Designing an Internet of Things Ecosystem for Smart Homes
VerifiedAdded on 2020/04/07
|16
|3858
|87
AI Summary
This research paper explores the integration of Internet of Things (IoT) technologies in smart homes to enhance energy efficiency and sustainability. It examines various IoT devices like solar panels, smart thermostats, and smart water heaters, analyzing their contributions to automating home environments and conserving energy. The study highlights how these technologies can lead to significant reductions in electricity consumption and carbon emissions, thereby promoting sustainable living. Additionally, the paper discusses the challenges and future prospects of widespread adoption of IoT solutions in residential settings.

Running head: INTERNET OF THINGS
Internet of Things
Name of the Student
Name of the University
Author note
Internet of Things
Name of the Student
Name of the University
Author note
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1INTERNET OF THINGS
Table of Contents
Introduction:....................................................................................................................................3
Applications of IoT:.....................................................................................................................3
1. Smart homes:........................................................................................................................3
2. Smart wearables:...................................................................................................................3
3. Use of IoT’s in controlling the house temperature:..............................................................3
4. Use of IoT in gardening:.......................................................................................................4
5. Use of IoT’s in controlling house and garage doors:............................................................4
6. Use of IoT’s in healthcare:...................................................................................................5
7. Cars are connected:...............................................................................................................5
8. Use of IoT for monitoring of the house:...............................................................................5
Diagram of a smart home:...............................................................................................................6
Problems faced by IoT:....................................................................................................................7
Problem using remote assets........................................................................................................7
Protection of private data:............................................................................................................7
Software used is insecure:...........................................................................................................8
Insufficient authentication processes:..........................................................................................8
Range of the device:....................................................................................................................9
More device more problem:.........................................................................................................9
Table of Contents
Introduction:....................................................................................................................................3
Applications of IoT:.....................................................................................................................3
1. Smart homes:........................................................................................................................3
2. Smart wearables:...................................................................................................................3
3. Use of IoT’s in controlling the house temperature:..............................................................3
4. Use of IoT in gardening:.......................................................................................................4
5. Use of IoT’s in controlling house and garage doors:............................................................4
6. Use of IoT’s in healthcare:...................................................................................................5
7. Cars are connected:...............................................................................................................5
8. Use of IoT for monitoring of the house:...............................................................................5
Diagram of a smart home:...............................................................................................................6
Problems faced by IoT:....................................................................................................................7
Problem using remote assets........................................................................................................7
Protection of private data:............................................................................................................7
Software used is insecure:...........................................................................................................8
Insufficient authentication processes:..........................................................................................8
Range of the device:....................................................................................................................9
More device more problem:.........................................................................................................9

2INTERNET OF THINGS
Security:.......................................................................................................................................9
Conclusion:....................................................................................................................................10
References:....................................................................................................................................11
Appendix:......................................................................................................................................13
Security:.......................................................................................................................................9
Conclusion:....................................................................................................................................10
References:....................................................................................................................................11
Appendix:......................................................................................................................................13
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3INTERNET OF THINGS
Introduction:
Internet is global system, which connects computer networks using Internet protocol suite
(TCP/IP) to link them worldwide. Internet has a wide range of information and services, which
include the use of electronic mails, telephone, file sharing and most importantly use of World
Wide Web (WWW) (Barnaghi et al., 2012). IoT helps in inter-networking of various devices and
helps in the exchange and storing of data. Remote controlling of certain objects is also possible
using IoT over a network infrastructure. IoT helps in increasing the efficiency and accuracy
along with economic benefits and reduced human interference (Gubbi et al., 2013). The objective
of the report is to discuss about the Internet of Things (IoT) technology.
Applications of IoT:
1. Smart entertainment system: Smart home is becoming a revolutionary ladder to
success in the residential spaces and smart homes are becoming as common as
smartphones. Smart homes help in saving time, energy and money. Many companies are
planning of delivering household items which no one has ever experienced. Smart home
technology helps in accessing of different household items even if the owner is away
from home (Sharma et al., 2017). talking about smart entertainment at home means the
devices which have made peoples enjoy during their downtime. These devices can be
controlled from any port ion of the house by means of simple voice, movement or touch.
