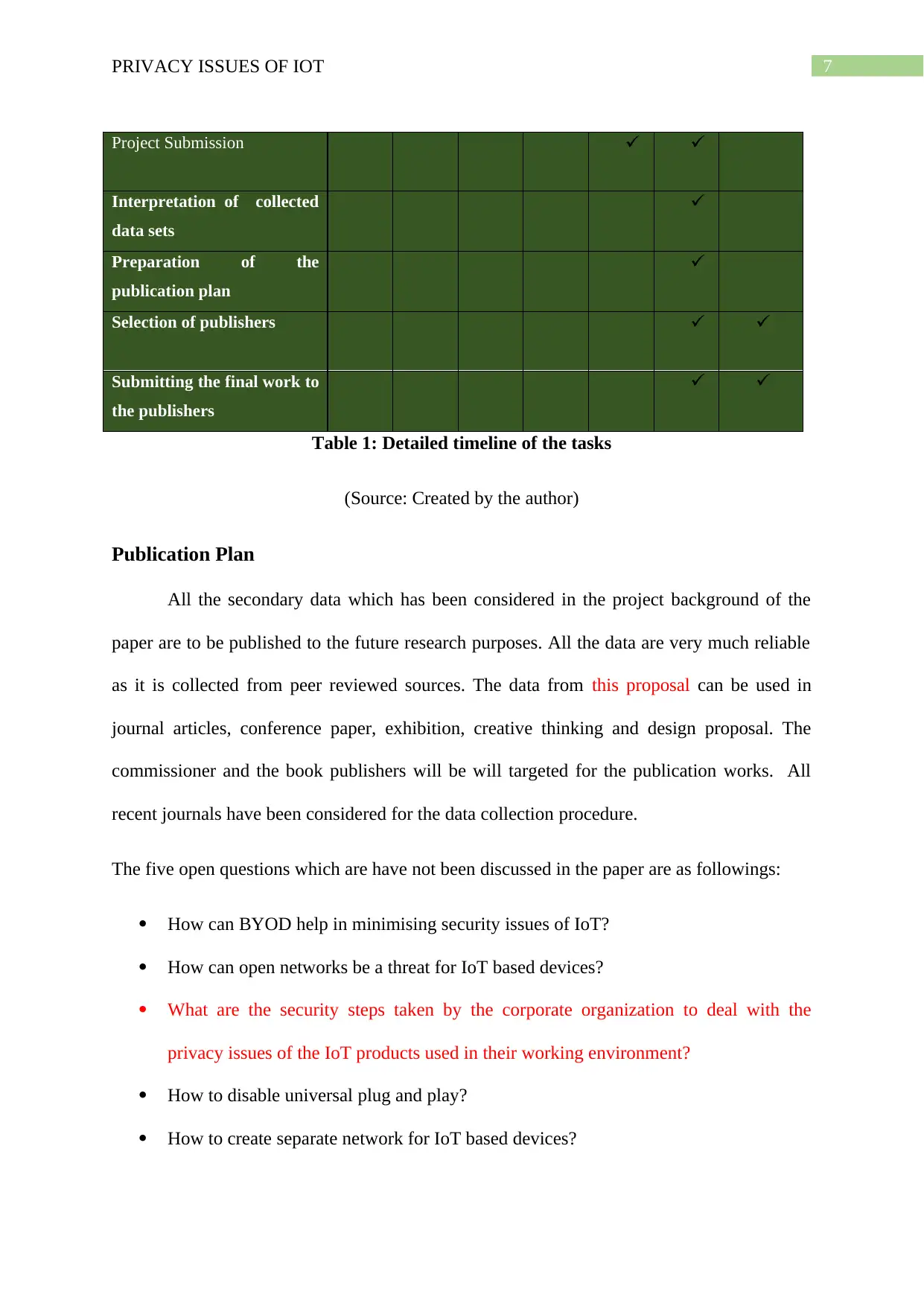
Project Submission
Interpretation of collected
data sets
Preparation of the
publication plan
Selection of publishers
Submitting the final work to
the publishers
Table 1: Detailed timeline of the tasks
(Source: Created by the author)
Publication Plan
All the secondary data which has been considered in the project background of the
paper are to be published to the future research purposes. All the data are very much reliable
as it is collected from peer reviewed sources. The data from this proposal can be used in
journal articles, conference paper, exhibition, creative thinking and design proposal. The
commissioner and the book publishers will be will targeted for the publication works. All
recent journals have been considered for the data collection procedure.
