Assessing IoT Security and Risk Management for ABC Company
VerifiedAdded on 2023/01/12
|9
|2509
|92
Report
AI Summary
This report provides a comprehensive overview of the security and risk management challenges associated with Internet of Things (IoT) devices. It begins with an introduction to IoT devices, their applications, and the various types available, emphasizing their role in data collection. The report then delves into the attacks that IoT devices are vulnerable to, categorizing them into hardware interface, communication channels, and application/services attacks. Addressing these threats, the report outlines crucial countermeasures, including secure boot and firmware integrity, mutual authentication, and encryption. Furthermore, it explores authentication protocols like Constrained Application Protocol (CoAP) and Message Queueing Telemetry Transport (MQTT), explaining their functionalities and relevance in securing IoT communications. The conclusion stresses the importance of implementing these measures to protect data and ensure the secure operation of IoT devices, specifically highlighting their relevance for ABC company's data collection operations.

IS Security and Risk
Management
Management
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Table of Contents
INTRODUCTION...........................................................................................................................3
Types of Internet of Things (IoT) Devices and Their Applications............................................3
Attacks against Internet of Things (IoT) Devices........................................................................4
Countermeasures Against IoT Attacks........................................................................................5
Authentication Protocols for IoT Devices...................................................................................7
CONCLUSION................................................................................................................................8
REFERENCES................................................................................................................................9
INTRODUCTION...........................................................................................................................3
Types of Internet of Things (IoT) Devices and Their Applications............................................3
Attacks against Internet of Things (IoT) Devices........................................................................4
Countermeasures Against IoT Attacks........................................................................................5
Authentication Protocols for IoT Devices...................................................................................7
CONCLUSION................................................................................................................................8
REFERENCES................................................................................................................................9

INTRODUCTION
Due to the modern digital revolution and the widespread adoption of the internet all
around the globe, it has never been easier to facilitate communications between any two parties.
Though digital technologies have immensely eased the way in which we communicate, they also
present us with several challenges relating to how we ought to protect the integrity of
communicating messages from individuals or groups with harmful intentions (Ray, 2018). This
report assesses and evaluates the various privacy and security challenges present for IoT devices,
so that they can safely and securely be used by ABC company for their data collection
operations.
Types of Internet of Things (IoT) Devices and Their Applications
In layman’s terms Internet of Things (IoT) is a combined network created by
interconnected devices and sensors all of which record and share useful data about their
operations without any outside interference from humans. In today’s world, the Internet of
Things is a growing digital technology which aims at connecting all existing devices to the
implemented internet infrastructure in an effort to improve their performance and to provide their
users with operational data that can further to be used to enhance the device’s operations and
functions. IoT devices collect and share data amongst one another through the internet in an
attempt to provide their users with increased productivity and efficiency. Any digital and
sometimes even traditional devices that can be connected to the existing internet infrastructure is
capable of being Internet of Things device. An IoT device comprises of the existing hardware
necessary for the device’s operations in addition to a dedicated sensor which can record and
transmit data to other systems or devices by accessing the internet (Jeschke and et.al., 2017). IoT
devices come in various shapes and forms, but all of them have the same purpose to record and
share operational data between one another. This data can be used by other IoT devices to
improve their individual operations or can also be transmitted to humans who can analyse it to
gain insights about the device’s operations and how they can be improved in order to enhance the
device’s performance and efficiency or to decrease operational costs.
There are numerous types of IoT devices used around the world, each having their own
applications and providing their own advantages and disadvantages. As IoT devices provide a
Due to the modern digital revolution and the widespread adoption of the internet all
around the globe, it has never been easier to facilitate communications between any two parties.
Though digital technologies have immensely eased the way in which we communicate, they also
present us with several challenges relating to how we ought to protect the integrity of
communicating messages from individuals or groups with harmful intentions (Ray, 2018). This
report assesses and evaluates the various privacy and security challenges present for IoT devices,
so that they can safely and securely be used by ABC company for their data collection
operations.
