Project: Analysis of TLS-Related Attacks in IoT Networks
VerifiedAdded on 2023/04/24
|42
|10071
|480
Project
AI Summary
This project dissertation delves into the critical domain of Transport Layer Security (TLS) within the context of Internet of Things (IoT) networks. The study initiates with an introduction to TLS and its significance, followed by an examination of its application in IoT environments. The research aims to identify and analyze various TLS-related attacks that can compromise the security of IoT devices and networks. The methodology involves a comprehensive literature review to understand existing research and identify research gaps. The project proceeds by identifying the different types of cyber-attacks which negatively affect the transport layer security, identifying the impact of TLS attack on the IOT architecture, and proposes a solution for securing and maintaining accuracy of the IOT working environment. The project's findings will be presented with an analysis of the attacks and their impact on the IoT working program. The dissertation concludes by offering a proposed solution and a discussion of future research directions, emphasizing the importance of robust security measures to protect IoT infrastructure from cyber threats and ensure the reliable and secure operation of interconnected devices. The structure of the dissertation includes an introduction, literature review, methodology, analysis, proposed solution, results, and conclusion.

Project Dissertation
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Contents
Chapter 1: Introduction:.............................................................................................................2
Research purpose:...................................................................................................................2
Research Aim:........................................................................................................................3
Research Objectives:..............................................................................................................3
Research Questions:...............................................................................................................3
Research Strategy:..................................................................................................................3
Significance of Study:............................................................................................................3
Thesis Structure......................................................................................................................4
Chapter 2: Literature Review.....................................................................................................5
Chapter 3: Research Methodology...........................................................................................13
Chapter 4: Research Analysis and approach............................................................................17
Chapter 5: Proposed Solution...................................................................................................23
Chapter 6: Result and Findings................................................................................................31
Chapter 7: Research Limitation, Future Scope and Conclusion..............................................36
References:...............................................................................................................................38
Chapter 1: Introduction:.............................................................................................................2
Research purpose:...................................................................................................................2
Research Aim:........................................................................................................................3
Research Objectives:..............................................................................................................3
Research Questions:...............................................................................................................3
Research Strategy:..................................................................................................................3
Significance of Study:............................................................................................................3
Thesis Structure......................................................................................................................4
Chapter 2: Literature Review.....................................................................................................5
Chapter 3: Research Methodology...........................................................................................13
Chapter 4: Research Analysis and approach............................................................................17
Chapter 5: Proposed Solution...................................................................................................23
Chapter 6: Result and Findings................................................................................................31
Chapter 7: Research Limitation, Future Scope and Conclusion..............................................36
References:...............................................................................................................................38

Chapter 1: Introduction:
The internet of things is the most promising and emerging technology which requires high
parameters of security to get accuracy in completing the flow of work done. The IOT
framework is plug-in with the various security challenges such as security associated with the
constrained devices, authorization and authentication of the system, managing updating
features to the devices, ensuring privacy and data integration, mobility of the cloud
applications, ensuring high availability of data and information, detecting cyber securities
attack, identifying and managing vulnerabilities, and prediction of the security issues (Gondi,
and et.al., 2016). The focus should be given on identifying the attacks associated with the
transport layer and socket layer so that the vulnerabilities can be handled at an early stage and
the proactive action plan can be prepared against the vulnerabilities. The transport layer
security requires the privacy between the two communicating devices and applications. The
security protocol should be developed for managing the transfer of files, virtual private
network connections, sending of instant messages to the communicating devices, and
managing the voice over Internet protocol. The handshaking protocol is used for
acknowledging the retrieval of secured information and data packets in the sequence sent by
the server (Hezam, Konstantas, Mahyoub, 2018). The message authentication codes are
added to the messages so that the sensitivity and confidentiality of the information can be
secured and failure of IOT communication can be minimized. Data integration helps in
providing security to the web applications by managing transfer of files by developing virtual
private network connections. The instant messaging system can be accelerated by developing
the two layer communication. TLS is made up of two protocols which are named as
Handshake protocol and record protocol (Siddiqui, and Badr, 2018). The authorization and
authentication is managed with the help of these protocols between the sender and receiver.
The TLS security architecture is composed of implementation obscure. The focus should be
given on developing the strong security protocol for the transport layer so that the accuracy in
the information flow can be managed for the effective working of the IOT infrastructure.
Research purpose:
The purpose of this paper is to develop a research program on identifying the problems and
issues which exist in the transport layer security and to propose a solution which is effective
for managing the TLS security in the IOT environment.