The five open questions which are have not been discussed in the paper are as followings:
How can BYOD help in minimising security issues of IoT?
How can open networks be a threat for IoT based devices?
What are the security steps taken by the corporate organization to deal with the
privacy issues of the IoT products used in their working environment?
How to disable universal plug and play?
How to create separate network for IoT based devices?
Project Submission
Interpretation of collected
data sets
Preparation of the
publication plan
Selection of publishers
Submitting the final work to
the publishers
Table 1: Detailed timeline of the tasks
(Source: Created by the author)
Publication Plan
All the secondary data which has been considered in the project background of the
paper are to be published to the future research purposes. All the data are very much reliable
as it is collected from peer reviewed sources. The data from this proposal can be used in
journal articles, conference paper, exhibition, creative thinking and design proposal. The
commissioner and the book publishers will be will targeted for the publication works. All
recent journals have been considered for the data collection procedure.
The five open questions which are have not been discussed in the paper are as followings:
How can BYOD help in minimising security issues of IoT?
How can open networks be a threat for IoT based devices?
What are the security steps taken by the corporate organization to deal with the
privacy issues of the IoT products used in their working environment?
How to disable universal plug and play?
How to create separate network for IoT based devices?

8PRIVACY ISSUES OF IOT
Conclusion
The proposal helps in understanding the numerous security as well as most of the
privacy related issues allied with IoT based systems which are used in corporate officialdoms
as well as in our society.
Conclusion
The proposal helps in understanding the numerous security as well as most of the
privacy related issues allied with IoT based systems which are used in corporate officialdoms
as well as in our society.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

9PRIVACY ISSUES OF IOT
References
Abomhara, M., 2015. Cyber security and the internet of things: vulnerabilities, threats,
intruders and attacks. Journal of Cyber Security and Mobility, 4(1), pp.65-88.
Alaba, F.A., Othman, M., Hashem, I.A.T. and Alotaibi, F., 2017. Internet of Things security:
A survey. Journal of Network and Computer Applications, 88, pp.10-28.
Alrawais, A., Alhothaily, A., Hu, C. and Cheng, X., 2017. Fog computing for the internet of
things: Security and privacy issues. IEEE Internet Computing, 21(2), pp.34-42.
Alur, R., Berger, E., Drobnis, A.W., Fix, L., Fu, K., Hager, G.D., Lopresti, D., Nahrstedt, K.,
Mynatt, E., Patel, S. and Rexford, J., 2016. Systems computing challenges in the Internet of
Things. arXiv preprint arXiv:1604.02980.
Andrea, I., Chrysostomou, C. and Hadjichristofi, G., 2015, July. Internet of Things: Security
vulnerabilities and challenges. In 2015 IEEE Symposium on Computers and Communication
(ISCC) (pp. 180-187). IEEE.
Arias, O., Wurm, J., Hoang, K. and Jin, Y., 2015. Privacy and security in internet of things
and wearable devices. IEEE Transactions on Multi-Scale Computing Systems, 1(2), pp.99-
109.
Borgohain, T., Kumar, U. and Sanyal, S., 2015. Survey of security and privacy issues of
internet of things. arXiv preprint arXiv:1501.02211.
Conti, M., Dehghantanha, A., Franke, K. and Watson, S., 2018. Internet of Things security
and forensics: Challenges and opportunities.
Dorri, A., Kanhere, S.S. and Jurdak, R., 2016. Blockchain in internet of things: challenges
and solutions. arXiv preprint arXiv:1608.05187.
References
Abomhara, M., 2015. Cyber security and the internet of things: vulnerabilities, threats,
intruders and attacks. Journal of Cyber Security and Mobility, 4(1), pp.65-88.
Alaba, F.A., Othman, M., Hashem, I.A.T. and Alotaibi, F., 2017. Internet of Things security:
A survey. Journal of Network and Computer Applications, 88, pp.10-28.
Alrawais, A., Alhothaily, A., Hu, C. and Cheng, X., 2017. Fog computing for the internet of
things: Security and privacy issues. IEEE Internet Computing, 21(2), pp.34-42.
Alur, R., Berger, E., Drobnis, A.W., Fix, L., Fu, K., Hager, G.D., Lopresti, D., Nahrstedt, K.,
Mynatt, E., Patel, S. and Rexford, J., 2016. Systems computing challenges in the Internet of
Things. arXiv preprint arXiv:1604.02980.