Types of Internet of Things (IoT) Devices and Their Applications
In layman’s terms Internet of Things (IoT) is a combined network created by
interconnected devices and sensors all of which record and share useful data about their
operations without any outside interference from humans. In today’s world, the Internet of
Things is a growing digital technology which aims at connecting all existing devices to the
implemented internet infrastructure in an effort to improve their performance and to provide their
users with operational data that can further to be used to enhance the device’s operations and
functions. IoT devices collect and share data amongst one another through the internet in an
attempt to provide their users with increased productivity and efficiency. Any digital and
sometimes even traditional devices that can be connected to the existing internet infrastructure is
capable of being Internet of Things device. An IoT device comprises of the existing hardware
necessary for the device’s operations in addition to a dedicated sensor which can record and
transmit data to other systems or devices by accessing the internet (Jeschke and et.al., 2017). IoT
devices come in various shapes and forms, but all of them have the same purpose to record and
share operational data between one another. This data can be used by other IoT devices to
improve their individual operations or can also be transmitted to humans who can analyse it to
gain insights about the device’s operations and how they can be improved in order to enhance the
device’s performance and efficiency or to decrease operational costs.
There are numerous types of IoT devices used around the world, each having their own
applications and providing their own advantages and disadvantages. As IoT devices provide a
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

host of different applications to the users, they are used in all sectors of the economy from
environmental data gathering efforts by scientists to doctors using IoT devices for recording
patient’s medical health data to normal consumers using IoT devices to transform their
traditional households to smart homes where all major devices in the house are connected to the
internet and communicate with each other to make the life of residents much easier and efficient.
IoT devices are now also being implemented by governing authorities of developed countries to
transform entire cities into smart cities where multiple operational devices such as street lights,
traffic lights, meters, sensors all are connected to the internet and collect and share data with
each other to improve their performance and efficiency and reduce costs incurred by the
government (Christidis and Devetsikiotis, 2016). IoT devices are also used in industrial settings
where assembly line machinery is installed with sensors and connected to the internet with the
intention to provide operational data to industrial supervisors, through which they can gain
valuable insights about the kinds of malfunctioning occurring in the equipment and which
distinct parts need to be repaired or replaced in order to maximise their industrial performance
and efficiency. Owing to their simplicity and low usage costs, ABC company too uses various
types of IoT devices to facilitate their data collection operations.
Attacks against Internet of Things (IoT) Devices
One of the most prevalent barriers to the widespread adoption of IoT devices across the
world is the privacy and security issues, installation of these devices provides to their users. As is
most often the case for newly developed technologies, their development and innovation moves
at much quicker rate than the development of mechanisms and protocol needed to safeguard
these devices and consumers from external attacks. As these IoT devices are dumb machines
who are all connected to the internet to improve their operational performance and efficiency, it
also opens up these devices to hackers and individuals or groups with harmful intentions who
can disrupt their operations and communications as per their whims and requirements and wreak
havoc on the overarching system either for personal or financial gains. This is one of the most
prevalent concerns for ABC company too, as their IoT devices are open to attacks from external
sources which can have a massive impact on the organisation’s data collection operations.
According to recent research estimates the 98% of the communicating IoT devices do not
encrypt their transmission data as it is sent over the internet. This is a massive concern for user’s
privacy and security of the data as it is available for all who wish to see it on the internet
environmental data gathering efforts by scientists to doctors using IoT devices for recording
patient’s medical health data to normal consumers using IoT devices to transform their
traditional households to smart homes where all major devices in the house are connected to the
internet and communicate with each other to make the life of residents much easier and efficient.