These devices help in enhancing the listening or visual experience. This includes wireless
Bluetooth audio systems to smart TV’s. few examples of smart entertainment system
include the Amazon Echo and the Alexa. This device is a stylish and efficient device
controlled by voice commands.
Introduction:
Internet is global system, which connects computer networks using Internet protocol suite
(TCP/IP) to link them worldwide. Internet has a wide range of information and services, which
include the use of electronic mails, telephone, file sharing and most importantly use of World
Wide Web (WWW) (Barnaghi et al., 2012). IoT helps in inter-networking of various devices and
helps in the exchange and storing of data. Remote controlling of certain objects is also possible
using IoT over a network infrastructure. IoT helps in increasing the efficiency and accuracy
along with economic benefits and reduced human interference (Gubbi et al., 2013). The objective
of the report is to discuss about the Internet of Things (IoT) technology.
Applications of IoT:
1. Smart entertainment system: Smart home is becoming a revolutionary ladder to
success in the residential spaces and smart homes are becoming as common as
smartphones. Smart homes help in saving time, energy and money. Many companies are
planning of delivering household items which no one has ever experienced. Smart home
technology helps in accessing of different household items even if the owner is away
from home (Sharma et al., 2017). talking about smart entertainment at home means the
devices which have made peoples enjoy during their downtime. These devices can be
controlled from any port ion of the house by means of simple voice, movement or touch.
These devices help in enhancing the listening or visual experience. This includes wireless
Bluetooth audio systems to smart TV’s. few examples of smart entertainment system
include the Amazon Echo and the Alexa. This device is a stylish and efficient device
controlled by voice commands.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

4INTERNET OF THINGS
2. Smart wearables: there is a huge demand of wearables in the markets all over the world.
This type of devices collects data and information about the user by the use of various
software’s and also sensors. The information and data are processed to collect
information about the user. These devices are low powered and are small in size. These
devices are made to cover the requirements of entertainment, fitness and health
(Hiremath, Yang & Mankodiya, 2014).
3. Use of IoT’s in controlling the house temperature: Many smart devices like smart
thermostat, automated heating systems and many more have been invented to control the
temperature of the house. This system is more readily available and can easily be
implemented. This not only helps in controlling the temperature of the house but also
helps in reducing the electricity costs. Use of automated HVAC (heating ventilation and
air conditioning) not only helps in reducing the temperature when the house or room is
not occupied but also helps in maintaining the temperature that is automatic increasing
and decreasing of the temperature when someone is present in the house or room
according to schedule or the residence of the house. One such example is the google
glasses. This device displays every information in a smartphone helps the user to give
voice commands to the device.
4. Use of IoT in gardening: many times the weather is not favorable for gardening. Many
house owner wants a green and healthy lawn but sometimes it is not possible due to the
weather conditions. Sprinkler control systems are helping in providing water by real time
communication with the local weather data. One such example is Skydrop sprinkler. In
cases of heavy rains when the water is logged then the device detects the level of water
and postpones its watering schedule. Similarly, the opposite happens when the weather
2. Smart wearables: there is a huge demand of wearables in the markets all over the world.
This type of devices collects data and information about the user by the use of various
software’s and also sensors. The information and data are processed to collect
information about the user. These devices are low powered and are small in size. These
devices are made to cover the requirements of entertainment, fitness and health
(Hiremath, Yang & Mankodiya, 2014).
3. Use of IoT’s in controlling the house temperature: Many smart devices like smart
thermostat, automated heating systems and many more have been invented to control the
temperature of the house. This system is more readily available and can easily be
implemented. This not only helps in controlling the temperature of the house but also
helps in reducing the electricity costs. Use of automated HVAC (heating ventilation and
air conditioning) not only helps in reducing the temperature when the house or room is
not occupied but also helps in maintaining the temperature that is automatic increasing
and decreasing of the temperature when someone is present in the house or room
according to schedule or the residence of the house. One such example is the google
glasses. This device displays every information in a smartphone helps the user to give
voice commands to the device.