The internet of things is the most promising and emerging technology which requires high
parameters of security to get accuracy in completing the flow of work done. The IOT
framework is plug-in with the various security challenges such as security associated with the
constrained devices, authorization and authentication of the system, managing updating
features to the devices, ensuring privacy and data integration, mobility of the cloud
applications, ensuring high availability of data and information, detecting cyber securities
attack, identifying and managing vulnerabilities, and prediction of the security issues (Gondi,
and et.al., 2016). The focus should be given on identifying the attacks associated with the
transport layer and socket layer so that the vulnerabilities can be handled at an early stage and
the proactive action plan can be prepared against the vulnerabilities. The transport layer
security requires the privacy between the two communicating devices and applications. The
security protocol should be developed for managing the transfer of files, virtual private
network connections, sending of instant messages to the communicating devices, and
managing the voice over Internet protocol. The handshaking protocol is used for
acknowledging the retrieval of secured information and data packets in the sequence sent by
the server (Hezam, Konstantas, Mahyoub, 2018). The message authentication codes are
added to the messages so that the sensitivity and confidentiality of the information can be
secured and failure of IOT communication can be minimized. Data integration helps in
providing security to the web applications by managing transfer of files by developing virtual
private network connections. The instant messaging system can be accelerated by developing
the two layer communication. TLS is made up of two protocols which are named as
Handshake protocol and record protocol (Siddiqui, and Badr, 2018). The authorization and
authentication is managed with the help of these protocols between the sender and receiver.
The TLS security architecture is composed of implementation obscure. The focus should be
given on developing the strong security protocol for the transport layer so that the accuracy in
the information flow can be managed for the effective working of the IOT infrastructure.
Research purpose:
The purpose of this paper is to develop a research program on identifying the problems and
issues which exist in the transport layer security and to propose a solution which is effective
for managing the TLS security in the IOT environment.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Research Aim:
The aim of the research is to identify the different types of cyber-attacks which negatively
affect the transport layer security and functioning of the IOT architecture and propose a
solution which helps in securing and maintaining accuracy of the IOT working environment.
Research Objectives:
The objectives of the research are highlighted below:
Identify the different types of cyber-attacks which negatively affect the transport layer
security
Identify the impact of TLS attack on the IOT architecture
Study of the literature for getting details of TLS attacks
Proposing a solution which helps in securing and maintaining accuracy of the IOT
working environment
Research Questions:
What type of TLS attacks occur which negatively affect the IOT architecture? How the TLS
attacks can be minimized for developing highly secured architecture to preserve the accuracy
of the IOT environment?
Research Strategy:
The focus should be given on constructing the research questions for giving particular
direction to the research study. The study of literature is carried out to identify the problems
and research gaps so that effective solution can be proposed according to the requirement of
the TLS security in IOT environment. The solution should be proposed for managing the
security in the transport layer of the IOT infrastructure against the vulnerabilities. The
conclusion should be drawn from the research to identify the major challenges in the IOT
environment and efficacy of the proposed model.
Significance of Study:
The research study helps in evaluating the impact and the major challenges which the IOT
architecture has to be faced due to the cyber-attacks on the transport layer. The efficiency of
the Transport layer security can be measured with respect to the negative impact seen on the
IOT working environment (Mendez, and et.al., 2015). During the study, it has been identified
that the smart sensor environment is cope up with various challenges such as ineffective
security parameters associated with the smart devices, giving authority and authentication to
The aim of the research is to identify the different types of cyber-attacks which negatively
affect the transport layer security and functioning of the IOT architecture and propose a
solution which helps in securing and maintaining accuracy of the IOT working environment.
Research Objectives:
The objectives of the research are highlighted below:
Identify the different types of cyber-attacks which negatively affect the transport layer
security
Identify the impact of TLS attack on the IOT architecture
Study of the literature for getting details of TLS attacks
Proposing a solution which helps in securing and maintaining accuracy of the IOT
working environment
Research Questions:
What type of TLS attacks occur which negatively affect the IOT architecture? How the TLS
attacks can be minimized for developing highly secured architecture to preserve the accuracy
of the IOT environment?
Research Strategy:
The focus should be given on constructing the research questions for giving particular
direction to the research study. The study of literature is carried out to identify the problems
and research gaps so that effective solution can be proposed according to the requirement of
the TLS security in IOT environment. The solution should be proposed for managing the
security in the transport layer of the IOT infrastructure against the vulnerabilities. The
conclusion should be drawn from the research to identify the major challenges in the IOT
environment and efficacy of the proposed model.
Significance of Study:
The research study helps in evaluating the impact and the major challenges which the IOT
architecture has to be faced due to the cyber-attacks on the transport layer. The efficiency of
the Transport layer security can be measured with respect to the negative impact seen on the
IOT working environment (Mendez, and et.al., 2015). During the study, it has been identified
that the smart sensor environment is cope up with various challenges such as ineffective
security parameters associated with the smart devices, giving authority and authentication to
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

the network devices for message transfers, updating the devices according to the security
requirement, not secured communication and information flow between the sender and the
receiver, unavailability of the devices, ineffective detection of the vulnerabilities, no
proactive program for detecting the presence of intruder, and many more. The analysis of the
cyber-attacks and their impact of the IOT working program help in developing an effective
solution for securing the flow of information between the smart devices.
Thesis Structure
The first chapter focuses on the introduction to the transport layer security and IOT
infrastructure. The second chapter reviews the literature in the direction of transport layer
security with respect to the IOT infrastructure. The chapter 3 gives the details of research
methodology which should be undertaken to identify the cyber-attack on the TLS. The
discussion of the research analysis is carried out in the chapter 4. The proposed solution
should be provided to resolve the vulnerabilities associated with the TLS in chapter 6. The
result and future scope of the research program should be brief in chapter 7. The conclusion
of the research program is given in the last chapter 8 of the research study.
