Digital Forensics Report: Contract Employee Theft Investigation
VerifiedAdded on 2023/06/12
|18
|2124
|374
Report
AI Summary
This document presents a comprehensive digital forensics report concerning the alleged intellectual property theft by a contract employee, Bob Aspen, from Exotic Mountain Tour Services (ETMS). The investigation utilizes ProDiscover and WinHex to analyze a USB drive and email communications. The analysis focuses on recovering and reconstructing potentially altered image files related to a joint marketing campaign with Superior Bicycles, LLC. Key steps include recovering digital photography evidence by searching for specific file signatures, rebuilding file headers to bypass security measures, and reconstructing file fragments from different clusters. The findings confirm that Bob Aspen attempted to leak intellectual property using email and USB drives. Two images were recovered from the USB drive, with one requiring cluster reconstruction and header repair using WinHex. The report references various sources on digital forensics, disk image indexing, and security measures.
[Document title]
[Document subtitle]
[DATE]
[Company name]
[Company address]
[Document subtitle]
[DATE]
[Company name]
[Company address]
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Table of Contents
Task 1.........................................................................................................................................2
Task 2.........................................................................................................................................4
Abstract..................................................................................................................................4
Introduction............................................................................................................................4
Analysis conducted................................................................................................................4
Findings................................................................................................................................16
References............................................................................................................................17
Task 1.........................................................................................................................................2
Task 2.........................................................................................................................................4
Abstract..................................................................................................................................4
Introduction............................................................................................................................4
Analysis conducted................................................................................................................4
Findings................................................................................................................................16
References............................................................................................................................17

Task 1
WinHex is the forensic software used in order to alter the values in binary data of the files,
this is done generally to repair the headers of the known file systems, scrambling the data and
to recover the data can only be retrieved back to recover the text. In order to recover the text
following operations are needed to be done:
Modify Data-> “left shift by 1-bit option”
Output:
WinHex is the forensic software used in order to alter the values in binary data of the files,
this is done generally to repair the headers of the known file systems, scrambling the data and
to recover the data can only be retrieved back to recover the text. In order to recover the text
following operations are needed to be done:
Modify Data-> “left shift by 1-bit option”
Output:
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
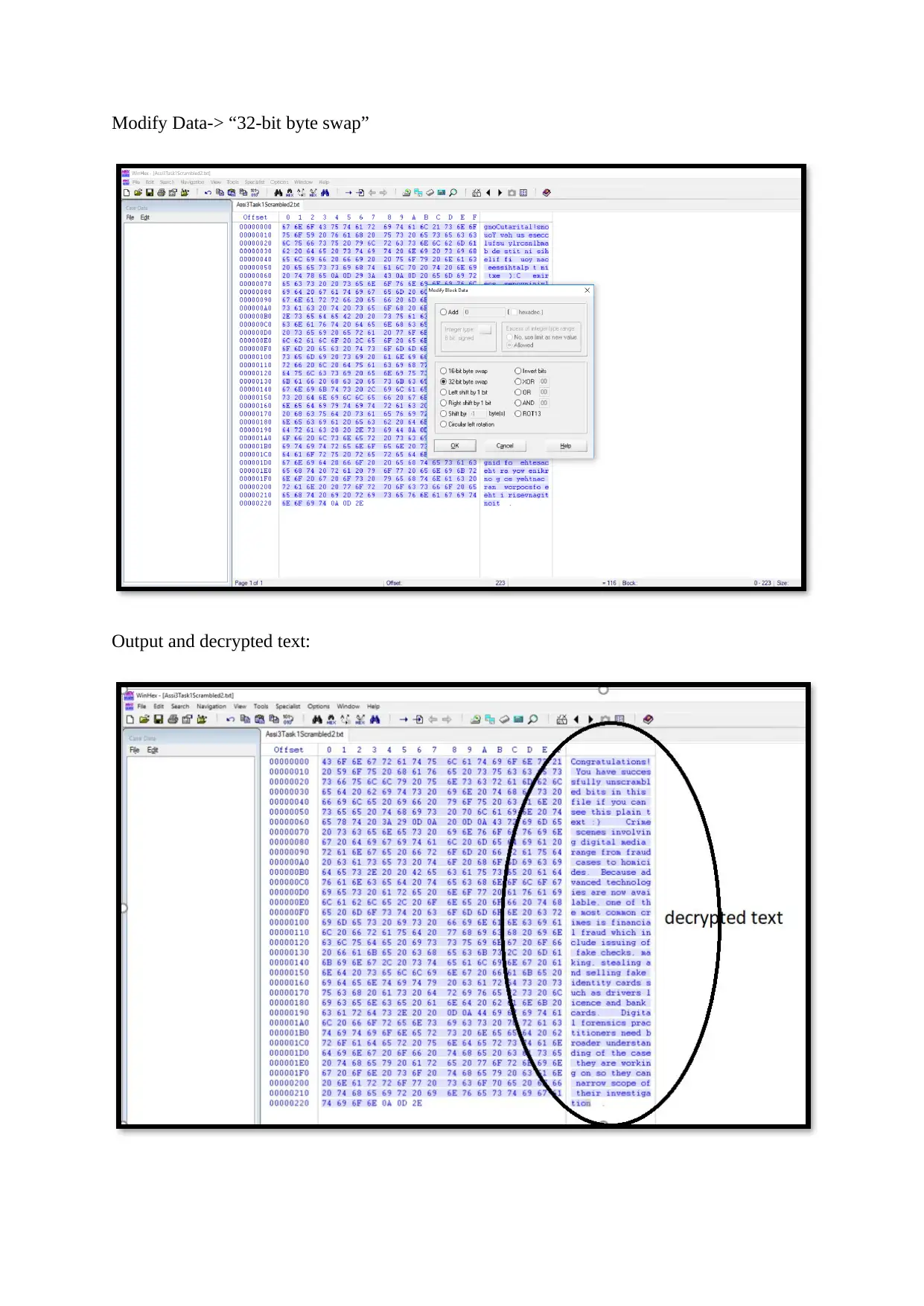
Modify Data-> “32-bit byte swap”
Output and decrypted text:
Output and decrypted text:
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Task 2
Abstract
The case under the investigation is about the contract employee attempt of theft of