4. Use of IoT in gardening: many times the weather is not favorable for gardening. Many
house owner wants a green and healthy lawn but sometimes it is not possible due to the
weather conditions. Sprinkler control systems are helping in providing water by real time
communication with the local weather data. One such example is Skydrop sprinkler. In
cases of heavy rains when the water is logged then the device detects the level of water
and postpones its watering schedule. Similarly, the opposite happens when the weather

5INTERNET OF THINGS
becomes dry. In such cases the device provides sufficient amount of water for the
nourishment of the plants (Lekjaroen et al., 2016).
5. Use of IoT’s in controlling house and garage doors: Monitoring and controlling of the
opening and closing of the doors are easily possible by simply using a smart phone or a
tablet. The doors are connected to the homes Wi-Fi by the simple use of simple smart
devices. No extra hardware is needed for the setup (Margulies, 2015). Smart locks are
also used for protection of the house. One such example is Kwlkset’s Kevo. There might
be use of Bluetooth controlled deadbolts and various security systems. One such example
is ISmartAlarm. These devices are connected to the mobiles or tablets and are easily
controllable via clouds. This helps in gaining real-time information about the house.
6. IoT’s in light controlling: This is mainly a lightning system designed to increase the
efficiency of the energy. These devices are remote controlled or works on an automated
way depending on the conditions of the house. Conditions may include the availability of
light inside the house or the occupancy of the house. This system helps in reducing the
energy consumption of the house by managing the brightness and working of the lights
manually. Some lights are also there whose color can be changed or which can be turned
on or off according to the user’s needs (Soliman et al., 2013). One example of smart
lightning system is the Philips Hue which can be controlled by smartphones even when
away from home it also had the ability to synchronize according to the music along with
the ability to change its color.
7. IoT is smart bathrooms: Many toilets are there which do not require any hands or
paper. This type of toilets has water whose temperature could be controlled, spritzing
wands and automatic dryers. There are also warmers in the toilet seats and led lights.
becomes dry. In such cases the device provides sufficient amount of water for the
nourishment of the plants (Lekjaroen et al., 2016).
5. Use of IoT’s in controlling house and garage doors: Monitoring and controlling of the
opening and closing of the doors are easily possible by simply using a smart phone or a
tablet. The doors are connected to the homes Wi-Fi by the simple use of simple smart
devices. No extra hardware is needed for the setup (Margulies, 2015). Smart locks are
also used for protection of the house. One such example is Kwlkset’s Kevo. There might
be use of Bluetooth controlled deadbolts and various security systems. One such example
is ISmartAlarm. These devices are connected to the mobiles or tablets and are easily
controllable via clouds. This helps in gaining real-time information about the house.
6. IoT’s in light controlling: This is mainly a lightning system designed to increase the
efficiency of the energy. These devices are remote controlled or works on an automated
way depending on the conditions of the house. Conditions may include the availability of
light inside the house or the occupancy of the house. This system helps in reducing the
energy consumption of the house by managing the brightness and working of the lights
manually. Some lights are also there whose color can be changed or which can be turned
on or off according to the user’s needs (Soliman et al., 2013). One example of smart
lightning system is the Philips Hue which can be controlled by smartphones even when
away from home it also had the ability to synchronize according to the music along with
the ability to change its color.
7. IoT is smart bathrooms: Many toilets are there which do not require any hands or
paper. This type of toilets has water whose temperature could be controlled, spritzing
wands and automatic dryers. There are also warmers in the toilet seats and led lights.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

6INTERNET OF THINGS
Many toilets are there which has a self-cleaning function and antimicrobial seats there are
also motion sensors in some cases which controls the motion of the toilet lids. Infrared
technology is used so as to control the flow of water in taps. This senses if the user’s
hand is present under the tap or not. There are also LCD shower panels whose
temperature could be controlled along with the flow of water, steam music and chromo
therapy (Bodhe, Singh & Bawa, 2016). One such example is NEOREST 700H DUAL
FLUSH TOILET which is a toilet with a technologically advanced wash let. This is a
combination of ecology as well as luxury.
