Federation University ITech3215: IPTable Firewall Security Assignment
VerifiedAdded on 2023/03/17
|12
|1725
|76
Practical Assignment
AI Summary
This assignment provides a detailed solution for configuring an IPTable firewall on a Linux system. It covers the installation of IPtables, and configuring the firewall to perform specific security tasks. The assignment addresses several key security aspects, including rejecting all Telnet packets, allowing Telnet remote connections, denying ping requests, rejecting traffic to the MySQL server, blocking incoming traffic to the virtual machine's IP address, and allowing inbound traffic on port 80 while rejecting outbound traffic on the same port. The solution includes the necessary commands, configurations, and screenshots to demonstrate the implementation of each security measure. Finally, the assignment discusses the advantages and disadvantages of using IPTable firewalls, highlighting their cost-effectiveness, transparency, and speed, while also pointing out limitations such as the lack of application layer protocol understanding and the need for user-based authentication. The solution also provides a list of references related to the subject matter.

Assignment 2
Securing system using IPTable firewall
Securing system using IPTable firewall
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Introduction
In the event that you are a broadband Internet client, the most ideal approach to keep malware
out of your PC is to set up an equipment firewall. An equipment firewall is an electronic
thingamajig introduced between the broadband modem and your PC. It's regularly included as a
component of the switch. An equipment switch screens all approaching active Internet traffic.
Most wired and remote switches sold today include a firewall directly out of the container. That is
uplifting news. The better news is that the firewall is in all likelihood arranged impeccably for you;
there's actually minimal left to do. You get to the switch by utilizing the PC's Internet browser to
see the switch's firewall setup screen. At its least complex dimension, the equipment firewall is an
on-off sort of issue. A few switches may highlight a propelled firewall where you can include rules
and such, however much of the time the guidelines are clear: Don't permit in any Internet traffic that
wasn't explicitly mentioned by a PC on the system. This standard basically obstructs all the Bad
Guys from traversing(Voronkov, Iwaya, Martucci, & Lindskog, 2018).
Install IPtables
iptables is an incredible asset used to design the Linux pieces incorporated firewall. It comes
preinstalled on most Ubuntu circulations, in any case in the event that you are utilizing an altered
Ubuntu form or running inside a holder you will undoubtedly need to introduce it physically. After
establishment, in the event that you are approached whether to spare your present standards, it
doesn't make a difference right now since you are going to expel or make new principles
later(Abbes, Bouhoula, & Rusinowitch, 2016).
In the event that you are a broadband Internet client, the most ideal approach to keep malware
out of your PC is to set up an equipment firewall. An equipment firewall is an electronic
thingamajig introduced between the broadband modem and your PC. It's regularly included as a
component of the switch. An equipment switch screens all approaching active Internet traffic.
Most wired and remote switches sold today include a firewall directly out of the container. That is
uplifting news. The better news is that the firewall is in all likelihood arranged impeccably for you;
there's actually minimal left to do. You get to the switch by utilizing the PC's Internet browser to
see the switch's firewall setup screen. At its least complex dimension, the equipment firewall is an
on-off sort of issue. A few switches may highlight a propelled firewall where you can include rules
and such, however much of the time the guidelines are clear: Don't permit in any Internet traffic that
wasn't explicitly mentioned by a PC on the system. This standard basically obstructs all the Bad
Guys from traversing(Voronkov, Iwaya, Martucci, & Lindskog, 2018).
Install IPtables
iptables is an incredible asset used to design the Linux pieces incorporated firewall. It comes
preinstalled on most Ubuntu circulations, in any case in the event that you are utilizing an altered
Ubuntu form or running inside a holder you will undoubtedly need to introduce it physically. After
establishment, in the event that you are approached whether to spare your present standards, it
doesn't make a difference right now since you are going to expel or make new principles
later(Abbes, Bouhoula, & Rusinowitch, 2016).