IoT devices are now also being implemented by governing authorities of developed countries to
transform entire cities into smart cities where multiple operational devices such as street lights,
traffic lights, meters, sensors all are connected to the internet and collect and share data with
each other to improve their performance and efficiency and reduce costs incurred by the
government (Christidis and Devetsikiotis, 2016). IoT devices are also used in industrial settings
where assembly line machinery is installed with sensors and connected to the internet with the
intention to provide operational data to industrial supervisors, through which they can gain
valuable insights about the kinds of malfunctioning occurring in the equipment and which
distinct parts need to be repaired or replaced in order to maximise their industrial performance
and efficiency. Owing to their simplicity and low usage costs, ABC company too uses various
types of IoT devices to facilitate their data collection operations.
Attacks against Internet of Things (IoT) Devices
One of the most prevalent barriers to the widespread adoption of IoT devices across the
world is the privacy and security issues, installation of these devices provides to their users. As is
most often the case for newly developed technologies, their development and innovation moves
at much quicker rate than the development of mechanisms and protocol needed to safeguard
these devices and consumers from external attacks. As these IoT devices are dumb machines
who are all connected to the internet to improve their operational performance and efficiency, it
also opens up these devices to hackers and individuals or groups with harmful intentions who
can disrupt their operations and communications as per their whims and requirements and wreak
havoc on the overarching system either for personal or financial gains. This is one of the most
prevalent concerns for ABC company too, as their IoT devices are open to attacks from external
sources which can have a massive impact on the organisation’s data collection operations.
According to recent research estimates the 98% of the communicating IoT devices do not
encrypt their transmission data as it is sent over the internet. This is a massive concern for user’s
privacy and security of the data as it is available for all who wish to see it on the internet
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
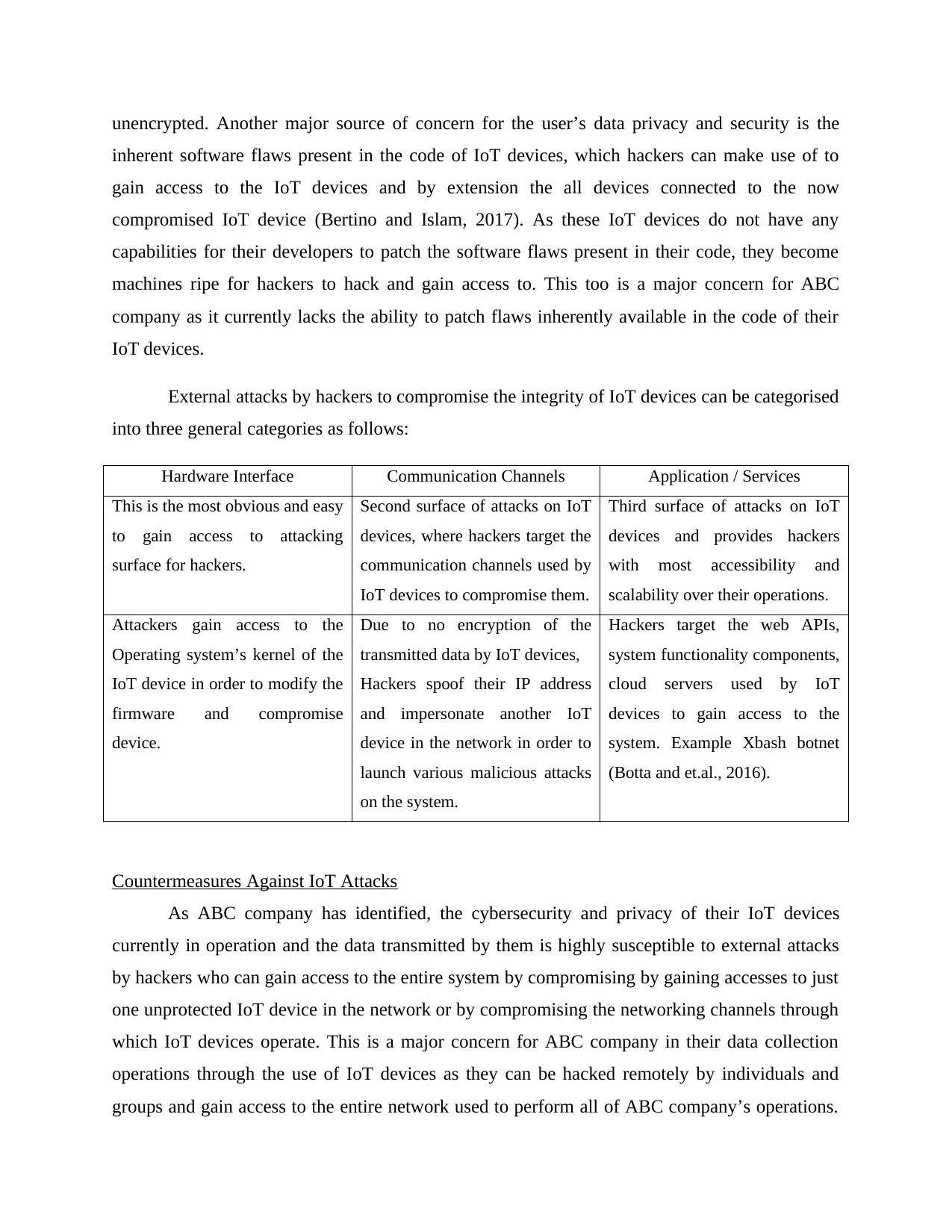
unencrypted. Another major source of concern for the user’s data privacy and security is the
inherent software flaws present in the code of IoT devices, which hackers can make use of to
gain access to the IoT devices and by extension the all devices connected to the now
compromised IoT device (Bertino and Islam, 2017). As these IoT devices do not have any