8. Use of IoT for monitoring of the house: Automatic control of house devices, smart
surveillance, management of smart energy, distribution of water, security and monitoring
the environment are some of the common applications of IoT for making a smart house.
Many major problems can be solved by the use of IoT. Sensors can help in finding the
movements of various devices across the house or the owner can gain knowledge when to
empty a bin or can detect issues regarding meter tapering, general malfunctions or any
type of issues related to installation of electricity system (Centenaro et al., 2016). One
example of such device which is used for monitoring the house is Logitech Circle
Wireless HD Video Battery Powered Security Camera with 2-way talk. This device
detects movements in an around the house and notifies the user whenever a motion is
detected. Another example is a solar-powered waste compactor that give s reading when
a waste bin is filled and triggers an automatic compaction of the waste.
Many toilets are there which has a self-cleaning function and antimicrobial seats there are
also motion sensors in some cases which controls the motion of the toilet lids. Infrared
technology is used so as to control the flow of water in taps. This senses if the user’s
hand is present under the tap or not. There are also LCD shower panels whose
temperature could be controlled along with the flow of water, steam music and chromo
therapy (Bodhe, Singh & Bawa, 2016). One such example is NEOREST 700H DUAL
FLUSH TOILET which is a toilet with a technologically advanced wash let. This is a
combination of ecology as well as luxury.
8. Use of IoT for monitoring of the house: Automatic control of house devices, smart
surveillance, management of smart energy, distribution of water, security and monitoring
the environment are some of the common applications of IoT for making a smart house.
Many major problems can be solved by the use of IoT. Sensors can help in finding the
movements of various devices across the house or the owner can gain knowledge when to
empty a bin or can detect issues regarding meter tapering, general malfunctions or any
type of issues related to installation of electricity system (Centenaro et al., 2016). One
example of such device which is used for monitoring the house is Logitech Circle
Wireless HD Video Battery Powered Security Camera with 2-way talk. This device
detects movements in an around the house and notifies the user whenever a motion is