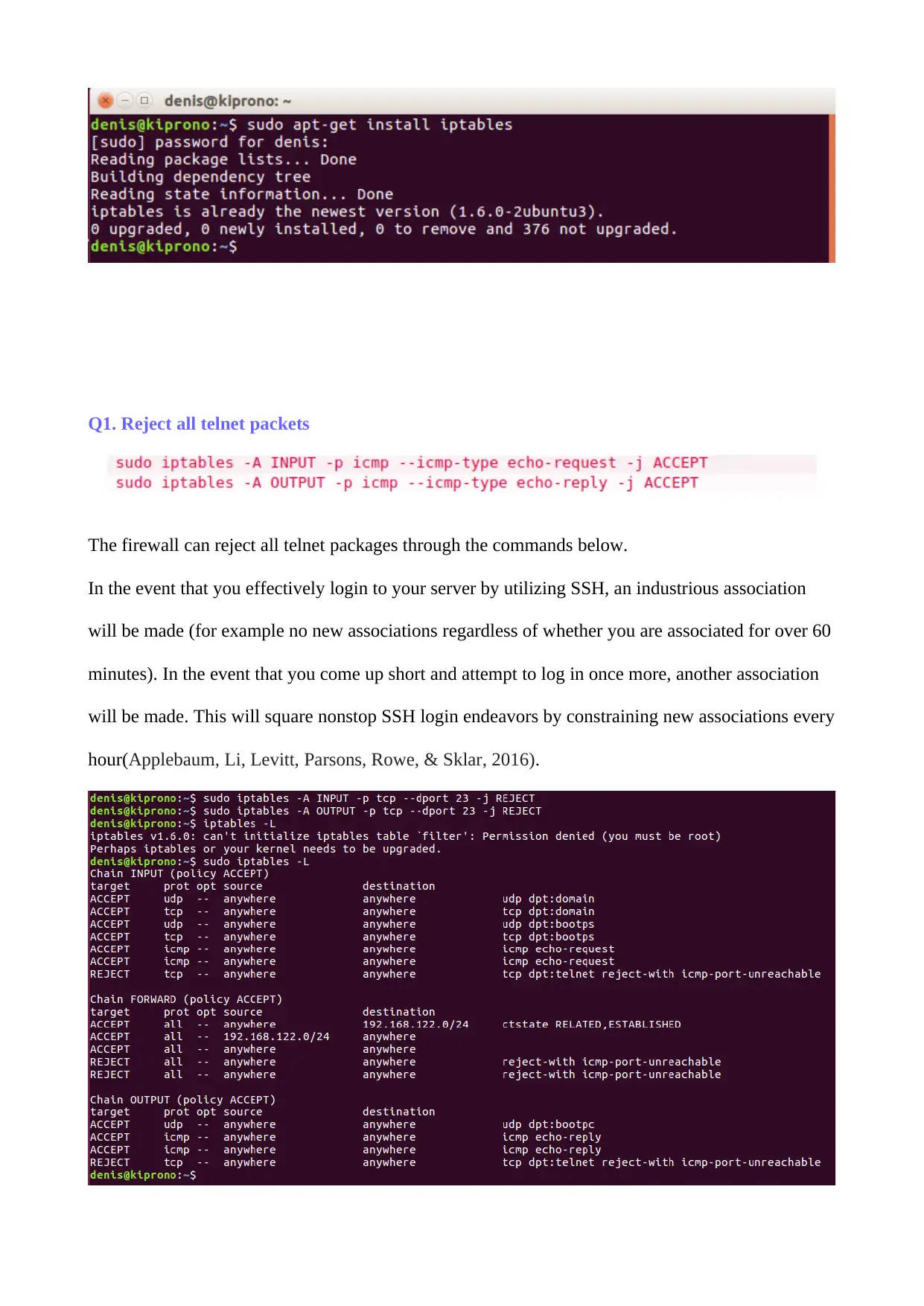
Q1. Reject all telnet packets
The firewall can reject all telnet packages through the commands below.
In the event that you effectively login to your server by utilizing SSH, an industrious association
will be made (for example no new associations regardless of whether you are associated for over 60
minutes). In the event that you come up short and attempt to log in once more, another association
will be made. This will square nonstop SSH login endeavors by constraining new associations every
hour(Applebaum, Li, Levitt, Parsons, Rowe, & Sklar, 2016).
The firewall can reject all telnet packages through the commands below.
In the event that you effectively login to your server by utilizing SSH, an industrious association
will be made (for example no new associations regardless of whether you are associated for over 60
minutes). In the event that you come up short and attempt to log in once more, another association
will be made. This will square nonstop SSH login endeavors by constraining new associations every
hour(Applebaum, Li, Levitt, Parsons, Rowe, & Sklar, 2016).
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
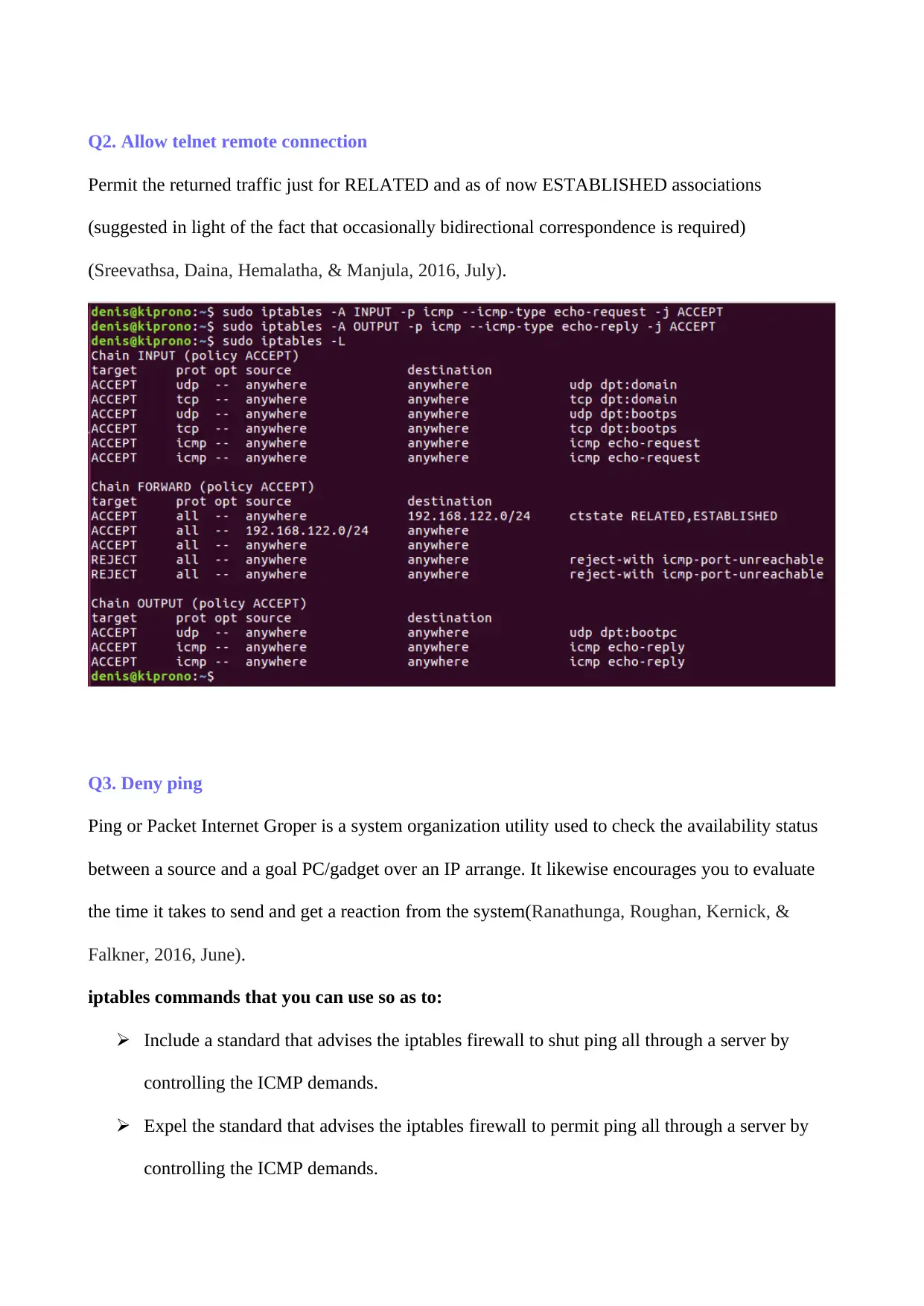
Q2. Allow telnet remote connection
Permit the returned traffic just for RELATED and as of now ESTABLISHED associations
(suggested in light of the fact that occasionally bidirectional correspondence is required)