capabilities for their developers to patch the software flaws present in their code, they become
machines ripe for hackers to hack and gain access to. This too is a major concern for ABC
company as it currently lacks the ability to patch flaws inherently available in the code of their
IoT devices.
External attacks by hackers to compromise the integrity of IoT devices can be categorised
into three general categories as follows:
Hardware Interface Communication Channels Application / Services
This is the most obvious and easy
to gain access to attacking
surface for hackers.
Second surface of attacks on IoT
devices, where hackers target the
communication channels used by
IoT devices to compromise them.
Third surface of attacks on IoT
devices and provides hackers
with most accessibility and
scalability over their operations.
Attackers gain access to the
Operating system’s kernel of the
IoT device in order to modify the
firmware and compromise
device.
Due to no encryption of the
transmitted data by IoT devices,
Hackers spoof their IP address
and impersonate another IoT
device in the network in order to
launch various malicious attacks
on the system.
Hackers target the web APIs,
system functionality components,
cloud servers used by IoT
devices to gain access to the
system. Example Xbash botnet
(Botta and et.al., 2016).
Countermeasures Against IoT Attacks
As ABC company has identified, the cybersecurity and privacy of their IoT devices
currently in operation and the data transmitted by them is highly susceptible to external attacks
by hackers who can gain access to the entire system by compromising by gaining accesses to just
one unprotected IoT device in the network or by compromising the networking channels through
which IoT devices operate. This is a major concern for ABC company in their data collection
operations through the use of IoT devices as they can be hacked remotely by individuals and
groups and gain access to the entire network used to perform all of ABC company’s operations.
inherent software flaws present in the code of IoT devices, which hackers can make use of to
gain access to the IoT devices and by extension the all devices connected to the now
compromised IoT device (Bertino and Islam, 2017). As these IoT devices do not have any
capabilities for their developers to patch the software flaws present in their code, they become
machines ripe for hackers to hack and gain access to. This too is a major concern for ABC
company as it currently lacks the ability to patch flaws inherently available in the code of their
IoT devices.
External attacks by hackers to compromise the integrity of IoT devices can be categorised
into three general categories as follows:
Hardware Interface Communication Channels Application / Services
This is the most obvious and easy
to gain access to attacking
surface for hackers.