detected. Another example is a solar-powered waste compactor that give s reading when
a waste bin is filled and triggers an automatic compaction of the waste.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
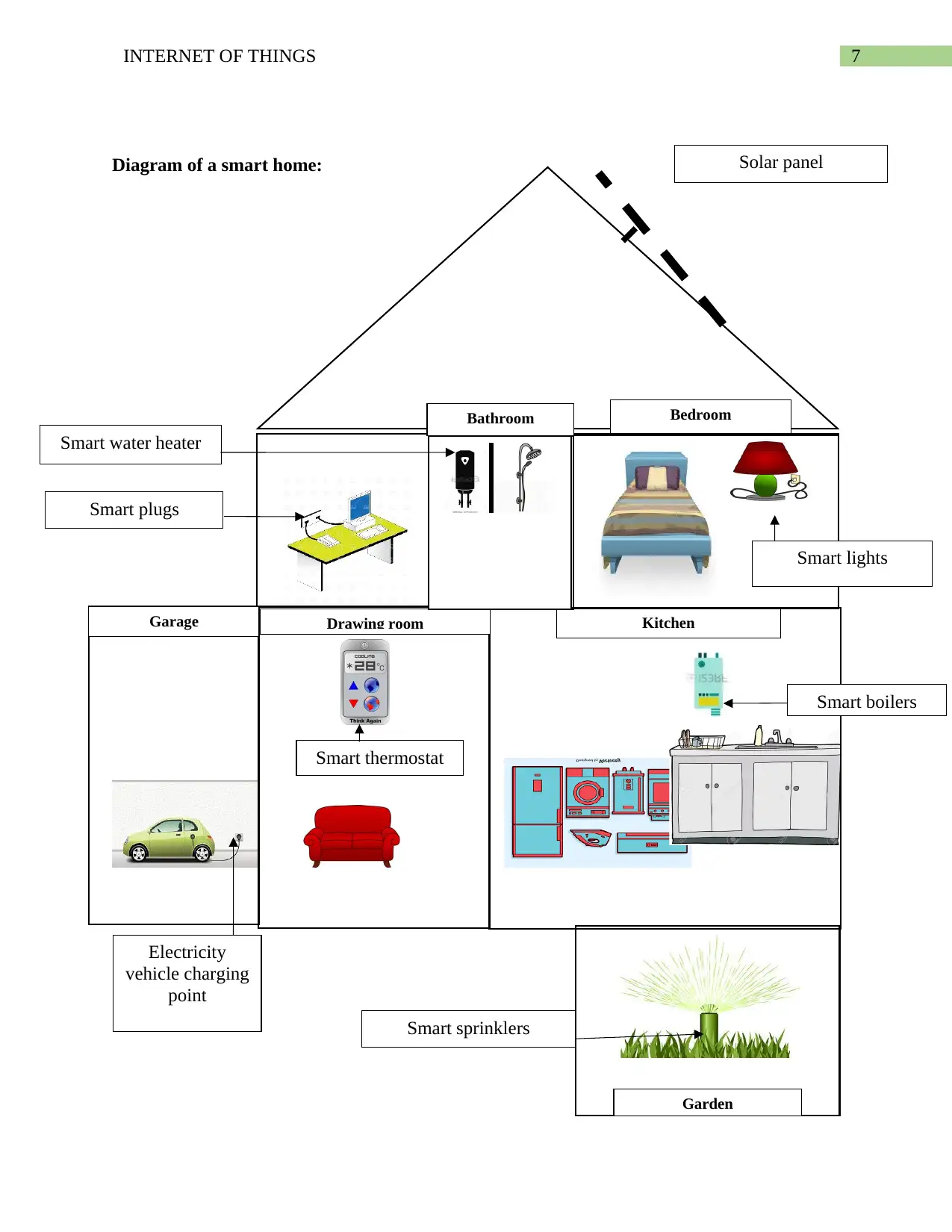
7INTERNET OF THINGS
Diagram of a smart home:
Drawing room KitchenGarage
Bathroom Bedroom
Garden
Smart water heater
Smart plugs
Electricity
vehicle charging
point
Smart thermostat
Smart boilers
Smart sprinklers
Smart lights
Solar panel
Diagram of a smart home:
Drawing room KitchenGarage
Bathroom Bedroom
Garden
Smart water heater
Smart plugs
Electricity
vehicle charging
point
Smart thermostat
Smart boilers
Smart sprinklers
Smart lights
Solar panel

8INTERNET OF THINGS
Problems faced by IoT:
Problem using remote assets
There is a problem in the nature of IoT. Connection with the remote device a system is made
therefore providing data stream between the decentralized management system and the devices.
Incorporation of data or the device on the organizational process so as to provide information on
the location status function and activity of the systems along with the information of the people
who owns the system or who operates the system (Lee et al., 2015).
There is a difference between the amount and the type of information received from the other
sets of big data from social media. The differences are in the following ways:
Instead of arriving in batches like test logs which can be processed and passed straight
away, it arrives as steady stream and at a steady pace.
Accumulation is very fast and comes in large quantities.
By the use of analytics only the data can be uncovered.
The system can rarely be used in production purpose.
Deleting is very easy, unless needed for compliance reasons.
Protection of private data:
Most of the smart devices contains personal data of the user either in the device or in the
clouds or via the mobile applications that is connected to the device. This data stored are often
unsecure and often gets sent without encryption across the network. Data encryption is very
much essential as it prevents unauthorized access. This particularly happens when the data is
being transferred from one device to another device or cloud by the use of internet. This
Problems faced by IoT:
Problem using remote assets
There is a problem in the nature of IoT. Connection with the remote device a system is made
therefore providing data stream between the decentralized management system and the devices.
