Assessment of Internet Technologies: IP Addressing, DHT, and HTTP
VerifiedAdded on 2023/06/05
|5
|1174
|393
Homework Assignment
AI Summary
This assignment solution delves into various aspects of internet technologies, starting with an efficiency calculation based on header sizes. It then examines IP addressing schemes, providing examples and subnet configurations. A detailed explanation of Distributed Hash Tables (DHTs) follows, including their function in P2P networks. The solution further analyzes the arrangement of HTTP and DNS messages, calculating delays in network communication scenarios. Finally, it addresses TCP segment analysis, interpreting acknowledgement numbers, source and destination ports, and retransmission mechanisms. The document provides a comprehensive overview with detailed responses and diagrams.

Running head: INTERNET TECHNOLOGIES
Assessment Item 2: Internet Technologies
(Student’s Name)
(Student ID)
(Student Email Contact)
(Professor’s Name)
(Course Title)
(Date of Submission)
Assessment Item 2: Internet Technologies
(Student’s Name)
(Student ID)
(Student Email Contact)
(Professor’s Name)
(Course Title)
(Date of Submission)
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

INTERNET TECHNOLOGIES 2
Question one
A hundred bytes plus ten bytes per layer header with an addition of five more headers gives one a
hundred and fifty bytes. Therefore efficiency is
100÷150= 66.6 percent efficiency (Tanenbaum & Wetherall, 2014)
Question two: IP addressing scheme
2.1)
129.17.129.01100001 129.17.129.96 to 129.17.129.127
2.2)
Question three: Distributed Hash Table
What is DHT?
Distributed Hash Table commonly known as DHT one of the class of the decentralized
distributed system which offers look-up services that is similar to a hash table. DHT forms infrastructures
which can be used in building complex services like anycast, p2p file sharing, content distribution
systems, multicast, instant messaging, web caching, and domain name services (Dabek, 2010)
How a DHT works with an example of P2P network
DHT are mainly used to avoid flooding as a routing procedure. Peer to peer networks have
unstructured and structured overlays, this means that structured networks usually have rules which dictate
where objects stored are located or are going to be located and how network topology is organized. DHT
are examples if structured, overlays dictates how queries should be routed using varying methods and
queries should be placed (Rossi, 2004).
Question 4
4.1
The arrangement of HTTP and DNS messages receive and sent from m1.a.com as any other
messages that enter or leave the a.com network
1. First, m1.a.com is required to make a decision of the designation www.b.com to the Internet
Protocol so that it can send a Domain Name Server REQUEST note to the native Domain Name
Server resolver
2. The local Domain Name Server serve doesn’t have any info meaning that it have to contact the
root DNS server may be a REQUEST message which can take around 599 ms
3. The root Domain Name Server then returns a name of Domain Name Server; top level domain
server for .com which can take five hundred ms
4. Native Domain Name Server then links with .com TLD which can also take 500ms as per
assumptions
5. The TLD.com server gives an outcome of an authoritive name server for b.com which take five
hundred ms
6. The native Domain Name Server then links authoritative name server with b.com which takes
around 100 ms
129.17.129.01100001 to129.17.129.96 129.17.129.127
129.17.129.96 103/29; 129.17.129.104 111/29;‐ ‐
129.17.129.112 119/29; 129.17.129.120 127/29‐ ‐
129.17.129.01100xxx
Question one
A hundred bytes plus ten bytes per layer header with an addition of five more headers gives one a
hundred and fifty bytes. Therefore efficiency is
100÷150= 66.6 percent efficiency (Tanenbaum & Wetherall, 2014)
Question two: IP addressing scheme
2.1)
129.17.129.01100001 129.17.129.96 to 129.17.129.127
2.2)
Question three: Distributed Hash Table
What is DHT?
Distributed Hash Table commonly known as DHT one of the class of the decentralized
distributed system which offers look-up services that is similar to a hash table. DHT forms infrastructures
which can be used in building complex services like anycast, p2p file sharing, content distribution
systems, multicast, instant messaging, web caching, and domain name services (Dabek, 2010)
How a DHT works with an example of P2P network
DHT are mainly used to avoid flooding as a routing procedure. Peer to peer networks have
unstructured and structured overlays, this means that structured networks usually have rules which dictate
where objects stored are located or are going to be located and how network topology is organized. DHT
are examples if structured, overlays dictates how queries should be routed using varying methods and
queries should be placed (Rossi, 2004).