Second surface of attacks on IoT
devices, where hackers target the
communication channels used by
IoT devices to compromise them.
Third surface of attacks on IoT
devices and provides hackers
with most accessibility and
scalability over their operations.
Attackers gain access to the
Operating system’s kernel of the
IoT device in order to modify the
firmware and compromise
device.
Due to no encryption of the
transmitted data by IoT devices,
Hackers spoof their IP address
and impersonate another IoT
device in the network in order to
launch various malicious attacks
on the system.
Hackers target the web APIs,
system functionality components,
cloud servers used by IoT
devices to gain access to the
system. Example Xbash botnet
(Botta and et.al., 2016).
Countermeasures Against IoT Attacks
As ABC company has identified, the cybersecurity and privacy of their IoT devices
currently in operation and the data transmitted by them is highly susceptible to external attacks
by hackers who can gain access to the entire system by compromising by gaining accesses to just
one unprotected IoT device in the network or by compromising the networking channels through
which IoT devices operate. This is a major concern for ABC company in their data collection
operations through the use of IoT devices as they can be hacked remotely by individuals and
groups and gain access to the entire network used to perform all of ABC company’s operations.

In order to safeguard themselves against external attempts by hackers to compromise the
operations of their IoT devices and gain access to their entire operational system, ABC company
needs to follow the following countermeasures in order to ensure the security and privacy of
their operations and of their transmitted operational data over the internet.
Secure Boot and Firmware Integrity: This is technique ABC company can implement in its IoT
devices to deter the attempts of external hackers looking to compromise ABC company’s IoT
devices and networking systems. Secure boot is a booting process for the IoT devices, which
makes use of cryptographic code signing techniques with the intention to ensure that the IoT
device executes genuine code which is created only by the device’s manufacturers or a trusted
third party source (Sethi and Sarangi, 2017). Using secure boot allows users to safeguard their
IoT devices against hackers who wish to gain access to the device by deleting the firmware
installed and running their own malicious code on the IoT device for nefarious purposes.
Mutual Authentication: This is another safety measure ABC company can implement into their
operations and network to better safeguard their operations against external intrusions by
hackers. This method requires all IoT devices of ABC company to be authenticated by the
network before they can connect to the network in order to do their data collection and sharing
operations. This mutual authentication process would allow only genuine ABC company’s IoT
devices to communicate through their network and safeguard their operations against hackers
who impersonate being one of their IoT devices in order to gain access to their network. To
implement mutual authentication ABC company’s IT department can make use of cryptographic
algorithms that make use of both symmetric and asymmetric keys such as Secure Hash
Algorithm (SHA-x).
Encryption: ABC company can also protect the data transmitted by their IoT devices by
encrypting it in order to deter hackers from compromising their system. Encryption would ensure
that only genuine recipients associated with ABC company can access transmitted data through
the use of secret decryption key.
Authentication Protocols for IoT Devices
There are various device management, communication, authentication, networking and
connectivity protocols available to effectively and efficiently facilitate the operations of IoT
operations of their IoT devices and gain access to their entire operational system, ABC company
needs to follow the following countermeasures in order to ensure the security and privacy of
their operations and of their transmitted operational data over the internet.
Secure Boot and Firmware Integrity: This is technique ABC company can implement in its IoT
devices to deter the attempts of external hackers looking to compromise ABC company’s IoT
devices and networking systems. Secure boot is a booting process for the IoT devices, which
makes use of cryptographic code signing techniques with the intention to ensure that the IoT
device executes genuine code which is created only by the device’s manufacturers or a trusted
third party source (Sethi and Sarangi, 2017). Using secure boot allows users to safeguard their
IoT devices against hackers who wish to gain access to the device by deleting the firmware
installed and running their own malicious code on the IoT device for nefarious purposes.