Chapter 2: Literature Review
The security is the major concern for managing communication between the sensor devices in
the IOT network because the whole system works on accuracy and flow of data packets
within the fraction of seconds. Industry 4.0 is the new revolution in the IOT framework
which is also called as fourth industrial revolution for building communication links in the
requirement, not secured communication and information flow between the sender and the
receiver, unavailability of the devices, ineffective detection of the vulnerabilities, no
proactive program for detecting the presence of intruder, and many more. The analysis of the
cyber-attacks and their impact of the IOT working program help in developing an effective
solution for securing the flow of information between the smart devices.
Thesis Structure
The first chapter focuses on the introduction to the transport layer security and IOT
infrastructure. The second chapter reviews the literature in the direction of transport layer
security with respect to the IOT infrastructure. The chapter 3 gives the details of research
methodology which should be undertaken to identify the cyber-attack on the TLS. The
discussion of the research analysis is carried out in the chapter 4. The proposed solution
should be provided to resolve the vulnerabilities associated with the TLS in chapter 6. The
result and future scope of the research program should be brief in chapter 7. The conclusion
of the research program is given in the last chapter 8 of the research study.
Chapter 2: Literature Review
The security is the major concern for managing communication between the sensor devices in
the IOT network because the whole system works on accuracy and flow of data packets
within the fraction of seconds. Industry 4.0 is the new revolution in the IOT framework
which is also called as fourth industrial revolution for building communication links in the
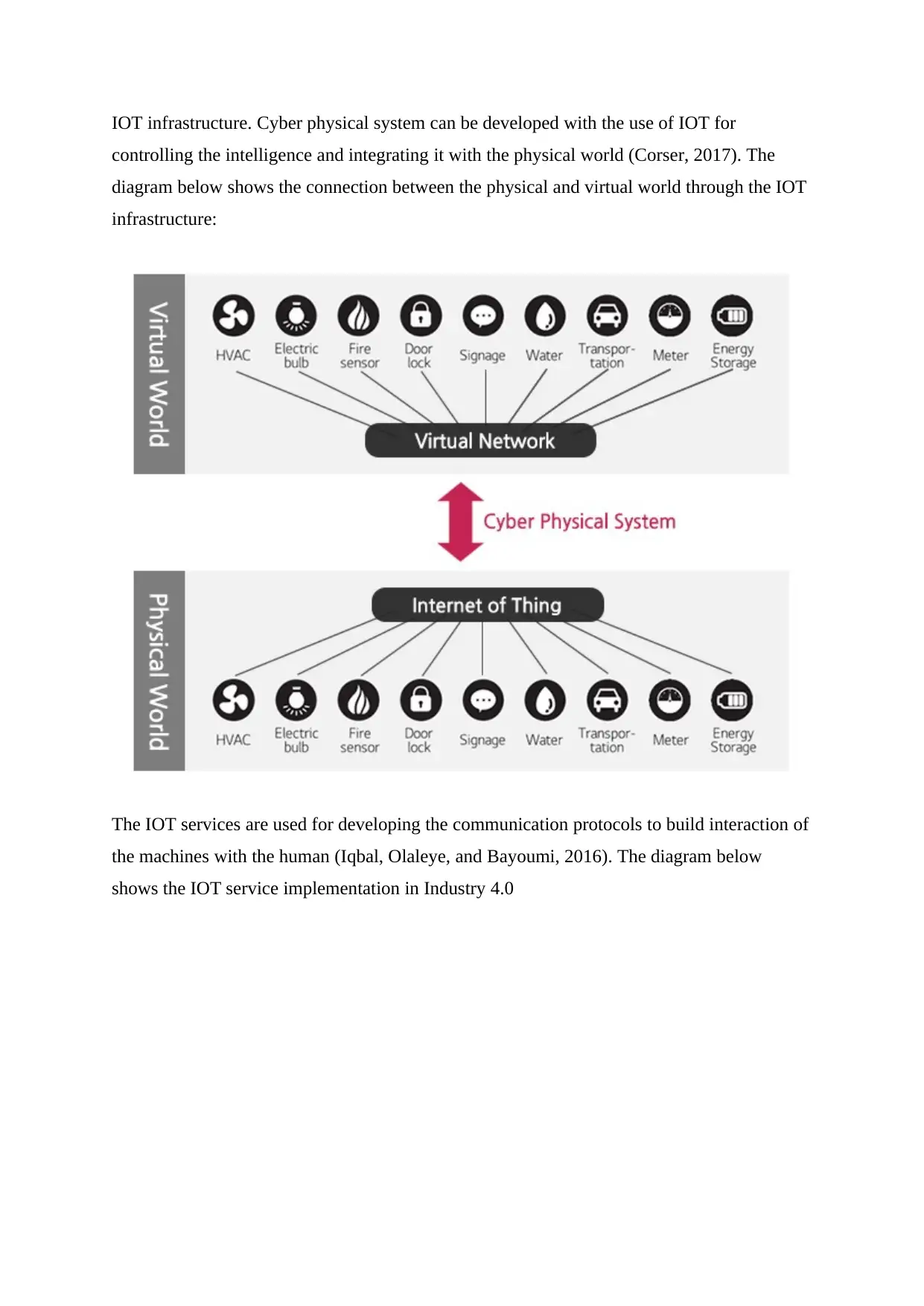