(Sreevathsa, Daina, Hemalatha, & Manjula, 2016, July).
Q3. Deny ping
Ping or Packet Internet Groper is a system organization utility used to check the availability status
between a source and a goal PC/gadget over an IP arrange. It likewise encourages you to evaluate
the time it takes to send and get a reaction from the system(Ranathunga, Roughan, Kernick, &
Falkner, 2016, June).
iptables commands that you can use so as to:
Include a standard that advises the iptables firewall to shut ping all through a server by
controlling the ICMP demands.
Expel the standard that advises the iptables firewall to permit ping all through a server by
controlling the ICMP demands.
Permit the returned traffic just for RELATED and as of now ESTABLISHED associations
(suggested in light of the fact that occasionally bidirectional correspondence is required)
(Sreevathsa, Daina, Hemalatha, & Manjula, 2016, July).
Q3. Deny ping
Ping or Packet Internet Groper is a system organization utility used to check the availability status
between a source and a goal PC/gadget over an IP arrange. It likewise encourages you to evaluate
the time it takes to send and get a reaction from the system(Ranathunga, Roughan, Kernick, &
Falkner, 2016, June).
iptables commands that you can use so as to:
Include a standard that advises the iptables firewall to shut ping all through a server by
controlling the ICMP demands.
Expel the standard that advises the iptables firewall to permit ping all through a server by
controlling the ICMP demands.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
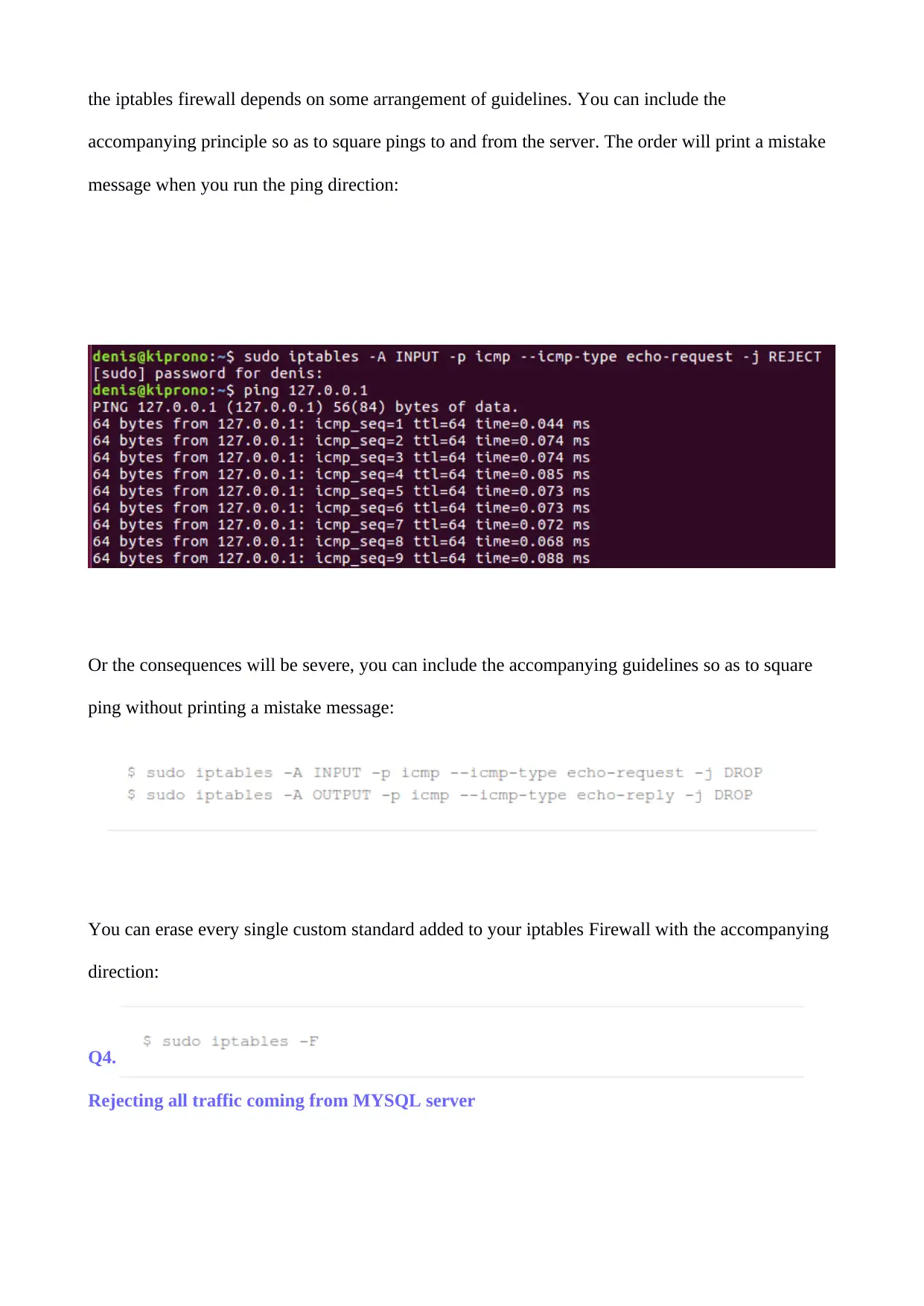
the iptables firewall depends on some arrangement of guidelines. You can include the
accompanying principle so as to square pings to and from the server. The order will print a mistake
message when you run the ping direction:
Or the consequences will be severe, you can include the accompanying guidelines so as to square
ping without printing a mistake message:
You can erase every single custom standard added to your iptables Firewall with the accompanying
direction:
Q4.
Rejecting all traffic coming from MYSQL server
accompanying principle so as to square pings to and from the server. The order will print a mistake
message when you run the ping direction:
Or the consequences will be severe, you can include the accompanying guidelines so as to square
ping without printing a mistake message:
You can erase every single custom standard added to your iptables Firewall with the accompanying
direction:
Q4.
Rejecting all traffic coming from MYSQL server
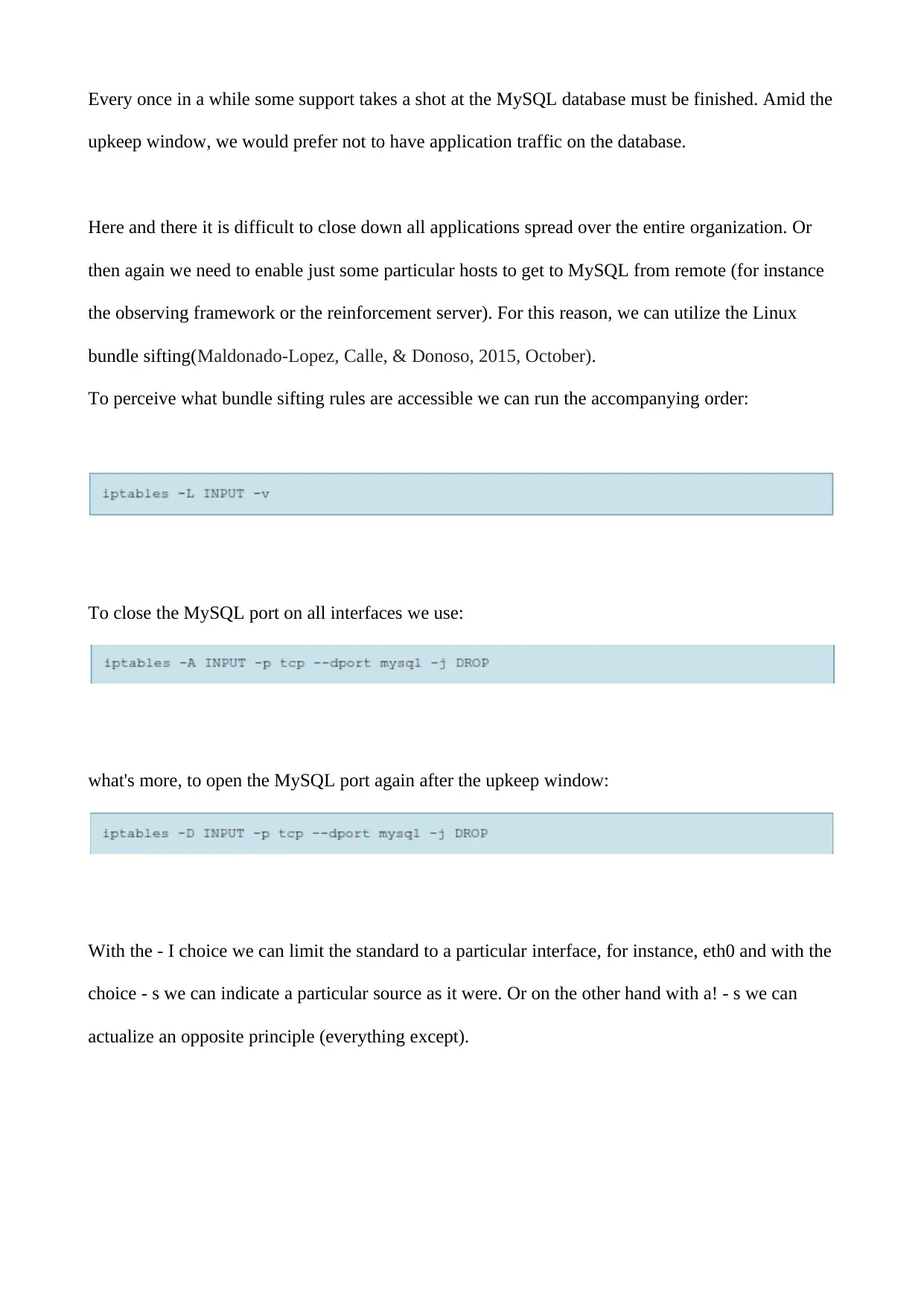
Every once in a while some support takes a shot at the MySQL database must be finished. Amid the
upkeep window, we would prefer not to have application traffic on the database.