Incorporation of data or the device on the organizational process so as to provide information on
the location status function and activity of the systems along with the information of the people
who owns the system or who operates the system (Lee et al., 2015).
There is a difference between the amount and the type of information received from the other
sets of big data from social media. The differences are in the following ways:
Instead of arriving in batches like test logs which can be processed and passed straight
away, it arrives as steady stream and at a steady pace.
Accumulation is very fast and comes in large quantities.
By the use of analytics only the data can be uncovered.
The system can rarely be used in production purpose.
Deleting is very easy, unless needed for compliance reasons.
Protection of private data:
Most of the smart devices contains personal data of the user either in the device or in the
clouds or via the mobile applications that is connected to the device. This data stored are often
unsecure and often gets sent without encryption across the network. Data encryption is very
much essential as it prevents unauthorized access. This particularly happens when the data is
being transferred from one device to another device or cloud by the use of internet. This
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

9INTERNET OF THINGS
challenge is particularly as the information generated by IoT is the main key for bringing better
service and management of the devices. Integration of security is a major part of IoT
infrastructure (Sicari et al., 2015).
Software used is insecure:
With the advancement in technology the manufacturers are under the pressure of
producing their product into the market as quickly as they can. This leads to rushing of security
and the testing of the software’s there by making the software face various vulnerabilities. A
survey has showed that even after producing updates of the software on a regular basis there is a
lack of encryption when the update is downloaded. This increases the risk of being intercepted or
modified by the hackers. Patching of vulnerabilities are not done immediately as the company
does not want to disrupt the users by forcing them to upgrade the firmware (Zhang et al., 2014).
Insufficient authentication processes:
The common vulnerability in all kind of digital devices are weak or insecure password.
Even if many computer software forces the user to use strong password still there are some
devices which do not do that. Besides this its common amongst user to use the same password
for different accounts. Once the hackers have the password of a connected device then they
might use the password to gain access of the other more sensitive data from more sensitive
accounts belonging to the same user. Use of secure socket protocol or SSL to face this security
issue. Many websites use the SSL certificate for encrypting and protecting data online. This is
one side whereas the other side is protection of the wireless protocol. Encryption of wireless data
challenge is particularly as the information generated by IoT is the main key for bringing better
service and management of the devices. Integration of security is a major part of IoT
infrastructure (Sicari et al., 2015).
Software used is insecure:
With the advancement in technology the manufacturers are under the pressure of
producing their product into the market as quickly as they can. This leads to rushing of security
and the testing of the software’s there by making the software face various vulnerabilities. A
survey has showed that even after producing updates of the software on a regular basis there is a
lack of encryption when the update is downloaded. This increases the risk of being intercepted or
modified by the hackers. Patching of vulnerabilities are not done immediately as the company
does not want to disrupt the users by forcing them to upgrade the firmware (Zhang et al., 2014).
Insufficient authentication processes:
The common vulnerability in all kind of digital devices are weak or insecure password.
Even if many computer software forces the user to use strong password still there are some
devices which do not do that. Besides this its common amongst user to use the same password
for different accounts. Once the hackers have the password of a connected device then they
might use the password to gain access of the other more sensitive data from more sensitive
accounts belonging to the same user. Use of secure socket protocol or SSL to face this security
issue. Many websites use the SSL certificate for encrypting and protecting data online. This is
one side whereas the other side is protection of the wireless protocol. Encryption of wireless data
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

10INTERNET OF THINGS
is also needed while transferring. Sensitive data are need to be available only to the concerned
user and no one else. It should be made sure that a wireless protocol should have inbuilt
encryption (Zhang et al., 2014).
Range of the device:
There is a need of specifying the range of the device. For example, in use of ZigBee
technology there is a need of calculating the number of repeaters for establishment of
communication range in the device (Lee & Choi, 2014). But one cannot blindly put any number
of repeaters. Increase in number of repeaters decreases the capacity of the system. Therefore, by
testing the range of device will help in finding a suitable spot for maximizing the range without
reaching the breakout point.