Mutual Authentication: This is another safety measure ABC company can implement into their
operations and network to better safeguard their operations against external intrusions by
hackers. This method requires all IoT devices of ABC company to be authenticated by the
network before they can connect to the network in order to do their data collection and sharing
operations. This mutual authentication process would allow only genuine ABC company’s IoT
devices to communicate through their network and safeguard their operations against hackers
who impersonate being one of their IoT devices in order to gain access to their network. To
implement mutual authentication ABC company’s IT department can make use of cryptographic
algorithms that make use of both symmetric and asymmetric keys such as Secure Hash
Algorithm (SHA-x).
Encryption: ABC company can also protect the data transmitted by their IoT devices by
encrypting it in order to deter hackers from compromising their system. Encryption would ensure
that only genuine recipients associated with ABC company can access transmitted data through
the use of secret decryption key.
Authentication Protocols for IoT Devices
There are various device management, communication, authentication, networking and
connectivity protocols available to effectively and efficiently facilitate the operations of IoT
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

devices across the globe. The specific nature of protocol in application depends on the needs and
requirements of the users and their IoT devices and operations. Authentication protocols for IoT
are as follows:
Constrained Application Protocol (CoAP): CoAP is a specialised authentication protocol used
by IoT devices during transfer of data through the internet. It enables constrained IoT devices
and peripheries to connect through constrained networks that possess low network bandwidth
and high congestion. CoAP is usually used for transmissions made between two machines or IoT
devices and provides asynchronous message exchanging capabilities to its users (Alaba and
et.al., 2017). When CoAP is implemented, IoT sensors and devices are share their transmitted
data by passing the information in the network as part of a system. CoAP uses UDP to secure the
transmission of data by IoT devices. The protocol allows high reliability of transmission in low
bandwidth and high congestion networks.
Message Queueing Telemetry Transport (MQTT): This is a lightweight messaging
authentication protocol that makes of dedicated publish and subscribe operations between the
IoT devices and operational servers in order to secure data transmission through the network.
Publish operation denotes to the server that an IoT device wishes to transmit it data while the
subscribe operates denotes to the server when an IoT device in the system wishes to receive data.
MQTT protocol is designed to perform in situations where there is less bandwidth available for
the transmission of data between IoT devices and server at little operational energy costs
incurred. The central communication server also known as broker is responsible for
communicating the relevant information to senders and receivers based on the dedicated publish
and subscribe operations integrated within the protocol’s functions. Each sender of transmitted
message to the broker includes a topic in the transmitted message which contains routing
information necessary for the broker’s operations (Lin and et.al., 2017). Receivers who wish to
receive transmitted messages send subscribe operation to broker along with relevant topic. The
broker matches topic wanted by receiving device to topics sent by sender and transmits all
relevant information.
requirements of the users and their IoT devices and operations. Authentication protocols for IoT
are as follows:
Constrained Application Protocol (CoAP): CoAP is a specialised authentication protocol used
by IoT devices during transfer of data through the internet. It enables constrained IoT devices
and peripheries to connect through constrained networks that possess low network bandwidth
and high congestion. CoAP is usually used for transmissions made between two machines or IoT
devices and provides asynchronous message exchanging capabilities to its users (Alaba and
et.al., 2017). When CoAP is implemented, IoT sensors and devices are share their transmitted
data by passing the information in the network as part of a system. CoAP uses UDP to secure the
transmission of data by IoT devices. The protocol allows high reliability of transmission in low
bandwidth and high congestion networks.
Message Queueing Telemetry Transport (MQTT): This is a lightweight messaging
authentication protocol that makes of dedicated publish and subscribe operations between the
IoT devices and operational servers in order to secure data transmission through the network.
Publish operation denotes to the server that an IoT device wishes to transmit it data while the
subscribe operates denotes to the server when an IoT device in the system wishes to receive data.
