Comprehensive Analysis of IoT Security: Risks, Threats, and Trends
VerifiedAdded on 2022/10/18
|16
|3575
|31
Report
AI Summary
This report provides a comprehensive overview of the security challenges within the Internet of Things (IoT). It explores the applications of IoT across various sectors, including healthcare, home automation, industry, and agriculture, while emphasizing the increasing importance of data security. The report delves into the types of risks associated with IoT, such as computer attacks, software vulnerabilities, and data interception, along with the threats posed by unsecured web and cloud interfaces, lack of encryption, and insufficient authentication. It analyzes countermeasures like data encryption (SSL/TLS), strong authentication, and secure cloud configurations. The report also examines future trends, including the convergence of big data with IoT, the rise of smart homes, and the adoption of IoT in healthcare for remote patient monitoring. Furthermore, the report underscores the importance of ethical considerations and data privacy in the design and implementation of IoT systems. The report aims to highlight the necessity of a proactive and multi-faceted approach to ensure the secure and ethical deployment of IoT technologies.

Internet of Things
Name
Institution
Professor
Course
Date
Name
Institution
Professor
Course
Date
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Abstract
The Internet of Things (IoT) has made possible for devices to communicate over the internet and
share data without any human intervention. In this regard, most of the studies on IoT have
concentrated on its use and application but security concerns have not been addressed. For the
secure implementation of IoT, security experts should be involved during and after its
implementation. The review of the past studies focuses on security aspects such as types of risks,
threats, security control and techniques that should be implemented to secure IoT infrastructure.
Countermeasures such data encryption during transmission, network protection through
SSL/TLS and creating strong authentication credentials to avoid SQL injection and cross-site
scripting. Similarly, the trends on the IoT has been analyzed to come up with expected changes
that might come up as a result of adopting required security measures. The security measures
such as incorporating Blockchain technology has been addressed to make sure IoT security is
given the highest priority.
The Internet of Things (IoT) has made possible for devices to communicate over the internet and
share data without any human intervention. In this regard, most of the studies on IoT have
concentrated on its use and application but security concerns have not been addressed. For the
secure implementation of IoT, security experts should be involved during and after its
implementation. The review of the past studies focuses on security aspects such as types of risks,
threats, security control and techniques that should be implemented to secure IoT infrastructure.
Countermeasures such data encryption during transmission, network protection through
SSL/TLS and creating strong authentication credentials to avoid SQL injection and cross-site
scripting. Similarly, the trends on the IoT has been analyzed to come up with expected changes
that might come up as a result of adopting required security measures. The security measures
such as incorporating Blockchain technology has been addressed to make sure IoT security is
given the highest priority.

Contents
Abstract......................................................................................................................................................2
Introduction...............................................................................................................................................3
Application of Internet of Things.............................................................................................................4
Types of Risks in the Internet of Things..................................................................................................5
Threats and countermeasures on the Internet of Things........................................................................6
A comparison of cybersecurity threats....................................................................................................9
Future Trends in Internet of Things......................................................................................................10
Conclusion................................................................................................................................................11
Bibliography............................................................................................................................................12
Appendix..................................................................................................................................................13
Abstract......................................................................................................................................................2
Introduction...............................................................................................................................................3
Application of Internet of Things.............................................................................................................4
Types of Risks in the Internet of Things..................................................................................................5
Threats and countermeasures on the Internet of Things........................................................................6
A comparison of cybersecurity threats....................................................................................................9
Future Trends in Internet of Things......................................................................................................10
Conclusion................................................................................................................................................11
Bibliography............................................................................................................................................12
Appendix..................................................................................................................................................13
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Introduction
The paper would highlight security and ethical issues on the Internet of Things (IoT). It
would majorly focus on data collection, transmission and protection. With IoT, it has been
possible to automate most of the electrical appliances to communicate with each other. When
addressing IoT, security concerns have not been dealt with adequately making it difficult for
users to decide which security parameters to focus on during its implementation (Leloglu 2017,
pp. 121-122).