Here and there it is difficult to close down all applications spread over the entire organization. Or
then again we need to enable just some particular hosts to get to MySQL from remote (for instance
the observing framework or the reinforcement server). For this reason, we can utilize the Linux
bundle sifting(Maldonado-Lopez, Calle, & Donoso, 2015, October).
To perceive what bundle sifting rules are accessible we can run the accompanying order:
To close the MySQL port on all interfaces we use:
what's more, to open the MySQL port again after the upkeep window:
With the - I choice we can limit the standard to a particular interface, for instance, eth0 and with the
choice - s we can indicate a particular source as it were. Or on the other hand with a! - s we can
actualize an opposite principle (everything except).
upkeep window, we would prefer not to have application traffic on the database.
Here and there it is difficult to close down all applications spread over the entire organization. Or
then again we need to enable just some particular hosts to get to MySQL from remote (for instance
the observing framework or the reinforcement server). For this reason, we can utilize the Linux
bundle sifting(Maldonado-Lopez, Calle, & Donoso, 2015, October).
To perceive what bundle sifting rules are accessible we can run the accompanying order:
To close the MySQL port on all interfaces we use:
what's more, to open the MySQL port again after the upkeep window:
With the - I choice we can limit the standard to a particular interface, for instance, eth0 and with the
choice - s we can indicate a particular source as it were. Or on the other hand with a! - s we can
actualize an opposite principle (everything except).
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
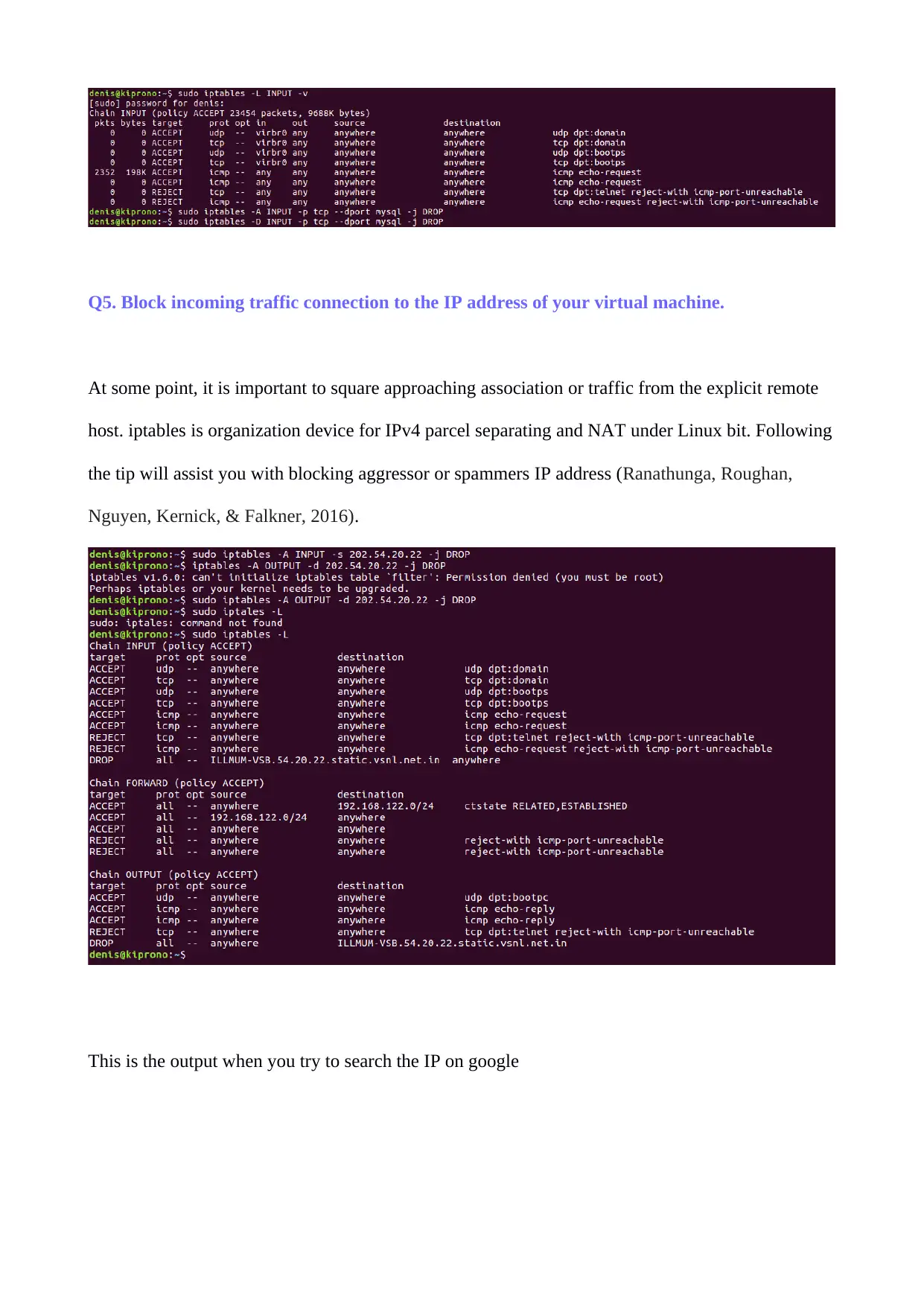
Q5. Block incoming traffic connection to the IP address of your virtual machine.