IOT infrastructure. Cyber physical system can be developed with the use of IOT for
controlling the intelligence and integrating it with the physical world (Corser, 2017). The
diagram below shows the connection between the physical and virtual world through the IOT
infrastructure:
The IOT services are used for developing the communication protocols to build interaction of
the machines with the human (Iqbal, Olaleye, and Bayoumi, 2016). The diagram below
shows the IOT service implementation in Industry 4.0
controlling the intelligence and integrating it with the physical world (Corser, 2017). The
diagram below shows the connection between the physical and virtual world through the IOT
infrastructure:
The IOT services are used for developing the communication protocols to build interaction of
the machines with the human (Iqbal, Olaleye, and Bayoumi, 2016). The diagram below
shows the IOT service implementation in Industry 4.0
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
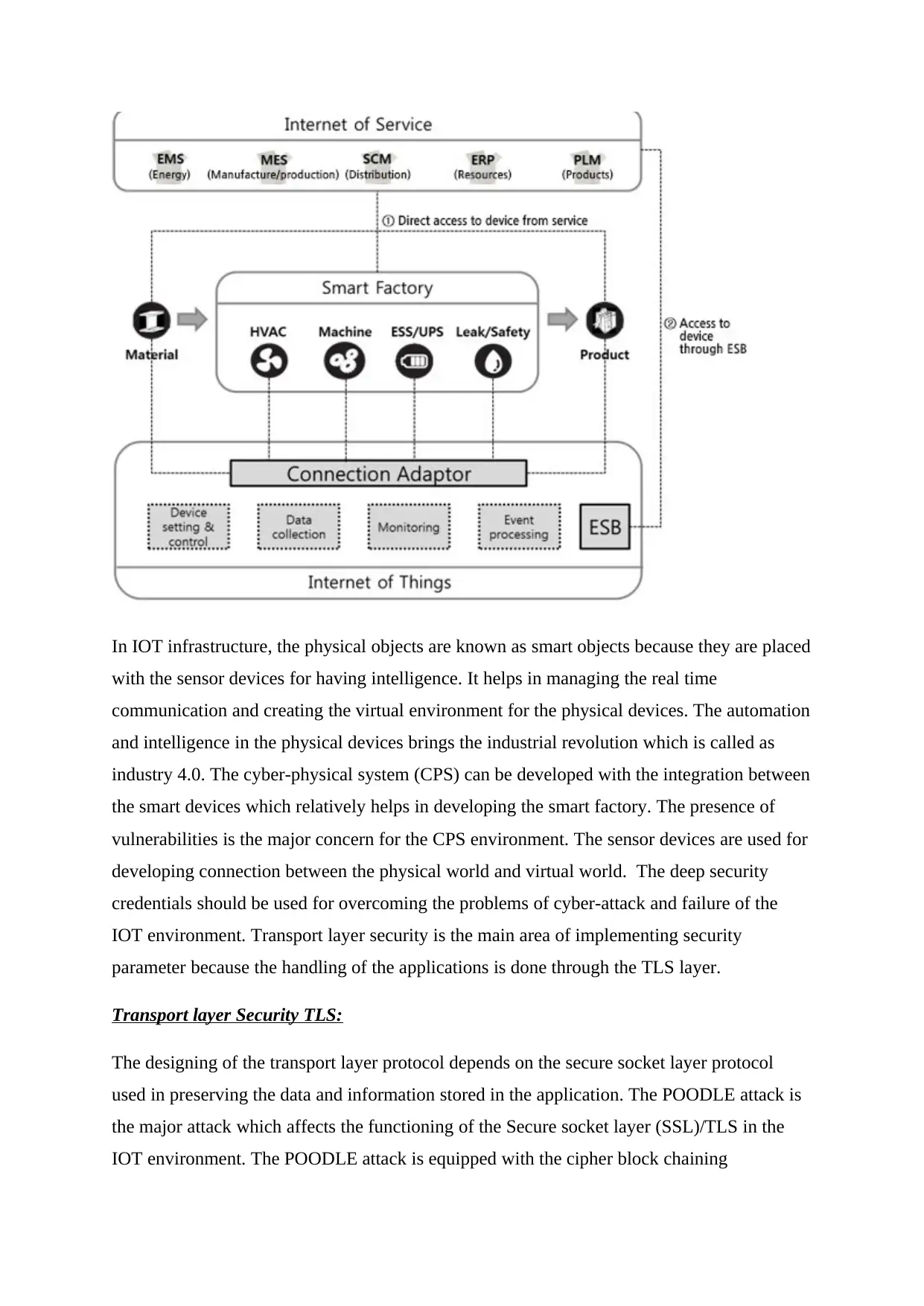
In IOT infrastructure, the physical objects are known as smart objects because they are placed
with the sensor devices for having intelligence. It helps in managing the real time
communication and creating the virtual environment for the physical devices. The automation
and intelligence in the physical devices brings the industrial revolution which is called as
industry 4.0. The cyber-physical system (CPS) can be developed with the integration between
the smart devices which relatively helps in developing the smart factory. The presence of
vulnerabilities is the major concern for the CPS environment. The sensor devices are used for
developing connection between the physical world and virtual world. The deep security
credentials should be used for overcoming the problems of cyber-attack and failure of the
IOT environment. Transport layer security is the main area of implementing security
parameter because the handling of the applications is done through the TLS layer.