The security of on IoT cannot be addressed without addressing ethical concerns which
may arise from the implementation and use of the Internet of Things. The topic is very important
because of the ever-increasing cybersecurity attacks on Internet of Things data and devices
(Leloglu 2017, pp. 121-122). It is very sensitive to technological and social aspect due to the
impact it has on personal data and IoT devices.
The article would cover the overview of IoT, its benefits in both local and industrial use
and application in the key sectors of the economy. First, the application of the Internet of Things
in the various economic sectors and the impact (Allhoff & Henschke 2018, pp. 56). Next, the
evolution of the Internet of Things in terms of legislation, security and ethical concerns. Finally,
the types of risks involved and countermeasures to protect data privacy would be substantially
discussed.
The position of the paper is to shed light on the security threats, data protection, and
privacy of data, ethical issues and trends on the Internet of Things (IoT). The discussion would
be based on, security threats, data protection and countermeasures in security data collected over
the IoT.
The paper would highlight security and ethical issues on the Internet of Things (IoT). It
would majorly focus on data collection, transmission and protection. With IoT, it has been
possible to automate most of the electrical appliances to communicate with each other. When
addressing IoT, security concerns have not been dealt with adequately making it difficult for
users to decide which security parameters to focus on during its implementation (Leloglu 2017,
pp. 121-122).
The security of on IoT cannot be addressed without addressing ethical concerns which
may arise from the implementation and use of the Internet of Things. The topic is very important
because of the ever-increasing cybersecurity attacks on Internet of Things data and devices
(Leloglu 2017, pp. 121-122). It is very sensitive to technological and social aspect due to the
impact it has on personal data and IoT devices.
The article would cover the overview of IoT, its benefits in both local and industrial use
and application in the key sectors of the economy. First, the application of the Internet of Things
in the various economic sectors and the impact (Allhoff & Henschke 2018, pp. 56). Next, the
evolution of the Internet of Things in terms of legislation, security and ethical concerns. Finally,
the types of risks involved and countermeasures to protect data privacy would be substantially
discussed.
The position of the paper is to shed light on the security threats, data protection, and
privacy of data, ethical issues and trends on the Internet of Things (IoT). The discussion would
be based on, security threats, data protection and countermeasures in security data collected over
the IoT.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Application of Internet of Things
Ineffective security on the interconnection of devices results in serious data breaches
mostly on personal information (Baldini et al. 2018, pp. 12). First, the healthcare industry has the
highest number of interconnected devices sharing sensitive data from either hospitals to patients
and vice versa. The data shared over the interconnected devices consist of personal information
and very sensitive health-related data which should remain confidential to the patient. Failing to
secure such data means individual healthcare status might end up in the public domain. The data
can be used by different people with the motives of victimizing the patient.
Next, IoT has been used in automating home appliances making it possible to eliminate
repetitive jobs done by human beings (Miraz et al. 2018, pp. 68). This helps to reduce the
number of house assistant which might seem expensive. The home appliance has been automated
and they are able to share data between interconnected devices such as bulbs, microwaves,
CCTVS and televisions. On the same note, IoT has been used in the industry to distribute
internet in the cities by expanding its coverage. It is only through the interconnection of
networked devices that makes possible to distribute network on an entire city.
Finally, the Internet of Things (IoT) has been implemented on the agricultural sector to
determine soil nutrients, moisture content and fertilizer level (Kang et al 2015, pp. 118). By
consolidating key agricultural aspects, it has been possible to increase production. In turn,
farmers are able to increase profit margin which contributes greatly to state economic growth.
With all these applications, the security of the IoT should be considered to make sure data
privacy has been given the highest priority.
Ineffective security on the interconnection of devices results in serious data breaches
mostly on personal information (Baldini et al. 2018, pp. 12). First, the healthcare industry has the
highest number of interconnected devices sharing sensitive data from either hospitals to patients
and vice versa. The data shared over the interconnected devices consist of personal information
and very sensitive health-related data which should remain confidential to the patient. Failing to
secure such data means individual healthcare status might end up in the public domain. The data
can be used by different people with the motives of victimizing the patient.