At some point, it is important to square approaching association or traffic from the explicit remote
host. iptables is organization device for IPv4 parcel separating and NAT under Linux bit. Following
the tip will assist you with blocking aggressor or spammers IP address (Ranathunga, Roughan,
Nguyen, Kernick, & Falkner, 2016).
This is the output when you try to search the IP on google
At some point, it is important to square approaching association or traffic from the explicit remote
host. iptables is organization device for IPv4 parcel separating and NAT under Linux bit. Following
the tip will assist you with blocking aggressor or spammers IP address (Ranathunga, Roughan,
Nguyen, Kernick, & Falkner, 2016).
This is the output when you try to search the IP on google
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
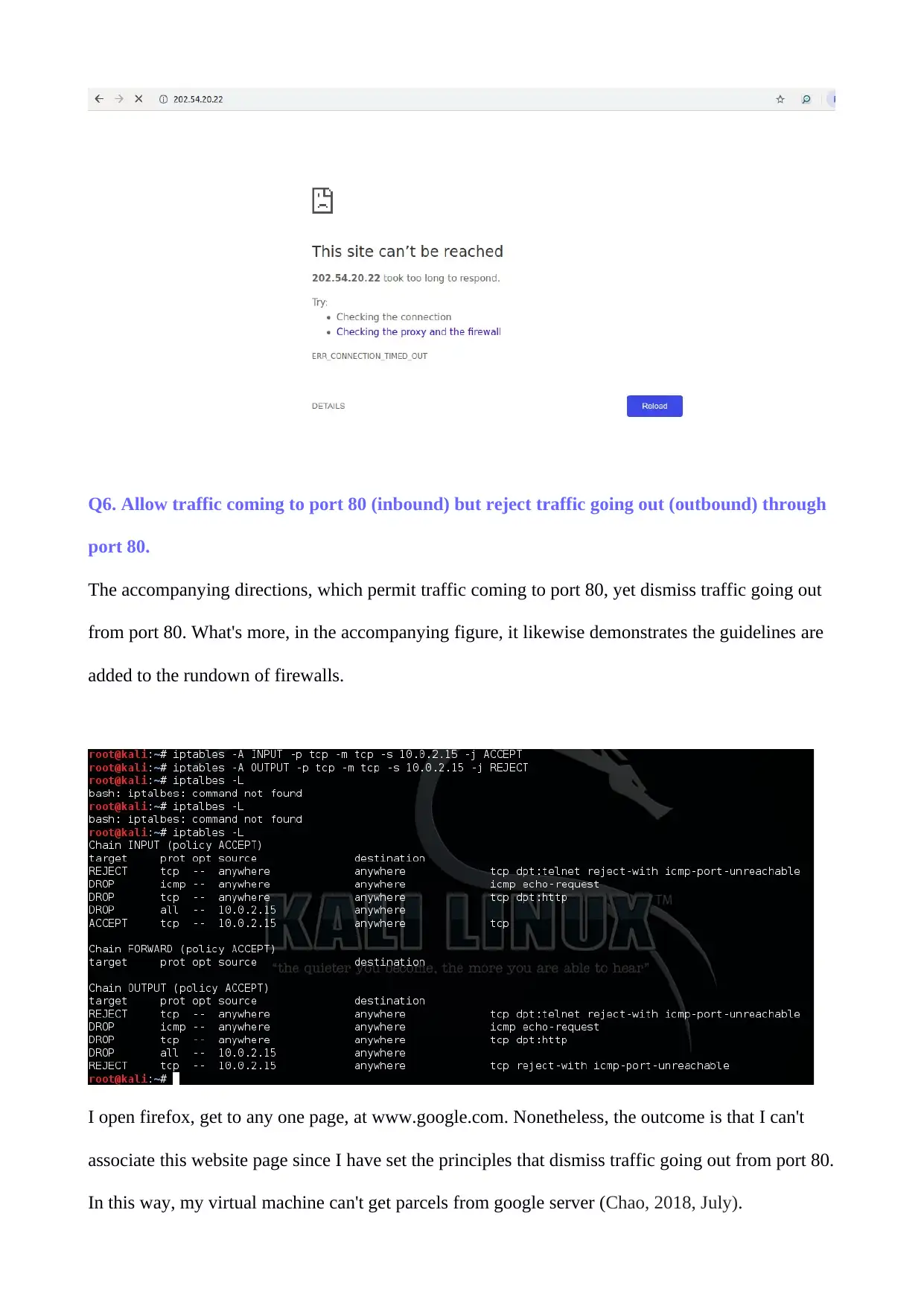
Q6. Allow traffic coming to port 80 (inbound) but reject traffic going out (outbound) through
port 80.