Question 4
4.1
The arrangement of HTTP and DNS messages receive and sent from m1.a.com as any other
messages that enter or leave the a.com network
1. First, m1.a.com is required to make a decision of the designation www.b.com to the Internet
Protocol so that it can send a Domain Name Server REQUEST note to the native Domain Name
Server resolver
2. The local Domain Name Server serve doesn’t have any info meaning that it have to contact the
root DNS server may be a REQUEST message which can take around 599 ms
3. The root Domain Name Server then returns a name of Domain Name Server; top level domain
server for .com which can take five hundred ms
4. Native Domain Name Server then links with .com TLD which can also take 500ms as per
assumptions
5. The TLD.com server gives an outcome of an authoritive name server for b.com which take five
hundred ms
6. The native Domain Name Server then links authoritative name server with b.com which takes
around 100 ms
129.17.129.01100001 to129.17.129.96 129.17.129.127
129.17.129.96 103/29; 129.17.129.104 111/29;‐ ‐
129.17.129.112 119/29; 129.17.129.120 127/29‐ ‐
129.17.129.01100xxx

INTERNET TECHNOLOGIES 3
7. The commanding name server referred to as b.com in the diagram then returns an Internet
Protocol of www.b1.com which have a duration of around 100 ms
8. Hype Text Transfer Protocol client then sends the Hyper Text Transfer Protocol GET note to
www.b1.com then send to Hyper Text Transfer Protocol cache which is found at the a.com
network which take no time
9. If HTTP cache lacks demanded document or message in the cache, then it have to send GET
request message to the www.b.com which takes 100ms
10. The www.b.com then receives the GET request; this transimmision takes only one second to send
a one Gbps file from b.com to R2
11. A one Gbit file is usually transmitted ove a one Mbps link which is between R1 and R2 which
takes around one thousand seconds
12. There is one second interval to send one Gbps file from Hyper Text Transfer Protocol cache to
the m1.a.com, one second delay to send one Gbps file from R1 to Hyper Text Transfer Protocol
cache. This means that the total delay is about one thousand, one hundered and five seconds
(1105 secs) (AmeritechLibraryServices., 2009)
4.2
2nd, 3rd, 4th, and 5th takes 500ms, 6th, 8th , 7th , 11th and 9th takes 100ms (11th step have and
added for propagation) , 11th step takes 1000 ms this means that the total delay is
500 * 4 = 2000ms
100 * 5 = 500ms
(2000+500)/6= 42 seconds
42 secs + 1000 = 1042 seconds
Takes around 1042 seconds
4.3
1. First, www. M2.a.com is required in mapping the name b.com to a certain Internet Protocol
address; this enables it to send the DNS request message to the local DNS resolver
2. The local DNS server then looks for cache so as to find the b.com
3. The Hyper Text Transfer Protocol client at m2.a.com then send Hyper Text Transfer Protocol
GET message to b1.com
4. The Hyper Text Transfer Protocol cache then finds the demanded document or message in cache
hence it send GET request
5. The www.b.com then receives the GET request hence the b.com has to send a short reply note to
the Hyper Text Transfer Protocol cache to HTTP cache
6. A One Gbps is sent to m2.a.com to the HTTP cache (McIsaac, 2015)
4.4: Time taken in 4.3
4th and 5th takes 100ms and the 6th takes one second hence the total time taken is 1.2 seconds
Question 5
a. The acknowledge number is 165
b. The source port number is 80
c. The destination port number is 303
5.2) Acknowledgement number is 145. This indicates that the receiver is waiting for 145 bytes and
onward. The source port is 303 and the destination port is 80.
5.3) Acknowledgments/segments are usually shown as dashed lines which is shown by figure one below.