Next, IoT has been used in automating home appliances making it possible to eliminate
repetitive jobs done by human beings (Miraz et al. 2018, pp. 68). This helps to reduce the
number of house assistant which might seem expensive. The home appliance has been automated
and they are able to share data between interconnected devices such as bulbs, microwaves,
CCTVS and televisions. On the same note, IoT has been used in the industry to distribute
internet in the cities by expanding its coverage. It is only through the interconnection of
networked devices that makes possible to distribute network on an entire city.
Finally, the Internet of Things (IoT) has been implemented on the agricultural sector to
determine soil nutrients, moisture content and fertilizer level (Kang et al 2015, pp. 118). By
consolidating key agricultural aspects, it has been possible to increase production. In turn,
farmers are able to increase profit margin which contributes greatly to state economic growth.
With all these applications, the security of the IoT should be considered to make sure data
privacy has been given the highest priority.

Types of Risks in the Internet of Things
It is obvious that cybersecurity related to IoT have been classified differently as they
occur at different levels. Some of these risks are; computer attacks which have been the most
rampant form of the cybercriminal. Computer attacks can be Denial of Service (DoS) attacks,
spreading of malware in IoT, data privacy infiltrations and electronic component modification
(Husamuddin & Qayyum 2017, pp. 94). In this case, unauthorized users try to gain access to the
interconnection of devices with a specific target of compromising the entire system.
Next, according to Kumar & Patel (2014, pp. 22), software vulnerabilities running on the
devices connected to the Internet of Things (IoT) poses major threats to data. Some devices that
constitute IoT require regular software updates to keep every piece of data secure and free from
intrusion. The security of the data collected by smart devices can be secure if the software
remains updated, scanning of interconnected devices is done frequently, security testing such as
penetration testing is done and necessary configurations are done on these devices.
Lastly, data interception between communicating devices. Once data has been collected
by any device, it should be shared with other devices for various uses in the system (Kumar &
Patel 2014, pp. 22). During transmission of data, it is possible some unauthorized interested third
parties are snooping on the data for personal gains. In this regard, data security needs to be
accorded the necessary preventive access measures to counter any external threat. This can only
be achieved by making sure all parties are equipped with the necessary basic skills to monitor
and counter any form of the data breach.
It is obvious that cybersecurity related to IoT have been classified differently as they
occur at different levels. Some of these risks are; computer attacks which have been the most
rampant form of the cybercriminal. Computer attacks can be Denial of Service (DoS) attacks,
spreading of malware in IoT, data privacy infiltrations and electronic component modification
(Husamuddin & Qayyum 2017, pp. 94). In this case, unauthorized users try to gain access to the
interconnection of devices with a specific target of compromising the entire system.
Next, according to Kumar & Patel (2014, pp. 22), software vulnerabilities running on the
devices connected to the Internet of Things (IoT) poses major threats to data. Some devices that
constitute IoT require regular software updates to keep every piece of data secure and free from
intrusion. The security of the data collected by smart devices can be secure if the software
remains updated, scanning of interconnected devices is done frequently, security testing such as
penetration testing is done and necessary configurations are done on these devices.
Lastly, data interception between communicating devices. Once data has been collected
by any device, it should be shared with other devices for various uses in the system (Kumar &
Patel 2014, pp. 22). During transmission of data, it is possible some unauthorized interested third
parties are snooping on the data for personal gains. In this regard, data security needs to be
accorded the necessary preventive access measures to counter any external threat. This can only
be achieved by making sure all parties are equipped with the necessary basic skills to monitor
and counter any form of the data breach.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Threats and countermeasures on the Internet of Things
Unsecured web interface which makes their connection to the IoT infrastructure. Through
unsecured web interfaces, it is possible to interact with devices but caution should be taken to
prevent cyber attackers from gaining access to infrastructure (Farooq et al. 2015, pp. 3-4). Some
of the security vulnerabilities that can result to data breaches over the web are; use of weak
access credentials and setting default web access passwords, database SQL injections, cross-site
scripting which can take place from both system management and users level and session
management. The insecure web interface can be addressed by implementing strong web access
credentials, changing of default passwords after initial account setup, making sure web interfaces
are free from SQL injections and cross-site scripting and ensuring systems prevents the use of
weak passwords.