Intellectual Property of Exotic Mountain Tour Services (ETMS). The company Exotic
Mountain Tour Services have just finished the extensive survey with association with
Superior Bicycles, LLC in order to formulate an extensive business strategy. The leak of any
such data would mean loss of revenue and trust for the ETMS that would lead to entire
campaign being under tremendous loss for them. The entire leak came into picture when the
contract employee’s emails were intercepted by the organization and via those they came to
know about the malicious practices of the contract employee. The USB drive was also
recovered from the desk of the employee about which the entire forensic investigation would
take place.
Introduction
The two major software used in the current case investigation case are ProDiscover and
WinHex. The ProDiscover software is the forensic software tool that is used to make and
analyze the images of the storage devices. There are number of feature set that are available
for the expert disposal, though only few of them are being generally used around the world
by the forensic experts. Using the special hardware write block we can develop exact copy of
images without altering the images of the storages.
Another important software tool for the same forensic purposes is WinHex, WinHex is the
forensic software used in order to alter the values in binary data of the files, this is done
generally to repair the headers of the known file systems, scrambling the data and to recover
the data can only be retrieved back to recover the text. It enables the user to edit the opened
file in binary by using the edit, cut, copy, paste, delete, insert etc. with different view
available like tree view, cluster view etc. The arithmetic and logical operations can be made
and done over the data, cluster-based search is important feature that enables the user to work
on different clusters to recover files directly or via clusters. The reporting feature of exporting
the reporting into HTML and RTF format is a nice addon feature.
Analysis conducted
In the start we have two emails that were being communicated outside the company that too
being communicated over the unofficial mail address that doesn’t belong to ETMS
Abstract
The case under the investigation is about the contract employee attempt of theft of
Intellectual Property of Exotic Mountain Tour Services (ETMS). The company Exotic
Mountain Tour Services have just finished the extensive survey with association with
Superior Bicycles, LLC in order to formulate an extensive business strategy. The leak of any
such data would mean loss of revenue and trust for the ETMS that would lead to entire
campaign being under tremendous loss for them. The entire leak came into picture when the
contract employee’s emails were intercepted by the organization and via those they came to
know about the malicious practices of the contract employee. The USB drive was also
recovered from the desk of the employee about which the entire forensic investigation would
take place.
Introduction
The two major software used in the current case investigation case are ProDiscover and
WinHex. The ProDiscover software is the forensic software tool that is used to make and
analyze the images of the storage devices. There are number of feature set that are available
for the expert disposal, though only few of them are being generally used around the world
by the forensic experts. Using the special hardware write block we can develop exact copy of
images without altering the images of the storages.
Another important software tool for the same forensic purposes is WinHex, WinHex is the
forensic software used in order to alter the values in binary data of the files, this is done
generally to repair the headers of the known file systems, scrambling the data and to recover
the data can only be retrieved back to recover the text. It enables the user to edit the opened
file in binary by using the edit, cut, copy, paste, delete, insert etc. with different view
available like tree view, cluster view etc. The arithmetic and logical operations can be made
and done over the data, cluster-based search is important feature that enables the user to work
on different clusters to recover files directly or via clusters. The reporting feature of exporting
the reporting into HTML and RTF format is a nice addon feature.