Andrea, I., Chrysostomou, C. and Hadjichristofi, G., 2015, July. Internet of Things: Security
vulnerabilities and challenges. In 2015 IEEE Symposium on Computers and Communication
(ISCC) (pp. 180-187). IEEE.
Arias, O., Wurm, J., Hoang, K. and Jin, Y., 2015. Privacy and security in internet of things
and wearable devices. IEEE Transactions on Multi-Scale Computing Systems, 1(2), pp.99-
109.
Borgohain, T., Kumar, U. and Sanyal, S., 2015. Survey of security and privacy issues of
internet of things. arXiv preprint arXiv:1501.02211.
Conti, M., Dehghantanha, A., Franke, K. and Watson, S., 2018. Internet of Things security
and forensics: Challenges and opportunities.
Dorri, A., Kanhere, S.S. and Jurdak, R., 2016. Blockchain in internet of things: challenges
and solutions. arXiv preprint arXiv:1608.05187.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

10PRIVACY ISSUES OF IOT
Hu, P., Ning, H., Qiu, T., Song, H., Wang, Y. and Yao, X., 2017. Security and privacy
preservation scheme of face identification and resolution framework using fog computing in
internet of things. IEEE Internet of Things Journal, 4(5), pp.1143-1155.
Kolias, C., Stavrou, A., Voas, J., Bojanova, I. and Kuhn, R., 2016. Learning internet-of-
things security" hands-on". IEEE Security & Privacy, 14(1), pp.37-46.
Kumar, S.A., Vealey, T. and Srivastava, H., 2016, January. Security in internet of things:
Challenges, solutions and future directions. In 2016 49th Hawaii International Conference on
System Sciences (HICSS) (pp. 5772-5781). IEEE.
Lee, K., Kim, D., Ha, D., Rajput, U. and Oh, H., 2015, September. On security and privacy
issues of fog computing supported Internet of Things environment. In 2015 6th International
Conference on the Network of the Future (NOF) (pp. 1-3). IEEE.
Li, S., Da Xu, L. and Zhao, S., 2015. The internet of things: a survey. Information Systems
Frontiers, 17(2), pp.243-259.
Li, S., Da Xu, L. and Zhao, S., 2018. 5G Internet of Things: A survey. Journal of Industrial
Information Integration, 10, pp.1-9.
Li, S., Tryfonas, T. and Li, H., 2016. The Internet of Things: a security point of view.
Internet Research, 26(2), pp.337-359.
Lin, J., Yu, W., Zhang, N., Yang, X., Zhang, H. and Zhao, W., 2017. A survey on internet of
things: Architecture, enabling technologies, security and privacy, and applications. IEEE
Internet of Things Journal, 4(5), pp.1125-1142.
Malina, L., Hajny, J., Fujdiak, R. and Hosek, J., 2016. On perspective of security and
privacy-preserving solutions in the internet of things. Computer Networks, 102, pp.83-95.
Hu, P., Ning, H., Qiu, T., Song, H., Wang, Y. and Yao, X., 2017. Security and privacy
preservation scheme of face identification and resolution framework using fog computing in
internet of things. IEEE Internet of Things Journal, 4(5), pp.1143-1155.
Kolias, C., Stavrou, A., Voas, J., Bojanova, I. and Kuhn, R., 2016. Learning internet-of-
things security" hands-on". IEEE Security & Privacy, 14(1), pp.37-46.
Kumar, S.A., Vealey, T. and Srivastava, H., 2016, January. Security in internet of things:
Challenges, solutions and future directions. In 2016 49th Hawaii International Conference on
System Sciences (HICSS) (pp. 5772-5781). IEEE.
Lee, K., Kim, D., Ha, D., Rajput, U. and Oh, H., 2015, September. On security and privacy
issues of fog computing supported Internet of Things environment. In 2015 6th International
Conference on the Network of the Future (NOF) (pp. 1-3). IEEE.
Li, S., Da Xu, L. and Zhao, S., 2015. The internet of things: a survey. Information Systems
Frontiers, 17(2), pp.243-259.
Li, S., Da Xu, L. and Zhao, S., 2018. 5G Internet of Things: A survey. Journal of Industrial
Information Integration, 10, pp.1-9.
Li, S., Tryfonas, T. and Li, H., 2016. The Internet of Things: a security point of view.