After the retransmission time for the 1st segment is expired, host A then retransmits the 1st segment. The
7. The commanding name server referred to as b.com in the diagram then returns an Internet
Protocol of www.b1.com which have a duration of around 100 ms
8. Hype Text Transfer Protocol client then sends the Hyper Text Transfer Protocol GET note to
www.b1.com then send to Hyper Text Transfer Protocol cache which is found at the a.com
network which take no time
9. If HTTP cache lacks demanded document or message in the cache, then it have to send GET
request message to the www.b.com which takes 100ms
10. The www.b.com then receives the GET request; this transimmision takes only one second to send
a one Gbps file from b.com to R2
11. A one Gbit file is usually transmitted ove a one Mbps link which is between R1 and R2 which
takes around one thousand seconds
12. There is one second interval to send one Gbps file from Hyper Text Transfer Protocol cache to
the m1.a.com, one second delay to send one Gbps file from R1 to Hyper Text Transfer Protocol
cache. This means that the total delay is about one thousand, one hundered and five seconds
(1105 secs) (AmeritechLibraryServices., 2009)
4.2
2nd, 3rd, 4th, and 5th takes 500ms, 6th, 8th , 7th , 11th and 9th takes 100ms (11th step have and
added for propagation) , 11th step takes 1000 ms this means that the total delay is
500 * 4 = 2000ms
100 * 5 = 500ms
(2000+500)/6= 42 seconds
42 secs + 1000 = 1042 seconds
Takes around 1042 seconds
4.3
1. First, www. M2.a.com is required in mapping the name b.com to a certain Internet Protocol
address; this enables it to send the DNS request message to the local DNS resolver
2. The local DNS server then looks for cache so as to find the b.com
3. The Hyper Text Transfer Protocol client at m2.a.com then send Hyper Text Transfer Protocol
GET message to b1.com
4. The Hyper Text Transfer Protocol cache then finds the demanded document or message in cache
hence it send GET request
5. The www.b.com then receives the GET request hence the b.com has to send a short reply note to
the Hyper Text Transfer Protocol cache to HTTP cache
6. A One Gbps is sent to m2.a.com to the HTTP cache (McIsaac, 2015)
4.4: Time taken in 4.3
4th and 5th takes 100ms and the 6th takes one second hence the total time taken is 1.2 seconds