Transport layer Security TLS:
The designing of the transport layer protocol depends on the secure socket layer protocol
used in preserving the data and information stored in the application. The POODLE attack is
the major attack which affects the functioning of the Secure socket layer (SSL)/TLS in the
IOT environment. The POODLE attack is equipped with the cipher block chaining
with the sensor devices for having intelligence. It helps in managing the real time
communication and creating the virtual environment for the physical devices. The automation
and intelligence in the physical devices brings the industrial revolution which is called as
industry 4.0. The cyber-physical system (CPS) can be developed with the integration between
the smart devices which relatively helps in developing the smart factory. The presence of
vulnerabilities is the major concern for the CPS environment. The sensor devices are used for
developing connection between the physical world and virtual world. The deep security
credentials should be used for overcoming the problems of cyber-attack and failure of the
IOT environment. Transport layer security is the main area of implementing security
parameter because the handling of the applications is done through the TLS layer.
Transport layer Security TLS:
The designing of the transport layer protocol depends on the secure socket layer protocol
used in preserving the data and information stored in the application. The POODLE attack is
the major attack which affects the functioning of the Secure socket layer (SSL)/TLS in the
IOT environment. The POODLE attack is equipped with the cipher block chaining
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

encryption methodology which can affect the accuracy of the data and information stored in
the SSL layer. The working of the TLS layer is comprised of three steps which are named as
deployment of the key exchange algorithm, managing cipher text, and developing
authentication code for the message. The POODLE attack results in disturbing the managing
the interoperations and compatibility. The block padding results in defining the handshaking
protocol. The man-in-the middle attack occurred in defining the vulnerability in sending the
connection between the sender and destination. The data is transferred between the layers in
the encrypted format. Public private key pair is created for the exchange of information for
encrypting the data (Alfaqih, and Muhtadi, 2016). The TLS_Method are used for managing
the connections between the devices. Unencrypted socket are created for loading the private
key to manage the call for certification. Communication channels are the major concern area
for the attack surface. The access control policies should be developed for managing the
vulnerabilities at the IOT attack surface. The data should be detected at high risks. The
authorization and authentication protocol should be checked for minimizing the data
leakages. The defence mechanism should be developed as follows:
Development of the administrative interface: The attack vectors are analysed with
respect to the malicious activities. The network server helps in managing the web
interface for the transfer of file from client to destination.
Interface of the devices: Managing vulnerabilities to develop the interface for the
credential management of the devices
Web interface for the cloud devices: The transport encryption policies should be
developed by applying the two factor authentication algorithm. The ineffective
encryption policies will result in the entrance of the vulnerabilities and cyber-attacks.
Development of the mobile applications: The low cyber securities parameters may be
broken down by the denial of service attacks and other cyber-attacks which can
directly affect the application program (Gomez, Moret, Crowcroft, 2015).
Network facilities and services: The service management program should be
developed for managing the denial of service attack, man in the middle attack, buffer
overflow, malfunctioning of the computer program, and others.
TLS Vulnerabilities and attacks:
The transport layer security of the IOT infrastructure is comprised of various vulnerabilities
which should be integrated in a specified format. The information of the IOT infrastructure is
the SSL layer. The working of the TLS layer is comprised of three steps which are named as
deployment of the key exchange algorithm, managing cipher text, and developing
authentication code for the message. The POODLE attack results in disturbing the managing
the interoperations and compatibility. The block padding results in defining the handshaking
protocol. The man-in-the middle attack occurred in defining the vulnerability in sending the
connection between the sender and destination. The data is transferred between the layers in
the encrypted format. Public private key pair is created for the exchange of information for
encrypting the data (Alfaqih, and Muhtadi, 2016). The TLS_Method are used for managing
the connections between the devices. Unencrypted socket are created for loading the private
key to manage the call for certification. Communication channels are the major concern area
for the attack surface. The access control policies should be developed for managing the
vulnerabilities at the IOT attack surface. The data should be detected at high risks. The
authorization and authentication protocol should be checked for minimizing the data
leakages. The defence mechanism should be developed as follows:
Development of the administrative interface: The attack vectors are analysed with
respect to the malicious activities. The network server helps in managing the web
interface for the transfer of file from client to destination.
Interface of the devices: Managing vulnerabilities to develop the interface for the
credential management of the devices
Web interface for the cloud devices: The transport encryption policies should be
developed by applying the two factor authentication algorithm. The ineffective
encryption policies will result in the entrance of the vulnerabilities and cyber-attacks.
Development of the mobile applications: The low cyber securities parameters may be
broken down by the denial of service attacks and other cyber-attacks which can
directly affect the application program (Gomez, Moret, Crowcroft, 2015).