Analysis conducted
In the start we have two emails that were being communicated outside the company that too
being communicated over the unofficial mail address that doesn’t belong to ETMS

organization trusted zones. Apart from this the USB drive was being found at the desk of the
Bob Aspen the contract employee, this is the information that we have in hand to work over
the case, we need to recover the data from the USB drive based on the information retrieved
from the emails in order to retrieve the concrete evidence against the accused Bob Aspen.
There were two different emails that were being used to communicate using the
terrysadler@groowy.com and being replied or communicated to baspen@aol.com. This
record matches the Bob Aspen email address used while working in the organization on the
contract position. The timestamp of the sent and received mails are off that means the
account operated must be from different time zoned location from west as the timestamps are
being given by the server not the user.
The next conversation asks the bob aspen to alter the data so that it can bypass the filters in
place of the organization. It also directed the Bob Aspen to change the extension of the file
and alter the header information as well.
Search for and Recovering Digital photography Evidence
In order to recover the files from the USB drive which was given by the EMTS, the initially
the image was created by using the ProDiscover and its image was loaded in the ProDiscover
software, the initial recovering involved the searching of the search criteria string matching
“FIF”, the reason for the “FIF” keyword is that JFIF and JPEG would lead to lot of false
positive images as well that would lead to time wastage as the expert would need to examine
each and every file that have been communicated. The important is to recover the recent files
as the Bob Aspen must have used to transfer the confidential Intellectual Property. In order to
recover the data and create a solid evidence case we would use the ProDiscover as well as the
WinHex to recover the header information or to reconstruct it in order to have the best
possible outcome of the file retrieved and file can be viewed easily.
Bob Aspen the contract employee, this is the information that we have in hand to work over
the case, we need to recover the data from the USB drive based on the information retrieved
from the emails in order to retrieve the concrete evidence against the accused Bob Aspen.
There were two different emails that were being used to communicate using the
terrysadler@groowy.com and being replied or communicated to baspen@aol.com. This
record matches the Bob Aspen email address used while working in the organization on the
contract position. The timestamp of the sent and received mails are off that means the
account operated must be from different time zoned location from west as the timestamps are
being given by the server not the user.