The accompanying directions, which permit traffic coming to port 80, yet dismiss traffic going out
from port 80. What's more, in the accompanying figure, it likewise demonstrates the guidelines are
added to the rundown of firewalls.
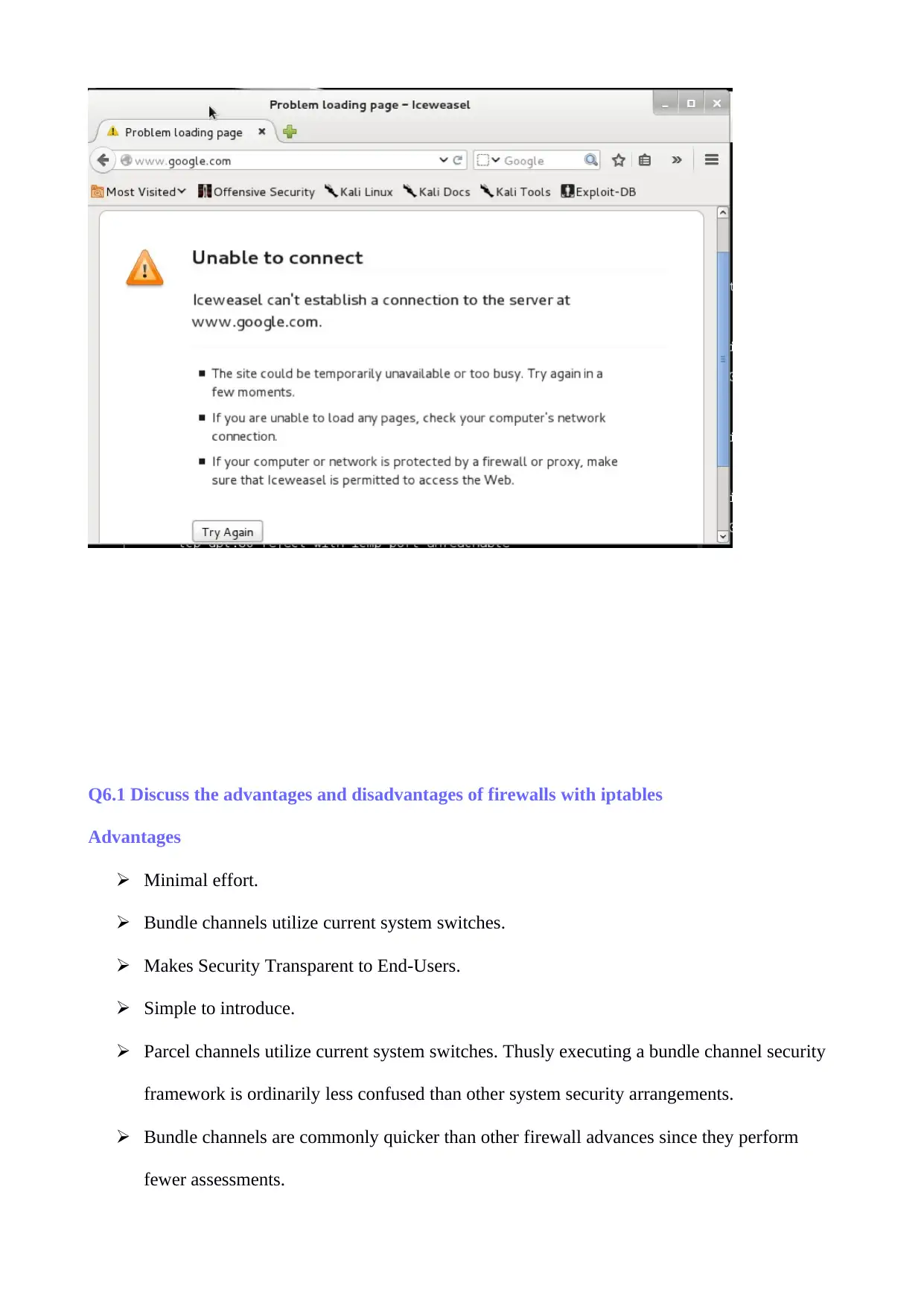
I open firefox, get to any one page, at www.google.com. Nonetheless, the outcome is that I can't
associate this website page since I have set the principles that dismiss traffic going out from port 80.
In this way, my virtual machine can't get parcels from google server (Chao, 2018, July).
port 80.
The accompanying directions, which permit traffic coming to port 80, yet dismiss traffic going out
from port 80. What's more, in the accompanying figure, it likewise demonstrates the guidelines are
added to the rundown of firewalls.
I open firefox, get to any one page, at www.google.com. Nonetheless, the outcome is that I can't
associate this website page since I have set the principles that dismiss traffic going out from port 80.
In this way, my virtual machine can't get parcels from google server (Chao, 2018, July).
Q6.1 Discuss the advantages and disadvantages of firewalls with iptables
Advantages
Minimal effort.
Bundle channels utilize current system switches.
Makes Security Transparent to End-Users.
Simple to introduce.
Parcel channels utilize current system switches. Thusly executing a bundle channel security
framework is ordinarily less confused than other system security arrangements.
Bundle channels are commonly quicker than other firewall advances since they perform
fewer assessments.
Advantages
Minimal effort.