Network facilities and services: The service management program should be
developed for managing the denial of service attack, man in the middle attack, buffer
overflow, malfunctioning of the computer program, and others.
TLS Vulnerabilities and attacks:
The transport layer security of the IOT infrastructure is comprised of various vulnerabilities
which should be integrated in a specified format. The information of the IOT infrastructure is

comprised of three parameters which are classified as confidentiality, availability, and
integrity. The storing and processing of the information should take place for managing the
authentication and authorization of the data (Aneela, Anusha, Malavika, and Saripalle, 2017).
The stored information can be exploited by the vulnerabilities and association of the
malicious activities. The security violation can affect the integrity and accuracy of the data
stored in the applications. Some of the common vulnerabilities are listed below:
Authentication: In authentication, the control on the working of the processes and
procedures is lost by the user. The third party can access the control over the
operational functionality of the applications. The reason behind the loss of
authentication is due to the use of weak password, data leakages, two-factor
authentication protocol, and log out by the user is not done.
Eavesdropping: The communication between the IOT devices is done in the
interrupted format due to the occurrence of tampering by the third party. The
configuration of the encryption procedure is not properly done. The implementation
of the encryption methods is not properly done.
During the Updating process: The updating of the IOT devices is done without
sending any prior message is the type of attack by the third party. The authenticated
methods are not used for getting remote control on managing the communication
between the sensor devices.
Physical accessing of the information: The information is extracted through the
firmware for gaining device control through the interlocking of the devices. The
device management program is the failure in providing security to the information due
to lack of physical storage control.
Device Management System: The denial of service attacks occurs in an IOT network
for managing the command information. The applications are in-secured in storing the
information. The third party attack can occur in managing the security control. The
systematic control should be applied for defining the information storage units. The
complexity of the information for streamlining the control over the applications.
The POODLE attack results in disturbing the managing the interoperations and compatibility.
The block padding results in defining the handshaking protocol. The man-in-the middle
attack occurred in defining the vulnerability in sending the connection between the sender
and destination. The downgrading of the information results in the vulnerabilities on the
secure socket layer (Kothmayr, Hu, Schmitt, Bruenig, 2011). The message authentication
integrity. The storing and processing of the information should take place for managing the
authentication and authorization of the data (Aneela, Anusha, Malavika, and Saripalle, 2017).
The stored information can be exploited by the vulnerabilities and association of the
malicious activities. The security violation can affect the integrity and accuracy of the data
stored in the applications. Some of the common vulnerabilities are listed below:
Authentication: In authentication, the control on the working of the processes and
procedures is lost by the user. The third party can access the control over the
operational functionality of the applications. The reason behind the loss of
authentication is due to the use of weak password, data leakages, two-factor
authentication protocol, and log out by the user is not done.
Eavesdropping: The communication between the IOT devices is done in the
interrupted format due to the occurrence of tampering by the third party. The
configuration of the encryption procedure is not properly done. The implementation
of the encryption methods is not properly done.
During the Updating process: The updating of the IOT devices is done without
sending any prior message is the type of attack by the third party. The authenticated
methods are not used for getting remote control on managing the communication
between the sensor devices.
Physical accessing of the information: The information is extracted through the
firmware for gaining device control through the interlocking of the devices. The
device management program is the failure in providing security to the information due
to lack of physical storage control.
Device Management System: The denial of service attacks occurs in an IOT network
for managing the command information. The applications are in-secured in storing the
information. The third party attack can occur in managing the security control. The
systematic control should be applied for defining the information storage units. The
complexity of the information for streamlining the control over the applications.
The POODLE attack results in disturbing the managing the interoperations and compatibility.
The block padding results in defining the handshaking protocol. The man-in-the middle
attack occurred in defining the vulnerability in sending the connection between the sender
and destination. The downgrading of the information results in the vulnerabilities on the
secure socket layer (Kothmayr, Hu, Schmitt, Bruenig, 2011). The message authentication
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

code protocol is used for converting the plaintext into cipher text. 256 byte formats should be
prepared for encrypting and decrypting the information. The cookies are generated for
managing the session and transfer of sensitive data from host to the clients. The focus should
be given on developing the physical layer security parameters for preventing the entrance of
the vulnerabilities in the IOT infrastructure. The protocols should be designed for preserving
the security of the transport layer protocol. The highest priority system should be used for
managing the encryption and decryption of the information between the sensor devices. The
vulnerabilities are added in the information stream stored in the transport layer security. The
compression ratio is used for compressing the information to manage secured connection
between the sender and receiver. The integrity and security is used for managing the
information to handle large amount of information effectively between the various devices.