More device more problem:
The most important weakness of internet of Things is that if more devices are connected
the problem also increases. The hackers can accomplish more as the risk of so many devices can
get hacked. For instance, a hacker can access the car remotely and control the speed of the car or
even home appliances to just uncover the private data and ruin the day of the user. The most
important thing which is to be considered is that the hackers do not break into the security
system of the user. So this problem can easily be avoided by just increasing the security of the
devices and more cautiousness of the user (Hossain, Fotouhi & Hasan 2015).
Security:
Many hackers are there who can easily use the connected devices to steal the
information’s and leak private data. According to IoT experts there are many ways to solve the
problems of IoT. This includes three steps, first is the building of interoperable security systems
is also needed while transferring. Sensitive data are need to be available only to the concerned
user and no one else. It should be made sure that a wireless protocol should have inbuilt
encryption (Zhang et al., 2014).
Range of the device:
There is a need of specifying the range of the device. For example, in use of ZigBee
technology there is a need of calculating the number of repeaters for establishment of
communication range in the device (Lee & Choi, 2014). But one cannot blindly put any number
of repeaters. Increase in number of repeaters decreases the capacity of the system. Therefore, by
testing the range of device will help in finding a suitable spot for maximizing the range without
reaching the breakout point.
More device more problem:
The most important weakness of internet of Things is that if more devices are connected
the problem also increases. The hackers can accomplish more as the risk of so many devices can
get hacked. For instance, a hacker can access the car remotely and control the speed of the car or
even home appliances to just uncover the private data and ruin the day of the user. The most
important thing which is to be considered is that the hackers do not break into the security
system of the user. So this problem can easily be avoided by just increasing the security of the
devices and more cautiousness of the user (Hossain, Fotouhi & Hasan 2015).
Security:
Many hackers are there who can easily use the connected devices to steal the
information’s and leak private data. According to IoT experts there are many ways to solve the
problems of IoT. This includes three steps, first is the building of interoperable security systems

11INTERNET OF THINGS
in every IoT device to stop the hackers and also to identify any attempt of hacking. Secondly the
vendors of IoT should make routine, automatic updates to software available to patch against
evolving vulnerabilities. Finally, the last step is to encrypt the data stored so that hacking
becomes difficult. Open data transmission makes IoT an easy target for hackers (Hossain,
Fotouhi & Hasan 2015, June).
Conclusion:
The report helps to conclude that implementation of IoT is much closer that anyone can
think of. For the advancement of this technology necessary advances have been made and most
of the manufacturers have already started the implementation of technology. The main reason for
which implementations of IoT’s are not taking place is that it will have a severe effect on
security, legal, and social fields. IoT’s can be affecting the workers severely. Hackers may hack
the technology and organizations might not want to share their data. This is the reason for which
IoT technologies implemented even if there is need of the technology. IoT is potentially abused
by the workers and even the absence of the privacy may not be liked by the individual users. Due
to various reasons the Internet of Things may very well be pushed back longer than it truly needs
to be.
in every IoT device to stop the hackers and also to identify any attempt of hacking. Secondly the
vendors of IoT should make routine, automatic updates to software available to patch against
evolving vulnerabilities. Finally, the last step is to encrypt the data stored so that hacking
becomes difficult. Open data transmission makes IoT an easy target for hackers (Hossain,
Fotouhi & Hasan 2015, June).
Conclusion:
The report helps to conclude that implementation of IoT is much closer that anyone can
think of. For the advancement of this technology necessary advances have been made and most
of the manufacturers have already started the implementation of technology. The main reason for
which implementations of IoT’s are not taking place is that it will have a severe effect on
security, legal, and social fields. IoT’s can be affecting the workers severely. Hackers may hack
the technology and organizations might not want to share their data. This is the reason for which
IoT technologies implemented even if there is need of the technology. IoT is potentially abused
by the workers and even the absence of the privacy may not be liked by the individual users. Due
to various reasons the Internet of Things may very well be pushed back longer than it truly needs
to be.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 16
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