Failing to encrypt data during storage and transmission leaves it vulnerable to
eavesdropping and interception (Kajtazi et al. 2018, pp. 12). The captured data can be used by
the intruder to either sabotage the system or victimize other people after gaining access to
confidential data. Some of the network vulnerabilities which can result in such data breaches are;
poor SSL/TLS implementation, failing to encrypt data services over the internet and using local
area network with unencrypted services. Data encryption issues can be resolved by making sure
data transmission over the internet is securely encrypted by SSL and TLS protocols. It can also
be protected by making sure multiple encryption standards are combined and using international
accepted standards. Data encryption remains the only guaranteed mechanism of securing data
because it is very difficult for any unauthorized user to crack the encryption technique required
to decrypt the data (Alandjani 2018, pp. 234).
Unsecured web interface which makes their connection to the IoT infrastructure. Through
unsecured web interfaces, it is possible to interact with devices but caution should be taken to
prevent cyber attackers from gaining access to infrastructure (Farooq et al. 2015, pp. 3-4). Some
of the security vulnerabilities that can result to data breaches over the web are; use of weak
access credentials and setting default web access passwords, database SQL injections, cross-site
scripting which can take place from both system management and users level and session
management. The insecure web interface can be addressed by implementing strong web access
credentials, changing of default passwords after initial account setup, making sure web interfaces
are free from SQL injections and cross-site scripting and ensuring systems prevents the use of
weak passwords.
Failing to encrypt data during storage and transmission leaves it vulnerable to
eavesdropping and interception (Kajtazi et al. 2018, pp. 12). The captured data can be used by
the intruder to either sabotage the system or victimize other people after gaining access to
confidential data. Some of the network vulnerabilities which can result in such data breaches are;
poor SSL/TLS implementation, failing to encrypt data services over the internet and using local
area network with unencrypted services. Data encryption issues can be resolved by making sure
data transmission over the internet is securely encrypted by SSL and TLS protocols. It can also
be protected by making sure multiple encryption standards are combined and using international
accepted standards. Data encryption remains the only guaranteed mechanism of securing data
because it is very difficult for any unauthorized user to crack the encryption technique required
to decrypt the data (Alandjani 2018, pp. 234).
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Collection of personal and sensitive data without proper protection mechanisms (Zheng
et al. 2018, pp. 200). The nature of the collected data can be categorized from the onset of the
project depending on the devices involved. Security vulnerabilities that result in data privacy
issues include collecting sensitive data without having proper technological techniques to secure
it. To secure the data, the following measures can be put in place; only the important data related
to the interconnected devices need to be collected, ensure any piece of data collected is properly
encrypted with strong decryption techniques and making sure only authorized data users are
given the access privileges (Tanaka et al. 2016, pp. 359).
Unsecured cloud interface which is used as a point of interaction devices. Cloud interface
insecurity can be caused by issues such as exposing account credentials to all network users,
failing to lock devices and enumeration of the accounts (Zheng et al. 2018, pp. 200). To protect
IoT infrastructure from insecure cloud interfaces, users are advised to make sure default user
credentials are changed frequently, implementing two-factor user authentication technique,
protecting cloud interfaces to make sure they are free from SQL injections and cross-site
scripting and setting up account lock after three login attempts are made without success.
The lack of sufficient authorization and authentication to the IoT infrastructure and
networks (Lee & Kim 2017, pp. 134-135). Some of the weaknesses that create these
vulnerabilities are; insufficient complexity of passwords by both administrators and users, failure
to implement effective role-based system access controls and insecure password recovery
techniques. To secure IoT infrastructure from these vulnerabilities, security experts should
enforce the creation of strong passwords, make sure system access controls in place are quite
effective, enforce implementation of two-factor authentication techniques and provide suitable
password configuration controls.
et al. 2018, pp. 200). The nature of the collected data can be categorized from the onset of the
project depending on the devices involved. Security vulnerabilities that result in data privacy
issues include collecting sensitive data without having proper technological techniques to secure
it. To secure the data, the following measures can be put in place; only the important data related
to the interconnected devices need to be collected, ensure any piece of data collected is properly
encrypted with strong decryption techniques and making sure only authorized data users are
given the access privileges (Tanaka et al. 2016, pp. 359).