Bundle channels utilize current system switches.
Makes Security Transparent to End-Users.
Simple to introduce.
Parcel channels utilize current system switches. Thusly executing a bundle channel security
framework is ordinarily less confused than other system security arrangements.
Bundle channels are commonly quicker than other firewall advances since they perform
fewer assessments.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Disadvantages
Parcel channels don't comprehend application layer conventions.
Bundle channels do not offer any esteem included highlights, for example, HTTP object
reserving, URL separating, and confirmation since they don't comprehend the conventions
being utilized.
Bundle separating switches are not extremely verified.
Can't separate among great and terrible parcel
New principles might be should have been included if a representative needs unique
necessities to interface with the web.
The trouble of setting up bundle sifting guidelines to the switch
There isn't any kind of client-based Authentication.
Parcel channel can't validate data originating from a particular client.
Suggestions
Improve the precision of test rules.
Look at a more elevated amount of documents or information.
Bundle sifting firewalls need a superior situation for actualizing dynamic standards.
Parcel channels don't comprehend application layer conventions.
Bundle channels do not offer any esteem included highlights, for example, HTTP object
reserving, URL separating, and confirmation since they don't comprehend the conventions
being utilized.
Bundle separating switches are not extremely verified.
Can't separate among great and terrible parcel
New principles might be should have been included if a representative needs unique
necessities to interface with the web.
The trouble of setting up bundle sifting guidelines to the switch
There isn't any kind of client-based Authentication.
Parcel channel can't validate data originating from a particular client.
Suggestions
Improve the precision of test rules.
Look at a more elevated amount of documents or information.
Bundle sifting firewalls need a superior situation for actualizing dynamic standards.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Reference
Voronkov, A., Iwaya, L. H., Martucci, L. A., & Lindskog, S. (2018). Systematic literature review
on
the usability of firewall configuration. ACM Computing Surveys (CSUR), 50(6), 87.
Abbes, T., Bouhoula, A., & Rusinowitch, M. (2016). Detection of firewall configuration errors with
updatable tree. International Journal of Information Security, 15(3), 301-317.
Applebaum, A., Li, Z., Levitt, K., Parsons, S., Rowe, J., & Sklar, E. I. (2016). Firewall
configuration: An application of multiagent metalevel argumentation. Argument &
Computation, 7(2-3), 201-221.
Voronkov, A., Iwaya, L. H., Martucci, L. A., & Lindskog, S. (2018). Systematic literature review
on
the usability of firewall configuration. ACM Computing Surveys (CSUR), 50(6), 87.
Abbes, T., Bouhoula, A., & Rusinowitch, M. (2016). Detection of firewall configuration errors with
updatable tree. International Journal of Information Security, 15(3), 301-317.
Applebaum, A., Li, Z., Levitt, K., Parsons, S., Rowe, J., & Sklar, E. I. (2016). Firewall
configuration: An application of multiagent metalevel argumentation. Argument &
Computation, 7(2-3), 201-221.

Sreevathsa, C. V., Daina, K. K., Hemalatha, K. L., & Manjula, K. (2016, July). Increasing the
performance of the firewall by providing customized policies. In 2016 2nd International
Conference on Applied and Theoretical Computing and Communication Technology
(iCATccT) (pp. 561-564). IEEE.
Ranathunga, D., Roughan, M., Kernick, P., & Falkner, N. (2016, June). Malachite: Firewall policy
comparison. In 2016 IEEE Symposium on Computers and Communication (ISCC)(pp. 310-
317). IEEE.
Maldonado-Lopez, F. A., Calle, E., & Donoso, Y. (2015, October). Detection and prevention
firewall-rule conflicts on software-defined networking. In 2015 7th International
Workshop on Reliable Networks Design and Modeling (RNDM) (pp. 259-265). IEEE.
Ranathunga, D., Roughan, M., Nguyen, H., Kernick, P., & Falkner, N. (2016). Case studies of scada
firewall configurations and the implications for best practices. IEEE Transactions on
Network and Service Management, 13(4), 871-884.
Chao, C. S. (2018, July). A Feasible Anomaly Diagnosis Mechanism for Stateful Firewall Rules.
In 2018 27th International Conference on Computer Communication and Networks
(ICCCN) (pp. 1-2). IEEE.
performance of the firewall by providing customized policies. In 2016 2nd International
Conference on Applied and Theoretical Computing and Communication Technology
(iCATccT) (pp. 561-564). IEEE.
Ranathunga, D., Roughan, M., Kernick, P., & Falkner, N. (2016, June). Malachite: Firewall policy
comparison. In 2016 IEEE Symposium on Computers and Communication (ISCC)(pp. 310-
317). IEEE.
Maldonado-Lopez, F. A., Calle, E., & Donoso, Y. (2015, October). Detection and prevention
firewall-rule conflicts on software-defined networking. In 2015 7th International
Workshop on Reliable Networks Design and Modeling (RNDM) (pp. 259-265). IEEE.
Ranathunga, D., Roughan, M., Nguyen, H., Kernick, P., & Falkner, N. (2016). Case studies of scada
firewall configurations and the implications for best practices. IEEE Transactions on
Network and Service Management, 13(4), 871-884.
Chao, C. S. (2018, July). A Feasible Anomaly Diagnosis Mechanism for Stateful Firewall Rules.
In 2018 27th International Conference on Computer Communication and Networks
(ICCCN) (pp. 1-2). IEEE.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 12
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.