The replication of the information can be controlled by identifying the value of compression
ratio. The third party focuses on identifying the cookie session managed between the sender
and receiver for getting the response of the cookie value. The breaches attack on the TLS
layer can be identified by demonstrating the level of compression technologies used in
managing the HTTP request. The reflection of HTTP response should be collected from the
sender side. The time period of the cookie session should be identified for calculating the
impact of the attack on the TLS layer (Santos, and et.al., 2015). The Vulnerabilities on the
TLS layer can be controlled by disabling the HTTP compression protocols. The secret
information can be obtained for the user defined input. The random number is generated for
preserving the protocols for identifying the request response. The XOR operations are
performed for masking the data value. The chart below shows the type of attacks associated
with the IOT architecture:
prepared for encrypting and decrypting the information. The cookies are generated for
managing the session and transfer of sensitive data from host to the clients. The focus should
be given on developing the physical layer security parameters for preventing the entrance of
the vulnerabilities in the IOT infrastructure. The protocols should be designed for preserving
the security of the transport layer protocol. The highest priority system should be used for
managing the encryption and decryption of the information between the sensor devices. The
vulnerabilities are added in the information stream stored in the transport layer security. The
compression ratio is used for compressing the information to manage secured connection
between the sender and receiver. The integrity and security is used for managing the
information to handle large amount of information effectively between the various devices.
The replication of the information can be controlled by identifying the value of compression
ratio. The third party focuses on identifying the cookie session managed between the sender
and receiver for getting the response of the cookie value. The breaches attack on the TLS
layer can be identified by demonstrating the level of compression technologies used in