The next conversation asks the bob aspen to alter the data so that it can bypass the filters in
place of the organization. It also directed the Bob Aspen to change the extension of the file
and alter the header information as well.
Search for and Recovering Digital photography Evidence
In order to recover the files from the USB drive which was given by the EMTS, the initially
the image was created by using the ProDiscover and its image was loaded in the ProDiscover
software, the initial recovering involved the searching of the search criteria string matching
“FIF”, the reason for the “FIF” keyword is that JFIF and JPEG would lead to lot of false
positive images as well that would lead to time wastage as the expert would need to examine
each and every file that have been communicated. The important is to recover the recent files
as the Bob Aspen must have used to transfer the confidential Intellectual Property. In order to
recover the data and create a solid evidence case we would use the ProDiscover as well as the
WinHex to recover the header information or to reconstruct it in order to have the best
possible outcome of the file retrieved and file can be viewed easily.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
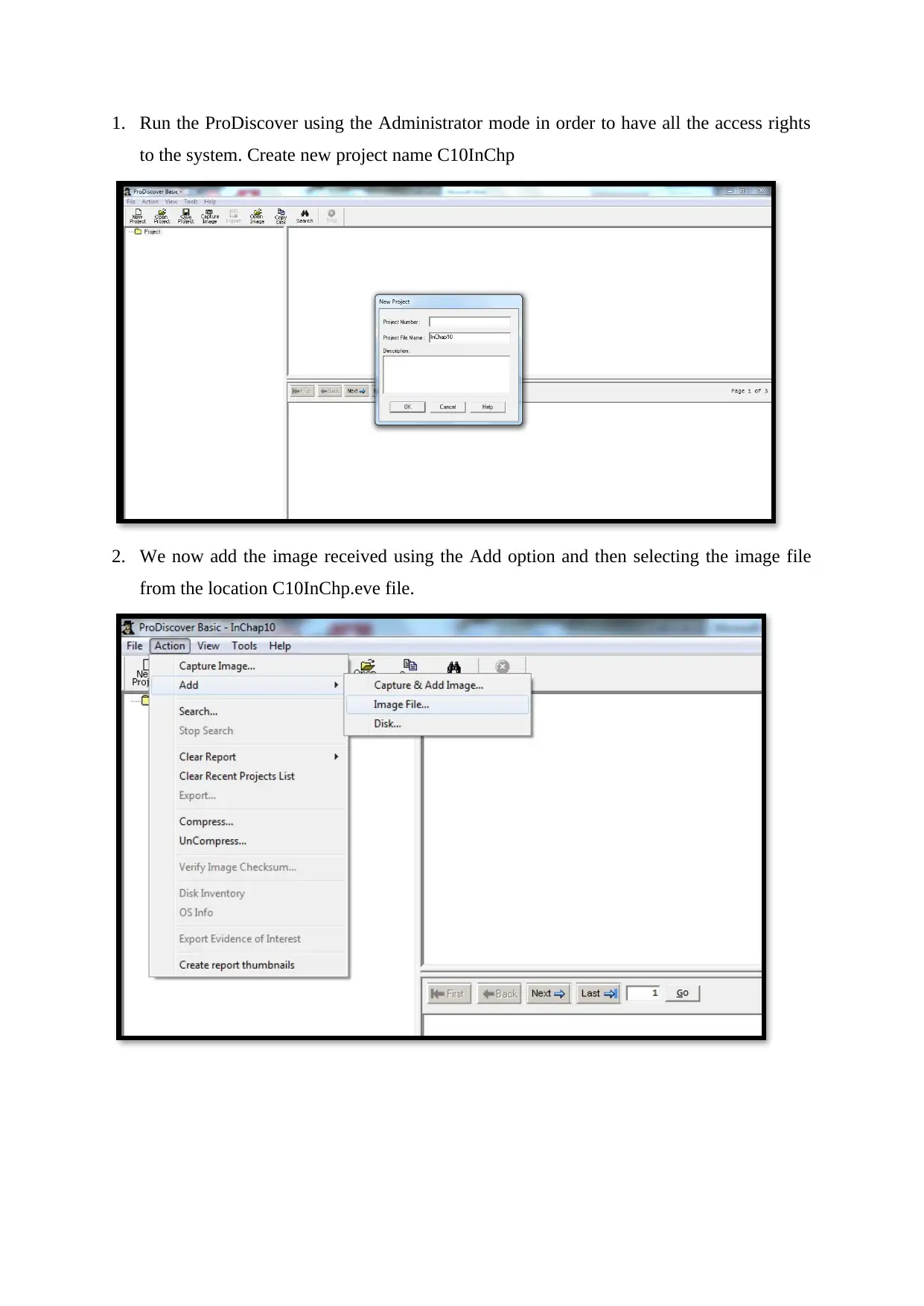
1. Run the ProDiscover using the Administrator mode in order to have all the access rights
to the system. Create new project name C10InChp