Unsecured cloud interface which is used as a point of interaction devices. Cloud interface
insecurity can be caused by issues such as exposing account credentials to all network users,
failing to lock devices and enumeration of the accounts (Zheng et al. 2018, pp. 200). To protect
IoT infrastructure from insecure cloud interfaces, users are advised to make sure default user
credentials are changed frequently, implementing two-factor user authentication technique,
protecting cloud interfaces to make sure they are free from SQL injections and cross-site
scripting and setting up account lock after three login attempts are made without success.
The lack of sufficient authorization and authentication to the IoT infrastructure and
networks (Lee & Kim 2017, pp. 134-135). Some of the weaknesses that create these
vulnerabilities are; insufficient complexity of passwords by both administrators and users, failure
to implement effective role-based system access controls and insecure password recovery
techniques. To secure IoT infrastructure from these vulnerabilities, security experts should
enforce the creation of strong passwords, make sure system access controls in place are quite
effective, enforce implementation of two-factor authentication techniques and provide suitable
password configuration controls.
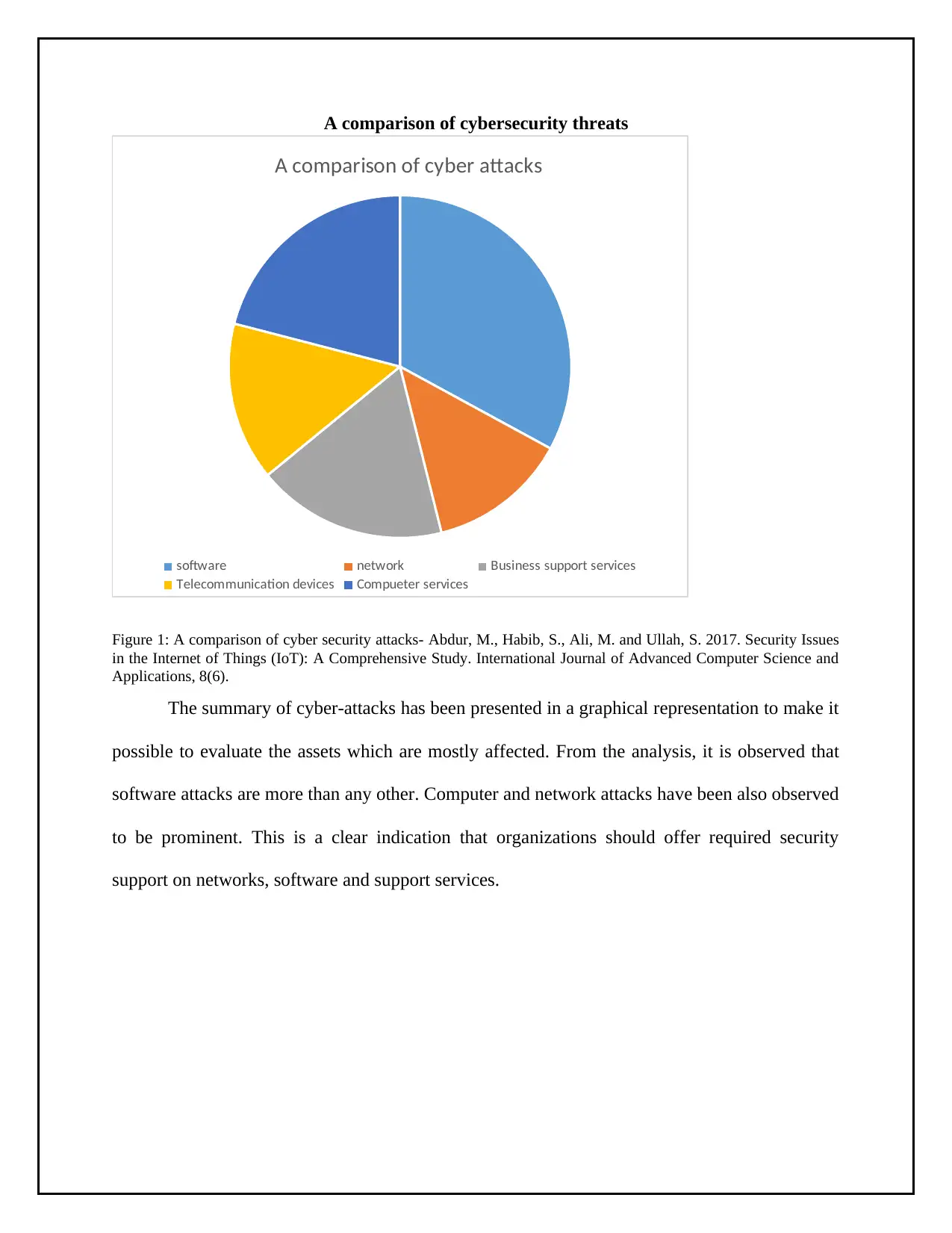
A comparison of cybersecurity threats
A comparison of cyber attacks
software network Business support services
Telecommunication devices Compueter services
Figure 1: A comparison of cyber security attacks- Abdur, M., Habib, S., Ali, M. and Ullah, S. 2017. Security Issues
in the Internet of Things (IoT): A Comprehensive Study. International Journal of Advanced Computer Science and
Applications, 8(6).
The summary of cyber-attacks has been presented in a graphical representation to make it
possible to evaluate the assets which are mostly affected. From the analysis, it is observed that
software attacks are more than any other. Computer and network attacks have been also observed
to be prominent. This is a clear indication that organizations should offer required security
support on networks, software and support services.
A comparison of cyber attacks
software network Business support services
Telecommunication devices Compueter services
Figure 1: A comparison of cyber security attacks- Abdur, M., Habib, S., Ali, M. and Ullah, S. 2017. Security Issues
in the Internet of Things (IoT): A Comprehensive Study. International Journal of Advanced Computer Science and
Applications, 8(6).
The summary of cyber-attacks has been presented in a graphical representation to make it
possible to evaluate the assets which are mostly affected. From the analysis, it is observed that