Question 5
a. The acknowledge number is 165
b. The source port number is 80
c. The destination port number is 303
5.2) Acknowledgement number is 145. This indicates that the receiver is waiting for 145 bytes and
onward. The source port is 303 and the destination port is 80.
5.3) Acknowledgments/segments are usually shown as dashed lines which is shown by figure one below.
After the retransmission time for the 1st segment is expired, host A then retransmits the 1st segment. The
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
INTERNET TECHNOLOGIES 4
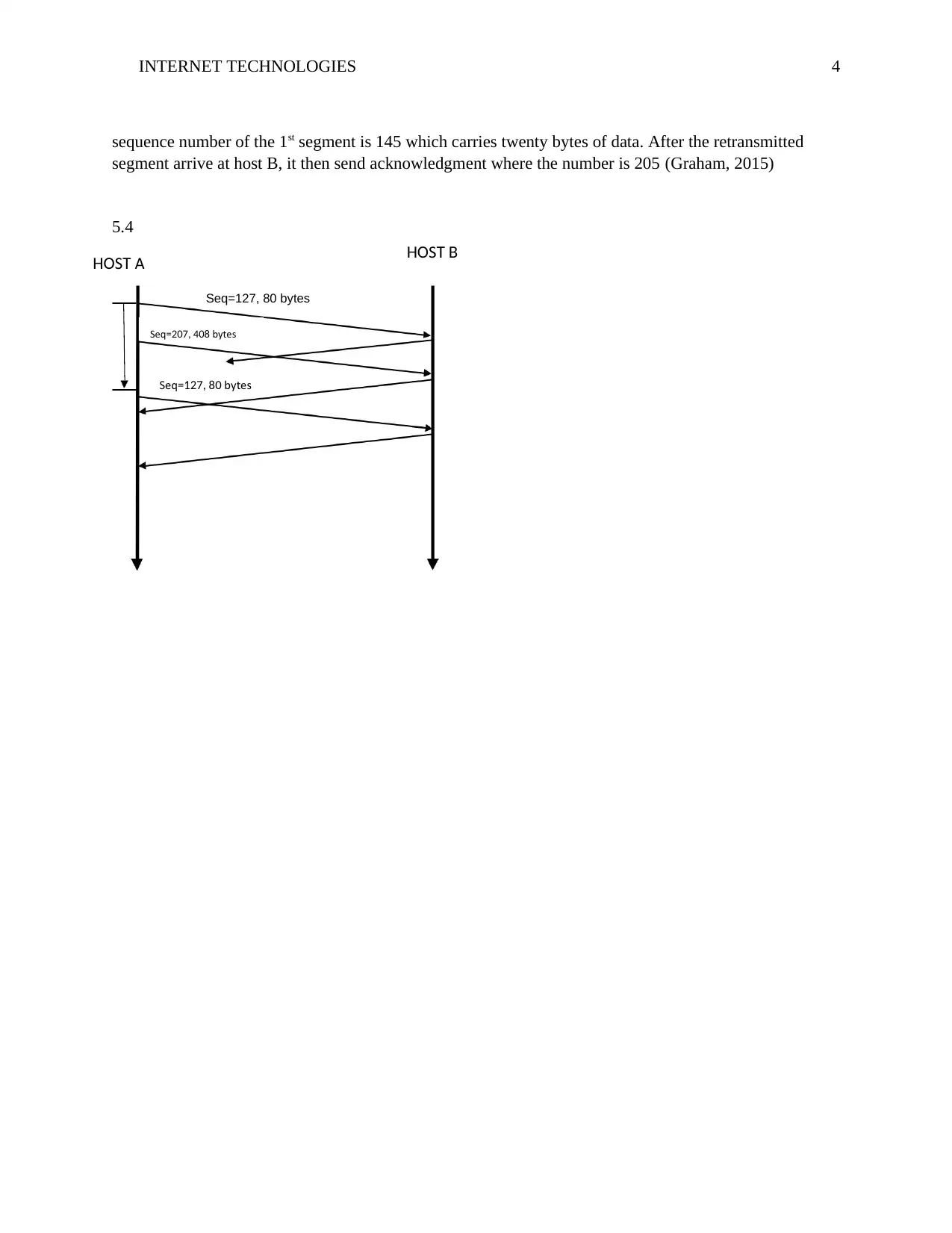
sequence number of the 1st segment is 145 which carries twenty bytes of data. After the retransmitted
segment arrive at host B, it then send acknowledgment where the number is 205 (Graham, 2015)
5.4
S AHO T SHO T B
Seq=127, 80 bytes
Seq bytes=207, 408
Seq bytes=127, 80
sequence number of the 1st segment is 145 which carries twenty bytes of data. After the retransmitted
segment arrive at host B, it then send acknowledgment where the number is 205 (Graham, 2015)
5.4
S AHO T SHO T B
Seq=127, 80 bytes
Seq bytes=207, 408
Seq bytes=127, 80
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

INTERNET TECHNOLOGIES 5
References
AmeritechLibraryServices. (2009). IP addressing & DNS.
Dabek, F. (2010). A distributed Hash table by Frank Dabek .
Graham, B. (2015). TCP/IP addressing : designing and optimizing your IP addressing scheme.
San Diego: Morgan Kaufmann.
McIsaac, N. (2015). CompTIA Mobility+ : IP Addressing. New Hampshire.
Rossi, L. D. (2004). Cisco and IP addressing by Louis D Rossi . New York: McGraw-Hill.
Tanenbaum, A. S., & Wetherall, D. (2014). Computer networks. Thomson Press India Limited.
References
AmeritechLibraryServices. (2009). IP addressing & DNS.
Dabek, F. (2010). A distributed Hash table by Frank Dabek .
Graham, B. (2015). TCP/IP addressing : designing and optimizing your IP addressing scheme.
San Diego: Morgan Kaufmann.
McIsaac, N. (2015). CompTIA Mobility+ : IP Addressing. New Hampshire.
Rossi, L. D. (2004). Cisco and IP addressing by Louis D Rossi . New York: McGraw-Hill.
Tanenbaum, A. S., & Wetherall, D. (2014). Computer networks. Thomson Press India Limited.
1 out of 5
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.