2. We now add the image received using the Add option and then selecting the image file
from the location C10InChp.eve file.
to the system. Create new project name C10InChp
2. We now add the image received using the Add option and then selecting the image file
from the location C10InChp.eve file.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
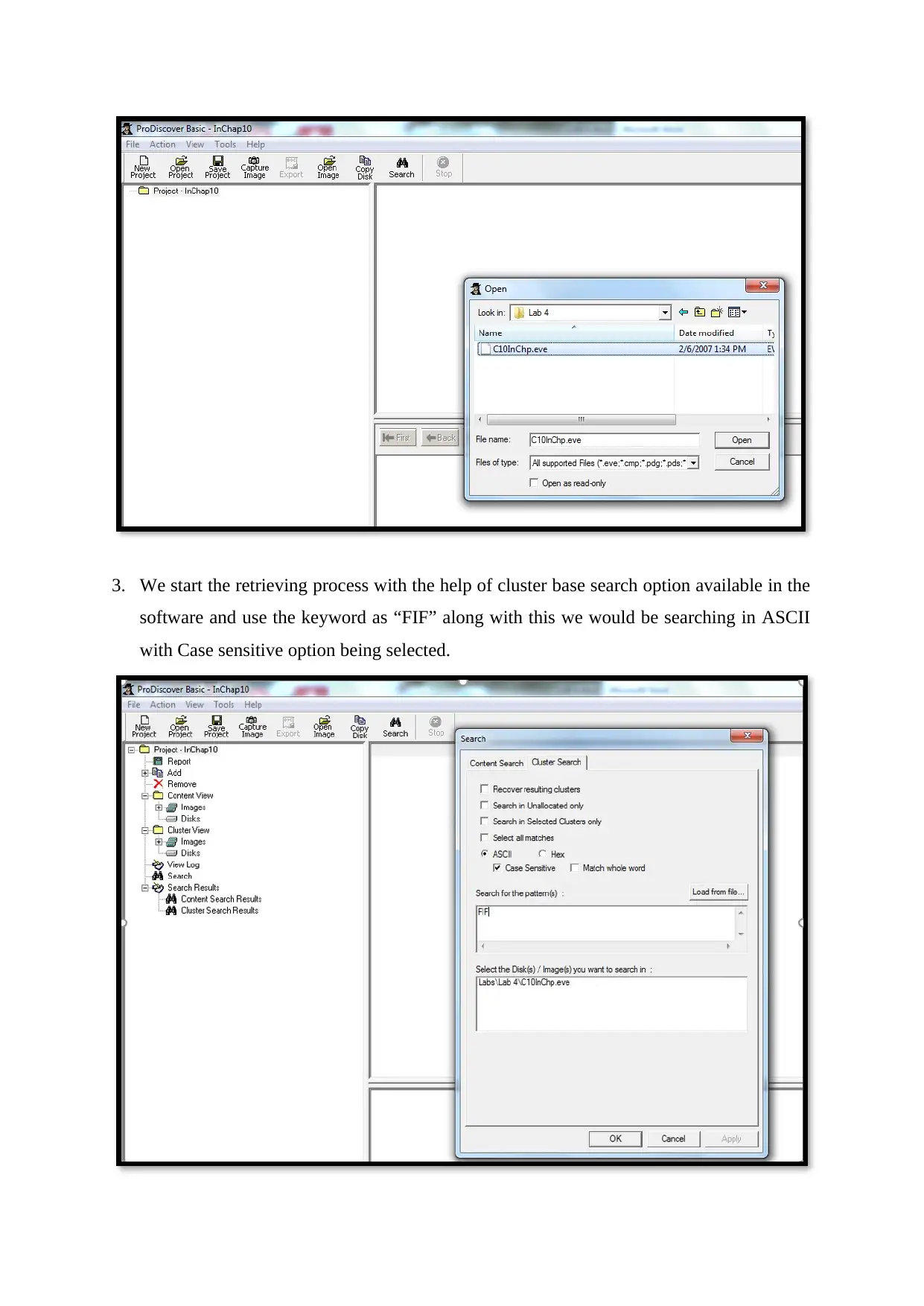
3. We start the retrieving process with the help of cluster base search option available in the
software and use the keyword as “FIF” along with this we would be searching in ASCII
with Case sensitive option being selected.
software and use the keyword as “FIF” along with this we would be searching in ASCII
with Case sensitive option being selected.
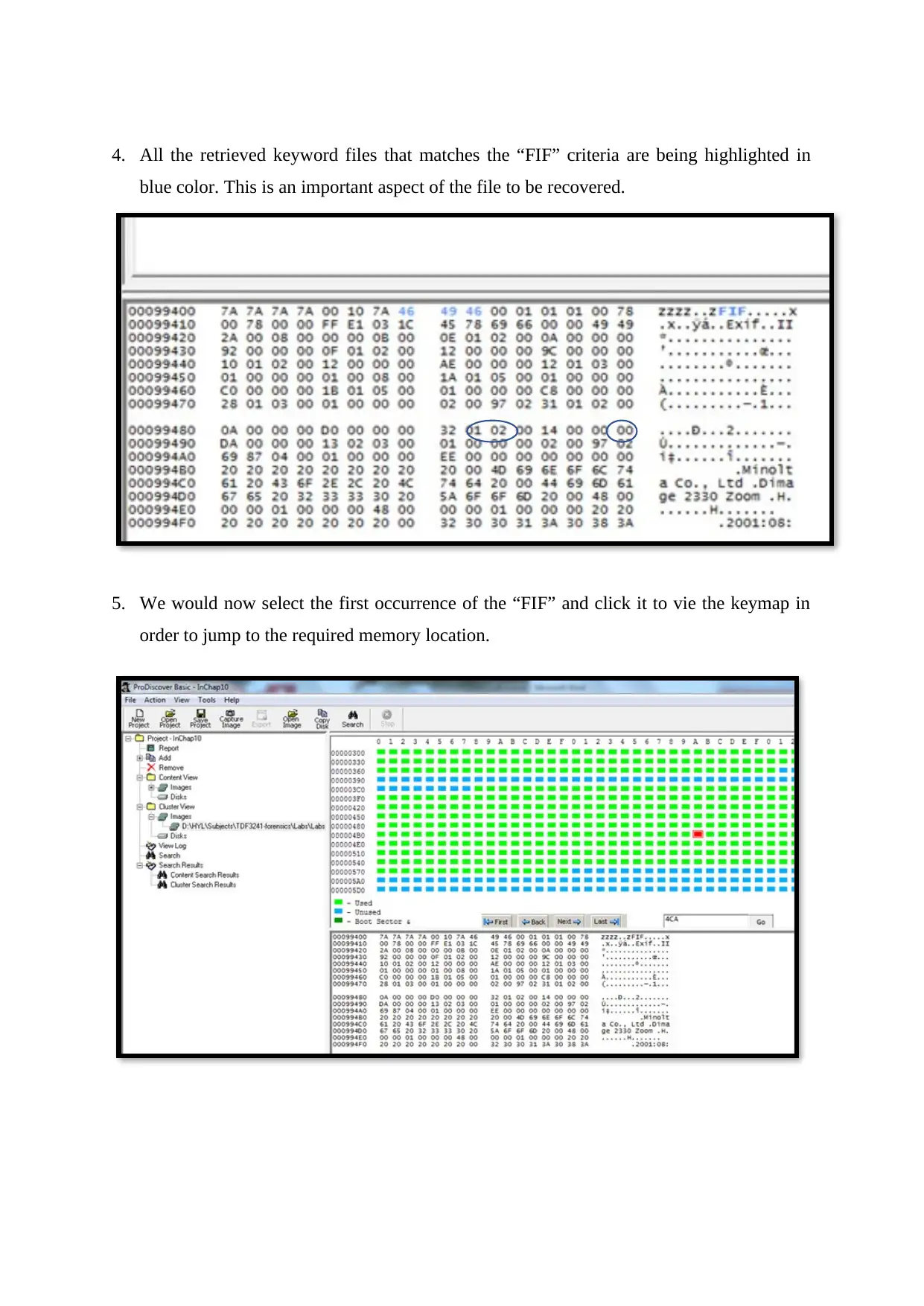
4. All the retrieved keyword files that matches the “FIF” criteria are being highlighted in
blue color. This is an important aspect of the file to be recovered.
5. We would now select the first occurrence of the “FIF” and click it to vie the keymap in
order to jump to the required memory location.
blue color. This is an important aspect of the file to be recovered.
5. We would now select the first occurrence of the “FIF” and click it to vie the keymap in
order to jump to the required memory location.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
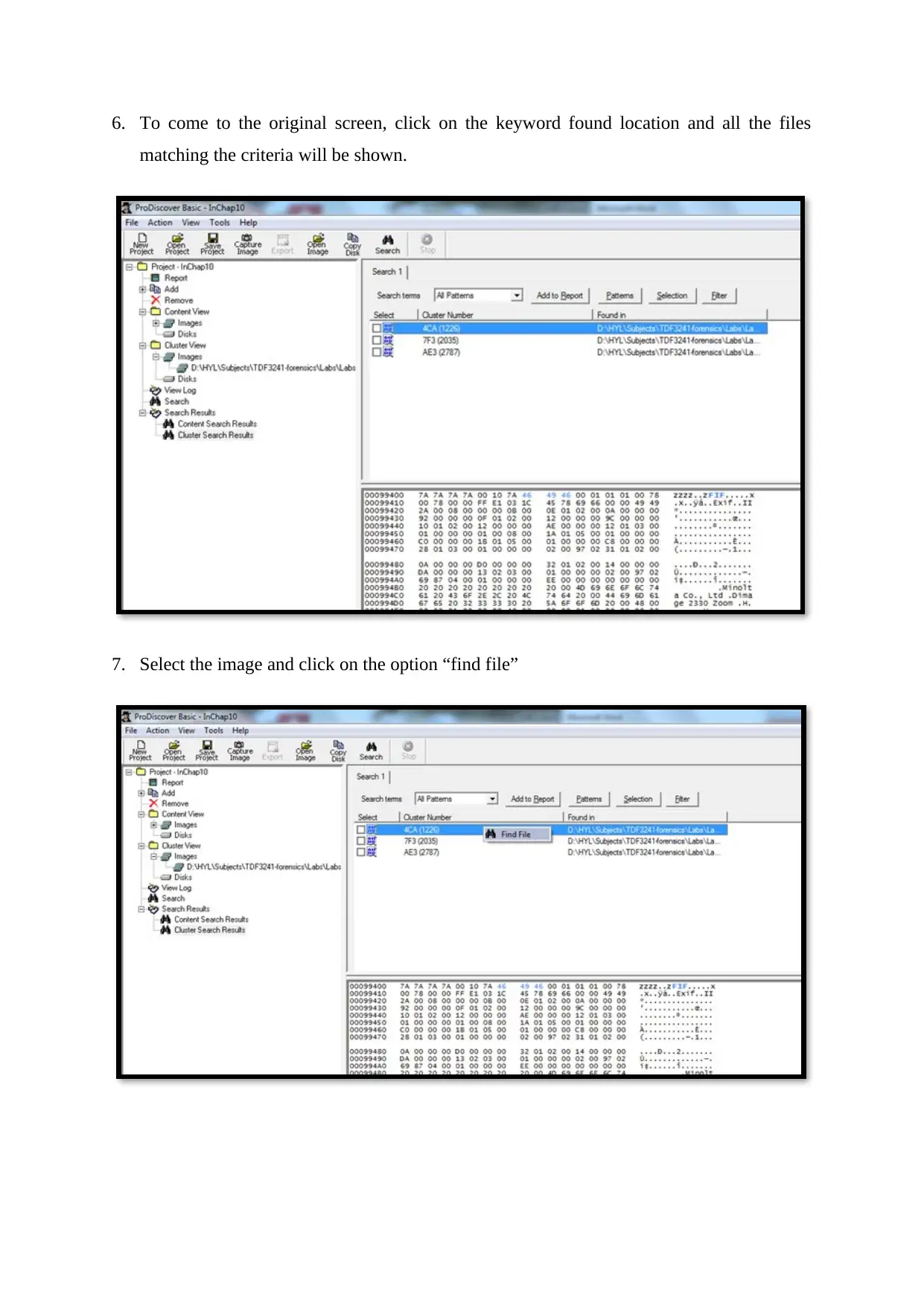
6. To come to the original screen, click on the keyword found location and all the files
matching the criteria will be shown.