software attacks are more than any other. Computer and network attacks have been also observed
to be prominent. This is a clear indication that organizations should offer required security
support on networks, software and support services.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Future Trends in Internet of Things
First, the convergence of big data on the Internet of Things (IoT). Ideally, it does not
focus on changing the business process but has some impact on the amount of data generated
(Razzaq et al. 2017, pp. 384). The main reason behind big data is to support large-scale storage
of data and perform an analysis of which data might be useful when extracted through IoT. The
big data and IoT have a direct correlation in that so many interconnected devices are being used
to access and extract data from the big data.
Next, smart home demand is expected to rise over time. Through the use of Nano-
technology device interconnections is expected to rise as more programmable devices are being
invented for both local and large-scale consumption (Abdul-Ghani & Konstantas 2019, pp. 22).
As smart homes demand increase, devices are expected to become more intelligent over time and
the device would be able to direct people on several issues rather than people directing the
devices.
Further, the adoption of the Internet of Things (IoT) in the healthcare industry to support
remote patient monitoring. Patients monitoring through wearable or implanted devices have been
adopted to reduce hospital congestion from outpatients’ visits. Doctors are able to monitor and
prescribe patients while at home and where possible advice patients to visit hospitals for close
supervision. As this technology is evident in only developed countries, it has not been the norm
in most parts of Australian countries (Yousuf et al. 2015, pp. 611).
Similarly, the growth of the Internet of Things (IoT) compared to other forms of
technology in the industry. IoT will continue to connect to a large pool of interconnected devices
to either receive data from other users (Ziegeldorf et al. 2014, pp. 2728). The data can be either
from other users or devices which have been automated to send and collect information from
First, the convergence of big data on the Internet of Things (IoT). Ideally, it does not
focus on changing the business process but has some impact on the amount of data generated
(Razzaq et al. 2017, pp. 384). The main reason behind big data is to support large-scale storage
of data and perform an analysis of which data might be useful when extracted through IoT. The
big data and IoT have a direct correlation in that so many interconnected devices are being used
to access and extract data from the big data.