Internet Research, 26(2), pp.337-359.
Lin, J., Yu, W., Zhang, N., Yang, X., Zhang, H. and Zhao, W., 2017. A survey on internet of
things: Architecture, enabling technologies, security and privacy, and applications. IEEE
Internet of Things Journal, 4(5), pp.1125-1142.
Malina, L., Hajny, J., Fujdiak, R. and Hosek, J., 2016. On perspective of security and
privacy-preserving solutions in the internet of things. Computer Networks, 102, pp.83-95.

11PRIVACY ISSUES OF IOT
Maple, C., 2017. Security and privacy in the internet of things. Journal of Cyber Policy, 2(2),
pp.155-184.
Mehmood, Y., Ahmad, F., Yaqoob, I., Adnane, A., Imran, M. and Guizani, S., 2017. Internet-
of-things-based smart cities: Recent advances and challenges. IEEE Communications
Magazine, 55(9), pp.16-24.
Mendez, D.M., Papapanagiotou, I. and Yang, B., 2017. Internet of things: Survey on security
and privacy. arXiv preprint arXiv:1707.01879.
Sadeghi, A.R., Wachsmann, C. and Waidner, M., 2015, June. Security and privacy challenges
in industrial internet of things. In 2015 52nd ACM/EDAC/IEEE Design Automation
Conference (DAC) (pp. 1-6). IEEE.
Sfar, A.R., Natalizio, E., Challal, Y. and Chtourou, Z., 2018. A roadmap for security
challenges in the Internet of Things. Digital Communications and Networks, 4(2), pp.118-
137.
Sicari, S., Rizzardi, A., Grieco, L.A. and Coen-Porisini, A., 2015. Security, privacy and trust
in Internet of Things: The road ahead. Computer networks, 76, pp.146-164.
Stojkoska, B.L.R. and Trivodaliev, K.V., 2017. A review of Internet of Things for smart
home: Challenges and solutions. Journal of Cleaner Production, 140, pp.1454-1464.
Thierer, A.D., 2015. The internet of things and wearable technology: Addressing privacy and
security concerns without derailing innovation. Adam Thierer, The Internet of Things and
Wearable Technology: Addressing Privacy and Security Concerns without Derailing
Innovation, 21.
Weinberg, B.D., Milne, G.R., Andonova, Y.G. and Hajjat, F.M., 2015. Internet of Things:
Convenience vs. privacy and secrecy. Business Horizons, 58(6), pp.615-624.
Maple, C., 2017. Security and privacy in the internet of things. Journal of Cyber Policy, 2(2),
pp.155-184.
Mehmood, Y., Ahmad, F., Yaqoob, I., Adnane, A., Imran, M. and Guizani, S., 2017. Internet-
of-things-based smart cities: Recent advances and challenges. IEEE Communications
Magazine, 55(9), pp.16-24.
Mendez, D.M., Papapanagiotou, I. and Yang, B., 2017. Internet of things: Survey on security
and privacy. arXiv preprint arXiv:1707.01879.
Sadeghi, A.R., Wachsmann, C. and Waidner, M., 2015, June. Security and privacy challenges
in industrial internet of things. In 2015 52nd ACM/EDAC/IEEE Design Automation
Conference (DAC) (pp. 1-6). IEEE.
Sfar, A.R., Natalizio, E., Challal, Y. and Chtourou, Z., 2018. A roadmap for security
challenges in the Internet of Things. Digital Communications and Networks, 4(2), pp.118-
137.
Sicari, S., Rizzardi, A., Grieco, L.A. and Coen-Porisini, A., 2015. Security, privacy and trust
in Internet of Things: The road ahead. Computer networks, 76, pp.146-164.
Stojkoska, B.L.R. and Trivodaliev, K.V., 2017. A review of Internet of Things for smart
home: Challenges and solutions. Journal of Cleaner Production, 140, pp.1454-1464.
Thierer, A.D., 2015. The internet of things and wearable technology: Addressing privacy and
security concerns without derailing innovation. Adam Thierer, The Internet of Things and
Wearable Technology: Addressing Privacy and Security Concerns without Derailing
Innovation, 21.
Weinberg, B.D., Milne, G.R., Andonova, Y.G. and Hajjat, F.M., 2015. Internet of Things:
Convenience vs. privacy and secrecy. Business Horizons, 58(6), pp.615-624.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 13
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