7. Select the image and click on the option “find file”
matching the criteria will be shown.
7. Select the image and click on the option “find file”
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
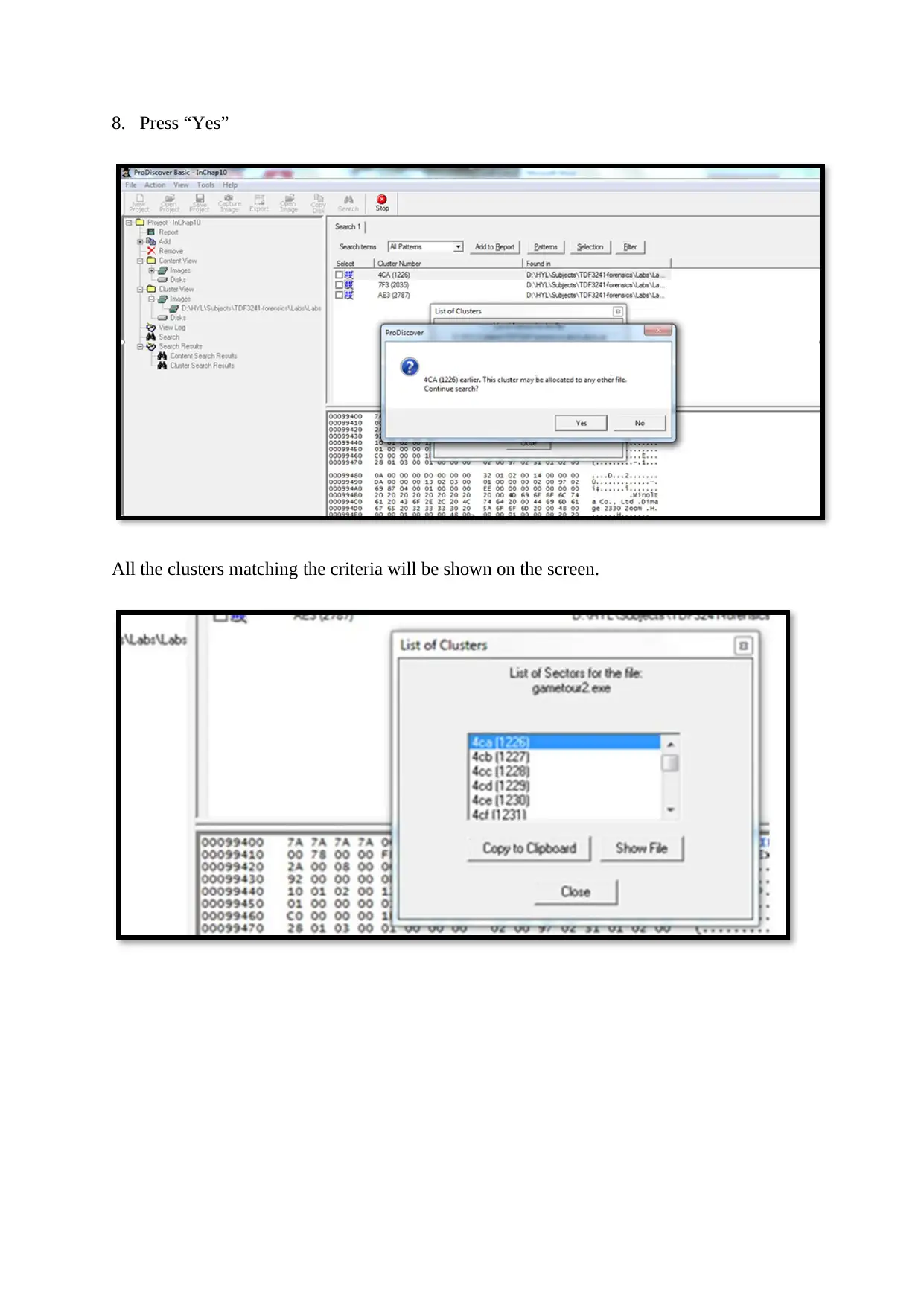
8. Press “Yes”
All the clusters matching the criteria will be shown on the screen.