Next, smart home demand is expected to rise over time. Through the use of Nano-
technology device interconnections is expected to rise as more programmable devices are being
invented for both local and large-scale consumption (Abdul-Ghani & Konstantas 2019, pp. 22).
As smart homes demand increase, devices are expected to become more intelligent over time and
the device would be able to direct people on several issues rather than people directing the
devices.
Further, the adoption of the Internet of Things (IoT) in the healthcare industry to support
remote patient monitoring. Patients monitoring through wearable or implanted devices have been
adopted to reduce hospital congestion from outpatients’ visits. Doctors are able to monitor and
prescribe patients while at home and where possible advice patients to visit hospitals for close
supervision. As this technology is evident in only developed countries, it has not been the norm
in most parts of Australian countries (Yousuf et al. 2015, pp. 611).
Similarly, the growth of the Internet of Things (IoT) compared to other forms of
technology in the industry. IoT will continue to connect to a large pool of interconnected devices
to either receive data from other users (Ziegeldorf et al. 2014, pp. 2728). The data can be either
from other users or devices which have been automated to send and collect information from
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

other devices. It would be good to assume IoT would continue growing to different fields such as
artificial intelligence and it will be a matter of time before devices start being controlled over the
internet. On the same note, it is expected that Blockchain technology would be adopted as a
security measure in IoT. It is only within a short period that centralized applications running on
IoT would be evolving to full pledge business opportunities. Through the application of IoT,
Blockchain technology is expected to be part of the modern technology used to secure IT
infrastructure.
Finally, the change of data analytics processes due to the uptake of the Internet of Things
(IoT). With IoT in the industry, data analytics tools would change to take new forms through
automation. Artificial Intelligence is expected to take new forms by being able to control and
perform complex data analysis processes over the Internet without involving human
interventions (El Mouaatamid et al. 2016, pp. 28). Through the use of IoT, data analysis tools
would be automated to make necessary decisions based on the response received from remote
data sensing.
Conclusion
Internet of things (IoT) has been shaping the industry by interconnecting devices to
facilitate collection and processing of data. As the automation and interconnection of many
devices continue to take new forms, the security of the collected data and the devices should be
given the necessary priority. Data collected need to be protected by taking necessary security
measures such as encryption of data, securing the network, training IoT users to secure collected
data while on storage or during transmission. It is evident that failing to secure data results to
loss of data privacy and confidentiality.
artificial intelligence and it will be a matter of time before devices start being controlled over the
internet. On the same note, it is expected that Blockchain technology would be adopted as a
security measure in IoT. It is only within a short period that centralized applications running on
IoT would be evolving to full pledge business opportunities. Through the application of IoT,
Blockchain technology is expected to be part of the modern technology used to secure IT
infrastructure.
Finally, the change of data analytics processes due to the uptake of the Internet of Things
(IoT). With IoT in the industry, data analytics tools would change to take new forms through
automation. Artificial Intelligence is expected to take new forms by being able to control and
perform complex data analysis processes over the Internet without involving human
interventions (El Mouaatamid et al. 2016, pp. 28). Through the use of IoT, data analysis tools
would be automated to make necessary decisions based on the response received from remote
data sensing.
Conclusion
Internet of things (IoT) has been shaping the industry by interconnecting devices to
facilitate collection and processing of data. As the automation and interconnection of many
devices continue to take new forms, the security of the collected data and the devices should be
given the necessary priority. Data collected need to be protected by taking necessary security
measures such as encryption of data, securing the network, training IoT users to secure collected
data while on storage or during transmission. It is evident that failing to secure data results to
loss of data privacy and confidentiality.

Internet of things (IoT) is coupled with security risks such as malware, database SQL
injections, cross-site scripting and hacking which might end up compromising the security of the
data if not well secured. It is important to note that, there are so many vulnerabilities which are
created through the collection of data over the internet. Implementation of IoT either for smart
homes or industrial use should be accorded the necessary security measures to make sure not
data breaches would happen as a result of device communication over the internet. Despite the
challenges and risks associated with IoT, its adoption and implementation should be not be
crippled by security issues. It is important to come up with more advanced innovations which
would help insecure implementation of device communication over the internet.