managing the HTTP request. The reflection of HTTP response should be collected from the
sender side. The time period of the cookie session should be identified for calculating the
impact of the attack on the TLS layer (Santos, and et.al., 2015). The Vulnerabilities on the
TLS layer can be controlled by disabling the HTTP compression protocols. The secret
information can be obtained for the user defined input. The random number is generated for
preserving the protocols for identifying the request response. The XOR operations are
performed for masking the data value. The chart below shows the type of attacks associated
with the IOT architecture:
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
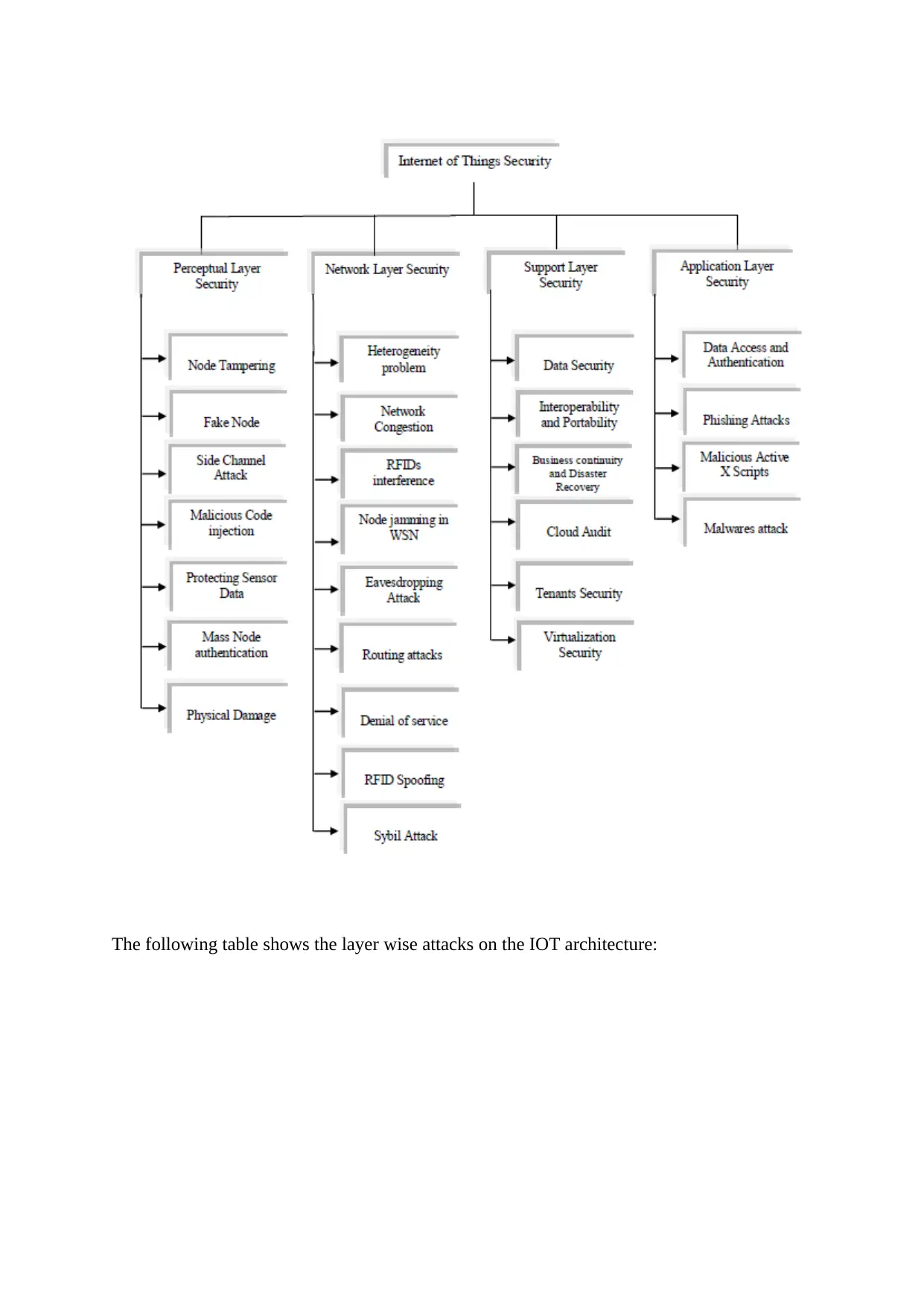
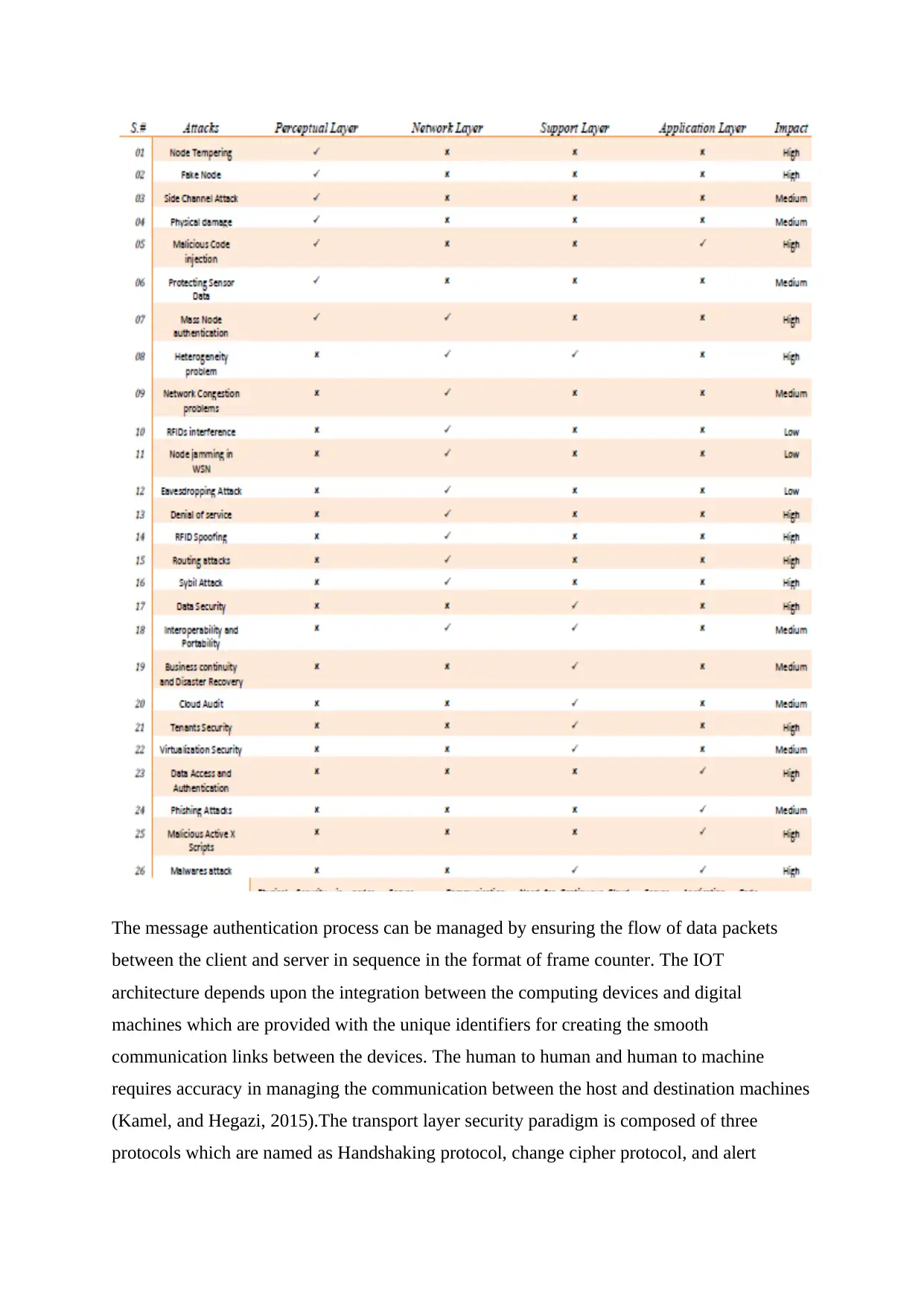
The following table shows the layer wise attacks on the IOT architecture:
The message authentication process can be managed by ensuring the flow of data packets
between the client and server in sequence in the format of frame counter. The IOT
architecture depends upon the integration between the computing devices and digital
machines which are provided with the unique identifiers for creating the smooth
communication links between the devices. The human to human and human to machine
requires accuracy in managing the communication between the host and destination machines
(Kamel, and Hegazi, 2015).The transport layer security paradigm is composed of three
protocols which are named as Handshaking protocol, change cipher protocol, and alert
between the client and server in sequence in the format of frame counter. The IOT
architecture depends upon the integration between the computing devices and digital
machines which are provided with the unique identifiers for creating the smooth
communication links between the devices. The human to human and human to machine
requires accuracy in managing the communication between the host and destination machines
(Kamel, and Hegazi, 2015).The transport layer security paradigm is composed of three
protocols which are named as Handshaking protocol, change cipher protocol, and alert
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 42
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