MQTT protocol is designed to perform in situations where there is less bandwidth available for
the transmission of data between IoT devices and server at little operational energy costs
incurred. The central communication server also known as broker is responsible for
communicating the relevant information to senders and receivers based on the dedicated publish
and subscribe operations integrated within the protocol’s functions. Each sender of transmitted
message to the broker includes a topic in the transmitted message which contains routing
information necessary for the broker’s operations (Lin and et.al., 2017). Receivers who wish to
receive transmitted messages send subscribe operation to broker along with relevant topic. The
broker matches topic wanted by receiving device to topics sent by sender and transmits all
relevant information.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

CONCLUSION
From this report, it can be concluded that it is immensely necessary for ABC company to
implement countermeasures designed to protect its IoT devices from various cyber attacks and
intrusions in order to improve their data collection operations. This report studies the different
types of IoT devices and their applications along with various kinds of cyber attacks against IoT
devices. Then the report identifies and analyses the countermeasures and formal security
protection methods which ABC company can implement to improve their data collection
operations. Finally the report evaluates two authentication protocols used by IoT devices.
From this report, it can be concluded that it is immensely necessary for ABC company to
implement countermeasures designed to protect its IoT devices from various cyber attacks and
intrusions in order to improve their data collection operations. This report studies the different
types of IoT devices and their applications along with various kinds of cyber attacks against IoT
devices. Then the report identifies and analyses the countermeasures and formal security
protection methods which ABC company can implement to improve their data collection
operations. Finally the report evaluates two authentication protocols used by IoT devices.

REFERENCES
Books and Journals
Alaba, F.A. and et.al., 2017. Internet of Things security: A survey. Journal of Network and
Computer Applications. 88. pp.10-28.
Bertino, E. and Islam, N., 2017. Botnets and internet of things security. Computer. 50(2). pp.76-
79.
Botta, A. and et.al., 2016. Integration of cloud computing and internet of things: a survey. Future
generation computer systems. 56. pp.684-700.
Christidis, K. and Devetsikiotis, M., 2016. Blockchains and smart contracts for the internet of
things. Ieee Access. 4. pp.2292-2303.
Jeschke, S. and et.al., 2017. Industrial internet of things and cyber manufacturing systems.
In Industrial internet of things (pp. 3-19). Springer, Cham.
Lin, J. and et.al., 2017. A survey on internet of things: Architecture, enabling technologies,
security and privacy, and applications. IEEE Internet of Things Journal. 4(5). pp.1125-
1142.
Ray, P.P., 2018. A survey on Internet of Things architectures. Journal of King Saud University-
Computer and Information Sciences. 30(3). pp.291-319.
Sethi, P. and Sarangi, S.R., 2017. Internet of things: architectures, protocols, and
applications. Journal of Electrical and Computer Engineering. 2017.
Books and Journals
Alaba, F.A. and et.al., 2017. Internet of Things security: A survey. Journal of Network and
Computer Applications. 88. pp.10-28.
Bertino, E. and Islam, N., 2017. Botnets and internet of things security. Computer. 50(2). pp.76-
79.
Botta, A. and et.al., 2016. Integration of cloud computing and internet of things: a survey. Future
generation computer systems. 56. pp.684-700.
Christidis, K. and Devetsikiotis, M., 2016. Blockchains and smart contracts for the internet of
things. Ieee Access. 4. pp.2292-2303.
Jeschke, S. and et.al., 2017. Industrial internet of things and cyber manufacturing systems.
In Industrial internet of things (pp. 3-19). Springer, Cham.
Lin, J. and et.al., 2017. A survey on internet of things: Architecture, enabling technologies,
security and privacy, and applications. IEEE Internet of Things Journal. 4(5). pp.1125-
1142.
Ray, P.P., 2018. A survey on Internet of Things architectures. Journal of King Saud University-
Computer and Information Sciences. 30(3). pp.291-319.
Sethi, P. and Sarangi, S.R., 2017. Internet of things: architectures, protocols, and
applications. Journal of Electrical and Computer Engineering. 2017.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 9
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