Bibliography
Abdul-Ghani, H.A. and Konstantas, D., 2019. A Comprehensive Study of Security and Privacy
Guidelines, Threats, and Countermeasures: An IoT Perspective. Journal of Sensor and Actuator
Networks, 8(2), p.22.
Alandjani, G., 2018. Features and Potential Security Challenges for IoT Enabled Devices in
Smart City Environment. International journal of advanced computer science and
applications, 9(8), pp.231-238.
Allhoff, F. and Henschke, A., 2018. The Internet of Things: Foundational ethical issues. Internet
of Things, 1, pp.55-66.
Baldini, G., Botterman, M., Neisse, R. and Tallacchini, M., 2018. Ethical design in the internet
of things. Science and engineering ethics, pp.1-21.
El Mouaatamid, O., Lahmer, M. and Belkasmi, M., 2016. Internet of Things Security: Layered
classification of attacks and possible Countermeasures. Electronic Journal of Information
Technology, (9)1, pp. 24-36.
Farooq, M.U., Waseem, M., Khairi, A. and Mazhar, S., 2015. A critical analysis of the security
concerns of the internet of things (IoT). International Journal of Computer Applications, 111(7),
pp.1-5.
Husamuddin, M. and Qayyum, M., 2017. Internet of Things: A study on security and privacy
threats. In 2017 2nd International Conference on Anti-Cyber Crimes (ICACC), pp. 93-97.
Kajtazi, M., Vogel, B., Bugeja, J. and Varshney, R., 2018. State-of-the-Art in Security Thinking
for the Internet of Things (IoT). In Proceedings of the 13th Pre-ICIS Workshop on Information
Security and Privacy (1)1, pp. 1-13.
injections, cross-site scripting and hacking which might end up compromising the security of the
data if not well secured. It is important to note that, there are so many vulnerabilities which are
created through the collection of data over the internet. Implementation of IoT either for smart
homes or industrial use should be accorded the necessary security measures to make sure not
data breaches would happen as a result of device communication over the internet. Despite the
challenges and risks associated with IoT, its adoption and implementation should be not be
crippled by security issues. It is important to come up with more advanced innovations which
would help insecure implementation of device communication over the internet.
Bibliography
Abdul-Ghani, H.A. and Konstantas, D., 2019. A Comprehensive Study of Security and Privacy
Guidelines, Threats, and Countermeasures: An IoT Perspective. Journal of Sensor and Actuator
Networks, 8(2), p.22.
Alandjani, G., 2018. Features and Potential Security Challenges for IoT Enabled Devices in
Smart City Environment. International journal of advanced computer science and
applications, 9(8), pp.231-238.
Allhoff, F. and Henschke, A., 2018. The Internet of Things: Foundational ethical issues. Internet
of Things, 1, pp.55-66.
Baldini, G., Botterman, M., Neisse, R. and Tallacchini, M., 2018. Ethical design in the internet
of things. Science and engineering ethics, pp.1-21.
El Mouaatamid, O., Lahmer, M. and Belkasmi, M., 2016. Internet of Things Security: Layered
classification of attacks and possible Countermeasures. Electronic Journal of Information
Technology, (9)1, pp. 24-36.
Farooq, M.U., Waseem, M., Khairi, A. and Mazhar, S., 2015. A critical analysis of the security
concerns of the internet of things (IoT). International Journal of Computer Applications, 111(7),
pp.1-5.
Husamuddin, M. and Qayyum, M., 2017. Internet of Things: A study on security and privacy
threats. In 2017 2nd International Conference on Anti-Cyber Crimes (ICACC), pp. 93-97.
Kajtazi, M., Vogel, B., Bugeja, J. and Varshney, R., 2018. State-of-the-Art in Security Thinking
for the Internet of Things (IoT). In Proceedings of the 13th Pre-ICIS Workshop on Information
Security and Privacy (1)1, pp. 1-13.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 16
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.