All the clusters matching the criteria will be shown on the screen.
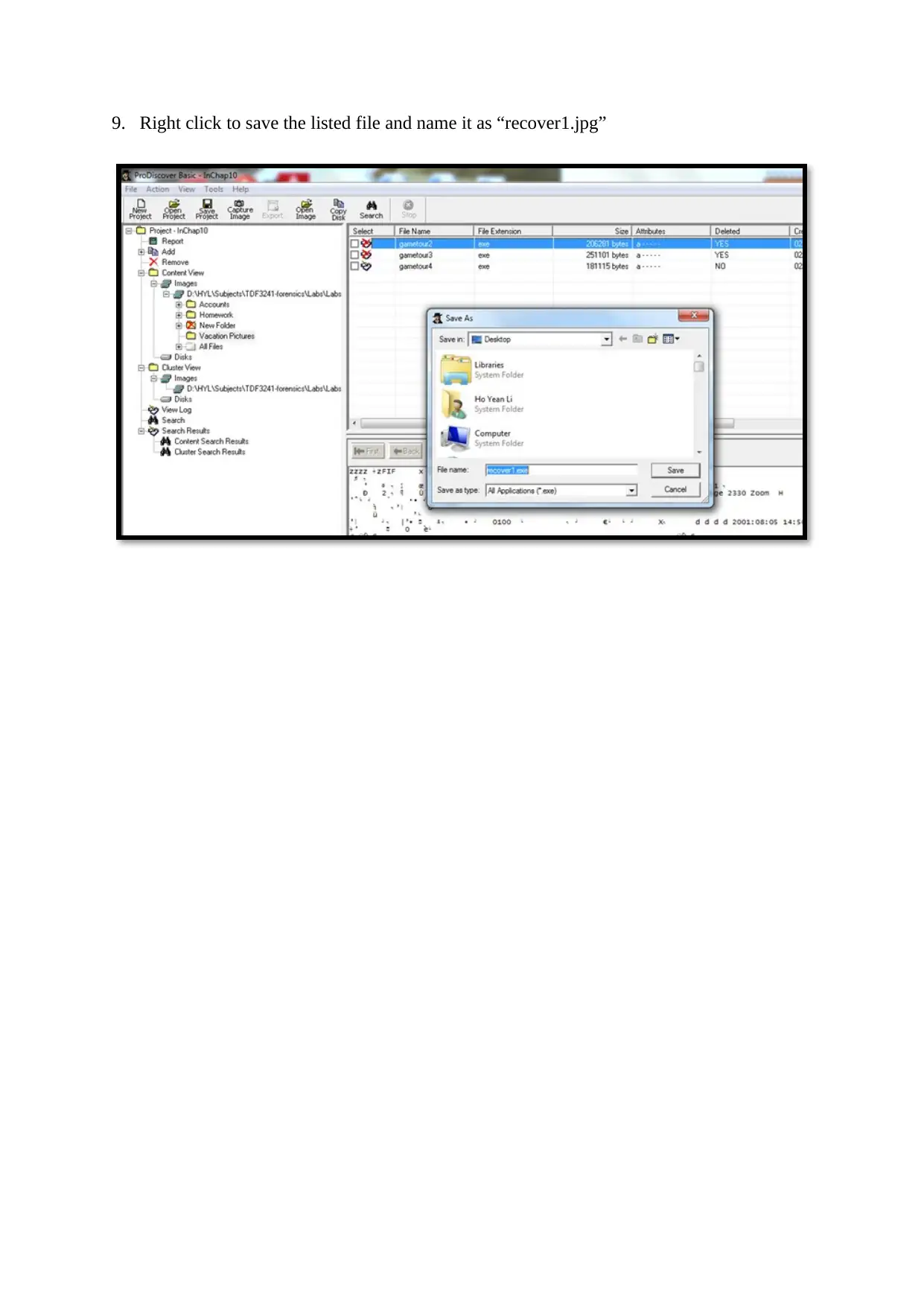
9. Right click to save the listed file and name it as “recover1.jpg”
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 18
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.




